Most organizations approach cybersecurity as a series of isolated technical decisions—patching vulnerabilities, deploying firewalls, responding to incidents as they occur. This creates a fundamental gap between security operations and enterprise risk management—a disconnect that becomes apparent when cybersecurity threats materialize as business disruptions, financial losses, or regulatory penalties.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), updated in its 2.0 edition released in 2024, is designed for all audiences, industry sectors and organization types, from the smallest schools and nonprofits to the largest agencies and corporations—regardless of their degree of cybersecurity sophistication. In 2026, enterprise-level organizations face escalating cyber risk across expanding attack surfaces, complex supply chains, and increasingly sophisticated threat actors. The CSF provides a structured approach to managing these risks by aligning security controls with business objectives, regulatory requirements, and operational realities.
This article explains what the NIST Cybersecurity Framework is, how its core components function, and how it supports data protection standards and threat mitigation strategies that meet enterprise compliance and security requirements.
What Is CSF?
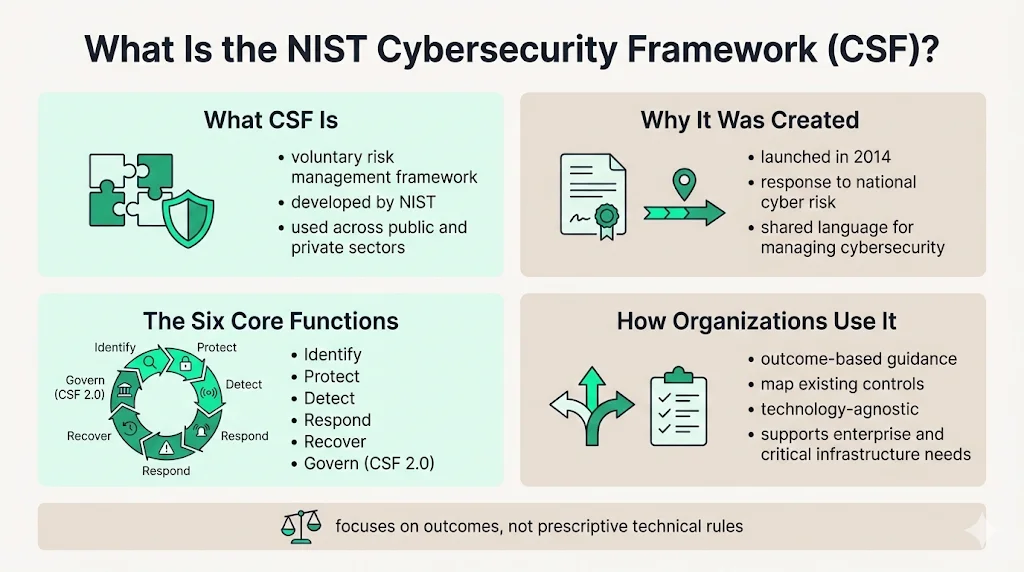
The NIST Cybersecurity Framework (CSF) is a voluntary guidance document for reducing cybersecurity risk, developed by the National Institute of Standards and Technology. NIST is a non-regulatory federal agency within the U.S. Department of Commerce that develops frameworks, standards, and guidelines for risk management and information security across government and private sector organizations.
Originally released in 2014 following a presidential Executive Order to help organizations understand, reduce and communicate about cybersecurity risk, the framework's core is now organized around six key functions: Identify, Protect, Detect, Respond and Recover, along with CSF 2.0's newly added Govern function. While the CSF is voluntary for most organizations, it has become a de facto standard in many industries, particularly for organizations working with federal agencies, critical infrastructure sectors, and enterprises seeking to demonstrate mature cybersecurity programs to stakeholders, investors, and customers.
The framework differs from prescriptive regulatory requirements by offering outcome-based guidance rather than specific technical mandates. Organizations can map their existing security controls to CSF categories and subcategories, creating a consistent structure for risk management regardless of underlying technologies or vendor solutions.
