Most organizations treat third-party vendor relationships as procurement decisions rather than extensions of their own risk surface. This approach creates a fundamental gap between contractual assurances and operational reality—a gap that becomes apparent when incidents occur, audits fail, or regulatory scrutiny intensifies. Organizations engaging extensively with third-party service providers benefit significantly from SSAE 18 audits, which comprehensively evaluate risk management practices across vendor networks, from payroll processors to cloud infrastructure providers.
SSAE 18—Statement on Standards for Attestation Engagements No. 18—is the attestation standard that governs how independent auditors examine and report on internal controls at service organizations. SSAE 18 is a Generally Accepted Auditing Standard produced and published by the American Institute of Certified Public Accountants (AICPA) Auditing Standards Board. Rather than a report vendors distribute to clients, SSAE 18 establishes the framework under which SOC 1, SOC 2, and SOC 3 reports are produced.
This article explains what SSAE 18 is, how it structures attestation engagements for service organizations, why it matters for businesses serving enterprise clients, and how to prepare for audits conducted under this standard. We address attestation standards, service organization controls, internal controls, risk management, regulatory compliance, and the SOC reporting framework—all critical elements for organizations operating in complex vendor ecosystems.
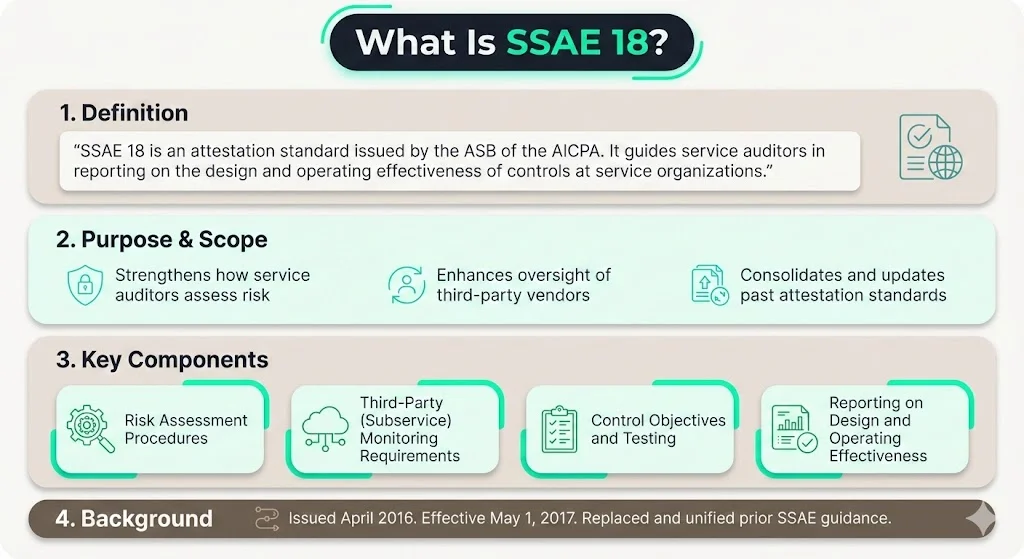
What is SSAE 18? (Definition, Scope, Key Components)
Statement on Standards for Attestation Engagements (SSAE) No. 18, is an attestation standard issued by the Auditing Standards Board (ASB) of the American Institute of Certified Public Accountants (AICPA). Specifically, SSAE 18 is an attestation standard geared towards addressing engagements conducted by practitioners (known as "service auditors") on service organizations for purposes of reporting on the design of controls and their operating effectiveness.
In April 2016, the AICPA published Statement on Standards for Attestation Engagements 18; Attestation Standards: Clarification and Recodification in response to "concerns over the clarity, length, and complexity of its standards", with most sections becoming effective on May 1, 2017. SSAE No. 18 supersedes and integrates most prior SSAE releases into a single clarified standard.
Scope and Purpose
SSAE 18 establishes how auditors conduct attestation engagements to evaluate controls at service organizations—companies whose services impact their clients' (user entities') internal control over financial reporting or trust services criteria. The standard emphasizes internal controls in two dimensions: design suitability and operating effectiveness. Design addresses whether controls, if implemented as described, would adequately mitigate risks. Operating effectiveness addresses whether those controls actually functioned as intended over a specified period.
