Most cloud service providers pursue compliance frameworks reactively—waiting until a procurement requirement surfaces before initiating authorization. This approach creates significant risk when contracting with Texas state agencies, where TX-RAMP certification isn't merely preferential but legally mandated. Organizations attempting to compress 6-9 months of security documentation and control implementation into shortened procurement windows discover that authorization timelines don't accommodate business urgency.
TX-RAMP represents Texas's systematic approach to cloud vendor risk management, mirroring the federal government's FedRAMP model at the state level. For companies serving enterprise clients—particularly those targeting public sector contracts—understanding this framework's cybersecurity governance requirements and regulatory compliance implications determines contract eligibility and procurement viability.
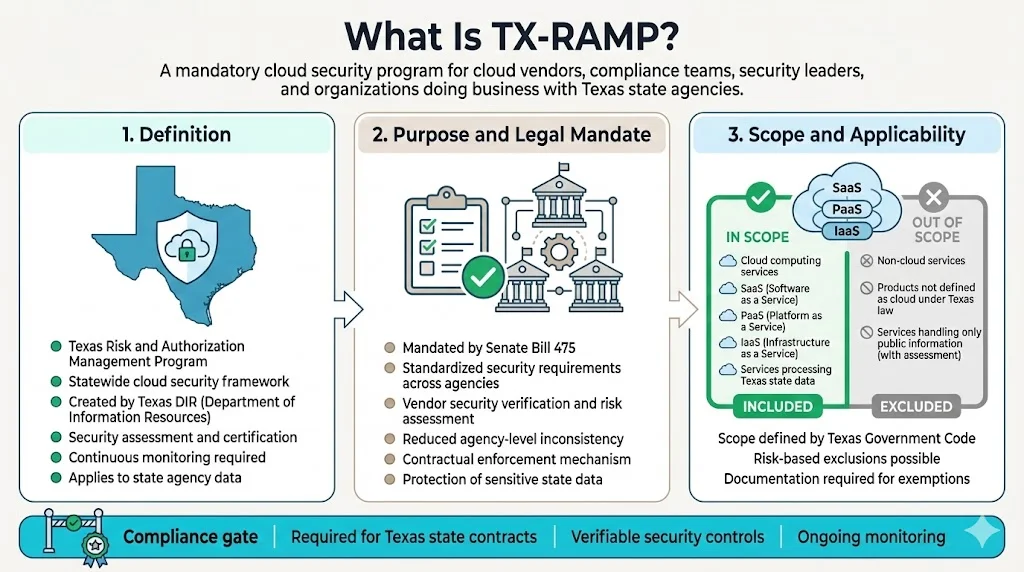
What is TX-RAMP?
The Texas Risk and Authorization Management Program (TX-RAMP) is a standardized approach for security assessment, certification, and continuous monitoring of cloud computing services that process the data of Texas state agencies. Created by the Texas Department of Information Resources (DIR), this program establishes mandatory cybersecurity requirements for cloud vendors contracting with Texas government entities.
Purpose
As mandated by Senate Bill 475, TX-RAMP establishes a standardized framework for evaluating, authorizing, and continuously monitoring the security of cloud services that process state data. The program addresses a fundamental problem: inconsistent security postures among cloud vendors created compliance gaps and exposure risks across state operations. By establishing uniform baseline requirements, TX-RAMP ensures cloud providers demonstrate verifiable security controls before accessing state data systems.
The framework protects information resources and enforces data protection standards across all Texas state agencies and public institutions. This isn't aspirational guidance—it's a legal mandate with contract enforcement mechanisms.
Scope
Only cloud computing services, as defined by Texas Government Code, section 2054.0593(a), are within scope for TX-RAMP. Not every software product or IT service requires certification. Products or services that are not cloud computing services are not subject to TX-RAMP. Certain specific cloud computing services are outside of the scope of Texas Government Code, section 2054.0593 and, as such, are not required to comply with TX-RAMP.
Cloud services processing state data through SaaS, PaaS, or IaaS models fall within TX-RAMP jurisdiction. Services handling exclusively public information or operating as low-impact resources with negligible confidential data may be excluded—but these determinations require documented risk assessments, not vendor assertions.
How TX-RAMP Works
Key Components of the Authorization Process
TX-RAMP operates through three interconnected mechanisms: initial security assessment, formal DIR authorization, and sustained continuous monitoring. This structure mirrors FedRAMP's operational model but applies Texas-specific control requirements and state-level oversight processes.
