Most organizations treat PIPEDA compliance as a Canadian market entry requirement rather than a continuous security discipline. This approach creates a fundamental gap between attestation and operational reality—a gap that becomes apparent when enterprise procurement teams conduct vendor due diligence or when breaches trigger regulatory scrutiny. PIPEDA became law in 2000 to promote consumer trust in electronic commerce and reassure the European Union that Canadian privacy law adequately protects personal information. Organizations serving Canadian enterprise clients face compliance expectations regardless of where they are headquartered.
What Is PIPEDA?
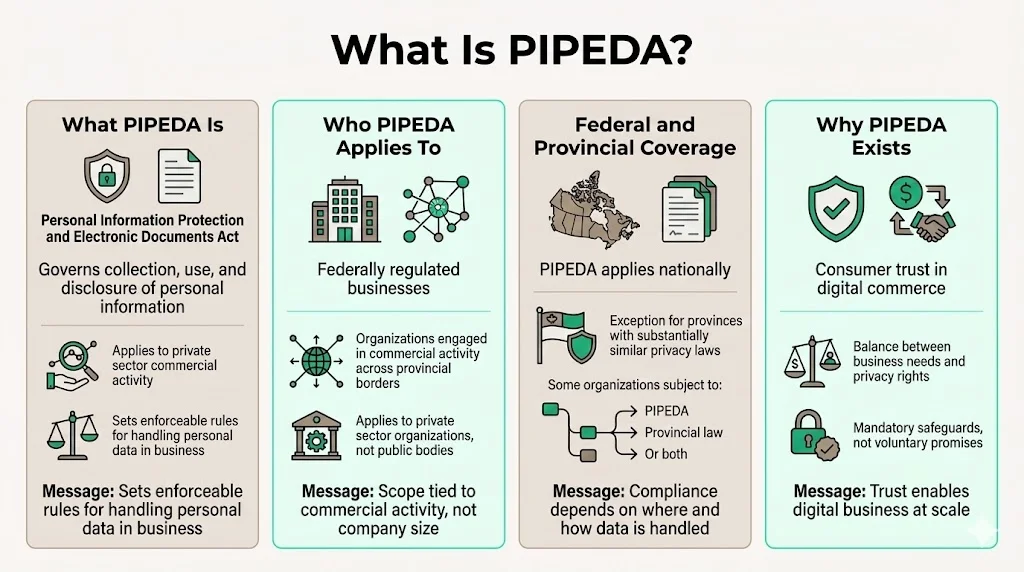
PIPEDA—the Personal Information Protection and Electronic Documents Act—is a Canadian law governing how private sector organizations collect, use and disclose personal information in the course of commercial business. The law sets out ground rules for how private sector organizations may collect, use or disclose personal information in the course of commercial activities. It applies to federally regulated businesses and organizations engaged in commercial activity across provincial boundaries.
PIPEDA applies to organizations' commercial activities in all provinces, except organizations that collect, use or disclose personal information entirely within provinces that have their own privacy laws deemed substantially similar to federal law. This creates a complex regulatory landscape where businesses may be subject to PIPEDA, provincial privacy legislation, or both depending on their operational footprint.
Why PIPEDA Exists
PIPEDA was enacted to promote consumer trust in electronic commerce during the early expansion of digital business operations. The legislation addresses a fundamental market problem: without enforceable privacy protections, consumers and businesses lack confidence in digital transactions involving personal information. Government regulation establishes baseline expectations for data handling practices, creating accountability mechanisms that self-regulation cannot consistently deliver.
The law balances legitimate business requirements for personal information against individual privacy rights. This balance reflects recognition that commercial activity requires data collection while simultaneously acknowledging the risks created by systematic information gathering. PIPEDA establishes mandatory practices rather than voluntary guidelines, ensuring organizations implement concrete safeguards rather than aspirational commitments.
The Purpose of PIPEDA
1) Protecting Personal Information
PIPEDA gives individuals the right to access and request correction of personal information organizations may have collected about them. Personal information under PIPEDA encompasses data about identifiable individuals—any information that can identify a person directly or through combination with other data points. This includes obvious identifiers such as names and addresses, as well as less direct information including IP addresses, device identifiers, and behavioral data that enables identification when combined with other datasets.
