Most organizations pursuing healthcare clients treat HIPAA compliance as a checklist exercise rather than a comprehensive security discipline. This approach creates fundamental gaps in protection—gaps that become apparent during OCR investigations, when preventable breaches expose electronic protected health information (ePHI), or when enterprise clients conduct vendor security assessments. The HIPAA Security Rule establishes national standards specifically designed to protect ePHI through systematic safeguards addressing confidentiality, integrity, and availability. For organizations selling to enterprise healthcare clients, demonstrating Security Rule compliance isn't optional—it's a prerequisite for business associate agreements, vendor risk assessments, and maintaining contractual relationships with covered entities.
The Security Rule intersects with broader data privacy regulations including health information protection requirements, electronic health records security standards, and regulatory frameworks governing sensitive data transmission. Unlike general data protection approaches, the Security Rule mandates specific technical, physical, and administrative safeguards tailored to the unique risks inherent in healthcare data systems.
What Is the HIPAA Security Rule?
The HIPAA Security Rule establishes national standards for the protection of individuals' electronic protected health information (ePHI) by covered entities and their business associates. Enacted as part of the Health Insurance Portability and Accountability Act of 1996 and subsequently updated to reflect the Health Information Technology for Economic and Clinical Health (HITECH) Act, the Security Rule operates as a federal regulatory framework specifically addressing electronic health data security.
The Rule's core objectives center on ensuring three fundamental properties of ePHI: confidentiality (preventing unauthorized access), integrity (ensuring data accuracy and preventing unauthorized alteration), and availability (ensuring authorized users can access information when needed). These objectives reflect security principles essential to healthcare operations—where data breaches compromise patient safety, inaccurate data leads to clinical errors, and system unavailability disrupts care delivery.
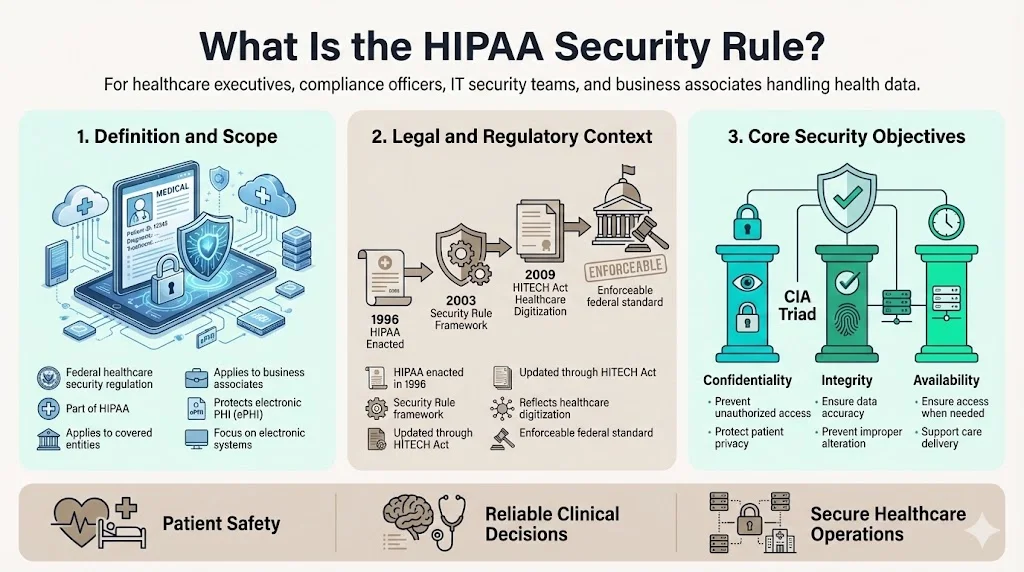
Scope of Information Protected
The Security Rule focuses exclusively on electronic protected health information—health data created, received, maintained, or transmitted in electronic form. This distinguishes the Security Rule from broader HIPAA privacy protections, which encompass PHI in all formats including paper records and verbal communications.
ePHI subject to Security Rule protections includes electronic health records systems, medical billing platforms, laboratory information systems, pharmacy management systems, health insurance claims, patient portals, telemedicine platforms, and any other electronic systems containing individually identifiable health information. Cloud-hosted applications, mobile health applications, and software-as-a-service platforms handling healthcare data all fall within the Security Rule's scope when they process, store, or transmit ePHI.