Security assessments evaluate control implementation against established baselines. DIR reviews evidence artifacts, technical documentation, and operational procedures to verify actual security posture—not self-attestations. Authorization grants formal certification following successful assessment completion. Continuous monitoring requires ongoing evidence submission, incident reporting within 48 hours of discovery, and sustained compliance demonstration throughout the certification period.
TX-RAMP Level 1 and Level 2 Certifications are valid for 3 years from the date the certification is granted, provided the cloud service maintains compliance with the program requirements.
Certification Levels
TX-RAMP has two assessment and certification levels: Level 1 for public/non-confidential information or low impact systems. Level 1 Certification is achieved after submitting the assessment responses and meeting the minimum requirements for the Level 1 Assessment Criteria or by submitting evidence of StateRAMP Category 1 authorization or FedRAMP Low authorization.
Level 2 for confidential/regulated data in moderate or high impact systems. Level 2 Certification is achieved after submitting the assessment responses and meeting the minimum requirements for the Level 2 Assessment Criteria or by submitting evidence of StateRAMP Category 2 authorization or FedRAMP Moderate authorization.
If they need to adhere to TX-RAMP Level 1, the controls use the NIST 800-53 Low baseline. If they need to adhere to TX-RAMP Level 2, the controls use the NIST 800-53 Moderate baseline. Level 1 requires implementing 117 controls; Level 2 encompasses 223 controls following recent program revisions.
Provisional and Fast Track Paths
TX-RAMP Provisional Status provides a provisional product certification permitting a state agency to contract for the use of a product for up to 18 months without receiving full TX-RAMP certification. This provisional pathway addresses immediate procurement needs while vendors complete full authorization processes—but it's not a compliance substitute. Agencies accepting provisional certifications assume documented risk, and vendors failing to achieve full certification within 18 months face contract termination.
The TX-RAMP Fast Track Assessment is a streamlined process designed to expedite the certification of cloud service providers by allowing providers to leverage existing DIR-approved third-party assessments or audit reports to provide verified evidence of security practices. Provisionally Authorized status will be granted TX-RAMP Level 2 Certification. StateRAMP Authorized – Cloud computing services that have a StateRAMP Authorization will be granted TX-RAMP Level 2 Certification. FedRAMP Moderate and StateRAMP Category 2 authorizations automatically qualify for TX-RAMP Level 2 certification through reciprocity agreements.
TX-RAMP and Cybersecurity Compliance
Relationship to Regulatory and State Standards
TX-RAMP establishes binding security requirements for cloud vendors accessing Texas state data. Unlike voluntary frameworks that organizations adopt selectively, TX-RAMP compliance is mandatory for contract eligibility. Texas state agencies, as defined by Texas Government Code 2054.003(13), are required to only contract with cloud service providers who meet TX-RAMP's security requirements starting January 1, 2022.
The program intersects with federal regulations governing data protection, privacy requirements under state law, and industry-specific compliance obligations. Vendors handling healthcare data must satisfy both HIPAA technical safeguards and TX-RAMP control baselines. Those processing personal information navigate GDPR or CCPA requirements alongside Texas-specific data protection standards.
Security Frameworks at Play
TX-RAMP builds on NIST SP 800-53 security control frameworks, aligning with federal risk management standards while incorporating Texas-specific requirements. The control baselines aren't theoretical—they're implementation-focused requirements demanding documented evidence of operational security controls.
Level 1 mirrors FedRAMP Low impact baselines. Level 2 aligns with FedRAMP Moderate requirements. This architectural decision enables reciprocity: vendors holding FedRAMP or StateRAMP authorizations can fast-track TX-RAMP certification by demonstrating equivalent control implementation.
Impact on Risk Management and Vendor Assessment
TX-RAMP fundamentally changes vendor security assessment practices for Texas procurement. State agencies no longer conduct individualized security reviews for each cloud service—they rely on centralized DIR authorization as baseline assurance. This shifts risk evaluation from contract-by-contract assessments to sustained compliance monitoring.
Vendors must implement comprehensive risk mitigation planning addressing control gaps, remediation timelines, and continuous improvement mechanisms. Failure of a cloud service provider to maintain baseline compliance with TX-RAMP requirements described by the Program Manual will result in revocation of a product's TX-RAMP certification. Certification revocation triggers immediate contract compliance issues across all Texas state agency relationships.
