An SAP security assessment constitutes a comprehensive, risk-based evaluation of security controls, user access rights, system configurations, and vulnerabilities within enterprise SAP environments. These assessments examine authorisation management, segregation of duties (SoD), transaction monitoring, data protection mechanisms, and compliance alignment across SAP landscapes—ranging from core ERP modules to S/4HANA, HANA databases, and Business Technology Platform (BTP) integrations.
As organisations deepen their reliance on SAP and navigate increasingly complex landscapes like RISE, S/4HANA, and BTP, the threat environment heading into 2026 is more active—and more unforgiving—than ever. SAP security breaches typically cost organisations between $4.5-7.8 million, including direct financial losses, remediation costs, regulatory penalties, reputation damage, and business disruption expenses. For enterprises managing critical financial, HR, supply chain, and customer data through SAP systems, the stakes extend beyond regulatory compliance to encompass operational continuity, data integrity, and stakeholder trust.
This definition examines the role of SAP security assessments in maintaining compliance posture and security infrastructure, the core components assessed, the structured evaluation process, and how organisations—including those providing managed services to enterprise clients—should position these assessments within broader risk management frameworks.
What is a SAP Security Assessment?
An SAP security assessment represents a structured, evidence-based review of access controls, authorisations, system configurations, vulnerabilities, audit mechanisms, and data protection practices within SAP environments. Unlike one-time compliance audits conducted for external attestation, security assessments function as ongoing components of enterprise risk management—identifying control gaps, prioritising remediation based on business impact, and establishing continuous monitoring to sustain audit readiness.
The assessment scope typically encompasses user provisioning workflows, role-authorisation mappings, SoD analysis, custom code vulnerabilities, patch management effectiveness, transaction monitoring capabilities, and data classification enforcement. Regular SAP security assessments are essential for identifying vulnerabilities and ensuring adherence to regulatory requirements, including reviewing roles and authorisations, transaction monitoring, vulnerability management, and patch management.
What exactly is SAP Security?
SAP security encompasses the discipline of protecting SAP systems through systematic management of user roles, authorisations, system configurations, segregation of duties, and data protection controls. This domain addresses how users authenticate, what transactions they can execute, which data they can access, and how their activities are monitored and audited.
