Most organizations view military network infrastructure as irrelevant to commercial technology decisions. This assumption creates a fundamental blind spot—particularly for vendors targeting defense contractors, federal agencies, or highly regulated enterprises where DoDIN-influenced security standards increasingly define baseline expectations. Understanding DoDIN means understanding the architectural and cybersecurity standards that increasingly shape how enterprise clients evaluate vendors.
The Department of Defense Information Network (DoDIN) is a global set of information capabilities, processes, and personnel for collecting, processing, storing, disseminating, and managing information on demand to warfighters, policymakers, and support personnel. DoDIN is a global infrastructure carrying DOD, national security, and related intelligence community information and intelligence. This network represents the technological backbone enabling every military communication, command decision, and data operation across classified and unclassified environments worldwide.
For businesses supplying IT, cybersecurity, networking, or cloud solutions to defense-adjacent markets, DoDIN represents both a technical benchmark and a compliance threshold. The security architecture, operational frameworks, and risk management practices developed for DoDIN directly influence how defense contractors and regulated enterprises evaluate vendor capabilities—making DoDIN literacy a competitive requirement for vendors aiming beyond commercial-grade security postures.
What is DoDIN?
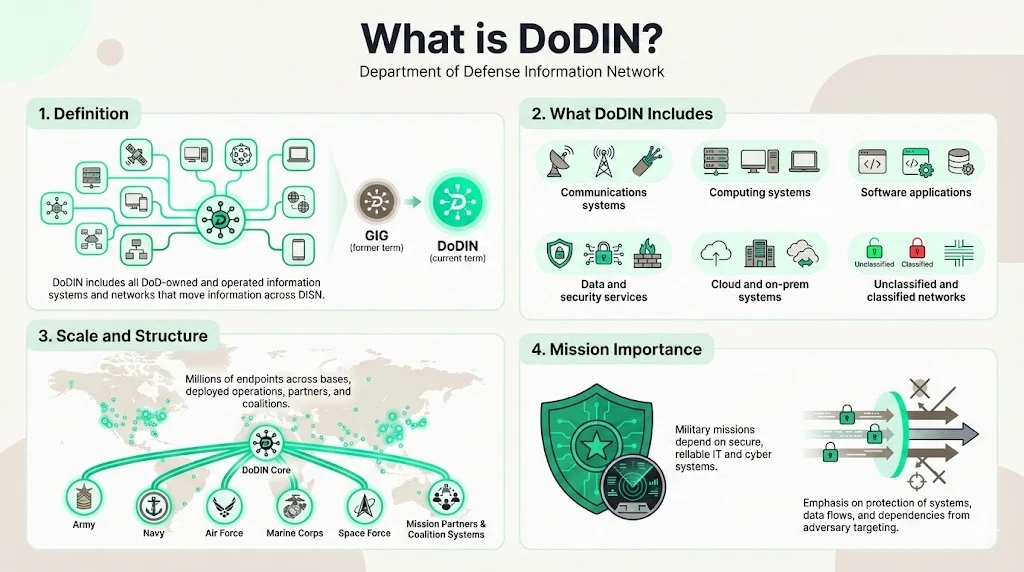
DoDIN comprises all Department of Defense (DoD) owned and operated information systems and networks that enable the movement of information across the Defense Information Systems Network (DISN). Historically, DoD referred to this infrastructure as the Global Information Grid (GIG)—terminology that has been largely replaced by DoDIN to reflect evolved operational and architectural realities.
DoDIN's scope extends far beyond traditional network infrastructure. It encompasses owned and leased communications systems, computing systems, software applications, data services, security services, national security systems, and both cloud and on-premises environments. This includes unclassified networks supporting routine military operations and classified networks handling sensitive intelligence and mission-critical communications.
The scale is massive: millions of endpoints distributed globally across bases, deployed operational environments, partner networks, and coalition forces. DoDIN functions as a network of networks—integrating service-specific networks (Army, Navy, Air Force, Marine Corps, Space Force), deployed operational networks in theater, enterprise IT infrastructure, mission partner environments, and coalition systems into a coherent, defendable whole.
DoD operational missions depend upon a secure, streamlined information technology and cyber infrastructure—making DoDIN architecture, design, data flows, and engineering considerations defense critical infrastructure. Information about the Department's cyber capabilities and dependencies would enable an adversary to locate, identify and target critical military functions and exploit operational vulnerabilities.
How DoDIN operates — infrastructure, architecture, and governance
DoDIN operates as an integrated ecosystem with multiple components: communications systems providing voice and data transport; computing systems supporting applications and workloads; data services enabling storage, processing, and analytics; software applications spanning mission and enterprise functions; security services protecting data in transit and at rest; cloud environments for scalable infrastructure; and national security systems handling classified operations.
