Most organizations discover security deficiencies during audits and assessments—unpatched systems, incomplete access controls, missing documentation. This reality creates an immediate challenge: regulatory frameworks and enterprise clients demand robust security, yet achieving perfection before authorization or contract execution is rarely feasible. Organizations need a systematic method to document gaps, commit to remediation, and maintain accountability throughout the correction process.
A Plan of Action and Milestones (POA&M) is a document that identifies tasks that need to be accomplished, details resources required to accomplish the elements of the plan, milestones for meeting the tasks, and the scheduled completion dates for the milestones. In practical terms, it functions as a structured corrective-action plan—a detailed roadmap tracking security weaknesses, control deficiencies, remediation strategies, assigned responsibility, and completion timelines. Security practitioners often describe it as a disciplined "to-do list" for security remediation, distinguished from informal tracking by its formal structure, accountability mechanisms, and integration with compliance frameworks.
The terminology varies: POA&M, POAM, and POA&Ms all reference the same fundamental concept. Organizations encounter these variations across different regulatory contexts and vendor documentation, but the underlying requirements remain consistent.
Why POA&M Exists—The Purpose and Need
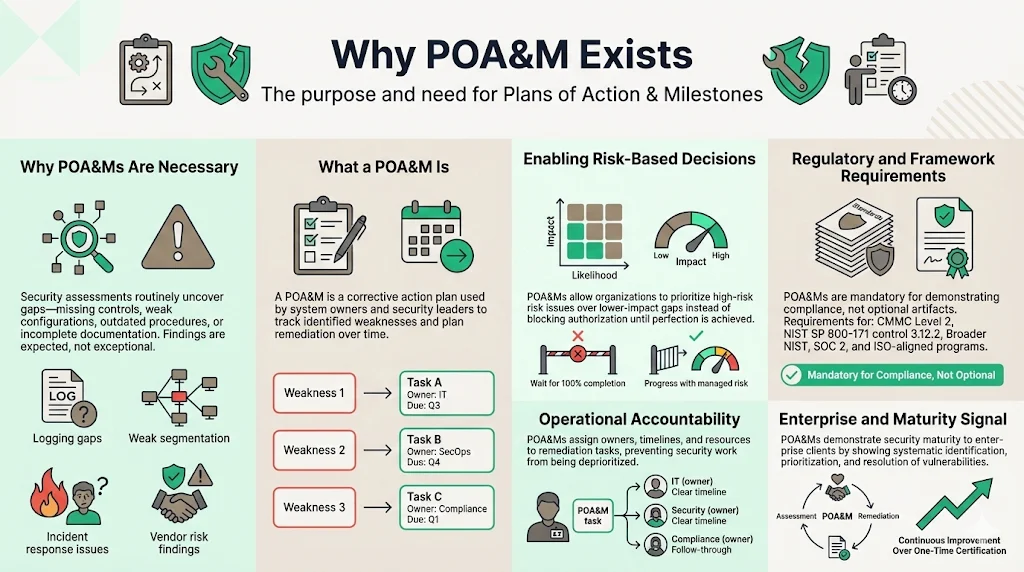
A POA&M is a corrective action plan that tracks system weakness and allows System Owners and Information System Security Officers to create a plan to resolve the identified weaknesses over time. In real-world security assessments—internal audits, third-party evaluations, vulnerability scans—discovering gaps is the norm rather than the exception. Organizations implementing SOC 2 controls, ISO 27001 requirements, or NIST-based frameworks inevitably identify areas requiring improvement: incomplete logging configurations, insufficient network segmentation, outdated incident response procedures, missing vendor risk assessments.
Rather than delaying authorization or certification until every control achieves full implementation—a timeline potentially extending 12-18 months—POA&M documentation provides a formal mechanism to acknowledge gaps while demonstrating commitment to systematic remediation. This approach supports risk-based decision-making: Organizations take a risk management approach to ensure that critical and high-impact weaknesses take precedence over lower security weaknesses.