SSAE 18 is the attestation standard used for reporting on controls at service organizations, one that is part of the American Institute of Certified Public Accountants' Service Organization Control (SOC) reporting framework, which consists of SOC 1, SOC 2, and SOC 3 reports. The standard itself is not a report—service organizations do not "get SSAE 18 certified." Rather, auditors apply SSAE 18 when producing SOC reports that service organizations then provide to clients as evidence of control effectiveness.
SSAE 18 introduced more rigorous requirements around risk assessment, sub-service organization oversight, and management assertions. SSAE 18 reporting – both Type 1 and Type 2 reports – require a description of its "system", along with a written statement of assertion by management, both of which are critically important. Service organizations must formally assert that their description is fairly presented, controls are suitably designed, and (for Type 2 reports) controls operated effectively throughout the observation period.
Key Terms and Types
Attestation engagements under SSAE 18 fall into three service levels, codified in the AT-C sections: examination engagements (providing reasonable assurance), review engagements (providing limited assurance), and agreed-upon procedures engagements (providing findings based on specific procedures). SOC reports are examination engagements.
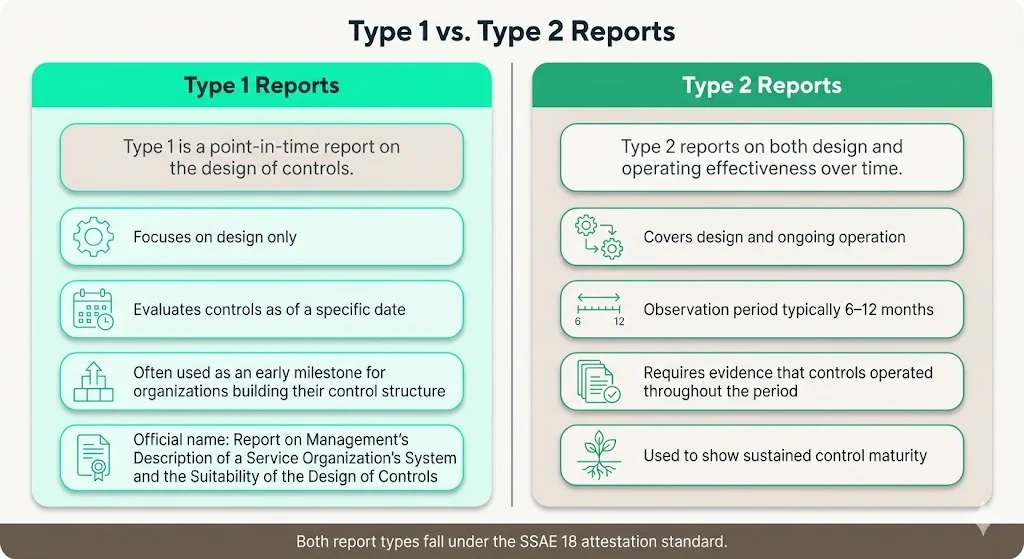
Type 1 vs. Type 2 reports:
- Type 1: A Type 1 report is technically known as a "Report on Management's Description of a Service Organization's System and the Suitability of the Design of Controls", or simply known as a SOC 1 SSAE 18 Type 1 report. Type 1 reports express an opinion on whether controls are suitably designed as of a specific date—a point-in-time assessment.
- Type 2: Type 2 reports express an opinion on both the suitability of design and the operating effectiveness of controls over a defined period (typically 6–12 months). Organizations seeking to demonstrate sustained control maturity pursue Type 2 reports, which require documented evidence of control operation throughout the observation period.
Service organizations and sub-service organizations: A service organization is any entity providing services that affect a user entity's internal controls. Under SSAE 18, these providers are classified as "sub-service organizations." That means they must undergo the same risk assessments to evaluate their organizational controls before the original service organization can receive a SOC attesting that it has the proper systems to manage risk. This carve-in or carve-out approach forces transparency about which controls reside with third parties and whether those third parties have been independently assessed.
Control objectives, internal controls, risk management: Control objectives define what the service organization aims to achieve (e.g., "logical access to production systems is restricted to authorized personnel"). Internal controls are the policies, procedures, and technical mechanisms implemented to achieve those objectives. Risk management encompasses the ongoing identification, assessment, and mitigation of risks that could prevent control objectives from being met.
