Most organizations treat vendor risk assessment as a procurement checkpoint rather than a security discipline. This creates a fundamental gap between compliance documentation and actual third-party risk posture—a gap that becomes apparent when breaches occur through vendor relationships. A breach in any link of that chain can become your problem.
If you're building or selling solutions to enterprise clients, understanding the Standardized Information Gathering (SIG) questionnaire is non-negotiable. Enterprise procurement teams, compliance officers, and partner-risk professionals expect vendors to navigate this framework with fluency. This article provides the technical and strategic context you need to position your security posture appropriately and reduce friction in enterprise sales cycles.
What Is a SIG?
The Standardized Information Gathering (SIG) questionnaire is an industry-leading framework for effective third-party risk assessments. The SIG questionnaire was created by Shared Assessments, which provides best practices, solutions, and tools helping third-party risk management teams create an environment of assurance for outsourcers and their vendors.
Shared Assessments is a membership-based organization of over 300 industry members across various industries, serving third-party risk professionals since 2005 with best practices, certifications, solutions, and third-party risk products. The term "shared assessment" was born out of the need to create efficiencies when assessing vendors—complete once and share many times since outsourcers use the same vendors and need the same security questions answered.
The framework was designed to address a specific operational problem: enterprises were spending hundreds of hours sending custom questionnaires to vendors, while vendors were completing dozens of variations of identical questions for different clients. This inefficiency created both resource drain and inconsistent risk visibility.
Scope and structure
The SIG uses a robust compilation of questions to gather pertinent information across a spectrum of 21 risk control areas within a service provider's environment. These domains include access control, application security, cloud hosting security, data classification, encryption, incident response, physical security, privacy, third-party management, and operational resilience.
The SIG is updated every year to keep up with the ever-changing risk environment and priorities. The SIG aligns with the most updated domestic and international regulatory guidance and industry standards for risk management.
Two versions of the SIG Questionnaire are offered: the SIG Core and the SIG Lite. The SIG Lite 2025 has 128 questions. The SIG Lite Questionnaire provides a broad higher-level understanding of a third party's internal information security controls, is for vendors that need basic levels of assessment due diligence, and can also be used as a preliminary assessment before a more detailed review.
The SIG Core Questionnaire is meant to assess third parties that store or manage highly sensitive or regulated information such as personal information or other sensitive data, provides a deeper level of understanding about how a third party secures information and services, and the SIG Core 2025 has 627 questions. The full SIG – also called the SIG Detail – has 1936 Questions.
Enterprises configure SIG questionnaires based on vendor risk profile, data sensitivity, regulatory requirements, and control domains relevant to the engagement. Organizations can generate SIGs based on scope, regulation, control family or risk domain.
Why the term matters for enterprise-selling companies
For companies selling into enterprise accounts—particularly in financial services, healthcare, technology infrastructure, or any regulated vertical—receiving a SIG questionnaire is a standard milestone in the procurement lifecycle. Understanding what the SIG is, how it's structured, and what level of detail enterprises expect signals operational maturity.
When your prospect's vendor-risk team asks if you've completed a SIG before, they're evaluating two things: your actual security controls and your readiness to navigate enterprise compliance expectations. Demonstrating familiarity with the SIG framework positions you as a sophisticated vendor rather than a company requiring hand-holding through due diligence.
Use Cases: How Enterprises and Vendors Use SIG
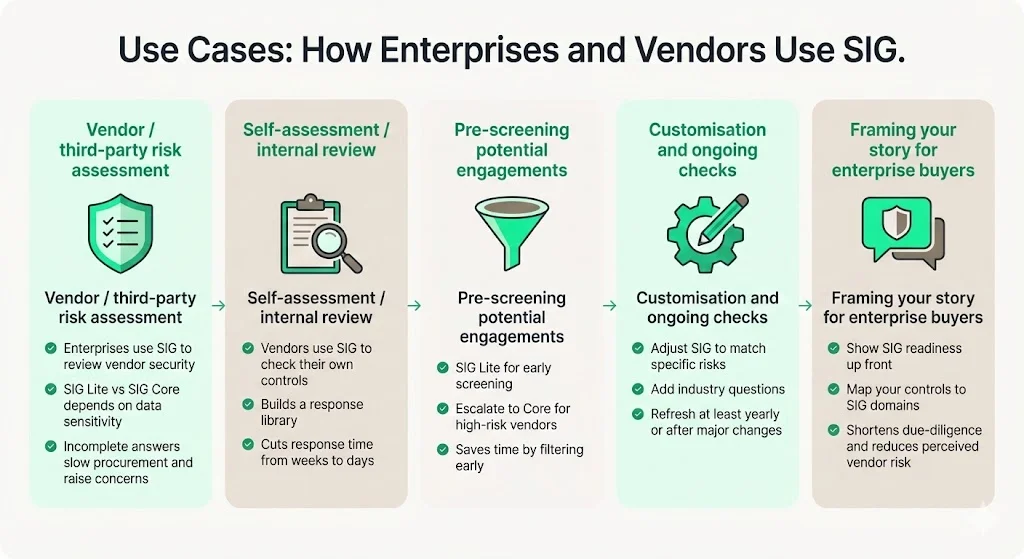
Vendor / third-party risk assessment
The primary use case of the SIG questionnaire is the assessment of vendors and other third parties before working with them. Enterprises use the SIG to evaluate whether a vendor's security posture aligns with their risk tolerance and regulatory obligations before establishing contractual relationships.
