Most healthcare organizations implement privacy safeguards only when audit deadlines approach or breach notifications become mandatory. This reactive approach creates fundamental operational gaps—gaps that become apparent when patient complaints escalate, regulatory investigations begin, or unauthorized disclosures occur. The HIPAA Privacy Rule establishes national standards that require sustained compliance, with key Notice of Privacy Practices modifications mandated by February 16, 2026.
What Is "The Privacy Rule"?
The HIPAA Privacy Rule represents the first comprehensive federal protection for the privacy of protected health information (PHI). Enacted as part of the Health Insurance Portability and Accountability Act of 1996, the Privacy Rule establishes baseline standards governing how covered entities collect, use, and disclose individually identifiable health information. These requirements extend beyond simple data protection—they mandate documented policies, workforce training, patient rights protocols, and accountability mechanisms that form the operational foundation for healthcare compliance.
The Privacy Rule operates within the broader HIPAA framework alongside the Security Rule and the Breach Notification Rule. While the Security Rule addresses technical safeguards specifically for electronic PHI, the Privacy Rule applies to all forms of PHI: written, oral, and electronic. Organizations frequently misunderstand this distinction, implementing robust cybersecurity measures while overlooking verbal disclosures, printed records, and faxed transmissions that equally require protection under Privacy Rule standards.
Who Must Follow the Privacy Rule
Covered entities bear primary responsibility for Privacy Rule compliance. This category encompasses three distinct types of organizations: health care providers who transmit health information electronically in connection with standard transactions, health plans that pay for medical care, and health care clearinghouses that process health information between nonstandard and standard formats. A physician practice conducting electronic billing, an employer-sponsored health plan, or a claims processing company all qualify as covered entities subject to full Privacy Rule requirements.
Business associates represent the second tier of regulated entities. These organizations perform functions or activities involving PHI on behalf of covered entities—medical billing services, cloud storage providers, practice management software vendors, and legal consultants handling patient records. Business associates face increasingly stringent obligations, including 24-hour breach reporting requirements that tighten third-party risk management. The business associate designation triggers contractual requirements: covered entities must execute business associate agreements establishing permitted uses, disclosure limitations, and security obligations before any PHI exchange occurs.
Not every organization handling health-related information falls under Privacy Rule jurisdiction. Employers maintaining employee health records in personnel files, life insurers, workers' compensation carriers, and many educational institutions operate outside HIPAA's scope. This creates compliance complexity for organizations operating in multiple regulatory environments—a hospital system must apply Privacy Rule protections to patient treatment records while managing employee health benefits under separate employment law frameworks.
What Information the Privacy Rule Protects
Protected health information comprises individually identifiable health information transmitted or maintained in any medium. PHI includes medical records, billing information, clinical laboratory results, pharmacy records, insurance claims, and any data element that could reasonably identify an individual. The identification threshold extends beyond obvious markers like names and Social Security numbers to encompass 18 specific identifiers: dates directly related to the individual, telephone numbers, email addresses, medical record numbers, health plan beneficiary numbers, device identifiers, biometric identifiers, full-face photographs, and any other unique identifying characteristic.
The Privacy Rule's protection scope encompasses all three information formats: electronic records stored in practice management systems, written documents including prescription pads and appointment schedules, and oral communications between providers discussing patient care in hospital corridors. This comprehensive coverage requires organizations to implement physical safeguards preventing unauthorized visual access to records, administrative policies governing verbal communications in public spaces, and technical controls securing electronic transmissions.
De-identified information falls outside Privacy Rule protections. Organizations may remove the 18 specified identifiers through the safe harbor method or obtain statistical certification that re-identification risk remains very small. Properly de-identified data enables research, quality improvement initiatives, and business analytics without triggering authorization requirements or use restrictions. However, organizations frequently fail to remove indirect identifiers—a combination of diagnosis, procedure date, and geographic location often permits re-identification despite removing explicit name and record number fields.
