Most organizations treat RFPs as procurement exercises focused on price comparisons and feature checklists. This approach fundamentally misrepresents the strategic role RFPs play in enterprise security infrastructure—a gap that becomes apparent when vendor relationships introduce vulnerabilities, compliance failures, or incident response breakdowns that could have been prevented through rigorous security evaluation during the proposal process.
When enterprises issue RFPs for security services or solutions, they're not purchasing software licenses or consulting hours. They're establishing a security relationship where vendors gain access to sensitive systems, process protected data, and become integral components of the organization's defense posture. The RFP serves as the mechanism through which enterprises verify that vendors demonstrate genuine security management capabilities, maintain documented compliance with regulatory frameworks, implement robust data protection controls, and possess the operational discipline to function as extensions of the enterprise's security team rather than weak points in its perimeter.
This article addresses how vendors should engage with security-focused RFPs to differentiate themselves in enterprise sales contexts, how enterprises should structure RFPs to elicit substantive security evidence rather than marketing narratives, and why RFPs function as both compliance documentation and risk-mitigation instruments rather than administrative formalities.
What is an RFP?
An RFP, or Request for Proposal, is a structured document organizations use to solicit proposals from potential vendors for specific products or services. The RFP process encompasses the broader documentation, evaluation, and vendor selection workflow used to solicit competitive bids for IT solutions, professional services, or operational engagements requiring detailed technical specifications and compliance verification.
In security contexts, RFPs extend far beyond feature comparisons. A cybersecurity request for proposal outlines the organization's needs, technical requirements, and how responses will be evaluated. The security RFP addresses vendor cybersecurity protocols, risk assessment methodologies, vendor evaluation processes for sub-vendors, access control mechanisms, authentication procedures, incident response capabilities, audit readiness, and continuous monitoring commitments. These requirements reflect the enterprise's recognition that vendor security posture directly impacts organizational risk exposure.
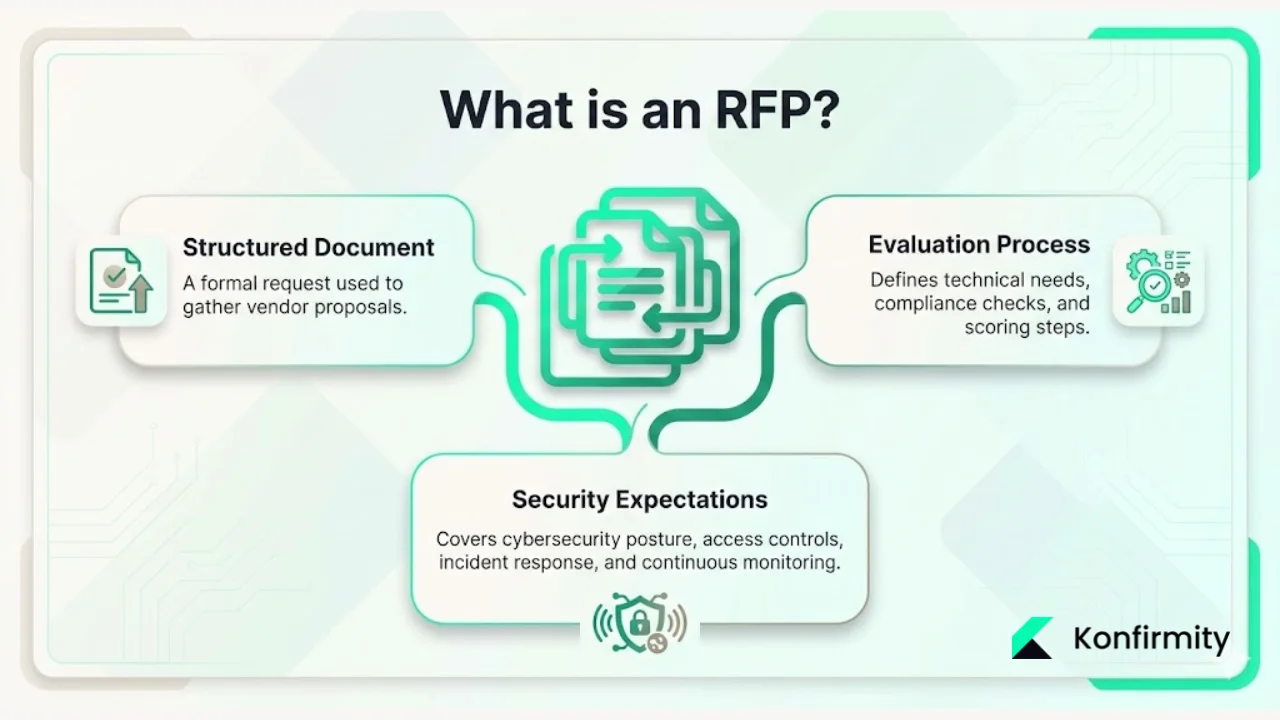
What does "RFP security" mean?