The law requires organizations to balance business requirements against privacy rights. Organizations can collect and use personal information for legitimate commercial purposes, but they must implement collection limitations, specify purposes before collection, and maintain security safeguards proportionate to sensitivity and volume.
2) Supporting Fair Commercial Activity
PIPEDA enables data-driven commercial activity while establishing mandatory boundaries. Organizations can collect personal information necessary for business operations—customer management, transaction processing, service delivery, and relationship management—but collection must serve identified purposes with appropriate consent mechanisms.
Consent represents a core principle under PIPEDA. Valid consent requires that it is reasonable to expect individuals to whom an organization's activities are directed would understand the nature, purpose and consequences of the collection, use or disclosure to which they are consenting. This standard requires clear communication rather than lengthy legal documents that obscure rather than clarify data practices.
3) Building Trust in the Market
Enterprise procurement processes include systematic privacy and security assessments. Organizations demonstrating PIPEDA compliance signal operational maturity, risk management capability, and commitment to documented practices rather than ad hoc approaches. PIPEDA compliance becomes a qualification criterion in vendor evaluations, particularly for organizations handling sensitive data or serving regulated industries.
Privacy law compliance functions as a trust signal during vendor due diligence. Enterprise buyers evaluate whether vendors implement documented controls, maintain audit readiness, and demonstrate accountability for personal information protection. Organizations lacking PIPEDA compliance face extended sales cycles, contractual limitations, or disqualification from procurement processes.
Who Must Comply With PIPEDA
1) Organizations Covered by the Law
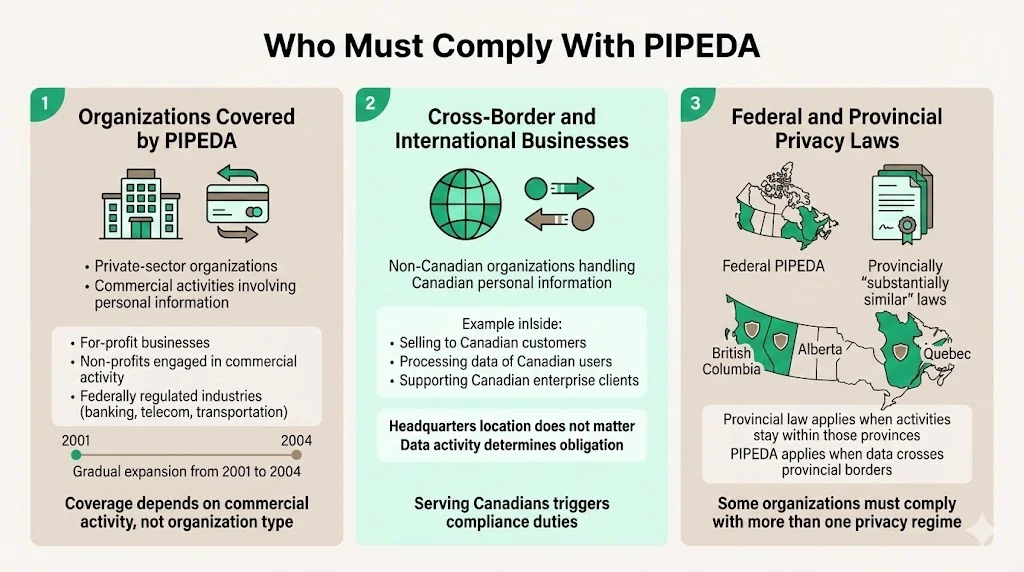
PIPEDA applies to private-sector organizations collecting, using, or disclosing personal information for commercial activities in Canada, or those serving Canadian users. Coverage extends to for-profit businesses, non-profit organizations engaged in commercial activity, and federally regulated industries including banking, telecommunications, and transportation.
The law initially applied to federally regulated industries in 2001, expanded to the health sector in 2002, and by 2004 covered any organization collecting personal information in commercial activity except in provinces with substantially similar privacy laws. This phased implementation created the current landscape where organizational obligations depend on operational scope and provincial jurisdiction.
2) Cross-Border and International Businesses
Non-Canadian organizations fall under PIPEDA when they collect, use, or disclose personal information of individuals in Canada during commercial activities. Selling products or services to Canadian enterprises, processing data from Canadian users, or maintaining business relationships involving Canadian personal information creates compliance obligations.
