Most organizations implement application security reactively—patching vulnerabilities after pen tests reveal them, scrambling to address findings before sales cycles close, treating security verification as a pre-deployment checklist rather than an ongoing discipline. This approach creates a fundamental gap between security theater and actual protection. The gap becomes apparent when enterprises scrutinize vendor security postures, when auditors demand evidence of systematic controls, or when breaches expose the difference between documented policies and implemented defenses.
What is OWASP ASVS?
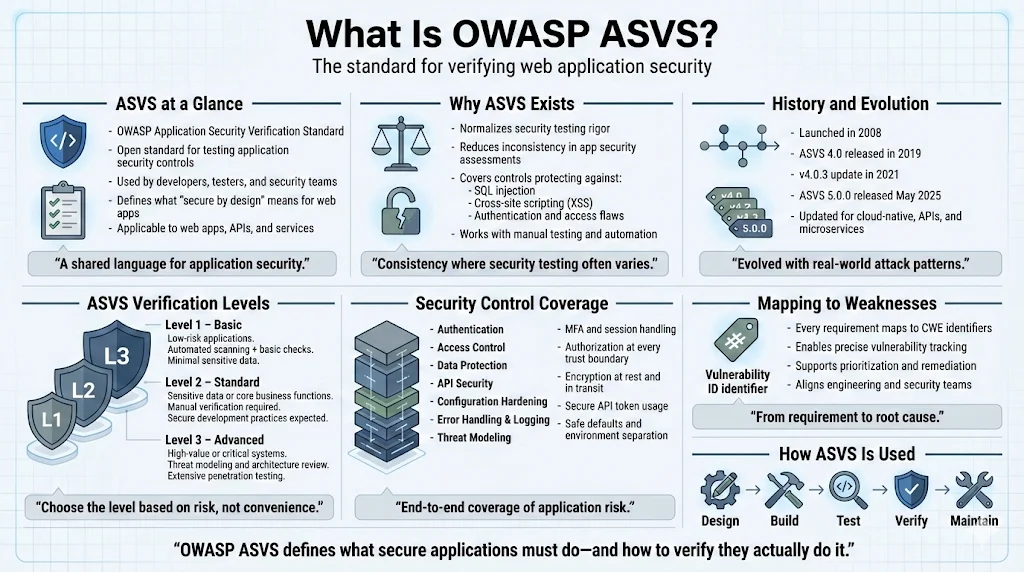
The OWASP Application Security Verification Standard (ASVS) provides a basis for testing web application technical security controls and provides developers with a list of requirements for secure development. Originally launched in 2008 through a global community collaboration, the ASVS defines a comprehensive set of security requirements for designing, developing, and testing modern web applications and services.
ASVS normalizes the range in coverage and level of rigor available in the market when performing web application security verification using a commercially-workable open standard. The standard provides a basis for testing application technical security controls, as well as any technical security controls in the environment, that are relied on to protect against vulnerabilities such as Cross-Site Scripting (XSS) and SQL injection.
History and Development
ASVS has evolved significantly since its 2008 inception. Following the release of ASVS 4.0 in 2019 and its minor update (v4.0.3) in 2021, Version 5.0 represents a significant milestone—modernized to reflect the latest advances in software security. The latest stable version is version 5.0.0 (dated May 2025). This continuous evolution reflects real-world implementation experience across thousands of organizations and addresses emerging attack vectors as application architectures shift toward cloud-native deployments, microservices, and API-driven integrations.
The development process involves extensive community collaboration. The ASVS Working Group consists of Shanni Prutchi, Ralph Andalis, Meghan Jacquot, Iman Sharafaldin, Ryan Armstrong, Gabriel Corona, Tobias Ahnoff, and Eden Yardeni. This global expertise ensures the standard remains technically accurate, implementable across diverse technology stacks, and aligned with actual security threats organizations face.
Core Components of ASVS
Levels of ASVS
ASVS employs a three-tiered verification model addressing different security postures and risk profiles. Level 1 targets applications with minimal security requirements—basic protection against common vulnerabilities through automated scanning and straightforward manual verification. Level 2 addresses applications handling sensitive data or implementing critical business functions, requiring thorough manual verification of security controls and evidence of secure coding practices throughout development. Level 3 applies to applications demanding the highest security assurance—critical infrastructure, high-value transactions, or systems protecting highly sensitive data—requiring comprehensive security architecture review, extensive penetration testing, and documented threat modeling.