For vendors, receiving a SIG questionnaire means you're undergoing formal due diligence. The rigor of the questionnaire—SIG Lite versus SIG Core—indicates how the enterprise categorizes your risk profile. A cloud hosting provider handling protected health information (PHI) will receive SIG Core; a marketing analytics vendor with limited data access might receive SIG Lite.
This assessment becomes part of the enterprise's decision-making process for vendor selection. Incomplete, inconsistent, or delayed responses create procurement friction and raise red flags about operational discipline.
Self-assessment / internal risk assessment
The SIG questionnaire can be an excellent tool for internal security reviews and audits, especially the SIG Core version, letting organizations assess all relevant security controls and risk management practices, minimize exposure to threats, and be ready to fill out security questionnaires they receive.
Vendors selling to multiple enterprise clients should conduct internal SIG assessments proactively. This approach accomplishes three objectives: it identifies control gaps before external scrutiny, it creates a response library for future questionnaires, and it demonstrates to prospects that you've invested in audit readiness rather than treating vendor assessments reactively.
Organizations implementing this practice typically reduce SIG response time from 4-6 weeks to 1-2 weeks—a competitive advantage in enterprise sales cycles where procurement velocity matters.
Pre-screening potential engagements
Enterprises often deploy SIG Lite early in the vendor evaluation process to filter candidates before investing resources in deeper assessment. This functions as a technical pre-qualification alongside commercial and financial due diligence.
For high-risk vendor relationships—those involving access to production systems, sensitive data processing, or critical infrastructure—enterprises escalate to SIG Core after initial approval. This tiered approach allows procurement teams to allocate assessment resources proportionally to vendor risk.
Customisation and ongoing monitoring
Some organizations use the SIG as a starting point, customizing the SIG to fit their specific assessment needs. Enterprises may append industry-specific questions, emphasize particular control families relevant to their threat model, or tailor questionnaires based on the vendor's access scope.
Once vendors are onboarded, SIG assessments don't terminate. The SIG questionnaire is updated at least annually to accommodate changing regulations, emerging threats, and new frameworks and standards. Enterprises typically require vendors to update SIG responses annually or when material changes occur in systems, personnel, or security architecture.
For companies selling to enterprises: framing your story
When engaging with enterprise compliance, procurement, or partner-risk teams, referencing your SIG readiness creates strategic positioning advantages. You can articulate how your platform or service implements controls that map directly to SIG domains—demonstrating alignment with their vendor risk management (VRM) program before they ask.
This positioning accelerates the due-diligence phase of the decision-making process. Rather than waiting for the enterprise to issue a questionnaire and then scrambling to gather evidence, you proactively demonstrate that you've anticipated their requirements. This reduces the enterprise's perception of vendor risk and differentiates you from competitors treating compliance as an afterthought.
Compliance Relevance & Why It Matters

1) Mapping to regulatory frameworks
The SIG aligns with the most updated domestic and international regulatory guidance and industry standards for risk management. The questionnaire maps to ISO 27001, NIST 800-53, GDPR, PCI DSS, HIPAA, SOC 2, and dozens of other frameworks. This design allows enterprises to conduct a single vendor assessment that satisfies multiple compliance obligations simultaneously.
For enterprises operating in regulated industries, vendor risk represents direct regulatory exposure. Financial institutions face examination scrutiny on third-party risk management programs. Healthcare organizations must ensure business associates maintain appropriate PHI safeguards. Technology companies processing EU resident data must verify that vendors provide adequate data protection.
The SIG provides standardized evidence that enterprises can present to auditors and regulators demonstrating systematic vendor due diligence.
2) Demonstrating due diligence
Regulatory frameworks increasingly hold organizations accountable for vendor-introduced risk. Having completed SIG assessments—with documented follow-up on identified gaps—demonstrates that the enterprise has exercised reasonable care in vendor selection and monitoring.
For vendors, providing thorough SIG responses with supporting evidence shows you're prepared for compliance scrutiny. This reduces friction in enterprise sales by eliminating concerns that onboarding your service will create regulatory risk for the buyer.
