Most organizations pursuing enterprise clients underestimate the documentation rigor required to close deals with security-conscious buyers. Enterprise procurement teams demand verifiable proof that vendors maintain robust security controls—and a Security Assessment Report (SAR) provides precisely that evidence. The SAR is one of three key required documents for system authorization, accurately reflecting the results of security control assessment for authorizing officials and system owners.
This glossary term explains what SAR documents are, why they matter for companies selling to enterprise clients, their structural components, how they support compliance frameworks, and best practices for creating effective security assessment documentation that builds client trust.
What is a SAR Document?
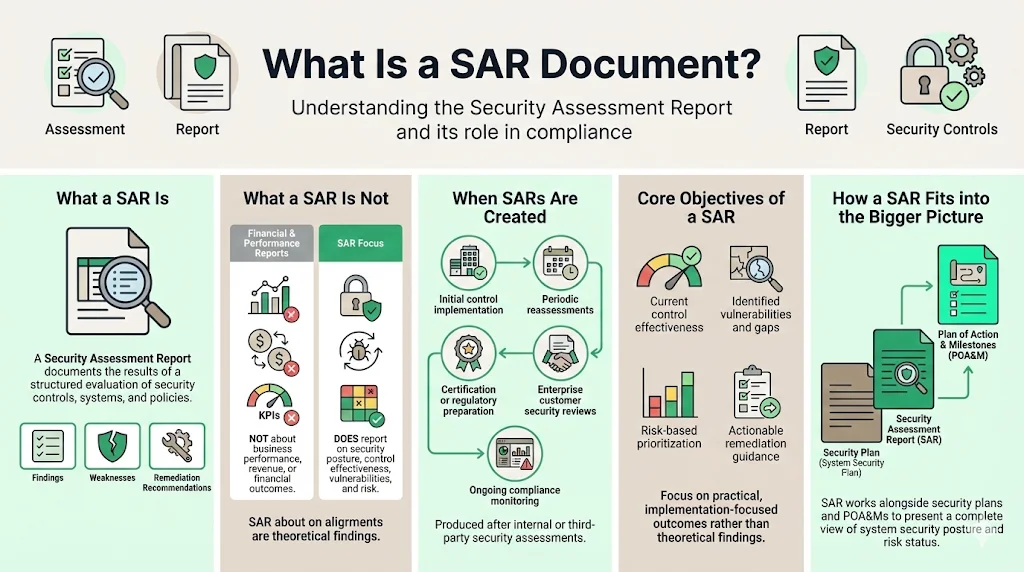
A Security Assessment Report (SAR) is a document that presents findings from security assessments and provides recommendations to address any vulnerabilities or deficiencies found. In the cybersecurity and compliance context, a SAR serves as formal documentation produced after systematic evaluation of an organization's security controls, infrastructure, and policies.
A SAR differs fundamentally from financial reports, performance analyses, or general audit documentation. While financial reports track revenue and expenditure, and performance reports measure operational metrics, the SAR reports on security control assessment results, including any issues, weaknesses and deficiencies, and recommendations. The document focuses exclusively on technical security posture, control effectiveness, vulnerability exposure, and remediation requirements.
Organizations prepare SARs following security assessments conducted by internal teams or third-party assessors. These security assessments typically occur both at initial deployment of control systems as well as during periodic checkpoints throughout the life of the control system. Companies generate SARs when seeking security certifications, responding to enterprise client security questionnaires, preparing for regulatory audits, or maintaining continuous compliance monitoring.
The primary purpose of a SAR centers on four objectives: documenting current security control effectiveness, identifying vulnerabilities or compliance gaps requiring remediation, providing risk-based prioritization of findings, and delivering actionable recommendations with clear implementation guidance. The SAR works together with the security plan and Plans of Action & Milestones (POA&Ms) to provide an overall picture of the security state and risk posture for the information system.
