Most organizations treat cybersecurity as a collection of tools and vendor relationships. This approach creates a fundamental gap between security spending and actual risk reduction—a gap that becomes apparent when enterprise buyers ask about your security program during procurement reviews.
Large enterprise buyers no longer evaluate vendors based solely on product capabilities. They assess security posture through structured frameworks, particularly the NIST Cybersecurity Framework (CSF). When a Fortune 500 procurement team asks about your CSF alignment during vendor risk assessment, they're testing whether you manage cyber risk systematically or reactively.
In cybersecurity, CSF refers to a structured approach for managing and communicating cyber risk using outcome-based functions rather than prescriptive technical requirements. The NIST Cybersecurity Framework is the most widely adopted CSF model, providing a common language that bridges technical security operations and business risk management.
This article explains what CSF means in cybersecurity, why enterprise-focused organizations depend on frameworks like NIST CSF, and how CSF alignment strengthens data protection standards, regulatory compliance, and vendor trust relationships.
What Is CSF in Cyber Security?
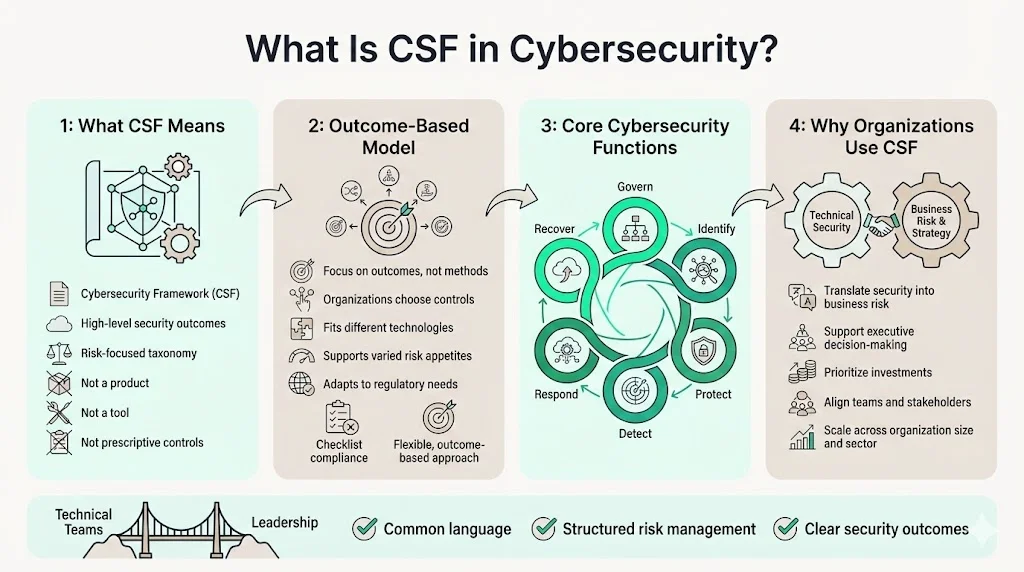
CSF Meaning in a Cybersecurity ContextA Cybersecurity Framework (CSF) is a taxonomy of high-level cybersecurity outcomes used to understand, assess, prioritize, and communicate cybersecurity efforts. Unlike security products or prescriptive technical controls, CSF describes desirable outcomes an organization can achieve without prescribing how to achieve them.
CSF operates as an outcome-based model rather than a checklist. Organizations define what good cybersecurity looks like for their specific risk environment, then implement controls that produce those outcomes. This approach accommodates different technologies, risk appetites, and compliance obligations without forcing uniform technical requirements across diverse enterprises.
The framework structure enables organizations to manage cyber risk systematically by establishing governance, identifying assets and threats, implementing protective controls, detecting incidents, responding effectively, and recovering operations. Any organization—regardless of size, sector, or maturity—can use CSF to translate technical security operations into business risk language that executive leadership and boards understand.
Origins of the NIST Cybersecurity Framework
NIST first released the CSF in 2014 following a presidential Executive Order to address growing cyber threats against critical infrastructure sectors. The framework was created to help private sector organizations develop a roadmap for critical infrastructure cybersecurity, initially targeting utilities, healthcare systems, financial institutions, and other sectors where cyber incidents could cause cascading physical or economic consequences.
