Most organizations treat compliance as a one-time achievement, but enterprise clients evaluating service providers require continuous assurance that critical internal controls operate effectively—particularly when those controls directly impact their own financial reporting obligations under regulations like Sarbanes-Oxley. SSAE 16 emerged as the attestation framework designed to address this need for documented, audited control environments at service organizations.
Enterprise buyers demand SSAE 16 attestation (or its successor standards) because outsourced services introduce operational dependencies that directly affect risk management, regulatory compliance, and internal control frameworks. When a public company relies on an external payroll processor, data center, or SaaS platform, that vendor's control failures become the client's compliance gaps. Service organizations faced client requirements for SSAE 16 precisely because it provided visibility into internal controls—moving beyond vendor assurances to independently verified evidence.
This article examines what SSAE 16 is, how the attestation framework operates, its practical implications for service providers and their clients, the evolution to SSAE 18, and what organizations must understand about this standard in 2026.
What is SSAE 16?
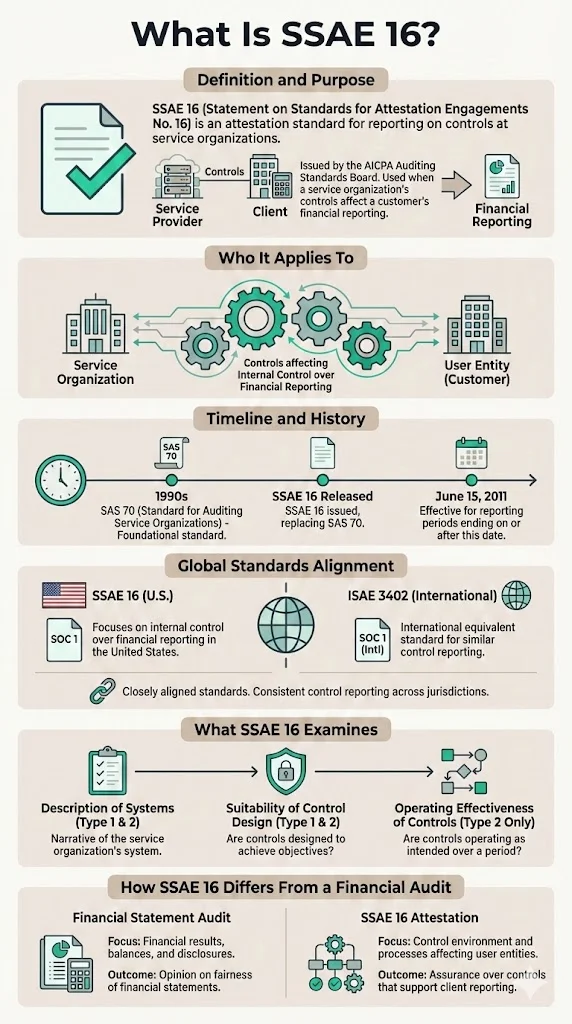
Statement on Standards for Attestation Engagements No. 16 is an attestation standard put forth by the Auditing Standards Board of the American Institute of Certified Public Accountants that addresses engagements undertaken by a service auditor for reporting on controls at organizations that provide services to user entities, where a service organization's controls are likely to be relevant to a user entity's internal control over financial reporting.
SSAE 16 was released in April 2010 and replaced Statement on Auditing Standards No. 70, which had been the prevailing standard for service organization reporting since the 1990s. SSAE 16 effectively replaced SAS 70 for service auditor's reporting periods ending on or after June 15, 2011.
The standard was designed to align with the international standard ISAE 3402, which closely mirrors SSAE 16 and was issued by the International Auditing and Assurance Standards Board. This alignment reflected the growing push for globally accepted accounting standards and allowed multinational enterprises to rely on consistent attestation frameworks across jurisdictions.
Unlike traditional financial statement audits, SSAE 16 focuses on attestation—a distinct engagement type where an independent CPA examines and reports on a service organization's description of its systems and the suitability and operating effectiveness of controls. The auditor provides assurance not about financial statements directly, but about the control environment that underpins client organizations' own financial reporting accuracy.