Why Companies—Especially Those Selling to Enterprises—Should Care About SARs
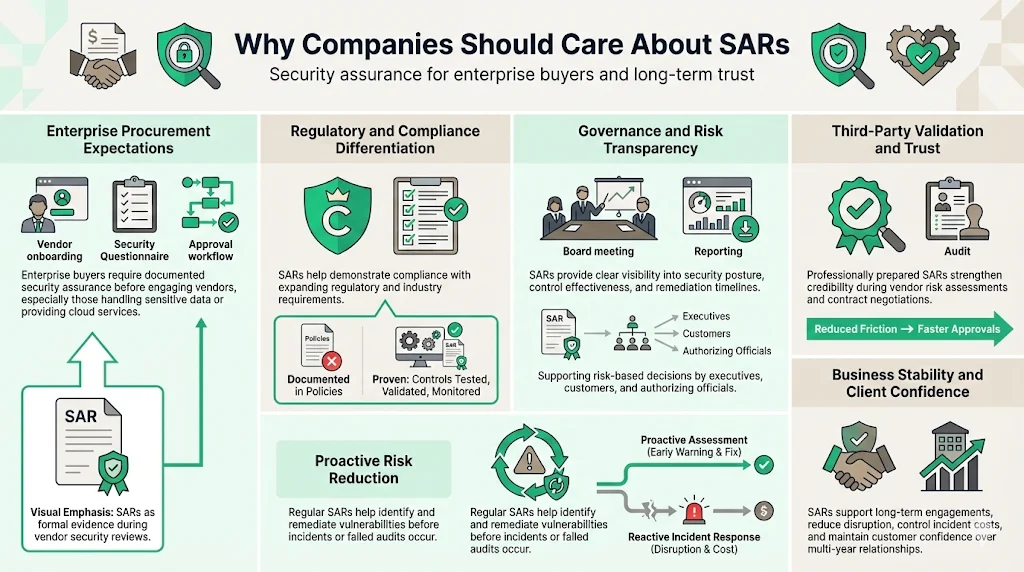
Enterprise procurement processes demand demonstrable security assurance before onboarding third-party vendors. Organizations handling customer data, operating in regulated industries, or providing cloud services face intensified scrutiny regarding their security controls, risk management practices, and audit readiness. A formal SAR provides the documented evidence enterprise clients require during vendor security reviews.
Many industries have stringent security regulations, and SARs help demonstrate compliance by documenting plans and standards. As compliance requirements expand—particularly for cloud service providers, data processors, and companies with access to sensitive enterprise systems—having a professionally prepared SAR differentiates vendors during competitive evaluations. The document demonstrates that security controls exist not merely as policy statements but as tested, validated, and continuously monitored implementations.
SAR documentation supports corporate governance by providing transparency about organizational risk posture, control effectiveness, and remediation timelines. The specific reporting format for security assessment results should provide enough detail to enable the authorizing official to establish a credible, risk-based decision. This transparency proves particularly valuable when enterprise clients conduct vendor risk assessments or require third-party validation before contract execution.
Beyond satisfying procurement requirements, SARs help organizations preempt security gaps before they escalate into incidents or audit failures. Regular security assessments with documented findings create a proactive remediation cycle—identifying vulnerabilities during controlled evaluation rather than discovering them during security incidents or customer-initiated audits. This approach supports long-term business stability, reduces incident response costs, and maintains client confidence throughout multi-year engagements.
Anatomy of a SAR Document: Key Sections & What They Should Cover
A comprehensive SAR follows a standardized structure ensuring consistency, completeness, and usability for technical and executive audiences. While organizational requirements vary, effective SARs contain these core components:
Management Summary / Executive Summary
Many organizations develop an executive summary of the SAR and include it in the beginning of the document. The executive summary highlights and summarizes assessment results, providing key information and recommendations based on weaknesses discovered during the assessment. This section distills complex technical findings into strategic context for decision-makers who need to understand risk exposure, remediation priorities, and resource requirements without parsing detailed technical documentation.
Scope & Methodology
This section defines what systems, applications, network segments, and processes underwent assessment. The methodology section should include details on vulnerability identification and risk categorization as this will impact how the results are interpreted. Documentation should reference specific frameworks or standards guiding the assessment—such as NIST SP 800-53, ISO 27001 controls, or FedRAMP requirements—and describe assessment techniques including vulnerability scanning, penetration testing, configuration reviews, and control validation procedures.
Results / Findings / Audit Findings
Details provided in this section often include identified vulnerabilities, risk rankings, and recommended actions. This core section catalogs each security weakness, control gap, or compliance deficiency discovered during assessment. Findings should include specific technical details, affected systems, evidence supporting the finding, and context explaining why the issue represents risk to the organization or its clients.