Why Organizations Use the CSF
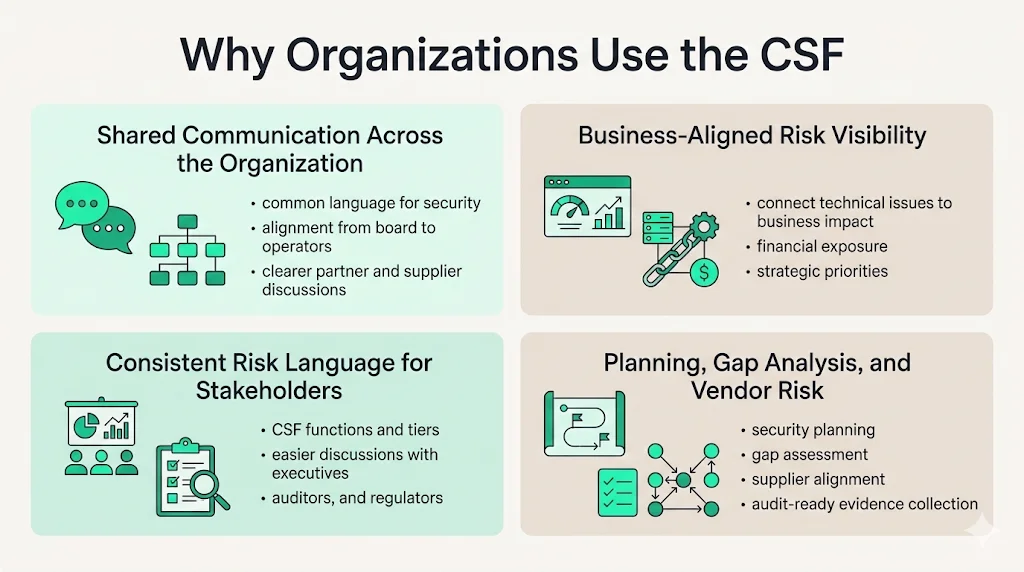
The CSF is particularly useful for fostering internal and external communication at all levels—including across internal teams, from the C-Suite through middle management to those carrying out daily cybersecurity responsibilities—and seeks to improve communication with suppliers and partners while helping organizations integrate cybersecurity-related issues with broader enterprise risk management strategies.
Enterprises adopt the CSF because it provides structured risk visibility across technical and business functions. Security teams can use the framework to inventory assets, document controls, and track remediation efforts against specific outcomes. Simultaneously, executives gain a business-aligned view of cybersecurity risk that connects technical vulnerabilities to operational impacts, financial exposure, and strategic priorities.
The framework creates a common language that translates technical security concepts into business risk terms. When discussing security posture with board members, third-party auditors, or regulatory authorities, organizations reference CSF functions and implementation tiers rather than granular technical specifications. This shared vocabulary enables more productive conversations about risk tolerance, resource allocation, and strategic security investments.
Organizations leverage the CSF for security planning, threat modeling, and vendor risk assessments. The framework's structure facilitates gap analysis by comparing current security posture against target implementation profiles. Supply chain risk management becomes more systematic when organizations require suppliers to demonstrate alignment with specific CSF categories. During security audits, the CSF provides a reference architecture for evidence collection and control validation.