Why SSAE 18 Matters for Businesses Selling to Enterprise Clients
Enterprise buyers impose rigorous vendor risk management programs. When an organization outsources payroll processing, cloud hosting, or data analytics, it effectively delegates portions of its own control environment to that vendor. If the vendor's controls fail, the enterprise's financial statements, data security, or regulatory compliance may be compromised—yet the enterprise remains accountable to auditors, regulators, and shareholders.
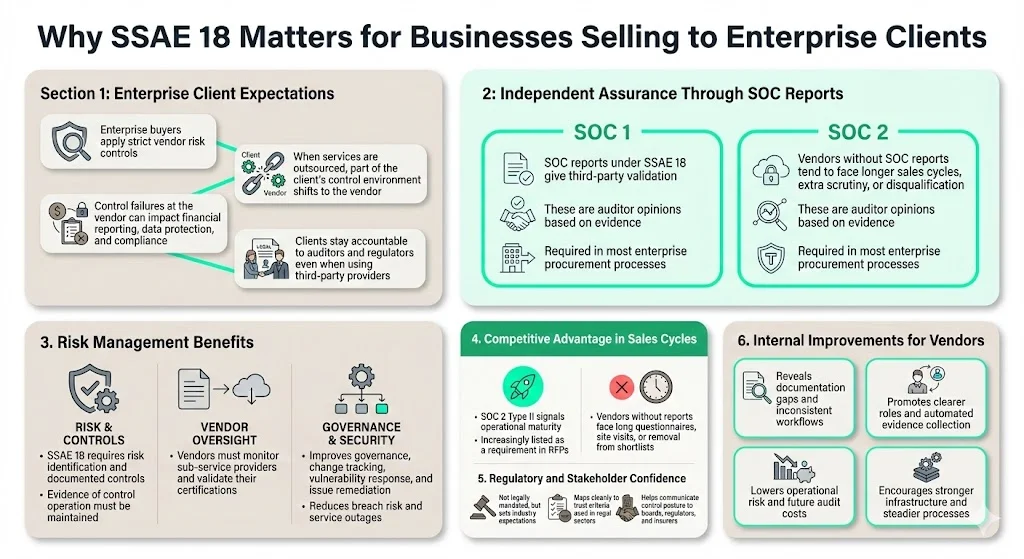
1) From the enterprise client's perspective: A SOC report prepared under SSAE 18 provides independent, third-party verification that a vendor's controls are suitably designed and operating effectively. This assurance is not vendor marketing—it is an auditor's professional opinion based on documented evidence. Enterprises routinely require SOC 1 reports (for vendors affecting financial reporting) or SOC 2 reports (for vendors handling sensitive data or providing critical services) as table stakes in procurement processes. Vendors without such reports face longer sales cycles, contractual restrictions, or outright disqualification from enterprise deals.
2) Risk management benefits: SSAE 18-based audits require service organizations to identify and assess risks, document control activities, maintain evidence of control operation, and monitor sub-service organizations. The auditing standards require that service organizations confirm and re-confirm third-party vendor certifications and controls on an ongoing basis. This discipline forces vendors to mature their operational governance, implement formal change management, track vulnerabilities through automated SLAs, and remediate control deficiencies systematically—practices that reduce breach likelihood, minimize downtime, and improve incident response.
3) Competitive differentiation and procurement requirement: In competitive enterprise sales, a SOC 2 Type II report can differentiate vendors by demonstrating sustained audit readiness and operational maturity. Procurement teams increasingly mandate SOC reports in RFPs. Vendors lacking such reports often face questionnaire burdens, on-site audits by client personnel, or exclusion from shortlists—each representing friction, cost, and lost opportunity.
4) Regulatory compliance and stakeholder assurance: Though SSAE 18 engagements aren't legally mandated, opting for these reports sets an industry benchmark for responsible trust services principles and criteria. Regulated industries (financial services, healthcare, government contractors) often require vendors to demonstrate compliance with frameworks that map directly to SOC 2 Trust Services Criteria. SSAE 18-based reports provide a common language for communicating control posture to regulators, board members, and insurance underwriters.
5) Internal benefits for the vendor: The audit process surfaces gaps in documentation, inconsistent processes, manual workarounds, and shadow IT. Remediation efforts yield better visibility into systems, clearer role definitions, automated evidence collection, and reduced operational risk. Organizations that treat SSAE 18 audits as operational improvements—not compliance theater—build more resilient infrastructure and reduce the cost of future audits.