Version 1.0 of the framework was published in 2014, primarily targeting operators of critical infrastructure. However, organizations outside those designated sectors recognized the framework's value for structuring security programs and communicating risk to stakeholders. CSF 2.0 now explicitly aims to help all organizations—not just those in critical infrastructure—manage and reduce risks.
The framework evolved from voluntary guidance for regulated sectors into a de facto standard for enterprise security programs. Developed in 2014 by the U.S. National Institute of Standards and Technology, cybersecurity professionals and organizations around the world have adopted the framework, establishing a shared vocabulary for cyber risk management across industries and geographies.
Why the NIST CSF Matters to Enterprise-Focused Companies
Why Enterprise Buyers Expect CSF Alignment
Enterprise procurement teams evaluate vendor security posture through standardized frameworks, not proprietary security narratives. CSF provides the common language that allows buyers to compare security programs across dozens or hundreds of vendors without translating each organization's unique approach into comparable risk assessments.
When enterprise buyers ask about CSF alignment during vendor risk reviews, they're testing whether your security program operates systematically or reactively. Organizations that map their controls to CSF functions can answer security questionnaires faster, provide evidence more efficiently, and demonstrate that security investments align with recognized risk management practices rather than ad hoc tool purchases.
CSF reduces friction in vendor assessments because both parties reference the same outcome-based model. Instead of explaining proprietary security architectures or justifying tool selections, vendors aligned with CSF can demonstrate how their controls achieve specific outcomes—asset visibility, access management, incident detection—that buyers already evaluate across their entire vendor portfolio.
CSF as a Trust Signal in B2B Sales
Enterprise buyers treat CSF alignment as a baseline security capability, not a competitive differentiator. Organizations without documented CSF mapping face extended security reviews, additional evidence requests, and higher perceived risk during procurement—delays that extend sales cycles and threaten deal closure.
CSF alignment directly supports the evidence collection required for security questionnaires, third-party risk assessments, and compliance audits. When vendors document how their security controls map to CSF functions, they can respond to standardized assessment frameworks—SIG Questionnaire, CAIQ, VSAQ—more efficiently because these assessments already reference CSF outcomes.
Long sales cycles and renewal negotiations depend on sustained security posture, not point-in-time assessments. Enterprise buyers increasingly require continuous security monitoring and regular attestations. Organizations using CSF as their operational security model can demonstrate ongoing control effectiveness rather than preparing security documentation specifically for procurement events.
Core Components of the NIST Cybersecurity Framework
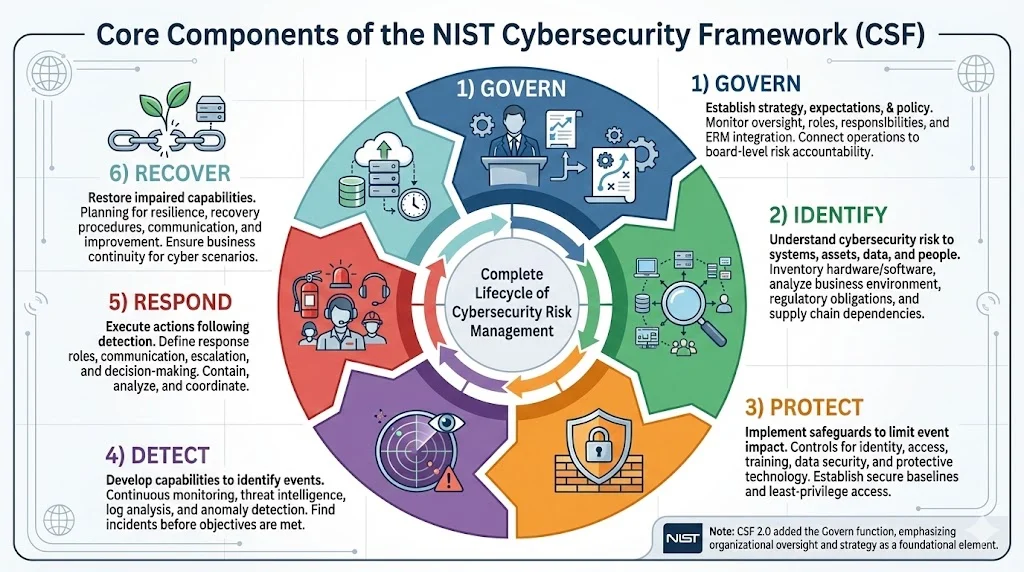
The framework's core is organized around six key functions: Identify, Protect, Detect, Respond and Recover, along with CSF 2.0's newly added Govern function. These functions represent the complete lifecycle of cybersecurity risk management.
