Most healthcare organizations handle the transition to electronic health records as a technology project rather than a regulatory imperative with ongoing compliance obligations. This approach creates a fundamental gap between adopting digital systems and understanding the legal framework that governs their use—a gap that becomes apparent when breach notifications are required, auditors examine evidence collection procedures, or civil monetary penalties escalate into six-figure enforcement actions.
The Health Information Technology for Economic and Clinical Health Act (HITECH Act) was enacted under Title XIII of the American Recovery and Reinvestment Act of 2009, with the U.S. Department of Health and Human Services committing $25.9 billion to promote and expand the adoption of health information technology. The Act addresses two core objectives: accelerating the adoption of electronic health records (EHRs) and health information technology across the healthcare sector, and strengthening the privacy and security protections surrounding electronic health information.
This definition explains what HITECH means for healthcare organizations, business associates, and vendors handling patient data—covering the Act's statutory provisions, compliance requirements, breach notification obligations, enforcement mechanisms, and practical implications for managing digital health records within a regulated environment.
c
HITECH stands for Health Information Technology for Economic and Clinical Health, a law specifically formulated to expand the use of EHRs within the healthcare system and facilitate more efficient, secure, and effective exchange of patients' health information between healthcare providers.
The Act was signed into law on February 17, 2009, to promote the adoption and meaningful use of health information technology. At the time, fewer than 20% of healthcare providers utilized electronic health records, and the transition from paper-based documentation to digital systems required both financial incentives and regulatory enforcement to achieve widespread implementation.
The legislative context matters: by 2009, healthcare remained largely paper-based while other sectors had adopted digital infrastructure decades earlier. The provisions of HITECH and implementing regulations represent a transformational shift in the delivery of healthcare in America from a paper-based to an electronic system that supports improvements in the quality and efficiency of care.
Why was HITECH introduced?
The HIPAA Act of 1996 required the creation of regulation standards for health information protection and stipulated that sensitive patient health information could not be disclosed without the patient's awareness, but the HITECH Act of 2009 played a role in closing loopholes of HIPAA so that electronic records could be safely used without compromising patient privacy.
HIPAA's original framework did not anticipate the scale of electronic data exchange that would characterize modern healthcare delivery. The Act addressed this gap by establishing financial incentives for adopting certified EHR systems while simultaneously imposing mandatory breach notification requirements, expanded business associate accountability, and tiered civil monetary penalties for violations.
Congress crafted HITECH to significantly revise health information privacy and security law, particularly HIPAA, broadening its reach and strengthening its privacy and security standards, in addition to adding new provisions related to enforcement and entities not covered by HIPAA.
Key Elements of HITECH – What businesses should know
1) Adoption of Electronic Health Records & Health IT
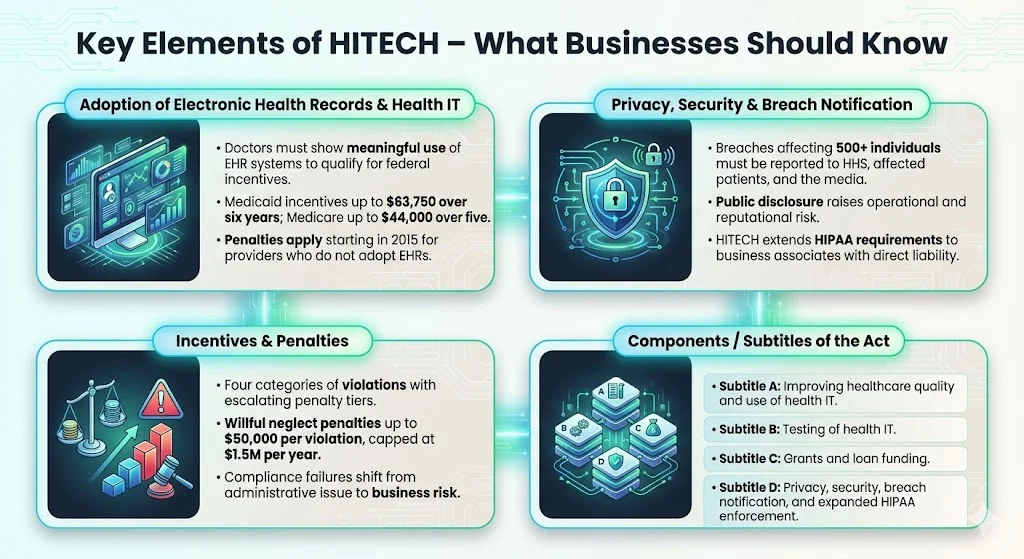
The HITECH Act requires doctors to show "meaningful use" of an EHR system to receive EHR stimulus money. The concept of meaningful use established specific criteria that healthcare providers must meet to qualify for incentive payments—criteria designed to ensure that EHR adoption translates into measurable improvements in care quality, patient engagement, and operational efficiency.
