22% of organizations have experienced a serious or business-disrupting IoT security incident in the past 12 months. Each network-connectable device represents a potential entry point for attackers targeting enterprise infrastructure—a reality that becomes apparent when ransomware propagates through building systems, medical devices leak protected health information, or industrial controllers become vectors for operational disruption.
UL 2900 provides consistent, testable criteria for evaluating the cybersecurity of network-connectable products across industrial control systems, medical devices, IoT hardware, and life-safety signaling systems. This standard addresses a fundamental gap: most organizations implement security controls reactively, after incidents occur, rather than embedding security into product architecture from initial design. For companies selling to enterprises—where procurement processes increasingly demand objective evidence of cybersecurity due diligence—UL 2900 certification serves as verifiable proof that products have undergone systematic vulnerability testing, malware analysis, and security control validation.
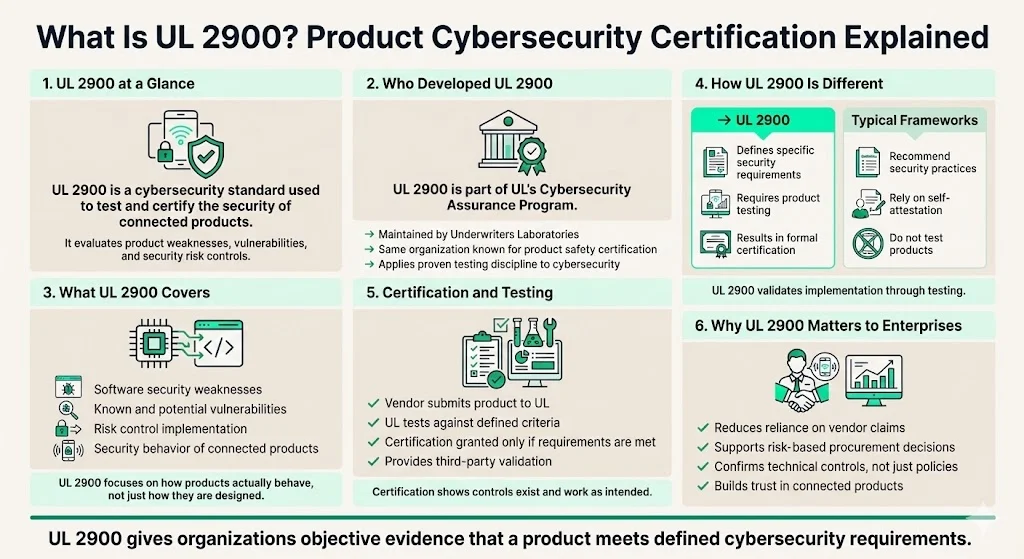
What is UL 2900?
UL 2900 is a series of standards developed as part of UL's Cybersecurity Assurance Program for assessing product weaknesses, vulnerabilities, and security risks controls. Underwriters Laboratories—the same organization that has certified electrical safety for over a century—maintains this standard to establish repeatable, objective evaluation methods for software and hardware security in connected products.
Unlike aspirational security frameworks that recommend practices without enforcement mechanisms, UL 2900 specifies product requirements for more secure products and a certification that UL tests a submitted product against—it spells out requirements for securing a product and the set of tests it is subjected to in order to gain certification. This approach provides enterprises with third-party validation that vendors have implemented specific technical controls, not merely documented security policies.
Structure: Parts and Their Scope
The UL 2900 series addresses different product categories through sector-specific requirements:
UL 2900-1 establishes general requirements for any network-connectable product. Published and adopted as an ANSI (American National Standards Institute) standard in July 2017, this baseline standard defines requirements for software vulnerability testing, secure architecture, access control, data confidentiality, firmware update mechanisms, logging capabilities, and decommissioning procedures. It applies to IoT devices, embedded systems, enterprise hardware, and any product that connects to networks.