1) Govern
The Govern function refers to how an organization's cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored. This function addresses organizational cybersecurity strategy, oversight, roles and responsibilities, policies, and integration with enterprise risk management. Governance establishes accountability structures that connect security operations to board-level risk discussions.
2) Identify
The Identify function establishes organizational understanding of cybersecurity risk to systems, people, assets, data, and capabilities. Organizations inventory hardware, software, data flows, and external dependencies. Risk assessments determine which assets support critical business functions and where vulnerabilities create material exposure. Business environment analysis identifies how regulatory obligations, supply chain relationships, and operational dependencies affect cyber risk.
3) Protect
The Protect function implements safeguards that limit or contain cybersecurity event impact. Controls address identity management and access control, awareness training, data security, protective technology, and maintenance procedures. Organizations establish baseline security configurations, implement least-privilege access models, encrypt sensitive data, and maintain secure development practices.
4) Detect
The Detect function develops and implements capabilities to identify cybersecurity events. Continuous monitoring, threat intelligence, security event logging, and anomaly detection enable organizations to discover incidents before adversaries achieve their objectives. Detection capabilities provide visibility into normal operations, making deviations from baseline behavior observable.
5) Respond
The Respond function executes actions following cybersecurity incident detection. Response planning defines roles, communication paths, escalation procedures, and decision-making authority before incidents occur. Organizations contain incidents, analyze root causes, coordinate with internal and external stakeholders, and document lessons learned to improve future response effectiveness.
6) Recover
The Recover function restores capabilities or services impaired by cybersecurity incidents. Recovery planning includes resilience requirements, recovery procedures, communication strategies, and improvement processes. Organizations define recovery time objectives, test restoration procedures, and ensure business continuity plans address cyber incident scenarios.
How These Functions Support the Security Lifecycle
When considered together, these functions provide a comprehensive view of the lifecycle for managing cybersecurity risk. The functions operate as interconnected capabilities rather than sequential phases. Effective Detect capabilities depend on knowing what assets exist (Identify) and having logging infrastructure in place (Protect). Response effectiveness improves when organizations understand their risk priorities (Govern) and have tested recovery procedures (Recover).
Organizations mature their security programs by strengthening capabilities across all functions simultaneously rather than perfecting one function before addressing others. A mature Protect function provides limited value without corresponding Detect capabilities to identify when protective controls fail. Similarly, sophisticated Detect capabilities overwhelm organizations without documented Response procedures.
Enterprise buyers value lifecycle-based security thinking because it demonstrates operational maturity beyond tool deployment. Organizations that explain their security posture using CSF functions signal that they've considered how controls work together to manage risk, not just which products they've purchased.
CSF and Risk Management for Enterprise Environments
Using CSF for Cyber Risk Assessment
CSF structures cyber risk assessment by connecting asset identification, threat analysis, and business impact evaluation. Organizations inventory critical assets through the Identify function, assess threats and vulnerabilities relevant to those assets, and determine potential business impacts—revenue loss, regulatory penalties, customer trust erosion—from successful attacks.
Risk prioritization using CSF focuses security investments on material risks rather than comprehensive threat coverage. Not every vulnerability warrants immediate remediation. Organizations evaluate which assets support critical business functions, which threat actors target their sector, and which attack vectors present realistic exploitation scenarios given existing controls.
CSF enables board-level risk discussions by translating technical vulnerabilities into business impact language. Instead of reporting the number of critical CVEs or misconfigured systems, security leaders using CSF explain how cyber risks affect strategic objectives: customer data protection, operational continuity, regulatory compliance, and competitive positioning. This translation makes cyber risk comparable to financial, operational, and reputational risks that boards already govern.
Risk-Based Decision Making With CSF
Organizations use CSF outcomes to evaluate security investment priorities. When budget constraints force trade-offs between security initiatives, CSF helps leaders assess which investments reduce the most material risks. Enhancing detection capabilities may provide greater risk reduction than additional protective controls when existing safeguards already address known threats but incident discovery takes weeks rather than hours.
CSF reduces security program noise by focusing attention on outcomes rather than compliance artifacts. Security teams managing hundreds of findings from vulnerability scanners, penetration tests, and audit reports can use CSF to categorize which findings affect critical outcomes and which represent theoretical risks with minimal business impact.