The relationship between SAP security and broader enterprise security posture proves direct: SAP systems typically process an organisation's most sensitive financial transactions, intellectual property, personally identifiable information (PII), and supply chain data. Weaknesses in SAP-specific controls—such as excessive authorisations, orphaned accounts, or inadequate audit logging—create exploitable gaps that compromise the entire security infrastructure regardless of perimeter defences or endpoint protection.
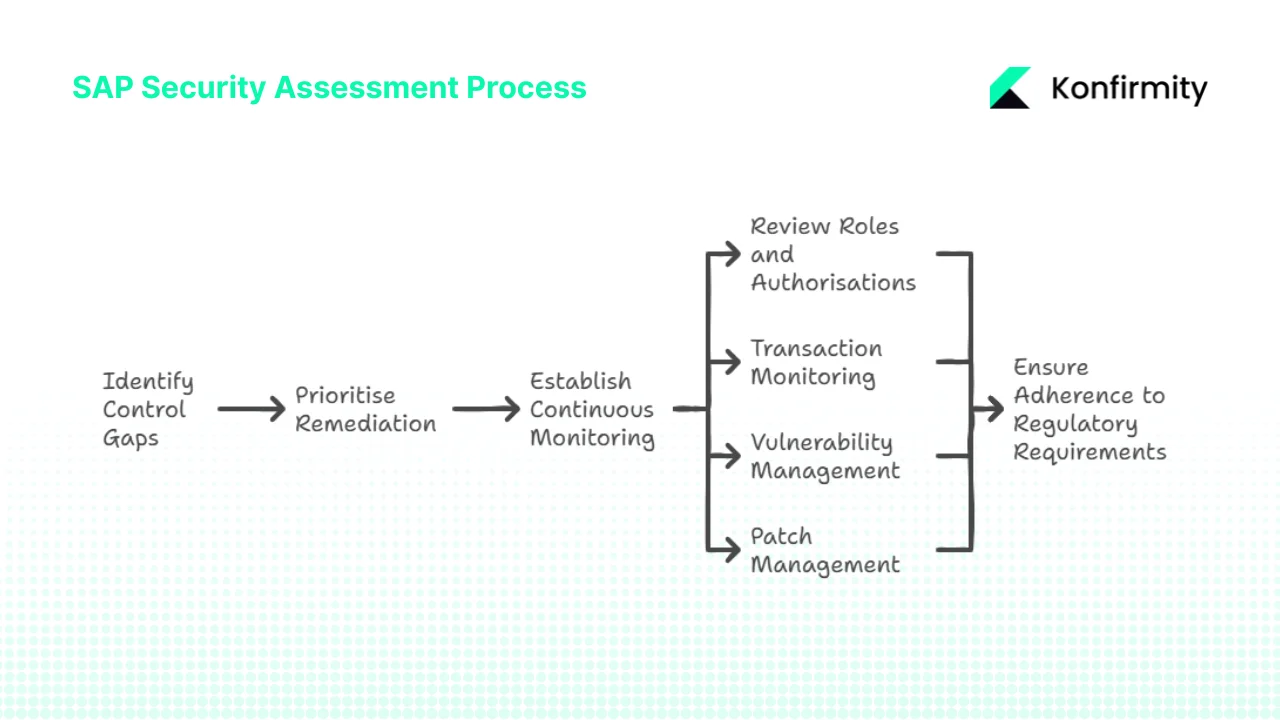
Why Enterprises Need SAP Security Assessments
SAP landscapes present inherent complexity: multiple modules (FI, CO, MM, SD, HR), custom ABAP code, third-party integrations, hybrid on-premises-cloud architectures, and extensive user populations with varying access requirements. This complexity generates persistent risks of authorisation creep, misconfigured roles, unpatched vulnerabilities, and insufficient monitoring.
In 2025, the evolving SAP threat landscape is primarily driven by challenges related to accelerated digital transformation, increased reliance on third-party vendors, and highly sophisticated cyberattacks. Although the increase in cyber attacks targeting SAP customers continues to increase, many challenges faced by customers in securing those systems have remained consistent for many years, starting with challenges with applying patches and updates. Since many successful attacks target systems for which patches are available and have not been applied, understanding and remediating these vulnerabilities is crucial in a layered cybersecurity strategy.
Regulatory drivers compound these technical realities. GDPR data processing requirements, SOX internal control mandates, HIPAA safeguards for protected health information, and sector-specific regulations demand documented evidence of access controls, audit trails, and data protection measures—evidence systematically generated through rigorous SAP security assessments. Beyond compliance, business continuity depends on preventing unauthorized transaction execution, fraud, data exfiltration, and system availability disruptions that erode customer confidence and stakeholder trust.
Core Components of an SAP Security Assessment
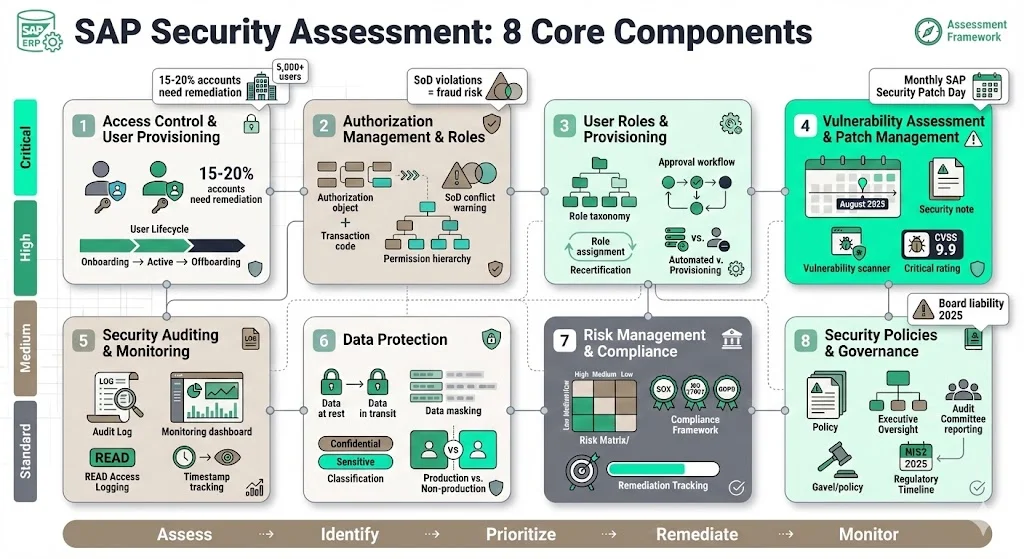
1) SAP Access Control & User Provisioning
Access control reviews examine user access rights, role assignments, authorisation objects, and provisioning workflows governing how users gain, maintain, and lose system access. Assessments identify access creep—the accumulation of unnecessary permissions as users change roles—and orphaned accounts remaining active after employee departures.
