Most organizations accept payment cards without fully understanding their security obligations. PCI DSS compliance isn't optional—it's a contractual obligation imposed by card brands, yet many companies treat it as a one-time certification exercise rather than a continuous operational discipline. This creates security gaps that become apparent when breaches occur, transaction fees escalate, or enterprise customers demand validation of payment security controls.
The Payment Card Industry Data Security Standard (PCI DSS) represents a global baseline for protecting cardholder data across every entity that stores, processes, or transmits payment card information. For organizations selling to enterprise clients, PCI DSS compliance demonstrates security maturity and operational discipline—capabilities that procurement teams scrutinize during vendor risk assessments.
This definition covers what PCI DSS requires, who must comply, how validation works, and the practical realities of maintaining continuous compliance in 2026.
What PCI DSS Is
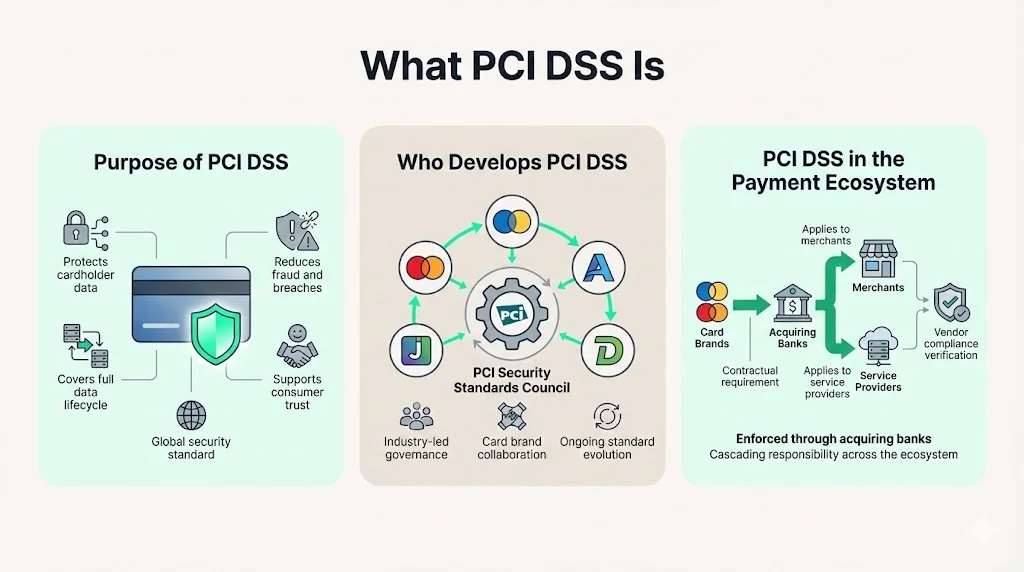
PCI DSS is a global security standard designed to protect cardholder data throughout its lifecycle. The standard establishes technical and operational requirements for securing payment card information, reducing fraud, preventing data breaches, and maintaining consumer trust in electronic payment systems.
Who Develops PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is intended for all entities involved in payment card processing, including merchants, processors, acquirers, issuers, and service providers. The Payment Card Security Standards Council (PCI SSC)—founded by major card brands including Visa, Mastercard, American Express, Discover, and JCB—develops, manages, and evolves the standard through industry collaboration.
How PCI DSS Fits into the Payment Ecosystem
Card brands mandate PCI DSS compliance through acquiring bank contracts, making it a contractual requirement rather than statutory regulation. Merchants agree to comply when they accept payment cards. Service providers that store, process, or transmit cardholder data on behalf of merchants face identical obligations. This cascading responsibility means enterprises evaluating vendors must verify that third-party service providers maintain compliant environments—a requirement that becomes critical during security assessments and customer audits.
Why PCI DSS Matters in 2026
Payment security threats continue evolving. New requirements have been implemented to prevent and detect new and ongoing threats against the payment industry, including phishing, e-commerce, and e-skimming attacks. Organizations face increasingly sophisticated attack vectors targeting payment infrastructure, including credential harvesting, script-based skimming on checkout pages, and API exploitation.
Enterprise customers demand documented security controls before onboarding vendors. Procurement teams require attestations of compliance, validation of security practices, and evidence that cardholder data remains protected throughout processing. Organizations lacking PCI DSS validation face immediate disqualification from enterprise sales opportunities.
