Most organizations in the automotive supply chain face recurring vendor security assessments from every original equipment manufacturer (OEM) they serve. Each assessment consumes internal security resources, repeats identical questions, and delays contract execution. Many organizations are now being told by suppliers and service providers across the automotive industry that TISAX compliance is mandatory before handling design files, prototype data, or sensitive business information. This creates a fundamental bottleneck: suppliers invest hundreds of hours annually demonstrating security compliance repeatedly, while buyers struggle to verify supplier risk consistently.
TISAX addresses this inefficiency through a standardized assessment framework that automotive industry participants recognize collectively. Rather than undergoing separate security audits for each customer relationship, suppliers complete a single assessment shared across the trusted network. For organizations seeking enterprise contracts in automotive manufacturing, TISAX increasingly functions as a prerequisite rather than a differentiator—the baseline expectation before commercial discussions advance.
What is TISAX?
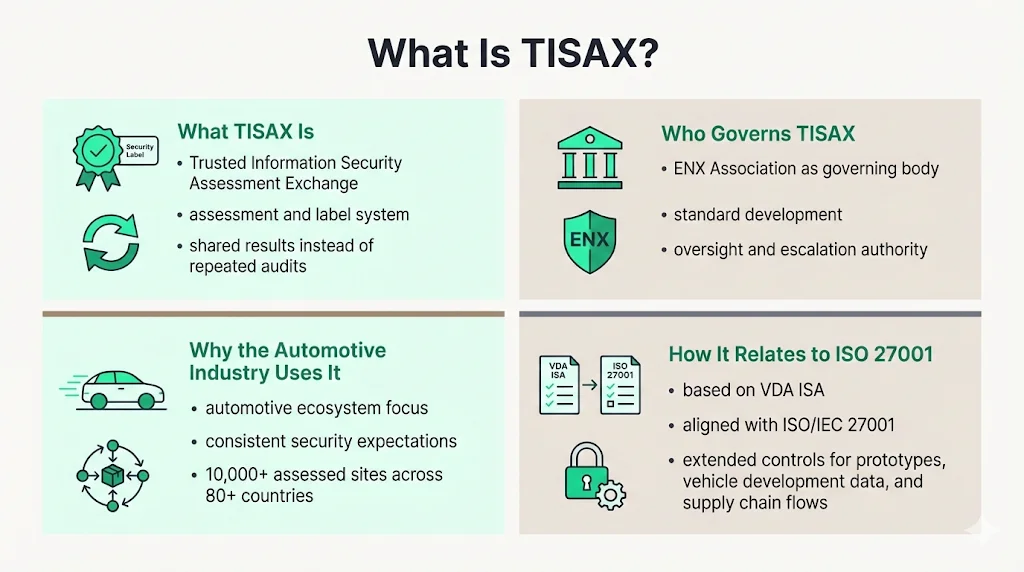
TISAX, short for Trusted Information Security Assessment Exchange, is an assessment and label exchange system created by the ENX Association in partnership with the German Association of the Automotive Industry (VDA). Unlike traditional certifications, TISAX operates as an assessment mechanism where organizations undergo independent audits, receive labels indicating their security maturity, and share those results through a centralized platform.
The ENX Association, founded in 2000, acts as the governing body and escalation authority, developing the TISAX cybersecurity standard and overseeing its correct implementation. The purpose is to help every participant in the automotive ecosystem demonstrate a consistent level of information security without undergoing multiple audits. With more than 10,000 assessed sites in more than 80 countries, TISAX has become the industry standard for information and cybersecurity assessments in the automotive industry.
The assessment is based on the ISA (Information Security Assessment) of the German Association of the Automotive Industry (VDA), which is closely aligned with the international standard ISO/IEC 27001. However, the VDA ISA catalogue extends ISO 27001 requirements with automotive-specific controls addressing prototype protection, confidential vehicle development data, and supply chain data flows.
