Most organizations still treat data breaches as hypothetical risks—something that happens to other companies—until the moment forensic investigators arrive to reconstruct how unauthorized access occurred. By then, the breach has already triggered notification obligations, regulatory scrutiny, and erosion of customer trust. For enterprises pursuing SOC 2 attestations, ISO 27001 certifications, or HIPAA compliance, the question "what is a data breach" carries direct legal and operational consequences that extend far beyond incident response protocols.Regulatory bodies track breach disclosure velocity more closely than ever. Over 3,100 data compromises were reported in the U.S. in 2025, affecting over 1.35 billion individuals. One in every two enterprises experienced at least one data breach in the past 12 months. What distinguishes organizations that maintain compliance posture from those facing regulatory penalties often comes down to how precisely they classify incidents and how rapidly they execute notification protocols.
This definition covers what constitutes a data breach under regulatory frameworks, how enterprises must interpret "unauthorized access" versus general security incidents, the specific types of sensitive information that trigger notification requirements, and the immediate operational steps required when containment begins.
What Is a Data Breach?
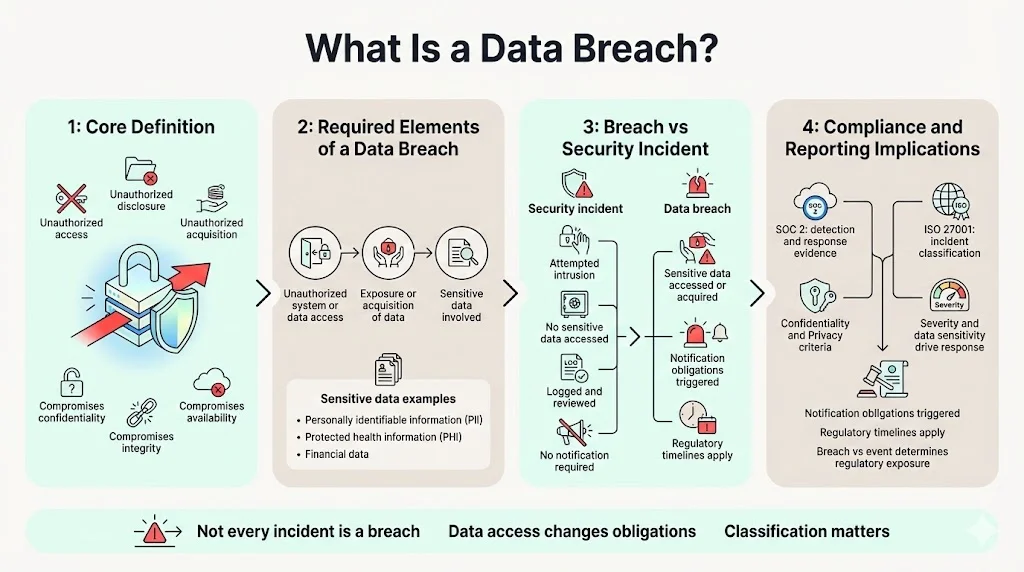
A data breach occurs when unauthorized parties gain access to, disclose, or acquire sensitive information in a manner that compromises confidentiality, integrity, or availability. This definition encompasses three necessary elements: unauthorized access to protected systems or data, the exposure or exfiltration of information, and the involvement of data categories defined as sensitive under applicable regulations.
The distinction between a breach and a general security incident lies in whether protected data was actually accessed or acquired. An attempted intrusion that fails to access sensitive information does not constitute a reportable breach under most regulatory frameworks. The moment unauthorized access to personally identifiable information (PII), protected health information (PHI), or financial data occurs—regardless of whether exfiltration is confirmed—notification obligations typically activate.
Organizations pursuing SOC 2 Type II attestations must document breach detection and response procedures as part of the Confidentiality and Privacy Trust Services Criteria. ISO 27001:2022 requires incident management processes that classify security events by severity and data sensitivity. The difference between a logged security event and a breach triggering formal notification often determines whether an organization faces regulatory scrutiny or merely documents an incident for continuous improvement purposes.