Title IV of the Act promises maximum incentive payments for Medicaid of $63,750 over 6 years beginning in 2011, while for Medicare, the maximum payments are $44,000 over 5 years. These incentives were structured to offset the substantial capital investment required for EHR implementation, including software acquisition, infrastructure upgrades, training, and workflow redesign.
Doctors who do not adopt an EHR by 2015 face a 1% penalty of Medicare payments, increasing to 3% over 3 years, and starting in 2015, hospitals and doctors became subject to financial penalties under Medicare if they are not using electronic health records.
2) Privacy, Security & Breach Notification
The HITECH Act requires entities covered under HIPAA to report data breaches that affect 500 or more persons to the U.S. Department of Health and Human Services, to the news media, and to the people affected by the data breaches, imposing new notification requirements on covered entities, business associates, vendors of personal health records and related entities if a breach of unsecured protected health information occurs.
HITECH mandates public notification of security breaches when unsecured PHI is disclosed or used for an unauthorized purpose; the Act requires that patients be notified of any breach of their data security, whether external or internal, and if a breach affects 500 patients or more, then HHS must also be notified and the name of the institution where the breach occurred will be posted on the HHS web site.
This breach notification framework introduces significant reputational and operational risk for healthcare organizations. The public disclosure requirement transforms data security incidents from internal operational issues into matters of public record, subjecting organizations to regulatory scrutiny, potential litigation, and loss of stakeholder trust.
The HITECH Act extended the reach of HIPAA to business associates of covered entities, who were now accountable for failures of HIPAA compliance. Prior to HITECH, business associates operated under contractual obligations but faced limited direct regulatory enforcement. The Act fundamentally altered this landscape by imposing direct liability for privacy and security violations.
3) Incentives & Penalties
Section 13410(d) of the HITECH Act revised section 1176(a) of the Social Security Act by establishing four categories of violations that reflect increasing levels of culpability and four corresponding tiers of penalty amounts that significantly increase the minimum penalty amount for each violation.
If the violation is due to willful neglect, the minimum penalty is $10,000 per violation, with a cap of $250,000 for violations of an identical requirement during a calendar year, and the maximum penalty is $50,000 per violation, with a cap of $1.5 million.
This tiered penalty structure reflects culpability ranging from violations where the entity was unaware despite due diligence (minimum $100 per violation) to willful neglect where violations are not corrected within the required timeframe (minimum $50,000 per violation). The substantial increase in penalty amounts signals a shift from compliance as administrative obligation to compliance as material business risk.
4) Components / Subtitles of the Act
There are four major components of the HITECH Act: Subtitle A is split into two parts related to improving healthcare quality, safety, and efficiency, and the application and use of health information technology; Subtitle B concerns the testing of health information technology, while Subtitle C covers grants and funding for loans.
Subtitle D of the HITECH Act addresses the privacy and security concerns associated with the electronic transmission of health information, in part, through several provisions that strengthen the civil and criminal enforcement of the HIPAA rules.