Core Components of the CSF
The CSF Core
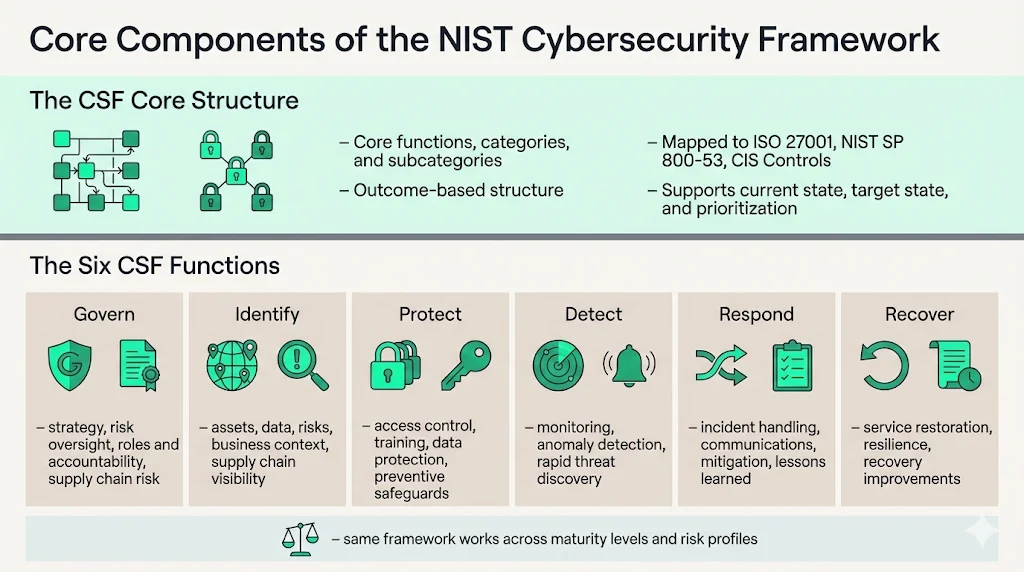
The framework's core is organized around six key functions that, when considered together, provide a comprehensive view of the life cycle for managing cybersecurity risk. Each function contains categories representing cybersecurity outcomes, which further break down into subcategories defining specific technical or management activities. Informative references connect these subcategories to control frameworks including ISO 27001, NIST SP 800-53, and CIS Controls, enabling cross-framework mapping and compliance alignment.
The core structure allows organizations to assess current capabilities, define target states, and prioritize implementation efforts based on risk assessment and business requirements. Organizations operating at different maturity levels can apply the same framework architecture while implementing controls appropriate to their specific risk environment and resource constraints.
The Framework Functions
CSF 2.0 organizes cybersecurity activities into six functions: Govern, Identify, Protect, Detect, Respond, and Recover. This expanded structure reflects the evolution of enterprise cybersecurity from operational activities to integrated risk governance.
Govern – This new function, with an expanded focus on governance, encompasses how organizations make and carry out informed decisions on cybersecurity strategy. The Govern function establishes organizational context, defines cybersecurity strategy and supply chain risk management, clarifies roles and responsibilities, sets policies, and provides oversight of cybersecurity programs. The governance component emphasizes that cybersecurity is a major source of enterprise risk that senior leaders should consider alongside others such as finance and reputation. For enterprises, this function codifies executive accountability and connects security investments to business risk tolerance and strategic objectives.
Identify – Understanding systems, assets, data, and risks across the enterprise environment. This function encompasses asset management, business environment analysis, governance structures, risk assessment, risk management strategy, and supply chain risk visibility. Organizations use Identify to establish the foundation for all subsequent security activities by documenting what requires protection and where risks concentrate.
Protect – Implementing safeguards and security controls to limit or contain potential cybersecurity events. Protect includes identity management and access control, awareness and training, data security, information protection processes, protective technology, and maintenance activities. These controls reduce the likelihood of successful attacks by hardening systems, restricting access, and implementing defense-in-depth architectures.
Detect – Finding threats and anomalies quickly through continuous monitoring and detection processes. This function covers anomalies and events identification, security continuous monitoring, and detection process maintenance. Effective detection capabilities reduce attacker dwell time and enable organizations to respond before significant damage occurs.
Respond – Taking action when incidents occur through response planning, communications, analysis, mitigation, and improvement activities. Organizations document incident response procedures, establish communication protocols with stakeholders, analyze incident scope and impact, contain threats, and capture lessons learned for process improvement.
Recover – Restoring services and learning from events through recovery planning, improvement processes, and communications. This function addresses business continuity, disaster recovery, incident recovery procedures, and organizational resilience. Recovery activities restore normal operations while implementing lessons learned to prevent recurrence.