Key Concepts and Terminology
1) Service Organization Controls and SOC Reports
SSAE 16 forms the underlying platform for the AICPA SOC reporting framework, which consists of SOC 1, SOC 2, and SOC 3 reports. Under SSAE 16, service auditors evaluate controls at organizations whose services affect user entities' financial reporting, issuing what became known as a SOC 1 report. This report documents the evaluation of controls over systems and processes relevant to clients' internal control over financial reporting (ICFR).
2) Internal Controls Assessment
SSAE 16 requires a comprehensive assessment of internal controls—both by the service organization's management and by the independent auditor. The service auditor must obtain an understanding of the service organization's control environment, assess the risk of material misstatement, test the operating effectiveness of the controls, and obtain sufficient appropriate evidence to support the opinion on the design and operating effectiveness of the controls. This dual-layer assessment ensures controls are both properly designed and functioning as intended.
3) Attestation Engagement
SSAE 16 defines an attestation engagement distinct from an audit. Management of the service organization must provide written assertions regarding the design and operating effectiveness of the controls, and the service auditor must evaluate the evidence obtained and the assertions made by management, providing a report that expresses an opinion on the fairness of the presentation of the description of the service organization's system and the suitability of the design and operating effectiveness of the controls. This structure places explicit accountability on management while providing independent verification.
4) Control Environment and Control Objectives
In the SSAE 16 context, service organizations define control objectives relevant to the services they provide—specifically those controls that could affect user entities' financial reporting. SSAE 16 is a service auditor's attestation that a service organization has been through an in-depth evaluation of their control objectives and control activities. The organization describes its systems, documents how controls are designed to meet stated objectives, and demonstrates through testing that controls operate effectively. The auditor then evaluates whether those controls actually achieve the defined objectives.
5) Audit Procedures and Reporting Requirements
SSAE 16 requires that the service organization provide a description of its "system" along with a written assertion by management. This is a substantive shift from prior standards—the report must include a full system description, not merely a list of controls. For Type 2 reports, evidence of operating effectiveness over an observation period (typically six or more months) is mandatory. The auditor performs detailed testing procedures, documents findings, and issues an opinion on both design suitability and operating effectiveness.
6) User Entity Controls
SSAE 16 reports delineate which controls reside with the service organization and which complementary controls user entities must implement. This concept acknowledges that effective internal control over financial reporting requires coordinated efforts—a service organization's controls function properly only when user entities implement their own corresponding controls. For example, a payroll service provider may control data processing accuracy, but user entities retain responsibility for reviewing reports and authorizing payments.
7) Risk Management and Assurance Services
By obtaining SSAE 16 attestation, service organizations provide structured assurance about risk mitigation and control practices. This moves beyond informal vendor promises to documented, independently verified control frameworks. The attestation becomes part of the service organization's risk management offering, demonstrating to clients that operational risks have been systematically identified, controls have been implemented to address those risks, and independent verification confirms control effectiveness.
Types of SSAE 16 Reports
SOC 1 Report
Under SSAE 16, SOC 1 reports focus on controls relevant to user entities' internal control over financial reporting. These reports are designed for service organizations whose services could materially affect clients' financial statements—data centers hosting financial systems, payroll processors, claims administrators, transaction processors, and similar providers. SOC 1 reports under SSAE 16 became the direct successor to SAS 70 reports.
