A VRM process—Vendor Risk Management process—is the structured framework enterprises use to identify, evaluate, and continuously oversee the security, compliance, and operational risks introduced by third-party vendors. Unlike ad hoc vendor checks, a formal VRM process applies standardized criteria, assigns risk tiers, enforces contract controls, and monitors vendor performance throughout the relationship lifecycle. For enterprise buyers, the VRM process determines whether a vendor qualifies for access to sensitive data, critical infrastructure, or mission-critical services—and whether that access can be sustained long term.
Enterprise procurement teams, security groups, and risk officers treat vendors as extensions of their own operations. A breach at a vendor can trigger regulatory fines, legal liability, and reputational damage for the buyer. That reality makes the VRM process a gatekeeper in enterprise sales cycles. Vendors that understand how enterprises structure their VRM programs—and prepare documentation accordingly—reduce review timelines, avoid late-stage deal blockers, and build long-term trust.
Why Enterprise Clients Invest Heavily in VRM
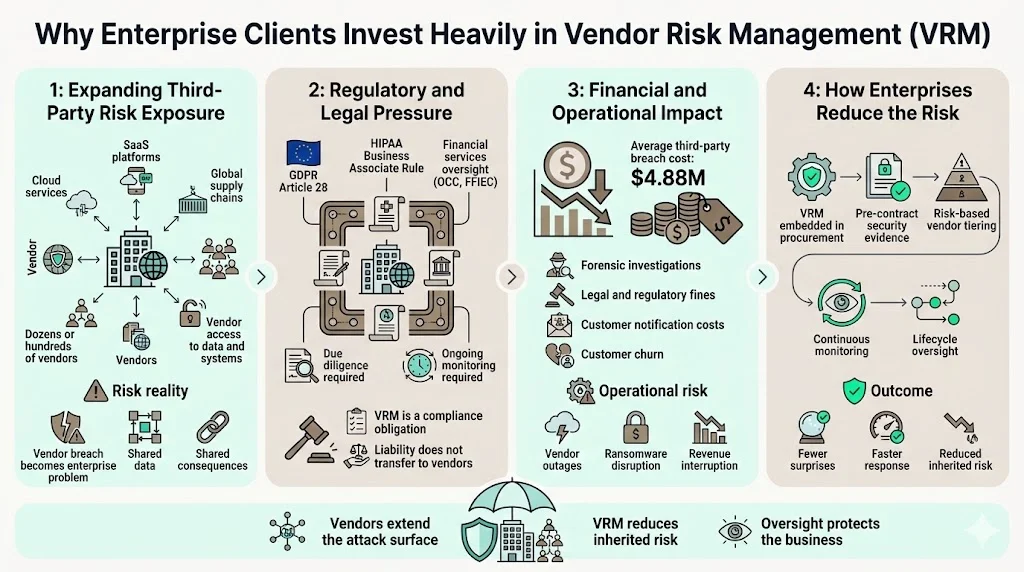
Third-party vendor relationships account for a substantial portion of organizational risk exposure, particularly as enterprises adopt cloud services, SaaS platforms, and global supply chains. Most organizations now rely on dozens or hundreds of vendors with varying levels of access to customer data, intellectual property, and operational systems. When a vendor suffers a data breach or service failure, the enterprise inherits the consequence—regulatory penalties under GDPR, HIPAA, or CCPA, customer notification obligations, forensic investigation costs, and lasting reputational harm.
Regulatory frameworks across industries now mandate formal oversight of third-party risk. GDPR Article 28 requires data processors to demonstrate appropriate security measures. HIPAA's Business Associate Rule imposes liability on covered entities for breaches caused by vendors handling electronic protected health information (ePHI). Financial services regulators, including the OCC and FFIEC, require financial institutions to conduct due diligence and ongoing monitoring of service providers. These obligations transform VRM from a best practice into a compliance requirement—and noncompliance carries material penalties.
The cost of inadequate VRM is quantifiable. Data breaches involving third-party vendors cost organizations an average of $4.88 million per incident, factoring in remediation, legal fees, regulatory fines, and customer attrition. Operational failures—such as a vendor's service outage or ransomware attack—disrupt revenue-generating activities and erode customer confidence. Enterprises mitigate these exposures by embedding VRM into procurement workflows, requiring evidence of security controls before contract execution, and maintaining continuous oversight throughout the vendor lifecycle.