Organizations select verification levels based on data sensitivity, regulatory requirements, threat landscape, and business criticality. An internal HR system might target Level 1, while a customer-facing payment platform requires Level 2, and a financial trading system demands Level 3 verification.
Security Controls and Requirements
ASVS is divided into 14 chapters, including areas like Authentication, Access Control, Data Protection, API Security, Configuration Hardening, and Threat Modeling. These chapters systematically address the control domains required for comprehensive application security. Authentication requirements specify password complexity, multi-factor authentication implementation, session token generation, and credential recovery mechanisms. Access control requirements mandate authorization checks at every trust boundary, principle of least privilege enforcement, and protection against insecure direct object references.
Data protection requirements encompass encryption at rest and in transit, key management practices, and protection of sensitive data in logs and error messages. API security requirements address input validation, rate limiting, authentication token management, and protection against injection attacks. Configuration requirements mandate secure defaults, separation of environments, and removal of unnecessary features or administrative interfaces.
Each requirement maps to Common Weakness Enumeration (CWE) identifiers, enabling precise vulnerability tracking and remediation prioritization. Every requirement consists of a description of 1-3 sentences and an ID of specific Common Weakness Enumeration (CWE)—a list of common software and hardware security weaknesses, maintained by the MITRE Corporation.
The Purpose of OWASP ASVS
Ensuring Comprehensive Security Verification
ASVS transforms security verification from ad-hoc testing into systematic validation across the software development lifecycle. Rather than discovering authentication bypass vulnerabilities during pre-production penetration tests, ASVS requirements guide architects toward secure session management during design, direct developers to implement proper token generation during development, and provide testers with specific verification criteria before deployment. This systematic approach prevents the pattern where security becomes a gate that projects rush through rather than a discipline integrated throughout development.
Risk Management
ASVS enables risk-based security prioritization by categorizing requirements across three verification levels and mapping each requirement to specific CWEs with documented exploit patterns. Security managers can quantify residual risk by identifying which requirements remain unimplemented, assess the potential impact using CWE severity ratings, and prioritize remediation based on business context rather than arbitrary severity scores from scanning tools.
Organizations operating multiple applications use ASVS to establish consistent security baselines while allowing targeted investment where risk justifies it. A startup's internal tool might target Level 1 with documented exceptions, while its customer-facing application achieves Level 2 verification before enterprise sales engagements. This differentiated approach allocates security resources based on actual risk rather than applying uniform controls regardless of business impact.
Enhancing Application Security
ASVS bridges the gap between security theory and implementation practice. Rather than general guidance to "implement secure authentication," ASVS provides verifiable requirements: generate new session tokens after authentication state changes, invalidate existing sessions during privilege escalation, implement absolute session timeouts regardless of activity. Developers gain specific implementation targets. Security reviewers gain objective verification criteria. Auditors gain evidence that controls exist and function as intended.
ASVS requirements highlight critical controls like the need to generate a new session token upon user authentication, preventing session fixation attacks. This specificity prevents the scenario where organizations believe they've implemented session management because sessions exist, while fundamental protections remain absent.
Compliance Framework
While ASVS itself is not a regulatory requirement, it directly supports compliance with frameworks that mandate application security controls. PCI-DSS Requirement 6 mandates secure development practices and regular security testing—ASVS Level 2 provides specific verification criteria satisfying these requirements. GDPR requires appropriate technical measures protecting personal data—ASVS data protection and cryptography requirements demonstrate these measures. ISO 27001 Annex A controls require secure development—ASVS documentation serves as evidence during certification audits.
Organizations pursuing SOC 2 certification reference ASVS requirements when documenting security controls, map ASVS verification results to trust services criteria, and provide ASVS compliance evidence during audit preparation. This approach transforms application security from subjective assessment into documented, verifiable implementation of recognized standards.
Real-World Importance of OWASP ASVS
Relevance to Enterprise Clients
Enterprise procurement increasingly demands evidence of systematic security practices before vendor approval. Security questionnaires no longer accept assertions that "we take security seriously"—they require documented security testing methodology, evidence of vulnerability management processes, and demonstrated implementation of recognized security standards. Organizations citing ASVS Level 2 compliance provide concrete evidence: systematic verification against 267 specific security requirements, documented evidence for each control, and annual reassessment maintaining security posture over time.
