Most organizations treat threat assessment as an annual documentation exercise rather than a systematic discipline informing daily security operations. This approach creates a fundamental gap between perceived security posture and actual vulnerability to attack—a gap that becomes apparent when incidents occur, enterprise clients conduct vendor due diligence, or regulatory scrutiny intensifies.
Enterprises increasingly rely on threat intelligence and assessment data to inform business-critical decisions, including strategic investments, purchasing, risk evaluation, and resource allocation. For vendors serving enterprise clients, demonstrating rigorous threat assessment capabilities has become a prerequisite for contract execution. Enterprise buyers evaluate supplier security postures against frameworks like SOC 2, ISO 27001, and industry-specific regulations—all of which require documented, ongoing threat identification and evaluation processes.
As organizations move toward 2026, the rise of generative AI and increasing regulatory accountability mean security can no longer be treated as a background function—it has become a core business priority. The distinction matters because enterprise procurement teams now demand evidence of continuous threat monitoring, not point-in-time assessments conducted weeks before audit season.
What Is Threat Assessment?
Threat assessment is the systematic process of identifying, analyzing, and prioritizing potential threats to organizational assets, operations, and personnel. Unlike broader risk management programs that encompass strategic business risks, threat assessment focuses specifically on identifying threat actors, attack vectors, and vulnerabilities that could compromise confidentiality, integrity, or availability of systems and data.
The distinction between threat assessment and general risk analysis lies in specificity and technical depth. Risk analysis addresses enterprise-wide concerns including market volatility, regulatory changes, and operational disruptions. Threat assessment concentrates on security-specific hazards: nation-state actors targeting intellectual property, ransomware groups exploiting unpatched systems, insider threats accessing sensitive data, or supply chain compromises enabling downstream attacks.
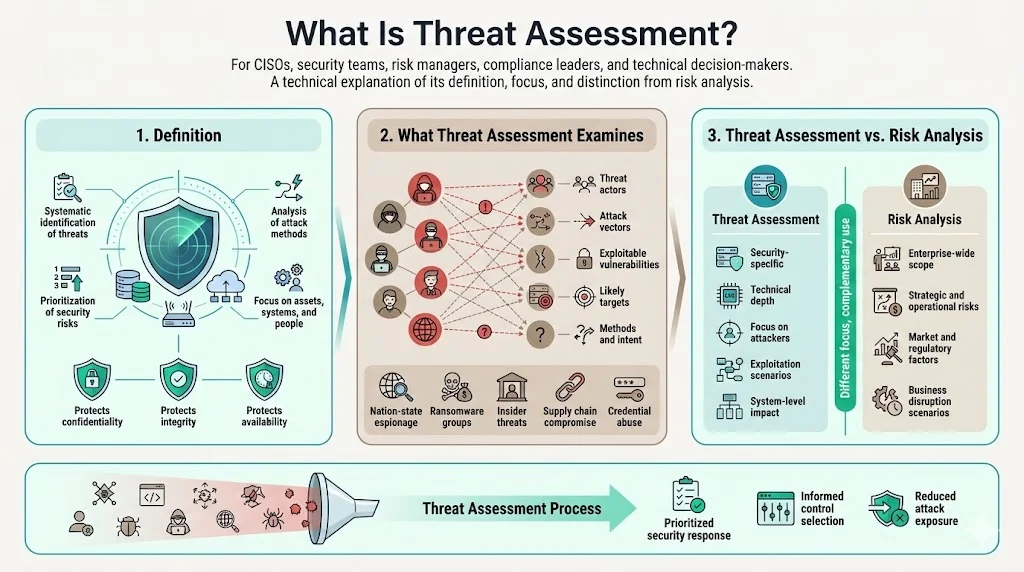
How It Fits Into Enterprise Security
Threat assessment serves as the foundation for evidence-based security decision-making within a comprehensive security program. Frameworks like NIST, ISO 27001, CMMC, and industry-specific regulations require organizations to demonstrate systematic threat identification and evaluation processes, with structured threat assessment programs providing audit-ready documentation.
Within the security lifecycle, threat assessment feeds vulnerability management, incident response planning, and control implementation decisions. Organizations conducting threat assessments identify which assets require protection, which threat actors pose the greatest risk, and which attack vectors warrant immediate remediation. This intelligence directs vulnerability scanning priorities, guides security architecture decisions, and informs resource allocation for detection and response capabilities.
