In the modern enterprise landscape, the security of personal data is scrutinized with the same intensity as financial records by buyers. Security questionnaires, procurement reviews, and third-party risk assessments all center on a single critical concern: how an organization protects personal data. A satisfactory answer is essential for securing contracts, managing insurance costs, and surviving due diligence.
Understanding "what is the data protection act" is still vital, even in an environment dominated by GDPR. This is because the UK Data Protection Act 2018 is domestic legislation that complements and implements GDPR, establishing the unified legal framework for data protection. Organizations that treat these as separate compliance tasks fail to grasp the single, unified risk surface that auditors actually assess.
Crucially, compliance with both frameworks is directly linked to a strong security posture. This is not just a regulatory mandate; the technical controls necessary to meet data protection obligations are the very same controls that prevent unauthorized access, misuse, and data breaches. When enterprise buyers evaluate your data protection practices, they are ultimately judging whether your security infrastructure is robust enough to withstand regulatory scrutiny, manage incident investigations, and scale to support the operational demands of data subject rights.
What Is the Data Protection Act
The UK Data Protection Act 2018 is domestic law established in the UK that makes up part of the legal privacy framework for the region alongside the UK GDPR. Its purpose extends beyond regulatory compliance—it establishes accountability mechanisms for how organizations collect, process, store, and delete personal data throughout its lifecycle.
The United Kingdom's Data Protection Act is domestic law originally passed in 1988 that governs how personal data and other information are managed in the UK. The regulation was updated in 1998, then replaced on May 25, 2018, with the UK DPA 2018. This evolution reflects technological advancement and the need for statutory alignment with European data protection standards before and after Brexit.
The Act's core goal: establish lawful and fair handling of personal data by defining controller and processor obligations, codifying data subject rights, and creating enforcement mechanisms through the Information Commissioner's Office (ICO). While GDPR provides the core framework of data protection principles, the DPA includes specific provisions and exemptions tailored for the UK context, such as rules for national security, public authorities, and the age of consent. This distinction matters for enterprise vendors operating across jurisdictions—compliance requires understanding both the baseline GDPR requirements and the UK-specific augmentations the Act introduces.
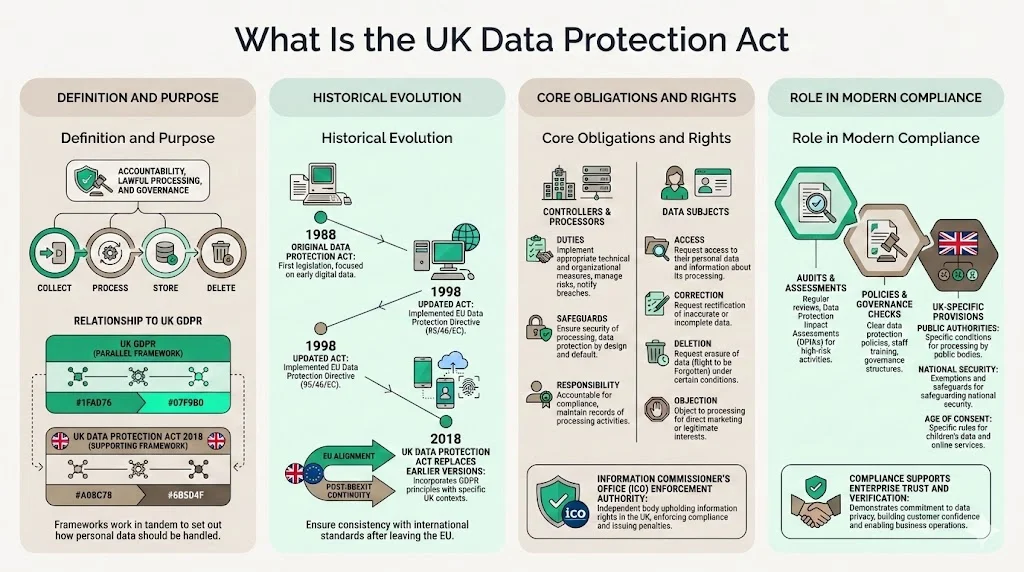
The Act fits into modern data privacy expectations by translating regulatory principles into operational requirements auditors can verify. Organizations demonstrating compliance signal to enterprise buyers that their data handling practices meet statutory standards, their security controls align with regulatory expectations, and their governance frameworks support continuous accountability.