Why TISAX Matters for Enterprise-Facing Companies
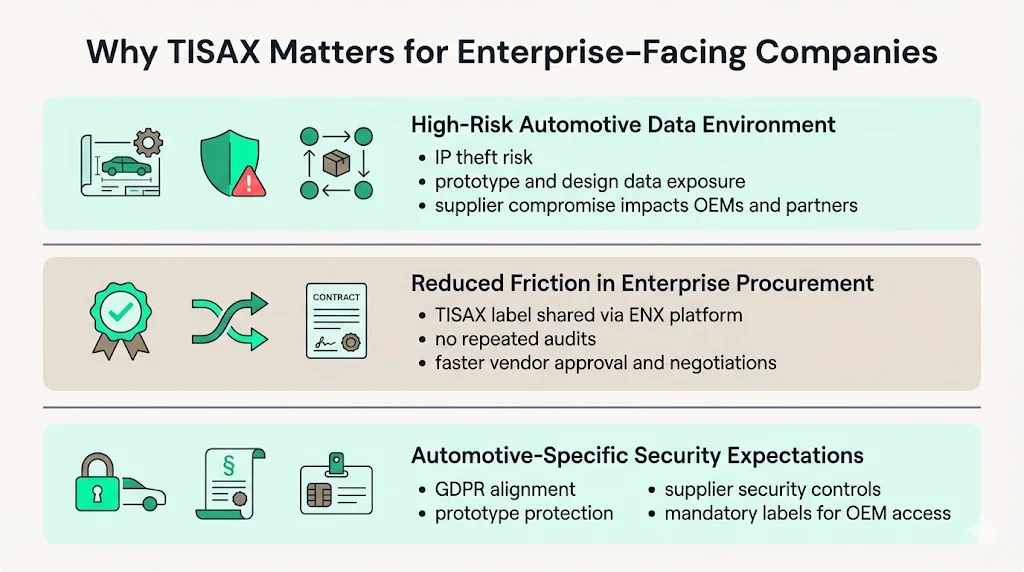
Automotive OEMs operate in an environment where intellectual property theft, prototype leaks, and supply chain data breaches pose existential risks. A single supplier compromise can expose next-generation vehicle designs, manufacturing processes, or competitive intelligence affecting billions in development investment. Buyers expect suppliers to implement information security controls commensurate with the sensitivity of data accessed.
Once an organization successfully passes its assessment, it receives a TISAX label uploaded to the ENX exchange platform, where approved partners can view and verify it. This exchange mechanism reduces friction during vendor assessments—buyers retrieve verified security attestations rather than conducting proprietary audits. For suppliers, TISAX provides proof of mature information security practices recognized across the automotive industry, accelerating contract negotiations and reducing redundant security questionnaires.
TISAX addresses data protection and confidentiality concerns systematically. The framework incorporates GDPR compliance requirements, physical security controls for prototype handling, and supplier security management—areas where generic information security frameworks provide insufficient guidance for automotive-specific risks. Organizations handling confidential vehicle development data face contractual requirements mandating TISAX labels before accessing OEM networks or facilities.
How TISAX Works
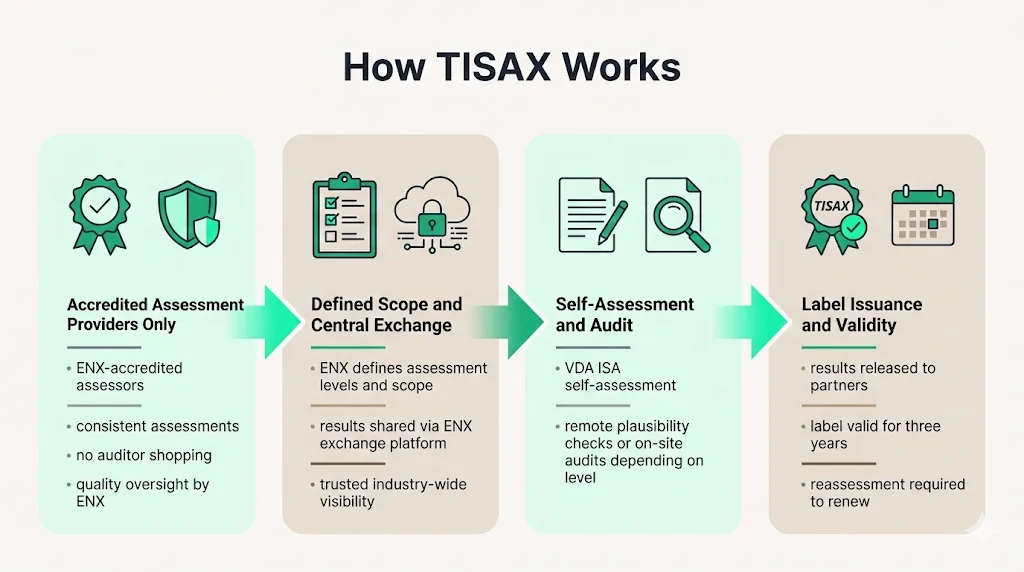
Assessments according to TISAX may only be carried out by ENX accredited TISAX assessment service providers, with the ENX Association authorizing respective assessment service providers and monitoring the quality of implementation and assessment results. This accreditation requirement ensures assessment consistency across providers and prevents assessment shopping—organizations cannot manipulate results by selecting lenient auditors.