For CMMC Level 2 certification, organizations must establish and maintain a formal POA&M process to track and manage the resolution of deficiencies in the implementation of NIST SP 800-171 security requirements. NIST SP 800-171 security control 3.12.2 requires organizations to develop and implement plans of action designed to correct deficiencies and reduce or eliminate vulnerabilities in organizational systems. Without POA&M documentation, organizations cannot demonstrate compliance with these explicit requirements.
Beyond regulatory mandates, POA&M documentation serves operational purposes. It establishes transparency and accountability by assigning each remediation task an owner, resource allocation, and timeline—reducing the risk that critical security work gets deprioritized amid competing business demands. For organizations pursuing enterprise contracts, POA&M documentation demonstrates security maturity: the capacity to identify vulnerabilities systematically, prioritize remediation based on risk, and maintain continuous improvement rather than treating security as a one-time project.
What Goes into a POA&M—Key Components
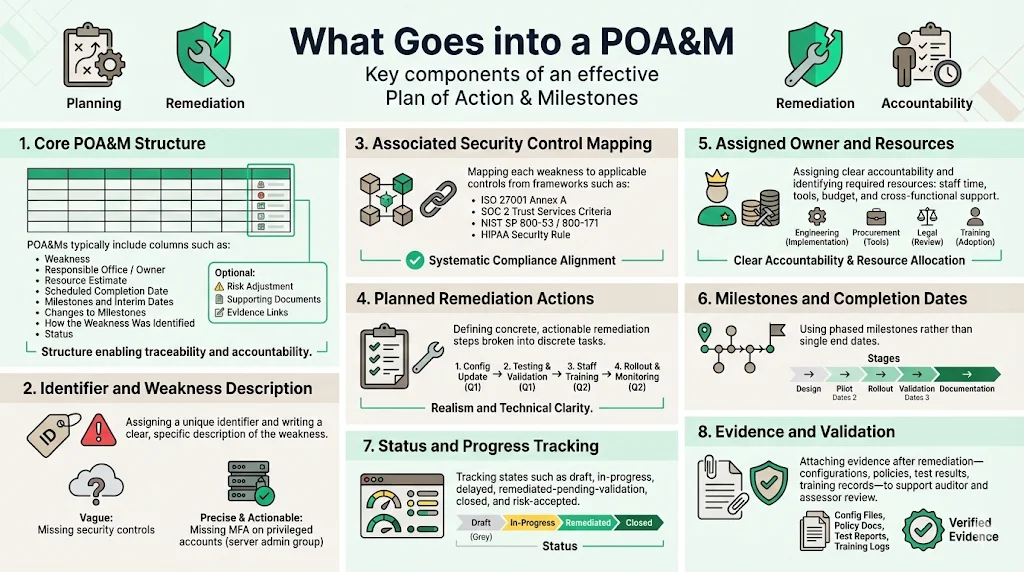
POA&M templates typically include a minimum of eight columns: Weakness; Responsible Office/Organization; Resource Estimate; Scheduled Completion Date; Milestones with Interim Completion Dates; Changes to Milestones; How was the Weakness Identified; and Status, with many POAMs also including columns for Risk Adjustments and Supporting Documents. Understanding these components ensures POA&M documentation serves its intended purpose rather than becoming performative paperwork.
Identifier and Description: Each entry receives a unique identifier linking to the specific vulnerability, control deficiency, or finding. The description articulates the security weakness in sufficient detail for remediation teams to understand the technical gap—not merely stating "access control deficiency" but specifying "privileged access accounts lack multi-factor authentication, creating unauthorized access risk to production database environments."
Associated Security Control: The POA&M identifies individual risks, including weakness description, risk statement, and other risk characteristics. Entries map to specific control requirements from applicable frameworks—ISO 27001 Annex A controls, SOC 2 Trust Services Criteria, NIST SP 800-53 control families, HIPAA Security Rule implementation specifications. This mapping ensures remediation efforts address compliance obligations systematically.