Type I vs Type II
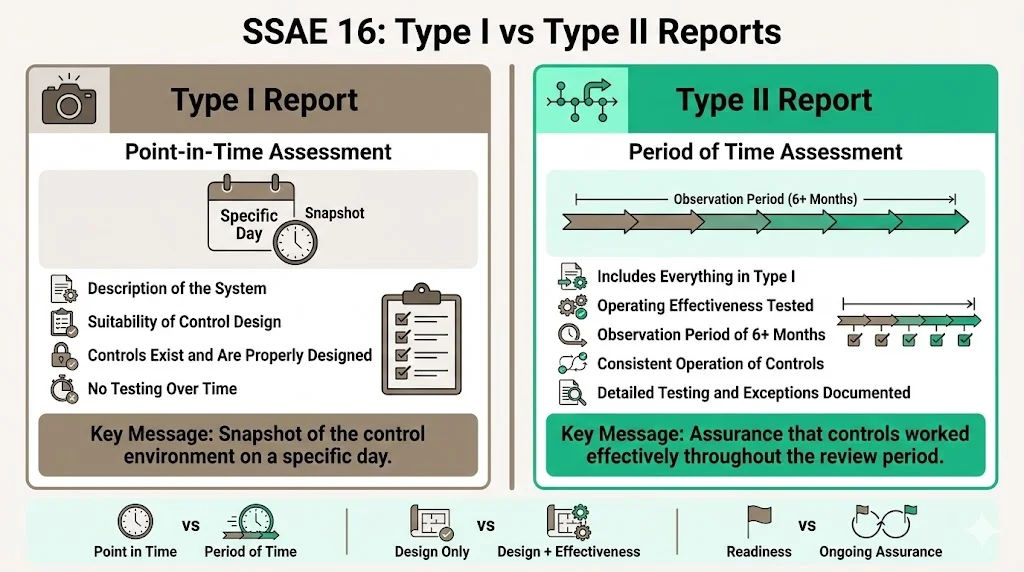
Two types of SSAE 16 reports are issued: Type 1 and Type 2.
- Type I reports provide an auditor's opinion on the description of the service organization's system and the suitability of the design of controls at a specific point in time. A SOC 1 Type 1 report is an independent snapshot to reflect the status of an organization's control landscape on a given day. This report confirms that controls exist and are appropriately designed to meet stated control objectives, but does not evaluate whether those controls operated effectively over time.
- Type II reports include everything in a Type I report, plus an evaluation of operating effectiveness over a defined observation period. A Type 2 report provides an opinion on the design and the effectiveness of the controls over a period of time, usually 6 or more months. The auditor tests whether controls operated consistently and effectively throughout the observation period, documents exceptions or deviations, and provides detailed test results.
How Organizations Use Them
Many service organizations begin with Type I reports to establish baseline control documentation and demonstrate initial audit readiness. However, enterprise clients—particularly public companies subject to Sarbanes-Oxley Section 404 requirements—typically require Type II reports. The extended observation period and operating effectiveness testing provide substantially greater assurance. A Type I report confirms controls exist; a Type II report proves controls work consistently over time, which is what auditors of user entities need when assessing reliance on service organization controls.
Why Companies Selling to Enterprises Care About SSAE 16
1) Demonstrates Internal Control Maturity
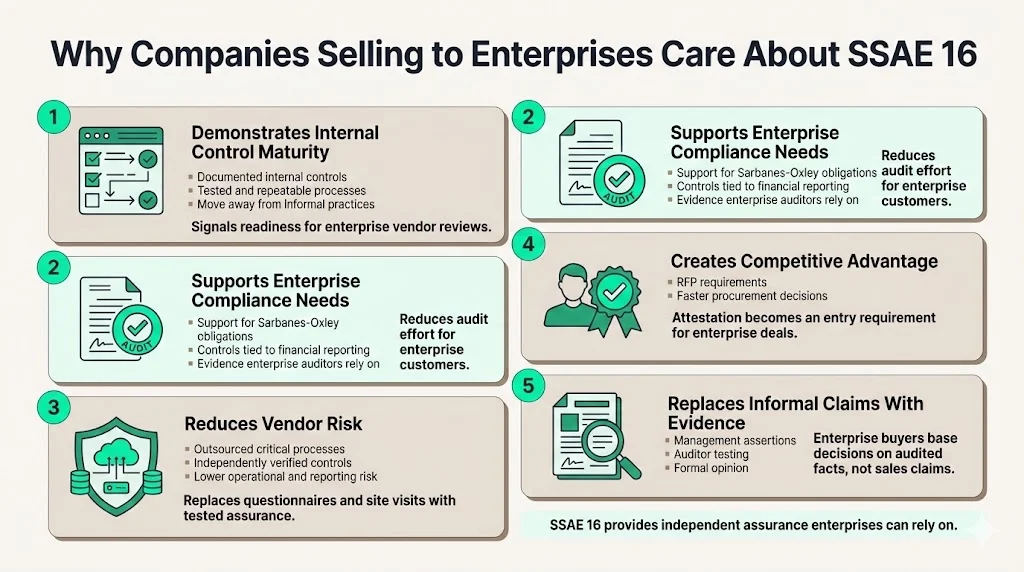
For companies providing outsourced services—hosting infrastructure, SaaS platforms, data processing, payroll administration, benefits management—SSAE 16 attestation demonstrates structured internal control maturity. It signals that the organization has moved beyond ad hoc operational practices to documented, tested control frameworks. This matters when selling to enterprises that evaluate vendor risk as part of procurement decisions and ongoing vendor management programs.