Beyond contractual obligations, compliance delivers quantifiable risk reduction. Implementing the 12 requirements establishes defense-in-depth security controls that protect not only payment data but broader organizational infrastructure. Companies that treat PCI DSS as continuous security operations rather than annual certification exercises build genuine protection against breaches—security that performs under scrutiny rather than satisfying auditors on paper.
Core PCI DSS Requirements
The 12 PCI DSS Requirements
PCI DSS 4.0 implements significant changes in requirements, focusing more on maintaining continuous security as well as adding new methods to meet requirements. The standard specifies 12 security requirements that address network architecture, data protection, vulnerability management, access controls, monitoring, and governance:
- Requirement 1: Install and maintain network security controls
- Requirement 2: Apply secure configurations to all system components
- Requirement 3: Protect stored cardholder data
- Requirement 4: Protect cardholder data with strong cryptography during transmission over open, public networks
- Requirement 5: Protect all systems and networks from malicious software
- Requirement 6: Develop and maintain secure systems and software
- Requirement 7: Restrict access to system components and cardholder data by business need to know
- Requirement 8: Identify users and authenticate access to system components
- Requirement 9: Restrict physical access to cardholder data
- Requirement 10: Log and monitor all access to system components and cardholder data
- Requirement 11: Test security of systems and networks regularly
- Requirement 12: Support information security with organizational policies and programs
Organized into Six Major Objectives
These 12 requirements organize into six foundational security objectives:
- Build and maintain a secure network and systems – Implement firewall configurations, eliminate vendor defaults, and establish network segmentation
- Protect cardholder data – Encrypt stored data, protect data in transit, and minimize retention
- Maintain a vulnerability management program – Deploy anti-malware, patch systems, and secure application development practices
- Implement strong access controls – Restrict access by business need, assign unique IDs, and control physical access
- Monitor and test networks regularly – Track access, conduct vulnerability scans, and perform penetration testing
- Maintain an information security policy – Document security policies, implement security awareness training, and establish incident response procedures
Of the 64 new requirements, 51 are future-dated and will be effective as of 31 March 2025, requiring organizations to plan implementation timelines that accommodate both immediate and future-dated obligations.
PCI DSS and Payment Card Security
PCI DSS establishes the operational discipline required to protect payment card data from unauthorized access, theft, and misuse. The standard addresses security throughout the payment lifecycle—from initial card data capture through processing, storage, and transmission to payment networks.
Enterprise customers evaluating vendors expect documented payment security controls. During vendor risk assessments, procurement teams request attestations of compliance, validate cardholder data environment boundaries, and verify that third-party processors maintain compliant infrastructure. Organizations unable to demonstrate PCI DSS compliance face immediate disqualification from enterprise contracts.
Credit Card Data Protection Under PCI DSS
PCI DSS distinguishes between two categories of payment card information:
Cardholder data includes the primary account number (PAN), cardholder name, expiration date, and service code. Organizations may store cardholder data when business requirements justify retention, subject to encryption and access controls.
Sensitive authentication data includes full magnetic stripe data, card verification codes (CVV2/CVC2), and PIN data. PCI DSS prohibits storing sensitive authentication data after authorization, regardless of encryption. Organizations that retain prohibited data violate compliance requirements even when other controls function correctly.
Controls for protecting this data include encryption at rest, encryption during transmission, tokenization to remove PAN from environments, access controls limiting data exposure to authorized personnel, and automated monitoring detecting unauthorized access attempts. Organizations must document data flows, identify every system touching cardholder data, and implement controls protecting data throughout its lifecycle.
Who Must Comply
Any entity that stores, processes, or transmits cardholder data must comply with PCI DSS. This includes:
- Merchants accepting payment cards through any channel—retail locations, e-commerce platforms, mail order, telephone order, or mobile applications
- Service providers processing cardholder data on behalf of merchants, including payment gateways, processors, hosting providers, and managed security services
- Processors facilitating transaction authorization and settlement between merchants and card brands
- Acquirers maintaining relationships with merchants and submitting transactions for processing
- Issuers distributing payment cards and authorizing transactions
Organizations selling to enterprise clients frequently discover they qualify as service providers when customers transmit cardholder data through their platforms. This triggers full PCI DSS obligations regardless of whether the organization considers itself a payment company.