The ENX Association is responsible for defining assessment levels and scopes within the TISAX program, and a specially developed online platform enables industry-wide exchange of assessment results for information security in the automotive sector. When companies release assessment results on this platform, they signal to direct business partners and all participating companies that their information security standards meet TISAX requirements.
The assessment process begins with organizational self-assessment against the VDA ISA catalogue. Audit providers carry out the assessment with the first step being self-assessment according to the ISA questionnaire, and depending on the assessment level, answers are verified by audit providers either remotely with plausibility checks or in person during on-site audits. Results remain valid for three years, after which reassessment is required to maintain label validity.
TISAX Certification Levels
TISAX uses a maturity-based assessment model rather than binary pass/fail certification. In contrast to ISO/IEC 27001, TISAX not only considers qualitative aspects but also uses a maturity model according to Automotive SPICE, which allows a quantitative assessment in the form of an overall maturity level. Organizations are assessed against defined maturity levels—organizations demonstrate not merely the presence of controls but their operational effectiveness and integration into business processes.
The framework defines three assessment levels—AL1, AL2, and AL3—reflecting increasing assessment rigor. AL1 involves self-assessment with plausibility checks conducted remotely. AL2 requires on-site audits with evidence verification and control testing. AL3 includes comprehensive on-site assessments with detailed control validation and process observation. Buyers specify which assessment level suppliers must achieve based on the sensitivity of data accessed and business relationship scope.
TISAX also defines protection needs—Normal, High, and Very High—corresponding to the confidentiality, integrity, and availability requirements of information handled. Normal protection applies to standard business information. High protection addresses confidential development data, technical specifications, or strategic business information. Very High protection covers extremely sensitive information such as pre-release prototype designs, merger and acquisition data, or information whose compromise would cause severe competitive harm.
Organizations choose their assessment scope according to requirements given by their customers from the automotive industry. A supplier might pursue High protection at AL2 for facilities handling prototype components, while maintaining Normal protection at AL1 for administrative offices. This scoping flexibility allows organizations to target assessments to actual business requirements rather than applying uniform controls enterprise-wide.
TISAX vs Other Frameworks
TISAX vs ISO 27001
TISAX controls are aligned with the ISO 27001 standard, with specific requirements for suppliers in the automotive industry. Organizations with existing ISO 27001 Information Security Management Systems (ISMS) possess foundational controls applicable to TISAX assessments. However, significant differences exist in scope, certification approach, and industry-specific requirements.
A key component of TISAX certification is compliance with the VDA-ISA catalogue of requirements, which contains specific requirements that go beyond ISO 27001 and are tailored to the particular needs of the automotive industry. These extensions address prototype protection, physical security for confidential materials, and data protection requirements specific to vehicle development processes—areas where ISO 27001 provides only generic control guidance.
ISO 27001 issues formal certifications valid for three years with annual surveillance audits. TISAX uses a label system shared through the ENX platform without formal certification. ISO 27001 applies broadly across industries and information types. TISAX focuses specifically on automotive supply chain information security, making it more prescriptive for automotive-specific risks while less comprehensive for general information security management.