Patient Rights Under the Privacy Rule
The Privacy Rule establishes six core individual rights that covered entities must honor through documented processes. The right of access permits individuals to inspect and obtain copies of their PHI maintained in designated record sets, with limited exceptions for psychotherapy notes and information compiled for legal proceedings. Covered entities must respond to access requests within 30 days, providing records in the format requested when readily producible. Organizations charging excessive fees for records or implementing bureaucratic obstacles to access face significant enforcement risk—the HHS Office for Civil Rights prioritizes access complaints in compliance investigations.
Patients possess the right to request amendments to their PHI when they believe information is inaccurate or incomplete. Covered entities may deny amendment requests if records were not created by the entity, the information is not part of the designated record set, or the record is accurate and complete. However, the denial must follow specific procedural requirements: providing written explanations, allowing patients to submit disagreement statements, and appending these statements to the contested record.
Additional rights include requesting restrictions on uses and disclosures for treatment, payment, and healthcare operations (which covered entities may deny except for restrictions on disclosures to health plans when patients pay out-of-pocket in full), requesting confidential communications through alternative means or locations, and obtaining an accounting of disclosures made for purposes other than treatment, payment, and operations. These rights require operational infrastructure—tracking systems, response protocols, staff training, and documentation procedures that many organizations implement inadequately until enforcement actions reveal deficiencies.
Permitted Uses and Disclosures of PHI
The Privacy Rule permits covered entities to use and disclose PHI without individual authorization for three core purposes: treatment, payment, and healthcare operations. Treatment encompasses providing, coordinating, or managing healthcare services—a primary care physician sharing records with a specialist consultant, an emergency department accessing a patient's medication history, or a physical therapist reviewing surgical notes before initiating rehabilitation. Payment activities include billing, claims management, utilization review, and determining coverage eligibility. Healthcare operations cover quality assessment, care coordination, case management, credentialing, compliance programs, and business planning activities essential to running healthcare organizations.
Beyond these core purposes, the Privacy Rule permits specific disclosures without authorization in defined circumstances: when required by law, for public health activities, to report abuse or neglect, for health oversight activities, in judicial proceedings pursuant to court orders, for law enforcement purposes under specific conditions, to avert serious threats to health or safety, for specialized government functions including military and veterans affairs, and for workers' compensation programs. Each permitted disclosure category includes specific requirements and limitations—disclosures for law enforcement purposes require warrants or administrative requests meeting defined criteria, public health disclosures must relate to preventing or controlling disease, and serious threat disclosures require good faith belief that disclosure is necessary to prevent imminent harm.
Organizations commonly exceed permitted disclosure boundaries through inadequate staff training and insufficient process controls. A provider sharing detailed clinical information with a patient's employer beyond fitness-for-duty determinations, a billing department disclosing treatment details to collection agencies without proper authorizations, or administrative staff confirming patient presence to unauthorized callers all constitute Privacy Rule violations stemming from operational failures rather than intentional misconduct.
The Minimum Necessary Standard
The minimum necessary standard requires covered entities to make reasonable efforts to limit PHI uses, disclosures, and requests to the minimum necessary to accomplish the intended purpose. This principle applies to all uses and disclosures except those for treatment purposes, disclosures to the individual, uses or disclosures pursuant to valid authorizations, and disclosures to HHS for compliance investigations. Organizations must implement policies identifying routine and recurring uses and disclosures, establishing the minimum necessary PHI for these situations, and limiting access to PHI based on workforce roles and responsibilities.
Applying the minimum necessary standard requires risk-based judgment rather than checklist compliance. A billing specialist requires access to diagnosis codes and procedure information but typically needs no access to detailed clinical notes. Registration staff members need demographic and insurance information but should not access treatment records. Organizations implementing role-based access controls, establishing default access limitations, and conducting periodic access reviews demonstrate operational maturity in applying minimum necessary principles.