Planned Remediation Actions: Each weakness should be matched with specific, actionable corrective measures that fully address the underlying vulnerability, broken into discrete milestones with realistic completion dates that consider technical complexity, resource requirements, and organizational constraints. Vague statements like "improve access controls" provide insufficient guidance; effective remediation plans specify concrete actions: "implement Okta MFA for all privileged accounts by Q2 2026, configure hardware token authentication for administrative access to production systems, establish exception approval workflow for temporary MFA exemptions."
Assigned Owner and Resources: Successful remediation requires clear resource allocation and responsibility assignment, with each action item identifying the specific individual accountable for implementation along with the resources—budget, personnel, tools—necessary for successful completion, preventing situations where vulnerabilities remain unaddressed because ownership is ambiguous. This accountability extends beyond individual names to encompass cross-functional requirements: engineering time for technical implementation, procurement budget for security tools, legal review for policy documentation, training resources for awareness programs.
Milestones and Completion Dates: Complex remediation efforts require phased implementation. Rather than setting a single distant deadline, effective POA&M entries establish interim milestones: initial design completion, pilot implementation, production rollout, validation testing, documentation finalization. These milestones enable progress tracking and early identification of schedule risks.
Status and Progress Tracking: Each POA&M entry includes risk information, plan for remediation, and status. Organizations typically track statuses including draft, in-progress, delayed, remediated-pending-validation, closed, and risk-accepted. Mature POA&M processes integrate automated tracking through GRC platforms or dedicated tools, ensuring real-time visibility into remediation progress.
Evidence and Documentation: Once remediation completes, organizations attach supporting evidence—configuration screenshots, policy documentation, penetration test results, training completion records—enabling auditors and assessors to verify control effectiveness without requiring full re-testing.
How POA&M Fits into Broader Security and Compliance Workflows
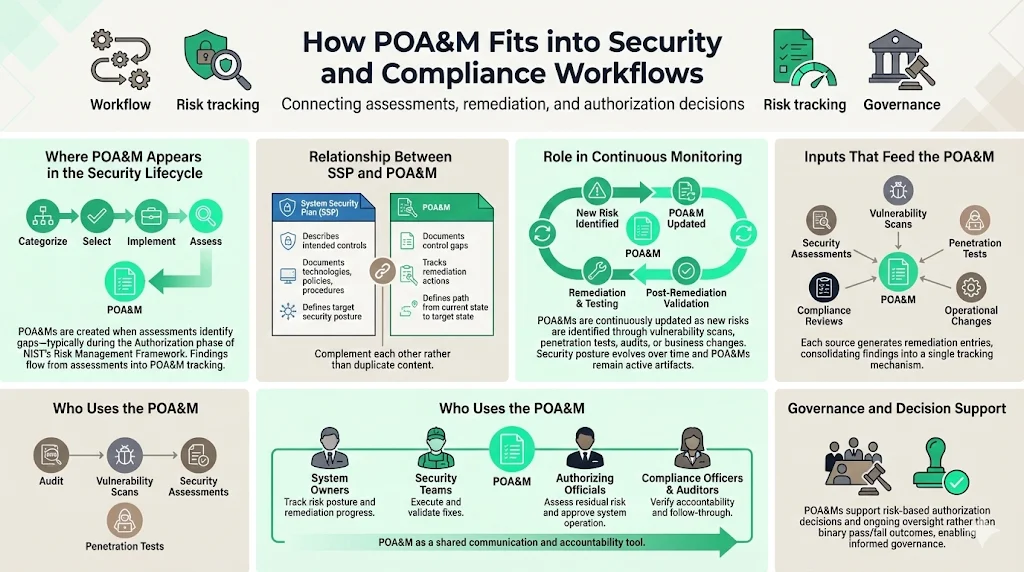
The POA&M model is used by anyone responsible for tracking and reporting compliance issues or risks identified for a system, supporting details typically associated with POA&M including source of discovery, risk description and recommendations, remediation planning and tracking, and disposition status. Within NIST's Risk Management Framework, POA&M creation typically occurs during the Authorization stage when assessments identify controls not yet fully implemented or effective.