Organizations headquartered outside Canada face the same PIPEDA requirements as domestic entities when their commercial activities involve Canadian personal information. Geographic location does not exempt organizations from compliance obligations—operational activities determine applicability. Enterprise vendors serving Canadian clients encounter PIPEDA requirements during procurement processes regardless of where corporate headquarters are located.
3) Federal vs Provincial Privacy Laws
Several provincial laws have been deemed substantially similar to PIPEDA, and wherever substantially similar provincial law applies, that law applies instead of PIPEDA. British Columbia, Alberta, and Quebec maintain provincial privacy legislation recognized as substantially similar, meaning organizations operating entirely within these provinces may be subject to provincial rather than federal law.
The requirement to comply with PIPEDA applies even when data flows from a province where PIPEDA applies to another where substantially similar privacy laws exist, meaning some businesses could be subject to two sets of privacy laws. Organizations operating across provincial boundaries must navigate overlapping compliance obligations, requiring legal analysis of which privacy regime applies to specific data processing activities.
Core Principles of PIPEDA (Plain-English Overview)
1) Accountability
Organizations must designate individuals responsible for PIPEDA compliance and implement policies governing personal information management. Accountability extends to third-party service providers—organizations remain responsible for personal information even when processing occurs through vendors, contractors, or cloud service providers.
2) Identifying Purposes
Organizations must identify and document purposes for collecting personal information before or at the time of collection. Purpose specification requires clear articulation rather than broad statements allowing unrestricted use. Purposes must be communicated to individuals in language that enables understanding without legal interpretation.
3) Consent
PIPEDA requires valid, documented consent for collecting, using, and disclosing personal data in many cases, especially sensitive information. Organizations must obtain appropriate consent based on sensitivity, context, and reasonable expectations. Express consent applies to sensitive information; implied consent may suffice for less sensitive data where reasonable expectations support collection.
4) Limiting Collection, Use, and Retention
Organizations must collect only information necessary for identified purposes. Data minimization requires evaluating whether specific data elements are essential rather than potentially useful. Retention periods must align with business requirements and legal obligations—organizations cannot maintain personal information indefinitely without documented justification.
5) Safeguards and Information Security
PIPEDA requires security safeguards appropriate to sensitivity, amount, distribution, format, and storage method. Technical safeguards include access controls, encryption, and monitoring systems. Physical safeguards protect premises and hardware. Organizational safeguards encompass policies, training, and accountability structures ensuring consistent implementation.
6) Openness and Access
Organizations must maintain privacy policies explaining information management practices. Individuals have the right to access and request correction of personal information organizations may have collected about them. Access rights require establishing processes for receiving requests, verifying identity, locating responsive information, and delivering responses within regulatory timeframes.
What Counts as Personal Information Under PIPEDA
Common Examples
Personal information includes any data about identifiable individuals. Names, email addresses, phone numbers, physical addresses, social insurance numbers, financial information, and health records all constitute personal information. Employee records—compensation, performance evaluations, disciplinary documentation, and personnel files—fall under PIPEDA when held by private-sector organizations.
Customer relationship management systems containing contact information, purchase history, communication records, and preference data hold personal information requiring PIPEDA compliance. Marketing databases, support ticketing systems, and analytics platforms collecting user behavior data all involve personal information subject to regulatory requirements.
Business Contact Information
PIPEDA does not apply to business contact information—including email addresses—which an organization collects, uses or discloses solely for communicating with a person in relation to their employment, business or profession. This exclusion applies narrowly: business contact information used for purposes beyond professional communication falls under PIPEDA requirements.
Organizations frequently misapply the business contact information exclusion. Using professional email addresses for marketing communications, combining professional contact data with behavioral tracking, or processing business contact information for purposes unrelated to professional communication eliminates the exclusion. The exemption protects routine professional communication—not comprehensive data collection using professional identifiers.
Sensitive vs Less Sensitive Data
Information sensitivity determines safeguard requirements and consent mechanisms. Financial information, health records, biometric data, and information about children requires enhanced protection. Less sensitive information—names, professional contact details, and general demographic data—permits proportionate rather than maximum security controls.