The minimum necessary standard extends to requests for PHI from other covered entities. When requesting records for payment or healthcare operations, organizations must limit requests to specific, relevant information rather than demanding entire medical records. A workers' compensation insurer investigating a back injury claim should request records related to the specific injury and treatment rather than complete lifetime medical histories. Covered entities receiving overly broad requests should push back, requesting clarification and limitation to reasonably necessary information.
The Privacy Rule's Role in Compliance
Privacy Rule compliance requires documented policies addressing every required standard, workforce training ensuring staff understand their obligations, designated privacy officials with authority to implement policies, complaint procedures allowing individuals to report concerns, sanctions for workforce members who violate policies, and mitigation procedures addressing harmful effects of improper uses or disclosures. These administrative requirements create audit trails demonstrating compliance efforts—documentation that becomes critical when investigations occur.
Organizations treating compliance as annual training completion and policy acknowledgment exercises fundamentally misunderstand Privacy Rule requirements. Effective compliance programs embed privacy considerations into operational workflows: authorization tracking integrated with scheduling systems, access logs reviewed regularly for inappropriate queries, disclosure accounting automated through information systems, and incident response protocols activated immediately when unauthorized access occurs. The HHS Office for Civil Rights evaluates compliance through this operational lens—examining how organizations actually implement policies rather than simply reviewing written procedures.
Recent developments confirm that OCR maintains Privacy Rule enforcement as an ongoing priority, with rule finalization remaining on the official regulatory agenda for May 2026. Enforcement actions increasingly target systemic failures: inadequate risk analyses, insufficient business associate oversight, delayed breach investigations, and failure to provide timely access to medical records. Organizations believing they can manufacture compliance through documentation without operational implementation inevitably face enforcement exposure when complaints trigger investigations revealing gaps between policies and practices.
The Privacy Rule and Security
The Privacy Rule and Security Rule function as complementary frameworks protecting health information from different angles. The Privacy Rule establishes comprehensive protections for all PHI regardless of format, governing appropriate uses and disclosures while ensuring individual rights. The Security Rule establishes specific technical, physical, and administrative safeguards for electronic PHI exclusively. This distinction matters operationally—printed records removed from a facility require Privacy Rule protections through physical safeguards despite falling outside Security Rule technical control requirements.
In December 2024, OCR issued a Notice of Proposed Rulemaking to modify the HIPAA Security Rule to strengthen cybersecurity protections for electronic protected health information, establishing national standards for protection by covered entities and their business associates. These proposed changes recognize that privacy protections remain theoretical without robust security implementation. Organizations implementing encryption, multi-factor authentication, vulnerability management, and incident response capabilities create the security foundation enabling Privacy Rule protections to function as intended.
Administrative safeguards bridge privacy and security requirements. Workforce training must address both Privacy Rule use and disclosure limitations and Security Rule access controls and password requirements. Risk assessments must evaluate both privacy risks from inappropriate disclosures and security vulnerabilities enabling unauthorized electronic access. Business associate agreements must specify both Privacy Rule use limitations and Security Rule security implementation obligations. Organizations artificially separating privacy and security functions create compliance gaps—privacy policies requiring minimum necessary access mean nothing without security controls technically limiting system access based on workforce roles.
