Most organizations pursuing cloud services for government clients treat security assessment as a procedural formality rather than a strategic validation of their security posture. This creates a fundamental gap between documentation and operational reality—a gap that becomes apparent when independent auditors examine actual controls versus stated intentions. Understanding what a Third-Party Assessment Organization (3PAO) does, and why that independence matters, determines whether your security certification represents genuine protection or merely performative compliance.
What is a 3PAO?
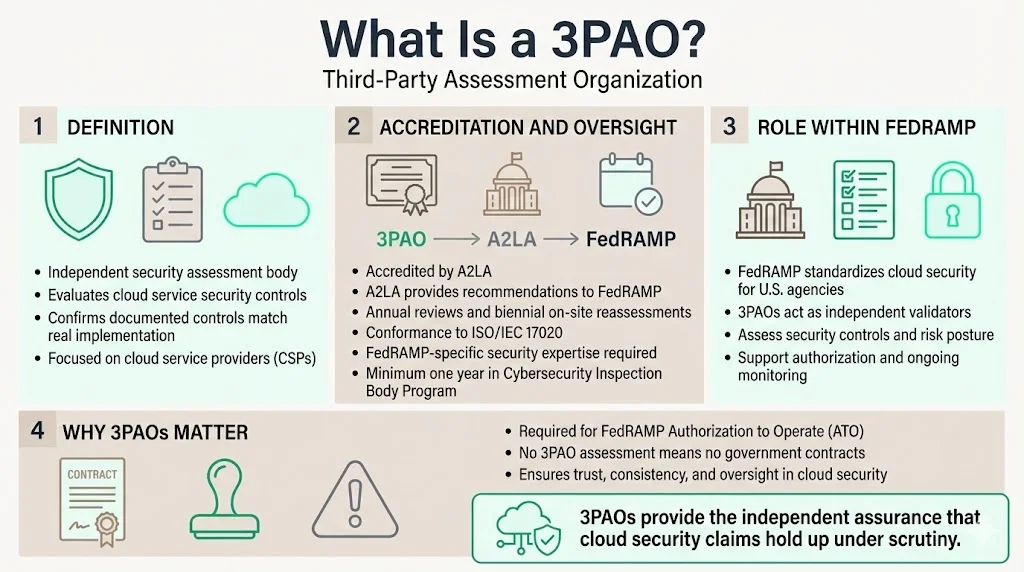
A Third-Party Assessment Organization (3PAO) is an independent, accredited entity that assesses the security of cloud service offerings, typically accredited by the American Association for Laboratory Accreditation (A2LA) and operating within frameworks such as the Federal Risk and Authorization Management Program (FedRAMP). These organizations exist to provide impartial evaluation of cloud security controls—evaluating whether a cloud service provider's (CSP) documented security measures match what's actually implemented.
3PAOs must undergo initial assessment by A2LA, which then provides an assessment recommendation to FedRAMP for approval. To maintain FedRAMP recognition, A2LA performs annual reviews and full on-site reassessments every two years, ensuring 3PAOs meet requirements of ISO/IEC 17020 and FedRAMP-specific knowledge requirements. Organizations seeking 3PAO accreditation must spend at least one year in the Cybersecurity Inspection Body Program demonstrating technical competence prior to FedRAMP 3PAO recognition.
3PAOs operate as the enforcement mechanism for FedRAMP—a government-wide program providing standardized security assessment, authorization, and continuous monitoring for cloud-based services used by federal agencies. Without 3PAO validation, cloud providers cannot obtain the Authorization to Operate (ATO) necessary for government contracts.
What 3PAOs Do — Role & Responsibilities
3PAOs evaluate cloud service security, identify weaknesses, ensure CSPs protect sensitive data, and help build trust through unbiased assessment to support achieving Authorization to Operate. Their responsibilities extend across documentation review, technical testing, and ongoing verification.
Security control assessment forms the foundation: assessors evaluate a CSP's system against required security controls defined in NIST 800-53 and FedRAMP baselines. Manual control testing involves assessors diving deep into security controls, examining implementation and functionality through document review, personnel interviews, and control observation to confirm FedRAMP compliance. This process validates whether controls listed in a System Security Plan (SSP) actually function as documented.