How SSAE 18 Works: The Process for Service Organizations
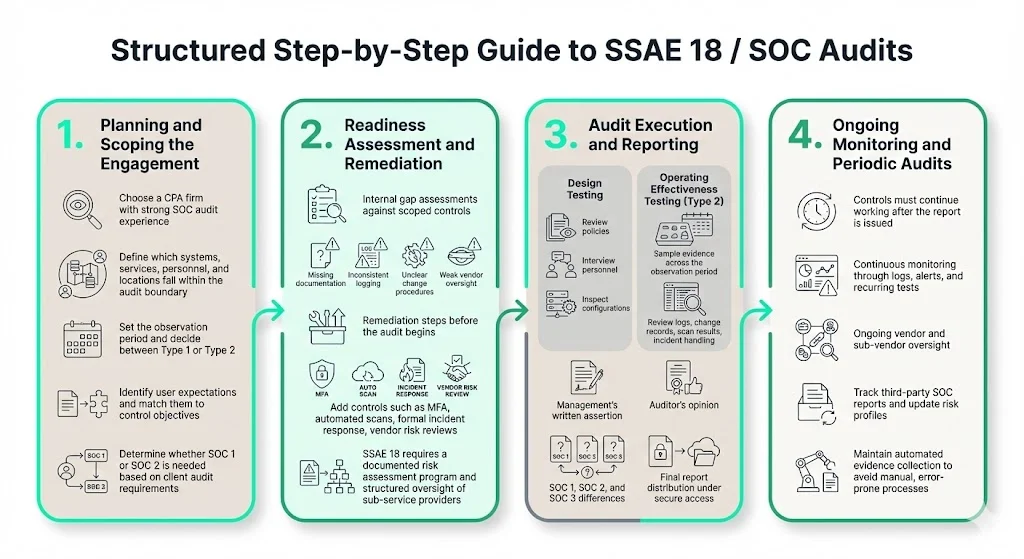
1) Planning and Scoping the Engagement
Service organizations begin by selecting a CPA firm experienced in SOC audits. Auditor selection matters—firms with deep domain expertise in your industry, technology stack, and control objectives reduce friction and improve report quality.
Scoping defines which services, systems, locations, personnel, and sub-service organizations fall within the audit boundary. A cloud provider might scope a SOC 2 engagement to cover its production infrastructure, identity and access management, change management, incident response, and backup procedures—but exclude its marketing website and internal HR systems. Scoping also defines the observation period (e.g., July 1 to December 31) and whether the report will be Type 1 or Type 2.
Control objectives must align with user entity requirements. If enterprise clients expect controls around encryption, vulnerability management, and logical access, those control objectives must be included. Missing control objectives that clients require undermines the report's value.
Mapping user entity expectations to vendor controls requires understanding client audit needs. Publicly traded clients undergoing Sarbanes-Oxley audits may need SOC 1 reports addressing financial reporting controls. Clients subject to GDPR, HIPAA, or PCI DSS may need SOC 2 reports demonstrating confidentiality, availability, and processing integrity.
2) Readiness Assessment and Remediation
Before audit execution, service organizations conduct internal readiness assessments. These gap assessments compare existing controls, documentation, and evidence against the scoped control objectives. Common gaps include incomplete policy documentation, missing access logs, inconsistent change control records, and undocumented sub-service organization oversight.
Remediation addresses control deficiencies before the auditor begins fieldwork. This might involve implementing multifactor authentication, automating vulnerability scans, establishing formal incident response procedures, or documenting vendor risk assessments. Organizations that remediate proactively avoid qualified opinions or control exceptions in the final report.
With this new standard, you are now required to conduct a risk assessment when completing your SOC report. SSAE 18 emphasizes formal risk assessment programs that identify threats, assess likelihood and impact, and document mitigation strategies. Organizations must also establish vendor and sub-vendor oversight programs, including periodic review of sub-service organization SOC reports, contractual commitments to maintain controls, and monitoring of service delivery.
3) Audit Execution and Reporting
The auditor tests control design and (for Type 2) operating effectiveness. Design testing involves reviewing policies, interviewing personnel, and inspecting system configurations. Operating effectiveness testing involves sampling evidence over the observation period—access logs, change tickets, vulnerability scan results, incident records—to confirm controls operated as described.