Why Every Enterprise Client Expects Strong Threat Assessment
Enterprise clients purchasing software, infrastructure services, or processing sensitive data require vendors to demonstrate mature threat assessment capabilities for three reasons: contractual risk transfer, regulatory compliance obligations, and cyber insurance requirements.
Contractual obligations increasingly include security attestations, right-to-audit clauses, and breach notification requirements. Enterprise buyers refuse to accept vendor assurances without evidence. They require documentation showing how vendors identify threats, evaluate vulnerabilities, implement controls, and measure effectiveness over time. Organizations lacking documented threat assessment processes fail vendor security questionnaires before technical evaluation begins.
By identifying potential threat scenarios and their business impact, organizations develop more effective business continuity and disaster recovery plans—while threat assessment enables focusing on protections that address the most significant and likely risks, optimizing security spending and operational efficiency.
Regulatory frameworks including GDPR, HIPAA, PCI DSS, and sector-specific requirements mandate risk-based security approaches. Regulators expect organizations to identify threats relevant to their operating environment, implement controls proportionate to risk levels, and demonstrate continuous monitoring. Cyber insurance carriers now require evidence of threat assessment processes during underwriting and policy renewals, with organizations lacking documented programs facing coverage denials or premium increases exceeding 40%.
The Core Elements of a Business Threat Assessment
Structured threat assessments encompass six interconnected components that transform abstract security concerns into actionable protection strategies.
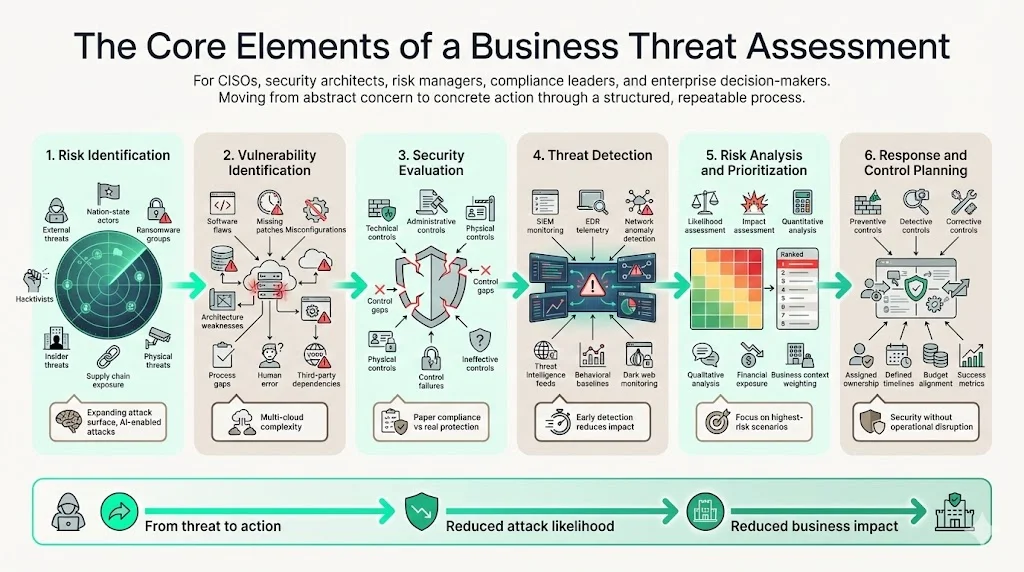
1) Risk Identification
Risk identification involves systematically cataloging potential threats across internal and external sources. Threats facing organizations have become more volatile, unpredictable, and sophisticated, with cybercriminals scaling operations using malware-as-a-service kits while state-sponsored actors quietly embed themselves within private and public networks.
External threats include nation-state espionage campaigns, organized cybercrime syndicates deploying ransomware, opportunistic hackers exploiting publicly disclosed vulnerabilities, and hacktivists targeting organizations based on ideological motivations. Internal threats encompass malicious insiders stealing intellectual property, negligent employees misconfiguring cloud resources, compromised credentials enabling unauthorized access, and third-party vendors introducing supply chain risk.
High-profile cyberattacks targeting a wide range of sectors have risen sharply, with AI-enhanced malware campaigns and growing exploitation of zero-day vulnerabilities threatening businesses through dangerous ransomware attacks and expanding attack surfaces. Physical threats including natural disasters, infrastructure failures, and unauthorized facility access must also be incorporated into comprehensive assessments.