Sensitivity assessment considers context rather than applying fixed classifications. Professional email addresses in B2B sales contexts present different sensitivity than the same addresses combined with purchase behavior, financial data, and personal preferences. Organizations must evaluate actual sensitivity based on potential harm from unauthorized disclosure rather than applying simplistic categorization.
Data Breaches and Reporting Obligations
What Is Considered a Data Breach
Breaches of security safeguards include loss, unauthorized access, or disclosure of personal information. Breaches encompass intentional attacks, accidental disclosures, system misconfigurations, and insider threats. Unauthorized access by employees, misconfigured cloud storage, phishing attacks compromising credentials, and ransomware incidents all constitute breaches requiring evaluation under reporting obligations.
When Breaches Must Be Reported
Organizations must report to the Office of the Privacy Commissioner and notify affected individuals and relevant third parties about breaches of security safeguards that pose a real risk of significant harm to affected individuals. The "real risk of significant harm" standard requires evaluating sensitivity of information involved, probability of misuse, and potential consequences to affected individuals.
Harm assessment considers identity theft risk, financial loss potential, reputational damage, physical safety threats, and psychological harm. Organizations must complete harm assessments promptly following breach discovery rather than delaying evaluation while investigating incident details. When assessment identifies real risk of significant harm, reporting obligations trigger regardless of whether harm actually occurs.
Record-Keeping Requirements
Organizations must maintain comprehensive breach records regardless of whether breaches meet reporting thresholds. Internal breach logs document incident details, investigation findings, harm assessments, notifications delivered, and remediation measures implemented. Documentation requirements support Privacy Commissioner investigations, demonstrate accountability, and enable pattern analysis identifying systemic vulnerabilities.
Breach documentation proves essential during audits and investigations. Organizations lacking documented breach response processes, harm assessments, and remediation tracking face challenges demonstrating compliance during regulatory review. Comprehensive records signal operational maturity and accountability—characteristics enterprise procurement teams evaluate during vendor assessments.
Penalties and Risks of Non-Compliance
1) Financial Penalties
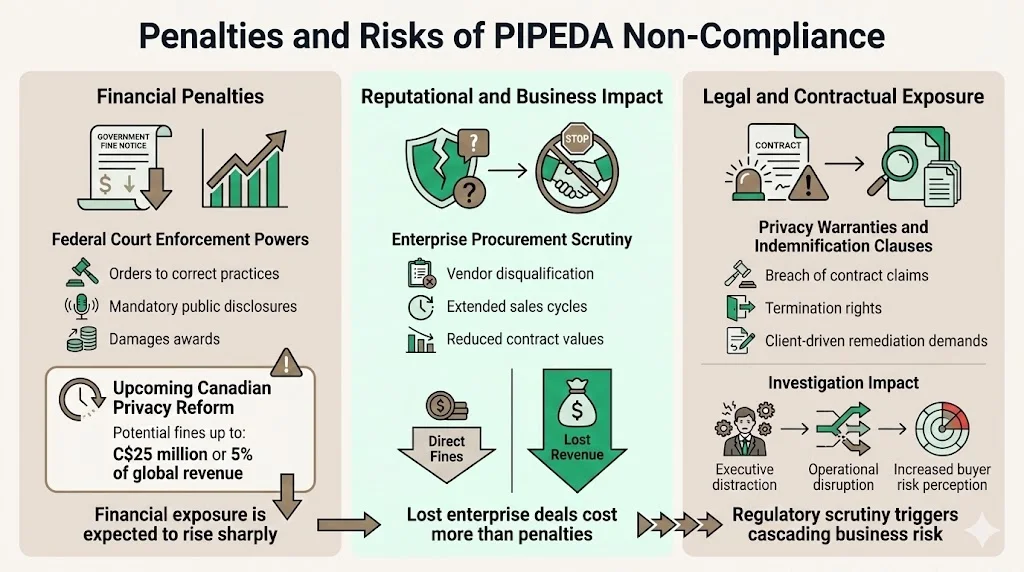
The Federal Court has power to order organizations to correct practices, publicize correction steps, and award damages. Current PIPEDA penalties remain limited compared to contemporary privacy regimes. However, proposed legislation to replace PIPEDA and establish the Consumer Privacy Protection Act is expected in late 2025 or early 2026, with potentially severe penalties including fines up to the greater of C$25 million or 5% of gross global revenue.