2) Supports Compliance Needs of Enterprise Clients
Public companies in the United States fall under Sarbanes-Oxley, and SSAE 16 reporting can help service organizations comply with requirements to show effective internal controls covering financial reporting. When enterprises outsource processes that affect financial reporting, they must evaluate whether service organization controls are adequate. An SSAE 16 SOC 1 report provides the documented evidence enterprise auditors need to assess whether reliance on service organization controls is appropriate. Without this attestation, enterprises face significantly more complex and costly audit procedures to verify vendor controls independently.
3) Reduces Vendor Risk
Enterprise clients outsource critical processes—payment processing, transaction reconciliation, data storage and retrieval, employee compensation administration. Each outsourced process introduces operational and financial reporting risk. Known, documented, independently verified internal controls reduce this risk materially. An SSAE 16 report allows enterprise risk management and audit teams to evaluate control effectiveness systematically rather than relying on vendor questionnaires, site visits, or contractual representations.
4) Adds Competitive Advantage and Trust Signal
Service providers with SSAE 16 attestation differentiate themselves when competing for enterprise clients who maintain formal vendor risk management programs. Procurement teams at regulated companies often include SOC report requirements in RFPs. Organizations without attestation face disqualification or extended evaluation cycles involving on-site audits, detailed control documentation requests, and elevated vendor risk ratings. SSAE 16 becomes a market entry requirement, not merely a nice-to-have credential.
5) Provides Structured Assurance Instead of Informal Promises
Vendor assurances about "strong controls" or "robust security" lack credibility without independent verification. SSAE 16 provides a documented control framework, management assertions about control effectiveness, independent auditor testing and evaluation, and a formal opinion. This structured assurance replaces vague vendor claims with verifiable evidence, allowing enterprise clients to make informed risk decisions based on audited facts rather than marketing representations.