Subtitle D represents the portion of the Act most directly relevant to compliance teams and risk management functions. It establishes business associate accountability, mandates breach notification procedures, revises enforcement provisions, and extends HIPAA's privacy and security requirements to scenarios not contemplated under the 1996 legislation.
Who Needs to Comply – Scope & Applicability for Healthcare Businesses
The HITECH Act now places Business Associates under the same comprehensive Security Rule requirements as covered entities to ensure consistency of security when health information is accessed or exchanged between organizations.
This expansion of regulatory scope has material implications for healthcare technology vendors, cloud service providers, claims processors, billing companies, consultants, legal service providers, and any entity that creates, receives, maintains, or transmits protected health information on behalf of a covered entity.
Covered entities under HIPAA—health plans, healthcare clearinghouses, and healthcare providers who transmit health information electronically—have long understood their compliance obligations. HITECH extends direct enforcement authority to business associates, eliminating the previous framework where covered entities bore sole regulatory liability for business associate failures.
Business Associates are now squarely in the middle of the HIPAA and HITECH world through the electronic exchange of protected health information, as they will now be held directly liable for breaches of protected health information.
Healthcare organizations selecting EHR platforms, cloud infrastructure providers, or data analytics vendors must evaluate not only technical capabilities and interoperability but also vendor compliance maturity, breach response procedures, security control implementation, and contractual indemnification provisions. The vendor selection process becomes a regulatory compliance decision with downstream liability implications.
Practical Implications for Healthcare Technology & Compliance
For Technology Adoption & EHR Implementation
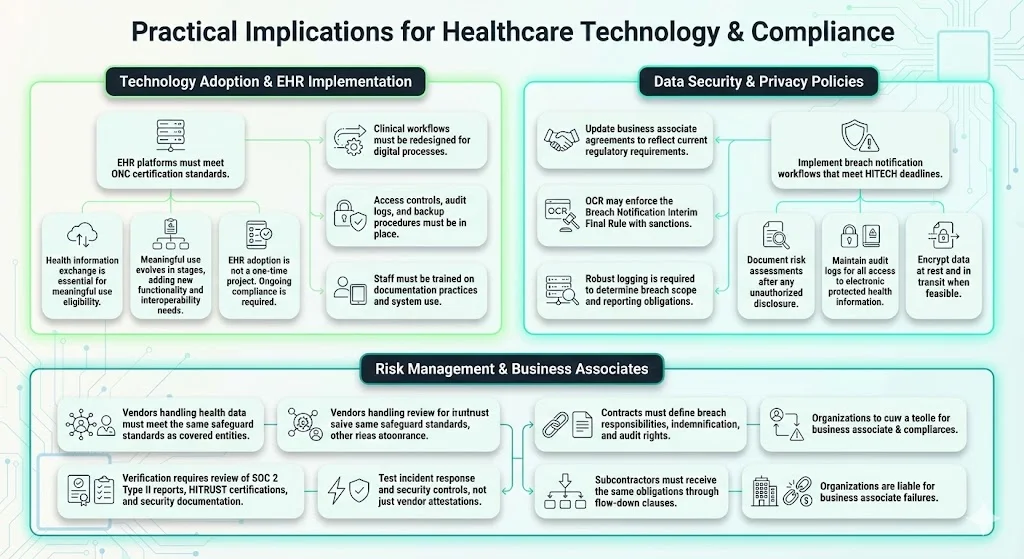
Healthcare organizations implementing EHR systems must verify that selected platforms meet certification criteria established by the Office of the National Coordinator for Health Information Technology. Health information exchange has emerged as a core capability for hospitals and physicians to achieve meaningful use and receive stimulus funding.
Meaningful use requirements evolve across multiple stages, each introducing additional functionality and interoperability requirements. Organizations treating EHR implementation as a one-time project rather than an ongoing compliance program inevitably face gaps when meaningful use criteria advance or when audit evidence demonstrates that systems are installed but not utilized according to statutory requirements.