SSAE 18 reporting requires a description of its "system", along with a written statement of assertion by management. Management's assertion is a formal written statement affirming that the system description is fairly presented, controls are suitably designed, and controls operated effectively (for Type 2). The auditor then expresses an opinion on management's assertion.
The auditor issues the SOC report (SOC 1, SOC 2, or SOC 3) prepared under SSAE 18 standards. SOC 1 reports address controls relevant to user entities' internal control over financial reporting. SOC 2 reports address controls relevant to the Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. SOC 3 reports are general-use summaries suitable for public distribution.
The report is delivered to the service organization, which then distributes it to user entities (clients) under nondisclosure agreements or through secure portals.
4) Ongoing Monitoring and Periodic Audits
SSAE 18-based SOC reports attest to controls over a historical period. Controls must continue operating effectively after report issuance. Continuous monitoring—automated logging, real-time alerting, periodic control testing—ensures sustained audit readiness.
The auditing standards require that service organizations confirm and re-confirm third-party vendor certifications and controls on an ongoing basis. Vendor management and sub-vendor oversight are ongoing obligations, not one-time activities. Service organizations must track sub-service organization SOC reports, assess changes in vendor risk profiles, and update control documentation as systems evolve.
Maintaining evidence—access logs, change control records, vulnerability scan results, incident tickets—requires automated evidence collection integrated into operational workflows. Manual evidence gathering is error-prone, resource-intensive, and unsustainable at scale.
Key Changes from the Prior Standard and Noteworthy Features
The main difference between SSAE 18 and SSAE 16 is that SSAE18 supersedes SSAE 16 as of May 1, 2017. SSAE 16 was primarily designed for SOC 1 audits focused on financial reporting controls. SSAE 18 integrates all prior attestation standards into a clarified, recodified framework that covers SOC 1, SOC 2, and SOC 3 engagements.
Stronger focus on sub-service organizations: SSAE No. 18 requires the consideration of Complementary Subservice Organization Controls, which are the controls for portions of the service organization's systems that are outsourced to third parties. SSAE 18 aims to avoid situations where customers might unwittingly expose their companies to risk because their service organizations partnered with sub-service organizations that didn't have the necessary risk management policies and procedures. This requirement forces transparency about the vendor-of-vendor supply chain and ensures that outsourced controls are independently assessed.
Formalized risk assessment programs: SSAE 18 mandates that service organizations conduct and document formal risk assessments as part of their control environment. This moves beyond static control checklists to dynamic risk management—identifying emerging threats, assessing control gaps, and prioritizing remediation based on risk severity.
Clarification and recodification of attestation sections: The AT section numbers for the superseded SSAEs were recodified in the Professional Standards as section "AT-C" to avoid confusion with the older standards codified as section "AT". This recodification aligns SSAE 18 with the clarity project applied to auditing standards, making the standard more accessible and reducing ambiguity in application.
For businesses, this means: Deeper vendor oversight requirements, stronger documentation expectations, broader audit scope (including sub-service organizations), and more rigorous evidence demands. Organizations that treated SSAE 16 audits as lightweight compliance exercises will find SSAE 18 demands greater operational discipline.
How SSAE 18 Impacts Vendor-Selection and Go-to-Market Strategy for Service Organizations
For vendors selling into enterprise clients, having a SOC report prepared under SSAE 18 is increasingly a table stake—not a differentiator, but a prerequisite for consideration. Enterprise procurement teams routinely require SOC 2 Type II reports as part of vendor risk assessments. Vendors without such reports face prolonged security questionnaires, on-site audits, contractual limitations (such as data residency restrictions or indemnification clauses), or disqualification from procurement processes.
Positioning SSAE 18-based SOC reports: Service organizations should position SOC reports as evidence of operational maturity, not marketing collateral. The report demonstrates that an independent auditor has examined control design and operating effectiveness over a sustained period. This narrative resonates with CISOs, CTOs, and risk committees who evaluate vendor risk exposure.
SOC 1 vs. SOC 2: Clients may request SOC 1 reports (addressing controls relevant to financial reporting) or SOC 2 reports (addressing security, availability, processing integrity, confidentiality, and privacy). Understanding which report type aligns with client needs is critical. A payroll processor serving publicly traded companies needs a SOC 1 report. A SaaS provider handling customer data needs a SOC 2 report. Some organizations pursue both to address diverse client requirements.