2) Vulnerability Identification
While distinct from vulnerability assessment, threat assessment must incorporate vulnerability data to understand how identified threats might exploit specific weaknesses in organizational defenses, including software flaws, configuration errors, missing patches, and architectural weaknesses.
Discovery techniques combine automated vulnerability scanning, penetration testing, code review, architecture analysis, and security questionnaires. Organizations map technical vulnerabilities across operating systems, applications, network devices, and cloud services. Process vulnerabilities include inadequate change management, insufficient access controls, gaps in security awareness training, and incomplete incident response procedures. Human vulnerabilities—social engineering susceptibility, credential reuse, and security policy violations—frequently provide initial access for sophisticated attacks.
Vulnerability identification extends beyond IT infrastructure to encompass supply chain dependencies, business partner access patterns, and third-party software components embedded in applications. Organizations operating multi-cloud environments face particular complexity tracking vulnerabilities across AWS, Azure, Google Cloud, and SaaS applications where misconfigurations create exposure.
3) Security Evaluation
Security evaluation assesses the effectiveness of existing controls against identified threats and vulnerabilities. This process examines technical controls including firewalls, intrusion detection systems, endpoint protection, and encryption implementations. Administrative controls encompass security policies, access management procedures, incident response plans, and vendor management processes. Physical controls include facility access systems, surveillance capabilities, and environmental protections.
Evaluation identifies control gaps where threats lack corresponding protections, control failures where implemented protections fail to function as designed, and control inefficiencies where protections impose operational friction without commensurate security benefit. Organizations frequently discover security controls satisfying compliance requirements on paper while providing minimal protection against realistic attack scenarios—a phenomenon we describe as compliance manufacturing rather than genuine security infrastructure.
4) Threat Detection
Threat detection capabilities determine how quickly organizations identify compromise attempts or successful breaches. With data breaches growing, most enterprises allocate substantial cybersecurity budgets to threat intelligence—with plans to increase spending in 2026.
Detection mechanisms include security information and event management (SIEM) platforms aggregating log data, endpoint detection and response (EDR) systems monitoring host behavior, network traffic analysis identifying anomalous communications, and threat intelligence feeds providing indicators of compromise. Organizations implement anomaly detection using baseline behavioral models to identify deviations suggesting compromise.
Dark web intelligence shifted from "good to have" to "mission critical" in 2025, with early indicators like leaked credentials, exploit listings, and ransomware negotiations providing first signs of upcoming breaches—making proactive monitoring essential for enterprise security resilience and informed cyber risk management. Organizations ignoring these intelligence sources face delayed detection, escalating incident impact and recovery costs.
5) Risk Analysis and Prioritization
Risk analysis evaluates both likelihood and impact for each identified threat-vulnerability combination. Quantitative approaches calculate risk using numerical values representing threat frequency, exploit probability, and financial impact. Organizations estimate annual loss expectancy by multiplying single loss expectancy by expected occurrence rates, enabling direct cost-benefit analysis of security investments.
Qualitative approaches use categorical ratings—high, medium, low—to assess likelihood and impact when precise numerical data proves unavailable. Risk matrices plot threats across likelihood and impact dimensions, creating heat maps visualizing risk distribution across the threat landscape. Quantitative threat assessment uses numerical data, statistical analysis, and mathematical models to evaluate threat likelihood and impact, providing objective, measurable results supporting business decision-making, the ability to calculate risk in financial terms, and clearer metrics for tracking improvement over time.
Organizations prioritize remediation based on combined risk scores, addressing critical risks requiring immediate action before moderate risks suitable for scheduled remediation. Business context influences prioritization—threats to revenue-generating systems receive higher priority than equal-severity threats to non-critical infrastructure.
6) Response and Control Planning
Response planning translates risk analysis into specific security controls reducing threat likelihood or impact. Preventive controls block attacks before successful compromise, including access controls, security awareness training, vulnerability patching, and network segmentation. Detective controls identify attacks in progress through monitoring, alerting, and security operations center (SOC) analysis. Corrective controls minimize damage after compromise through incident response procedures, backup restoration, and business continuity activation.
Organizations document control implementation timelines, assign ownership, allocate budgets, and establish success metrics. Control selection balances risk reduction against implementation cost, operational impact, and user experience considerations. Security controls must protect systems without rendering them unusable—a balance requiring deep understanding of both threat landscape and business operations.