RFP security refers to how security-related requirements are embedded into the RFP process from both perspectives: how enterprises structure security expectations in the RFP document, and how vendors respond with verifiable evidence of security capabilities rather than aspirational commitments.
RFP security bridges multiple security domains: security management frameworks, cybersecurity protocols, security standards implementation, incident response procedures, access control systems, data protection measures, and vendor evaluation methodologies. Buyers in 2025 are prioritizing RFP requirements for security services that verify compliance and certification as foundational, not optional. This shift reflects enterprise recognition that vendors asking for exceptions to security requirements signal operational immaturity.
Enterprises view RFPs not as procurement paperwork but as compliance and risk-mitigation strategy. The RFP establishes baseline expectations for security compliance, confidentiality agreements, data handling procedures, and audit cooperation. Organizations treating RFPs as administrative exercises discovered during audits or incidents that their vendors lack the documented controls, evidence trails, and operational discipline required to meet regulatory obligations or respond effectively to security events.
Why Security Matters in an RFP for Enterprises
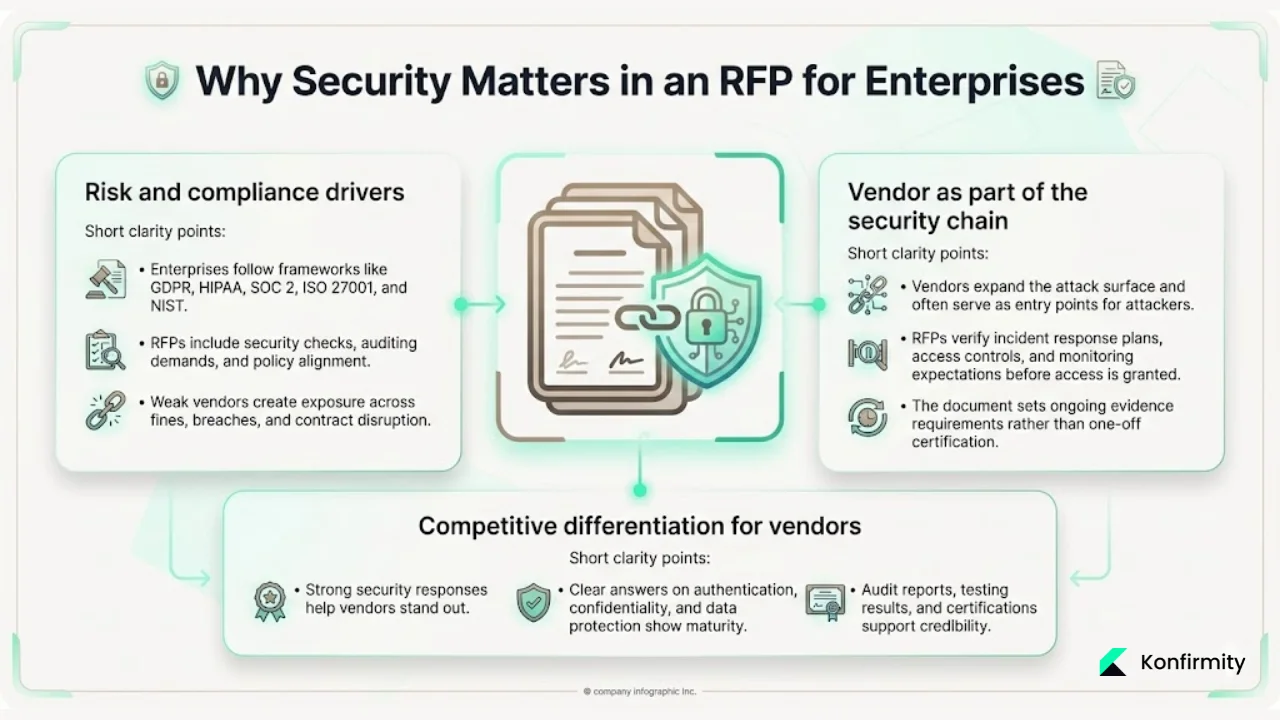
1) Risk & compliance drivers
Enterprises face regulatory requirements spanning GDPR, HIPAA, SOC 2, ISO 27001, NIST frameworks, and industry-specific mandates. When they issue RFPs, they embed risk assessment criteria, auditing and monitoring expectations, and security policy alignment requirements into vendor evaluation because vendor failures translate directly into enterprise compliance violations, regulatory fines, and audit findings.