This documented approach accelerates enterprise sales cycles. Rather than extended security reviews where enterprise security teams perform independent assessments, ASVS compliance provides recognized baseline verification. Sales engineering teams reference specific ASVS requirements when addressing security questions. Procurement teams verify ASVS assessment reports rather than conducting duplicate security evaluations. This shared framework reduces friction in vendor security assessment while maintaining rigorous standards.
ASVS and Penetration Testing
Leveraging ASVS for deriving security test cases creates a common theme across all stages of the software development lifecycle. Penetration testers use ASVS requirements as structured test plans—rather than exploratory testing that might miss systematic control gaps, ASVS ensures comprehensive coverage across all security domains. Authentication testing verifies session token randomness, timeout implementation, and privilege escalation protections. Access control testing validates authorization checks at every endpoint, tests for horizontal and vertical privilege escalation, and confirms proper resource isolation.
This systematic approach produces actionable findings. Rather than generic recommendations to "improve authentication," penetration test reports cite specific ASVS requirements that remain unimplemented, reference the associated CWE for context, and map findings to verification levels indicating remediation priority. Development teams receive clear implementation guidance. Security teams track remediation against specific requirements rather than subjective assessments of fix adequacy.
Improving Secure Coding Practices
Developers implementing ASVS requirements gain specific, testable security criteria integrated into feature development rather than addressed through post-development remediation. During authentication implementation, developers reference ASVS session management requirements—implementing proper token generation, secure cookie attributes, and session invalidation from the initial implementation rather than retrofitting these controls after security testing identifies gaps.
This shift-left approach dramatically reduces remediation costs and timeline impact. Organizations implementing ASVS on Level 2 verify compliance through penetration testing and internal security team audit based on a self-assessment sheet with acceptable comments confirming each requirement. Security becomes a development criterion rather than a deployment gate, preventing the cycle where features are code-complete but fail security review, requiring rework that impacts release schedules and team velocity.
OWASP ASVS in the Software Development Lifecycle
ASVS provides security requirements at every SDLC phase. During architecture and design, teams reference ASVS requirements for threat modeling—identifying which components handle sensitive data, where authentication boundaries exist, and which verification level each component requires. During development, ASVS requirements guide implementation decisions and inform code review criteria. During testing, ASVS provides specific verification procedures. During deployment, ASVS configuration requirements ensure secure environment setup.
Additionally, ASVS compliance checks are performed annually, ensuring the system remains aligned with the standard over time. This continuous verification prevents security regression as applications evolve, new features are added, and architectures change. Organizations document initial ASVS verification, track changes that might affect security controls, and reverify at regular intervals or after significant modifications.
Case Studies and Implementation Examples
Organizations implementing ASVS report measurable security improvements. Implementation teams working on microservice-based systems deployed on Kubernetes with React UIs and Scala backends—mature projects around 3 years old already developed with application security in mind—still identify significant control gaps during systematic ASVS verification. This demonstrates that even security-conscious development teams benefit from systematic verification against comprehensive requirements rather than relying on general security awareness.
Financial services organizations use ASVS Level 2 as baseline requirements for customer-facing applications, SaaS vendors target ASVS Level 2 for enterprise sales enablement, and healthcare technology companies map HIPAA technical safeguards to ASVS requirements for systematic compliance verification. These implementations demonstrate ASVS applicability across industries, technology stacks, and organizational sizes.