Organizations frequently pursue both frameworks. ISO 27001 provides an enterprise-wide ISMS structure applicable across all business lines. TISAX addresses automotive-specific requirements and provides industry-recognized attestation for automotive customers. The frameworks complement rather than duplicate each other—ISO 27001 establishes foundational security management, while TISAX validates automotive-specific control implementation.
Who Needs TISAX Certification
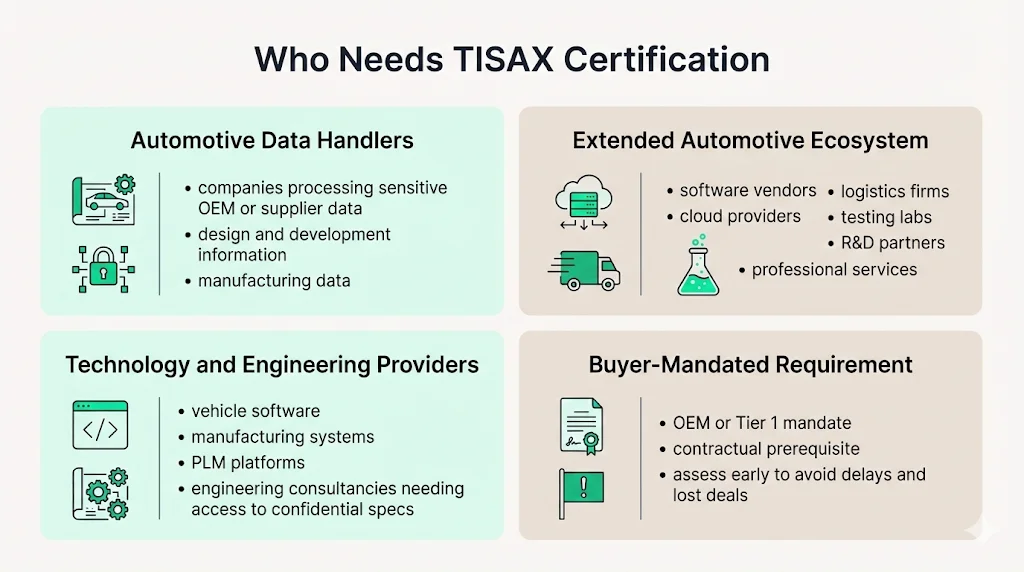
TISAX is relevant to all companies involved in processing sensitive information related to automotive manufacturers or suppliers, including engineering companies, software providers, testing laboratories, and research and development associates. This extends beyond traditional automotive suppliers to technology vendors, cloud service providers, logistics companies, and professional services firms supporting automotive operations.
Software providers developing applications for vehicle systems, manufacturing execution systems, or product lifecycle management platforms increasingly face TISAX requirements. Cloud infrastructure providers hosting automotive data encounter customer demands for TISAX labels before executing contracts. Engineering consultancies performing design services for OEMs require TISAX to access confidential specifications and development environments.
The determination of TISAX necessity ultimately rests with buyers. When an automotive OEM or Tier 1 supplier mandates TISAX as a contractual prerequisite, suppliers must comply or forfeit commercial opportunities. Organizations should evaluate TISAX requirements during initial customer discussions rather than after contract negotiations—retroactive TISAX implementation delays project initiation and strains customer relationships.