How It Works With Other HIPAA Rules
The Security Rule functions as a companion regulation to the HIPAA Privacy Rule and Breach Notification Rule, forming an integrated compliance framework. The Privacy Rule governs the use and disclosure of all PHI regardless of format, establishing permissions and restrictions on how covered entities share patient information. The Security Rule builds on these privacy protections by specifying how organizations must safeguard ePHI through concrete technical, physical, and administrative controls.
Where the Privacy Rule asks "who can access this information and under what circumstances," the Security Rule addresses "how do we protect this information from unauthorized access, alteration, or destruction." The Breach Notification Rule then establishes response obligations when Security Rule protections fail, requiring notification to affected individuals, HHS, and in some cases media outlets when unsecured ePHI is compromised.
This regulatory structure means compliance requires simultaneous attention to all three rules—implementing Security Rule safeguards, honoring Privacy Rule use restrictions, and maintaining Breach Notification readiness.
Who Must Comply With the HIPAA Security Rule
Covered Entities
Covered entities include health plans, health care clearinghouses, and most health care providers that transmit health information electronically. Health plans encompass commercial insurance companies, government healthcare programs (Medicare, Medicaid), employer-sponsored health plans, and health maintenance organizations. Healthcare clearinghouses process health information between providers and payers, converting data into standardized formats for electronic transactions. Healthcare providers subject to the Rule include hospitals, physician practices, clinics, pharmacies, nursing homes, and any other provider conducting standard electronic transactions such as claims submission or eligibility verification.
The "electronic transmission" threshold means virtually all modern healthcare providers fall under Security Rule requirements, as contemporary medical practice inherently involves electronic billing, prescription systems, and health information exchange.
Business Associates
Business associates are entities that handle ePHI on behalf of covered entities to perform functions or services involving access to protected health information. This category extends Security Rule obligations far beyond traditional healthcare organizations to encompass cloud infrastructure providers, electronic health record vendors, medical billing companies, healthcare consultants, data analytics firms, IT managed service providers, and any other organization requiring ePHI access to deliver contracted services.
The HITECH Act made business associates directly liable for Security Rule compliance, eliminating the previous model where only covered entities faced regulatory enforcement. Software vendors, SaaS providers, and technology companies serving healthcare clients must now implement the same safeguards required of hospitals and health plans—a requirement frequently underestimated by technology organizations entering the healthcare market.
Why Compliance Matters for Enterprise Sellers
Organizations pursuing enterprise healthcare clients face Security Rule compliance as a non-negotiable vendor requirement. Healthcare organizations conducting vendor risk assessments explicitly verify Security Rule adherence before executing business associate agreements. Non-compliant vendors are categorically excluded from consideration regardless of product capabilities or pricing.
Beyond contractual access, OCR administers and enforces the Security Rule, conducting investigations following breach reports, responding to complaints, and performing compliance audits. Enforcement actions result in financial penalties ranging from thousands to millions of dollars depending on violation severity and culpability, along with corrective action plans requiring extensive remediation. The reputational impact of OCR enforcement—publicly reported through HHS breach databases and enforcement announcements—compounds financial penalties with lost business opportunities and customer attrition.
Key Components of the Security Rule
The Security Rule structures compliance requirements across three safeguard categories, each addressing distinct aspects of ePHI protection. Organizations must implement all applicable safeguards, documenting implementation decisions and maintaining evidence of ongoing compliance.