Some RFPs specifically seek qualified cybersecurity firms to perform comprehensive assessments of current cybersecurity posture, including technical infrastructure, organizational policies, and user practices. These security assessment RFPs explicitly evaluate vendor capabilities to identify vulnerabilities, assess risk, and provide remediation guidance aligned with regulatory frameworks.
If a vendor fails security criteria evaluation, it exposes enterprises to threat mitigation failures, data breaches, regulatory enforcement actions, and the operational disruption of vendor replacement mid-contract. The financial and reputational consequences of selecting vendors unable to maintain security standards far exceed any initial cost savings from choosing less-qualified providers.
2) Vendor as part of the security chain
When enterprises outsource functions or engage third-party vendors, those vendors become components of the organization's attack surface. Adversaries routinely compromise organizations through vendor access rather than direct attacks. The RFP ensures vendors meet security standards and align with the enterprise's incident response frameworks, access control policies, and continuous monitoring requirements before they gain privileged access to systems or data.
The RFP functions as a vendor evaluation and ongoing assurance mechanism. It establishes the security baseline against which vendor performance will be measured throughout the contract lifecycle, defines audit rights, and specifies the evidence vendors must produce to demonstrate sustained compliance rather than point-in-time certification.
3) Competitive differentiation for vendors
For companies selling to enterprise clients, demonstrating RFP security competence differentiates vendors in competitive evaluations. Being able to respond clearly to RFP questions on authentication procedures, confidentiality agreements, data protection implementations—and providing evidence rather than assertions—demonstrates operational maturity that procurement teams and security officers recognize immediately.
Vendors who understand threat mitigation, articulate their security management frameworks using industry-standard terminology, and provide audit reports, penetration testing results, and compliance certifications position themselves as partners capable of meeting enterprise security obligations rather than vendors requiring constant oversight.
Key Components of a Security-Focused RFP
Enterprises structure security-focused RFPs to extract substantive information about vendor capabilities rather than accepting generic marketing responses.
Introduction & Background
The RFP opens with purpose, scope, timeline, and contact details. The introduction includes background context, scope of work, proposal requirements, evaluation criteria, contract terms, and submission details.
Background sections establish the enterprise's current security posture, threat landscape, and compliance frameworks—such as ISO 27001, SOC 2 Type II, HIPAA, or GDPR—that the vendor relationship must support. This context allows vendors to tailor responses to demonstrated organizational priorities rather than generic security capabilities.
Scope of Work (SOW) / Requirements
The scope provides detailed descriptions of required services or solutions: security management responsibilities, cybersecurity protocols (endpoint protection, network security, SOC operations), data protection obligations, confidentiality agreements, authentication procedures, and access control requirements.
The SOW defines deliverables, implementation timelines, integration requirements with enterprise systems, and performance metrics. Vendors require this specificity to price services accurately and allocate appropriate resources rather than providing placeholder estimates that prove inadequate during implementation.