How to Get TISAX Certified
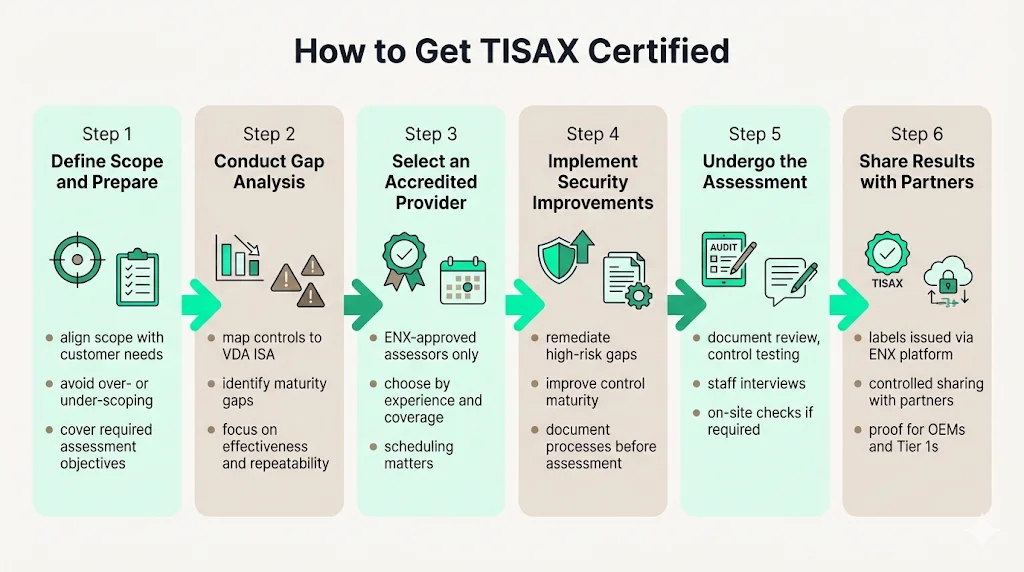
PreparationOrganizations begin by conducting gap analysis against the VDA ISA catalogue. This assessment identifies existing controls, control gaps, and maturity deficiencies requiring remediation. Gap analysis should address all applicable assessment objectives—information security management, data protection, supplier management, physical security, and prototype protection depending on scope.
The scope definition determines which facilities, processes, and information types the assessment covers. Organizations should align scope with customer requirements—overscoping increases audit complexity and cost without commercial benefit, while underscoping results in labels insufficient for customer needs.
Gap Analysis
Detailed gap analysis maps existing security controls to VDA ISA requirements and identifies maturity gaps. Organizations frequently discover that controls exist but lack documentation, metrics, or continuous improvement processes required for higher maturity levels. The maturity model evaluates not merely control presence but control effectiveness, repeatability, and optimization.
Selecting an Accredited Assessment Provider
The ENX Association maintains the ISA, audit provider criteria and assessment requirements (TISAX ACAR), and also approves audit providers and monitors the quality of implementation and assessment results. Organizations select from ENX-approved providers based on provider availability, industry experience, and geographic coverage. Provider selection impacts assessment scheduling, auditor expertise, and assessment quality.
Executing Security Improvements
Gap remediation requires implementing missing controls, enhancing existing control maturity, and documenting security processes systematically. Organizations should prioritize high-risk gaps affecting assessment objectives directly. Control implementation must precede assessment—attempting assessment before control maturity reaches target levels results in unsatisfactory labels requiring reassessment.
Undergoing the Audit
The assessment process includes documentation review, control testing, interviews with personnel, and facility inspections for on-site assessment levels. Auditors evaluate control implementation against VDA ISA requirements and assign maturity ratings. Organizations should prepare evidence supporting control effectiveness—policies, procedures, logs, metrics, incident records, and training documentation.
Sharing Results with Partners
Following successful assessment, organizations receive labels uploaded to the ENX portal. When companies release their assessment results on this platform, they signal to their direct business partners and all participating companies that their information security standards meet the requirements of TISAX. Organizations control which partners access their results, maintaining confidentiality while demonstrating compliance to authorized customers.
Common Requirements Covered by TISAX
TISAX's Information Security Assessment controls are grouped under Information Security, Data Protection and Prototype protection categories. Information security requirements address governance, risk management, security organization, asset management, access control, cryptography, physical security, operations security, communications security, incident management, business continuity, and compliance.
Data protection requirements extend beyond GDPR baseline compliance to address automotive-specific data handling. This includes data minimization for vehicle development data, purpose limitation for confidential business information, and data subject rights management affecting connected vehicle data.
Supplier security requirements mandate that organizations extend security expectations to subcontractors and service providers. Automotive supply chains involve multiple tiers—OEMs rely on Tier 1 suppliers, who rely on Tier 2 and Tier 3 suppliers. TISAX requires organizations to assess supplier security, impose contractual security requirements, and monitor supplier compliance continuously.
Access control requirements address logical and physical access to confidential information. Organizations must implement role-based access controls, need-to-know principles, and access logging for sensitive data. Physical security controls protect prototype materials, confidential documents, and restricted areas from unauthorized access.