The "network of networks" concept reflects DoDIN's federated architecture. Rather than a single monolithic network, DoDIN integrates disparate service networks, theater-deployed operational networks, enterprise IT systems, and mission partner networks under unified operational command and security governance. This integration enables seamless information flow while maintaining appropriate segmentation for classification levels and operational security.
The operational responsibility for the DoDIN is shared among different entities within the DoD, with the Defense Information Systems Agency (DISA) playing a leading role in its operation and defense. JFHQ-DODIN oversees the day-to-day operation of DOD's networks and actively defends the DODIN, with the JFHQ-DODIN commander dual-hatted as the director of DISA. DISA provides enterprise telecommunications, computing, and security services, while JFHQ-DODIN (Joint Force Headquarters–DoDIN) executes operational command for securing and defending the network.
Governance operates through structured policy frameworks. DoDI 8410.02 defines support to DoDIN operations including responsibilities for securing, operating, and defending the network. These policies establish standardized approaches for control implementation, risk management, incident response, and continuous monitoring—ensuring every component connecting to DoDIN meets rigorous technical and security requirements regardless of which service or agency owns it.
Architecture principles emphasize defense-in-depth, segmentation, continuous monitoring, and increasingly, Zero Trust architectures. DoD has published reference architecture guides for implementing Zero Trust across DoDIN—requiring identity verification, least-privilege access, micro-segmentation, and continuous validation for every user, device, and application accessing network resources.
DoDIN and Cybersecurity — why it matters
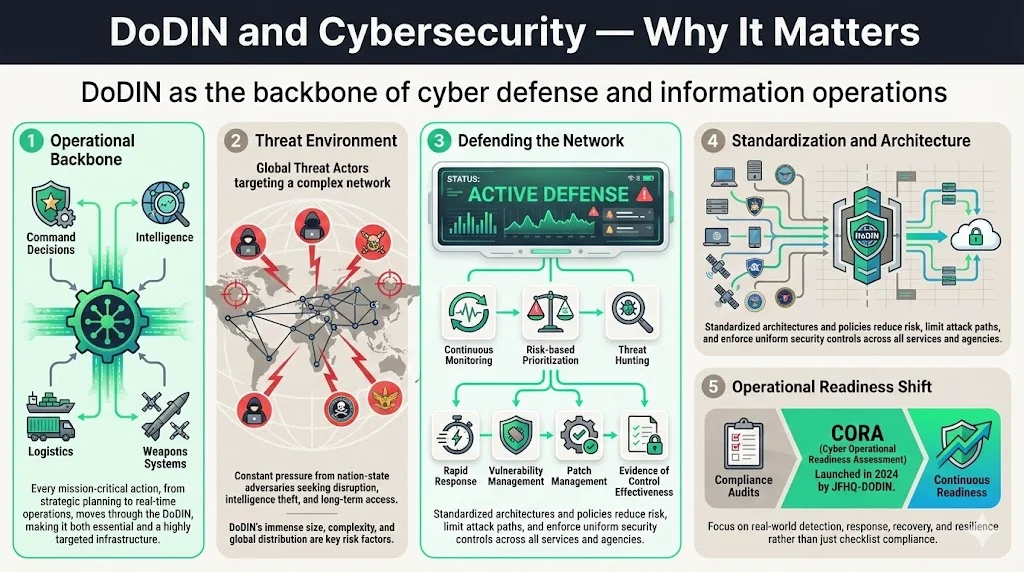
DoDIN serves as the operational backbone of DoD's cyber defense and information operations. Every command decision, intelligence report, logistics coordination, and weapons system communication traverses DoDIN infrastructure—making it the most critical and most targeted network infrastructure in existence.
The threat environment is unrelenting. An adversary gaining information about the Department's cyber capabilities and dependencies could locate, identify and target critical military functions and exploit operational vulnerabilities. DoDIN's size, complexity, global distribution, and mission-criticality make it a primary target for nation-state adversaries seeking to sabotage military operations, exfiltrate classified intelligence, or establish persistent access for future conflict scenarios.
Defense requires continuous monitoring, risk-based prioritization, threat hunting, and rapid response across both unclassified and classified network segments. To ensure the secure and seamless function of DoDIN, the DoD employs various security measures and protocols, adheres to stringent cybersecurity standards, and engages in continuous monitoring and defense against cyber threats. This includes implementing standardized security architectures, enforcing configuration baselines, conducting vulnerability assessments, managing patch cycles, and maintaining detailed evidence of control effectiveness.