Role-based access control (RBAC) implementation receives scrutiny: whether roles align with business functions, whether assignment workflows include appropriate approvals, and whether de-provisioning processes execute consistently. Enterprises with 5,000+ SAP users frequently discover 15-20% of accounts require immediate revocation or modification based on current job responsibilities.
2) SAP Authorisation Management & Roles
Authorisation management reviews focus on what transactions users can perform, which data they can access, and whether permission levels align with least-privilege principles. Assessments examine authorisation objects (the granular building blocks of SAP security), transaction codes assigned to roles, and whether composite roles inadvertently grant excessive privileges.
Segregation of duties analysis identifies incompatible permission combinations—such as users who can both create vendors and process payments, or modify financial records and approve journal entries. These SoD violations represent fraud risks and internal control weaknesses requiring immediate remediation to satisfy audit requirements.
3) SAP User Roles & Provisioning Workflows
Role design quality determines security effectiveness. Assessments evaluate whether organisations maintain clean role taxonomies (avoiding role proliferation), whether roles map clearly to business functions, and whether approval workflows enforce proper authorisation before granting access.
Provisioning workflow reviews examine onboarding speed versus control rigor, de-provisioning completeness, and periodic recertification processes where managers validate that direct reports' access remains appropriate. Manual provisioning introduces delays and errors; automated workflows with embedded SoD checks accelerate provisioning while maintaining control quality.
4) SAP Vulnerability Assessment and Patch Management
SAP releases monthly security updates, known as "SAP Security Notes", which address newly identified risk across SAP platforms. A well-defined patch management policy should include regular monitoring of SAP Security Patch Day announcements, assessing the risk and applicability of each patch, and conducting thorough testing in controlled environments before deployment. Ensuring timely implementation of relevant patches into production systems is critical.
Configuration vulnerability reviews assess system hardening: default passwords, unnecessary services enabled, transport security settings, and HANA database configurations. Custom code reviews identify security flaws in ABAP programs, RFC-enabled function modules, and custom interfaces where input validation failures create injection vulnerabilities. August 2025 Patch Day represents the most severe release this year in terms of RCE risk. Three separate CVEs with CVSS 9.9 highlight the fragility of RFC-exposed modules — often overlooked yet central to SAP integration.
5) SAP Security Auditing & Monitoring
Audit log configuration and transaction monitoring capabilities determine an organisation's ability to detect anomalous behaviour, investigate incidents, and generate compliance evidence. Assessments review whether audit logging captures sufficient detail (user, transaction, timestamp, changed values), whether log retention meets regulatory requirements, and whether monitoring tools analyse logs for suspicious patterns.
SAP Read Access Logging records when sensitive data is viewed, helping organisations track who accessed confidential information, meet compliance requirements, and identify potential data privacy violations or unauthorised access patterns. Without comprehensive auditing, organisations lack the forensic evidence required during security incidents and external audits.
6) SAP Data Protection
Critical data processed through SAP systems—financial records, employee information, customer details, intellectual property—requires protection through encryption, masking, and classification. Assessments evaluate encryption implementations for data at rest and in transit, masking effectiveness in non-production environments, and whether data classification policies govern how sensitive information is handled.
Non-production environment security frequently receives inadequate attention, yet development and testing systems containing production data copies represent significant data leakage risks. Assessments verify that non-production environments implement equivalent controls or utilise effective data masking to eliminate exposure.