Limitations and What SSAE 16 Does Not Cover
1) No Fixed Universal Control Set
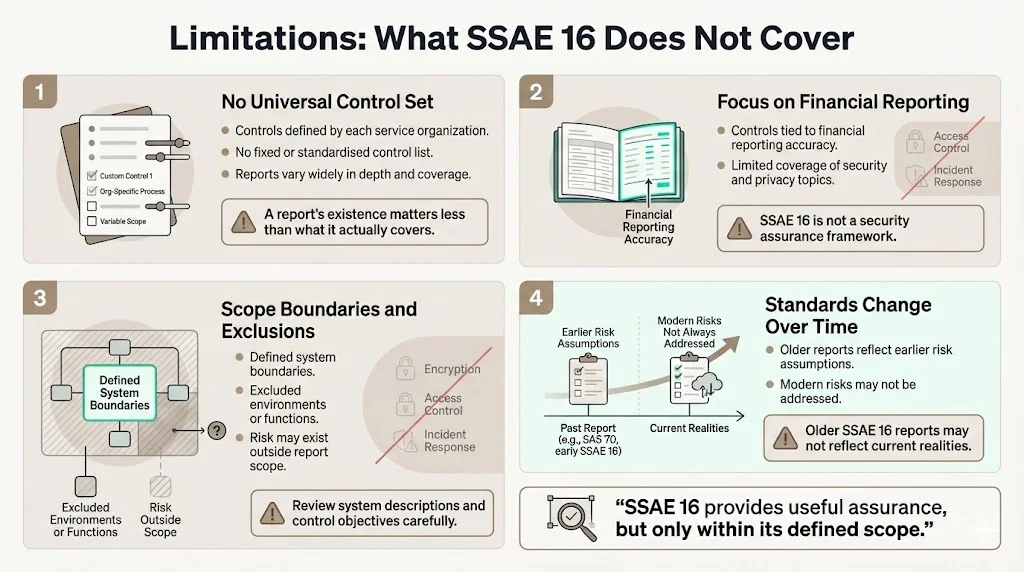
SSAE 16 does not mandate a specific set of controls that every service organization must implement. Each organization defines its own control objectives based on the services it provides and the risks those services present to user entities' financial reporting. This means SSAE 16 SOC 1 reports vary significantly across providers. One organization's report might address 35 control objectives across transaction processing, data integrity, and change management; another might address 60 control objectives including disaster recovery, logical access, and vendor management. Enterprises evaluating SSAE 16 reports must scrutinize which control objectives were assessed, not merely whether a report exists.
2) Primarily Covers Financial Reporting Controls
SSAE 16 focuses on controls relevant to internal control over financial reporting. It does not necessarily address data security, confidentiality, privacy, availability, or processing integrity unless those aspects directly affect financial reporting accuracy. A service organization with an SSAE 16 SOC 1 report may have strong controls over transaction completeness and accuracy but weak controls over data encryption, access management, or incident response. Organizations seeking assurance over information security controls need different reporting frameworks—typically SOC 2.
3) Scope Limitations
Because service organizations define their own control objectives and system boundaries, SSAE 16 reports may exclude significant operational areas. A report might cover production systems but exclude disaster recovery capabilities, or address application controls but not infrastructure security. User entities must carefully review system descriptions and control objective statements to identify what falls outside report scope—and assess whether excluded areas present unmitigated risks.
4) Evolution of Standards
SSAE 16 represented a specific point in the evolution of attestation standards. Audit frameworks, regulatory expectations, and technology risks continue advancing. Reports prepared under SSAE 16 may not address contemporary concerns about cloud security, API integrations, continuous monitoring, or advanced persistent threats. Organizations relying on older SSAE 16 reports should consider whether those reports reflect current operational realities and emerging risk factors.
What Happened After SSAE 16: Evolution and Current Status
SSAE 16 was superseded by an updated set of auditing standards, SSAE 18, on May 1, 2017. For audit opinion letters dated on or after that date, SSAE 18 became the applicable standard for attestation engagements.
SSAE 18 was put forth to address concerns over the clarity, length, and complexity of various standards developed by the Auditing Standards Board of the American Institute of Certified Public Accountants. The new standard clarified attestation requirements, refined terminology, and incorporated lessons learned from years of SSAE 16 implementation. SSAE 18 consolidated multiple prior attestation standards into a unified framework, improving consistency and usability for both auditors and service organizations.
SSAE 18 introduced enhanced requirements around risk assessment, evidence evaluation, and reporting. SSAE 18 defined evidence with more clarity, requiring SOC auditors to dig deeper in asking for more detailed evidence, and service organizations in turn needing to start retaining more detailed records. The standard also placed greater emphasis on subservice organization controls and how service organizations manage vendor relationships—recognizing that modern service delivery often involves complex vendor ecosystems.
Even though SSAE 16 itself is no longer the current standard, legacy SSAE 16 SOC 1 reports remain in circulation and may still provide useful information about historical control environments. However, for organizations pursuing new attestation engagements or evaluating vendor compliance, SSAE 18 is the governing framework. The transition from SSAE 16 to SSAE 18 was evolutionary rather than revolutionary—core concepts remained consistent, with refinements to improve clarity and address implementation challenges identified over six years of SSAE 16 practice.