How to Implement OWASP ASVS in Your Organization
Step-by-Step Guide for Security Managers
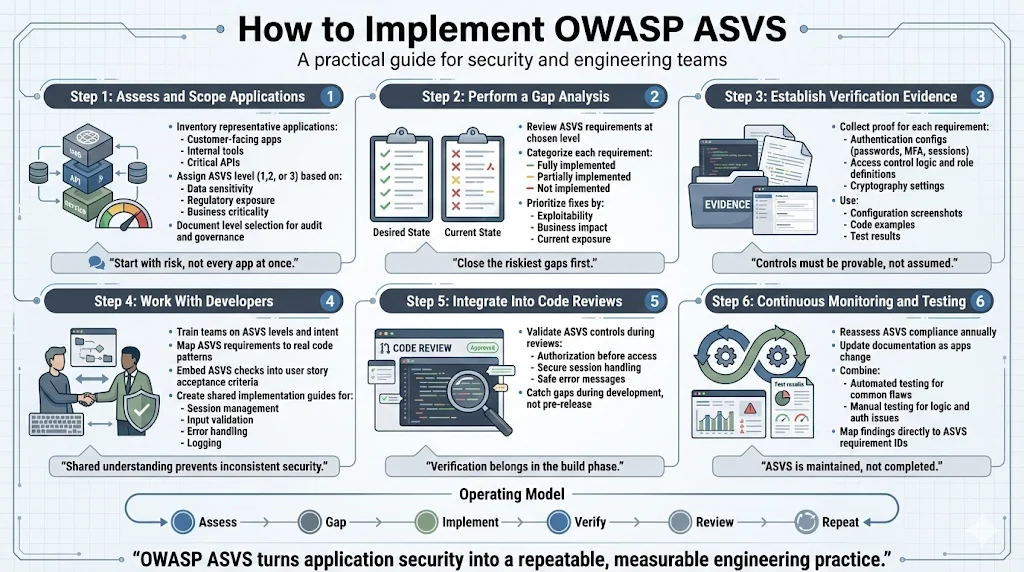
Begin implementation by assessing current security posture against ASVS requirements. Select representative applications across different risk profiles—customer-facing applications handling sensitive data, internal tools with limited external exposure, and APIs providing critical business functions. For each application, determine appropriate verification level based on data sensitivity, regulatory requirements, and business criticality. Document this risk-based level selection as it demonstrates mature security governance to auditors and enterprise customers.
Conduct gap analysis by systematically reviewing each ASVS requirement at the selected verification level against current implementation. Document which requirements are fully implemented with verifiable evidence, which are partially implemented requiring enhancement, and which are not implemented requiring new controls. Prioritize remediation based on current vulnerability exposure, exploitation complexity, and business impact rather than attempting comprehensive implementation across all requirements simultaneously.
Establish verification processes documenting evidence for each implemented requirement. Authentication requirements require evidence of password policies, multi-factor authentication configuration, and session management implementation. Access control requirements require evidence of authorization checks, role definitions, and privilege management. Collect this evidence systematically—configuration screenshots, code samples demonstrating control implementation, and test results verifying control effectiveness.
Collaborating with Developers
Security managers and development teams must establish a shared understanding of ASVS requirements and their implementation. Conduct training sessions explaining verification levels, walking through representative requirements from each chapter, and demonstrating how requirements map to actual code. Integrate ASVS requirements into user story acceptance criteria—authentication features include ASVS session management requirements, API endpoints include ASVS input validation requirements, and data handling includes ASVS cryptography requirements.
Create implementation guides for common requirements across applications. Rather than individual developers interpreting requirements independently, document organizational approaches to session management, input validation, error handling, and logging that satisfy ASVS requirements while remaining consistent with technology stack and architecture patterns. These guides accelerate implementation while ensuring consistent application of controls across development teams.
Incorporate ASVS verification into code review processes. Reviewers validate that authentication implementation includes proper session token generation, access control logic performs authorization checks before resource access, and error handling avoids information disclosure. This systematic review identifies control gaps during development rather than during pre-deployment security testing.
Continuous Monitoring and Testing
ASVS compliance requires ongoing verification as applications evolve. Establish annual reassessment cycles reviewing each ASVS requirement against current implementation, identifying changes affecting security controls, and updating documentation reflecting current state. This systematic reassessment prevents security regression as features are added, dependencies are updated, and architectures evolve.
Integrate ASVS requirements into continuous security testing. Automated security testing verifies input validation, authentication bypass protections, and configuration security. Manual testing validates business logic security, authorization controls, and complex authentication flows. Map testing results to specific ASVS requirements—rather than generic vulnerability reports, teams receive findings indicating which ASVS requirements remain unsatisfied and what implementation changes satisfy those requirements.
ASVS vs. Other OWASP Projects
OWASP ASVS vs. OWASP Top 10
The OWASP Top 10 and ASVS serve complementary but distinct purposes. The OWASP Top 10 identifies the most critical security risks based on prevalence and impact—providing awareness of common vulnerability categories like injection flaws, broken authentication, and sensitive data exposure. It functions as an awareness document highlighting what risks to prioritize.