A Step-by-Step Process for Conducting a Threat Assessment
Systematic threat assessment follows a structured workflow ensuring comprehensive coverage and actionable outcomes.
1. Set scope and objectives. Define which systems, data, processes, and locations fall within assessment boundaries. Establish specific goals—preparing for SOC 2 audit, supporting cyber insurance application, evaluating merger and acquisition target, or establishing baseline security posture. Document assessment timeframe, resource allocation, and success criteria.
2. Asset mapping and value determination. Understanding what requires protection is essential for effective threat assessment, involving comprehensive asset inventory and classification based on business criticality, data sensitivity, and operational importance. Catalog servers, applications, databases, network devices, cloud services, and endpoints. Classify data by sensitivity level—public, internal, confidential, restricted. Map asset dependencies identifying single points of failure. Assign business value based on revenue impact, operational necessity, and regulatory requirements.
3. Identify threats and vulnerabilities. Research threat actors targeting your industry, geography, and technology stack. Review threat intelligence feeds, security advisories, and incident reports. Conduct vulnerability scans across infrastructure. Perform application security testing. Interview stakeholders about operational concerns. Document third-party risks through vendor assessments.
4. Analyze likelihood and impact. Evaluate each threat-vulnerability pair for exploitation probability based on threat actor capability, attack complexity, and existing control effectiveness. Assess potential impact across confidentiality, integrity, availability, financial loss, regulatory penalties, and reputational damage. Calculate risk scores using organizational risk methodology.
5. Develop and implement security controls. Prioritize risks requiring treatment based on score, regulatory obligations, and stakeholder concerns. Select appropriate controls from technical, administrative, and physical categories. Assign implementation responsibility with specific deadlines. Allocate budget and resources. Document control objectives, implementation specifications, and testing procedures.
6. Review and update regularly. Establish reassessment frequency based on industry, threat landscape velocity, and regulatory requirements. Monitor control effectiveness through security metrics. Track new vulnerabilities, emerging threats, and technology changes requiring assessment updates. Incorporate lessons learned from security incidents and near-misses.
Common Tools and Techniques Used in Threat Assessment
Organizations deploy specialized tools and methodologies to systematically evaluate threats across complex environments.
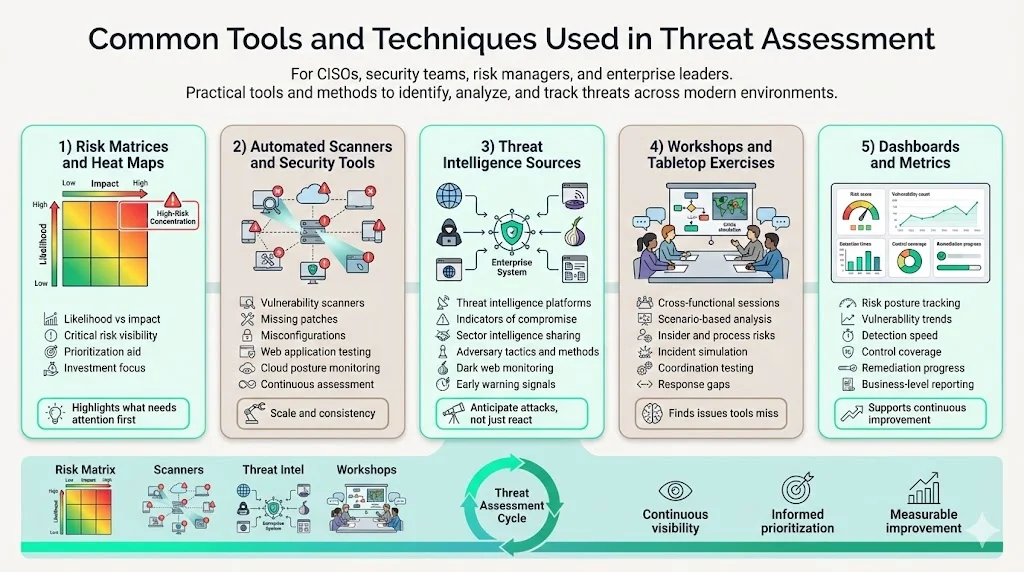
Risk matrices and heat maps provide visual representations of threat distribution across likelihood and impact dimensions. Matrices enable rapid identification of critical risks requiring immediate attention while deprioritizing low-probability, low-impact scenarios. Heat maps aggregate individual risks, revealing concentration patterns guiding strategic security investment.