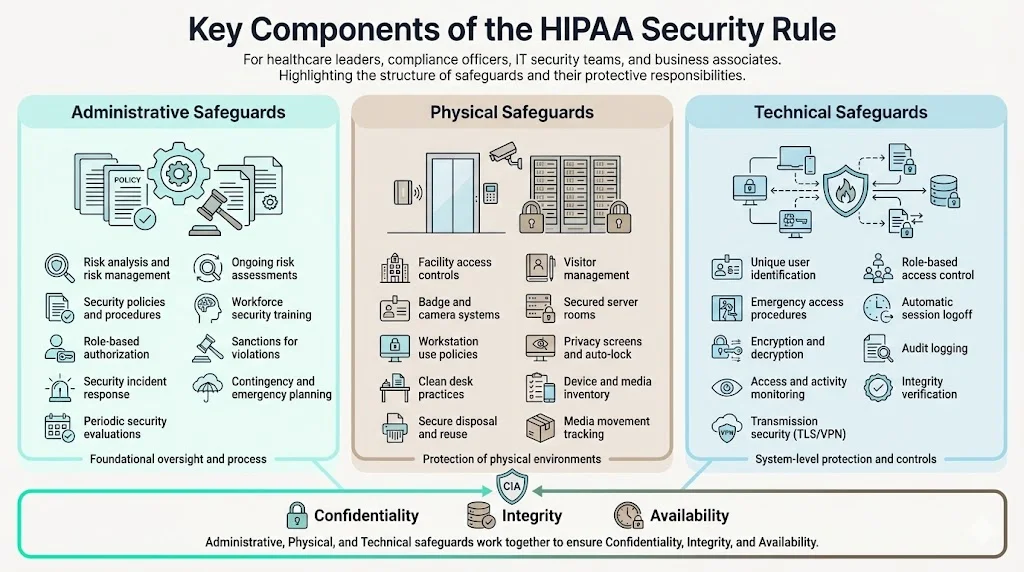
Administrative Safeguards
Administrative safeguards constitute organizational policies, procedures, and management processes governing workforce conduct and security oversight. These represent the Security Rule's most extensive category, establishing the governance foundation for all security activities.
Risk analysis and risk management requirements mandate comprehensive, documented assessments identifying threats and vulnerabilities to ePHI, evaluating current security measures, determining risk likelihood and impact, and implementing controls to reduce risks to reasonable and appropriate levels. Organizations must conduct risk analyses regularly and following significant environmental or operational changes—not as one-time certification exercises but as continuous security disciplines.
Workforce training requirements mandate security awareness education for all employees with ePHI access, covering security policies, incident response procedures, malware protection, password management, physical security, and sanctions for policy violations. Training must occur upon hire, annually thereafter, and when security policies change materially.
Security management oversight requires designating a security official responsible for developing and implementing security policies, establishing authorization and supervision procedures for workforce members accessing ePHI, implementing workforce clearance procedures verifying employee appropriateness for ePHI access, and maintaining sanctions policies for employees violating security requirements.
Additional administrative safeguards address information access management (limiting ePHI access to authorized users performing legitimate job functions), security incident response procedures, contingency planning for emergency operations, and periodic security evaluations assessing compliance effectiveness.
Physical Safeguards
Physical safeguards address facility security, workstation controls, and device management—protecting the physical infrastructure housing ePHI from unauthorized access, theft, and environmental hazards.
Facility access controls govern who can physically enter locations where ePHI systems operate, requiring organizations to implement visitor logs, badge access systems, security cameras, locked server rooms, and procedures controlling facility access during emergencies. These controls extend beyond primary offices to include remote locations, mobile workstations, and any physical space where ePHI resides.
Workstation security policies specify appropriate workstation uses, physical attributes protecting workstations from unauthorized viewing, and procedures limiting ePHI exposure. Implementation includes privacy screens, automatic screen locks, workstation positioning preventing public visibility, and clean desk policies requiring ePHI removal when workstations are unattended.
Device and media controls govern ePHI receipt, removal, and disposal across all hardware and electronic media. Organizations must maintain hardware and media inventories, implement secure disposal procedures rendering ePHI unrecoverable (including device sanitization before disposal or reuse), create media reuse procedures ensuring complete data removal, and track media movements documenting ePHI transfers.