Core Stages of the VRM Process
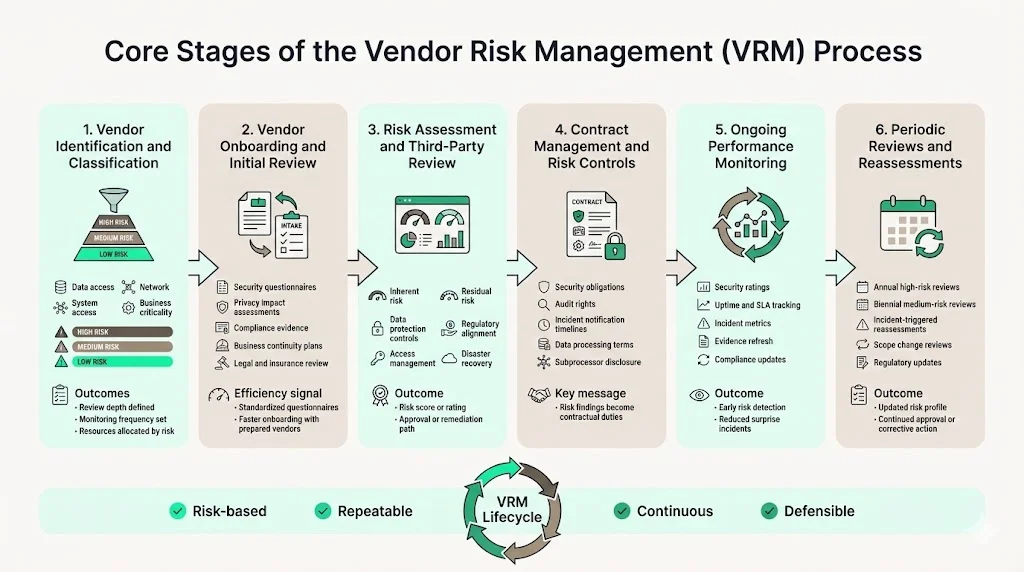
1) Vendor Identification and Classification
Enterprises classify vendors according to risk exposure, assigning each relationship to a tier that determines the depth and frequency of review. Classification criteria typically include:
- Data access: Does the vendor process, store, or transmit sensitive data such as personally identifiable information (PII), protected health information (PHI), or payment card data?
- System access: Does the vendor connect to internal networks, access production systems, or maintain privileged credentials?
- Business criticality: Would a vendor outage, data loss, or security incident materially disrupt operations, revenue, or regulatory standing?
High-risk vendors—those handling sensitive data or critical infrastructure—undergo comprehensive security assessments, annual audits, and continuous monitoring. Medium-risk vendors face periodic reviews and targeted questionnaires. Low-risk vendors may require only baseline due diligence. Correct classification shapes resource allocation, review timelines, and contract terms. Vendors that self-classify accurately and document their risk profile expedite this stage.
2) Vendor Onboarding and Initial Risk Review
Once a vendor is classified, enterprises initiate onboarding procedures designed to surface risks before contract execution. Buyers request detailed information through security questionnaires, privacy impact assessments, and operational due diligence documents. Common requests include:
- Security posture: Descriptions of data encryption practices, access controls, vulnerability management programs, and incident response capabilities
- Compliance status: Evidence of certifications such as SOC 2 Type II, ISO 27001, HIPAA compliance attestations, or GDPR data processing agreements
- Business continuity: Disaster recovery plans, backup procedures, uptime SLAs, and vendor redundancy strategies
- Legal and contractual: Insurance coverage, indemnification terms, subprocessor disclosures, and data residency commitments
Enterprises use standardized questionnaires—often based on frameworks like the SIG Core or CAIQ—to compare vendors consistently. Sellers that maintain current, comprehensive documentation and respond promptly to information requests reduce onboarding timelines from months to weeks.
3) Risk Assessment and Third-Party Risk Review
After collecting vendor information, enterprise risk teams conduct formal assessments to quantify third-party risk. This stage evaluates security, legal, operational, and financial dimensions, often scoring vendors using inherent risk (the risk before controls are applied) and residual risk (the risk remaining after controls are implemented).