7) SAP Risk Management & Compliance Alignment
Assessment findings feed into enterprise risk management frameworks: identified vulnerabilities receive risk ratings based on likelihood and business impact, remediation priorities emerge from risk-based analysis, and tracking mechanisms ensure closure of high-priority gaps within defined timeframes.
Compliance alignment reviews map SAP-specific controls to external frameworks (SOX Section 404 internal controls, ISO 27001 control objectives, GDPR data processing requirements) and internal policies. This mapping demonstrates how SAP security controls satisfy broader compliance obligations and generates audit evidence supporting external attestations.
8) SAP Security Policies & Governance
Effective SAP security depends on comprehensive policies governing access management, role administration, change management, segregation of duties, user provisioning, and security monitoring. Assessments evaluate policy completeness, whether policies reflect current operational reality, and whether enforcement mechanisms ensure consistent application.
Embedding SAP security into corporate governance means executive oversight, defined accountability for security outcomes, regular reporting to audit committees, and integration with enterprise risk frameworks. Governments and regulatory bodies worldwide will demand increased executive attention to SAP Security in 2025. Compliance frameworks like NIST and the European Union's NIS2 directive are set to impose stricter standards, including personal liability for board members failing to achieve compliance.
The Assessment Process: Essential Steps & Best Practices
A structured SAP security assessment follows systematic phases:
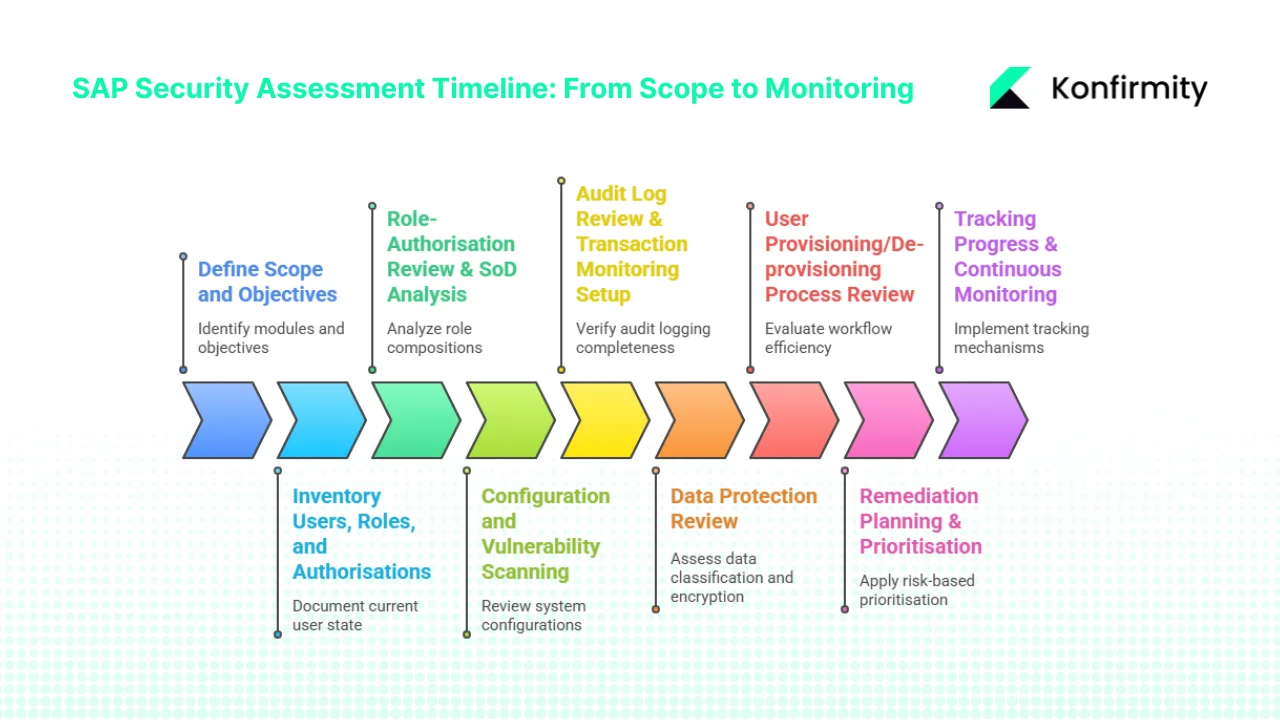
- Define Scope and Objectives: Identify which SAP modules, interfaces, integrations, and environments (production, non-production) require assessment. Align assessment objectives with regulatory requirements, audit findings, or identified security incidents.