UL 2900-2-1 addresses particular requirements for healthcare, wellness, and medical-device systems. Published and adopted as an ANSI standard in September 2017, this standard applies to network connected components of healthcare systems and was officially recognized by the FDA in June 2018. Medical device manufacturers seeking FDA approval or healthcare enterprise procurement contracts leverage this certification to demonstrate compliance with cybersecurity guidance for electronic protected health information (ePHI) and patient safety systems.
UL 2900-2-2 targets industrial control systems, automation components, and SCADA devices. Published in March 2016 as an Outline of Investigation, it has not been developed into a standard and published. This part faced objections from the International Society of Automation (ISA) due to overlap with IEC 62443, which already provides comprehensive industrial cybersecurity requirements. Organizations in the industrial sector typically adopt IEC 62443 for process-level security while using UL 2900-1 for product-level certification where applicable.
UL 2900-2-3 covers security and life-safety signaling systems—building security controls, alarm systems, access control devices, and video management systems. Tested under the 'Security and Life Safety' category, UL 2900-2-3 specifically evaluates physical-security products for cybersecurity readiness and applies a three-tiered evaluation model, ranking with an increasing level of security for each tier. This addresses vulnerabilities in building automation systems that, when compromised, can disable emergency response capabilities or provide physical access to facilities.
Why UL 2900 Matters for Enterprise-Focused Companies
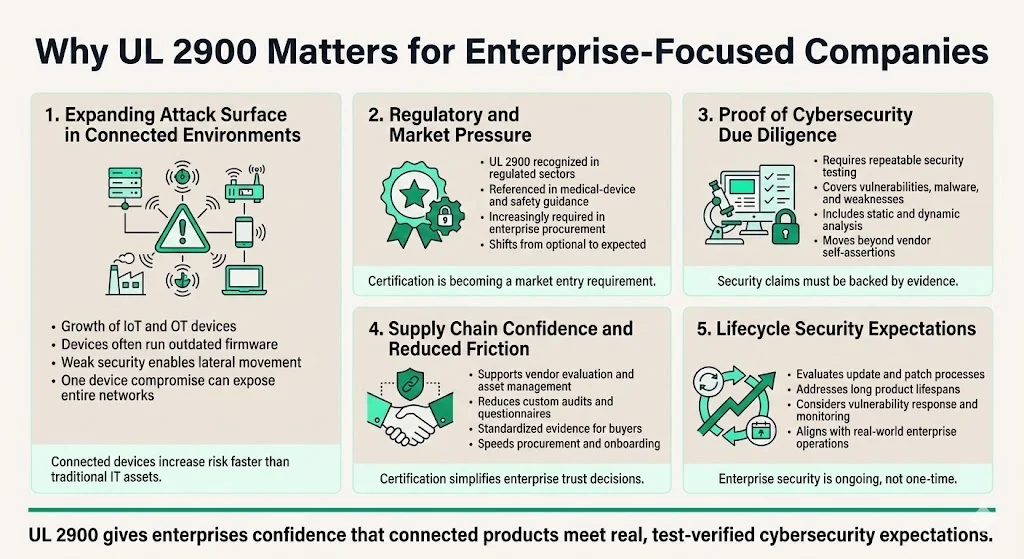
1) Rising Cybersecurity Risk in Connected Infrastructure
Network-connectable devices proliferate across enterprise environments—from industrial sensors monitoring production lines to medical infusion pumps managing patient care. Each device expands the attack surface. Attackers increasingly target IoT and operational technology (OT) devices because they frequently lack robust security controls, run outdated firmware, and provide lateral movement opportunities within enterprise networks. A single compromised device can serve as the entry point for network-wide breaches.