Common focus areas include:
- Data protection: Encryption in transit and at rest, data retention policies, secure deletion procedures, and cross-border data transfer mechanisms
- Regulatory compliance: Alignment with GDPR, HIPAA, SOC 2, ISO 27001, PCI DSS, or industry-specific mandates
- Business continuity: Recovery time objectives (RTOs), recovery point objectives (RPOs), and documented disaster recovery testing
- Access management: Multi-factor authentication (MFA), role-based access controls (RBAC), privileged access management (PAM), and account lifecycle policies
Risk assessments generate scores or ratings that inform contract negotiations, insurance requirements, and ongoing monitoring frequency. Vendors with demonstrable security controls, documented policies, and third-party attestations (such as SOC 2 Type II reports covering a 12-month observation period) achieve higher risk scores and faster approvals.
4) Contract Management and Risk Controls
Contract management translates risk findings into enforceable obligations. Enterprise legal and procurement teams embed standard clauses designed to allocate responsibility, define remediation timelines, and preserve audit rights. Typical contract provisions include:
- Security obligations: Requirements to maintain specific controls (e.g., encryption standards, penetration testing cadence, vulnerability remediation SLAs)
- Audit rights: The buyer's ability to conduct or commission independent security audits, request evidence, and review control effectiveness
- Incident response timelines: Notification windows following security incidents (often 24–72 hours), forensic investigation cooperation, and breach remediation responsibilities
- Data processing terms: Subprocessor disclosures, data residency commitments, and deletion obligations upon contract termination
Contracts establish shared accountability. Vendors that negotiate these terms transparently—offering documented controls, clear incident response procedures, and audit-ready evidence—build credibility and reduce legal friction.
5) Ongoing Performance Monitoring
VRM extends beyond contract signing. Enterprises monitor vendor performance continuously to detect emerging risks, validate control effectiveness, and track compliance with contractual obligations. Performance monitoring methods include:
- Security ratings: Third-party services that scan vendor domains, IP ranges, and public-facing infrastructure for vulnerabilities, misconfigurations, or leaked credentials
- Service level tracking: Uptime metrics, incident frequency, mean time to resolution (MTTR), and customer support responsiveness
- Evidence reviews: Annual SOC 2 reports, updated penetration test results, business continuity test summaries, and compliance attestations
Continuous monitoring identifies risks before they escalate. Vendors that proactively share updated evidence—such as renewal SOC 2 Type II reports or remediation documentation following penetration tests—demonstrate operational maturity and reduce buyer anxiety.
6) Periodic Reviews and Reassessments
Enterprises reassess vendors at regular intervals, typically annually for high-risk relationships and biennially for medium-risk tiers. Reassessments refresh risk scores, validate control effectiveness, and capture changes in vendor scope, data access, or regulatory obligations. Off-cycle reviews occur in response to:
- Security incidents: Breaches, ransomware attacks, or unauthorized access events at the vendor or its subprocessors
- Scope changes: New data types processed, expanded system integrations, or additional subprocessors introduced
- Regulatory updates: New compliance mandates such as GDPR amendments, HIPAA updates, or industry-specific guidance
Reassessments ensure risk profiles remain accurate. Vendors that maintain current documentation, communicate scope changes promptly, and demonstrate continuous improvement in security controls preserve their standing and avoid contract suspensions or terminations.
Audit and Assurance Within the VRM Process
Audit procedures validate the accuracy of vendor-provided information and confirm control effectiveness. Enterprises conduct internal audits—often led by compliance or internal audit teams—and review external audit reports vendors commission from independent firms. Evidence vendors are frequently asked to share includes:
- SOC 2 Type II reports: Attestations covering security, availability, processing integrity, confidentiality, and privacy over a minimum six-month observation period
- ISO 27001 certifications: Evidence of an operational Information Security Management System (ISMS), including risk assessments, statement of applicability, and surveillance audit results
- Penetration test results: Executive summaries or full reports from third-party penetration testing firms, including identified vulnerabilities, severity ratings, and remediation timelines
Vendors with current, unqualified audit reports reduce enterprise review burdens and accelerate approvals. Organizations that treat audit readiness as continuous—maintaining evidence repositories, documenting control changes, and scheduling annual assessments—convert the VRM process from a compliance burden into a competitive advantage.