What Counts as a Data Breach in an Enterprise Environment
Regulatory agencies define sensitive information categories that trigger breach notification requirements. Understanding these classifications prevents the compliance gap between treating minor incidents as reportable breaches and failing to recognize actual notification obligations.
Personally Identifiable Information (PII) includes names combined with Social Security numbers, driver's license numbers, financial account credentials, or biometric data. Most state breach notification laws specifically enumerate these combinations as protected data requiring disclosure when compromised.
Financial and payment data encompasses credit card numbers, bank account credentials, and transaction histories. Payment Card Industry Data Security Standard (PCI DSS) compliance requires organizations to report breaches involving cardholder data to acquiring banks and card brands within specific timeframes—typically 72 hours following initial discovery.
Health and employee records fall under HIPAA regulations when they contain electronic protected health information (ePHI). Employee records containing health insurance details, background check results, or medical accommodations documentation trigger the same notification protocols as customer health data.
Customer credentials and access tokens represent a category frequently misclassified by organizations. Authentication credentials—including passwords, API keys, OAuth tokens, and session identifiers—constitute sensitive information under most frameworks because they enable unauthorized account access. Even hashed credentials qualify as compromised data when organizations cannot guarantee cryptographic strength prevents reversal.
Intellectual property and internal business data may not trigger statutory breach notification requirements, but SEC disclosure rules require public companies to report material cybersecurity incidents. Trade secrets, product designs, and strategic planning documents accessed by unauthorized parties often meet materiality thresholds that mandate shareholder notification.
The Federal Trade Commission evaluates breach notification based on whether compromised information creates "significant risk of harm" to individuals. This standard encompasses identity theft risk, financial fraud potential, and reputational damage—not just confirmed malicious use of stolen data.
Common Causes of Data Breaches
External Threats
Credential abuse remains the most common vector of data breaches in 2025, accounting for 22%. Attackers obtain credentials through previous breaches, phishing campaigns, or credential-stuffing attacks that exploit password reuse across platforms.
Ransomware incidents account for a substantial portion of breaches reported to regulatory agencies. Ransomware is linked to 75% of system-intrusion breaches. These attacks frequently involve data exfiltration before encryption—a dual-extortion tactic that transforms what organizations might classify as an availability incident into a full breach requiring notification.
Exploited vulnerabilities provide initial access vectors. Organizations that maintain unpatched systems face extended exposure windows. Malware deployment following successful exploitation allows attackers to establish persistent access and move laterally through networks before detection.
Phishing remains a foundational attack method. Infostealers delivered via phishing emails per week increased by 84% year-over-year. These campaigns target credentials, session tokens, and authentication factors that enable subsequent unauthorized access to protected systems.
Internal and Operational Failures
Malicious insider attacks resulted in the highest average breach costs among initial threat vectors, costing an average of $4.92 million in 2025. Employees with legitimate access credentials who intentionally exfiltrate data or provide unauthorized third parties with system access create breaches indistinguishable from external attacks regarding notification requirements.
Breaches caused by insider error cost an average of $3.62 million in 2025. Accidental data exposure—misconfigured cloud storage buckets, emails sent to incorrect recipients, or improperly disposed physical media—triggers the same notification obligations as malicious attacks when sensitive information becomes accessible to unauthorized parties.
Roughly 46% of breaches originated in cloud-hosted or hybrid environments. Misconfigured infrastructure-as-a-service platforms, inadequate access controls on software-as-a-service applications, and insufficient monitoring of API endpoints create exposure that organizations discover only after data appears on public repositories or underground forums.
Lost or stolen devices containing unencrypted sensitive information constitute breaches under most state notification laws. Laptop theft, misplaced backup drives, or decommissioned equipment improperly sanitized all trigger notification requirements when encryption protocols were not implemented.
Poor access controls—excessive privileges, inadequate segmentation, absence of least-privilege principles—amplify breach scope once initial access occurs. Organizations that grant broad system access discover post-incident that attackers traversed environments accessing databases and file shares far beyond the initial compromise point.
Data Breach vs. Data Leak vs. Security Incident
Precise terminology matters for regulatory reporting and stakeholder communication. Organizations that misclassify incidents face delayed notifications, improper evidence collection, and regulatory penalties for failing to execute required protocols.