2) Regulation and Market Expectations
For medical device manufacturers, the U.S. FDA has recognized UL 2900 as a consensus standard to establish safety and effectiveness. IMDRF's latest guidance document references UL 2900, and many countries—including Australia, Canada, China, France, the U.S. and Vietnam—have referenced UL 2900 in their local or regional guidance documents. This regulatory recognition transforms UL 2900 from voluntary best practice to competitive necessity for companies targeting regulated sectors. Enterprises purchasing medical devices, industrial control systems, or life-safety equipment increasingly require vendors to demonstrate cybersecurity certifications as part of procurement processes.
3) Demonstrable Cybersecurity Due Diligence
UL 2900 provides registrants with repeatable tests that can provide evidence to support device cybersecurity claims, including tests covering vulnerabilities, malware, and software weaknesses for connectable devices. This objective evidence addresses a fundamental problem in enterprise procurement: vendors can claim "secure by design" or "enterprise-grade security" without verifiable proof. UL 2900 certification requires documented evidence from static analysis, dynamic testing, penetration testing, and fuzz testing—technical evaluations that reveal actual security posture rather than marketing claims.
4) Supply Chain and Enterprise Trust
Healthcare delivery organizations (HDOs) can use the UL 2900 Standard as part of their procurement process, for asset management through looking at certificates, and for integration risk management. Enterprises face substantial due-diligence burdens when evaluating vendors. Security questionnaires, on-site audits, and penetration testing requirements consume time and resources from both buyers and sellers. A UL 2900 certificate reduces this friction by providing standardized evidence that specific security controls exist, attack surfaces have been assessed, and vulnerabilities have been systematically identified and remediated.
5) Lifecycle Security and Maintenance Expectations
UL 2900 evaluation extends beyond point-in-time testing to assess lifecycle processes: how vendors identify and patch vulnerabilities, deploy security updates, monitor security events, manage configuration changes, and handle decommissioning. Products deployed in enterprise environments operate for years, often decades in industrial settings. Security certifications that evaluate only initial release fail to address the reality that vulnerabilities emerge continuously. UL 2900's emphasis on update mechanisms, patch management, and monitoring capabilities aligns with enterprise expectations for sustained security posture.
What UL 2900 Certification Involves — Key Requirements and Process
Core Requirements and Controls (under UL 2900-1)
- Risk Management and Attack Surface Documentation: Requirements regarding the software developer (vendor or other supply chain member) risk management process for their product mandate documented threat modeling based on intended use, network exposure, data sensitivity, and potential attack vectors. Vendors must identify which components communicate over networks, what data they transmit, what protocols they use, and what privileges they require.
- Software Security Testing: Methods by which a product shall be evaluated and tested for the presence of vulnerabilities, software weaknesses, and malware include static code analysis, dynamic application security testing, penetration testing, and fuzz testing. All source code provided by the vendor shall be evaluated by means of static code analysis, and the product shall be evaluated for at least all software weaknesses listed in the latest versions of sources mentioned in Appendix A. This encompasses Common Weakness Enumeration (CWE) Top 25, OWASP Top 10, and other recognized vulnerability catalogs.
- Security Controls Implementation: Requirements regarding the presence of security risk controls in the architecture and design of a product mandate specific technical implementations: multi-factor authentication or role-based access control; encrypted communication channels using current cryptographic standards; data confidentiality protections for data at rest and in transit; signed firmware updates with rollback protection; security event logging with tamper-evident storage; secure decommissioning procedures that purge sensitive data; defense-in-depth architecture with security boundaries between components.
- Documentation Requirements: Documentation and process assessment includes quality management system (QMS), risk management (RM) and software development life cycle (SDLC) process review, and product document review. Vendors must provide architecture diagrams showing trust boundaries, design documentation explaining security decisions, test reports demonstrating vulnerability remediation, and security-related operational procedures.
Lifecycle and Post-Market Procedures
Certification evaluation extends to operational capabilities: continuous monitoring mechanisms for security events; logging infrastructure that captures authentication attempts, configuration changes, and anomalous behavior; security update distribution channels with cryptographic verification; configuration and change control processes that prevent unauthorized modifications; decommissioning procedures that ensure data purging when devices are retired, resold, or repurposed.