Automated scanners and security evaluation tools identify technical vulnerabilities at scale. Vulnerability scanners detect missing patches, misconfigurations, and known weaknesses across networks and endpoints. Web application scanners test for injection flaws, authentication bypasses, and logic errors. Cloud security posture management (CSPM) tools continuously monitor infrastructure-as-code and cloud configurations for security deviations.
Intelligence sources for threat detection deliver actionable information about threat actor tactics, techniques, and procedures. Threat intelligence platforms aggregate indicators of compromise from multiple sources. Information sharing and analysis centers (ISACs) distribute sector-specific intelligence. Dark web monitoring services identify leaked credentials and reconnaissance activity signaling impending attacks.
Workshops and tabletop exercises engage stakeholders in collaborative threat identification and scenario planning. Facilitated sessions with technical teams, business leaders, and security personnel surface threats automated tools overlook. Tabletop exercises simulate incident response to specific threat scenarios, revealing procedural gaps and coordination challenges before real incidents occur.
Dashboards for performance review and trend tracking present security metrics enabling continuous improvement. Dashboards visualize vulnerability remediation rates, mean time to detection, control implementation status, and risk posture trends over time. Executive dashboards translate technical metrics into business context, demonstrating security program value and identifying investment needs.
How Threat Assessment Supports Other Business Functions
Threat assessment data provides strategic value extending beyond security operations into enterprise risk management, operational resilience, and regulatory compliance.
Risk Management
Threat assessment feeds enterprise risk management (ERM) frameworks by quantifying cybersecurity risks alongside operational, financial, and strategic risks. ERM programs incorporate threat assessment findings into board-level risk reporting, enabling executives to make informed decisions about risk acceptance, transfer, mitigation, or avoidance. Insurance placement, business continuity planning, and capital allocation decisions all depend on accurate threat and vulnerability data.
Organizations with mature threat assessment programs demonstrate security risk management sophistication during mergers and acquisitions, facilitating due diligence and integration planning. Investors increasingly demand security risk transparency, with threat assessment documentation influencing valuations and deal structures.
Incident Prevention and Response
Threat assessments identify likely attack scenarios before compromise occurs, enabling proactive control implementation and response preparation. Organizations develop incident response playbooks addressing specific threat scenarios revealed through assessment. Security operations centers prioritize monitoring and alerting based on threats most relevant to organizational assets and vulnerabilities.
Post-incident analysis validates or refutes threat assessment assumptions, creating continuous improvement feedback loops. Organizations discovering attacks through vectors overlooked in threat assessments update methodologies preventing similar oversights. Organizations are shifting their mindset from pure prevention to resilience, prioritizing rapid recovery, incident response planning, and business continuity to minimize operational disruption during attacks—with cyber resilience emerging as a board-level priority alongside financial and operational resilience.
Compliance and Reporting
Regulatory frameworks mandate risk-based security approaches requiring documented threat assessment processes. SOC 2 auditors expect evidence that organizations identify threats to Trust Services Criteria, implement corresponding controls, and monitor effectiveness over observation periods. ISO 27001 certification requires risk assessments identifying threats to confidentiality, integrity, and availability within the Information Security Management System (ISMS) scope.
GDPR Data Protection Impact Assessments (DPIAs) incorporate threat analysis for processing activities presenting high risk to individual rights. HIPAA Security Rule compliance demands risk analysis identifying threats to electronic protected health information (ePHI). PCI DSS requires annual risk assessments addressing threats to cardholder data environments. Organizations lacking documented threat assessment processes face audit findings, certification delays, and regulatory penalties.
Threat Assessment for Different Risk Types
Threat assessment methodologies adapt to address distinct risk categories presenting unique challenges and requiring specialized expertise.
Cybersecurity threat assessment focuses on adversaries targeting information systems—nation-state actors conducting espionage, organized crime deploying ransomware, opportunistic attackers exploiting vulnerabilities, and insider threats stealing data. Assessments evaluate threats across attack surfaces including web applications, cloud infrastructure, network perimeter, endpoints, and identities. In 2026, attacks are expected to become more coordinated and controlled, making detection increasingly difficult for standard security tools—with organizations facing volatile threat landscapes shaped by rapid technological change and geopolitical shifts, from professionalization of ransomware-as-a-service collectives to supply chain disruption.