Incident handling requirements mandate documented incident response procedures, security event monitoring, and breach notification processes. Organizations must demonstrate capability to detect, respond to, and recover from security incidents affecting automotive data. Incident response testing and continuous improvement are assessed as maturity indicators.
How TISAX Strengthens Data Security in the Supply Chain
TISAX establishes standardized security expectations across automotive suppliers, reducing variability in security posture. Before TISAX, OEMs conducted proprietary supplier assessments with inconsistent criteria, assessment rigor, and acceptance thresholds. This fragmentation created compliance complexity for suppliers serving multiple OEMs and provided inadequate assurance to buyers regarding actual supplier security.
Standardization lowers risk of data leakage by ensuring all supply chain participants implement baseline security controls. When every supplier handling High protection data maintains physical security, access controls, and incident response capabilities verified through independent assessment, the attack surface across the supply chain contracts significantly.
Intellectual property protection improves through automotive-specific prototype security requirements absent from generic frameworks. TISAX addresses physical security for prototype components, visitor access controls in development areas, and confidential waste disposal—operational realities affecting automotive manufacturers directly but covered inadequately in ISO 27001.
Trust between OEMs and vendors increases when security attestations derive from independent assessment rather than supplier self-declaration. The ENX accreditation model and quality monitoring reduce assessment inconsistency and prevent lenient assessment practices that would undermine label credibility. Buyers rely on TISAX labels knowing assessments follow standardized methodology with governance oversight.
TISAX for Technology and Cloud Providers
Software and cloud vendors face increasing pressure toward TISAX as automotive customers extend security requirements beyond traditional manufacturing suppliers to technology partners. Cloud platforms hosting vehicle development data, software-as-a-service applications supporting automotive operations, and infrastructure-as-a-service providers enabling connected vehicle services encounter TISAX mandates during enterprise procurement.
Enterprise adoption of TISAX in procurement policies reflects automotive industry recognition that information security risks extend beyond manufacturing facilities to digital infrastructure and software supply chains. OEMs understand that cloud provider compromise, software vulnerability exploitation, or third-party data breaches threaten intellectual property equivalently to physical supplier breaches.
Microsoft has pursued TISAX assessment for Azure services supporting automotive customers. Public documentation indicates Microsoft's recognition of TISAX as a requirement for European automotive accounts. Cloud providers pursuing automotive market share increasingly view TISAX as a competitive necessity rather than optional differentiation.
Costs, Timelines, and Practical Considerations
TISAX costs vary based on assessment level, organizational scope, number of sites assessed, and existing security maturity. Organizations should budget for gap assessment, control implementation, internal resource allocation, and assessment provider fees. Assessment provider fees depend on assessment level—AL1 costs substantially less than AL3—and organizational complexity. Multi-site assessments increase cost proportionally.
Timeline from initiation to label receipt typically ranges from four to nine months for organizations without existing ISO 27001 certification. Organizations with mature ISMS and ISO 27001 certification can compress timelines to three to five months by leveraging existing controls and documentation. Gap remediation constitutes the longest phase—organizations with significant control gaps require extended implementation periods before achieving assessment readiness.
Internal teams should anticipate substantial effort investment. Organizations without dedicated information security personnel face resource constraints affecting implementation speed. Security leadership, IT operations, physical security, human resources, legal, and business units all participate in control implementation and evidence preparation. Smaller organizations frequently require 200-400 hours of internal effort for initial TISAX implementation.
External support options include consulting firms specializing in TISAX preparation, managed security service providers offering control implementation, and fractional CISO services providing security leadership during assessment preparation. Organizations lacking internal security expertise should engage external support early—attempting self-implementation without automotive security experience frequently results in inefficient control implementation and assessment delays.
How TISAX Helps With Enterprise Sales
TISAX accelerates security questionnaire completion during enterprise sales cycles. Automotive buyers conducting vendor due diligence request detailed security information through questionnaires often exceeding 100 questions. TISAX labels provide pre-verified security attestation, allowing suppliers to reference assessment results rather than answering detailed questionnaires repeatedly.