Manufacturers can use UL 2900 cybersecurity certifications to manage the supply chain security of components they integrate into their products—supply chain risks are a particularly daunting challenge for manufacturers as they increasingly leverage third-party software components, and companies need a way to identify, assess, and correct vulnerabilities in all product components before they are integrated into systems.
Certification Process (via UL / Third-Party Testing Labs)
- Gap Analysis: Initial assessment identifies where products or organizational processes fail to meet UL 2900 criteria. This phase reveals missing security controls, insufficient documentation, architectural vulnerabilities, or process weaknesses in secure development lifecycle.
- Full Evaluation: UL Solutions offers tests not only as part of certification so manufacturers can bring a product to market, but also during R&D, development activities or post-market—the UL 2900-2-1 evaluation process can be implemented flexibly depending on how and when an organization is engaging with UL Solutions. Hands-on testing evaluates the actual product under realistic network conditions, reviewing documentation completeness, verifying control effectiveness, and assessing lifecycle procedures.
- Certification Issuance: The UL Cybersecurity Assurance Program (UL CAP) is a certification program for evaluating the IoT security of network-connectable products and systems—UL CAP uses the UL 2900 series of standards. Once compliance is verified across all evaluation areas, UL issues certification under the CAP program.
- Periodic Reassessment: While UL 2900 documentation does not mandate specific recertification intervals, the lifecycle nature of security implies follow-up assessments—particularly when products undergo significant changes in functionality, network connectivity, or data handling. Enterprises often require vendors to maintain current certifications, driving periodic reevaluation.
Which Industries and Product Types Benefit Most
1) Industrial Control Systems and Industrial IoT: Devices connecting to networks in manufacturing, energy, water treatment, or building automation require robust security. Current coverage includes industrial control systems—UL 2900-2-2, specifically designed for industrial control systems, aligns with IEC 62443 criteria. While UL 2900-2-2 has not achieved full standardization, vendors building programmable logic controllers (PLCs), human-machine interfaces (HMIs), supervisory control systems, or industrial IoT sensors can adopt UL 2900-1 requirements to demonstrate security commitment.
2) Medical Devices and Healthcare Systems: UL 2900-2-1 applies to network connected components of healthcare systems, covering medical device data systems, electronic health record interfaces, connected diagnostic equipment, infusion pumps, patient monitoring systems, and wellness devices. For companies targeting hospital networks, medical device manufacturers, or healthcare providers, this certification directly supports FDA regulatory submissions and healthcare enterprise procurement requirements.
3) General Connected Products: UL 2900-1 provides broad coverage for enterprise-grade IoT devices, smart building components, network-attached hardware, embedded systems with network connectivity, and software platforms managing connected devices. Any product transmitting data over networks—whether Ethernet, Wi-Fi, cellular, or industrial protocols—falls within UL 2900-1 scope.
4) Safety and Life-Safety Signaling Systems: UL 2900-2-3 addresses video surveillance systems, access control platforms, intrusion detection systems, fire alarm panels with network connectivity, emergency notification systems, and building security management platforms. Compromise of these systems can disable emergency response, provide unauthorized physical access, or mask security incidents—making cybersecurity certification critical for enterprise facilities.
5) Connected Hardware Where Safety and Security Converge: Products combining hardware vulnerability concerns, software security requirements, and network security compliance benefit particularly from UL 2900's comprehensive approach. This includes embedded systems in safety-critical applications, industrial controllers managing hazardous processes, or medical devices where cybersecurity failures create patient safety risks.
While UL 2900 does not explicitly address automotive cybersecurity, companies in automotive supply chains designing network-connectable components—telematics units, infotainment systems, or vehicle-to-infrastructure communication modules—can adopt UL 2900 practices to demonstrate security rigor, particularly when those components share similarities with industrial embedded systems or IoT devices.