Managing Incidents and Escalations
Enterprises expect vendors to detect, contain, and report security or service incidents promptly. VRM processes define incident response roles, communication paths, and documentation requirements. Standard enterprise expectations include:
- Notification timelines: Contractual obligations to notify the buyer within 24–72 hours of detecting a security incident involving customer data or system integrity
- Forensic cooperation: Vendor support during investigations, including access to logs, root cause analyses, and remediation plans
- Remediation tracking: Documented corrective actions, timelines for control implementation, and evidence of testing
Incident handling affects future vendor standing. Vendors that respond transparently, provide detailed root cause analyses, and demonstrate systemic improvements maintain buyer trust. Those that delay notification, withhold information, or repeat incidents face contract termination or reclassification to higher-risk tiers requiring intensive oversight.
Who Owns the VRM Process Inside Large Organizations
VRM responsibilities are distributed across functional teams, each contributing domain expertise:
- Procurement: Manages vendor selection, contract negotiation, and commercial terms
- Security: Evaluates technical controls, reviews security questionnaires, and assesses incident response capabilities
- Risk and compliance: Scores vendor risk, tracks regulatory obligations, and coordinates audit activities
- Legal: Drafts data processing agreements, negotiates liability terms, and ensures contractual enforceability
Vendors selling into enterprises interact with multiple stakeholders throughout the sales cycle. Security reviews initiated by one team often trigger parallel evaluations by compliance, legal, and procurement groups. Understanding this shared ownership helps sellers coordinate responses, anticipate questions, and avoid redundant documentation requests.
Tools Enterprises Use to Run the VRM Process
Enterprises deploy specialized platforms to standardize assessments, automate monitoring, and centralize evidence. VRM tool categories include:
- Risk assessment platforms: Software that distributes questionnaires, scores vendor responses, and tracks remediation (e.g., OneTrust, ServiceNow VRM, Prevalent)
- Security rating services: Tools that scan vendor infrastructure for vulnerabilities, misconfigurations, and exposed credentials, generating continuous risk scores (e.g., SecurityScorecard, BitSight, UpGuard)
- Workflow and evidence tracking systems: Centralized repositories for contracts, audit reports, questionnaire responses, and compliance attestations
Vendors should expect buyers to request access to security documentation through these platforms. Preparing responses in standardized formats—such as SIG Core or CAIQ templates—and maintaining evidence repositories reduces response time and improves consistency.
How Sellers Can Reduce Friction in the VRM Process
Vendors that anticipate enterprise VRM requirements convert reviews from obstacles into trust signals:
- Prepare documentation before it is requested: Maintain current security policies, data flow diagrams, penetration test summaries, SOC 2 reports, and compliance attestations in accessible formats
- Keep policies current and consistent: Align documented policies with operational practices, ensuring auditors and buyers observe the same controls
- Provide clear answers to common enterprise questions: Document data residency, subprocessor relationships, encryption standards, and incident response procedures in vendor-facing materials
- Build trust through transparency: Acknowledge gaps candidly, provide remediation timelines, and demonstrate continuous improvement in security posture
Proactive preparation reduces enterprise review timelines from months to weeks, minimizes back-and-forth questionnaire iterations, and signals operational maturity.
Business Impact of a Strong VRM Process
Vendors with mature security programs and audit-ready documentation experience measurable advantages:
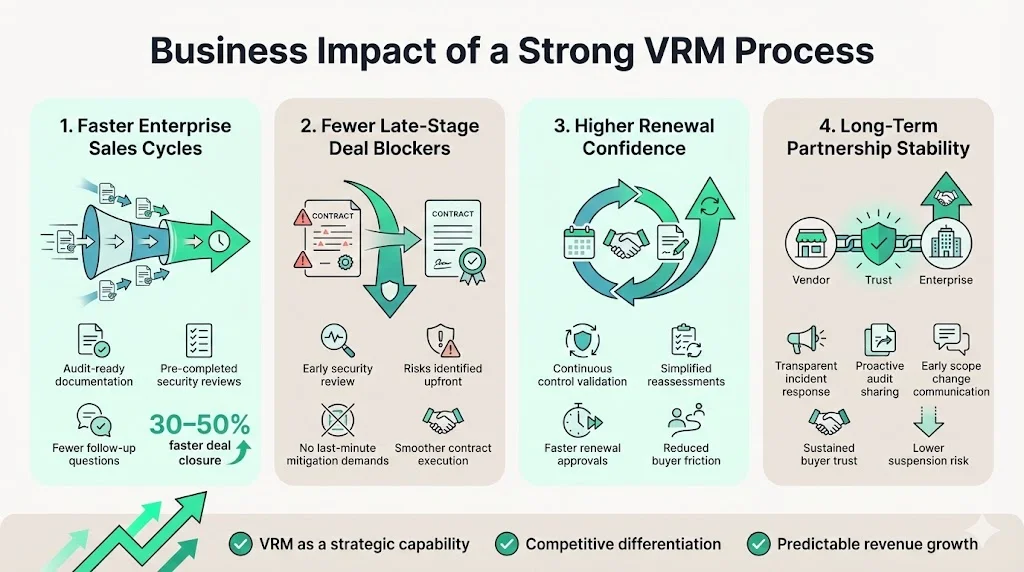
- Faster enterprise sales cycles: Pre-prepared documentation eliminates delays caused by information requests, reducing time-to-close by 30–50%