Enforcement and Penalties
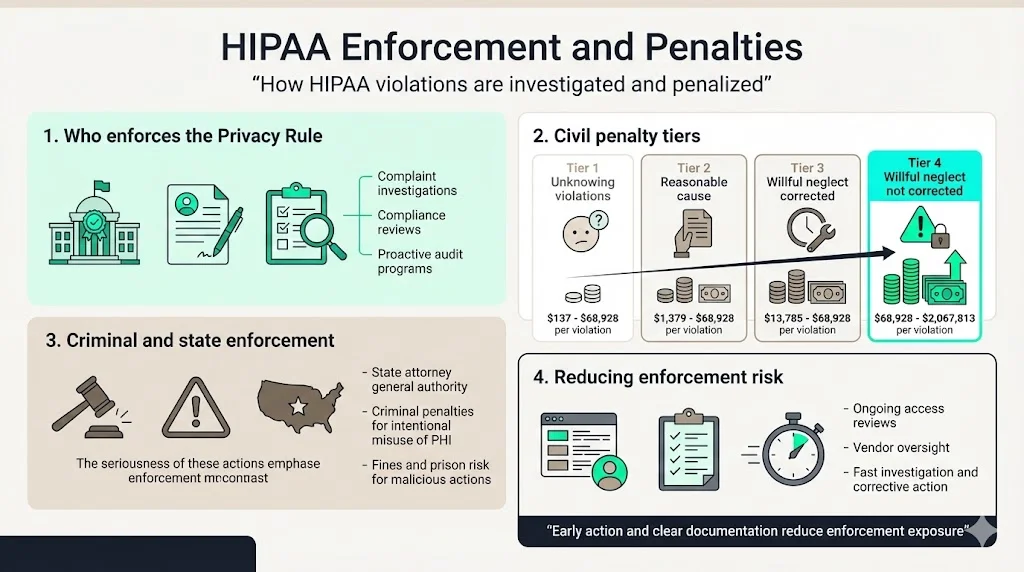
The HHS Office for Civil Rights enforces Privacy Rule compliance through complaint investigations, compliance reviews, and increasingly through proactive audits examining specific compliance areas across covered entity populations. OCR received over 35,000 HIPAA complaints in recent years, investigating potential violations and requiring corrective action when investigations substantiate non-compliance. Enforcement mechanisms range from voluntary compliance agreements requiring specific remedial actions to civil monetary penalties reaching $1.919 million per violation category annually.
The penalty structure establishes four tiers based on culpability: $100 to $50,000 per violation for unknowing violations, $1,000 to $50,000 per violation for reasonable cause, $10,000 to $50,000 per violation for willful neglect corrected within 30 days, and $50,000 per violation for willful neglect not corrected. Annual caps range from $25,000 to $1.919 million depending on the violation tier. State attorneys general possess concurrent enforcement authority, adding another layer of regulatory exposure. Criminal penalties apply when covered entities knowingly obtain or disclose PHI improperly, with potential fines reaching $250,000 and imprisonment up to 10 years for offenses committed with intent to sell, transfer, or use PHI for commercial advantage or malicious harm.
Organizations avoiding enforcement actions implement continuous monitoring rather than reactive compliance. Regular access log audits identifying inappropriate record access before complaints arrive, business associate assessments verifying subcontractor compliance before breaches occur, and patient request tracking ensuring timely responses before OCR complaints materialize all demonstrate proactive compliance. When incidents occur, immediate investigation, transparent reporting, comprehensive remediation, and documented corrective action substantially mitigate enforcement risk compared to delayed responses and defensive postures that escalate regulatory scrutiny.
Practical Tips for Healthcare Companies
Implementing effective Privacy Rule compliance requires operational integration rather than standalone privacy programs. Begin with comprehensive policy documentation addressing every Privacy Rule standard, then focus implementation efforts on high-risk areas: patient access procedures ensuring 30-day response timeframes, authorization forms capturing required elements for permitted uses, business associate agreements executed before any PHI sharing, workforce training conducted upon hire and annually thereafter, and complaint procedures prominently communicated through notices of privacy practices.
Designate privacy officials with genuine authority, adequate resources, and direct leadership access. Privacy compliance fails when relegated to compliance committees meeting quarterly to review policy updates without operational implementation responsibility. Effective privacy officials embed privacy considerations into system selection decisions, vendor contracting processes, facility design reviews, and workflow development initiatives—preventing privacy problems rather than discovering them through incident investigations.
Invest in monitoring capabilities providing visibility into PHI uses and disclosures. Audit logging capturing system access with regular review for inappropriate queries, disclosure tracking documenting non-routine PHI sharing, breach investigation protocols activating immediately upon suspected unauthorized access, and patient request tracking ensuring timely responses all create accountability mechanisms demonstrating compliance efforts. Organizations implementing these operational controls position themselves to identify and address issues before regulatory complaints trigger investigations.