Enterprises document their vendor's controls through SIG responses, creating an audit trail that demonstrates risk mitigation efforts. This documentation becomes critical during regulatory examinations, SOC 2 audits, or ISO 27001 surveillance assessments where auditors verify third-party risk management processes.
3) Risk management, audit trails & transparency
The SIG's comprehensive scope across access control, application security, cloud hosting, operational resilience, and privacy means enterprises can evaluate vendor risk holistically rather than in isolated domains. This breadth creates transparency into how vendors actually implement security—not just what they claim in marketing materials.
Failing to conduct adequate vendor risk assessment—or accepting vendors who cannot demonstrate appropriate controls—creates both operational and regulatory exposure. Breaches originating from vendor relationships have resulted in regulatory penalties, contractual liability, and reputational damage that often exceeds the direct incident costs.
4) Implications for companies selling to enterprise clients
Enterprise procurement processes increasingly include mandatory vendor risk assessments. Being SIG-ready reduces delays in the decision-making process that can extend sales cycles by months.
For enterprises managing vendor portfolios across different risk profiles, SIG responses help categorize vendors appropriately. Your ability to complete a comprehensive SIG positions you favorably in their vendor mix—demonstrating you meet the security standards required for sensitive engagements.
This also touches enterprise operational risk strategy: vendor risk management represents an investment in operational resilience. Enterprises evaluate whether vendors contribute to or detract from their overall security posture. SIG readiness signals you understand this dynamic and have invested in controls that support—rather than undermine—their security goals.
Practical Advice for Vendors/Enterprise-Selling Companies
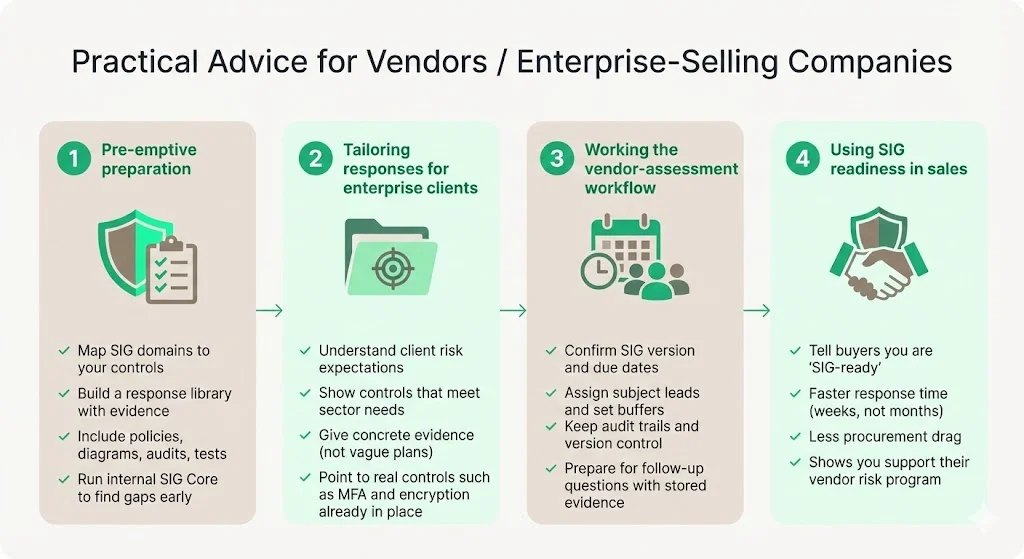
1) Pre-emptive preparation
Identify the typical domains covered in SIG assessments and map them to your existing controls. Build documentation for access management policies, encryption standards, incident response procedures, business continuity plans, data classification practices, and vendor management processes before you're asked.
Create a response library containing standard answers to common SIG questions. This library should include not just responses but supporting evidence: policy documents, architecture diagrams, audit reports, penetration test results, and certification attestations.
Conduct an internal SIG assessment using SIG Core—even if you expect most clients will issue SIG Lite. This exercise identifies gaps before external scrutiny and provides time for remediation rather than discovering deficiencies during active procurement cycles.
2) Tailoring your responses to enterprise clients
Understand your client's risk appetite and vendor risk policy before completing their SIG questionnaire. A financial institution will have different risk tolerance than a technology startup; adjust the depth and formality of responses accordingly.
Demonstrate how your controls support their specific risk assessment needs and compliance obligations. If you're selling to healthcare organizations, emphasize HIPAA-aligned controls. If your client operates in Europe, highlight GDPR compliance measures.
Provide concrete evidence rather than aspirational statements. "We plan to implement multi-factor authentication" raises concerns; "We enforce MFA across all administrative access with hardware token requirements documented in our access control policy" demonstrates operational discipline.
3) Working the vendor-assessment workflow
When you receive a SIG questionnaire, scope the version immediately—Core, Lite, or custom. Clarify due dates and understand dependencies: you'll likely need input from multiple teams including infrastructure, security, legal, and operations.