Documentation review and validation requires 3PAOs to compare what CSPs claim in security documentation against what's implemented operationally. Assessors examine System Security Plans, policies, procedures, and evidence artifacts—identifying discrepancies between stated controls and operational reality. This verification prevents "compliance manufacturing"—the practice of generating documentation that satisfies auditors on paper while leaving actual systems vulnerable.
Testing and evaluation includes vulnerability scanning, penetration testing, control testing, stakeholder interviews, and site visits when needed. 3PAO assessment comprises three crucial components: Manual Control Testing, Compliance and Vulnerability Scanning, and Penetration Testing. These evaluations produce concrete evidence of security posture beyond self-reported claims.
Deliverables include Security Assessment Reports (SARs), Security Assessment Plans (SAPs), Readiness Assessment Reports (RARs), risk exposure tables, scan results, and test workbooks. These standardized documents provide federal agencies with consistent, comparable security evaluations across different cloud providers.
Independence and impartiality remain mandatory throughout the assessment process. While some CSPs use 3PAOs as consultants for security documentation or advisory services, they must select a different 3PAO to conduct assessments to ensure assessor impartiality. This separation prevents conflicts of interest where the organization advising on control implementation also validates that implementation.
For the FedRAMP Program Authorization process, CSPs must use FedRAMP recognized 3PAOs for annual assessments of cloud offerings and to evaluate the impact of changes. This continuous or periodic assessment ensures sustained compliance beyond initial certification.
Why 3PAOs Matter — Impact on Businesses & Risk Management
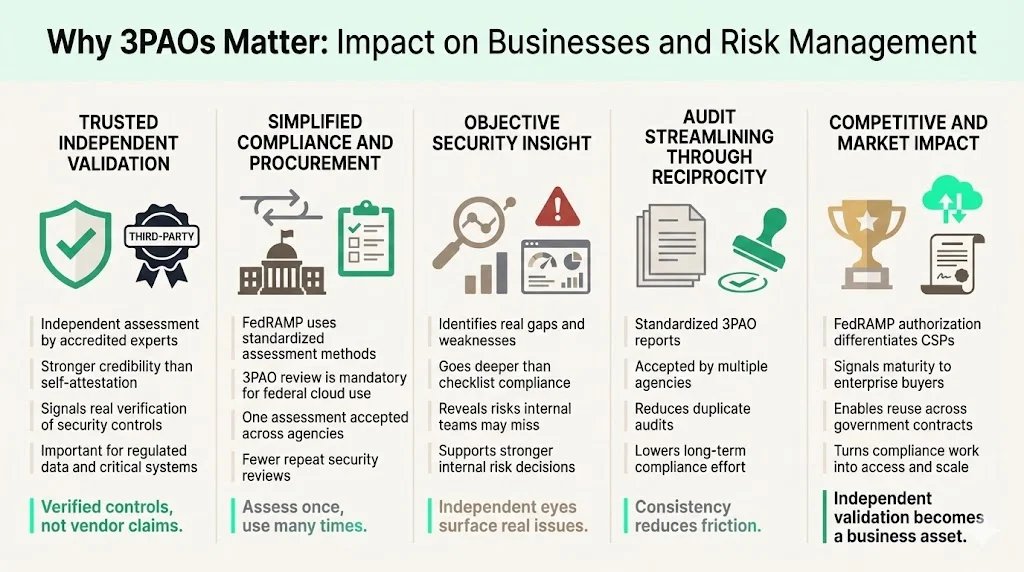
- Trusted third-party validation provides credibility that internal audits or vendor self-assessments cannot match. For government agencies and security-conscious enterprises, 3PAO attestation signals that independent experts have verified security controls—not merely that a vendor claims compliance. This independent verification becomes particularly valuable in sectors handling sensitive data, regulated information, or critical infrastructure.
- Simplified compliance and procurement follows from standardized assessment frameworks. FedRAMP provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud-based services. Cloud providers pursuing federal contracts must complete 3PAO assessment as a mandatory authorization step. Once complete, that assessment applies across federal agencies—eliminating redundant security reviews for every potential customer.
- Objective security posture assessment extends beyond compliance checkbox exercises. Independent evaluation identifies genuine gaps, vulnerabilities, and control weaknesses requiring remediation. For CSPs, this provides actionable intelligence about actual security risks—information useful for internal risk management regardless of regulatory requirements. Many organizations discover implementation gaps during 3PAO assessment that internal teams overlooked or underestimated.