Standardized cybersecurity architecture and policy frameworks reduce risk by ensuring consistent security posture across every DoDIN component. When thousands of systems, operated by different services and agencies, must interconnect securely, architectural consistency becomes operational necessity. Every system connecting to DoDIN must meet documented security requirements—reducing the attack surface and limiting adversary opportunities to exploit inconsistent implementations.
DoD has shifted from compliance-focused inspections toward continuous operational readiness assessments. In 2024, JFHQ-DODIN launched the Cyber Operational Readiness Assessment (CORA)—replacing periodic compliance audits with continuous, holistic assessments designed to measure actual defensive capability rather than checkbox compliance. CORA evaluates whether organizations can detect, respond to, and recover from realistic attack scenarios—emphasizing operational resilience over documentation artifacts.
What DoDIN Means for Businesses
For vendors supplying IT, security, networking, cloud, or data solutions to defense contractors or federal agencies, DoDIN establishes architectural and security baselines that increasingly influence procurement decisions. Organizations operating in defense-adjacent markets expect vendors to understand—and often meet—DoDIN-style security requirements even for non-DoD engagements.
Compliance and product certification represent significant barriers to entry. The DoDIN Approved Products List (APL) defines products that have undergone rigorous evaluation before being authorized for DoDIN use. Achieving APL certification requires demonstrating compliance with technical specifications, security controls, interoperability requirements, and operational standards—a process demanding substantial documentation, testing, and investment.
Vendors targeting DoD, defense contractors, or national security clients face heightened responsibility. Solutions must comply with strict cybersecurity frameworks, architectural standards, and interoperability requirements—from secure communications protocols to compliance with DoDIN policy frameworks. Meeting these requirements often necessitates implementing controls beyond commercial best practices: enhanced encryption standards, rigorous access controls, detailed audit logging, vulnerability management with defined remediation SLAs, and continuous monitoring capabilities.
The impact extends beyond direct DoD engagements. Defense contractors and companies in the Defense Industrial Base (DIB) increasingly demand DoDIN-aligned security standards from their vendors—creating cascading compliance requirements throughout supply chains. A software vendor serving a defense contractor may face requirements for secure cloud architecture, end-to-end encryption, identity management aligned with Zero Trust principles, and evidence-based compliance documentation—even if their solution never directly touches classified networks.
DoDIN's influence on broader enterprise security practices is growing. As cyber threats intensify globally, DoDIN's operational models—Zero Trust architecture, risk-based continuous assessment, defense-in-depth, and outcome-focused readiness validation—increasingly inform enterprise cybersecurity strategies. Organizations in regulated sectors such as finance, healthcare, and critical infrastructure adopt DoDIN-inspired frameworks to strengthen their security postures against sophisticated adversaries.
For vendors, this creates both opportunity and obligation. Companies capable of meeting DoDIN-level security requirements position themselves for defense, federal, and highly regulated enterprise markets. However, achieving this capability requires genuine investment in security infrastructure, not performative compliance. Organizations seeking DoDIN alignment must implement actual security controls—technical safeguards, operational processes, continuous monitoring, and evidence collection—that demonstrate security effectiveness under adversarial conditions.
Challenges and Considerations
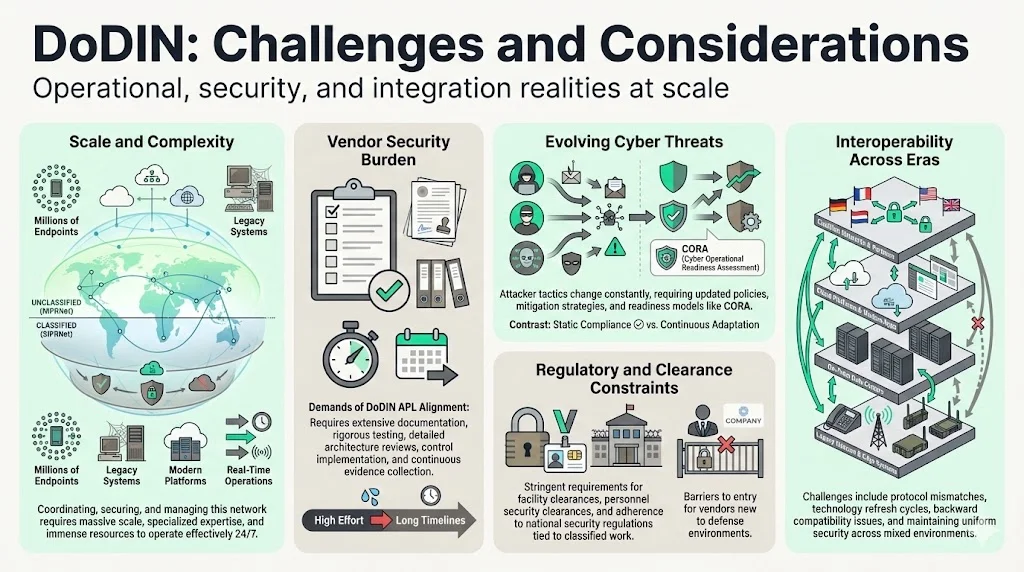
DoDIN's complexity presents substantial operational challenges. Managing a globally interconnected infrastructure with millions of endpoints, spanning classified and unclassified environments, integrating legacy and modern systems, and supporting real-time mission-critical operations demands extraordinary coordination, technical expertise, and resources.