Comparing UL 2900 with Other Standards and Frameworks
IEC 62443 vs. UL 2900
IEC 62443 focuses on industrial automation and control systems (IACS) security across multiple dimensions: secure development lifecycle processes, component-level security requirements, system integration security, and operational security. It provides process-oriented guidance for establishing industrial cybersecurity programs, defining security levels, and implementing defense-in-depth across zones and conduits.
UL 2900 is product-centric and evaluation-focused: it defines concrete, testable security criteria for network-connectable products and provides certification through systematic testing. UL 2900-2-2 applies some security criteria from IEC 62443 for product testing and process validation.
Many organizations adopt both standards: IEC 62443 guides internal secure development processes, security architecture decisions, and system-level integration, while UL 2900 provides product-level certification demonstrating that specific components meet testable security requirements. For industrial control system vendors, this combination addresses both process maturity and product security validation.
The overlap between UL 2900-2-2 and IEC 62443 led to objections from ISA—the standards development organization behind IEC 62443—resulting in UL 2900-2-2 remaining as an outline rather than fully ratified standard. Organizations in industrial sectors typically prioritize IEC 62443 certification for components while using UL 2900-1 for broader product-level validation where regulatory or customer requirements demand it.
Complementarity with Risk Management and Lifecycle Standards
UL 2900 focuses on technical security requirements and testing methodologies. Comprehensive security risk management requires additional standards: AAMI TIR 57 for medical device security risk management, IEC 62304 for medical device software lifecycle, ISO 13485 for medical device quality management, or NIST Cybersecurity Framework for organizational risk management.
UL 2900 certification validates that specific technical controls exist and function correctly. It does not, on its own, define enterprise-wide risk assessment processes, incident response procedures, or governance frameworks. Organizations often pair UL 2900 product certification with broader risk-management standards to demonstrate comprehensive cybersecurity posture across products, processes, and organizational practices.
Practical Steps for Companies Considering UL 2900 Certification
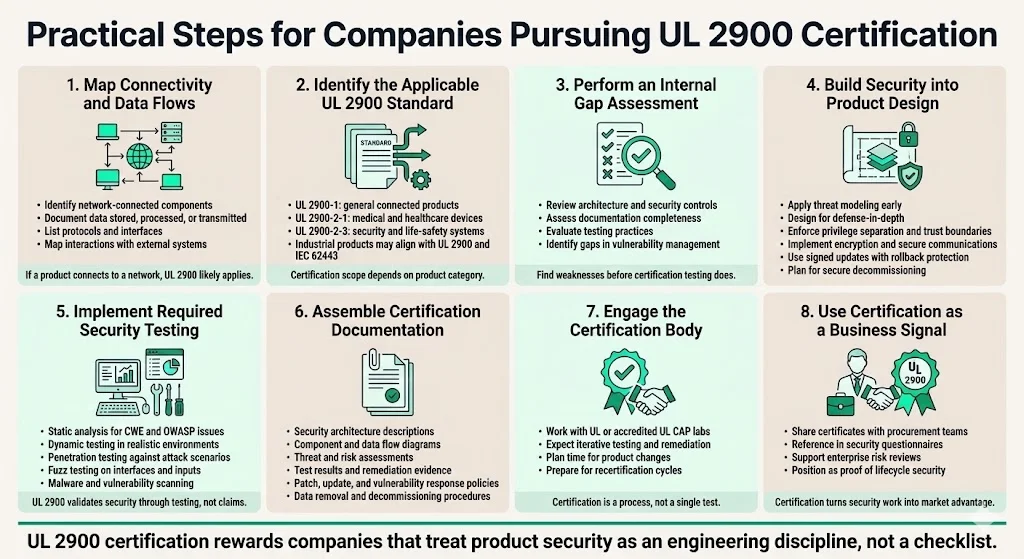
1. Map Product Connectivity and Data Flows: Document which components connect to networks, what data they transmit or store, what protocols they implement, and what external systems they interact with. If your product is network-connectable and handles sensitive data, UL 2900 applies.