POA&M documentation works alongside System Security Plans (SSPs). Defense contractors seeking compliance with NIST 800-171 and CMMC must have a System Security Plan that describes the technologies, policies and procedures they are implementing to meet the 110 NIST controls. While SSPs document intended security controls and implementation approaches, POA&M documentation tracks where those controls fall short of full implementation or require improvement. The two documents create complementary perspectives: SSPs describe your target security posture, POA&Ms document the path from current state to target state.
This relationship extends to continuous monitoring. Continuous monitoring practitioners consume the POA&M as part of monitoring the system's security posture. As vulnerability scans identify new weaknesses, penetration tests reveal additional gaps, or business changes introduce new risk scenarios, organizations add corresponding POA&M entries. Security is never "complete"—new vulnerabilities emerge constantly through software updates, infrastructure changes, evolving threat landscapes, and expanding business operations.
System owners consume the POA&M to understand the risk posture of their system and ensure remediation activities are occurring as planned, while Authorizing Officials consume the POA&M in the adjudication of a system as part of approving an authorization to operate, and periodically to ensure the system continues to operate in a secure manner. This makes POA&M documentation a communication vehicle between technical security teams, executive leadership, compliance officers, and external auditors.
Why This Matters for Businesses Selling to Enterprise Clients
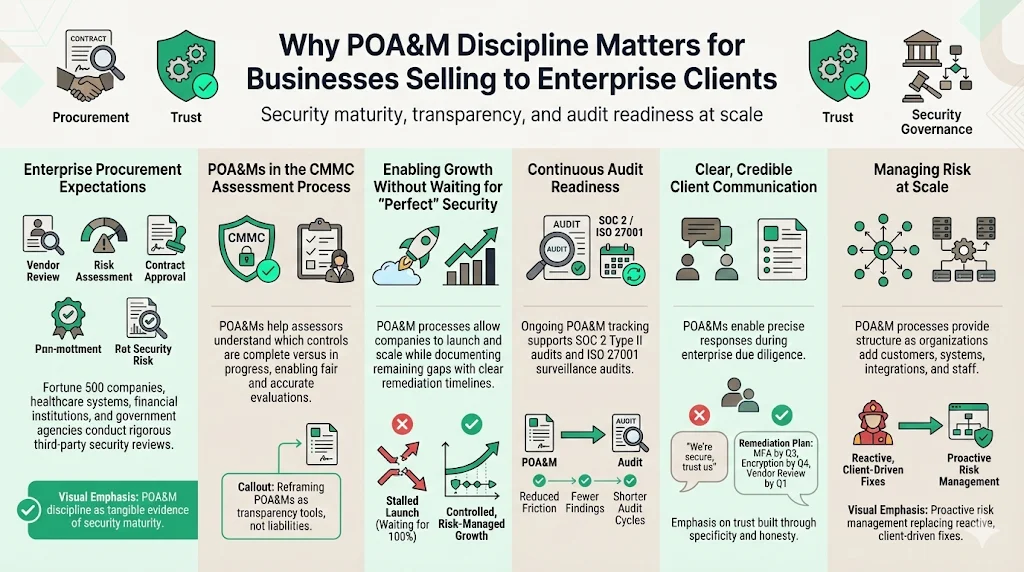
Enterprise procurement teams evaluate vendor security posture before contract execution. Organizations pursuing contracts with Fortune 500 clients, healthcare systems, financial institutions, or government agencies face increasingly rigorous third-party risk assessments. Demonstrating POA&M discipline provides concrete evidence of security maturity.
The CMMC Assessment Process places significant emphasis on POA&Ms as evidence of organizational commitment to security improvement, with POA&M documentation providing context for current security posture and helping assessors understand which controls are fully implemented versus those still in development, allowing assessors to develop a more accurate and fair assessment approach. Rather than appearing as a liability, well-maintained POA&M documentation demonstrates transparency—an organization willing to acknowledge gaps while proving systematic remediation plans.