Risk Assessment & Impact Analysis
The risk assessment evaluates the potential impact of each vulnerability, assigning a risk level—low, medium, or high—based on likelihood of exploitation and potential damage. Effective risk assessments connect technical findings to business consequences: data breach potential, regulatory non-compliance exposure, operational disruption scenarios, or reputational damage. This contextualization helps prioritize remediation resources toward findings representing the most significant organizational risk.
Recommendations & Remediation Plan
Recommendations must provide specific, actionable guidance beyond generic advice. Document required technical configurations, policy updates, architectural changes, or process improvements. Include implementation timelines, resource requirements, and responsible parties. This is often the lengthiest and most in-depth component because it's about taking action.
Audit Trail / Evidence & Documentation
Evidence produced during the security assessment should be retained by the organization for reuse in future security assessment-related activities either through manual or automated consumption. This section documents the assessment methodology applied to each control, testing procedures executed, evidence collected, and results obtained. Maintaining detailed audit trails proves essential during third-party reviews, regulatory examinations, or when enterprise clients request validation of security claims.
Compliance Review / Regulatory Mapping
Map findings to specific regulatory requirements or framework controls. Document which compliance obligations each finding impacts—whether GDPR data protection requirements, HIPAA technical safeguards, SOC 2 Trust Services Criteria, or ISO 27001 control objectives. This mapping demonstrates compliance awareness and helps prioritize remediation based on regulatory deadlines or certification timelines.
Document Management & Versioning
Once the system is authorized, it enters a state of continuous monitoring. The controls continue to be assessed and the SAR is updated based on the results of these assessments. Document version history, approval dates, distribution lists, and update schedules. Establish clear procedures for maintaining SAR currency as systems change, new vulnerabilities emerge, or remediation activities complete.
Appendices / Annexures
Include supporting technical data: detailed vulnerability scan results, penetration test findings, system inventories, network diagrams, control test procedures, and evidence artifacts. This supplementary material provides technical depth without overwhelming the primary document sections.
How SAR Documents Fit into Broader Corporate Governance, Risk Assessment, and Compliance Frameworks
SARs function as a critical component within comprehensive governance, risk, and compliance (GRC) programs. The document connects security assessment activities to strategic risk management, regulatory compliance requirements, and continuous improvement cycles.
Organizations implementing NIST SP 800-53 security controls conduct assessments validating control implementation and effectiveness—the SAR documents these assessment results. NIST Special Publication 800-115 provides a comprehensive guide for conducting technical security assessments. NIST standards are primarily for government agencies in the U.S., but various industries adopt them due to their rigorous approach to cybersecurity. Companies pursuing ISO 27001 certification use SAR-equivalent documentation to demonstrate Information Security Management System (ISMS) effectiveness during surveillance audits.
When engaging enterprise clients, SARs provide verifiable evidence during vendor security assessments. Procurement teams reviewing third-party risk request documentation proving security controls exist and function as intended—the SAR fulfills this requirement. Organizations undergoing SOC 2 audits reference SAR findings when addressing control deficiencies before the observation period. Companies subject to GDPR compliance leverage SAR documentation during Data Protection Impact Assessments (DPIAs) or when responding to regulatory inquiries about technical safeguards.
The SAR is extensively used for determining reciprocity of the system's authorization by other organizations. This document describes the effectiveness of security controls implemented by the system and identifies controls that are not implemented, functioning as required, or not providing adequate level of protection. This reciprocity proves valuable when multiple enterprise clients require similar security validations—a single comprehensive SAR can satisfy multiple vendor assessment processes.
The SAR operates as part of a continuous security lifecycle rather than a static compliance artifact. Organizations conduct periodic assessments, update SAR documentation, track remediation progress through POA&Ms, and conduct follow-up assessments validating control improvements. This iterative approach demonstrates security maturity and sustained commitment to risk management.
Best Practices for Creating an Effective SAR Document
Most organizations use templates to maintain a clean and clear SAR format. Standardized templates ensure consistency across assessment cycles, facilitate reviewer comprehension, and reduce preparation time. Organizations should adopt templates aligned with their compliance requirements—FedRAMP providers use the official FedRAMP SAR template, while companies pursuing multiple framework compliance may develop hybrid templates addressing overlapping control requirements.