- Audit streamlining and reduced duplication emerges from FedRAMP's reciprocity principle. Because 3PAO reports follow standardized formats and meet consistent evaluation criteria, federal agencies accept these assessments without requiring separate vendor audits. This reciprocity reduces compliance burden for CSPs while providing agencies with reliable, comparable security data.
- Competitive advantage accrues to CSPs that complete FedRAMP authorization via 3PAO assessment. For cloud providers targeting enterprise customers prioritizing security, FedRAMP authorization differentiates them from competitors operating without independent validation. Organizations serving multiple government agencies leverage this single authorization across contracts—converting compliance investment into market access.
The 3PAO Process — Step by Step
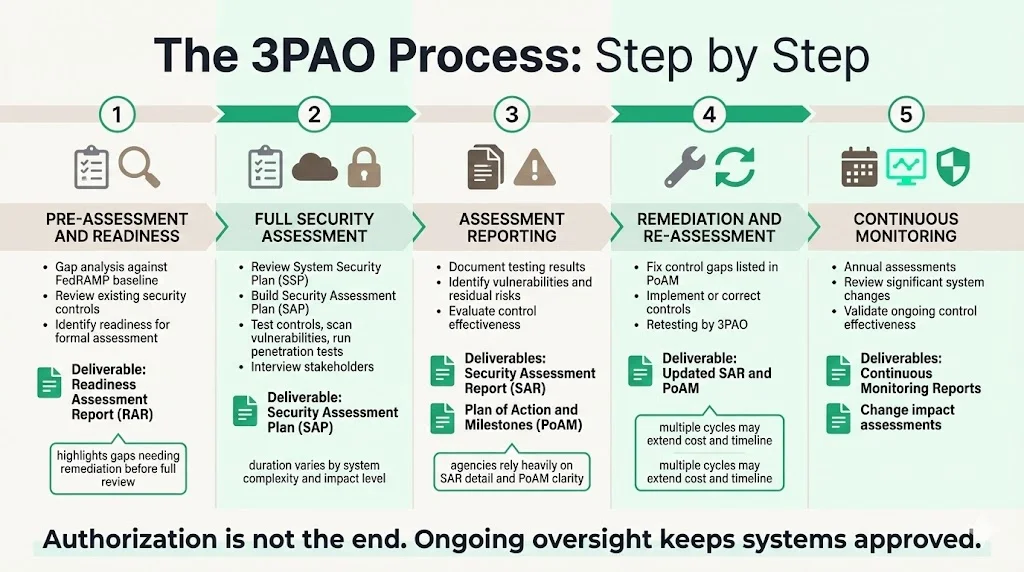
1) Pre-assessment and readiness phase begins with gap analysis determining whether a system likely meets FedRAMP requirements. During this phase, 3PAOs conduct readiness assessments examining current controls against baseline requirements. The resulting Readiness Assessment Report (RAR) identifies gaps requiring remediation before formal assessment. This stage helps CSPs understand the work necessary for certification without the expense of failed formal audits.
2) Full security assessment commences once readiness is established. 3PAOs review System Security Plans and related documentation, then build a Security Assessment Plan (SAP) detailing testing methodology, scope, and evaluation criteria. Assessors conduct control testing, vulnerability scans, penetration tests, and stakeholder interviews according to the SAP. This comprehensive evaluation typically spans weeks or months depending on system complexity and baseline level (Low, Moderate, or High impact).
3) Reporting produces the Security Assessment Report (SAR) documenting test results, risk findings, control effectiveness, and recommendations. The SAR includes detailed evidence of testing conducted, vulnerabilities identified, and residual risks. When findings require remediation, assessors document these in a Plan of Action and Milestones (PoAM) specifying required corrective actions, responsible parties, and completion timeframes. Federal agencies reviewing authorization requests rely heavily on SAR detail and PoAM clarity.
4) Remediation and re-assessment occurs when initial testing identifies control deficiencies. CSPs address findings documented in the PoAM, implementing missing controls or correcting ineffective implementations. 3PAOs then perform retesting or additional evaluation verifying successful remediation before final authorization. This cycle may repeat multiple times for systems with significant gaps—extending timeline and cost beyond initial projections.
5) Continuous monitoring and periodic audits sustain compliance after authorization. Even with Authorization to Operate, regular assessments ensure ongoing compliance, particularly after major system changes, infrastructure updates, or control modifications. 3PAOs conduct annual assessments and evaluate significant changes to determine whether modifications affect security posture or require authorization updates.