The shift from paper to digital records requires redesigning clinical workflows, implementing access controls that balance usability with security requirements, establishing audit log monitoring, training staff on proper documentation practices, and creating backup and disaster recovery procedures that ensure business continuity without compromising data integrity.
For Data Security & Privacy Policies
Compliance teams in healthcare organizations must implement breach notification workflows that meet HITECH's strict timeframes, document risk assessments following unauthorized disclosures, maintain audit controls that track access to electronic protected health information, encrypt data at rest and in transit where technically feasible, and ensure that business associate agreements reflect current regulatory requirements.
Covered entities and business associates must comply with breach notification obligations for breaches discovered on or after September 23, 2009, and OCR enforces the Breach Notification Interim Final Rule, including with the possible imposition of sanctions, as it does with the HIPAA Privacy and Security Rule requirements.
The breach notification trigger—unauthorized acquisition, access, use, or disclosure of unsecured protected health information—requires organizations to maintain robust logging and monitoring capabilities. Without comprehensive audit trails, organizations cannot determine breach scope, affected individuals, or appropriate notification procedures.
For Risk Management & Business Associates
Organizations must verify that vendors handling protected health information on their behalf have implemented administrative, physical, and technical safeguards equivalent to those required of covered entities. This verification cannot rely solely on vendor attestations or marketing materials; it requires reviewing third-party audit reports (SOC 2 Type II, HITRUST certifications), examining security control documentation, testing incident response capabilities, and establishing contractual provisions that address breach notification responsibilities, indemnification, and audit rights.
Business Associates should review their HIPAA policies and procedures to ensure compliance with the Security Rule safeguards and review their Business Associate agreements with Covered Entities to ensure that the new requirements are incorporated.
The business associate ecosystem extends beyond direct vendors to subcontractors—a chain of custody for protected health information that requires contractual flow-down provisions ensuring that compliance obligations extend throughout the supply chain. Organizations failing to manage third-party risk face direct regulatory liability for business associate violations.
HITECH vs HIPAA – Understanding the Difference
HIPAA, enacted in 1996, established foundational privacy and security requirements for protected health information, focusing primarily on covered entities (health plans, healthcare clearinghouses, and healthcare providers transmitting health information electronically). HIPAA's Privacy Rule governs permissible uses and disclosures of protected health information, while the Security Rule establishes administrative, physical, and technical safeguards for electronic protected health information.
The Health Information Technology for Economic and Clinical Health Act is the part of the American Recovery and Reinvestment Act of 2009 that incentivized the meaningful use of EHRs and strengthened the privacy and security provisions of HIPAA, introducing tougher penalties for violations of HIPAA.
Key differences include:
- Scope of Enforcement: HIPAA enforcement focused on covered entities, with business associates subject primarily to contractual obligations. HITECH extends direct regulatory enforcement to business associates, making them independently liable for privacy and security violations.
- Business Associate Accountability: HITECH requires business associates to comply with applicable HIPAA Security Rule provisions and subjects them to civil monetary penalties and enforcement actions previously reserved for covered entities.
- Breach Notification: HIPAA contained no federal breach notification requirement. HITECH mandates notification to affected individuals, HHS, and in cases affecting 500 or more individuals, media notification and public disclosure on the HHS breach portal.
- Incentives for Health IT Adoption: HIPAA established privacy and security baselines but provided no financial incentives for technology adoption. HITECH allocates billions in incentive payments tied to meaningful use criteria while imposing payment penalties for failure to adopt certified EHR systems.
Healthcare organizations must treat HIPAA and HITECH as integrated components of a comprehensive regulatory framework governing health information technology, recognizing that HITECH builds upon and extends HIPAA's foundational requirements rather than replacing them.
Current Context & Trends in Health IT Regulatory Landscape
The healthcare industry continues to navigate the ongoing implications of HITECH requirements well beyond the initial meaningful use incentive period. Interoperability remains a persistent challenge, with healthcare organizations managing data exchange across disparate EHR platforms, health information exchanges, and patient access applications.