Security-Specific Requirements / Standards
This section specifies required security standards—ISO 27001, NIST Cybersecurity Framework, SOC 2, PCI DSS—and outlines vendor expectations for access control implementation, authentication procedures, incident response capabilities, threat mitigation strategies, and auditing and monitoring processes.
Enterprises include requirements for vendor certifications, compliance evidence, past audit reports, penetration testing results, and vulnerability management practices. These requirements serve as qualification thresholds; vendors unable to provide documented evidence typically lack the operational maturity to maintain security throughout the contract term.
Vendor Evaluation Criteria
Evaluation criteria define how responses will be scored: technical capabilities (security management, cybersecurity protocols, risk assessment methodologies), vendor reputation, past performance, cost structure, and compliance readiness.
The criteria address how vendors monitor and audit their own operations, how they manage vendor risk in their supply chain (sub-vendors and service providers), and their track record responding to security incidents. Enterprises assign weightings to each criterion, clarifying whether technical capability, compliance credentials, or cost predominates in selection decisions.
Contract Terms, SLAs & Confidentiality Agreements
Service Level Agreements specify security incident response times, escalation procedures, and performance penalties for SLA violations. Contract terms address confidentiality agreements, data protection obligations, liability provisions, indemnification, and audit rights.
These sections establish expectations around access control mechanisms, authentication procedures, incident response protocols, and the enterprise's right to audit vendor security practices. Vendors unable to accept standard security contract terms signal inadequate insurance coverage, immature security operations, or business models incompatible with enterprise risk management requirements.
Submission Details & Vendor Questions
RFPs specify proposal format, submission deadline, point of contact, and the process for vendor questions and clarifications. This procedural information ensures proposals arrive in formats enabling consistent evaluation and provides vendors clarity on timeline expectations.
Budget Constraints (optional)
Some RFPs include budget ranges or financial expectations. While not universal, budget guidance allows vendors to propose solutions within enterprise financial parameters rather than proposing capabilities the organization cannot afford.
How Vendors Should Respond to a Security RFP
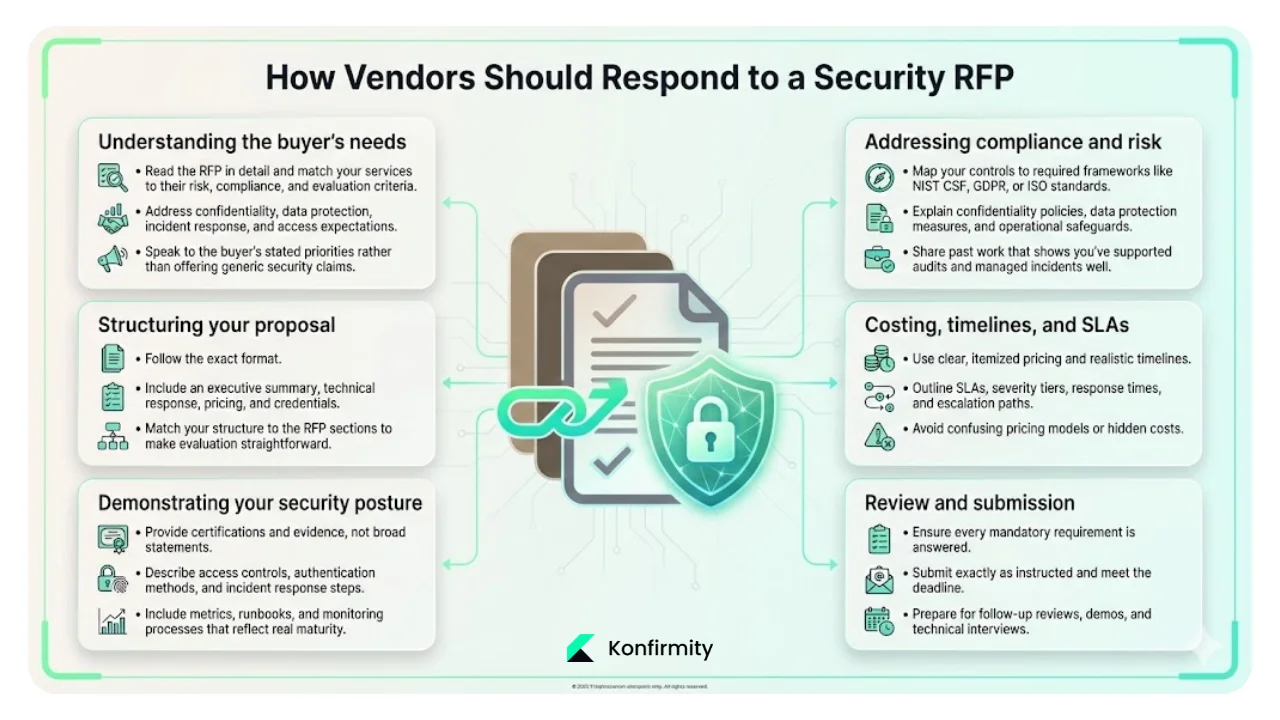
1) Understanding the buyer's needs
Read the RFP thoroughly; map your services to their risk assessment requirements, security compliance frameworks, and vendor evaluation criteria. Identify where they emphasize confidentiality agreements, data protection, incident response capabilities, and access control expectations.