- Fewer late-stage deal blockers: Security reviews completed early in the sales process prevent contract execution delays or unexpected risk mitigation requirements
- Higher renewal confidence: Buyers renewing contracts with vendors that demonstrate continuous control effectiveness face simplified reassessments and faster approvals
- Long-term partnership stability: Vendors that respond transparently to incidents, share updated audit reports proactively, and communicate scope changes early preserve buyer trust and avoid contract suspensions
Treating VRM as a strategic capability—not a compliance obligation—differentiates vendors in competitive procurement processes and supports predictable revenue growth.
Common VRM Challenges for Vendors
Vendors navigating enterprise VRM processes encounter recurring obstacles:
- Long questionnaires: Security assessments containing 200+ questions across multiple domains, requiring cross-functional coordination and documentation synthesis
- Conflicting customer requirements: Buyers requesting different control standards, data residency commitments, or audit formats, creating compliance fragmentation
- Resource strain on security teams: Small or mid-sized vendors lacking dedicated compliance personnel struggle to respond to multiple simultaneous VRM reviews
- Audit cost and timing: Annual SOC 2 or ISO 27001 audits require budget allocation, auditor scheduling, and operational readiness
Vendors address these challenges by standardizing responses, leveraging compliance automation platforms, maintaining centralized evidence repositories, and scheduling audits to align with peak sales periods. Organizations that invest in audit readiness and documentation infrastructure scale enterprise sales without proportional increases in compliance overhead.
Conclusion
The VRM process is now a standard component of enterprise procurement, embedded in security reviews, contract negotiations, and ongoing vendor oversight. Buyers treat vendors as extensions of their own operations, transferring regulatory obligations, data protection responsibilities, and operational accountability through contractual terms and continuous monitoring. Vendors that understand how enterprises structure VRM programs—classifying vendors by risk, conducting multi-stage assessments, embedding controls in contracts, and monitoring performance continuously—prepare documentation accordingly and reduce review friction.
Preparation transforms VRM from a deal blocker into a trust signal. Vendors with current SOC 2 reports, documented security policies, transparent incident response procedures, and audit-ready evidence convert enterprise security reviews from months-long obstacles into weeks-long validations of operational maturity. In an environment where third-party risk drives procurement decisions, VRM readiness determines sales velocity, renewal confidence, and long-term partnership stability.
FAQs
1) What is the purpose of a VRM process?
The VRM process identifies, assesses, and manages risks introduced by third-party vendors, ensuring vendors meet security, compliance, and operational standards before and throughout the business relationship.
2) How does VRM reduce third-party risk?
VRM reduces third-party risk through structured vendor classification, initial and ongoing risk assessments, contractual controls, continuous performance monitoring, and periodic reassessments that validate control effectiveness.
3) Who owns the VRM process in large organizations?
VRM ownership is shared across procurement, security, risk and compliance, and legal teams, with each group contributing domain expertise during vendor selection, risk evaluation, contract negotiation, and ongoing oversight.
4) How often should vendors be reassessed?
Reassessment frequency depends on vendor risk tier, business criticality, and scope changes—typically annually for high-risk vendors, biennially for medium-risk vendors, and on demand following security incidents or material scope expansions.
5) What tools support VRM programs?
Enterprises use risk assessment platforms for questionnaire distribution and scoring, security rating services for continuous infrastructure monitoring, and workflow systems for evidence tracking, contract management, and audit coordination.



.svg)
.svg)
.svg)