Physical security assessment identifies threats to facilities, personnel, and tangible assets. Considerations include unauthorized access to buildings and data centers, theft of equipment containing sensitive data, workplace violence targeting employees, and surveillance or reconnaissance by adversaries. Physical security integrates with cybersecurity through considerations like badge reader networks, surveillance camera feeds, and building automation systems presenting cyber-physical attack vectors.
Operational and supply chain assessment addresses threats disrupting business processes and third-party dependencies. Organizations evaluate supplier financial stability, geopolitical factors affecting supply chains, single-source dependencies creating fragility, and compromised software or hardware introduced through vendors. Supply chain attacks demonstrated in incidents like SolarWinds and Kaseya require assessing not only direct suppliers but downstream dependencies cascading through software bill of materials (SBOM).
Natural and environmental hazards assessment considers threats beyond adversarial actors including earthquakes, floods, hurricanes, wildfires, and pandemics. Geographic analysis identifies location-specific threats to facilities and personnel. Business continuity planning incorporates threat assessment findings to ensure critical operations survive environmental disruptions.
Insider risks assessment addresses threats from employees, contractors, and business partners with legitimate access. Privileged users including system administrators and developers present elevated risk through intentional malicious activity or unintentional errors. Assessments identify high-risk roles, excessive access permissions, inadequate segregation of duties, and monitoring gaps enabling insider actions to evade detection.
Common Mistakes and How to Avoid Them
Organizations conducting threat assessments frequently encounter predictable pitfalls undermining effectiveness and wasting resources.
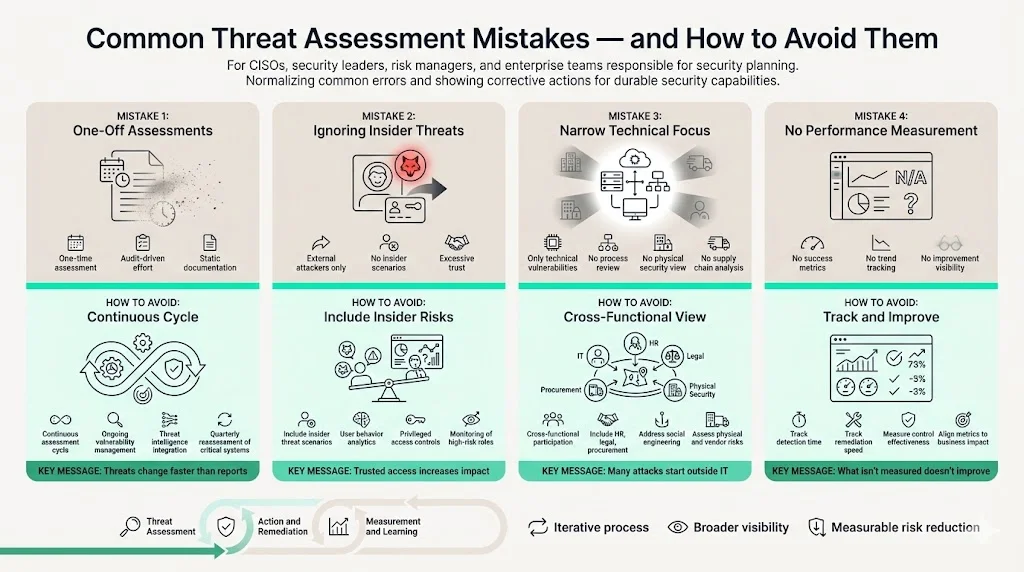
Treating threat assessment as a one-off project rather than an iterative process represents the most common failure mode. Organizations commissioning assessments before audits or compliance deadlines generate documentation satisfying immediate requirements without establishing ongoing capability. Threat landscapes evolve continuously—new vulnerabilities disclosed daily, threat actors shifting tactics, business systems changing functionality. Annual threat assessments prove obsolete within months. Establish continuous threat assessment incorporating vulnerability management, threat intelligence monitoring, and quarterly reassessment of critical systems.
Ignoring internal threats leaves organizations vulnerable to insider attacks accounting for substantial breaches. Assessments focusing exclusively on external adversaries overlook malicious employees, negligent contractors, and compromised privileged accounts. Internal threats prove particularly damaging because insiders possess system knowledge, legitimate access, and trusted status bypassing perimeter controls. Include insider threat scenarios in assessments, implement user behavior analytics, and establish privileged access management programs.