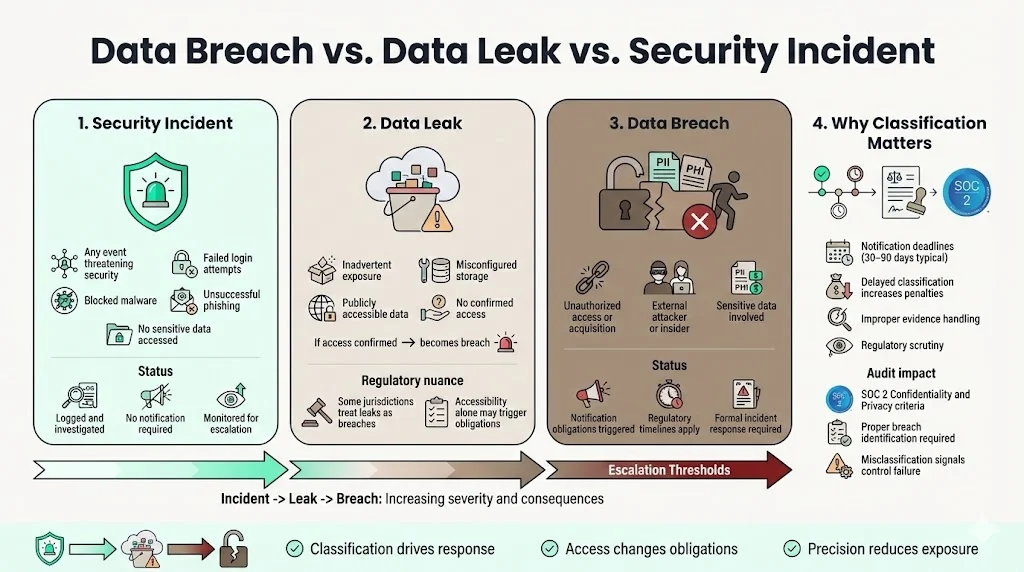
A data breach involves unauthorized access to or acquisition of sensitive information. The unauthorized element is critical—whether access occurred through external attack, malicious insider action, or accidental exposure, the result is data compromise requiring notification when statutory thresholds are met.
A data leak typically describes inadvertent exposure without confirmed unauthorized access. A publicly accessible cloud storage bucket containing customer records constitutes a data leak. The moment evidence confirms external parties accessed that bucket, the incident reclassifies as a breach. Some jurisdictions make no legal distinction between leaks and breaches—if protected data becomes accessible to unauthorized parties, notification requirements activate regardless of terminology.
A security incident is the broader category encompassing any event that threatens information security. Failed login attempts, malware detected before execution, or unsuccessful phishing campaigns are security incidents. They become breaches only when sensitive data is accessed or acquired by unauthorized parties.
Misclassification creates legal exposure. Organizations that classify actual breaches as minor security incidents delay required notifications. State breach notification laws impose specific timeframes—commonly 30 to 90 days following discovery—for notifying affected individuals and regulatory agencies. Treating a breach as a routine security incident postpones investigation and notification processes, potentially extending regulatory timeframes and increasing penalties.
The regulatory consequence of proper classification extends to audit findings. SOC 2 auditors evaluate whether organizations correctly identified breaches and executed documented incident response procedures. Misclassifying a breach as a leak or general security incident demonstrates insufficient control effectiveness for the Confidentiality and Privacy criteria.
Why Data Breaches Are High-Risk Events for Enterprises
Data breaches trigger cascading consequences that extend far beyond immediate incident response costs. In the United States, the average cost rose to USD 10.22 million, making breach financial impact a material business risk requiring C-suite attention.
Legal exposure begins when notification obligations activate. Organizations that fail to report breaches within statutory timeframes face regulatory penalties from state attorneys general, the Federal Trade Commission, and industry-specific regulators. Healthcare organizations failing to report HIPAA breaches within 60 days face Office for Civil Rights investigations that commonly result in corrective action plans and financial penalties.
Contractual impact with enterprise customers creates immediate revenue risk. Business associate agreements, data processing addendums, and master service agreements typically require breach notification within 24 to 72 hours. Customers frequently invoke termination clauses following breaches, particularly when root cause analysis reveals control deficiencies that contradict SOC 2 or ISO 27001 certifications provided during procurement.