Use Cases for TX-RAMP
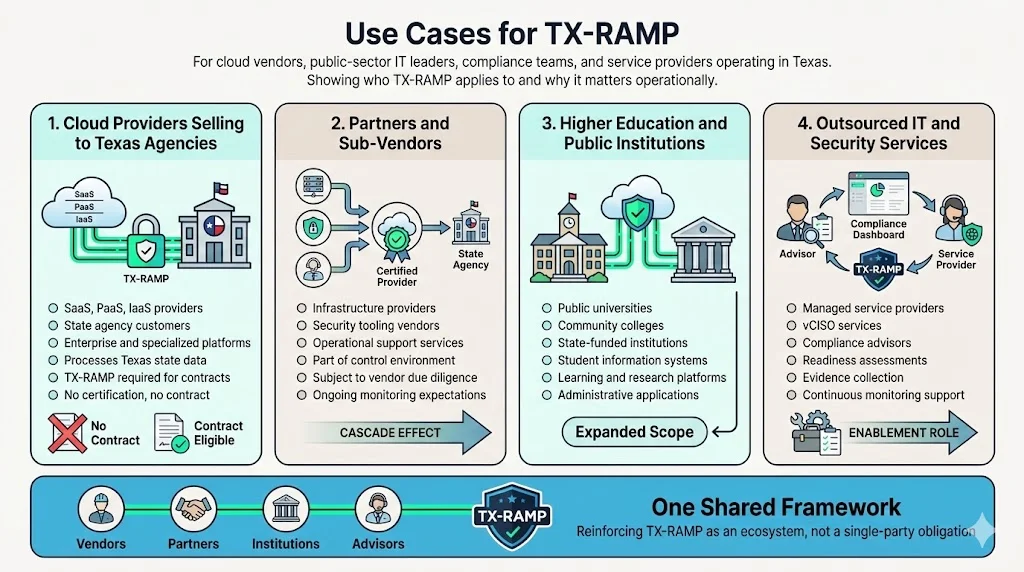
1) Cloud Providers Selling to Texas Agencies
Any organization offering SaaS, PaaS, or IaaS solutions to Texas state entities requires TX-RAMP certification. This includes enterprise software platforms, infrastructure services, collaboration tools, data analytics platforms, and specialized applications processing state data. Without certification, vendors cannot legally execute contracts with Texas government agencies—regardless of technical capability or market position.
2) Partners and Sub-Vendors
Organizations providing services to TX-RAMP certified cloud providers may enter the compliance ecosystem indirectly. If your infrastructure, security services, or operational support directly impacts a certified vendor's control environment, expect due diligence requirements reflecting TX-RAMP obligations. While sub-vendors don't necessarily require independent certification, they become part of the certified provider's supply chain risk assessment and continuous monitoring responsibilities.
3) Higher Education and Public Institutions
State agencies, institutions of higher education, and public community colleges as defined by Texas Government Code 2054.003(13) must only enter or renew contracts to receive cloud computing services that comply with TX-RAMP requirements. This extends certification requirements beyond executive branch agencies to public universities, community colleges, and state-funded educational institutions. Student information systems, learning management platforms, research computing services, and administrative applications all fall within scope when processing institutional data.
4) Outsourced IT and Security Services
Managed service providers, vCISO firms, and compliance consultancies help clients navigate TX-RAMP authorization processes. These engagements span initial readiness assessments, control gap analysis, evidence collection, continuous monitoring support, and sustained compliance management. Organizations lacking internal compliance expertise often engage specialized advisors to compress authorization timelines and ensure thorough evidence documentation.
Why Compliance Matters to Enterprise Clients
1) Contract Eligibility
State agencies must comply with the statutory requirements of contracting for cloud services with appropriate TX-RAMP certification. This isn't procurement preference—it's a legal requirement. Vendors lacking certification cannot bid on contracts, cannot execute agreements, and cannot provide services to Texas state entities. Organizations pursuing Texas public sector revenue must treat TX-RAMP as a prerequisite qualification, not optional enhancement.
2) Procurement Efficiency
Pre-authorized vendors accelerate procurement cycles by eliminating agency-specific security reviews. Texas state agencies can execute contracts with certified providers through streamlined processes, reducing procurement timelines from months to weeks. This procurement efficiency creates competitive advantage: certified vendors win contracts while competitors navigate protracted authorization processes.