How CSF Supports Data Protection Standards
Mapping CSF to Data Protection Needs
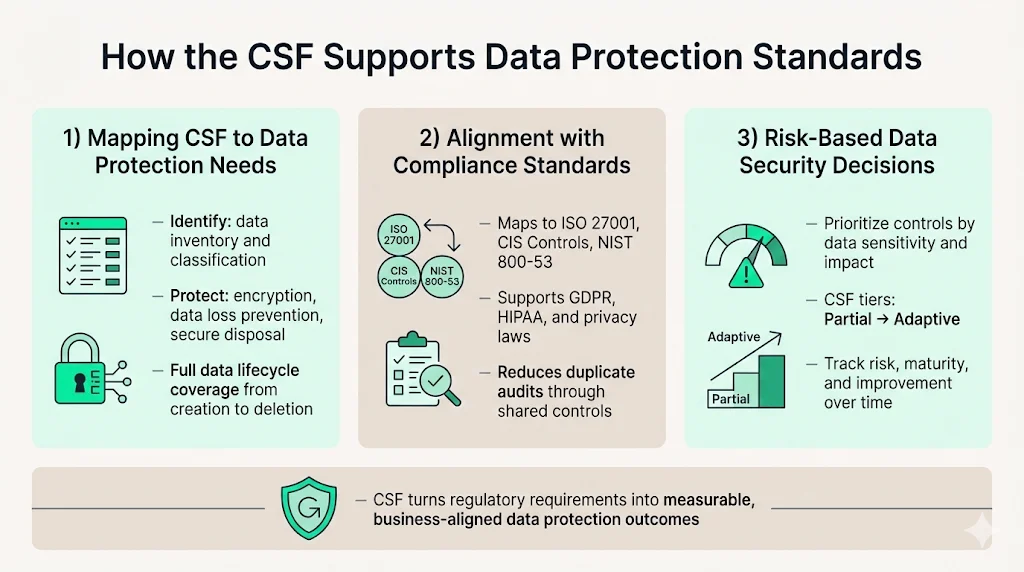
The Protect function within CSF 2.0 includes data security categories that directly address enterprise data protection requirements. Subcategories specify outcomes for data classification, encryption at rest and in transit, data loss prevention, secure disposal, and integrity verification. Organizations map these outcomes to their specific data assets—customer information, intellectual property, regulated data sets—and implement controls proportional to data sensitivity and business impact.
The Identify function establishes data inventory and classification as foundational activities. Before implementing protection measures, organizations must understand what data they possess, where it resides, who accesses it, and what regulatory or contractual obligations apply. This systematic data discovery enables risk-based security decisions rather than uniform protection approaches that either over-invest in low-risk data or under-protect sensitive information.
Data protection within the CSF context extends beyond technical controls to include data governance policies, retention schedules, access management procedures, and breach response protocols. This comprehensive approach addresses the full data lifecycle from creation through disposal, ensuring consistent protection regardless of where data moves within enterprise systems or supply chains.
Aligning with Compliance and Security Standards
The framework integrates better with other security standards, including CIS Controls, ISO 27001, and NIST 800-53. Organizations pursuing ISO 27001 certification can map their Information Security Management System (ISMS) controls to CSF subcategories, demonstrating how their security program satisfies multiple frameworks simultaneously. This cross-mapping reduces redundant audit efforts and enables organizations to leverage CSF implementation toward compliance with sector-specific regulations.
For data protection specifically, CSF alignment supports GDPR data processing principles, HIPAA safeguards for protected health information, and state privacy law requirements. Organizations document how CSF controls implement specific regulatory requirements—for example, mapping access control subcategories to GDPR Article 32 security measures or HIPAA's access control specifications. This systematic approach transforms abstract regulatory language into concrete security outcomes with measurable implementation evidence.
The CSF's informative references provide direct mappings between framework subcategories and authoritative security standards. Organizations can reference these mappings during audits, regulatory examinations, or customer security assessments to demonstrate comprehensive security programs that satisfy multiple compliance obligations through unified control implementations.
Enabling Risk-Based Decisions on Data Security
The CSF architecture supports risk-based prioritization by connecting security outcomes to business impact assessments. Organizations evaluate which data protection controls warrant investment based on data sensitivity, threat likelihood, potential business consequences, and regulatory exposure. This analytical approach replaces checklist compliance with strategic security resource allocation.
CSF implementation tiers—Partial, Risk Informed, Repeatable, and Adaptive—provide maturity benchmarks for continuous improvement. Organizations measure current data protection capabilities against tier definitions, establish target maturity levels aligned with business risk tolerance, and track progress through successive assessments. This structured improvement cycle enables organizations to demonstrate measurable security maturity advancement to executives, board members, and external stakeholders.