2. Determine Applicable UL 2900 Part: General connected devices use UL 2900-1. Medical devices, healthcare system components, or wellness products require UL 2900-2-1. Security systems, access control, or life-safety signaling devices target UL 2900-2-3. Industrial control components may reference UL 2900-2-2 criteria or adopt UL 2900-1 with IEC 62443.
3. Conduct Internal Gap Analysis: Identify missing security controls, insufficient documentation, architectural vulnerabilities, or process weaknesses. Assess current static analysis capabilities, penetration testing practices, malware scanning, and vulnerability management processes against UL 2900 requirements.
4. Embed Security in Design Phase: Implement threat modeling during requirements definition. Design security architecture with defense-in-depth, privilege separation, and trust boundaries. Establish access control mechanisms, cryptographic protections for data and communications, signed update mechanisms with rollback protection, security event logging infrastructure, and decommissioning procedures. Address supply-chain security for third-party components.
5. Implement Comprehensive Testing: UL 2900 specifically requires static analysis and commercial products are better suited to provide the reporting and documentation trail needed for certifications. Deploy static analysis tools addressing CWE and OWASP vulnerabilities. Conduct dynamic application security testing under realistic network conditions. Perform penetration testing simulating attacker techniques. Execute fuzz testing against network interfaces and input parsing. Scan for known vulnerabilities and malware signatures.
6. Prepare Certification Documentation: Compile design documents explaining security architecture and trust boundaries. Create architecture diagrams showing component interactions and security controls. Document risk assessments identifying threats and mitigations. Assemble test reports demonstrating vulnerability identification and remediation. Write update and patch management policies defining security response procedures. Define decommissioning procedures ensuring data purging.
7. Engage Certification Body: The UL 2900 Standard can be used by certifiers (such as UL Solutions) to do repeatable, reproducible testing, and to issue third-party product certification and recertification. Contact UL or accredited testing laboratories under the UL CAP program. Plan for iterative evaluation cycles—initial assessment often reveals issues requiring remediation before full certification. Budget time for potential product modifications or documentation enhancements.
8. Leverage Certification as Differentiator: Use UL 2900 certification in enterprise sales processes to demonstrate objective security validation. Provide certificates to procurement teams conducting vendor assessments. Reference certification in responses to security questionnaires. Position certification as evidence of lifecycle security commitment, not merely point-in-time testing.
Challenges, Limitations, and Considerations
Incomplete Standard Coverage: Parts of UL 2900—specifically 2900-2-2 and initially 2900-2-3—have faced ratification challenges or development delays. For industrial control systems, IEC 62443 provides more comprehensive and widely accepted requirements. Organizations must evaluate which standards their target markets recognize and prioritize accordingly.
Not a Complete Risk Management Framework: UL 2900 validates technical security controls and testing rigor. It does not define comprehensive cybersecurity risk-management processes, organizational governance structures, or incident response capabilities. Companies require additional frameworks—NIST CSF, ISO 27001, or sector-specific standards—to address enterprise-wide security management.
Cost and Timeline Impact: Certification involves design effort, security testing infrastructure, documentation development, and potential redesign cycles. Organizations unprepared for security requirements at design phase face substantial rework costs. Initial certification typically requires several months, depending on product complexity and existing security maturity. This impacts development timelines and budgets, particularly for companies treating security as late-stage validation rather than design-phase requirement.
Ongoing Maintenance Requirements: Security updates, patch management, vulnerability monitoring, logging infrastructure, and decommissioning procedures require sustained operational investment. Products evolving rapidly through feature additions or architectural changes must maintain compliance—potentially requiring recertification or reassessment. Organizations lacking mature security operations capabilities struggle with post-certification maintenance.