Enterprises structure RFPs to reveal which security concerns predominate: regulatory compliance, operational resilience, supply chain risk, or specific threat scenarios. Vendors who address stated priorities directly rather than reciting generic security capabilities demonstrate they understand the buyer's environment.
2) Structuring your proposal
Follow the required format exactly. Include an executive summary, technical response addressing each requirement, cost breakdown with transparent pricing models, and compliance credentials.
Use a clear structure aligned with RFP sections. Enterprises evaluate dozens of proposals; proposals that deviate from requested formats create evaluation friction and signal inability to follow client specifications—a concerning indicator for vendors seeking security engagements requiring precise adherence to documented procedures.
3) Demonstrating your security posture
Provide evidence of your security management framework, cybersecurity protocols, and certifications (ISO 27001, SOC 2 Type II, HITRUST, FedRAMP). Show your vendor evaluation process for your own supply chain, acknowledging that your sub-vendors and service providers represent risk to the enterprise.
Detail your access control and authentication procedures with specific technologies and implementation details. Describe your incident response plan with documented runbooks, escalation paths, and mean time to respond/remediate metrics from past incidents. Articulate your threat mitigation strategy and auditing and monitoring processes using industry-standard frameworks and terminology.
4) Addressing compliance & risk
Show how you meet required security standards and regulatory frameworks with specific control mappings. If the RFP references NIST CSF, map your controls to NIST functions. If it requires GDPR compliance, address data processing principles, data subject rights, and cross-border transfer mechanisms.
Highlight your approach to confidentiality agreements and data protection with documented policies, technical safeguards, and operational procedures. Provide case studies or references demonstrating past success in enterprise-scale security engagements, including how you've supported client audits or responded to security incidents without service disruption.
5) Costing, timelines, and SLAs
Provide transparent cost models with itemized pricing, implementation timelines with specific milestones, and resource commitments. Explain your SLA structure including incident response times (acknowledging severity levels), escalation paths with named roles, and your approach to performance monitoring and reporting.
Avoid pricing models that obscure true costs or introduce unexpected fees after contract signature. Invoicing transparency and hidden fees now appear at the top of nearly every security RFP. Enterprises have learned that vendors offering unsustainably low initial pricing compensate through change orders, scope restrictions, or service degradation.
6) Review & submission
Proofread responses to ensure you've answered all evaluation criteria completely. Incomplete responses to mandatory requirements typically result in automatic disqualification regardless of technical capabilities.
Submit by deadline following submission instructions exactly. Be prepared for vendor follow-up including presentations, demonstrations, technical deep-dives with security teams, and reference checks. Enterprises conducting serious security vendor evaluation will verify claims made in proposals rather than accepting assertions at face value.