Risk registers document identified data security risks, map them to relevant CSF categories, track control implementation status, and measure residual risk after controls deploy. This systematic risk tracking provides audit evidence, supports executive risk reporting, and enables data-driven decisions about accepting, transferring, or further mitigating specific risks.
Implementation in Enterprise Context
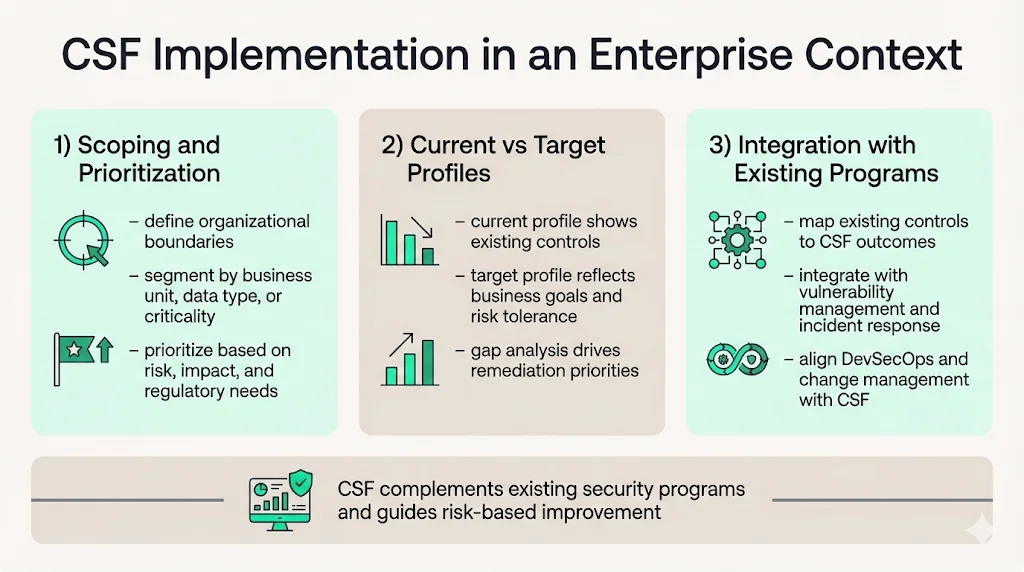
Scoping and Prioritization
Enterprise CSF implementation begins with environmental scoping—defining organizational boundaries, identifying critical systems and data assets, and establishing risk priorities. Organizations segment their environment by business unit, data classification, regulatory scope, or system criticality, then apply CSF guidance proportionally to each segment's risk profile.
Prioritization decisions consider threat intelligence, vulnerability assessments, business impact analysis, and regulatory requirements. Critical infrastructure supporting revenue-generating operations receives higher implementation priority than back-office systems with limited business exposure. Data sets subject to regulatory protection requirements warrant comprehensive control implementation regardless of system criticality.
Current Profile vs Target Profile
Organizations should create a personalized organizational profile and compare its current and target profiles; by comparing these profiles, an organization can identify business objectives, gaps, and necessary actions to improve its cybersecurity posture. The current profile documents existing security capabilities mapped to CSF categories and subcategories, establishing a baseline assessment of organizational cybersecurity maturity.
Target profiles define desired future states based on business objectives, risk tolerance, threat environment, and resource availability. Gap analysis between current and target profiles identifies specific control deficiencies, prioritizes remediation activities, and establishes measurable improvement objectives. Organizations update profiles periodically to reflect control implementations, emerging threats, business changes, or regulatory developments.
Integrating with Existing Security Programs
The CSF enhances rather than replaces existing security controls and programs. Organizations map current vulnerability management, access control, incident response, and security monitoring capabilities to CSF categories, identifying where existing controls satisfy framework outcomes and where gaps require additional investment.
DevSecOps practices integrate with CSF through secure software development subcategories within the Govern function. Security automation, continuous integration/continuous deployment pipelines, and infrastructure-as-code implementations provide technical controls that satisfy multiple CSF outcomes while maintaining development velocity. Risk governance processes incorporate CSF assessments into change management, ensuring new systems and services satisfy established security requirements before production deployment.