Emerging Trends in Privacy and Security (2026 Perspective)
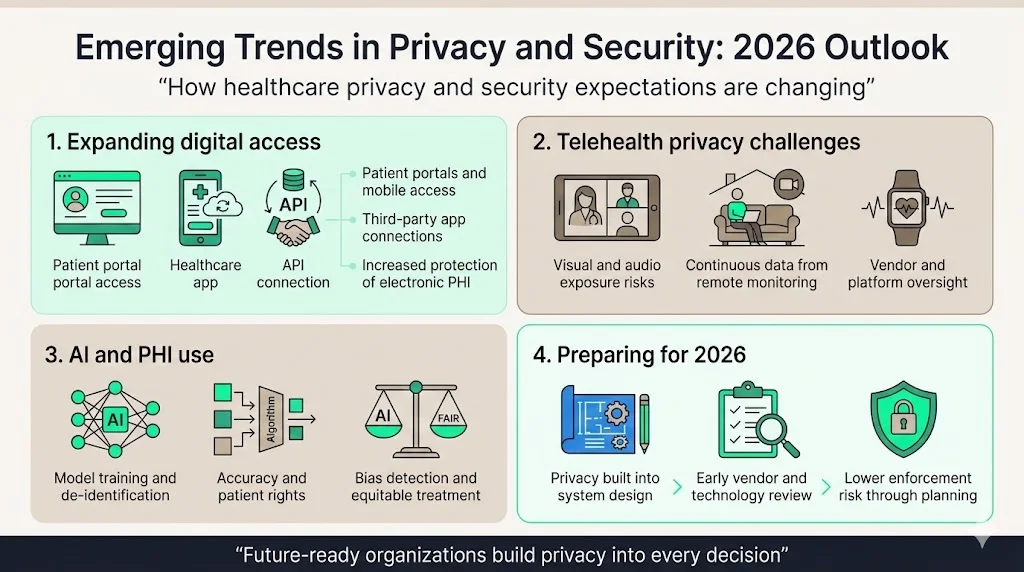
Healthcare digitization, telehealth proliferation, and artificial intelligence deployment fundamentally transform PHI protection challenges. Patients increasingly expect digital access to their health information through patient portals, mobile applications, and third-party apps connecting to provider systems through application programming interfaces. These technologies expand HIPAA's reach—proposed regulations would require health plans, health care clearinghouses, and most health care providers, and their business associates to better protect individuals' electronic protected health information against both external and internal threats.
Telehealth implementations require careful privacy analysis beyond Security Rule technical controls. Video consultations conducted in patient homes may inadvertently disclose PHI to family members or others visible on camera. Remote patient monitoring devices collect continuous health data requiring privacy protections throughout the data lifecycle. Third-party telehealth platforms functioning as business associates require comprehensive agreements and due diligence verification of their security implementations.
Artificial intelligence tools analyzing patient data for clinical decision support, population health management, and operational optimization create novel privacy considerations. Training AI models on PHI requires either de-identification meeting safe harbor requirements or determining that model training constitutes healthcare operations permitting PHI use without authorization. AI-generated clinical documentation must maintain accuracy standards supporting patients' amendment rights. Algorithmic bias detection and mitigation implicates Privacy Rule principles requiring equitable treatment regardless of demographic characteristics.
Organizations positioning themselves for 2026 compliance challenges implement privacy by design principles—embedding privacy considerations into technology selection, vendor evaluation, and system implementation from the outset rather than retrofitting privacy controls onto deployed systems. This proactive approach proves more cost-effective than reactive remediation while substantially reducing enforcement risk.
Conclusion
The Privacy Rule establishes the operational framework protecting patient privacy throughout the healthcare ecosystem. Organizations treating Privacy Rule compliance as documentation exercises rather than operational disciplines inevitably face enforcement actions, patient complaints, and reputational damage when gaps between policies and practices become apparent. Effective compliance requires sustained investment in workforce training, operational controls, monitoring capabilities, and business associate oversight—implemented continuously rather than episodically.