For startups and fast-growing companies, achieving perfect security before market launch creates untenable delays. POA&M processes offer a pragmatic alternative: implement core security controls immediately, document remaining gaps with clear remediation timelines, and demonstrate to prospective enterprise clients that security deficiencies receive systematic attention rather than being ignored or deprioritized. This approach enables revenue growth while maintaining security discipline.
Audit readiness requires ongoing preparation, not frantic pre-audit scrambling. Organizations conducting annual SOC 2 Type II audits or ISO 27001 surveillance audits maintain continuous POA&M tracking, ensuring auditors can review up-to-date remediation status rather than encountering stale documentation reflecting outdated security posture. This discipline reduces audit duration, minimizes findings, and demonstrates operational maturity.
POA&M documentation enables clear client communication. When enterprise procurement teams ask about specific security controls during due diligence, organizations can reference POA&M entries transparently: "Our vulnerability management process currently relies on monthly scans; we have documented a POA&M item to transition to weekly automated scanning by Q3 2026, with continuous monitoring implementation following in Q4 2026." This specificity builds trust far more effectively than vague assurances or defensive posturing about existing gaps.
As organizations scale—adding customers, systems, integrations, personnel—security complexity compounds. POA&M processes provide the operational discipline necessary to manage evolving risk landscapes systematically rather than reactively addressing security issues only when clients demand evidence or audits reveal deficiencies.
How to Build and Maintain a POA&M—Best Practices
Effective POA&M implementation requires systematic execution:
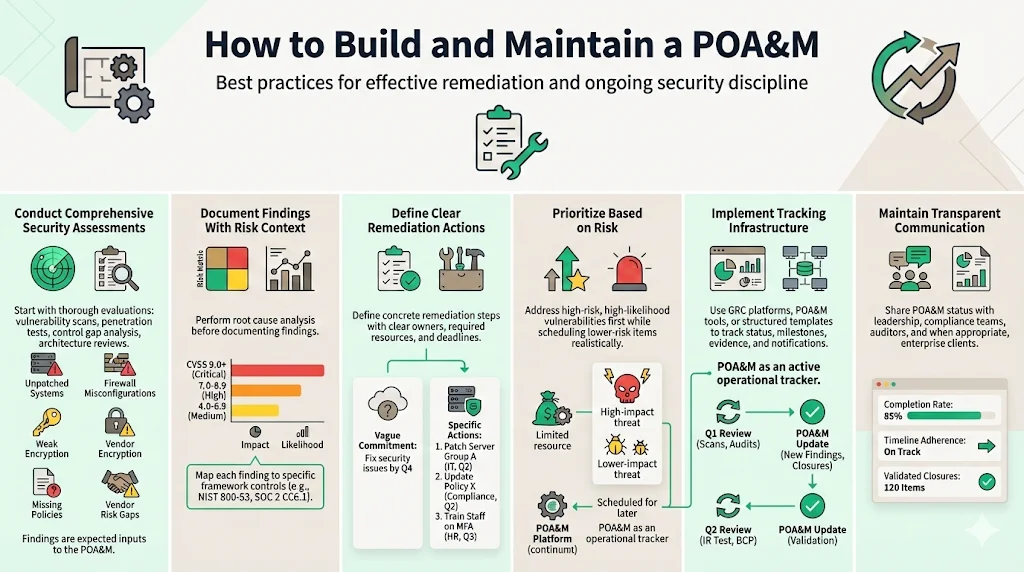
Conduct Comprehensive Security Assessments: Begin with thorough evaluation—vulnerability scanning, penetration testing, control gap analysis against applicable frameworks, security architecture review. Identify both technical vulnerabilities (unpatched systems, misconfigured firewalls, weak encryption) and control deficiencies (missing policies, inadequate training, incomplete vendor risk assessments).
Document Findings with Risk Context: All weaknesses must be examined to determine their root cause prior to documentation in the POA&M, as Root Cause Analysis is an important and effective methodology used to correct information security or privacy weaknesses by eliminating the underlying cause. Categorize findings by severity using CVSS scoring, impact analysis, and likelihood assessment. Map each finding to specific controls or security requirements within your applicable frameworks.