Long-term security planning requires understanding how business changes affect cyber risk. Organizations planning mergers, product launches, or market expansions use CSF to assess how new assets, data flows, and threat exposures alter their risk profile and which security capabilities require investment before business changes occur.
How CSF Supports Data Protection and Compliance Standards
CSF and Regulatory Alignment
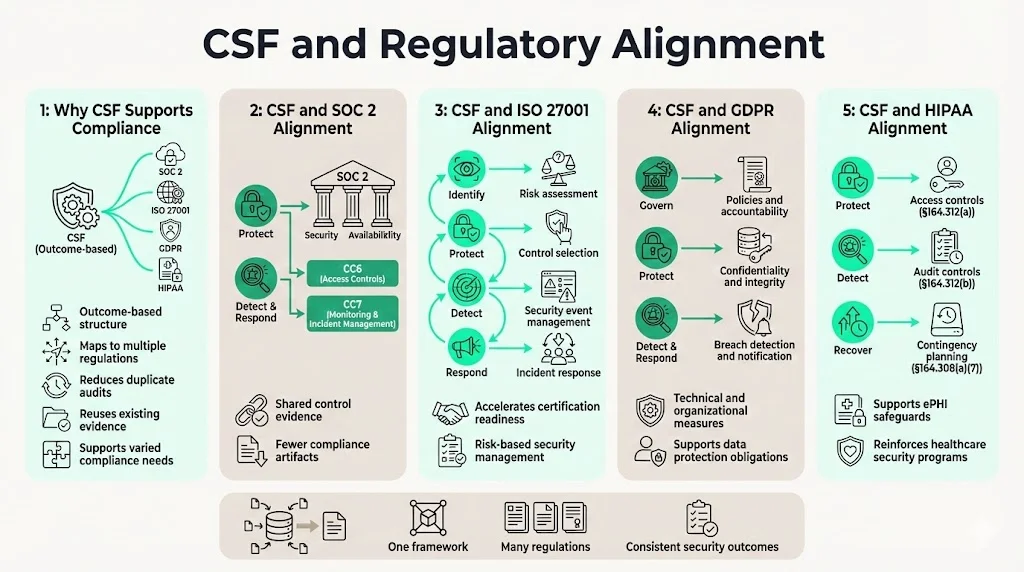
CSF functions map to compliance requirements across multiple regulatory frameworks without duplicating audit work. Organizations subject to SOC 2, ISO 27001, HIPAA, or GDPR requirements can demonstrate how their CSF-aligned security program satisfies specific regulatory controls. CSF's outcome-based structure accommodates different compliance standards that require similar security objectives through different technical specifications.
SOC 2 Trust Services Criteria for Security, Availability, and Confidentiality align directly with CSF functions. The CC6 (Logical and Physical Access Controls) criteria maps to Protect function outcomes for identity management and access control. CC7 (System Operations) criteria corresponds to Detect and Respond function outcomes for monitoring and incident management. Organizations maintaining CSF documentation can reference existing security program evidence during SOC 2 audits rather than generating compliance-specific artifacts.
ISO 27001 control objectives share CSF's risk-based approach to information security management. Organizations implementing CSF have already established many foundational elements required for ISO 27001 certification: risk assessment methodologies (Identify), security control selection (Protect), security event management (Detect), and incident response procedures (Respond). CSF alignment accelerates ISO 27001 implementation by providing existing security program structure that auditors recognize.
GDPR data protection requirements depend on technical and organizational measures that CSF addresses through multiple functions. Data minimization and purpose limitation principles connect to Govern function outcomes for policy development. Technical safeguards protecting personal data confidentiality and integrity align with Protect function outcomes. Data breach notification obligations require Detect and Respond capabilities that CSF already addresses.
HIPAA technical safeguards for electronic protected health information (ePHI) map to CSF security control categories. Access control implementation specifications (§164.312(a)(1)) correspond to Protect function identity management outcomes. Audit controls requirements (§164.312(b)) align with Detect function logging and monitoring outcomes. Contingency planning requirements (§164.308(a)(7)) connect directly to Recover function business continuity outcomes.
CSF as a Compliance Bridge, Not a Checklist
CSF differs from compliance standards because it describes security outcomes rather than prescribing mandatory requirements. Regulatory frameworks establish legal obligations and audit criteria. CSF provides the operational security structure that produces compliance as a natural outcome rather than treating certifications as standalone projects.