Assign subject matter experts to specific domains and establish internal deadlines that precede the client deadline by at least one week. This buffer allows for quality review and prevents last-minute submissions that appear rushed or incomplete.
Maintain audit trails and version control throughout the response process. Enterprises often request clarifications or follow-up evidence; being able to reference exactly what was submitted and when prevents confusion and demonstrates operational maturity.
4) Leveraging SIG readiness in your sales message
Position yourself as "SIG-ready" in enterprise sales conversations. You've invested in preparing comprehensive questionnaire responses, you can deliver them within 2-3 weeks rather than 6-8 weeks, and you've already mapped your controls to common compliance frameworks.
Use your SIG preparedness as a competitive differentiator. Reduced procurement friction translates to faster time-to-contract—often 60-90 days faster than competitors requiring extensive back-and-forth on security questions.
Highlight how enterprise clients can trust you to align with their vendor risk and third-party compliance frameworks. Reference your familiarity with SIG structure, your experience completing assessments for similar organizations, and your documented security controls that satisfy SIG requirements.
Pitfalls & what to avoid:
SIG Core assessments require significant resource investment—often 80-120 hours for first-time completion depending on organizational size and control maturity. Underestimating this effort leads to missed deadlines and incomplete responses that damage credibility.
Providing inconsistent responses across different sections of the questionnaire raises red flags. If your access control responses reference annual security training but your HR section indicates training occurs quarterly, enterprises question the reliability of your entire submission.
Treating the SIG as a compliance checkbox rather than an opportunity to improve actual controls is a strategic error. Enterprises increasingly conduct validation assessments—onsite reviews, control testing, or third-party attestations—that verify questionnaire responses. Misrepresenting your security posture creates contractual and reputational risk.
Bringing It Together: SIG in the Broader Vendor Risk Ecosystem
The SIG is central to the vendor risk management lifecycle: profiling → assessment (SIG) → contracting → monitoring → reassessment. Initial risk profiling determines if a vendor receives SIG Lite or Core, informing contract terms on security, insurance, and audits. Post-onboarding, continuous assessment and updated SIG responses maintain security posture.
SIG compliance is an ongoing discipline, requiring continuous investment in security infrastructure, training, and process improvement. Vendors often encounter SIG requirements late in procurement, causing delays. Understanding the SIG framework provides a strategic advantage.
Being SIG-ready elevates credibility, demonstrates maturity, and differentiates proactive vendors from reactive competitors. Proactive SIG preparation reduces procurement friction, positioning vendors as low-risk partners amidst increasing regulatory scrutiny. For enterprises, SIG readiness is a competitive imperative. Prepare early, maintain controls, and leverage preparedness as a differentiator.
FAQs
Q1: What is the difference between SIG Core and SIG Lite?
SIG Lite 2025 has 128 questions while SIG Core 2025 has 627 questions. SIG Core provides comprehensive assessment across all risk domains for high-risk vendors handling sensitive or regulated data. SIG Lite offers a streamlined evaluation suitable for initial assessments or lower-risk vendor relationships.
Q2: Who typically issues a SIG questionnaire?
An enterprise organization's vendor-risk, compliance, or procurement team issues SIG questionnaires to assess third-party vendors during onboarding or periodic reviews. Some vendors also complete SIG assessments internally as self-evaluation exercises to prepare for external requests.
Q3: Do I need to complete a SIG questionnaire if I'm a small vendor?
It depends on your client's risk classification methodology and the sensitivity of data or systems you'll access. Smaller vendors with limited data exposure might receive SIG Lite or simplified custom questionnaires. However, preparing for a comprehensive SIG Core assessment eliminates surprises and demonstrates security maturity regardless of company size.
Q4: How often should a SIG questionnaire be updated or completed?
The SIG questionnaire is updated at least annually to accommodate changing regulations, emerging threats, and new frameworks and standards. Enterprise clients typically require vendors to update responses annually or when significant changes occur in systems, personnel, security architecture, or regulatory environment.
Q5: Can the SIG questionnaire help meet compliance frameworks like ISO or NIST?
The SIG aligns with the most updated domestic and international regulatory guidance and industry standards for risk management. The questionnaire maps to ISO 27001, NIST 800-53, GDPR, PCI DSS, HIPAA, and other frameworks, allowing one vendor assessment to support multiple compliance objectives simultaneously.
Q6: What should a vendor do if they identify gaps while completing the SIG?
Document the gaps transparently, indicate planned remediation with specific timelines, provide interim compensating controls where applicable, and communicate proactively with the enterprise client about scope and risk. Demonstrating awareness of gaps with concrete remediation plans builds more trust than claiming complete compliance when controls are incomplete.



.svg)
.svg)
.svg)