Merchant Levels & Compliance Obligations
Card brands classify merchants into compliance levels based on annual transaction volume, with each level carrying different validation requirements:
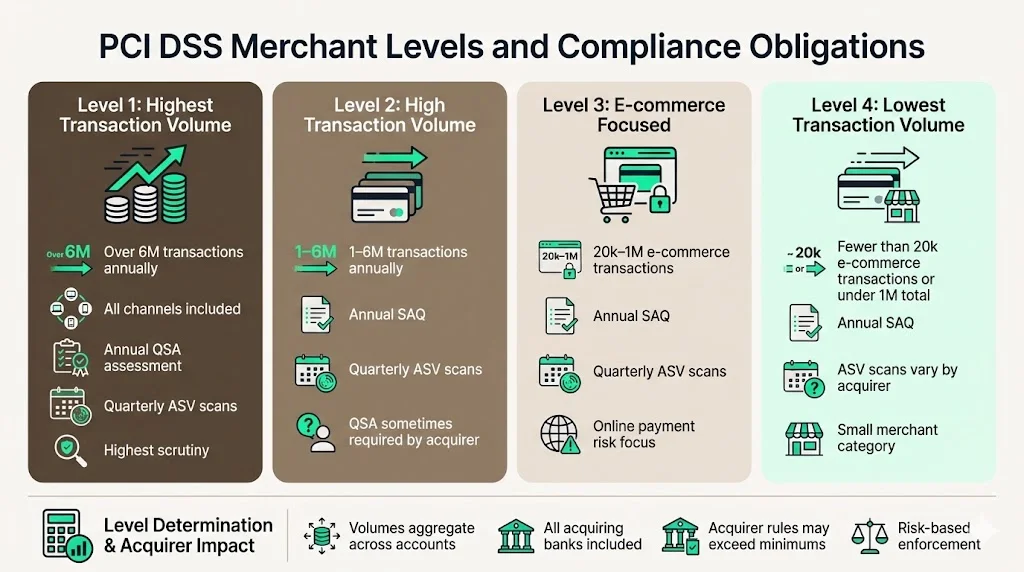
Level 1: Merchants processing over 6 million transactions annually across all channels. Level 1 merchants must complete annual assessments by Qualified Security Assessors (QSAs) and quarterly network scans by Approved Scanning Vendors (ASVs).
Level 2: Merchants processing 1-6 million transactions annually. Level 2 merchants typically complete annual Self-Assessment Questionnaires (SAQs) and quarterly ASV scans, though some acquiring banks require QSA assessments.
Level 3: Merchants processing 20,000-1 million e-commerce transactions annually. Level 3 merchants complete annual SAQs and quarterly ASV scans.
Level 4: Merchants processing fewer than 20,000 e-commerce transactions or fewer than 1 million total transactions annually. Level 4 merchants complete annual SAQs, with ASV scan requirements varying by acquirer.
Transaction volumes aggregate across all acquiring relationships. Organizations processing through multiple merchant accounts must calculate total annual volume when determining compliance level. Acquiring banks may impose more stringent validation requirements than card brand minimums based on risk assessment.
How Companies Validate PCI DSS Compliance
Validation methods vary by merchant level and business model:
Self-Assessment Questionnaires (SAQs) allow qualifying merchants to validate compliance through documented responses to control questions. Multiple SAQ types exist, each corresponding to specific payment processing scenarios—from simple card-not-present transactions to complex integrated payment environments. Organizations must select the SAQ matching their actual payment processing methods and infrastructure.
Qualified Security Assessor (QSA) assessments involve independent third-party validation of PCI DSS compliance. QSAs conduct onsite reviews, evaluate control implementation, test security controls, interview personnel, and produce Reports on Compliance (ROCs) documenting findings. Level 1 merchants and many Level 2 merchants require annual QSA assessments.
Internal Security Assessor (ISA) assessments allow large organizations to conduct internal compliance assessments using certified ISA personnel. ISAs follow identical assessment procedures as external QSAs but provide organizations with internal compliance expertise.
All validation methods require quarterly external vulnerability scans by Approved Scanning Vendors. Organizations must achieve passing scan results before attestations of compliance receive acceptance from acquiring banks.
Practical Steps to Become PCI DSS Compliant
Achieving compliance requires systematic implementation across technical, operational, and governance domains:
Scope your cardholder data environment. Your organization's PCI DSS scope is documented and confirmed at least once every 12 months, including your organization's Cardholder Data Environment, the people, processes, and technology that store, process, or transmit cardholder data or sensitive authentication data. Identify every system, network segment, application, database, and person with access to cardholder data.
Map data flows end-to-end. Document how cardholder data enters your environment, which systems process or store it, where it transmits across networks, and when it's deleted. Data flow diagrams reveal unexpected data exposure and guide control implementation.