ASVS provides comprehensive verification requirements addressing these risks and extending far beyond them. While the OWASP Top 10 identifies broken authentication as a critical risk, ASVS provides 30+ specific requirements verifying authentication implementation—password strength requirements, multi-factor authentication implementation, session management controls, and credential recovery mechanisms. Organizations use the Top 10 for risk awareness and ASVS for systematic verification that controls addressing those risks are properly implemented.
It is better to refer to more detailed standards, such as OWASP ASVS for requirements or OWASP SAMM for program maturity, and keep the Top 10 as context. Procurement requirements should reference ASVS verification levels rather than vague "OWASP Top 10 compliance" that lacks clear verification criteria.
OWASP ASVS vs. SAMM
OWASP Software Assurance Maturity Model (SAMM) and ASVS operate at different organizational levels. SAMM assesses organizational security program maturity across governance, design, implementation, verification, and operations. It evaluates whether organizations have established security policies, conduct threat modeling, implement secure coding training, perform security testing, and maintain incident response capabilities.
ASVS focuses specifically on application-level security controls—whether individual applications correctly implement authentication, properly validate input, adequately protect sensitive data, and securely configure environments. Organizations use SAMM to build security programs and ASVS to verify that programs produce secure applications.
Mature security programs use both frameworks complementarily. SAMM assessment identifies program gaps—lack of threat modeling process, inadequate security testing, or insufficient secure coding training. SAMM improvement roadmap addresses these organizational gaps. ASVS verification confirms that improved processes produce applications meeting specific security requirements. This combination ensures both program maturity and application security outcomes.
Security Testing and Verification
How ASVS Guides Security Testing
ASVS transforms security testing from exploratory assessment into systematic verification. Testers work through each ASVS requirement at the selected verification level, documenting test procedures used, results observed, and evidence collected. Authentication testing verifies requirements 2.1 through 2.10, access control testing addresses requirements 4.1 through 4.3, and cryptography testing validates requirements 6.1 through 6.4.
This systematic approach ensures comprehensive coverage while providing clear completion criteria. Rather than subjective assessment of when testing is "complete," ASVS provides specific verification requirements. Testing concludes when all requirements at the selected verification level have been verified with documented evidence or documented compensating controls where direct implementation is not feasible.
Integrating ASVS with Penetration Testing
Penetration testing engagements incorporating ASVS provide more actionable results than traditional penetration tests. Test planning begins with ASVS requirements—identifying which requirements apply to the application under test based on functionality, selecting appropriate verification level based on business context, and planning test procedures verifying each requirement. Testing execution systematically addresses each requirement rather than relying solely on tester intuition and experience.
Findings reference specific ASVS requirements—"Application fails ASVS requirement 3.2.1: Application does not generate new session token after authentication." This specificity enables precise remediation. Developers understand exactly what control is missing, reference the ASVS requirement for implementation guidance, and verify successful remediation by confirming the specific requirement is satisfied.
Common Vulnerabilities Covered by ASVS
ASVS requirements systematically address the vulnerability classes that cause the majority of application security incidents. Injection flaws—SQL injection, command injection, LDAP injection—are prevented through comprehensive input validation and output encoding requirements in Chapter 5. Cross-site scripting vulnerabilities are mitigated through context-aware output encoding requirements and content security policy implementation. Broken authentication is prevented through session management requirements specifying token generation, secure cookie attributes, timeout implementation, and session invalidation during privilege changes.
Authorization bypass vulnerabilities are addressed through access control requirements mandating authorization checks at every endpoint, principle of least privilege enforcement, and protection against insecure direct object references. Sensitive data exposure is prevented through cryptography requirements specifying encryption algorithms, key management practices, and protection of data in transit and at rest. Security misconfigurations are addressed through requirements for secure defaults, removal of unnecessary features, and proper environment separation.
Compliance and Industry Standards
OWASP ASVS in the Context of Compliance
ASVS complements formal compliance frameworks by providing specific technical implementation guidance for security requirements that frameworks mandate at higher abstraction levels. ISO 27001 Annex A.14.2 requires "security in development and support processes"—ASVS provides 286 specific requirements demonstrating how organizations implement this control. PCI-DSS Requirement 6.5 mandates addressing common coding vulnerabilities—ASVS requirements provide specific verification criteria confirming these vulnerabilities are prevented.