Healthcare organizations in 2026 face expanding privacy obligations extending beyond traditional compliance frameworks. Reproductive health privacy protections, substance use disorder record requirements, enhanced cybersecurity standards, and evolving patient expectations all demand operational maturity exceeding minimum regulatory compliance. Organizations building genuine privacy programs protecting patient information as an operational priority rather than manufacturing compliance artifacts position themselves for sustainable success regardless of regulatory evolution.
FAQ Section
1) What is the HIPAA Privacy Rule?
The HIPAA Privacy Rule establishes national standards protecting the privacy of protected health information. It governs how covered entities and business associates may use and disclose PHI, establishes individual rights to access and control health information, and requires administrative, technical, and physical safeguards preventing unauthorized uses and disclosures. The Privacy Rule applies to all PHI formats—electronic, written, and oral—distinguishing it from the Security Rule's exclusive focus on electronic PHI.
2) Who must follow the Privacy Rule?
Covered entities must follow the Privacy Rule: health care providers conducting electronic transactions, health plans, and health care clearinghouses. Business associates performing functions involving PHI access on behalf of covered entities also must comply through business associate agreements. Examples include medical billing companies, cloud storage providers, practice management software vendors, legal consultants handling patient records, and claims processing organizations. Employers maintaining employee health records, life insurers, and workers' compensation carriers typically fall outside HIPAA coverage.
3) What rights does the Privacy Rule give patients?
The Privacy Rule grants patients six core rights: accessing and obtaining copies of their PHI within 30 days, requesting amendments to inaccurate or incomplete information, requesting restrictions on uses and disclosures for treatment, payment, and healthcare operations, requesting confidential communications through alternative means, obtaining accountings of disclosures made for non-treatment/payment/operations purposes, and receiving notices of privacy practices explaining how their information may be used. Covered entities must implement documented procedures honoring these rights while maintaining evidence of compliance.
4) How does the Privacy Rule support compliance?
The Privacy Rule supports compliance by establishing specific administrative requirements: documented policies addressing every standard, designated privacy officials with implementation authority, workforce training programs ensuring staff understand obligations, complaint procedures allowing individuals to report concerns, sanction policies for workforce violations, and mitigation procedures addressing harmful effects of improper disclosures. These requirements create operational frameworks and audit trails demonstrating compliance efforts during regulatory investigations.
5) What is a key concept of the privacy rule?
The minimum necessary standard represents a key Privacy Rule concept requiring covered entities to limit PHI uses, disclosures, and requests to the minimum necessary to accomplish the intended purpose. Organizations must establish policies identifying routine uses and disclosures, implement role-based access controls limiting workforce access based on job functions, and scrutinize requests for PHI to ensure they seek only reasonably necessary information. This standard applies to all uses except treatment purposes, disclosures to individuals, authorized uses, and HHS compliance investigations.
6) What is not covered by the privacy rule?
The Privacy Rule does not protect de-identified health information meeting safe harbor requirements or statistical certification standards. Employment records maintained by employers in workforce member capacity fall outside coverage, as do education records covered by FERPA and workers' compensation records maintained by employers. Information held by life insurers, many schools and universities in their educational capacity, and law enforcement agencies in their investigative functions typically operates outside HIPAA jurisdiction despite containing health-related information.
7) What is a violation of the privacy rule?
Privacy Rule violations include unauthorized uses or disclosures of PHI, failure to implement required safeguards, denial of individuals' rights to access their records, failure to provide notices of privacy practices, inadequate business associate agreements, impermissible uses for marketing without authorization, disclosure of more than the minimum necessary PHI, and retaliation against individuals exercising their privacy rights. Violations range from unknowing technical non-compliance to willful neglect, with corresponding penalties from corrective action requirements to civil monetary penalties reaching $1.919 million annually per violation category.



.svg)
.svg)
.svg)