Organizations treating compliance as checkbox exercises create security programs that satisfy auditors while leaving actual systems vulnerable. CSF prevents this compliance theater by focusing on whether security controls function effectively, not whether documentation exists. When organizations implement CSF-aligned security programs, compliance evidence emerges from operational security activities—logging, monitoring, incident response—rather than artifacts created specifically for audits.
Enterprise buyers prefer vendors with CSF-aligned security programs because compliance certifications provide point-in-time attestations while CSF demonstrates ongoing operational security. A SOC 2 Type II report covers a specific observation period, typically six to twelve months. Organizations using CSF as their security operating model maintain continuous audit readiness because their security controls operate systematically year-round, not just during formal audit periods.
Security Controls and Operational Practices Under CSF
Translating CSF Outcomes Into Security Controls
CSF outcomes require implementation through specific policies, processes, and technical controls. The Protect function outcome for identity management and access control translates into technical controls including multi-factor authentication, privileged access management, and automated provisioning/deprovisioning. Process controls include access review procedures, least-privilege enforcement, and segregation of duties policies.
Data protection outcomes under the Protect function require controls addressing data classification, encryption in transit and at rest, data loss prevention, and secure deletion. Organizations classify data based on sensitivity and business impact, implement encryption appropriate to each classification tier, and monitor for unauthorized data exfiltration attempts.
Logging and monitoring outcomes under the Detect function depend on centralized log aggregation, security information and event management (SIEM) platforms, automated alerting rules, and analyst workflows for investigating anomalies. Organizations define which events warrant logging, how long logs must be retained, and which event patterns indicate potential security incidents.
Maintaining consistency across security teams requires documented standards that connect CSF outcomes to specific control implementations. When different teams implement access controls, data protection, or monitoring independently, organizations create security gaps where controls don't interoperate or visibility is incomplete. CSF provides the shared framework that ensures security initiatives align across infrastructure, application, and data security teams.
Improving Day-to-Day Security Practices
CSF guides security operations without mandating specific tools or procedures. Organizations select technologies and processes appropriate for their risk environment, operational constraints, and existing infrastructure. A startup protecting customer data implements different controls than a healthcare provider managing ePHI, but both achieve CSF outcomes relevant to their risk profiles.
Mature threat detection and response depend on security operations centers (SOCs) or managed security service providers (MSSPs) that execute CSF Detect and Respond functions continuously. Organizations define detection use cases, escalation thresholds, and response playbooks that operationalize CSF outcomes into repeatable procedures that security analysts execute during incidents.
Building repeatable processes ensures that security operations continue effectively as personnel change and organizations grow. When security procedures exist only in individual practitioners' knowledge, organizations lose capabilities during staff transitions. CSF encourages documenting how security outcomes are achieved so that processes remain consistent regardless of which team members execute them.
CSF in Incident Response and Business Continuity
Incident Response Planning With CSF
The Respond function addresses incident preparation before security events occur. Organizations establish incident response teams with defined roles, develop communication procedures for coordinating with internal stakeholders and external parties, and document escalation paths for different incident severity levels.
Effective incident response requires tabletop exercises and simulation scenarios that test whether response procedures work under pressure. Organizations discover procedural gaps, unclear authority structures, and missing stakeholder contacts during exercises rather than during actual incidents when response delays cause additional damage.
Post-incident analysis improves future response effectiveness by documenting lessons learned, identifying control failures that allowed incidents, and implementing corrective actions. Organizations mature their security programs by treating incidents as learning opportunities that reveal where existing controls require strengthening.
Business Continuity and Recovery
The Recover function connects cyber incidents to operational resilience. Organizations define recovery time objectives (RTOs) and recovery point objectives (RPOs) that specify how quickly systems must be restored and how much data loss is acceptable following incidents. These objectives inform backup frequency, redundancy requirements, and failover procedures.
Recovery procedures require testing to verify that backup systems function, restoration procedures are documented accurately, and recovery timeframes meet business requirements. Organizations that discover backup failures during actual incidents face extended downtime and potential permanent data loss.
Enterprise buyers tie CSF Recover capabilities directly to uptime commitments and customer trust. Service providers offering availability SLAs must demonstrate that recovery procedures account for cyber incidents, not just hardware failures. Organizations suffering extended outages following ransomware or destructive malware attacks lose customer confidence regardless of whether other security controls functioned effectively.