- Inventory Users, Roles, and Authorisations: Document the current state—total user accounts, active versus inactive users, role catalogue, authorisation objects, and permission assignments. Baseline data enables gap identification and progress measurement.
- Role-Authorisation Review & SoD Analysis: Analyse role compositions for excessive permissions, evaluate authorisation object assignments, and execute segregation of duties checks against defined ruleset. Identify toxic permission combinations requiring immediate remediation.
- Configuration and Vulnerability Scanning: Review system configurations against security baselines, scan for known vulnerabilities, assess patch levels against SAP Security Notes, and evaluate custom code for security flaws through static analysis and manual review.
- Audit Log Review & Transaction Monitoring Setup: Verify audit logging completeness, review existing logs for anomalous activity, and configure transaction monitoring rules to detect suspicious behaviour patterns.
- Data Protection Review: Assess data classification implementation, evaluate encryption configurations, verify masking effectiveness in non-production environments, and review data access controls.
- User Provisioning/De-provisioning Process Review: Evaluate workflow efficiency, approval mechanism effectiveness, de-provisioning completeness, and periodic recertification execution.
- Remediation Planning & Prioritisation: Apply risk-based prioritisation to findings—addressing critical vulnerabilities and SoD violations first, then remediating moderate risks, and finally resolving low-impact findings. Establish remediation timelines, assign accountability, and define success metrics.
- Tracking Progress & Continuous Monitoring: Implement tracking mechanisms ensuring remediation closure, establish ongoing monitoring for sustained audit readiness, and schedule periodic reassessments to identify new risks.
Best practices for enterprise environments emphasise automation where feasible—automated user access reviews, SoD analysis tools, vulnerability scanners—reducing manual effort while improving coverage. Prioritisation must reflect business risk: high-value transactions, sensitive data access, and privileged accounts receive scrutiny before lower-risk areas. Alignment with external compliance frameworks streamlines audit preparation. Non-production environments require equivalent rigour to prevent data exposure through inadequately secured development or testing systems.
Common pitfalls include maintaining outdated role definitions that no longer match business functions, failing to remediate orphaned accounts, implementing weak audit logging that captures insufficient detail, ignoring custom code vulnerabilities, and establishing policies without enforcement mechanisms.
Compliance & Security Implications for Enterprises
SAP security assessments directly support compliance obligations by generating documented evidence of controls, demonstrating periodic user access reviews, providing audit trails, and validating that data protection mechanisms function effectively. SOX compliance requires documented internal controls over financial reporting—controls implemented through SAP role design, SoD enforcement, and change management. GDPR demands documented data processing activities, access controls protecting personal data, and mechanisms enabling data subject rights—capabilities validated through SAP security assessments.
Security benefits extend beyond compliance: reduced risk of unauthorised access, prevention of fraudulent transactions, protection against data breaches, and improved incident detection through comprehensive monitoring. The business value manifests as strengthened customer confidence, improved internal control effectiveness, fewer audit findings requiring remediation, and enhanced readiness for third-party security assessments demanded by enterprise customers.
Traditional, manual SAP compliance audits are notoriously slow, expensive, and only provide point-in-time snapshots of your security posture, leaving organisations vulnerable between assessments. This legacy approach creates significant friction and consumes valuable resources. Continuous assessment models address this gap through automated monitoring, real-time risk scoring, and ongoing evidence collection supporting sustained audit readiness.
For organisations selling to enterprise clients, demonstrating rigorous SAP security positions your offering as addressing clients' most significant compliance and security obligations. Enterprise procurement increasingly demands vendor attestations, third-party audit reports, and documented security controls. Organisations managing SAP environments meeting these requirements differentiate themselves competitively while enabling faster procurement cycles.