How to Write an RFP for Security Services (from the buyer's side)
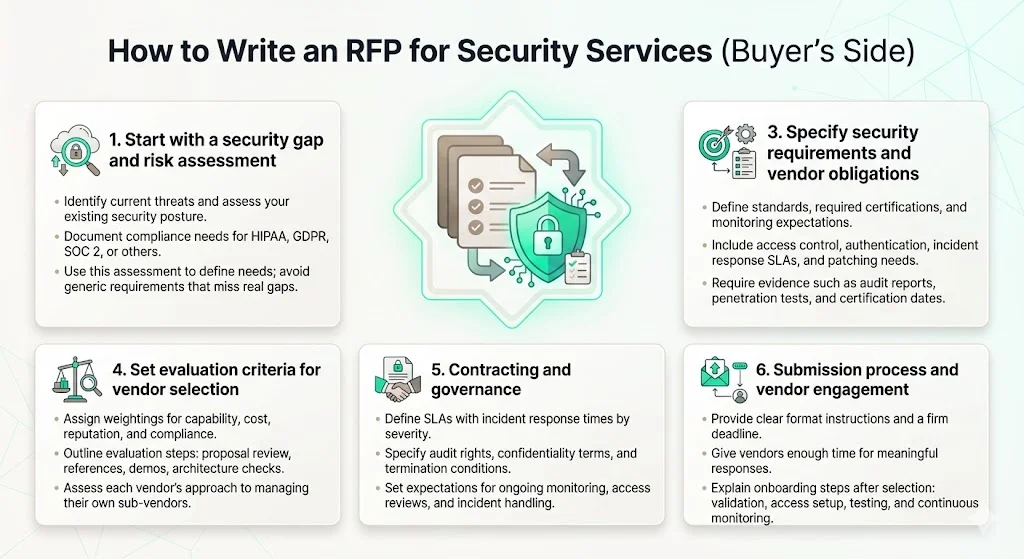
1) Start with a security gap and risk assessment
Before issuing the RFP, conduct a risk assessment: identify current threats, evaluate existing security posture, document compliance obligations (HIPAA, GDPR, SOC 2), and determine which security gaps require vendor capabilities to address.
Use this assessment as background to define RFP requirements. RFPs written without understanding current security posture produce generic requirements that fail to address actual organizational needs, resulting in vendor proposals that solve problems the organization doesn't have while ignoring critical vulnerabilities.
2) Define the scope & desired outcomes
Specify which systems, applications, data repositories, or business processes fall within scope. Clarify what vendors must deliver: security management for specific infrastructure, threat mitigation for identified attack vectors, incident response for defined scenarios, or access control for particular user populations.
Clarify which compliance frameworks apply (HIPAA for healthcare data, PCI DSS for payment processing, GDPR for EU personal data). Set implementation timelines with realistic milestones recognizing that substantive security implementations require time for proper design, testing, and validation.
3) Specify security requirements & vendor obligations
State required security standards, vendor certification expectations (ISO 27001, SOC 2 Type II), auditing and monitoring obligations, confidentiality agreement terms, and data protection requirements with specific technical controls.
Include vendor access control mechanisms, authentication procedures, incident response responsibilities with defined SLAs, vulnerability management processes, and patch management commitments. Specify evidence vendors must provide: audit reports, penetration testing results, compliance certifications with current dates, and documentation of security policies and procedures.
4) Set evaluation criteria for vendor selection
Define weightings for technical capability, cost, vendor reputation, and compliance credentials. Include vendor evaluation steps: proposal review, reference checks, technical demonstrations, security architecture reviews, and potentially site visits to vendor facilities or SOC operations.
Clarify how you'll evaluate vendor security management practices including their own vendor risk management for sub-vendors. Vendors with weak supply chain security introduce risk regardless of their direct security capabilities.
5) Contracting & governance
Use SLAs for security incidents with specific response time requirements by severity level. Define confidentiality agreements, audit rights allowing enterprise security teams to review vendor practices, and termination rights if vendors fail to maintain required security standards.
Define how vendor performance will be monitored, how access will be controlled and reviewed periodically, and how incident response will be triggered and managed. Establish governance mechanisms for ongoing security review rather than treating security as a point-in-time contract requirement.
6) Submission process & vendor engagement
Provide clear instructions for submission format, timeline with specific deadline, and vendor question process. Establish realistic timelines; vendors require adequate time to prepare substantive responses rather than rushing generic proposals that fail to address specific requirements.