3PAO vs Other Assessment Bodies — What Makes 3PAO Unique
3PAOs differ fundamentally from internal audits or self-assessments through mandatory independence, impartiality, and standardization. Internal security teams assess their own implementations—creating inherent conflicts of interest and lacking the objectivity external auditors provide. Self-assessments allow organizations to evaluate controls according to their own interpretation of requirements, without external validation of completeness or accuracy.
The A2LA assessment process involves rigorous evaluation of 3PAO technical competence and compliance with ISO/IEC 17020. This accreditation standard requires demonstration of impartiality, competence, and consistent operation—requirements not imposed on internal audit functions or consulting engagements. The accreditation process itself validates that 3PAOs maintain technical expertise across security frameworks, testing methodologies, and compliance requirements.
C3PAO distinction requires clarification: Certified Third-Party Assessment Organizations (C3PAOs) serve the Cybersecurity Maturity Model Certification (CMMC) program for defense contractors rather than FedRAMP for cloud providers. While acronyms appear similar, programs serve different regulatory frameworks—CMMC focuses on defense industrial base security, while FedRAMP addresses cloud service authorization for federal agencies. Organizations may hold both designations, but recognition for one program doesn't automatically transfer to the other.
Accreditation requirements distinguish legitimate 3PAOs from generic security consultants. A2LA accreditation under ISO/IEC 17020, combined with FedRAMP-specific technical competence requirements, ensures 3PAO assessments meet consistent quality standards. Ad-hoc audits conducted by non-accredited firms may provide value for internal risk management but don't satisfy FedRAMP authorization requirements or provide federal agency acceptance.
What This Means for Businesses Selling to Enterprise Clients
Cloud service providers offering SaaS, PaaS, IaaS, or other cloud-based services to government agencies face 3PAO assessment as a de facto market entry requirement. Federal procurement regulations increasingly mandate FedRAMP authorization for cloud solutions handling government data—making 3PAO assessment unavoidable for vendors pursuing this market segment. Security-conscious enterprises in regulated industries often adopt similar requirements, extending 3PAO relevance beyond government contracts.
- Cost, time, and effort planning requires realistic expectations: 3PAO assessments are rigorous, expensive, and time-intensive. Initial authorization typically spans six to twelve months from readiness assessment through final ATO—requiring substantial documentation development, control implementation, evidence collection, and potential remediation cycles. CSPs should factor assessment costs (often $100,000-$500,000+ depending on system complexity and baseline level) into product roadmaps and go-to-market planning. Organizations underestimating this investment frequently face delayed market entry or incomplete authorizations.
- Differentiation opportunity emerges for CSPs that complete FedRAMP authorization. Passing a 3PAO-based audit and obtaining authorization provides powerful trust signals to enterprise clients and partners. In competitive procurements, FedRAMP authorization demonstrates security commitment beyond marketing claims—validated by independent assessment against recognized standards. This certification particularly differentiates providers in markets where competitors lack equivalent validation.
- Ongoing commitment extends beyond initial certification. Security compliance isn't a one-time checkbox but requires sustained investment in continuous monitoring, annual assessments, change management, and control maintenance. Organizations treating FedRAMP as a project with a defined endpoint discover that sustaining authorization demands permanent operational changes—including dedicated compliance personnel, continuous evidence collection, and regular 3PAO reassessment. This ongoing requirement supports long-term trust building and genuine risk management rather than momentary compliance theater.
Common Misconceptions & Pitfalls

1) 3PAO ≠ internal audit or vendor self-assessment. Independence is mandatory—organizations cannot self-certify FedRAMP compliance or use internal teams for formal assessment. Federal agencies require 3PAO validation specifically because of the impartiality and expertise accreditation ensures. Vendors claiming "FedRAMP compliance" without 3PAO assessment misrepresent their security posture and authorization status.
2) Not all third-party auditors qualify as 3PAOs. Security consulting firms may offer compliance services, control assessments, or gap analyses without holding 3PAO accreditation. The list of FedRAMP recognized 3PAOs is maintained on the FedRAMP Marketplace—organizations should verify 3PAO status before engaging assessors for FedRAMP authorization. Using non-recognized assessors wastes resources on evaluations federal agencies won't accept.