Meeting buyer due diligence requirements becomes straightforward when TISAX labels address security requirements directly. Procurement teams increasingly accept TISAX labels as satisfying information security due diligence, eliminating lengthy security reviews that delay contract execution. Suppliers without TISAX face extended evaluation periods while security teams assess control implementation manually.
Competitive advantage materializes when bidding against competitors lacking TISAX. Buyers facing equivalent technical and commercial proposals favor suppliers demonstrating verified security maturity. In competitive procurements where differentiation is marginal, TISAX frequently functions as the deciding factor separating winning and losing bids.
Security review objections decrease substantially with TISAX labels. Buyer security teams raise fewer implementation questions, request less evidence, and approve vendors faster when independent assessments verify control effectiveness. This reduces sales cycle friction and shortens time-to-revenue for new customer relationships.
Practical Tips for Getting Ready
Organizations should start with comprehensive risk assessment and control inventory before committing to assessment timelines. Understanding existing control maturity and gap severity enables realistic project planning and resource allocation. Rushing assessment before achieving adequate control maturity results in unsatisfactory labels requiring reassessment.
Organizations with ISO 27001 practices already in place should leverage existing ISMS documentation, control evidence, and security processes. TISAX builds upon ISO 27001 foundations—organizations reinvent minimal controls when ISO 27001 certification exists. Mapping ISO 27001 controls to VDA ISA requirements identifies gaps efficiently without duplicating foundational security work.
Documenting security processes early accelerates assessment preparation. Auditors require documented evidence demonstrating control implementation and effectiveness. Organizations operating controls without documentation face substantial effort retroactively documenting processes. Implementing documentation discipline during control deployment prevents last-minute evidence collection scrambles.
Preparing evidence to satisfy auditors requires understanding assessment methodology and evidence expectations. Organizations should review VDA ISA assessment objectives, understand maturity level definitions, and identify evidence types supporting control verification. Mock assessments or pre-assessment reviews with assessment providers identify evidence gaps before formal assessment, reducing assessment delays.
Related Industry Compliance Concepts
TISAX represents one component of broader supplier security standards increasingly prevalent across industries. Financial services implement Third-Party Risk Management (TPRM) programs requiring vendor security assessments. Healthcare organizations mandate HIPAA Business Associate Agreements and security attestations. Technology companies require SOC 2 reports from service providers. These frameworks address similar objectives—reducing supply chain risk through standardized security verification.
Confidential data handling requirements extend beyond TISAX to encompass non-disclosure agreements, data classification policies, and contractual data protection obligations. Organizations handling automotive confidential information must implement controls addressing data lifecycle management—collection, processing, storage, transmission, and disposal. TISAX provides framework structure, but contractual obligations frequently impose requirements exceeding TISAX baseline controls.
Automotive regulations increasingly affect information security requirements. The United Nations Economic Commission for Europe (UNECE) WP.29 regulations mandate vehicle cybersecurity and software update management systems. European Union regulations addressing connected vehicle data protection, autonomous vehicle safety, and supply chain cybersecurity create compliance obligations intersecting with TISAX. Organizations pursuing automotive business must navigate regulatory complexity alongside industry framework compliance.
Vendor security programs implemented by automotive OEMs establish procurement policies, acceptable risk thresholds, and vendor classification schemes determining assessment requirements. Suppliers should understand customer-specific vendor security programs alongside TISAX—customers frequently impose requirements exceeding TISAX baseline expectations. Treating TISAX as comprehensive coverage for all automotive security requirements creates compliance gaps affecting customer relationships.
TISAX has transitioned from an emerging framework to mandatory requirements in the automotive sector. Organizations pursuing automotive business relationships face clear expectations: demonstrate information security maturity through independent assessment or accept competitive disadvantage. The framework's standardization benefits suppliers by reducing redundant assessments while providing buyers verified security attestation supporting supply chain risk management.
TISAX helps vendors demonstrate strong information security through automotive-specific control implementation addressing prototype protection, confidential data handling, and supply chain security. Organizations treating TISAX as a compliance checkbox exercise rather than genuine security improvement miss the framework's fundamental purpose—protecting intellectual property, reducing breach risk, and enabling trusted collaboration across automotive value chains.