Clarify how you'll manage vendor onboarding after selection, including security validation, access provisioning, integration testing, and continuous monitoring throughout the contract lifecycle.
Integrating RFP Security into Ongoing Compliance and Monitoring
1) Vendor onboarding & ongoing vendor evaluation
Vendor selection represents the beginning of security governance, not the conclusion. Once selected, vendors require continuous monitoring: auditing and monitoring of security practices, periodic risk assessments, vendor evaluation updates as threat landscapes evolve, and validation that vendors maintain compliance certifications.
The RFP establishes the baseline; enterprises must maintain vendor compliance with security standards, incident response readiness, and access control commitments throughout the contract term. This requires documented vendor governance processes, not informal check-ins.
2) Contract governance & SLA monitoring
Use the SLAs and contract terms defined in the RFP to structure ongoing monitoring. Track vendor performance against incident response SLAs, validate that vendors execute agreed monitoring procedures, and trigger incident response protocols when security events occur.
Ensure vendors adhere to access control commitments, authentication requirements, and audit cooperation obligations. Vendors who resist security reviews or audit cooperation signal operational practices inconsistent with their RFP representations.
3) Continuous improvement & alignment with evolving threats
Threat landscapes change continuously; vendors and enterprises must revisit cybersecurity protocols, threat mitigation strategies, and risk assessments regularly rather than treating security as static contract requirements.
Plan for periodic security audits, control effectiveness reviews, and updates to security policies as part of vendor governance lifecycle. This includes reviewing vendor security incidents, assessing their response effectiveness, and implementing lessons learned to strengthen security posture continuously.
Common Pitfalls and Best Practices

Pitfalls
Vague scope or requirements lead to mismatched vendor responses, misaligned expectations, and unclear deliverables that create conflict during implementation. Ambiguity in security requirements allows vendors to propose minimal capabilities that technically satisfy RFP language while failing to address actual security needs.
Ignoring vendor's own vendor management exposes enterprises to supply chain risk. A vendor with strong direct security but weak sub-vendor oversight introduces vulnerabilities through their suppliers, contractors, and service providers.
Over-emphasis on cost at the expense of security credentials and compliance creates false economies. Vendors offering significantly lower pricing than competitors typically reduce costs by eliminating security controls, using less experienced personnel, or implementing operational shortcuts that create risk.
Lack of clear SLAs around incident response and access control allows vendors to deprioritize security incidents, delay responses, or fail to maintain access controls rigorously. Without specific SLAs, "best effort" becomes the de facto standard.
No continuous monitoring plan after contract award allows vendor security posture to degrade over time. Initial compliance doesn't guarantee sustained performance without ongoing governance.
Best practices
Be specific about data protection requirements, confidentiality agreement terms, access control mechanisms, and authentication procedures. Specificity allows accurate vendor responses and eliminates ambiguity that creates risk.
Use standard frameworks (ISO 27001, NIST Cybersecurity Framework) and require vendor compliance with documented evidence. Standards provide common language and verifiable criteria rather than subjective security assessments.
Ask for vendor audit reports (SOC 2 Type II reports), penetration testing results with findings and remediation evidence, and incident response track records including specific examples of how they've handled security events.
Build evaluation criteria that balance cost, technical capability, vendor reputation, and compliance credentials with explicit weightings. This forces disciplined evaluation rather than allowing subjective preferences to override objective security requirements.
Plan vendor governance beyond selection: define audit schedules, monitoring procedures, performance review processes, and escalation mechanisms for security concerns. Security governance requires sustained organizational commitment, not procurement department handoffs.
Maintain clear communication and governance mechanisms including regular security reviews, defined points of contact for security issues, and documented processes for addressing security concerns or SLA violations.
Conclusion
Embedding security into RFPs is critical for both enterprises evaluating vendors and vendors competing for enterprise business. Enterprises that treat RFPs as procurement paperwork rather than security evaluation instruments discover too late that vendors lack the operational discipline, technical capabilities, or compliance maturity to function as trusted security partners. The resulting remediation—vendor replacement mid-contract, security incident response while simultaneously managing vendor transitions, or audit findings requiring immediate vendor oversight improvements—consumes far more resources than rigorous initial evaluation would have required.