Beyond SOC 1 reporting, the broader SOC framework under SSAE 18 includes SOC 2 reports (addressing security, availability, processing integrity, confidentiality, and privacy based on Trust Services Criteria) and SOC 3 reports (general-use versions of SOC 2 for public distribution). This expanded framework recognizes that service organizations must address control concerns beyond financial reporting—particularly as data security, privacy regulations, and cyber risk have become primary enterprise concerns.
Practical Implications for Service Providers and Their Clients
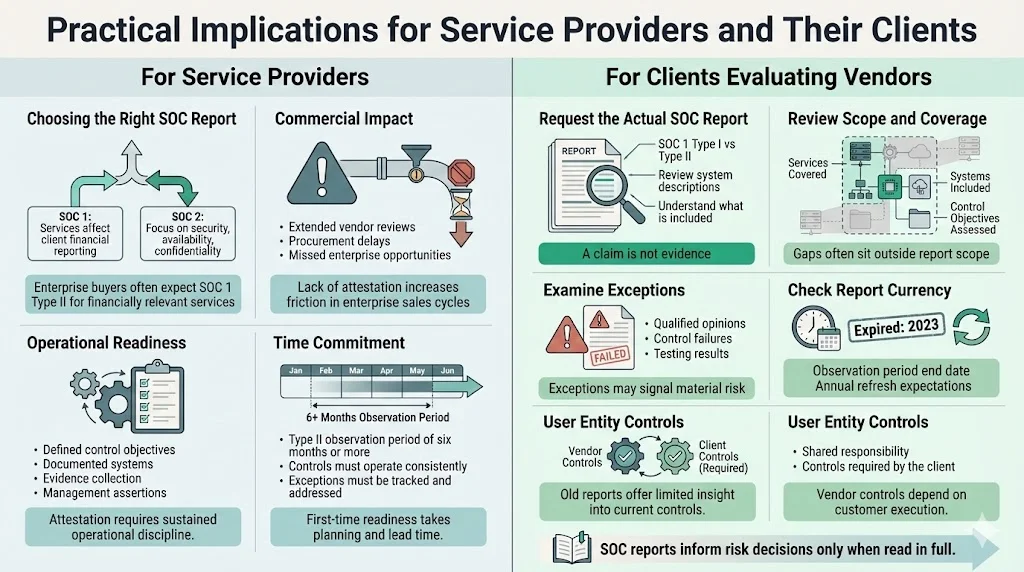
For Service Providers
Service organizations offering hosting, SaaS, payroll processing, benefits administration, or data management should evaluate whether SOC 1 attestation (formerly under SSAE 16, now under SSAE 18) is necessary to meet enterprise client requirements. If your services materially affect client financial reporting—transaction processing, financial data storage, calculation services, reconciliation functions—expect enterprise procurement and audit teams to require SOC 1 Type II reports. Without this attestation, you face competitive disadvantage and extended vendor evaluation cycles.
Consider whether SSAE 18 SOC 2 reporting better addresses your client needs. Many modern service organizations pursue SOC 2 rather than SOC 1 because enterprise clients increasingly prioritize data security, availability, and confidentiality over narrow financial reporting controls. Evaluate your services, client requirements, and risk profile to determine the appropriate reporting framework.
Internal readiness requires substantial operational maturity. Organizations must define clear control objectives, implement control activities, document systems comprehensively, establish evidence collection processes, and prepare management assertions. Type II reports require observation periods of six months minimum—meaning first-time attestation takes significant lead time. Controls must operate consistently and effectively throughout the observation period, with documented evidence of control performance, exception handling, and remediation. This operational discipline cannot be manufactured in weeks before an audit; it requires systematic implementation and sustained execution.
For Clients Evaluating Vendors
Don't accept vague claims of "SSAE 16 compliance." Request the actual SOC report—either SOC 1 Type I or Type II—and scrutinize the contents carefully. Review the system description to understand what services and systems are covered. Examine the control objectives to determine whether they address risks relevant to your organization. Check the observation period for Type II reports—reports covering only three months provide less assurance than those covering twelve months.