Overlooking non-technical risks creates blind spots in threat coverage. Security professionals concentrating on technical vulnerabilities miss social engineering, physical security gaps, business process weaknesses, and supply chain dependencies. Comprehensive threat assessment requires cross-functional participation including physical security teams, procurement, human resources, legal, and business unit leaders who understand operational risks invisible to IT security.
Failing to measure performance and refine plans prevents organizations from determining whether threat assessment processes deliver value. Without metrics tracking detection time, remediation velocity, control effectiveness, and incident frequency, organizations cannot demonstrate improvement or justify security investment. Establish key performance indicators aligned with business objectives, track metrics over time, and use data to refine threat assessment methodologies.
Measuring and Reviewing Performance
Effective threat assessment programs establish metrics demonstrating value and identifying improvement opportunities across detection, response, and control implementation dimensions.
Mean time to detect (MTTD) measures the duration between compromise and identification, indicating monitoring effectiveness and threat detection maturity. Organizations track MTTD for different threat categories, with improvements demonstrating enhanced visibility. Industry benchmarks show mature security programs achieving MTTD under 24 hours compared to weeks or months for organizations lacking systematic threat detection.
Mean time to respond (MTTR) quantifies the duration from detection to containment, reflecting incident response capability and preparedness. Organizations track MTTR across incident severity levels, with critical incidents requiring sub-hour response times. Tabletop exercises validate response procedures and identify gaps before real incidents test capabilities under pressure.
Vulnerability remediation rate indicates the velocity of addressing identified weaknesses, typically expressed as mean time to patch or percentage of vulnerabilities remediated within service-level objectives. Organizations categorize vulnerabilities by severity using Common Vulnerability Scoring System (CVSS) scores, applying aggressive remediation timelines to critical findings. Leading organizations remediate critical vulnerabilities within 15 days while addressing moderate findings within 30 days.
Control implementation completion tracks the percentage of planned security controls deployed and operational, demonstrating risk treatment execution. Organizations monitor implementation against project timelines and budgets, escalating delays to executive leadership. Quarterly control effectiveness reviews validate that implemented controls function as designed and deliver intended risk reduction.
Incident frequency trends reveal whether threat assessment and control implementation reduce successful attacks over time. Organizations track incident counts by category, severity, and attack vector. Decreasing incident rates in threat categories addressed by recent control implementations validate assessment accuracy and remediation effectiveness. Increasing incident rates signal emerging threats requiring assessment updates.
Periodic program reviews conducted quarterly or semi-annually evaluate threat assessment methodology effectiveness, identify process improvements, validate risk prioritization accuracy, and ensure alignment with evolving business objectives. Reviews incorporate lessons learned from security incidents, near-miss events, control failures, and external threat intelligence. Organizations adjust assessment scope, update risk models, refine prioritization criteria, and enhance detection capabilities based on review findings.
Conclusion
Threat assessment strengthens business resilience by transforming abstract security concerns into evidence-based protection strategies addressing realistic attack scenarios. Organizations conducting systematic threat assessments identify which assets require protection, which adversaries pose genuine risk, and which vulnerabilities warrant immediate remediation—enabling risk-based security investment delivering measurable protection.
For enterprise clients evaluating vendor security postures, documented threat assessment processes demonstrate organizational maturity distinguishing genuine security infrastructure from compliance theater. Organizations articulating specific threats to their environments, implemented controls addressing those threats, and metrics demonstrating control effectiveness signal security competence enterprise buyers demand.
Internal stakeholders including boards of directors, executive leadership, and operational teams benefit from threat assessment translating technical vulnerabilities into business impact language. Risk quantification enables informed decisions about security investment, risk acceptance, and strategic priorities. Business continuity planning incorporates realistic threat scenarios ensuring preparedness for likely disruptions rather than generic disaster recovery templates.
Embed systematic threat assessment into security planning as a continuous discipline rather than periodic project. Establish cross-functional assessment teams incorporating security, IT operations, business units, and risk management perspectives. Implement threat intelligence programs delivering actionable information about adversaries targeting your industry and technology stack. Deploy automated tools identifying vulnerabilities at scale while conducting manual assessments uncovering business logic flaws and process weaknesses. Document findings in risk registers tracking threats, vulnerabilities, controls, and residual risk. Establish metrics demonstrating program effectiveness and continuous improvement. Update assessments when business systems change, new vulnerabilities emerge, or threat actors shift tactics.