The framework supports trust and smoother enterprise procurement by establishing common security language, standardizing assessment methodology, and providing verified attestation recognized industry-wide. Organizations investing in TISAX implement security capabilities extending beyond compliance—controls protecting confidential data, incident response procedures limiting breach impact, and risk management processes supporting business resilience.
By 2026, TISAX will likely function as baseline expectation for automotive suppliers equivalent to how SOC 2 functions for SaaS providers—not differentiating achievement but disqualifying absence. Organizations should evaluate TISAX requirements proactively rather than reactively, implementing controls before customer mandates force rushed preparation compromising implementation quality.
FAQs
1) What is TISAX?
TISAX (Trusted Information Security Assessment Exchange) is an assessment and label exchange system for information security in the automotive industry created by the ENX Association in partnership with the German Association of the Automotive Industry (VDA). Organizations undergo independent security assessments, receive labels indicating security maturity, and share results through the ENX platform with automotive business partners.
2) What is the difference between TISAX and ISO 27001?
TISAX builds upon ISO 27001 controls but includes automotive-specific requirements for prototype protection, physical security, and data protection absent from ISO 27001. ISO 27001 issues formal certifications requiring annual surveillance audits, while TISAX uses labels valid for three years shared through the ENX platform. TISAX employs maturity-based assessment quantifying control effectiveness, whereas ISO 27001 uses binary compliance evaluation. Organizations frequently pursue both—ISO 27001 for enterprise-wide ISMS and TISAX for automotive-specific attestation.
3) Who needs TISAX certification?
Automotive suppliers, technology vendors, software providers, cloud infrastructure companies, engineering consultancies, testing laboratories, logistics providers, and professional services firms handling confidential automotive information require TISAX when customers mandate assessment. The need derives from contractual requirements rather than regulatory obligation—automotive OEMs and Tier 1 suppliers increasingly mandate TISAX labels before granting access to confidential data or executing contracts.
4) Is Microsoft TISAX certified?
Microsoft has pursued TISAX assessment for Azure services supporting automotive customers. Public documentation indicates Microsoft recognizes TISAX as a competitive requirement for European automotive accounts. Organizations should verify current TISAX status directly through the ENX platform or Microsoft documentation, as assessment results are not publicly disclosed outside the trusted exchange network.
5) What are the levels of TISAX certification?
TISAX defines three assessment levels (AL1, AL2, AL3) reflecting assessment rigor and three protection levels (Normal, High, Very High) corresponding to information sensitivity. AL1 involves self-assessment with remote plausibility checks. AL2 requires on-site audits with evidence verification. AL3 includes comprehensive on-site assessments with detailed control validation. Protection levels determine control requirements—Very High protection mandates stronger controls than Normal protection for the same assessment objectives.
6) How do I get TISAX certified?
Organizations register with the ENX Association, define assessment scope and protection levels based on customer requirements, conduct gap analysis against VDA ISA requirements, implement missing controls and enhance control maturity, select an ENX-accredited assessment provider, undergo assessment including documentation review and control testing, and receive labels uploaded to the ENX platform for sharing with business partners. The process typically requires four to nine months depending on existing security maturity and organizational complexity.
7) What is the process for TISAX certification?
The certification process follows defined methodology: scope definition aligned with customer requirements, self-assessment against VDA ISA catalogue, gap remediation implementing missing controls, assessment provider selection from ENX-approved providers, formal assessment including evidence review and facility inspection for on-site levels, label issuance uploaded to ENX platform, and results sharing with authorized business partners. Organizations must reassess every three years to maintain label validity.
8) How does TISAX impact data security in the supply chain?
TISAX standardizes security expectations across automotive suppliers, reducing variability in security posture and supply chain attack surface. The framework lowers data leakage risk by ensuring all participants implement baseline security controls verified through independent assessment. Automotive-specific prototype protection requirements address intellectual property risks inadequately covered in generic frameworks. The trusted exchange mechanism increases buyer confidence in supplier security, enabling collaboration while reducing redundant assessments that consume resources without improving actual security.



.svg)
.svg)
.svg)