Impact on scale, trust, procurement cycles: SOC reports reduce procurement friction by providing standardized, auditor-verified evidence of control effectiveness. This accelerates contract negotiations, reduces legal holdups, and shortens sales cycles. Organizations with mature SOC reporting programs close enterprise deals faster and at higher average contract values than competitors without such assurance.
Practical advice: Start early. Achieving SOC 2 readiness typically requires 4–6 months of preparation, evidence collection, and remediation. Align internal controls and risk assessment programs with Trust Services Criteria or relevant financial reporting control objectives. Select an auditor with domain expertise in your industry and technology stack. Communicate proactively with clients about report scope, observation period, and control objectives—transparency builds trust.
Common Pitfalls and Challenges with SSAE 18 / SOC Audit Readiness
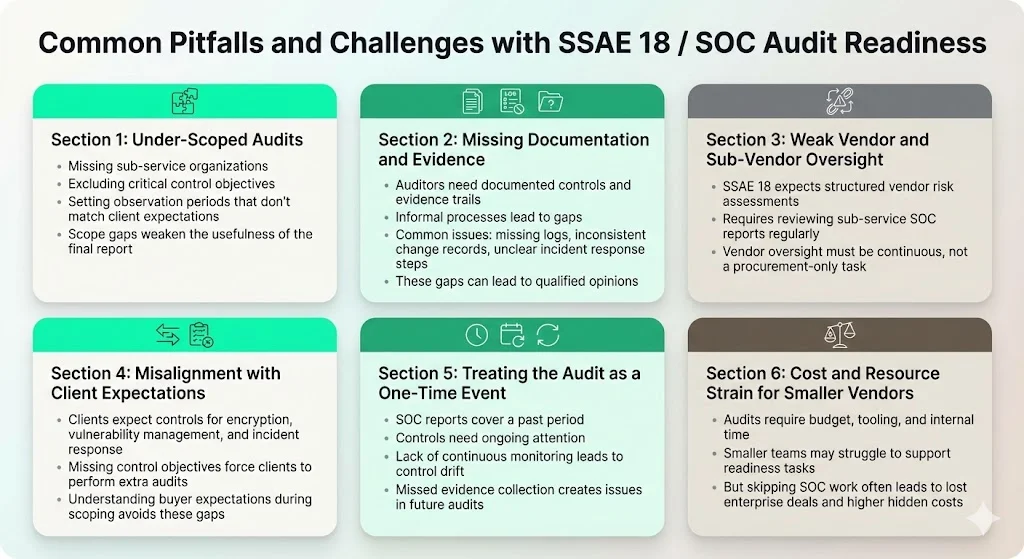
1) Under-scoped audits: Organizations often exclude sub-service organizations from audit scope, omit critical control objectives, or define observation periods that misalign with client expectations. Under-scoping undermines report value. If a cloud provider excludes its infrastructure-as-a-service vendor from scope, clients cannot rely on the report for complete assurance.
2) Lack of documented controls and missing evidence: Auditors require documented policies, procedures, and evidence trails. Organizations with informal processes, tribal knowledge, or manual workflows struggle to produce evidence. Missing access logs, incomplete change control records, or undocumented incident response procedures result in qualified opinions or control exceptions.
3) Poor vendor and sub-vendor oversight: SSAE 18 requires formal vendor risk assessments, monitoring of sub-service organization SOC reports, and documentation of vendor controls. Organizations that treat vendor management as a procurement function—rather than an ongoing risk management discipline—fail this requirement.
4) Misalignment between enterprise buyer expectations and report scope: Clients expect controls addressing specific risks (e.g., encryption at rest and in transit, vulnerability management, incident response). If the SOC report omits these control objectives, clients conduct supplementary audits or impose contractual restrictions. Understanding client expectations before scoping the engagement is critical.
5) Assuming one audit is enough: SOC reports attest to historical control effectiveness. Organizations must maintain controls, collect evidence, and monitor risks continuously. Treating the audit as a one-time project—rather than an operational discipline—leads to control drift, failed subsequent audits, or incidents that contradict the report's assurances.
6) Cost and resource implications for smaller vendors: SOC audits require investment in auditor fees, remediation efforts, evidence collection tooling, and personnel time. Smaller vendors may struggle to justify the cost. However, the alternative—losing enterprise deals or accepting unfavorable contract terms—often carries higher long-term cost.