For vendors selling to enterprise clients, mastery of RFP security across the full lifecycle (understanding enterprise security assessment priorities, structuring proposals with verifiable evidence, delivering on security commitments, and maintaining compliance throughout the contract term) represents significant competitive advantage. Today's RFPs focus less on price and more on performance and partnership. Vendors demonstrating they understand this shift differentiate themselves from competitors still competing primarily on cost.
Organizations should build internal processes for vendor evaluation, incident response coordination, access control management, and continuous security monitoring so that responding to or issuing security-focused RFPs becomes an operational strength rather than an administrative scramble requiring heroic effort from already-overwhelmed security teams.
FAQs
1) What is an RFP in security?
A cybersecurity RFP is a formal document organizations use to outline their specific cybersecurity needs and invite vendors to submit proposals to meet those needs, serving as a starting point for the vendor selection process and playing a crucial role in ensuring the security and integrity of digital assets. The security RFP addresses vendor capabilities across security management, incident response, access control, data protection, compliance frameworks, and operational security practices. It functions as both procurement documentation and risk-mitigation mechanism by establishing security baselines vendors must meet before gaining access to enterprise systems or data.
2) What does RFP stand for?
RFP stands for Request for Proposal—a structured document organizations use to solicit competitive proposals from vendors for products, services, or solutions requiring detailed technical specifications and evaluation criteria.
3) How to respond to a security RFP?
Understand the buyer's security priorities by thoroughly reading the RFP and mapping your capabilities to their stated requirements. Align your offering with their scope, compliance frameworks, and evaluation criteria. Show your security credentials and security posture with documented evidence: certifications (ISO 27001, SOC 2 Type II), audit reports, penetration testing results, data protection implementations, access control mechanisms, and incident response capabilities with specific metrics. Follow submission guidelines exactly, provide transparent pricing without hidden costs, and proofread responses to ensure you've addressed all mandatory requirements. Submit by deadline and prepare for follow-up including technical demonstrations, reference checks, and security deep-dives with the enterprise security team.
4) How to write an RFP for security services?
Conduct risk assessment to identify current security gaps, threats, and compliance obligations before drafting the RFP. Define scope precisely: specify which systems, data, or processes require security services and which compliance frameworks (HIPAA, GDPR, ISO 27001) apply. Specify security requirements including required standards, vendor certification expectations, access control mechanisms, authentication procedures, incident response SLAs, auditing obligations, and confidentiality agreement terms. Set evaluation criteria with explicit weightings for technical capability, compliance credentials, vendor reputation, and cost. Define contract and governance terms including SLAs for security incidents, audit rights, performance monitoring processes, and termination provisions if vendors fail to maintain security standards. Provide clear submission process instructions with realistic timelines allowing vendors adequate time to prepare substantive responses rather than generic proposals.
5) What is the role of security in RFPs?
Security ensures vendor solutions satisfy enterprise risk mitigation requirements, compliance obligations, data protection mandates, confidentiality requirements, access control standards, and incident response capabilities. Security in RFPs functions as a qualification mechanism—establishing baseline security requirements vendors must demonstrate before consideration—and as an ongoing governance framework defining how vendor security performance will be monitored, audited, and maintained throughout the contract lifecycle. Security requirements in RFPs translate regulatory obligations and organizational risk tolerance into specific, verifiable vendor capabilities and operational commitments.
6) What are the components of an RFP for security services?
Security RFPs include: introduction and background establishing organizational context, current security posture, and compliance frameworks; scope of work defining required services, deliverables, timelines, and integration requirements; security-specific requirements specifying standards (ISO 27001, SOC 2), certifications, access control expectations, authentication procedures, incident response capabilities, and evidence vendors must provide; vendor evaluation criteria with weightings for technical capability, compliance credentials, reputation, and cost; contract terms including SLAs for security incidents, confidentiality agreements, data protection obligations, audit rights, and liability provisions; submission details specifying format, deadline, and vendor question process; and optionally, budget constraints providing financial parameters for proposed solutions.



.svg)
.svg)
.svg)