Scope of the Data Protection Act
The Data Protection Act covers personal data: any information relating to an identified or identifiable natural person. This includes names, identification numbers, location data, online identifiers, and factors specific to physical, physiological, genetic, mental, economic, cultural, or social identity. The definition extends to pseudonymized data when combined with additional information that could identify an individual.
Data processing encompasses collection, recording, organization, structuring, storage, adaptation, retrieval, consultation, use, disclosure, transmission, alignment, restriction, erasure, and destruction. Any operation performed on personal data—automated or manual—constitutes processing under the Act.
The law applies to businesses, service providers, and vendors handling enterprise data. It applies to organizations processing personal data in the context of the activities of an establishment of a controller or a processor in the United Kingdom, regardless of whether the processing takes place in the United Kingdom or not. This extraterritorial reach creates compliance obligations for organizations without UK physical presence if they process data of UK residents.
A UK business may still be subject to the EU GDPR if it offers goods or services to, or monitors the behavior of, individuals in the European Economic Area. This layered applicability means enterprise vendors serving multinational clients must maintain compliance with multiple parallel frameworks simultaneously—a reality that shapes architecture decisions, data residency strategies, and contractual obligations in vendor agreements.
Core Principles of Data Protection
The Act establishes seven data protection principles organizations must follow when processing personal data. These principles represent auditable requirements, not aspirational guidance.
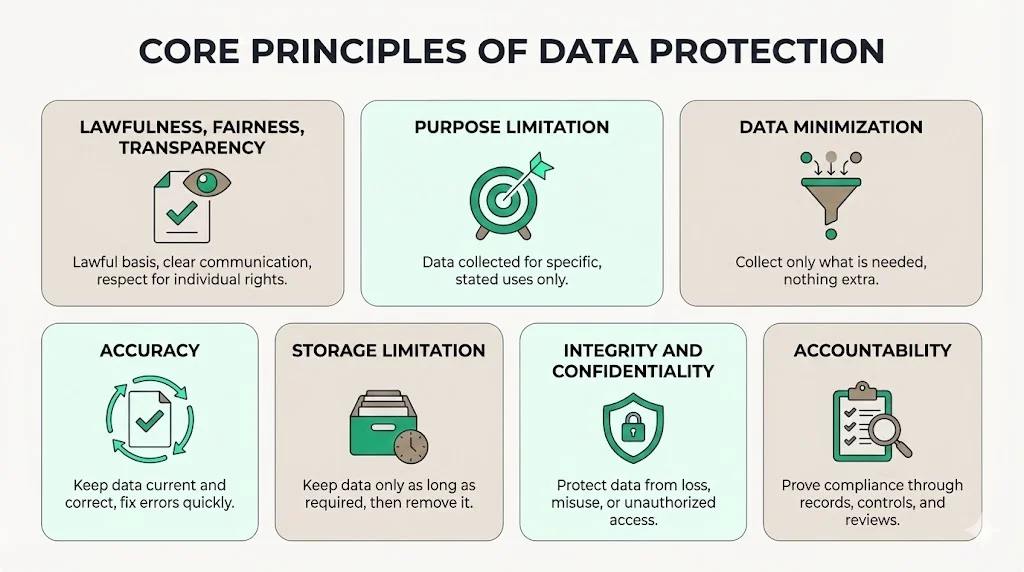
Lawfulness, fairness, and transparency requires organizations to have legitimate legal basis for processing and to communicate data handling practices clearly to data subjects. Processing must not be detrimental to individuals and must respect their rights.
Purpose limitation mandates that personal data be collected for specific, explicit, and legitimate purposes and not processed in ways incompatible with those purposes. Organizations cannot repurpose data without establishing new legal bases and informing data subjects.
Data minimization restricts collection to data adequate, relevant, and limited to what is necessary for the stated purpose. This principle curtails organizations from accumulating personal data without clear business justification—a practice that increases breach exposure and regulatory risk.
Accuracy obligates organizations to maintain current, correct personal data and to rectify or erase inaccurate information promptly when identified or when data subjects request correction.
Storage limitation requires organizations to retain personal data only as long as necessary for the processing purposes. Retention schedules must be documented, defensible, and operationalized through automated deletion or manual review processes.