Define assessment scope precisely before beginning evaluation activities. Document which systems, applications, network segments, and data flows fall within scope and which remain excluded. Ambiguous scope creates confusion during assessment execution and undermines SAR credibility when reviewers question coverage completeness. Use robust assessment methodologies combining automated vulnerability scanning, manual penetration testing, configuration reviews, control validation procedures, and personnel interviews. Document the specific tools, techniques, and procedures applied.
Document findings objectively with supporting evidence. Avoid vague language such as "security may be inadequate" or "potential vulnerability exists." Instead, provide specific technical details: "Administrative access to production database servers lacks multi-factor authentication enforcement, creating unauthorized access risk if credentials are compromised." Include screenshots, log excerpts, configuration files, or test results substantiating each finding.
A key piece of information that should be included is a breakdown of the risks identified and their corresponding risk level/category. Categorize findings using consistent risk scoring—whether CVSS scores for technical vulnerabilities or qualitative high/medium/low ratings for control gaps. Assign clear ownership for each remediation item, establish realistic completion timelines, and track progress through formal POA&M processes.
A SAR isn't a one-time solution. Maintain SAR documentation as a living document that evolves with your security posture. Update findings as remediation completes, add new vulnerabilities discovered through continuous monitoring, and refresh assessment results following major system changes or architectural updates. This sustained maintenance demonstrates security maturity and provides enterprise clients with current security posture visibility throughout long-term engagements.
Secure the SAR document itself through appropriate access controls and classification. SARs contain sensitive information about security weaknesses, control gaps, and system architecture that could assist adversaries if disclosed. Implement need-to-know access restrictions, encrypt SAR files, track document distribution, and establish procedures for sharing sanitized versions with clients or auditors when full disclosure proves inappropriate.
Common Misconceptions & What a SAR Is Not
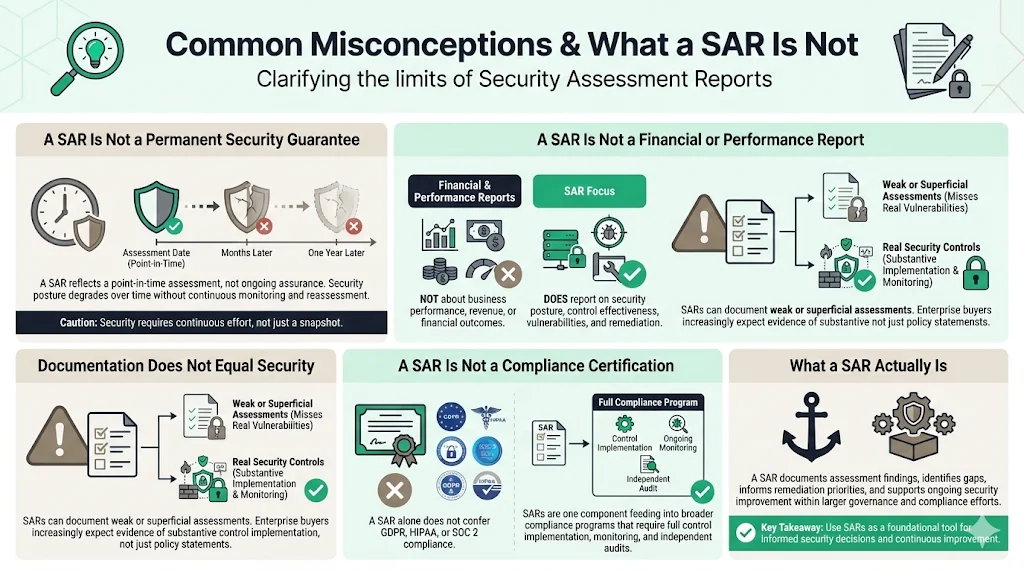
Organizations frequently misunderstand SAR purpose and limitations. A SAR represents a point-in-time assessment of security controls—not a perpetual certification of security adequacy. Security posture changes continuously as systems evolve, new vulnerabilities emerge, and threat landscapes shift. A SAR documenting strong security controls in January provides limited assurance by December if the organization hasn't conducted interim assessments or maintained continuous monitoring.
A SAR differs fundamentally from financial performance reports despite sharing the "report" terminology. Financial reports analyze revenue, expenses, profitability, and fiscal health. Security Assessment Reports evaluate technical controls, vulnerability exposure, compliance gaps, and remediation requirements. Conflating these document types creates confusion during procurement processes or executive reviews.