CSF and Threat Mitigation in Practice
Following the CSF functions systematically reduces security gaps by ensuring organizations address all phases of the security lifecycle. The Identify function prevents threats stemming from unknown assets or unassessed risks. Protect controls reduce attack surface and increase attacker costs. Detection capabilities shorten incident detection timelines. Response procedures contain damage and prevent lateral movement. Recover processes restore operations while implementing lessons learned.
Organizations operationalize CSF-based threat mitigation through documented playbooks aligned with framework functions. Detection alerts trigger response procedures mapped to specific incident categories. Response actions reference recovery procedures for affected systems. Post-incident reviews identify control gaps, feeding back into Identify and Protect improvements. This continuous improvement cycle progressively strengthens security posture against evolving threats.
Enterprise breach preparation exemplifies CSF integration across functions. Identify activities document critical data locations. Protect controls implement data encryption and access restrictions. Detecting capabilities monitor for data exfiltration indicators. Response playbooks define breach notification procedures, forensic investigation protocols, and stakeholder communications. Recovery processes restore compromised systems, rotate credentials, and implement additional controls addressing attack vectors. This comprehensive preparation transforms reactive incident response into systematic breach management aligned with regulatory requirements and business continuity objectives.
Benefits for Enterprise Clients
Organizations implementing the CSF gain several measurable advantages. Security investments align with documented business risks rather than vendor-driven technology acquisitions or compliance theater disconnected from actual threat mitigation. Executive leadership understands cybersecurity risk in business terms, enabling informed resource allocation decisions and strategic security program support.
Audit readiness improves through structured evidence collection mapped to CSF categories. Compliance programs track control implementation status, document risk acceptance decisions, and measure security maturity progression against established benchmarks. Organizations demonstrate comprehensive security programs to customers, regulators, and business partners through CSF profile documentation rather than disparate control lists lacking strategic context.
Communication between technical security teams and non-technical stakeholders becomes more productive when discussions reference CSF functions and outcomes rather than technical implementation details. Board members evaluate cybersecurity risk using the same framework that guides operational security decisions. Business unit leaders understand how security controls protect their specific operations. Third-party risk assessments compare vendor security capabilities against consistent CSF criteria.
Challenges and Considerations
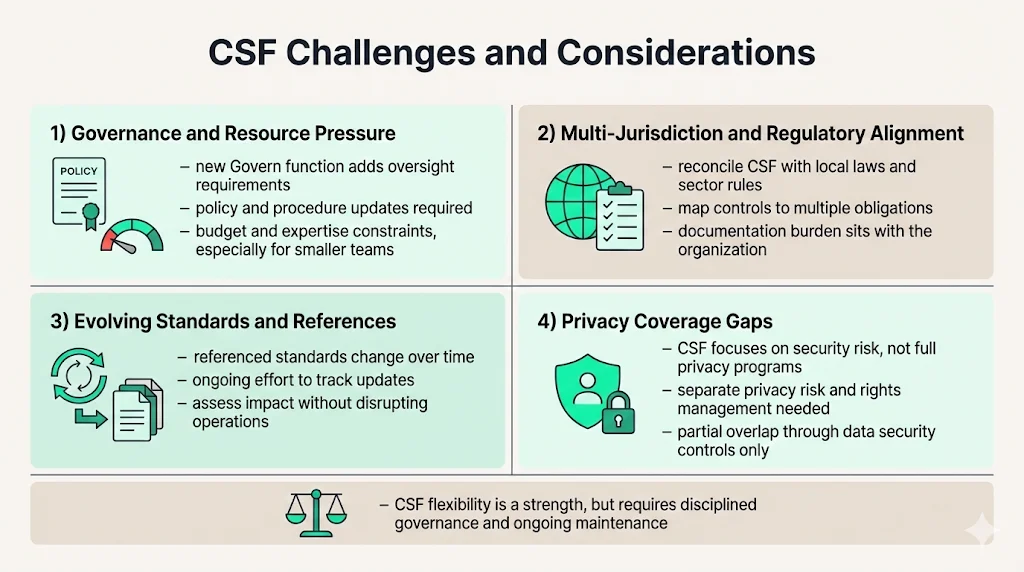
The addition of new elements, specifically the Govern function, necessitates a reassessment of potential restructuring on governance policies and procedures; adding new procedures and policies may be daunting for organizations, especially small and medium-sized enterprises that may not have the budget, resources, or cybersecurity expertise to comply with the framework. Enterprises face resource constraints balancing CSF implementation against operational security demands, competing compliance requirements, and technology modernization initiatives.