Integrity and confidentiality demands appropriate security measures to protect personal data against unauthorized or unlawful processing, accidental loss, destruction, or damage. This principle connects directly to information security controls—encryption, access management, vulnerability remediation, and incident response capabilities.
Accountability establishes organizational responsibility for demonstrating compliance with all principles. This means maintaining documentation, implementing data protection by design, conducting impact assessments, and producing evidence auditors and regulators can verify. Accountability transforms compliance from a checkbox exercise into an operational discipline requiring continuous evidence collection and control effectiveness monitoring.
Roles Defined by the Act
Data Controller
The data controller determines the purposes and means of processing personal data. Controllers make decisions about what data to collect, why to collect it, how long to retain it, and who can access it. Legal duties include establishing lawful basis for processing, implementing appropriate security measures, responding to data subject requests, and reporting breaches to the ICO and affected individuals.
Enterprise impact when selecting vendors centers on controller accountability. When your organization acts as controller and engages processors (vendors, subcontractors, SaaS providers), you remain liable for their data handling practices. Procurement reviews focus on processor security posture, subprocessor transparency, and contractual commitments because controller obligations don't transfer—they extend through the supply chain.
Data Processor
Processors handle personal data on behalf of controllers under specific instructions. They differ from controllers in that they lack decision-making authority over processing purposes and means. Contractual and operational duties include processing data only as instructed, implementing security measures, assisting controllers with data subject requests, deleting or returning data when instructed, and maintaining records of processing activities.
Shared risk in enterprise supply chains emerges because processor breaches trigger controller notification obligations, regulatory scrutiny, and potential liability. Enterprise buyers evaluate processor security controls, audit rights, breach notification procedures, and subprocessor management because inadequate processor security directly impacts controller compliance posture and risk exposure.
Data Subjects
Data subjects are identified or identifiable natural persons whose personal data is processed. Any individual about whom an organization collects, stores, or uses personal data qualifies as a data subject—employees, customers, prospects, website visitors, or third parties whose information appears in enterprise systems.
Enterprise buyers focus on downstream exposure because their customers, employees, and partners become data subjects when using vendor systems. Vendors unable to support data subject rights—access requests, deletion requests, portability requirements—create operational liability and compliance gaps that surface during audits, investigations, or regulatory inquiries.
Data Subject Rights Under the Act
The Act codifies eight rights data subjects can exercise regarding their personal data.
Right to access enables individuals to obtain confirmation that their data is being processed, access that data, and receive information about processing purposes, categories, recipients, retention periods, and their other rights.
Right to rectification allows data subjects to request correction of inaccurate personal data and completion of incomplete data.
Right to erasure ("right to be forgotten") permits individuals to request deletion of personal data when processing is no longer necessary, consent is withdrawn, processing is unlawful, or legal obligation requires erasure.
Right to restrict processing lets data subjects limit how organizations use their data in specific circumstances—when accuracy is contested, processing is unlawful but erasure is not desired, data is no longer needed for original purpose but required for legal claims, or while objections to processing are under consideration.
Right to object enables individuals to challenge processing based on legitimate interests or public tasks, direct marketing, and processing for research or statistical purposes.
Right to data portability allows data subjects to receive personal data in structured, commonly used, machine-readable format and to transmit that data to another controller without hindrance.
Rights related to automated decision-making protect individuals from decisions based solely on automated processing, including profiling, that produce legal or similarly significant effects.
Enterprise buyers expect vendors to support these rights by design—not through manual, ad-hoc processes requiring engineering escalation. Vendors demonstrating automated data discovery, documented retention policies, and efficient request fulfillment workflows signal operational maturity. Those requiring custom development or prolonged timelines to satisfy basic data subject requests expose enterprise buyers to regulatory risk, particularly when those buyers must aggregate responses from multiple processors to fulfill their own obligations to data subjects.
How the Data Protection Act Protects Personal Data
Organizations must implement appropriate technical, physical, and organizational security controls including encryption or pseudonymization depending on risks, measures ensuring ongoing confidentiality, integrity, availability, and resilience of processing systems, and measures ensuring ability to restore availability and access to personal data timely after security incidents.