Technical Safeguards
Technical safeguards implement technology-based protections controlling ePHI access and securing electronic transmissions.
Access controls authenticate users and grant appropriate system permissions, requiring unique user identifiers for each person accessing ePHI, emergency access procedures enabling authorized users to access ePHI during crises, automatic logoff terminating sessions after predetermined inactivity periods, and encryption/decryption mechanisms protecting ePHI confidentiality. Organizations must implement role-based access controls ensuring users access only information necessary for job responsibilities.
Audit controls implement hardware, software, and procedural mechanisms recording and examining ePHI access and system activity. Organizations must log user access attempts (successful and failed), system configuration changes, security policy modifications, and administrative actions, maintaining these audit logs for investigation purposes and periodic review to identify suspicious activity patterns.
Integrity controls protect ePHI from improper alteration or destruction, implementing mechanisms confirming ePHI hasn't been modified or deleted in unauthorized ways. This includes checksums, digital signatures, version controls, and database transaction logs maintaining ePHI integrity throughout its lifecycle.
Transmission security safeguards protect ePHI transmitted across electronic networks from unauthorized access or modification. Organizations must implement network encryption (TLS/SSL for data in transit), VPN connections for remote access, secure messaging systems for ePHI communication, and protections against network-based attacks.
Risk Management and Threat Protection
One of the most commonly identified HIPAA Security Rule violations is the failure to conduct a comprehensive and accurate risk analysis. The Security Rule's risk management requirements drive formal assessment processes identifying threats ranging from external cyberattacks and malware to internal policy violations and system failures. Organizations must evaluate technical vulnerabilities (unpatched systems, weak authentication), physical vulnerabilities (unsecured facilities, portable device theft), and administrative vulnerabilities (inadequate training, insufficient policies).
This risk-based approach integrates with enterprise risk management frameworks, allowing organizations to contextualize healthcare data security within broader operational, financial, and strategic risk profiles. Security Rule risk assessments inform prioritization decisions, resource allocation, and control implementation strategies aligned with organizational risk tolerance.
The Security Rule's risk management discipline directly addresses healthcare data breach prevention. By identifying vulnerabilities before exploitation, organizations implement controls protecting confidential patient data against ransomware, hacking, insider threats, and accidental disclosures—the primary breach vectors reported to OCR. Effective risk management transforms compliance from reactive breach response to proactive threat mitigation.
What Happens If Companies Fail to Comply
The Office for Civil Rights enforces Security Rule compliance through investigations triggered by breach reports (required under the Breach Notification Rule), patient complaints, and proactive compliance audits. OCR investigations examine whether organizations implemented required safeguards, conducted adequate risk analyses, maintained appropriate policies and procedures, and responded appropriately to identified security incidents.
Enforcement outcomes range from voluntary corrective action (for minor violations remediated promptly) to civil monetary penalties and mandatory corrective action plans. Penalty amounts depend on violation severity and culpability level, ranging from $100 to $50,000 per violation with annual maximum penalties reaching $1.5 million per violation category. Organizations demonstrating willful neglect face mandatory minimum penalties regardless of violation count.
Beyond financial penalties, OCR enforcement includes multi-year corrective action plans requiring comprehensive security program overhauls, third-party security assessments, regular compliance reporting to OCR, and workforce training. These remediation obligations consume substantial organizational resources over periods extending three to five years post-resolution.
For enterprise vendors, non-compliance creates compounding impacts beyond regulatory penalties. Healthcare clients terminate business associate agreements following breach incidents or compliance failures, triggering revenue loss and customer attrition. Organizations appearing in HHS breach databases or OCR enforcement announcements face reputational damage impeding new customer acquisition. The contractual exposure from breaching business associate agreements includes indemnification obligations covering clients' breach notification costs, regulatory penalties, and litigation expenses—potentially exceeding direct OCR penalties.