Regulatory focus has shifted from initial EHR adoption to data blocking prohibitions, application programming interface requirements under the 21st Century Cures Act, patient access to electronic health information, and third-party application access to health data. These developments extend HITECH's original objectives while introducing additional compliance complexity.
Breach risks continue to evolve as healthcare organizations face sophisticated ransomware attacks, business email compromise schemes, insider threats, and vulnerabilities in connected medical devices and Internet of Things infrastructure. The regulatory expectation has moved beyond perimeter security to comprehensive risk management programs that address supply chain vulnerabilities, continuous monitoring, incident response capabilities, and third-party risk management.
Organizations must recognize that compliance with HITECH requirements is not a project with a defined completion date but an operational discipline requiring sustained investment in security infrastructure, policy maintenance, staff training, vendor oversight, and evidence collection to demonstrate ongoing adherence to meaningful use criteria and privacy and security safeguards.
Best Practices for Healthcare Companies to Address HITECH
Develop or update policies and procedures that address EHR adoption requirements, meaningful use criteria, breach notification workflows, business associate oversight, patient access rights to electronic health information, and accounting of disclosures for organizations using electronic health records.
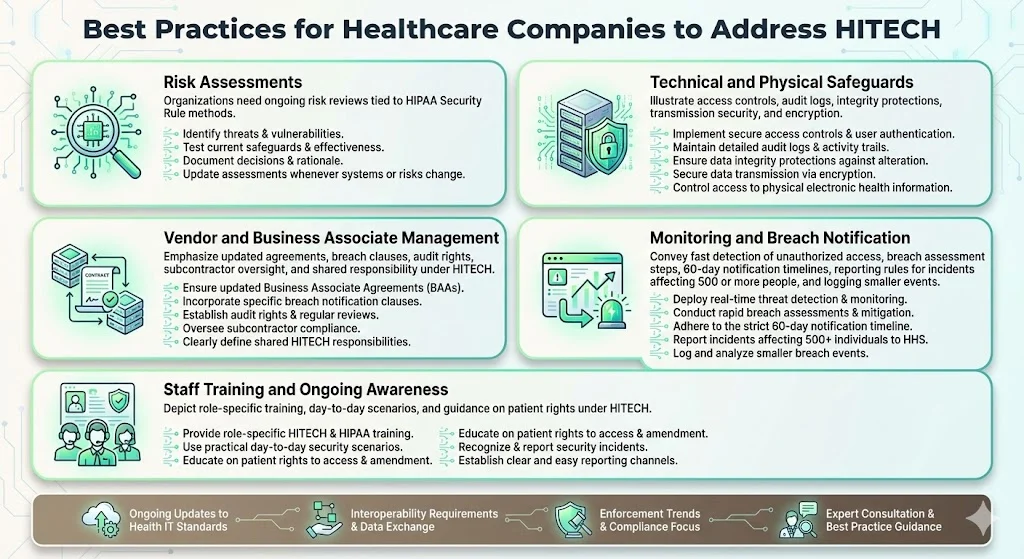
1) Conduct regular risk assessments following the methodology outlined in HIPAA Security Rule implementation specifications, identifying threats and vulnerabilities to electronic protected health information, evaluating current security measures, determining residual risk, and documenting risk mitigation decisions. Risk assessments cannot be annual checkbox exercises; they must reflect changes in technology infrastructure, threat landscape, business operations, and regulatory requirements.
2) Ensure technical and physical safeguards including access controls that limit information system access to authorized users, audit controls that record and examine activity in systems containing electronic protected health information, integrity controls that protect against improper alteration or destruction, transmission security measures, and encryption where appropriate based on risk assessment findings.