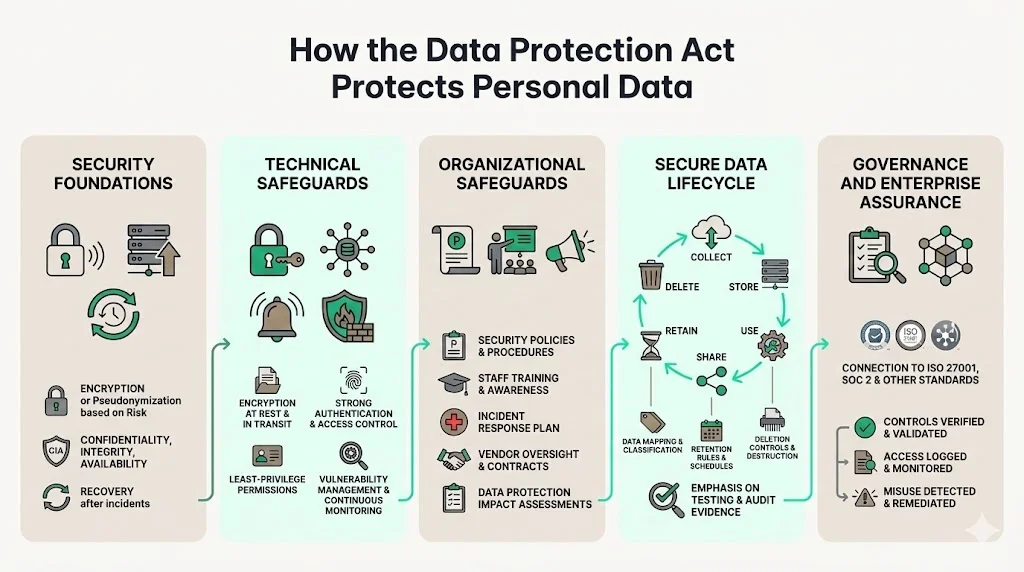
Technical safeguards include encryption at rest and in transit, secure authentication mechanisms, access controls based on least privilege, vulnerability management programs, and automated security monitoring. These controls prevent unauthorized access and detect anomalous activity before data compromise occurs.
Organizational safeguards encompass policies, procedures, training programs, incident response plans, vendor management processes, and data protection impact assessments. These mechanisms ensure security controls are implemented consistently, maintained over time, and adapted as threat landscape and processing activities evolve.
Secure data lifecycle management requires documented processes for data collection, storage, use, sharing, retention, and deletion. Organizations must map data flows, classify data based on sensitivity, implement controls appropriate to risk, and demonstrate those controls function as designed through testing and audit evidence.
Alignment with information governance practices connects data protection to broader risk management frameworks. Organizations treating data protection as an isolated compliance initiative miss the integration point with information security management systems, business continuity planning, and operational risk management. The Act's security requirements mirror control families in ISO 27001, SOC 2, and other frameworks enterprise buyers use to evaluate vendor maturity.
Security controls prevent misuse by restricting access to authorized personnel, logging activity for audit review, detecting policy violations through automated monitoring, and enabling incident investigation through forensic capabilities. Organizations unable to demonstrate these controls during vendor assessments signal inadequate data protection—a disqualifying finding in enterprise procurement.
Data Breaches and Legal Obligations
A data breach constitutes any security incident resulting in accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to personal data. This definition extends beyond external attacks to include internal misconfigurations, access control failures, accidental transmissions, and improper disposal.
Data breaches must be reported to the ICO and affected individuals within 72 hours. Organizations discovering breaches face immediate obligations: assess breach scope and impact, contain the incident, document circumstances and response actions, notify the ICO within 72 hours unless the breach is unlikely to result in risk to individuals' rights and freedoms, and communicate directly with affected individuals when breach presents high risk.
Reporting duties and timelines compress incident response into structured phases. Organizations lacking documented breach response procedures, pre-established communication protocols, and forensic capabilities struggle to meet 72-hour notification windows—particularly when breaches span multiple systems, involve third-party processors, or require technical investigation to determine scope.
Communication with regulators and affected individuals must include specific information: nature of the breach, categories and approximate number of affected data subjects and records, contact details for the data protection officer or responsible point of contact, likely consequences, and measures taken or proposed to address the breach and mitigate adverse effects.
Commercial fallout for enterprise vendors extends beyond regulatory penalties. Breaches trigger customer notification obligations under contracts, insurance claims investigations, potential litigation from affected individuals, customer churn, reputational damage affecting new sales, and heightened scrutiny in future audits. Vendors experiencing breaches often face mandatory security improvements, increased audit frequency, and contractual penalties before customers will continue the relationship. Enterprise buyers evaluate breach response capabilities during due diligence because vendor incidents become their incidents when that vendor processes their data.