3) Data Protection and Customer Trust
TX-RAMP certification demonstrates implemented security controls, not aspirational commitments. The framework requires documented evidence of access controls, encryption standards, incident response capabilities, vulnerability management processes, and continuous monitoring mechanisms. Organizations achieving certification signal genuine security posture to enterprise buyers evaluating vendor risk.
This matters beyond Texas contracts. Enterprise security teams increasingly reference state-level authorizations when assessing cloud vendor risk across all procurement decisions. TX-RAMP certification becomes a proxy for security maturity in broader vendor assessment processes.
4) Continuous Oversight
TX-RAMP requires ongoing compliance demonstration through regular reporting, incident notification, and sustained control effectiveness evidence. Events that can result in a TX-RAMP certification being revoked include, but are not limited to, the following: Failure to inform required parties of significant changes to the cloud computing service within 30 days, failure to inform required parties of the loss of other accepted risk and authorization management program (FedRAMP, StateRAMP) certifications, failure to provide the required continuous monitoring documents.
This continuous monitoring requirement prevents "audit theater"—organizations cannot implement controls temporarily for assessment then revert to inadequate security practices. DIR expects sustained operational security aligned with certified control baselines.
Practical Steps for Vendors
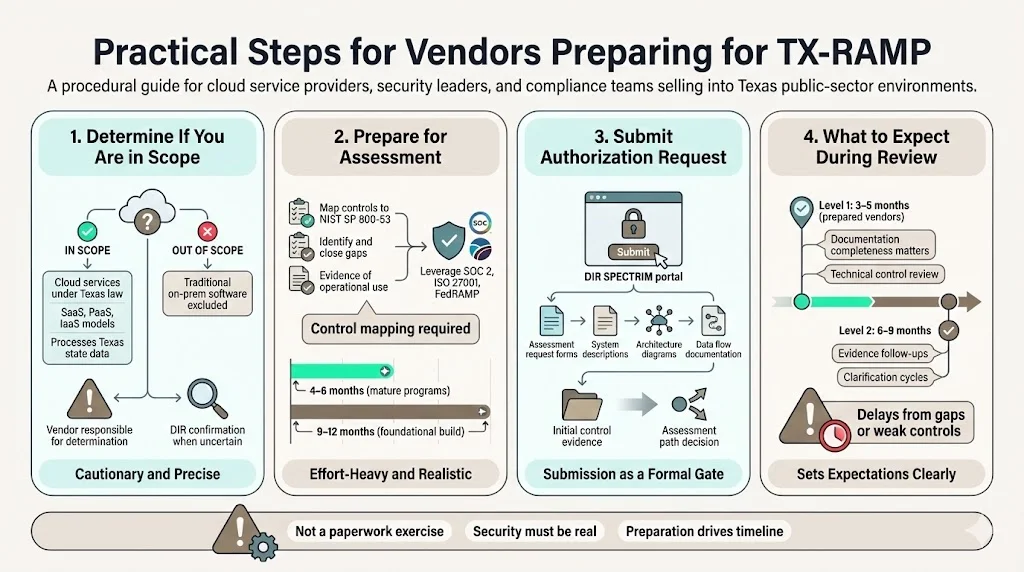
1) Determining If You Are in Scope
Cloud computing services as defined by Texas law require evaluation against TX-RAMP scope criteria. DIR provides assessment forms helping vendors determine applicability, but ultimate responsibility rests with providers. Services processing state data through remote infrastructure, platform capabilities, or software delivery models typically fall within scope. Traditional software licenses, on-premises installations, and non-cloud IT products generally remain outside TX-RAMP jurisdiction.
Organizations uncertain about scope should request formal DIR determination rather than self-assessing exclusion. Incorrect scope determinations create contract compliance risks when agencies discover vendors should have obtained certification.
2) Preparing for Assessment
Document existing security controls against NIST SP 800-53 baselines before initiating formal assessment. Identify control gaps, implement missing safeguards, and establish evidence collection processes demonstrating operational effectiveness. Organizations holding SOC 2 Type II, ISO 27001, or FedRAMP certifications can leverage existing control documentation—but must map those controls to TX-RAMP specific requirements.
Preparation timelines vary significantly based on current security maturity. Organizations with comprehensive security programs and documented controls can achieve readiness in 4-6 months. Those lacking foundational security infrastructure require 9-12 months implementing controls before assessment readiness.