Define Clear Remediation Actions: For each finding, establish concrete remediation steps with assigned ownership, resource requirements, and deadlines. Avoid vague commitments—specify technical implementation details, procurement needs, policy development requirements, and training deliverables.
Prioritize Based on Risk: Critical vulnerabilities affecting production systems with high exploitation likelihood demand immediate remediation; lower-risk issues receive scheduled attention aligned with organizational capacity. This risk-based prioritization ensures limited security resources address the most significant threats first.
Implement Tracking Infrastructure: Utilize GRC platforms, dedicated POA&M tools, or structured spreadsheet templates supporting status updates, evidence attachment, milestone tracking, and automated notifications. Treat POA&M documentation as a live operational tool rather than static compliance artifact.
Integrate into Continuous Security Processes: POA&M functions as a living resource used to document vulnerabilities found when performing vulnerability scans, security assessments, and other reviews such as testing incident response plans and business continuity plans, with any deficiency identified in your security program needing documentation in your POA&M. Schedule regular POA&M reviews—quarterly at minimum—to assess remediation progress, update timelines, add newly identified vulnerabilities, and close completed items with supporting evidence.
Maintain Transparent Communication: Share POA&M status with stakeholders including executive leadership, compliance teams, and when appropriate, enterprise clients and auditors. Demonstrate remediation progress through status reports documenting completion percentages, timeline adherence, and evidence of closed items.
Common Misunderstandings and Pitfalls
Organizations frequently misuse POA&M processes in ways that undermine their value:
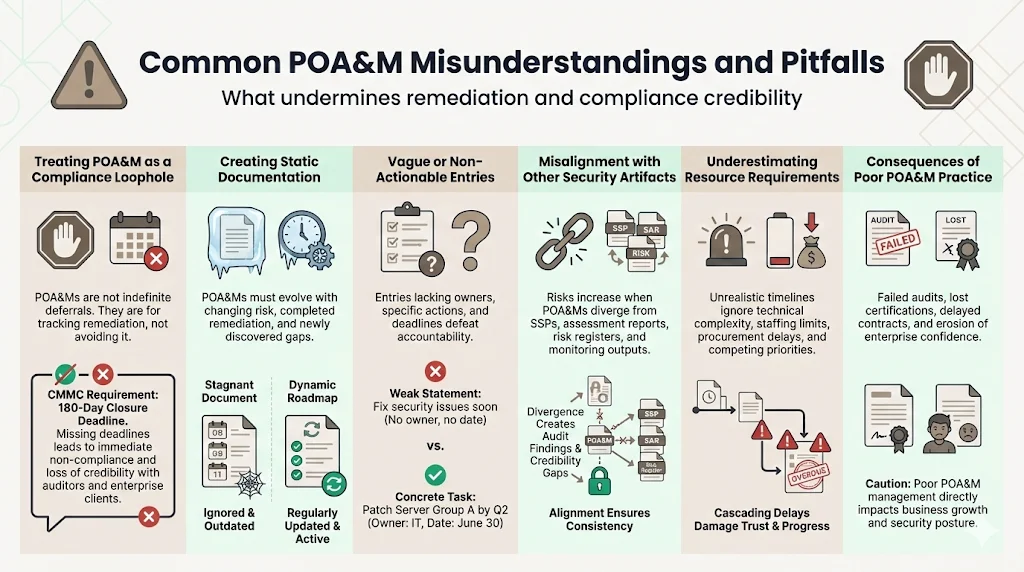
Treating POA&M as Compliance Loophole: Some organizations view POA&M entries as indefinite deferrals—documenting critical gaps without genuine remediation commitment. Under CMMC, POAMs are time-bound with defense contractors having 180 days to close them out in their SSP, and failing to meet that deadline requires starting the CMMC certification process over. Regulators, auditors, and enterprise clients recognize this misuse; leaving critical issues unresolved while claiming POA&M documentation provides cover undermines compliance credibility and client trust.