Best Practices for Service Organizations Preparing for SSAE 18-Based SOC Reports
Start with a readiness assessment early. Engage an auditor or consultant to conduct a gap assessment 6–9 months before the target audit date. Identify control deficiencies, missing documentation, and evidence gaps while time remains for remediation.
Map services to control objectives relevant to enterprise clients. Understand what enterprise buyers expect. If clients need assurance around data encryption, vulnerability management, and incident response, ensure those control objectives are in scope.
Build a formal vendor and sub-vendor oversight program. Document vendor risk assessments, maintain an inventory of sub-service organizations, collect and review sub-service organization SOC reports, and monitor vendor performance against contractual commitments.
Automate monitoring, logging, change control, and incident tracking. Manual evidence collection is unsustainable. Implement centralized logging (SIEM), automated vulnerability scanning, change management workflows, and incident ticketing systems that produce auditable evidence as a byproduct of normal operations.
Choose an auditor experienced in SOC audits under SSAE 18. Auditor experience matters. Firms with expertise in your industry, technology stack, and control framework reduce friction, provide actionable remediation guidance, and produce higher-quality reports.
Ensure clear communication to enterprise clients. Specify report scope, observation period, report type (Type 1 or Type 2), and control objectives. Transparency prevents misunderstandings and builds trust.
Use the report in go-to-market materials—but maintain operational discipline. SOC reports are powerful sales tools, but they reflect historical control effectiveness. Organizations must sustain controls, update documentation, and address emerging risks. The report is evidence of operational maturity, not a compliance checkbox.
Periodically review and update controls and risk assessments. Systems change. Threats evolve. Sub-service organizations are added or replaced. Periodic review ensures controls remain relevant, risk assessments remain current, and evidence collection processes remain effective.
Conclusion
SSAE 18—Statement on Standards for Attestation Engagements No. 18—establishes how independent auditors examine and report on controls at service organizations. SSAE 18 is a Generally Accepted Auditing Standard produced and published by the American Institute of Certified Public Accountants (AICPA) Auditing Standards Board, and it underpins the SOC 1, SOC 2, and SOC 3 reporting frameworks that have become essential for organizations serving enterprise clients.
SSAE 18 is more than a compliance requirement—it is a framework for operational control, transparency, and risk management. Organizations that approach SSAE 18-based audits as opportunities to strengthen internal controls, formalize risk assessment programs, and mature vendor oversight build more resilient operations and stronger client trust. The alternative—treating audits as performative exercises—produces reports that satisfy procurement teams on paper while leaving organizations fundamentally insecure.
Service organizations should consider SSAE 18-based SOC reports as part of their enterprise-client strategy, not merely a cost. The investment in audit readiness, control implementation, and evidence automation yields faster sales cycles, higher contract values, reduced incident likelihood, and improved operational governance. In the era of complex vendor ecosystems, cloud services, and outsourced business functions, being able to answer "what is SSAE 18" clearly—and demonstrate operational alignment with the standard—is a competitive advantage.
FAQs
1) What does SSAE 18 stand for?
Statement on Standards for Attestation Engagements No. 18.
2) Is SSAE 18 the same as SOC 2?
No. SSAE 18 is the attestation standard that governs how SOC 2 audits are conducted. SOC 2 is the specific report focused on Trust Services Criteria (security, availability, processing integrity, confidentiality, and privacy). SSAE 18 provides the framework; SOC 2 is the output.
3) Are SSAE 18 and SOC 1 the same?
Not exactly. SOC 1 is a type of report focused on controls relevant to financial reporting. SOC 1 audits are conducted under the SSAE 18 standard, but SSAE 18 itself is broader—it also governs SOC 2 and SOC 3 engagements.
4) What is the difference between ISO 27001 and SSAE 18?
ISO 27001 is an international standard for Information Security Management Systems (ISMS), focusing on building, implementing, and maintaining a security management system. SSAE 18 is a U.S. attestation standard for auditing controls at service organizations, typically yielding SOC reports. ISO 27001 results in certification of an organization's ISMS; SSAE 18 results in an auditor's opinion on control design and operating effectiveness. They serve different audiences and purposes, though both address controls, risk management, and internal control environments.



.svg)
.svg)
.svg)