Consider scenarios illustrating non-compliance consequences: a cloud service provider experiencing a ransomware attack encrypting customer ePHI faces OCR penalties for inadequate access controls and vulnerability management, customer lawsuits for contractual breach, business associate agreement terminations across its customer base, and years of mandatory security reporting. A medical billing company failing to conduct required risk analyses and implement encryption faces similar enforcement even absent actual breaches, as OCR may discover violations through complaint-triggered investigations or compliance audits.
Best Practices for Enterprise-Level HIPAA Security
Organizations achieving sustained Security Rule compliance implement practices extending beyond minimum regulatory requirements to create mature security programs protecting ePHI while supporting business operations.
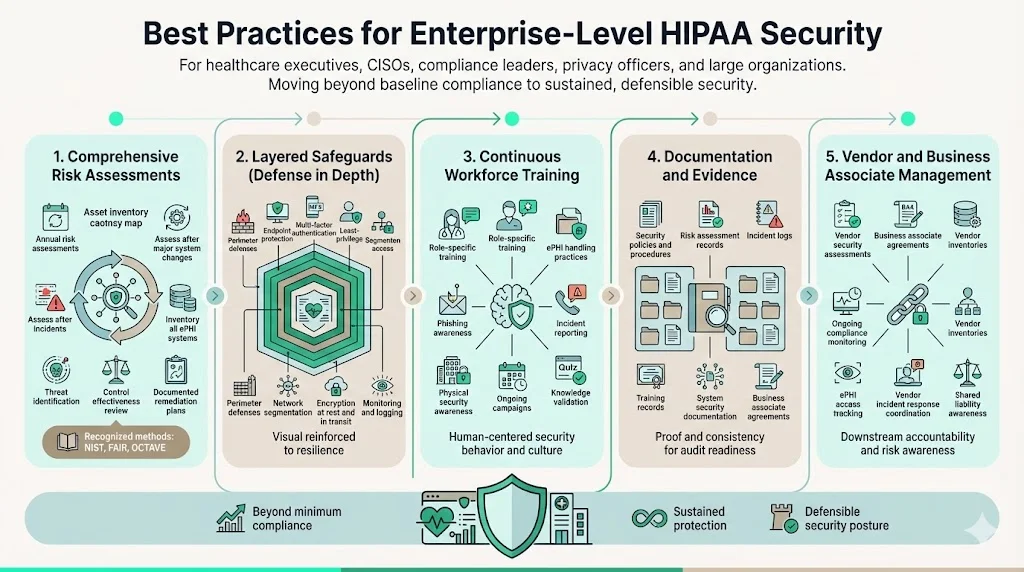
Conduct thorough risk assessments annually at minimum, but also following significant system changes, security incidents, or environmental shifts. Risk analyses should inventory all systems processing, storing, or transmitting ePHI; identify threats from malware, hacking, insider threats, physical theft, and system failures; evaluate existing security measure effectiveness; and document risk reduction strategies with implementation timelines. Organizations using recognized risk assessment methodologies (NIST Risk Management Framework, FAIR, OCTAVE) demonstrate systematic approaches satisfying Security Rule requirements while integrating with broader cybersecurity programs.
Implement layered safeguards creating defense-in-depth protection where multiple control failures must occur before ePHI exposure. This includes perimeter defenses (firewalls, intrusion detection), endpoint protection (antivirus, device encryption), access controls (multi-factor authentication, least privilege), network segmentation isolating ePHI systems, data protection (encryption at rest and in transit), and monitoring/logging enabling threat detection. Single control points create single points of failure; layered approaches provide resilience against diverse attack vectors.
Establish continuous workforce training programs covering security policies, ePHI handling procedures, phishing recognition, incident reporting, and physical security. Training effectiveness depends on relevance (role-specific scenarios rather than generic content), frequency (ongoing awareness campaigns supplementing annual compliance training), and assessment (testing comprehension rather than attendance tracking). Security awareness must become embedded in organizational culture, not relegated to annual checkbox exercises.