Relationship Between the Data Protection Act and GDPR
The UK Data Protection Act took effect on the same day as GDPR because it is meant to be read in conjunction with the EU General Data Protection Regulation. Post-Brexit, the EU GDPR was incorporated into UK domestic law, creating a new parallel regime known as the UK GDPR.
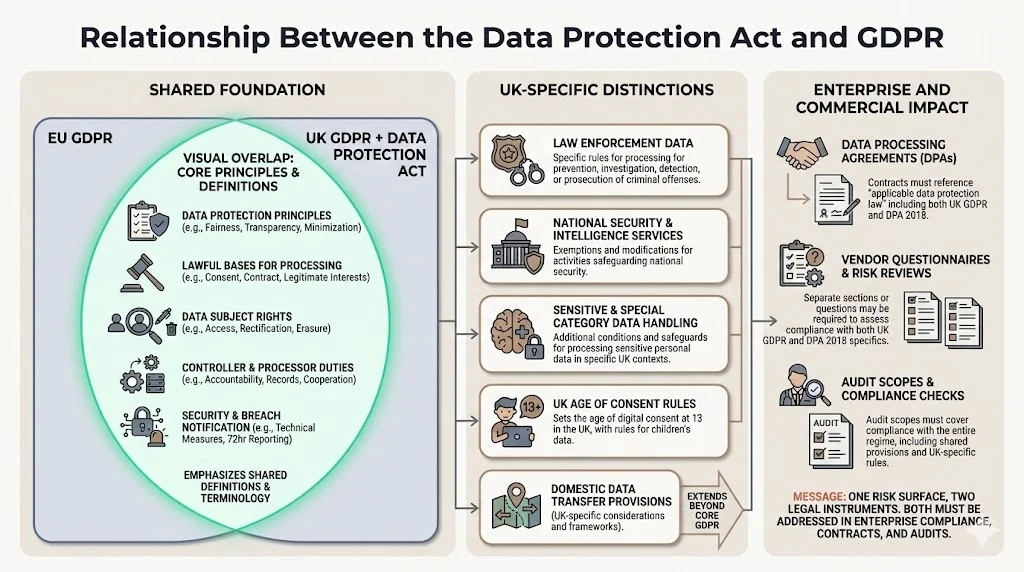
Areas of overlap include core data protection principles, lawful bases for processing, data subject rights, controller and processor obligations, security requirements, and breach notification duties. The frameworks share definitional consistency—terms like personal data, processing, controller, processor, and consent carry identical meaning across both regulations.
Distinction emerges in specific provisions. The DPA features provisions around law enforcement, data transfers, and processing of sensitive personal information not explicitly covered in GDPR. The Act addresses intelligence services processing, national security exemptions, and UK-specific age of consent thresholds—areas where domestic law supplements the broader European framework.
Enterprise buyers view the Act and GDPR as one risk surface because non-compliance with either creates regulatory exposure, contractual breach, and operational liability. Vendors claiming GDPR compliance without addressing DPA-specific requirements demonstrate incomplete understanding of the UK regulatory landscape—particularly concerning data transfers, law enforcement data handling, and special category data processing where the frameworks diverge.
Practical impact on contracts, audits, and due diligence appears in data processing agreements requiring compliance with "applicable data protection law" rather than naming specific regulations. Security questionnaires ask about UK GDPR and DPA 2018 compliance separately to assess whether vendors understand the distinction. Audit scopes encompass both frameworks because enterprise customers operate across jurisdictions and need assurance their processors maintain compliance regardless of where data resides or where processing occurs.
Regulatory Compliance in Practice
Compliance is ongoing operational discipline, not milestone achievement. Organizations obtaining certification or passing audits face continuous obligations—monitoring control effectiveness, updating documentation as processing activities change, conducting regular reviews of data flows and retention practices, training personnel on updated procedures, and maintaining evidence demonstrating sustained compliance.
Enterprise buyers expect to see documented policies governing data protection, privacy notices informing data subjects about processing, data processing agreements with processors and subprocessors, records of processing activities, data protection impact assessments for high-risk processing, breach response procedures, data subject request fulfillment workflows, and retention schedules with documented deletion procedures.