Who Should Use a Cybersecurity Framework Like CSF?
Enterprises and Large Organizations
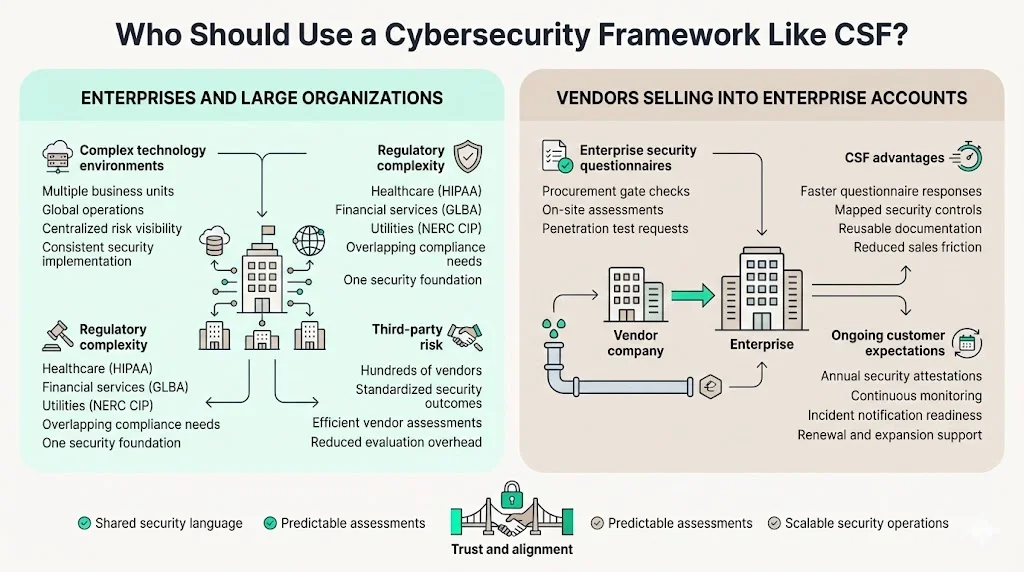
Organizations operating complex technology environments across multiple business units, geographies, and regulatory jurisdictions require structured approaches to cyber risk management. CSF provides the common framework that allows distributed security teams to coordinate their efforts, leadership to understand aggregate risk exposure, and business units to implement security consistently.
Regulatory pressure from sector-specific requirements—HIPAA for healthcare, GLBA for financial services, NERC CIP for utilities—creates compliance complexity that CSF helps manage. Organizations subject to multiple regulatory frameworks use CSF as the foundational security program that satisfies overlapping requirements rather than implementing separate compliance initiatives for each regulation.
Third-party risk management depends on vendors implementing security programs that enterprise buyers can assess efficiently. Organizations managing hundreds of vendor relationships cannot perform detailed security assessments of each supplier. CSF enables standardized vendor evaluations because buyers assess whether suppliers achieve specific security outcomes rather than evaluating each vendor's unique security architecture.
Vendors Selling Into Enterprise Accounts
Organizations selling to enterprise customers face security requirements during procurement that determine whether opportunities progress or stall. Security questionnaires, on-site assessments, and penetration test requirements represent gate checks in enterprise sales processes. Vendors without CSF-aligned security programs face extended evaluation periods that delay deal closure and consume sales engineering resources.
CSF alignment enables faster security questionnaire responses because vendors document how their controls map to commonly requested frameworks. Standard assessments like SIG Questionnaire include hundreds of questions addressing access control, encryption, logging, incident response, and business continuity. Organizations with CSF documentation can reference existing security program evidence rather than researching answers to each question individually.
Supporting customer security expectations throughout the customer lifecycle—not just during initial procurement—requires continuous security operations. Enterprise customers increasingly require annual security attestations, regular penetration testing, and prompt incident notifications. Vendors using CSF as their operational security model maintain audit readiness year-round rather than preparing documentation when renewals approach.
How Often a CSF Should Be Reviewed and Updated
Continuous Improvement Over Static Policies
CSF operates as a living framework that adapts as organizations evolve, not a static policy documented once and archived. Organizations review their CSF implementation when business changes, risk landscape shifts, or security incidents reveal control gaps. Treating CSF as an annual compliance exercise rather than an operational security model creates the same gaps that occur when organizations approach other certifications as point-in-time projects.