Pay attention to exceptions and qualifications. The auditor's opinion may be qualified if control deficiencies were identified or if testing revealed exceptions. Read the detailed test results and exception descriptions to understand control effectiveness. Evaluate whether identified exceptions present material risk to your organization's financial reporting or operations.
Verify that reports are current. SOC reports typically cover annual observation periods, but organizations often allow reports to age significantly before pursuing new audits. A SOC 1 Type II report with an observation period ending eighteen months ago provides limited assurance about current control effectiveness. Establish vendor management policies requiring annual SOC reports and evaluate vendors whose reports lapse or become outdated.
Understand user entity controls. SOC reports identify complementary user entity controls—controls that your organization must implement for the service organization's controls to function effectively. Review these carefully and ensure your organization has implemented required controls. Failure to implement user entity controls creates control gaps even when the service organization maintains effective controls.
Conclusion
SSAE 16 represented a critical evolution in how service organizations demonstrate control maturity and provide assurance to enterprise clients. Though superseded by SSAE 18 in 2017, the framework established under SSAE 16—independent attestation on control design and operating effectiveness through SOC reports—remains fundamental to enterprise vendor risk management.
Organizations treating these attestations as compliance checkboxes miss the substantive value. Implementing documented control frameworks, maintaining consistent control operation, collecting systematic evidence, and subjecting controls to independent evaluation builds operational discipline that reduces risk, prevents control failures, and supports sustainable service delivery. For service organizations selling to enterprises, this discipline becomes a competitive requirement. For enterprises evaluating vendors, audited control frameworks provide the documented assurance necessary to manage outsourcing risk effectively.
The shift from SSAE 16 to SSAE 18, and the expansion from SOC 1 to SOC 2 and SOC 3 reporting, reflects the evolving nature of service organization risk. Financial reporting controls remain critical for certain service categories, but data security, availability, and privacy have become equally important assurance areas. Organizations must evaluate which attestation frameworks address their specific risk profile and client requirements—then commit to the operational maturity necessary to maintain effective controls over time.
Frequently Asked Questions
1) What is an SSAE 16 audit?
An SSAE 16 audit is a service auditor's attestation that a service organization has been through an in-depth evaluation of their control objectives and control activities, with results reported. The engagement involves an independent CPA examining the service organization's system description, evaluating control design, testing operating effectiveness (for Type II reports), and issuing a SOC 1 report providing an opinion on controls relevant to user entities' financial reporting.
2) Is SSAE 16 the same as SOC 2?
No. SSAE 16 typically results in a SOC 1 report focusing on internal controls relevant to financial reporting. SOC 2 is a different report type addressing security, availability, processing integrity, confidentiality, and privacy of data based on AICPA Trust Services Criteria. SOC 1 addresses financial reporting accuracy; SOC 2 addresses information security and data protection. Organizations whose services primarily affect client financial reporting pursue SOC 1; those whose services involve data handling, system availability, or processing sensitive information typically pursue SOC 2.
3) What is an SSAE audit?
An SSAE audit refers broadly to an attestation engagement conducted under Statement on Standards for Attestation Engagements standards, where a CPA assesses and reports on a service organization's control environment, systems, and control objectives. The auditor evaluates whether management's assertions about control design and operating effectiveness are fairly stated, performs testing procedures, and issues an independent opinion. SSAE audits differ from financial statement audits in that they focus on control frameworks rather than financial results.
4) Is SSAE 16 still valid?
Officially, no. SSAE 18 superseded SSAE 16 on May 1, 2017. For audits with opinion dates on or after that date, SSAE 18 governs attestation engagements and SOC report issuance. However, older SSAE 16 SOC 1 reports may still circulate and provide relevant information about historical control environments. Organizations evaluating vendors should request current reports prepared under SSAE 18 standards rather than relying on outdated SSAE 16 reports.



.svg)
.svg)
.svg)