Implement the 12 requirements systematically. Address network security controls, encryption, access management, logging, vulnerability management, and security policies. Each requirement includes specific testing procedures that assessors will validate during compliance reviews.
Establish continuous monitoring. Compliance represents ongoing operational discipline, not annual certification. Implement automated logging, configure security information and event management (SIEM) systems, deploy file integrity monitoring, and establish processes detecting control failures before assessments.
Organizations reducing cardholder data environment scope through tokenization, point-to-point encryption, or hosted payment pages simplify compliance substantially. Moving card capture over to hosted payment pages or hosted fields means raw PAN data never reaches your servers—combine that with tokenization for stored credentials and Point-to-Point encryption, reducing the number of systems requiring PCI DSS controls.
Common Challenges Companies Face
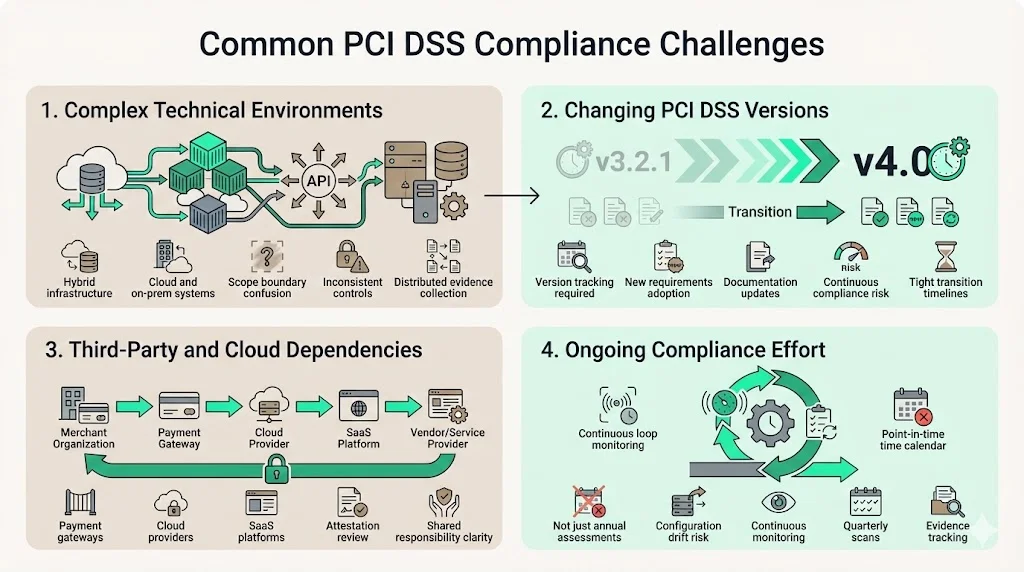
1) Managing complex technical environments. Modern payment infrastructure spans cloud platforms, containerized applications, third-party APIs, and legacy systems. Determining scope boundaries, implementing consistent controls across hybrid environments, and maintaining evidence of compliance across distributed infrastructure requires dedicated expertise.
2) Keeping up with changing versions. PCI DSS v4.0 will be retired on 31 December 2024. After that point, PCI DSS v4.0.1 will be the only active version. Organizations must track version transitions, implement new requirements, and update control documentation while maintaining continuous compliance with current standards.
3) Third-party and cloud dependencies. Payment processing relies on payment gateways, processors, hosting providers, and SaaS platforms. Organizations remain responsible for validating that third-party service providers maintain compliant environments, reviewing provider attestations of compliance, and ensuring contractual agreements address security responsibilities. Cloud environments introduce shared responsibility models requiring clear delineation between provider and customer security obligations.
4) Ensuring ongoing compliance beyond point-in-time. Assessments validate compliance at specific moments. Maintaining compliance between assessments requires continuous monitoring, change management processes preventing configuration drift, security awareness training, quarterly vulnerability scans, and remediation tracking. Organizations treating compliance as annual exercises inevitably face rushed preparations and incomplete evidence collection.
What Happens When Companies Fail PCI DSS
Non-compliance triggers escalating consequences from card brands and acquiring banks:
Financial penalties range from monthly fines of $5,000-$100,000 depending on violation severity and merchant level. Acquirers assess these penalties directly against merchant accounts, with fees continuing until organizations achieve compliance.
Transaction fee increases penalize non-compliant merchants through elevated per-transaction costs, directly impacting profit margins. These increases remain in effect until compliance validation occurs.