3) Advisory and assessment conflicts create problematic situations when single firms provide both services. While 3PAOs may offer consulting services, they cannot advise on control implementation then independently assess those same controls for the same client. This dual relationship compromises the impartiality that makes 3PAO assessment valuable. Many providers separate advisory and assessment functions completely—using one 3PAO for readiness consulting and a different recognized organization for formal assessment.
4) Assessment ≠ automatic authorization. Completing 3PAO assessment doesn't guarantee Authorization to Operate. The assessment produces a Security Assessment Report documenting control effectiveness and identified risks—but federal agencies review this SAR before granting authorization. Significant findings may require remediation cycles, agency acceptance of risk, or additional compensating controls before authorization. Organizations assuming assessment completion equals market access face unexpected delays when authorization requires additional work.
Conclusion
Third-Party Assessment Organizations provide independent validation that cloud service providers implement effective security controls—not merely document aspirational policies. 3PAOs play a critical role in the authorization process by assessing the security of cloud service offerings, particularly within FedRAMP's standardized framework for federal cloud security. For CSPs targeting government agencies or security-conscious enterprises, 3PAO assessment represents mandatory validation rather than optional certification.
Organizations selling to government clients face 3PAO evaluation as an unavoidable requirement for market access. This assessment process demands substantial investment—typically six to twelve months and significant resources for documentation, control implementation, testing, and potential remediation. However, vendors completing this process gain differentiation through independently validated security posture, streamlined procurement across federal agencies via FedRAMP reciprocity, and demonstrated commitment to operational security beyond compliance theater.
The process demands effort and resources, but for vendors pursuing government contracts or security-sensitive enterprise relationships, 3PAO assessment isn't merely a compliance checkbox—it's strategic investment in credibility, market access, and verifiable security infrastructure that produces compliance as a natural outcome rather than a manufactured artifact.
FAQs
1) What is the difference between 3PAO and C3PAO?
A 3PAO (Third-Party Assessment Organization) performs security assessments for cloud service providers seeking FedRAMP authorization—evaluating controls against NIST 800-53 requirements for federal cloud services. A C3PAO (Certified Third-Party Assessment Organization) conducts assessments under the Cybersecurity Maturity Model Certification (CMMC) program for defense contractors in the defense industrial base. While both require accreditation and perform independent security evaluations, they serve distinct regulatory frameworks: FedRAMP for federal cloud procurement and CMMC for Department of Defense supply chain security. Organizations may hold both designations, but recognition for one program doesn't transfer to the other.
2) What is a 3rd party assessment?
A third-party assessment is an independent evaluation of an organization's security controls, documentation, and operational environment conducted by an accredited external entity. For cloud providers pursuing FedRAMP authorization, this assessment verifies compliance with standards defined under the Federal Information Security Modernization Act (FISMA) and Risk Management Framework (RMF). The independent assessor examines whether documented controls in the System Security Plan actually function as claimed—testing implementations, reviewing evidence, conducting vulnerability scans and penetration tests, and interviewing personnel. This external validation provides objective verification that internal self-assessments or vendor claims cannot match.
3) Who approves or recognizes 3PAOs?
The American Association for Laboratory Accreditation (A2LA) must perform initial assessment of 3PAOs and provide assessment recommendations to FedRAMP for approval. A2LA accredits 3PAOs under ISO/IEC 17020 standards with FedRAMP-specific technical competence requirements. After A2LA accreditation and FedRAMP approval, recognized 3PAOs appear on the official FedRAMP Marketplace—the authoritative registry of organizations eligible to conduct FedRAMP assessments. Cloud service providers should verify 3PAO status on the FedRAMP Marketplace before engaging assessors, as only recognized organizations can perform assessments that federal agencies will accept for authorization decisions.
4) Is Coalfire a 3PAO?
Organizations seeking to verify whether specific companies hold 3PAO recognition should consult the official FedRAMP Marketplace maintained by the FedRAMP Program Management Office. The marketplace provides the current, authoritative list of recognized 3PAOs eligible to conduct FedRAMP assessments. Because 3PAO status requires ongoing A2LA accreditation with periodic reassessment, and because organizations may gain or lose recognition based on compliance with accreditation requirements, the FedRAMP Marketplace represents the most reliable source for confirming current 3PAO status rather than relying on dated information or vendor claims.



.svg)
.svg)
.svg)