3) Manage vendor contracts and business associate agreements to ensure they reflect HITECH's expanded business associate obligations, establish breach notification procedures, define security control requirements, provide audit rights, address subcontractor arrangements, and clarify liability allocation. Standard vendor templates rarely address these requirements adequately; organizations must negotiate contractual provisions that align with their risk tolerance and regulatory obligations.
4) Implement monitoring and breach notification workflows that enable rapid detection of unauthorized access to or disclosure of protected health information, document breach risk assessments to determine notification obligations, execute notification to affected individuals within 60 days of breach discovery, report breaches affecting 500 or more individuals to HHS and media outlets, and maintain breach logs for smaller incidents requiring annual reporting.
5) Train staff on health information technology regulations, proper handling of electronic protected health information, patient rights under HITECH (including rights to electronic copies of health information and direction of those copies to third parties), recognition of security incidents, breach reporting procedures, and sanctions for policy violations. Training cannot be an annual compliance theater; it must address role-specific risks and provide practical guidance for scenarios staff encounter in daily operations.
Stay current with health IT standards, interoperability requirements, and meaningful use evolutions through participation in industry organizations, monitoring HHS Office for Civil Rights guidance, tracking enforcement actions to understand regulatory priorities, and engaging with legal counsel and compliance advisors who maintain expertise in healthcare privacy and security regulations.
Conclusion
The Health Information Technology for Economic and Clinical Health Act represents the foundational legislation that accelerated healthcare's transition to electronic health records while establishing the privacy, security, and breach notification framework that governs how healthcare organizations manage patient data. For organizations handling protected health information—whether as covered entities or business associates—understanding HITECH is not optional: it defines compliance obligations tied to technology adoption, data security infrastructure, regulatory enforcement, and civil monetary penalty exposure.
The Act's dual focus on incentivizing health information technology adoption and strengthening accountability for privacy and security failures reflects a fundamental premise: digital health records offer substantial benefits in care quality, efficiency, and patient engagement, but only when implemented within a robust regulatory framework that protects patient information and establishes meaningful consequences for failures.
Review your health information technology infrastructure to ensure processes align with HITECH's requirements around meaningful use, breach notification, business associate accountability, and security safeguards. Evaluate whether your organization treats compliance as ongoing operational discipline or as completed project, recognizing that the regulatory environment continues to evolve beyond HITECH's original provisions to address interoperability, patient access, data blocking, and emerging cybersecurity threats.
FAQs
1) What is the meaning of HITECH?
The Health Information Technology for Economic and Clinical Health Act or HITECH Act is the part of the American Recovery and Reinvestment Act of 2009 that incentivized the meaningful use of EHRs and strengthened the privacy and security provisions of HIPAA. The Act promotes adoption of health information technology and electronic health records while strengthening privacy, security, and breach notification regulations for healthcare organizations and their business associates.
2) How is HITECH different from HIPAA?
While HIPAA established foundational rules around privacy and security of protected health information among healthcare providers, health plans, and clearinghouses, HITECH builds on HIPAA by incentivizing adoption of health information technology and EHR systems, extending certain HIPAA obligations (such as breach notification and Security Rule compliance) directly to business associates, imposing stronger enforcement through tiered civil monetary penalties with substantially increased amounts, and encouraging meaningful use of digital health records through financial incentives and payment penalties. Healthcare organizations must address both HIPAA and HITECH as integrated components of their regulatory compliance framework.
3) What are the three components of the HITECH Act?
The three major components are: (1) Incentives and promotion of health information technology through meaningful use requirements and financial incentive payments for EHR adoption; (2) Strengthened privacy and security provisions including mandatory breach notification requirements, expanded business associate accountability under HIPAA Security Rule provisions, and patient rights to electronic copies of health information; (3) Expanded enforcement and penalties through a four-tier civil monetary penalty structure that significantly increases fines for violations, with penalties ranging from $100 to $50,000 per violation depending on culpability level, and maximum annual penalties reaching $1.5 million for willful neglect violations.



.svg)
.svg)
.svg)