Organizations must prepare for substantially increased financial exposure as Canadian privacy law modernizes. The enforcement landscape will shift from complaint-driven investigations toward proactive compliance audits and administrative monetary penalties comparable to GDPR enforcement mechanisms.
2) Reputational and Business Impact
Privacy violations damage market reputation and competitive positioning. Enterprise buyers systematically evaluate vendor privacy practices during procurement. Organizations with documented violations, Privacy Commissioner investigations, or weak privacy postures face disqualification from enterprise sales processes.
Lost enterprise deals represent more significant financial impact than direct penalties. Extended sales cycles, reduced contract values, and procurement disqualification create measurable revenue effects. Privacy incidents become permanent procurement obstacles—enterprise buyers remember and reference vendor privacy failures during multi-year relationship evaluations.
3) Legal and Contractual Exposure
Enterprise contracts include privacy and security representations, warranties, and indemnification provisions. PIPEDA violations trigger contractual breach claims, indemnification demands, and relationship termination rights. Clients facing regulatory exposure from vendor privacy failures pursue contractual remedies regardless of whether regulators impose direct penalties.
Privacy Commissioner investigations create operational disruption beyond financial penalties. Investigations require substantial internal resources, executive attention, and documented remediation. Organizations under investigation face competitive disadvantage during enterprise sales processes as buyers evaluate regulatory risk and operational stability.
PIPEDA vs GDPR: Key Differences for Enterprise Vendors
Scope and Geographic Reach
PIPEDA applies to commercial activities involving Canadian personal information. GDPR applies to organizations offering goods or services to EU residents or monitoring EU resident behavior regardless of organizational location. PIPEDA focuses on Canadian commercial activity; GDPR establishes extraterritorial reach based on data subject location rather than organizational presence.
Consent and Legal Bases
Unlike GDPR, PIPEDA does not require a legal basis for data processing, though organizations must have legitimate purposes for collecting and processing personal information. GDPR establishes six lawful bases for processing—consent, contract, legal obligation, vital interests, public task, and legitimate interests. PIPEDA centers on consent with exceptions for specific circumstances rather than multiple distinct legal bases.
Consent mechanisms differ substantially. GDPR requires explicit consent for sensitive data processing and prohibits processing based on contract necessity for non-essential purposes. PIPEDA applies sensitivity-based consent standards without GDPR's strict separation between consent and contract-based processing.
Penalties and Enforcement Style
GDPR administrative fines reach €20 million or 4% of annual global turnover. Current PIPEDA enforcement relies primarily on Federal Court orders rather than administrative monetary penalties. The proposed Consumer Privacy Protection Act will align Canadian penalties more closely with GDPR levels, fundamentally changing enforcement dynamics.
Privacy Commissioner enforcement under current PIPEDA emphasizes investigation, recommendation, and court application rather than direct penalty assessment. GDPR enables data protection authorities to impose administrative fines without court proceedings. This procedural difference affects enforcement speed and organizational risk profiles.
Why Enterprises Often Expect Both
Enterprise procurement questionnaires routinely assess both GDPR and PIPEDA compliance. Organizations serving multinational enterprises face overlapping privacy requirements regardless of whether they directly process EU resident data. Procurement teams evaluate vendor privacy maturity using the most stringent applicable standards rather than limiting assessment to specific regulatory requirements.
Strong privacy programs address GDPR and PIPEDA requirements simultaneously. Core practices—data minimization, purpose limitation, security safeguards, breach response, and access rights—apply across privacy regimes. Organizations implementing comprehensive privacy programs satisfy overlapping requirements more efficiently than managing compliance through jurisdiction-specific silos.
Why PIPEDA Matters in Real-World Enterprise Sales
1) Enterprise Procurement Reality
Enterprise procurement includes systematic privacy and security assessments. Vendor questionnaires evaluate privacy policies, security controls, breach response capabilities, data processing agreements, and regulatory compliance status. Organizations lacking documented PIPEDA compliance face procurement obstacles before reaching commercial negotiations.
Security and compliance questionnaires assess specific controls: data encryption, access management, vulnerability management, incident response procedures, and third-party risk management. PIPEDA compliance signals operational capabilities extending beyond basic privacy policy publication—it demonstrates implemented controls, documented procedures, and accountability structures.