How to Present SAP Security Assessment to Enterprise Clients
Organisations providing managed security services to enterprise clients should position SAP security assessments through messaging emphasising depth of SAP-specific expertise rather than generic IT security capabilities. SAP security demands intimate knowledge of authorisation objects, transaction codes, role hierarchies, and ABAP security—expertise distinct from network security or application security.
Structure service offerings as baseline assessment yielding current-state documentation and prioritised findings, risk prioritisation applying business context to technical vulnerabilities, remediation roadmap defining actionable steps with timelines, and ongoing monitoring maintaining sustained security posture between formal assessments.
Demonstrate outcomes through audit-ready reports documenting control effectiveness, metrics quantifying user access reduction (percentage of excessive permissions removed), role simplification (reduction in total role count while maintaining business functionality), and risk mitigation (vulnerabilities remediated by severity classification). Address procurement concerns directly: compliance readiness supporting client audit requirements, transparency in assessment methodology, integration with clients' existing control frameworks, and measurable return on investment through reduced audit findings and accelerated attestation processes.
Conclusion
SAP security assessments constitute essential components of enterprise compliance and security programmes, providing systematic evaluation of access controls, authorisations, configurations, vulnerabilities, and data protection mechanisms within SAP environments. For enterprise organisations managing critical business processes through SAP systems, rigorous assessments identify exploitable gaps, generate compliance evidence, and establish continuous monitoring sustaining audit readiness.
Because SAP systems are highly valuable targets for malicious actors, organisations must prioritise securing them. The complexity of SAP landscapes, combined with sophisticated threat actors and stringent regulatory requirements, demands assessment programmes executed with SAP-specific domain expertise, risk-based prioritisation, and integration with broader enterprise security frameworks.
Organisations operating SAP environments should incorporate security assessments as recurring discipline rather than periodic projects, implement continuous monitoring mechanisms, and ensure remediation tracking closes identified gaps within risk-appropriate timeframes. Managed security service providers supporting enterprise clients must demonstrate practiced expertise in SAP-specific security domains, deliver actionable outcomes beyond report generation, and position assessments as enabling client compliance obligations while strengthening actual security posture.
FAQ Section
Q1: What is SAP security testing?
SAP security testing encompasses vulnerability scanning, penetration testing of SAP modules and custom code, configuration review against security baselines, role misuse testing, and exploitation attempts against identified weaknesses. Testing validates whether implemented controls function effectively under adversarial conditions, identifying weaknesses that vulnerability assessments might miss. Penetration testing specifically examines RFC-enabled function modules, web interfaces (SAP Fiori, Portal), and custom ABAP programmes for exploitable vulnerabilities.
Q2: What are assessments in SAP?
Assessments in SAP refer to structured reviews examining access controls, authorisations, system configurations, and vulnerabilities to uncover security gaps and compliance deficiencies. These evaluations analyse user-role assignments, segregation of duties violations, patch management effectiveness, audit logging completeness, and data protection implementations. Assessment outputs include current-state documentation, prioritised findings based on business risk, and remediation roadmaps defining corrective actions.
Q3: What is the salary of an SAP security analyst?
SAP security analyst compensation varies significantly by geography, organisation size, and experience level. In the United States, SAP security analysts typically earn between $85,000-$135,000 annually, with senior specialists commanding $120,000-$170,000 in major metropolitan markets. European markets range from €65,000-€110,000 depending on location. Specialists with expertise in SAP GRC (Governance, Risk, and Compliance) modules, S/4HANA security, or both technical and functional SAP security domains command premium compensation due to limited talent availability.
Q4: What exactly is SAP security?
SAP security represents the comprehensive discipline of protecting SAP environments through user and role management, authorisation controls, system configuration hardening, data protection mechanisms, audit logging, policy enforcement, and governance frameworks. This domain encompasses authentication methods, transaction authorisation, segregation of duties enforcement, vulnerability management, patch application, custom code security, interface protection, and monitoring capabilities detecting anomalous behaviour. SAP security extends beyond perimeter defences to address application-layer risks specific to SAP system architecture and business process integration.



.svg)
.svg)
.svg)