Having a SAR doesn't guarantee comprehensive security. Organizations can produce SARs documenting superficial assessments that miss critical vulnerabilities or control weaknesses. "Compliance manufacturing" approaches generate impressive documentation while leaving actual security posture fundamentally weak—a practice that satisfies auditors on paper without protecting systems against real threats. Enterprise clients increasingly recognize this distinction, demanding evidence of substantive security controls rather than documentation artifacts.
SARs are not standalone compliance certificates. Organizations cannot achieve GDPR compliance, HIPAA adherence, or SOC 2 certification by simply producing a SAR. These frameworks require comprehensive control implementation, sustained monitoring, formal audits by qualified assessors, and ongoing evidence collection. The SAR serves as one component within broader compliance programs—documenting assessment findings that inform remediation priorities and demonstrate control effectiveness.
When Should Companies Generate a SAR—Typical Triggers & Timing
Organizations should produce or update SAR documentation during several scenarios:
Before engaging enterprise clients who demand security validation during vendor assessment processes. Proactively preparing a comprehensive SAR accelerates procurement cycles and demonstrates security maturity. Companies entering competitive evaluations with well-documented security postures differentiate themselves from vendors lacking formal assessment evidence.
After major system changes—infrastructure migrations, application deployments, architectural redesigns, or technology stack updates—that potentially impact security control effectiveness. Significant changes invalidate previous assessment results, requiring fresh evaluation and updated SAR documentation.
Following periodic review cycles aligned with organizational risk management cadence. Security assessments typically occur both at initial deployment of control systems as well as during periodic checkpoints throughout the life of the control system. Organizations handling sensitive data or operating under regulatory oversight commonly conduct quarterly, semi-annual, or annual assessments depending on risk tolerance and compliance requirements.
After security incidents or near-misses that expose previously unidentified vulnerabilities or control weaknesses. Post-incident assessments document the root causes, control failures that enabled the incident, and remediation measures implemented. These incident-driven SARs prove valuable when communicating with affected clients about response actions and control improvements.
When preparing for third-party audits, certifications, or compliance assessments. Organizations pursuing SOC 2 Type II attestation, ISO 27001 certification, or FedRAMP authorization conduct pre-audit assessments identifying and remediating control gaps before formal auditor evaluation begins. This proactive approach reduces audit findings, accelerates certification timelines, and minimizes remediation costs.
How to Use SAR Documents to Win Enterprise Clients & Build Trust
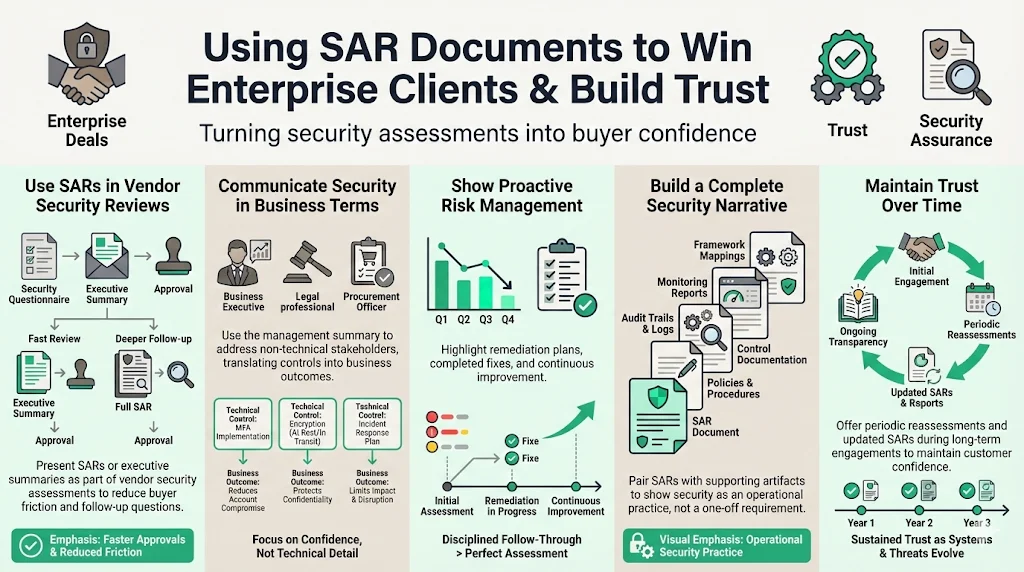
Present SAR documentation—or executive summaries sanitized to remove sensitive technical details—as part of vendor security assessment responses. The authorizing official can use this summary to quickly understand the security status of the system and use the detailed SAR to provide full details for those items that require a more detailed explanation. Enterprise procurement teams reviewing dozens of vendor responses appreciate concise, professional security documentation that answers their due diligence questions without requiring extensive follow-up.