2) Competitive Advantage
Privacy maturity accelerates enterprise sales cycles. Organizations demonstrating comprehensive privacy programs reduce procurement friction, satisfy security review requirements without extended back-and-forth, and signal operational sophistication. Strong privacy posture differentiates vendors in competitive evaluations where functional capabilities prove similar.
Privacy compliance enables market access. Organizations serving financial services, healthcare, government, or other regulated industries face mandatory privacy requirements. PIPEDA compliance becomes a qualification threshold rather than a competitive differentiator—absence of compliance eliminates vendors from consideration regardless of product capabilities.
3) Internal Alignment
PIPEDA compliance requires coordination among legal, security, engineering, sales, and support teams. Effective compliance programs establish clear ownership, documented responsibilities, and cross-functional workflows. Legal teams interpret requirements; security teams implement controls; engineering teams build privacy into systems; sales teams communicate capabilities; support teams handle access requests and incident response.
Organizations treating privacy as exclusively legal or security responsibility fail to achieve operational compliance. Privacy programs require enterprise-wide implementation with executive sponsorship, adequate resources, and accountability mechanisms ensuring consistent practices rather than sporadic efforts.
Practical Steps for Enterprise-Focused Companies
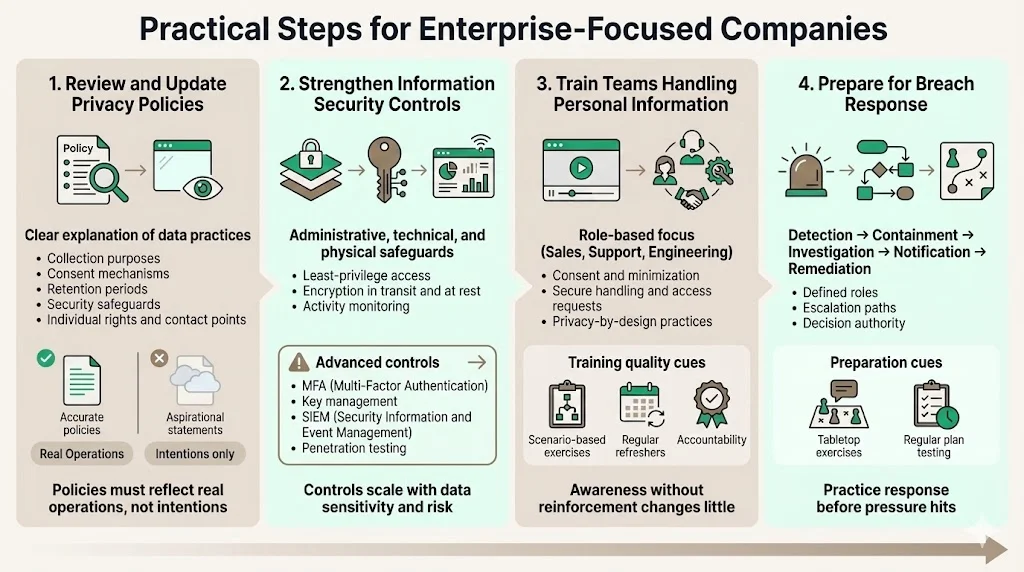
1) Review and Update Privacy Policies
Privacy policies must explain information management practices in clear language enabling understanding without legal interpretation. Policies should identify collection purposes, describe consent mechanisms, specify retention periods, explain security safeguards, document individual rights, and provide contact information for privacy inquiries.
Transparency requires accuracy. Privacy policies describing aspirational rather than actual practices create regulatory exposure and undermine stakeholder trust. Regular policy reviews ensure alignment with operational reality, technology changes, and evolving business models.
2) Strengthen Information Security Controls
Security safeguards must address administrative, technical, and physical controls. Access controls implement least-privilege principles limiting data access to roles requiring it for identified purposes. Encryption protects data in transit and at rest. Monitoring systems detect unauthorized access attempts and anomalous behavior patterns.
Security control implementation must align with sensitivity, volume, and distribution of personal information. Organizations processing high-sensitivity data require enhanced controls including multi-factor authentication, encryption key management, security information and event management systems, and regular penetration testing.