The security and compliance burden for vendors is significant. Achieving DoDIN APL certification or meeting DoDIN-aligned requirements demands rigorous documentation, extensive testing, architectural reviews, security control implementation, and ongoing evidence collection. Organizations unprepared for this investment level will struggle to compete in defense-adjacent markets.
Cyber threats evolve continuously. Adversaries adapt tactics, develop new exploitation techniques, and persistently probe for vulnerabilities—requiring DoDIN governance to continuously update policies, refine mitigation strategies, and enhance readiness assessment methodologies like CORA. Static compliance frameworks become obsolete; continuous adaptation becomes operational imperative.
Regulatory and clearance constraints further complicate vendor participation. Handling classified information, accessing sensitive systems, or supporting national security operations may require facility clearances, personnel security clearances, and compliance with additional regulations beyond technical security controls—creating barriers for vendors without existing defense relationships.
Interoperability challenges persist across DoDIN's heterogeneous environment. The network spans decades of technology evolution: legacy telecommunications infrastructure, modern cloud environments, on-premises data centers, tactical edge systems, and coalition partner networks. Ensuring security, performance, and reliability across this diversity requires bridging incompatible protocols, managing technology refresh cycles, and maintaining backward compatibility—all while continuously hardening security posture.
Conclusion
DoDIN represents a globally interconnected, defense-grade information network providing the communications, computing, data, and security infrastructure underpinning every DoD mission. Its architecture, operational frameworks, and cybersecurity standards reflect decades of experience defending against sophisticated nation-state adversaries in contested environments.
For businesses targeting defense contractors, federal agencies, or highly regulated enterprises, DoDIN awareness extends beyond academic interest. DoDIN's architectural rigor, security standards, and continuous readiness assessment models increasingly influence how enterprise clients evaluate vendor capabilities. Organizations in the Defense Industrial Base demand DoDIN-aligned security postures from their suppliers—creating cascading compliance expectations throughout technology supply chains.
Vendors serious about defense-adjacent markets must recognize DoDIN-style requirements as the baseline, not the ceiling. This means implementing genuine security controls—technical safeguards, operational processes, continuous monitoring, evidence-based validation—that demonstrate effectiveness under adversarial conditions. Architecture rigor, standardized security frameworks, and operational readiness assessments represent the standard for organizations operating where security failure carries mission consequences.
Understanding DoDIN provides vendors with a strategic advantage: insight into the security expectations, architectural principles, and compliance frameworks that define how defense and regulated-sector clients evaluate technology partners. Organizations capable of meeting these standards position themselves for markets where security represents operational necessity, not regulatory checkbox.
FAQs
1) What does DoDIN mean?
DoDIN stands for the Department of Defense Information Network—the globally interconnected set of information capabilities, processes, and infrastructure used by the DoD for collecting, storing, processing, and disseminating data across its networks.
2) What is the DoDIN?
The DoDIN refers to the totality of DoD-owned and leased communications and computing systems, services (including software, data, security services), networks (classified and unclassified), and national-security systems that together enable secure, mission-critical information and communications for warfighters, policymakers, support staff, and other DoD stakeholders.
3) What is DoDIN certification?
This refers to the process through which products (hardware, software, services) must be evaluated and approved before being allowed to connect or be used within DoDIN. For instance, the DoDIN Approved Products List (APL) defines how products must meet DoDIN security, interoperability, and compliance standards before being certified.
4) What is a DoDIN network?
A DoDIN network refers to any network (or system of networks) that is part of or connected to the broader DoDIN—whether that's base-level service-specific networks, deployed operational networks, enterprise IT, cloud environments, or national security systems. All these networks collectively form the broader DoDIN infrastructure.



.svg)
.svg)
.svg)