Identity theft risks for customers and employees generate long-tail liability. An estimated 166 million individuals were affected by data compromises in the first half of 2025. Organizations face class-action litigation when compromised credentials enable account takeover, financial fraud, or synthetic identity creation using stolen PII.
Loss of trust erodes sales pipeline velocity. Enterprise buyers conducting vendor security assessments discover breach history through public disclosures and media coverage. Organizations pursuing compliance certifications to close deals find that recent breaches extend sales cycles 3 to 6 months while prospects conduct enhanced due diligence and demand additional security controls before contract execution.
Organizations took an average of 197 days to identify and 74 days to contain a breach in 2025. This 271-day window from initial compromise to containment represents sustained operational disruption, forensic investigation expenses, and remediation costs that divert engineering resources from product development to security infrastructure hardening.
Data Breach Laws and Notification Requirements
All 50 U.S. states maintain data breach notification statutes with varying definitions of personal information, notification timeframes, and regulatory agency reporting requirements. This fragmented landscape creates compliance complexity for organizations operating nationally or serving customers across multiple jurisdictions.
State-level notification rules commonly require organizations to notify affected residents within 30 to 90 days following breach discovery. "Discovery" typically means when the organization knew or reasonably should have known that unauthorized access occurred—not when forensic investigation concludes. Delayed discovery due to insufficient monitoring does not extend notification deadlines under most statutes.
Federal guidance from the Federal Trade Commission establishes baseline expectations for reasonable data security practices. The FTC Act Section 5 prohibits unfair or deceptive practices, which the Commission interprets to include failure to implement reasonable security measures. Organizations experiencing breaches due to known vulnerabilities, lack of encryption, or inadequate access controls face FTC enforcement actions requiring comprehensive security overhauls and extended compliance monitoring.
The Cybersecurity and Infrastructure Security Agency provides breach response frameworks emphasizing evidence preservation, stakeholder notification, and coordination with law enforcement. CISA guidance recommends organizations notify federal authorities through the agency's reporting portal when breaches involve critical infrastructure or may indicate nation-state activity.
Industry-specific rules layer additional requirements onto state and federal baselines. HIPAA-covered entities and business associates must report breaches affecting 500 or more individuals to the Department of Health and Human Services within 60 days. Financial institutions face notification requirements under the Gramm-Leach-Bliley Act and guidance from federal banking regulators. Educational institutions handling student records must comply with FERPA notification protocols when unauthorized parties access education records.
International exposure affects enterprises with European customers or employees. The General Data Protection Regulation (GDPR) requires organizations to notify supervisory authorities within 72 hours of becoming aware of breaches involving EU residents' personal data. This timeline is substantially shorter than most U.S. state requirements and applies regardless of where the breached organization is headquartered.
What Enterprises Should Do Immediately After a Data Breach
The first 72 hours following breach discovery determine whether organizations maintain regulatory compliance, preserve forensic evidence, and contain damage before additional data exposure occurs.