Use the management summary section to communicate with non-technical stakeholders at client organizations—procurement officers, legal counsel, compliance managers, or executive sponsors. These audiences need confidence that your security controls adequately protect their data without understanding technical implementation details. Translate technical findings into business context: explain how multi-factor authentication protects against credential compromise, how encryption safeguards data confidentiality, or how incident response procedures minimize breach impact.
Demonstrate proactive risk management by highlighting your remediation plan and continuous improvement approach. Enterprise clients distinguish between vendors who discover vulnerabilities and ignore them versus vendors who systematically identify, prioritize, and remediate control weaknesses. Document completed remediation activities, show declining vulnerability counts over successive assessment cycles, and provide evidence of sustained security investment.
Combine SAR documentation with complementary compliance artifacts: security policies, control implementation documentation, audit trail evidence, continuous monitoring reports, and compliance framework mappings. This comprehensive security profile demonstrates maturity beyond minimal compliance—showing that security represents an operational discipline rather than a procurement checkbox.
Offer periodic re-assessments and updated SAR documentation throughout long-term client engagements. Security isn't static—enterprise clients recognize this reality and value vendors who provide ongoing transparency about evolving security posture. Regular SAR updates reassure clients that initial security claims remain valid and that the vendor actively monitors for emerging threats or control degradation.
Conclusion
Security Assessment Reports serve as essential documentation for organizations selling to enterprise clients, pursuing compliance certifications, or operating under regulatory oversight. A well-structured SAR—documenting assessment scope and methodology, cataloging findings with supporting evidence, analyzing risks and business impacts, and providing specific remediation guidance—transforms security assessment from a compliance exercise into a strategic governance tool.
Organizations that treat SARs as living documents, updated continuously as security posture evolves, demonstrate the operational discipline enterprise clients demand. This approach positions vendors as trustworthy partners who understand that security compliance represents an outcome of sustained security operations rather than a certification milestone.
With 6,000+ completed audits, Konfirmity understands the documentation rigor enterprise procurement demands. We implement security controls within your existing infrastructure and produce the compliance evidence—including comprehensive SAR documentation—that satisfies even the most security-conscious clients.
Frequently Asked Questions (FAQ)
1) What is a SAR document?
A SAR (Security Assessment Report) is a document that presents findings from security assessments and provides recommendations to address any vulnerabilities or deficiencies found. The report documents security control effectiveness, identifies compliance gaps, assesses risk levels, and includes specific remediation guidance. Organizations produce SARs following systematic evaluation of security infrastructure, policies, and technical controls.
2) Who needs to file a SAR report?
Organizations undergoing security assessments—particularly those handling sensitive data, operating in regulated industries, providing cloud services, or pursuing enterprise client relationships—need SAR documentation. Companies seeking security certifications such as FedRAMP authorization, ISO 27001 certification, or SOC 2 attestation produce SARs as part of formal audit processes. A Security Assessment Report is a document prepared by a Third-Party Assessment Organization (3PAO) that details findings from a security assessment of a cloud service provider. Internal security teams or qualified third-party assessors prepare SARs depending on organizational requirements and compliance frameworks.
3) What is a SAR file?
"SAR file" refers to the document file containing the complete Security Assessment Report. The file includes all SAR sections—executive summary, methodology documentation, detailed findings, risk assessments, remediation recommendations, supporting evidence, and appendices. Organizations typically maintain SAR files as controlled documents with version history, distribution tracking, and access restrictions due to sensitive security information content.
4) What is the purpose of a SAR report?
The SAR serves multiple purposes: documenting current security control implementation and effectiveness, identifying vulnerabilities or compliance gaps requiring remediation, providing risk-based prioritization of findings based on potential business impact, offering actionable recommendations with specific implementation guidance, supporting compliance framework requirements and regulatory reviews, and demonstrating to enterprise clients that the organization maintains robust security governance. The SAR is critical in determining the level of risk that will be introduced to the organization if the system is placed into production.



.svg)
.svg)
.svg)