3) Train Teams Handling Personal Information
Sales, support, and engineering teams require role-specific privacy training. Sales teams must understand consent requirements, data minimization principles, and privacy representations in customer communications. Support teams need training on access request procedures, breach identification, and appropriate data handling. Engineering teams require privacy-by-design principles, secure development practices, and data protection impact assessment methodologies.
Training effectiveness requires regular refreshers, scenario-based exercises, and accountability for compliance failures. Organizations conducting annual training without measuring comprehension or reinforcing principles throughout the year achieve minimal compliance improvement.
4) Prepare for Breach Response
Incident response plans must address detection, containment, investigation, harm assessment, notification, and remediation. Plans should designate response team members, establish communication protocols, document decision-making authorities, and define escalation procedures.
Breach response preparation includes tabletop exercises testing plan effectiveness before incidents occur. Organizations discovering plan gaps during actual breaches face compressed timelines, regulatory scrutiny, and reputational damage amplified by inadequate response. Regular testing identifies process weaknesses, clarifies roles, and builds organizational muscle memory enabling effective response under pressure.
Conclusion
PIPEDA represents more than a regulatory checkbox for organizations serving Canadian enterprise markets. The law establishes mandatory privacy practices supporting stakeholder trust, competitive positioning, and operational excellence. Organizations treating PIPEDA compliance as documentation exercise rather than operational discipline discover gaps during enterprise procurement processes, regulatory investigations, or breach incidents.
Privacy law readiness supports long-term enterprise growth by reducing sales friction, enabling market access, and building client confidence. Organizations implementing comprehensive privacy programs—documented policies, implemented controls, trained personnel, and tested incident response—demonstrate operational maturity that enterprise buyers evaluate systematically during vendor selection.
New federal private sector privacy legislation is expected in late 2025 or early 2026, fundamentally changing Canada's privacy enforcement landscape. Organizations building strong privacy foundations under current PIPEDA requirements position themselves to adapt efficiently as regulatory expectations intensify rather than facing rushed compliance efforts under compressed timelines.
FAQs
1) Who must comply with PIPEDA?
PIPEDA applies to private-sector organizations collecting, using, or disclosing personal information for commercial activities in Canada, or those serving Canadian users. This includes Canadian organizations engaged in commercial activity and non-Canadian companies processing Canadian personal information during business operations. Organizations operating entirely within provinces maintaining substantially similar privacy laws may be subject to provincial rather than federal requirements, though cross-border data flows often trigger PIPEDA obligations regardless of provincial legislation.
2) What counts as personal information?
Personal information encompasses any data about identifiable individuals including names, contact details, financial information, health records, and behavioral data enabling identification. PIPEDA does not apply to business contact information—including email addresses—collected, used or disclosed solely for communicating with a person regarding their employment, business or profession. This exclusion applies narrowly to routine professional communication rather than comprehensive data processing using business identifiers.
3) What are the penalties for non-compliance?
The Federal Court can order organizations to correct practices, publicize correction steps, and award damages. However, proposed legislation is expected to include potentially severe penalties including fines up to the greater of C$25 million or 5% of gross global revenue. Beyond direct financial penalties, non-compliance creates reputational damage, lost enterprise sales opportunities, contractual breach claims, and Privacy Commissioner investigations disrupting operations.
4) How does PIPEDA compare to GDPR?
PIPEDA focuses on Canadian commercial activities while GDPR establishes global reach based on data subject location. Unlike GDPR, PIPEDA does not require a legal basis for data processing, instead centering on consent with specific exceptions. Current PIPEDA penalties remain lower than GDPR fines, though proposed legislation will establish comparable penalty levels. Enterprise vendors typically face expectations to comply with both frameworks as procurement teams evaluate privacy maturity using the most stringent applicable standards.
5) When must breaches be reported?
Organizations must report breaches of security safeguards posing a real risk of significant harm to the Office of the Privacy Commissioner and notify affected individuals. Real risk of significant harm assessment considers information sensitivity, probability of misuse, and potential consequences including identity theft, financial loss, reputational damage, and physical safety threats. Organizations must maintain breach records regardless of reporting thresholds, documenting incidents, harm assessments, notifications, and remediation measures.



.svg)
.svg)
.svg)