Regional Recognition Variability: While UL 2900-2-1 has achieved international recognition through IMDRF guidance and country-specific references, UL 2900 generally has stronger recognition in North America than in Europe or Asia. European enterprises may prioritize CE marking, IEC standards, or ETSI cybersecurity requirements. Asian markets may emphasize local certification schemes. Companies targeting global markets may need multiple certifications to address regional expectations.
Why UL 2900 Matters for Critical Infrastructure and Enterprise Products
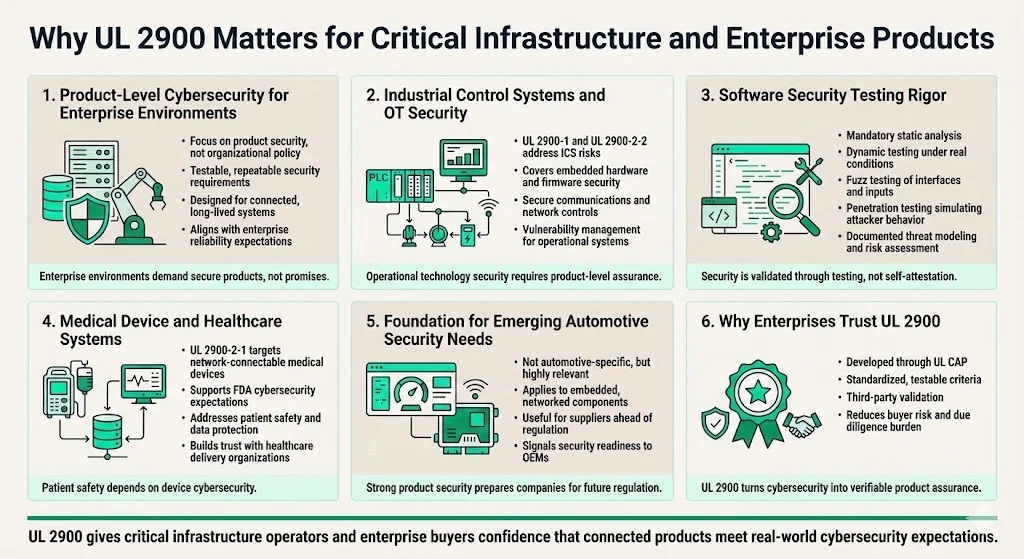
UL 2900 provides robust standards for product-level cybersecurity, aligning with enterprise expectations for secure, reliable connected devices. The UL Cybersecurity Assurance Program (UL CAP) was created to help industrial end users and product manufacturers minimize cybersecurity risks through standardized, testable criteria for assessing software vulnerabilities and weaknesses—this group developed the specifications which have since become the testable technical criteria of the UL 2900 Series of Standards.
For industrial control systems and hardware vulnerability evaluation, UL 2900-1 and the criteria outlined in UL 2900-2-2 address vulnerabilities in embedded hardware, firmware security, and network security compliance. Companies building ICS components, industrial IoT devices, or automation equipment demonstrate that they have systematically addressed attack surfaces, implemented secure communication protocols, and established vulnerability management processes.
For software security testing and risk assessment protocols, UL 2900 mandates thorough evaluation through static analysis, dynamic testing, fuzzing, and penetration testing—combined with documented threat modeling and risk assessment. This meets enterprise-level scrutiny on software security, particularly in procurement processes where buyers demand evidence rather than assertions.
For medical device security, UL 2900-2-1 directly targets network-connectable medical devices, medical device data systems, and wellness devices. Certification supports regulatory compliance with FDA cybersecurity guidance and reassures healthcare enterprises evaluating patient-safety-critical systems.
While UL 2900 does not explicitly target automotive cybersecurity, companies creating network-connectable hardware or software for automotive systems can adopt UL 2900 practices—particularly for components sharing characteristics with industrial embedded systems or IoT devices—to demonstrate security commitment ahead of automotive-specific cybersecurity regulations.