Loss of card acceptance privileges represents the most severe consequence. Acquiring banks may terminate merchant accounts for persistent non-compliance, effectively preventing organizations from accepting payment cards. For businesses dependent on card transactions, this outcome proves catastrophic.
Breach-related costs compound when non-compliant organizations experience data compromises. Card brands assess forensic investigation costs, fraud losses, card reissuance expenses, and regulatory penalties against merchants that suffer breaches while non-compliant. These costs frequently exceed millions of dollars.
Reputational damage and legal exposure extend beyond direct financial penalties. Customers, partners, and enterprise procurement teams scrutinize security failures. Organizations experiencing payment data breaches face customer attrition, contract terminations, and litigation from affected cardholders.
Best Practices for Long-Term PCI Compliance
1) Establish internal governance structures. Assign clear ownership for PCI DSS compliance, define roles and responsibilities across security, IT, and business functions, and establish executive sponsorship ensuring adequate resources. Compliance programs lacking dedicated ownership inevitably fail.
2) Automate logging and monitoring. Manual log review cannot scale across enterprise infrastructure. Deploy SIEM platforms aggregating logs from all in-scope systems, configure automated alerting for security events, and implement file integrity monitoring detecting unauthorized changes to critical system files.
3) Conduct regular training and awareness programs. The security awareness program must be reviewed and updated annually and address phishing, social engineering, and acceptable use of end-user technologies. Personnel must understand their responsibilities protecting cardholder data, recognize social engineering attacks, and follow secure handling procedures.
4) Leverage continuous audit readiness. Organizations maintaining ongoing compliance documentation, evidence collection, and control monitoring approach assessments with confidence. Implement automated evidence gathering, maintain current network diagrams and data flow documentation, and conduct quarterly internal compliance reviews identifying gaps before external assessments.
5) Reduce scope strategically. The most effective compliance strategy involves minimizing cardholder data environment scope. Implement tokenization replacing PANs with non-sensitive tokens, deploy point-to-point encryption protecting data from capture through processing, utilize hosted payment pages preventing PAN data from reaching internal systems, and eliminate unnecessary cardholder data storage.
Conclusion
PCI DSS compliance represents foundational security discipline for any organization handling payment card data. For companies selling to enterprise clients, demonstrated compliance proves operational maturity and security capability—criteria that procurement teams evaluate during vendor risk assessments.
Organizations are challenged with complying with 60+ updated or new requirements in PCI DSS 4.0, requiring systematic implementation across technical controls, operational processes, and governance frameworks. Organizations treating compliance as continuous security operations rather than annual certification exercises build genuine protection that withstands scrutiny and protects customer data.
The standard continues evolving to address emerging threats, changing technologies, and sophisticated attack methods. Organizations establishing disciplined compliance programs, implementing defense-in-depth security controls, and maintaining continuous audit readiness position themselves to adapt as requirements evolve while protecting payment infrastructure from compromise.
FAQs
1) What does PCI DSS mean?
PCI DSS stands for Payment Card Industry Data Security Standard—a comprehensive set of technical and operational requirements developed by the PCI Security Standards Council for protecting cardholder data throughout its lifecycle.
2) What are the 6 major principles of PCI DSS?
The six principles organize the 12 requirements into security objectives: build and maintain secure networks and systems; protect cardholder data; maintain vulnerability management programs; implement strong access controls; monitor and test networks regularly; and maintain information security policies.
3) What are the four things that PCI DSS covers?
PCI DSS addresses how organizations secure networks protecting cardholder data, implement encryption and access controls for sensitive information, manage vulnerabilities through patching and testing, and monitor systems detecting unauthorized access or security events.
4) What is the main objective of PCI DSS?
The primary objective is protecting payment card data from unauthorized access, theft, and misuse while preventing fraud and data breaches that compromise consumer trust in electronic payment systems.
5) What is PCI DSS?
PCI DSS is a global security standard developed by the Payment Card Industry Security Standards Council that establishes mandatory requirements for all organizations storing, processing, or transmitting cardholder data.
6) Who must comply with PCI DSS?
Any entity that stores, processes, or transmits cardholder data must comply with PCI DSS, regardless of organizational size, transaction volume, or business model—including merchants, service providers, processors, acquirers, and issuers.
7) What happens if a company fails PCI DSS checks?
Non-compliance results in monthly fines from $5,000-$100,000, elevated per-transaction fees, potential loss of card acceptance privileges through merchant account termination, and significantly increased liability for breach-related costs including forensic investigations, fraud losses, and card reissuance expenses.



.svg)
.svg)
.svg)