Processes enterprises evaluate include how vendors identify and classify personal data in their systems, how they manage consent and other lawful bases, how they fulfill data subject requests within statutory timelines, how they assess and manage processor risk, how they conduct employee training, and how they respond to breaches and near-miss incidents.
Controls auditors verify include access management restricting data access based on role and need, encryption protecting data at rest and in transit, logging and monitoring detecting unauthorized access or policy violations, vulnerability management addressing security weaknesses, backup and recovery capabilities ensuring data availability, and secure deletion processes removing data when retention periods expire.
Mapping data flows and ownership requires documenting what data is collected, from what sources, for what purposes, under what lawful basis, where it is stored, who can access it, with whom it is shared, how long it is retained, and how it is ultimately deleted. Organizations unable to produce current, accurate data maps during vendor assessments reveal inadequate governance and expose buyers to unknown risk.
Penalties and Enforcement
The standard maximum penalty that can be imposed is £10 million or 2% of the undertaking's total annual worldwide turnover in the preceding financial year, whichever is higher. More serious violations can result in penalties up to £17.5 million or 4% of annual global turnover. When deciding whether to impose an administrative fine and the amount, the ICO considers factors including nature, severity, and duration of failure, whether it was intentional or negligent, actions taken to mitigate harm, the controller's or processor's responsibility and cooperation, relevant past failures, categories of data affected, and whether penalty would be effective and proportional.
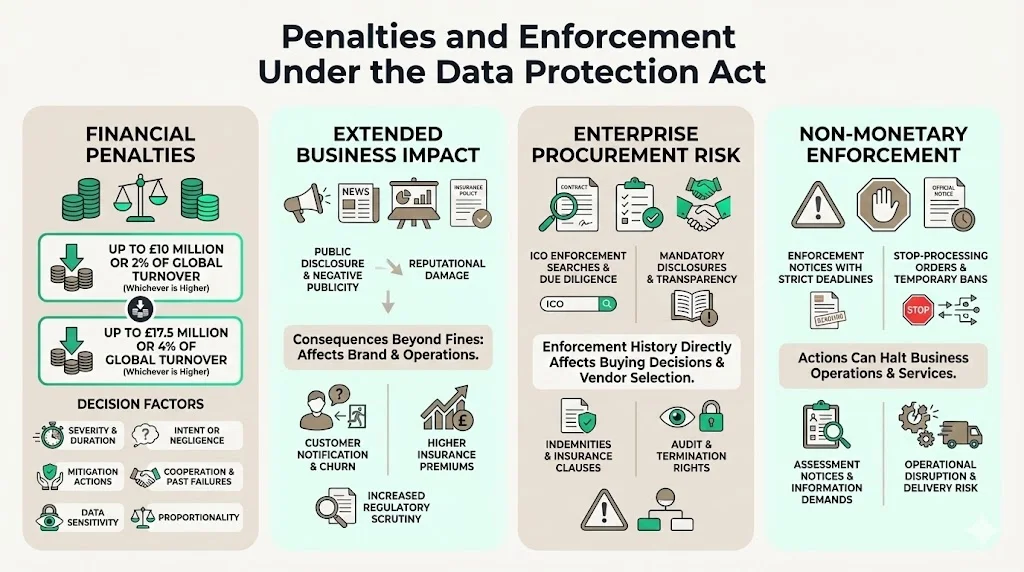
Financial penalties represent direct cost, but legal and reputational effects extend further. Organizations fined by the ICO face mandatory disclosure in security questionnaires, negative media coverage affecting brand perception, customer notification obligations triggering churn, increased insurance premiums, board-level scrutiny of data protection practices, and regulatory attention increasing likelihood of future investigation.
Enforcement risk shapes enterprise buying decisions because vendors under ICO investigation or subject to enforcement action introduce unquantifiable risk into the relationship. Procurement teams conducting due diligence search ICO enforcement databases, require disclosure of regulatory inquiries and findings, and negotiate contractual protections—indemnification clauses, insurance requirements, audit rights, and termination provisions triggered by regulatory action.
Enforcement also includes non-monetary measures: enforcement notices requiring specific actions within defined timelines, stop-processing orders halting specific data processing activities, and assessment notices compelling organizations to provide information for compliance evaluation. These interventions disrupt operations and can prevent vendors from fulfilling contractual obligations to enterprise customers.