Organizations treating threat assessment as foundational security discipline build resilience against evolving adversaries while demonstrating security maturity enterprise clients, regulators, and insurers increasingly demand.
FAQs
Q1. What's the difference between threat assessment and risk analysis?
Threat assessment focuses specifically on identifying and evaluating security threats—adversaries, attack vectors, and vulnerabilities—that could compromise systems and data. Risk analysis encompasses broader enterprise risks including market conditions, operational disruptions, regulatory changes, and strategic challenges. Threat assessment feeds into risk analysis as one component of comprehensive risk management, providing detailed security intelligence informing overall risk posture. Organizations conduct threat assessments to understand security-specific hazards, then incorporate findings into enterprise risk analysis alongside financial, operational, and strategic risks.
Q2. How often should a business conduct a threat assessment?
Conduct comprehensive threat assessments annually at minimum, with quarterly reviews of critical systems and continuous monitoring of threat intelligence and vulnerability data. Organizations in rapidly evolving sectors including financial services, healthcare, and technology require more frequent assessment—quarterly or even monthly for highest-risk assets. Trigger reassessment when significant changes occur including major system deployments, mergers and acquisitions, new regulatory requirements, or after security incidents revealing assessment gaps. Continuous vulnerability management and threat intelligence monitoring enable near-real-time assessment updates between formal review cycles.
Q3. Can threat assessment help prevent cybersecurity breaches?
Threat assessment prevents breaches by identifying vulnerabilities before adversaries exploit them and implementing controls blocking attack vectors threat actors actually use against organizations in your industry. Assessment translates abstract security concerns into specific remediation priorities based on likelihood and impact. Organizations discovering unpatched systems vulnerable to actively exploited vulnerabilities can remediate before compromise occurs. However, threat assessment represents one component of comprehensive security programs—prevention requires combining assessment with vulnerability management, security awareness training, detection capabilities, and incident response procedures. No single activity prevents all breaches, but systematic threat assessment substantially reduces attack surface and exploitation probability.
Q4. Who should be involved in a threat assessment team?
Effective threat assessment requires cross-functional teams incorporating diverse perspectives. Security architects and engineers provide technical expertise identifying vulnerabilities and evaluating controls. Security operations teams contribute threat intelligence and incident response insights. IT operations teams understand infrastructure dependencies and change management implications. Business unit leaders articulate operational requirements and impact tolerance. Risk management professionals quantify financial exposure and prioritize remediation. Legal and compliance teams identify regulatory obligations. Physical security teams assess facility and personnel threats. Procurement teams evaluate supply chain dependencies. Executive sponsorship ensures resource availability and remediation accountability. External penetration testers and security consultants provide independent validation and specialized expertise organizations lack internally.
Q5. What tools are commonly used in threat assessments?
Threat assessment leverages vulnerability scanners detecting technical weaknesses across networks and applications, threat intelligence platforms aggregating indicators of compromise and adversary tactics, security information and event management (SIEM) systems correlating security events across infrastructure, cloud security posture management (CSPM) tools monitoring configuration drift, penetration testing frameworks simulating attacks, risk management platforms documenting findings and tracking remediation, and business impact analysis tools quantifying potential losses. Organizations combine automated scanning identifying known vulnerabilities with manual assessment techniques uncovering business logic flaws, process gaps, and human factors automated tools miss. Tool selection depends on environment complexity, regulatory requirements, and assessment scope.
Q6. Does threat assessment replace risk management?
Threat assessment complements rather than replaces risk management by providing detailed security intelligence informing broader risk management programs. Enterprise risk management addresses strategic, financial, operational, and compliance risks extending beyond security concerns. Threat assessment focuses specifically on security threats, vulnerabilities, and controls—generating findings incorporated into enterprise risk registers alongside non-security risks. Organizations require both disciplines: risk management establishes governance, risk appetite, and treatment strategies while threat assessment provides granular security analysis supporting risk-based decision-making. Mature organizations integrate threat assessment into risk management frameworks, ensuring security risks receive appropriate attention within overall risk prioritization and treatment processes.



.svg)
.svg)
.svg)