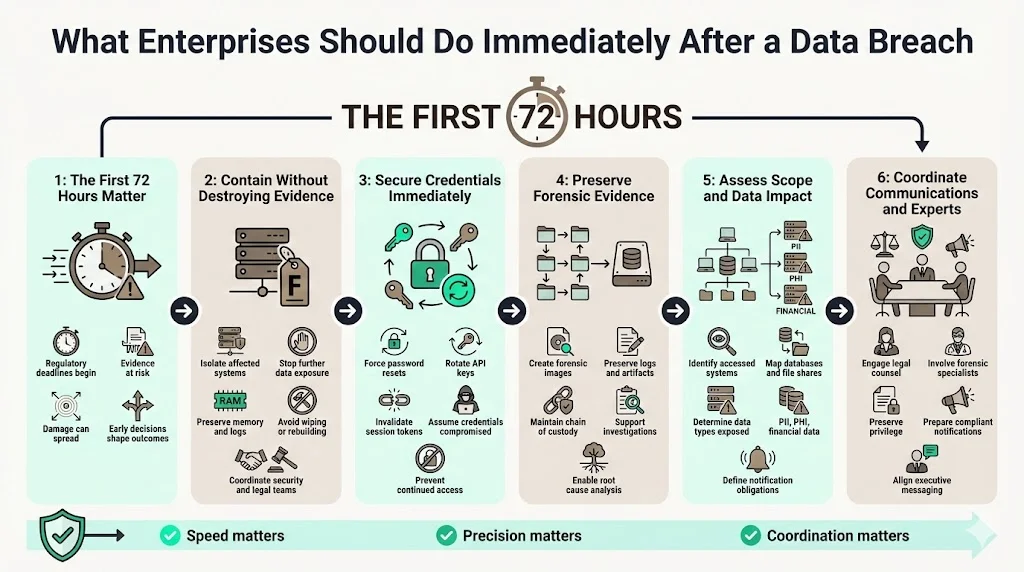
Contain the incident by isolating affected systems without destroying evidence. Disconnecting compromised servers from networks prevents further data exfiltration, but forensic investigators require system memory contents and active network connections to reconstruct attacker activity. Coordination between security operations and legal teams ensures containment actions preserve evidence required for regulatory investigations and potential litigation.
Secure affected systems and credentials through forced password resets, API key rotation, and session token invalidation. Organizations that delay credential rotation discover weeks later that attackers retained access through valid authentication mechanisms despite containment efforts. Assume all credentials potentially accessible from compromised systems are compromised until cryptographic analysis proves otherwise.
Preserve evidence by creating forensic images of affected systems before remediation begins. Chain-of-custody documentation for all evidence ensures admissibility in legal proceedings and regulatory investigations. Many organizations discover during FTC or state attorney general investigations that insufficient evidence preservation prevents definitive root cause determination—a deficiency that regulators interpret as inadequate security practices extending beyond the breach itself.
Assess scope and data types by identifying which databases, file shares, and applications unauthorized parties accessed. This assessment determines notification obligations by mapping compromised systems to sensitive information categories. Organizations that skip comprehensive scope assessment notify affected individuals months after initial disclosure when forensic analysis reveals additional data exposure—a second notification round that amplifies reputational damage and regulatory scrutiny.
Prepare internal and external communications by coordinating legal, security, marketing, and executive leadership input. Notification letters must meet statutory content requirements specifying what information was compromised, when unauthorized access occurred, and what steps organizations are taking to prevent recurrence. Vague or minimizing language in breach notifications invites regulatory criticism and media attention that extends negative coverage.
Involve legal, forensic, and security teams immediately upon breach discovery. Outside counsel often coordinates forensic investigations under attorney-client privilege, protecting investigation findings from disclosure in subsequent litigation. Third-party incident response firms provide forensic capabilities and investigation experience that internal teams typically lack. Delayed engagement of specialized resources extends containment timelines and increases total breach costs substantially.
Preventing Data Breaches in Enterprise Organizations
Organizations that maintain continuous audit readiness and implement defense-in-depth security architectures substantially reduce breach likelihood and contain incidents faster when compromise occurs.
Risk assessments and regular audits identify control gaps before attackers exploit them. ISO 27001 risk assessment methodologies require organizations to evaluate information assets, identify threats and vulnerabilities, and implement controls proportionate to risk. SOC 2 readiness assessments conducted quarterly ensure continuous control effectiveness rather than annual scrambles to collect evidence before audit observation periods begin.
Access control and least-privilege practices limit breach scope by ensuring users and service accounts possess only permissions required for defined job functions. Role-based access control (RBAC) implementations combined with regular access reviews identify privilege creep that accumulates as employees change roles. Organizations implementing just-in-time privileged access reduce standing administrative credentials that represent high-value targets for attackers.
Employee security awareness transforms workforce members from vulnerability to defensive layer. Effective programs move beyond annual training videos to include monthly phishing simulations, role-specific security education, and incident reporting mechanisms that employees actually use. 60% of all breaches include the human element, making investment in human-factor controls as critical as technical security infrastructure.