3) Submitting Authorization Requests
Complete TX-RAMP Assessment Request forms through DIR's SPECTRIM portal. Submissions require detailed system descriptions, architecture diagrams, data flow documentation, and preliminary control implementation evidence. DIR reviews submissions to determine assessment pathway—standard review, fast track leveraging existing certifications, or provisional authorization while completing full assessment.
4) What to Expect
Authorization timelines depend on certification level, documentation completeness, and DIR review volume. Level 1 assessments typically conclude in 3-5 months for well-prepared vendors. Level 2 reviews extend 6-9 months given expanded control scope and evidence requirements. These timelines assume thorough preparation—organizations submitting incomplete documentation or demonstrating control gaps experience significant delays while remediating deficiencies.
DIR evaluates technical controls, policy documentation, operational procedures, and evidence artifacts demonstrating sustained implementation. Expect detailed technical questions, requests for additional evidence, and clarification discussions throughout assessment. Organizations treating this as documentation exercise rather than genuine security evaluation inevitably face extended timelines and potential certification denial.
Challenges and Common Missteps
Many organizations underestimate documentation requirements, assuming narrative descriptions suffice. TX-RAMP demands specific evidence artifacts: configuration screenshots, access control matrices, encryption validation reports, vulnerability scan results, incident response records, and operational logs demonstrating continuous control operation. Vendors lacking systematic evidence collection processes scramble to reconstruct historical compliance documentation during assessment.
Another critical failure: treating TX-RAMP as a one-time certification checkpoint rather than continuous compliance obligation. Organizations achieving initial authorization then neglecting ongoing monitoring, incident reporting, and control sustainment face certification revocation. This isn't theoretical risk—DIR actively monitors certified providers and revokes authorizations when vendors demonstrate non-compliance.
The most damaging misstep involves delayed control implementation. Vendors postponing security infrastructure investment until procurement opportunities surface cannot compress 6-9 months of control implementation into compressed timelines. Organizations pursuing Texas public sector contracts must implement foundational security controls proactively, not reactively when RFPs emerge.
Conclusion
TX-RAMP represents Texas's systematic approach to cloud vendor risk management, establishing mandatory security baselines for organizations serving state agencies and public institutions. The program aligns with federal authorization frameworks while incorporating Texas-specific requirements and state-level oversight mechanisms. For cloud providers targeting public sector contracts, TX-RAMP certification determines market access—not competitive positioning, but fundamental contract eligibility.
The framework reinforces a critical principle: compliance certifications emerge from implemented security controls, not documentation manufacturing. Organizations building genuine security infrastructure that protects systems and data discover that TX-RAMP certification becomes a natural outcome of operational security discipline. Those attempting to manufacture compliance artifacts without underlying security posture face extended authorization timelines, potential certification denial, and eventual revocation when continuous monitoring reveals control deficiencies.
Companies serving enterprise clients—particularly those targeting government contracts—must integrate TX-RAMP requirements into broader security and compliance strategies. The authorization process demands 6-9 months minimum preparation, systematic control implementation aligned with NIST SP 800-53 baselines, comprehensive evidence collection mechanisms, and sustained compliance management infrastructure. Organizations treating this as a procurement checkbox rather than security transformation inevitably discover that authorization timelines don't accommodate business urgency.
FAQs
1) What is TX-RAMP?
TX-RAMP is Texas's state-level cybersecurity authorization program providing standardized security assessment, certification, and continuous monitoring for cloud computing services used by Texas state agencies and public institutions.
2) Who needs TX-RAMP certification?
Cloud service providers offering SaaS, PaaS, or IaaS solutions to Texas state agencies, higher education institutions, or public entities handling Texas government data require appropriate TX-RAMP certification levels based on data sensitivity and system impact.
3) Is TX-RAMP required for cloud vendors?
Yes—Texas state agencies cannot legally contract with cloud vendors lacking appropriate TX-RAMP certification. This represents a statutory requirement under Texas Government Code, not procurement preference.
4) How long does TX-RAMP authorization take?
Authorization timelines vary by certification level and vendor preparedness. Level 1 assessments typically require 3-5 months for well-prepared vendors; Level 2 reviews extend 6-9 months given expanded control scope and evidence requirements.



.svg)
.svg)
.svg)