Creating Static Documentation: Without detailed planning including discrete milestones and realistic completion dates, POA&Ms often become static documents rather than active roadmaps. Security posture evolves constantly—new vulnerabilities emerge, business changes introduce risk, remediation efforts complete. POA&M documentation must reflect this dynamic reality through regular updates, not annual token reviews.
Providing Vague Entries: POA&M items lacking clear owners, specific remediation steps, or concrete deadlines defeat accountability purposes. Entries stating "improve network security" without specifying responsible parties, technical implementation details, resource allocation, or milestone dates provide no actionable guidance and enable indefinite delay.
Failing Documentation Alignment: POA&M documentation must synchronize with SSPs, assessment reports, continuous monitoring outputs, and risk registers. Discrepancies between these documents—POA&M referencing controls not documented in SSPs, assessment findings absent from POA&M tracking, closed POA&M items without supporting evidence—create audit failures and compliance gaps.
Underestimating Resource Requirements: Organizations frequently set unrealistic timelines by failing to account for technical complexity, competing priorities, procurement delays, or staffing constraints. This creates cascading delays, overdue milestones, and credibility damage with stakeholders expecting adherence to documented commitments.
Conclusion
POA&M documentation represents essential infrastructure for tracking and remediating security deficiencies, managing risk systematically, and meeting compliance requirements across frameworks including CMMC, FedRAMP, NIST 800-171, and standards incorporating NIST guidance. Organizations treating POA&M as performative paperwork—documenting gaps without genuine remediation commitment or maintaining static entries detached from operational reality—undermine both compliance credibility and actual security posture.
For businesses targeting enterprise clients, robust POA&M processes differentiate security programs built on operational discipline from those producing compliance theater. Enterprise procurement teams recognize the difference between organizations acknowledging gaps transparently with systematic remediation plans versus those concealing deficiencies or making vague improvement commitments. Well-maintained POA&M documentation demonstrates professionalism, accountability, and proactive security management—qualities enterprise clients demand when entrusting sensitive data and critical operations to third-party vendors.
It is impossible for an information system to ever be 100% secure, but what is important is demonstrating due care and due diligence by implementing contractually mandated requirements. Treat POA&M as part of ongoing security discipline rather than a one-time compliance task. Organizations conducting 6,000+ audits consistently observe that mature security programs maintain continuous POA&M tracking, regular remediation progress reviews, risk-based prioritization, and transparent stakeholder communication. This operational discipline produces both compliance outcomes and genuine security improvement—not compliance manufacturing disconnected from actual risk reduction.
Frequently Asked Questions
1) What is the purpose of a POA&M?
A POA&M helps organizations identify, track, and remediate security weaknesses or control deficiencies systematically. It organizes remediation tasks with assigned responsibility, resource allocation, milestones, and deadlines—ensuring gaps receive systematic attention rather than being ignored amid competing priorities. POA&M documentation supports risk-based prioritization, compliance with regulatory requirements, audit readiness, and transparent communication with stakeholders about security posture and improvement commitments.
2) What does POA&M mean?
POA&M stands for Plan of Action and Milestones. It is a formal document outlining what needs to be accomplished to address security or compliance issues, when remediation will occur, who is responsible for execution, and what resources are required. POA&M documentation is required under multiple regulatory frameworks including CMMC, FedRAMP, NIST 800-171, and standards based on NIST Risk Management Framework guidance.
3) Is it POAM or POA&M?
Both terms refer to the same concept—Plan of Action and Milestones. Some organizations and regulatory documents write it as "POAM" without the ampersand, while others use "POA&M" with the ampersand explicitly included. The terminology variation does not indicate different requirements or document types; both abbreviations reference identical remediation tracking processes.
4) What does POAM stand for?
POAM (or POA&M) stands for Plan of Action and Milestones—a structured document identifying security weaknesses or control deficiencies requiring remediation, detailing specific corrective actions, assigning responsibility and resources, establishing milestones, and tracking progress toward completion. Organizations use POAMs to demonstrate systematic security improvement, meet compliance obligations, and maintain transparency with auditors, regulators, and enterprise clients regarding security posture and remediation commitments.



.svg)
.svg)
.svg)