Organizations document ASVS as their application security standard during compliance audits. Rather than explaining security practices abstractly, they reference ASVS verification level selection methodology, demonstrate gap analysis documentation, and provide evidence of systematic verification. This documented approach satisfies auditor requirements for security governance and technical controls.
How ASVS Helps Achieve Security Certification
SOC 2 Type II audits require documented evidence that security controls operate effectively over the observation period. Organizations implementing ASVS document initial verification, maintain evidence files demonstrating ongoing control operation, and conduct annual reverification confirming controls remain effective. This systematic documentation directly supports SOC 2 audit preparation—providing evidence that security controls are not just documented but systematically verified and maintained.
ISO 27001 certification requires a documented Information Security Management System (ISMS) including security controls, regular security assessments, and continuous improvement. ASVS implementation demonstrates security controls at the application layer, ASVS verification provides documented security assessments, and annual ASVS reverification demonstrates continuous improvement as findings are remediated and new requirements are implemented as applications evolve.
Organizations pursuing security certifications find ASVS accelerates preparation by providing structured framework for documenting existing controls, systematic methodology for identifying control gaps, and recognized standards that auditors understand. Rather than creating custom security documentation that auditors must evaluate from first principles, ASVS provides a recognized framework that auditors can verify against established criteria.
Application security demands systematic verification against comprehensive requirements—not ad-hoc testing that addresses obvious vulnerabilities while missing systematic control gaps. ASVS provides this verification framework, transforming security from subjective assessment into documented validation that specific controls exist and function as intended. Organizations implementing ASVS gain measurable security improvements, accelerated enterprise sales cycles through documented security posture, and efficient compliance preparation through systematic control documentation.
Security controls must protect actual systems rather than existing solely in documentation. ASVS bridges this gap by providing specific, verifiable requirements that confirm controls are not just described but implemented. The difference becomes apparent during incident response, when enterprise clients scrutinize vendor security postures, or when auditors demand evidence rather than assertions. ASVS verification demonstrates that security measures extend beyond documentation into actual protection mechanisms operating within production systems.
Frequently Asked Questions
What is ASVS OWASP?
The OWASP Application Security Verification Standard (ASVS) is a comprehensive framework providing specific security requirements for web applications and web services. It defines 286 security requirements across 14 domains including authentication, access control, data protection, API security, and configuration management. Organizations use ASVS to verify that applications implement security controls systematically rather than reactively addressing vulnerabilities discovered during testing.
What is the difference between OWASP ASVS and OWASP Top 10?
The OWASP Top 10 identifies the ten most critical web application security risks based on prevalence and impact—functioning as an awareness document highlighting what vulnerability categories to prioritize. ASVS provides comprehensive verification requirements addressing these risks through specific, testable controls. While the Top 10 identifies broken authentication as a critical risk, ASVS provides 30+ specific requirements verifying proper authentication implementation. Organizations use the Top 10 for risk awareness and ASVS for systematic verification that protective controls are properly implemented.
What is the difference between OWASP ASVS and SAMM?
OWASP Software Assurance Maturity Model (SAMM) assesses organizational security program maturity across governance, design, implementation, verification, and operations—evaluating whether organizations have established security policies, conduct threat modeling, and maintain incident response capabilities. ASVS focuses specifically on application-level security controls—whether individual applications correctly implement authentication, validate input, and protect sensitive data. Organizations use SAMM to build security programs and ASVS to verify those programs produce secure applications. Mature security programs employ both frameworks complementarily.
What would be a good use of the OWASP ASVS from a security manager perspective?
Security managers leverage ASVS to establish consistent security baselines across application portfolios, document security posture for enterprise customer due diligence, and guide systematic security testing rather than ad-hoc vulnerability assessments. ASVS enables risk-based control prioritization by categorizing requirements across three verification levels, provides objective criteria for security acceptance during development, and produces documented evidence satisfying compliance framework requirements for application security controls. Security managers reference ASVS during procurement discussions, use ASVS verification results to quantify security improvements over time, and integrate ASVS requirements into secure development lifecycle processes.



.svg)
.svg)
.svg)