Vendor and third-party risk management addresses the reality that enterprise breach vectors increasingly originate from suppliers, service providers, and technology partners. 30% of breaches involved third-party vendors, twice the rate reported last year. Comprehensive vendor risk management programs require security questionnaires during procurement, annual SOC 2 review for critical vendors, and contractual requirements for breach notification within defined timeframes.
Incident response planning and testing ensures organizations execute coordinated response procedures rather than improvising under pressure. Tabletop exercises simulating ransomware attacks, data exfiltration scenarios, and insider threats identify gaps in communication protocols, decision-making authority, and technical response capabilities. Organizations that test incident response plans quarterly contain breaches substantially faster than those treating plans as compliance artifacts never exercised until actual incidents occur.
Conclusion
A data breach is unauthorized access to, acquisition of, or disclosure of sensitive information creating notification obligations under applicable regulatory frameworks. The definition's precision matters because classification errors delay required notifications, compromise forensic investigations, and demonstrate control deficiencies during compliance audits.
Enterprise organizations must understand that breach scope encompasses not only external attacks but also insider actions, operational failures, and vendor compromises. The distinction between security incidents and reportable breaches determines whether organizations execute notification protocols within statutory timeframes or face regulatory penalties for delayed disclosure.
Breach prevention and rapid response capabilities directly correlate with enterprise customer trust. Organizations demonstrating mature security posture through certifications like SOC 2 Type II and ISO 27001 still face procurement delays when prospects discover breach history. Security infrastructure that produces compliance as a natural outcome—continuous monitoring, automated control testing, evidence-based risk management—creates operational resilience that prevents breaches rather than merely documenting security practices that look effective on paper.
FAQs
1) What really counts as a data breach?
A data breach occurs when unauthorized parties access, acquire, or disclose sensitive information defined under applicable regulations. The breach threshold activates when protected data—PII, PHI, financial credentials, or other categories specified in state breach notification laws—is accessed by individuals or systems lacking authorization. Intent is irrelevant: accidental exposure through misconfiguration triggers the same notification requirements as malicious attack when sensitive information becomes accessible to unauthorized parties.
2) Are internal mistakes considered data breaches?
Yes. Accidental data exposure through employee error—misconfigured systems, misdirected emails, improper access controls—constitutes a breach when sensitive information becomes accessible to unauthorized parties. Notification requirements activate based on unauthorized access occurrence, not attacker intent or malicious purpose. Organizations must execute identical notification protocols for accidental exposure as for deliberate attacks when statutory thresholds are met.
3) How is a data breach different from a data leak?
A data breach involves confirmed unauthorized access to or acquisition of sensitive information. A data leak typically describes inadvertent exposure without confirmed access—for example, a publicly accessible database that may or may not have been accessed by external parties. Many jurisdictions make no legal distinction: if protected data becomes accessible to unauthorized parties, notification requirements activate regardless of whether the incident is labeled breach or leak. Organizations pursuing precision distinguish leaks (potential exposure) from breaches (confirmed access), but regulatory frameworks focus on unauthorized accessibility rather than terminology.
4) What laws require breach notification?
All 50 U.S. states maintain data breach notification statutes requiring organizations to notify affected individuals within defined timeframes—commonly 30 to 90 days following discovery. Federal regulations layer additional requirements: HIPAA mandates 60-day notification for healthcare breaches affecting 500 or more individuals; GLBA governs financial institutions; and the FTC enforces baseline security standards through Section 5 authority. International regulations including GDPR require notification to supervisory authorities within 72 hours for breaches involving EU residents' personal data. Organizations operating across jurisdictions must comply with all applicable requirements, which often means adhering to the most stringent timeline.
5) What should enterprises do immediately after a breach?
Contain the incident while preserving forensic evidence, secure all credentials potentially accessible from compromised systems, assess which sensitive data categories were accessed, prepare legally compliant notifications, and engage legal counsel plus incident response specialists within the first 24 hours. Organizations that delay containment, credential rotation, or scope assessment discover weeks later that attackers maintained access or that additional data was compromised—revelations requiring supplemental notifications that amplify regulatory scrutiny and stakeholder concern. The initial 72-hour response window determines whether organizations meet notification deadlines and demonstrate control effectiveness during subsequent investigations.



.svg)
.svg)
.svg)