Organizations operating across multiple regulatory jurisdictions must reconcile CSF guidance with region-specific data protection requirements, sector regulations, and contractual obligations. The framework provides flexibility for these adaptations, but organizations bear responsibility for mapping CSF outcomes to applicable legal requirements and documenting how controls satisfy multiple obligations simultaneously.
Standards referenced by NIST CSF change over time, creating difficulties for organizations aligning with both NIST CSF standards and other cybersecurity standards; when NIST releases documentation with references and helpful resources, the underlying standards may change after publication, and when pointing to a community that is constantly changing, it becomes difficult to maintain current references. Enterprises must establish processes for monitoring framework updates, assessing impacts on current implementations, and incorporating relevant changes into security programs without disrupting operations.
Privacy frameworks present additional integration considerations. While CSF addresses cybersecurity risk, organizations must separately address privacy risk assessments, data processing limitations, and individual rights management required by comprehensive privacy regulations. The CSF provides partial coverage of these requirements through data security controls but does not constitute a complete privacy management framework.
Conclusion
In 2026, enterprises require systematic approaches to cybersecurity that connect technical controls to business risk management, regulatory compliance, and operational resilience. The NIST Cybersecurity Framework provides a voluntary structure organizations can use to understand, assess, prioritize, and communicate cybersecurity risks, fostering communication across internal teams and with external stakeholders while integrating cybersecurity with enterprise risk management strategies.
The CSF translates abstract security concepts into concrete outcomes organizations can implement, measure, and continuously improve. Rather than treating compliance as documentation exercises disconnected from actual security, organizations using the framework build genuine protective capabilities that produce regulatory compliance as a natural outcome of mature security operations. This approach addresses both immediate threat mitigation requirements and long-term strategic security objectives aligned with business goals.
FAQ Section
1) What is CSF?
CSF stands for the National Institute of Standards and Technology Cybersecurity Framework—a voluntary guidance document that organizations use to manage and reduce cybersecurity risk through systematic identification, protection, detection, response, and recovery activities aligned with business objectives and regulatory requirements.
2) What are the CSF functions?
The CSF core is organized around six functions: Govern, Identify, Protect, Detect, Respond, and Recover. Govern establishes cybersecurity strategy and oversight. Identify documents assets and risks. Protect implements security controls. Detectives find threats and anomalies. Respond addresses incidents when they occur. Recover restores operations and captures lessons learned.
3) Is the CSF mandatory?
The NIST CSF is voluntary for private sector organizations. However, certain regulations, federal contracts, or industry requirements may mandate CSF adoption or alignment. Organizations in critical infrastructure sectors face regulatory expectations to implement cybersecurity frameworks, and many enterprises adopt the CSF to demonstrate security program maturity to customers, investors, and business partners regardless of formal mandates.
4) Who uses the CSF?
Organizations of all types use the CSF, including small businesses, enterprise risk managers, and organizations seeking to secure their supply chains. Federal agencies, government contractors, critical infrastructure operators, financial services firms, healthcare organizations, and technology companies implement the framework to structure risk management programs and satisfy regulatory or contractual security requirements.
5) How does the CSF support data protection?
The Identify and Protect functions include specific categories and subcategories addressing data security throughout its lifecycle. Organizations use these outcomes to classify sensitive data, implement encryption and access controls, establish data loss prevention measures, and document data protection procedures. The framework also maps to data protection standards including ISO 27001, GDPR technical measures, and HIPAA safeguards, enabling organizations to demonstrate comprehensive data security programs satisfying multiple regulatory requirements through unified control implementations.



.svg)
.svg)
.svg)