Conclusion
UL 2900 offers tangible value to companies targeting enterprise customers by transforming security from marketing claim to verifiable fact. Enterprises demand objective evidence that vendors have implemented specific security controls, tested for vulnerabilities, and established lifecycle security processes. UL 2900 certification provides that evidence through systematic evaluation of software security, hardware vulnerabilities, network security controls, and operational security capabilities.
Adopting UL 2900 requirements during design and development phases—rather than treating certification as late-stage validation—reduces security risk, accelerates regulatory acceptance, and builds trust with enterprise procurement teams. Most organizations discover during certification attempts that their security posture falls short of testable requirements: missing access controls, inadequate logging, absent update mechanisms, or undocumented threat models. Companies embedding UL 2900 requirements into product architecture from initial design avoid costly remediation cycles.
Certification is not merely a badge for marketing materials. It reflects genuine attention to software and hardware security, lifecycle management practices, and risk control implementation. For companies selling network-connectable products into regulated industries, critical infrastructure, or enterprise environments, UL 2900 certification demonstrates that security claims can withstand third-party scrutiny—a differentiator when enterprises face mounting pressure to reduce supply-chain cybersecurity risk.
Frequently Asked Questions (FAQs)
1) What is the difference between UL 2900 and IEC 62443?
UL 2900 is a product-level standard providing concrete, testable security criteria for network-connectable devices, with certification through systematic evaluation of vulnerabilities, malware, software weaknesses, and security controls.
IEC 62443 is a comprehensive framework for industrial automation and control systems (IACS) security, covering secure development lifecycle processes, component and system security requirements, security levels, zones and conduits architecture, and operational security practices.
Many organizations use them together: IEC 62443 guides system-level security architecture and secure development processes, while UL 2900 provides product-level cybersecurity validation through third-party testing and certification. For industrial control system vendors, this combination addresses both process maturity and component security.
2) What is the highest certification for cybersecurity?
No universal "highest" cybersecurity certification exists because requirements vary by industry, product type, regulatory environment, and organizational context.
For network-connectable products, UL 2900 certification under UL CAP represents well-recognized validation in North America, particularly for medical devices and life-safety systems.
For industrial automation and control systems, certifications under IEC 62443—demonstrating component or system security level achievement—provide widely accepted validation.
For organizational security posture, many enterprises combine product-level certifications (UL 2900, Common Criteria, FIPS 140-2/140-3) with process certifications (ISO 27001, SOC 2) and framework adoption (NIST CSF, IEC 62443) to demonstrate comprehensive security across products, processes, and operations.
3) What is UL 2900-1?
UL 2900-1 is "Software Cybersecurity for Network-Connectable Products, Part 1: General Requirements"—the baseline standard defining security requirements for any connected product regardless of industry.
It establishes requirements for software vulnerability testing through static and dynamic analysis, secure architecture and design with defense-in-depth, access control and authentication mechanisms, data confidentiality protections, secure firmware and software update capabilities, security event logging and monitoring, decommissioning procedures ensuring data purging, supply-chain security for third-party components, and documentation supporting risk assessment and threat modeling.
UL 2900-1 serves as the foundation for sector-specific parts (2900-2-1 for healthcare, 2900-2-2 for industrial control, 2900-2-3 for life-safety systems) that add industry-specific requirements on top of these general baseline controls.
4) What is UL 2900-2-3?
UL 2900-2-3 provides specific requirements for security and life-safety signaling systems—products including video management systems, access control platforms, intrusion detection systems, fire alarm systems with network connectivity, emergency notification systems, and building security infrastructure.
This standard recognizes that compromise of life-safety and physical security systems creates immediate risk: disabled emergency alerts, unauthorized facility access, or concealed security incidents. UL 2900-2-3 applies a three-tiered evaluation model, with increasing security requirements at each level, allowing organizations to demonstrate progressive security maturity while meeting baseline protection requirements for systems where cybersecurity failures directly impact physical safety and security.



.svg)
.svg)
.svg)