Why the Data Protection Act Matters for Enterprise Sales
Compliance functions as a trust signal in enterprise procurement. Organizations demonstrating sustained compliance with the Act and GDPR through certifications, audit reports, and documented controls differentiate themselves from competitors unable to provide equivalent assurance. Security teams reviewing vendor options prioritize those requiring minimal oversight and presenting lowest regulatory risk.
Procurement reviews and security questionnaires directly assess Data Protection Act compliance. Standard assessments ask about data processing activities, lawful bases, data subject rights fulfillment procedures, security controls, breach notification processes, processor management, and retention practices. Vendors without documented, auditable answers to these questions fail initial screening before commercial discussions advance.
Competitive advantage for compliant vendors appears in shortened sales cycles, reduced legal negotiation friction, streamlined contract execution, and access to enterprise accounts where non-compliant vendors are automatically disqualified. Organizations investing in compliance infrastructure—data protection officers, privacy management platforms, automated controls, regular audits—recover that investment through improved win rates and contract terms reflecting lower perceived risk.
Reducing friction during legal and security reviews requires preparation before RFP response or vendor assessment. Organizations maintaining current audit reports, documented policies, completed security questionnaires in standard formats, data processing agreement templates aligned with enterprise requirements, and evidence of control effectiveness can respond to due diligence requests in days rather than weeks. This responsiveness signals operational maturity and reduces buyer concerns about vendor capability to maintain compliance post-contract.
Conclusion
Reframing "what is the data protection act" as a business question rather than a legal one reveals its strategic importance. The Act establishes operational requirements that directly impact vendor selection, contract terms, audit outcomes, and regulatory risk exposure. Organizations treating data protection as compliance checkbox exercise rather than integrated security discipline face enforcement risk, commercial disadvantage, and operational disruption when breaches occur or audits reveal control gaps.
Strong data privacy and information security practices support enterprise growth by enabling access to markets where compliance is prerequisite, reducing cost and friction in procurement cycles, minimizing breach risk and associated financial and reputational impact, and demonstrating governance maturity that enterprise buyers require from strategic vendors.
The Act functions as a baseline for responsible data handling—the minimum standard organizations must meet to operate legally in the UK market. Organizations aspiring to enterprise sales must exceed this baseline by implementing controls that satisfy multiple frameworks simultaneously, maintaining continuous audit readiness, and demonstrating through documented evidence that their data protection practices protect not just against regulatory scrutiny but against actual security threats.
FAQ Section
1) What is the Data Protection Act?
The UK Data Protection Act 2018 is domestic law established in the UK that makes up part of the legal privacy framework for the region alongside the UK GDPR. It governs how organizations collect, process, store, and delete personal data, establishes data subject rights, defines controller and processor obligations, and creates enforcement mechanisms through the Information Commissioner's Office.
2) How does the Data Protection Act relate to GDPR?
The UK Data Protection Act 2018 supplements and enacts GDPR, working alongside it to govern data protection. While GDPR provides the core framework of data protection principles, the DPA includes specific provisions and exemptions tailored for the UK context, such as rules for national security, public authorities, and the age of consent. Organizations must comply with both frameworks as they function as integrated regulatory requirements.
3) Who must comply with the Data Protection Act?
The Act applies to organizations processing personal data in the context of activities of an establishment of a controller or processor in the United Kingdom, regardless of whether the processing takes place in the United Kingdom or not. This includes businesses, service providers, vendors, and any organization handling personal data of UK residents—even organizations without UK physical presence.
4) What penalties apply for non-compliance?
The standard maximum penalty is £10 million or 2% of the undertaking's total annual worldwide turnover in the preceding financial year, whichever is higher. More serious violations can result in fines up to £17.5 million or 4% of annual global turnover. Beyond financial penalties, organizations face enforcement notices, stop-processing orders, reputational damage, customer churn, and increased regulatory scrutiny.
5) How does the Act protect personal data?
The Act requires organizations to implement appropriate technical, physical, and organizational security controls including encryption or pseudonymization, measures ensuring ongoing confidentiality, integrity, availability, and resilience of processing systems, and measures ensuring ability to restore availability and access to personal data timely after security incidents. Protection extends through data subject rights enabling individuals to access, correct, delete, restrict, and port their data, and through breach notification requirements ensuring transparency when security incidents occur.



.svg)
.svg)
.svg)