Trigger points for CSF review include new or emerging cyber threats affecting your sector, security incidents that exposed control weaknesses, changes to regulatory requirements, and audit findings identifying security program deficiencies. Organizations experiencing ransomware incidents reassess Protect function backup controls and Recover function restoration procedures. New data privacy regulations prompt Govern function policy updates and Protect function data security enhancements.
CSF maturity increases through iterative improvement cycles rather than comprehensive program overhauls. Organizations strengthen specific functions based on risk priorities and operational needs. Enhancing Detect capabilities may take priority when incident discovery times exceed acceptable thresholds. Improving Govern function becomes critical when board members request better cyber risk reporting.
Aligning Updates With Business Growth
Mergers and acquisitions introduce new technology environments, data types, and threat exposures that require CSF reassessment. Organizations acquiring companies inherit security programs with different maturity levels, control implementations, and risk profiles. CSF provides the common framework for integrating acquired security capabilities and identifying where the combined entity faces new risks.
New product launches and market expansions change what assets require protection and which threats become relevant. Organizations entering regulated markets face compliance obligations that affect Govern and Protect functions. Products handling sensitive customer data require enhanced data security controls even when existing products manage only non-sensitive information.
Keeping CSF relevant as organizations scale prevents security programs from becoming obstacles to business objectives. Security controls designed for fifty employees operating from a single office don't accommodate distributed workforces, cloud infrastructure, or global operations. Organizations review CSF implementation to ensure security capabilities support business growth rather than constraining it through outdated policies and inflexible controls.
Conclusion
CSF in cybersecurity refers to structured frameworks—most prominently the NIST Cybersecurity Framework—that organizations use to manage cyber risk through outcome-based functions rather than prescriptive technical requirements. CSF provides the common language that enables enterprises to assess their own risk posture, evaluate vendor security programs, and communicate cyber risk to boards and stakeholders.
CSF strengthens data protection standards by connecting technical security controls to business outcomes and regulatory requirements. Organizations implementing CSF-aligned security programs satisfy multiple compliance frameworks more efficiently because their operational security activities produce the evidence that auditors require rather than generating compliance-specific artifacts.
Enterprise-focused companies gain long-term value from CSF alignment through accelerated vendor assessments, sustained audit readiness, and security programs that adapt as organizations grow. Organizations treating CSF as their operational security model rather than a compliance checkbox build security capabilities that actually reduce risk instead of simply impressing auditors on paper.
FAQs
1) What does CSF mean in cybersecurity?
CSF refers to Cybersecurity Framework, a structured approach for managing cyber risk using outcome-based functions. The NIST Cybersecurity Framework is the most widely adopted CSF model, organizing security operations around six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. CSF differs from security products or tools by describing desired security outcomes rather than prescribing specific technologies or implementations.
2) Is the NIST CSF mandatory?
The NIST CSF is voluntary guidance, not a regulatory requirement. However, many enterprise buyers, regulators, and industry sectors treat CSF alignment as expected practice during vendor assessments and procurement reviews. Organizations in certain regulated sectors face mandatory security requirements that CSF helps satisfy, but the framework itself carries no legal enforcement mechanism.
3) How does a CSF support compliance standards?
CSF supports compliance by providing an operational security structure that produces regulatory compliance as a natural outcome. Organizations map CSF functions to specific requirements in SOC 2, ISO 27001, HIPAA, GDPR, and other frameworks. This mapping demonstrates how security controls satisfy multiple compliance obligations simultaneously, reducing duplicate audit work and enabling organizations to maintain continuous compliance rather than preparing specifically for scheduled audits.
4) Who should use a cybersecurity framework?
Enterprises managing complex technology environments, organizations in regulated industries, and vendors selling into enterprise accounts benefit most from CSF implementation. Any organization managing meaningful cyber risk—customer data, intellectual property, operational technology, or regulatory obligations—should implement structured security frameworks rather than relying on ad hoc security initiatives.
5) How often should a CSF be updated?
Organizations review CSF implementation when business changes occur, new risks emerge, incidents expose control gaps, or regulatory requirements change. Typical review cycles range from quarterly assessments of specific functions to annual comprehensive program evaluations. Events requiring immediate CSF updates include mergers and acquisitions, significant security incidents, new product launches affecting data handling, and regulatory changes imposing new security obligations.



.svg)
.svg)
.svg)