Maintain comprehensive documentation including security policies and procedures, risk assessment results, security incident logs, audit findings and remediation tracking, business associate agreements, workforce training records, and system security documentation. Documentation serves dual purposes: operationally, it ensures consistent security implementation across the organization; from a compliance perspective, it provides evidence demonstrating Security Rule adherence during OCR investigations or customer audits.
Implement rigorous vendor and business associate management ensuring downstream security. This includes conducting vendor security assessments before ePHI sharing, executing business associate agreements specifying security obligations, monitoring vendor compliance through periodic assessments, maintaining vendor inventories, tracking which vendors access ePHI, and establishing vendor incident response procedures. Organizations remain liable for business associate failures, making vendor security management a critical compliance component.
The Future of the HIPAA Security Rule
On December 27, 2024, OCR issued a Notice of Proposed Rulemaking to modify the HIPAA Security Rule to strengthen cybersecurity protections for electronic protected health information. The proposed updates reflect regulatory evolution addressing modern threat landscapes, technological advances, and enforcement experience accumulated over two decades.
Proposed modifications include removing the distinction between "required" and "addressable" implementation specifications and making all implementation specifications required with specific, limited exceptions. This change addresses longstanding confusion where organizations misinterpreted "addressable" specifications as optional rather than requiring documented assessments of reasonableness and appropriateness.
Additional proposed requirements include mandatory technology asset inventories and network maps documenting ePHI locations and flows, multi-factor authentication for all ePHI access, encryption for ePHI at rest and in transit with limited exceptions, vulnerability scanning every six months, annual penetration testing, and enhanced incident response procedures with defined timelines. These requirements align the Security Rule with contemporary cybersecurity best practices and frameworks including NIST Cybersecurity Framework guidance.
The regulatory proposal faces public comment periods extending through early 2025, with final rule publication potentially occurring in late 2026 followed by implementation periods allowing organizations 240 days for compliance. However, regulatory finalization depends on administrative priorities and may experience delays or modifications based on stakeholder feedback and political transitions.
Organizations maintaining proactive security programs aligned with frameworks such as NIST CSF, ISO 27001, or HITRUST already implement many proposed requirements, positioning themselves for seamless adaptation to strengthened regulatory standards. Those treating current Security Rule requirements as compliance ceilings rather than security foundations face substantial gaps requiring remediation when enhanced standards take effect.
Conclusion
The HIPAA Security Rule establishes the regulatory foundation for electronic health information protection in the United States, mandating administrative, physical, and technical safeguards ensuring ePHI confidentiality, integrity, and availability. For organizations offering solutions to healthcare clients, Security Rule compliance represents both regulatory obligation and competitive prerequisite—healthcare enterprises will not engage vendors unable to demonstrate systematic ePHI protection.
Effective Security Rule compliance extends beyond checkbox exercises to comprehensive security programs integrating risk management, layered controls, continuous monitoring, workforce training, and vendor oversight. Organizations treating security as genuine operational discipline rather than paper compliance achieve dual outcomes: regulatory adherence satisfying OCR and customer requirements, and actual security protecting systems against threats targeting healthcare data. As cybersecurity threats intensify and regulatory requirements evolve, the gap between performative compliance and genuine security widens—with consequences increasingly measured in breached records, regulatory penalties, and lost business relationships.
FAQs
1) What is the HIPAA Security Rule?
The HIPAA Security Rule is a federal regulation establishing national standards for protecting electronic protected health information (ePHI). It requires covered entities and business associates to implement administrative, physical, and technical safeguards ensuring ePHI confidentiality, integrity, and availability.
2) Who must comply with the HIPAA Security Rule?
Covered entities (health plans, healthcare clearinghouses, and healthcare providers transmitting health information electronically) and business associates (organizations handling ePHI on behalf of covered entities) must comply with the Security Rule. This includes technology vendors, cloud providers, consultants, and any other organization accessing ePHI to deliver services to covered entities.
3) How is the Security Rule different from the Privacy Rule?
The Security Rule focuses specifically on safeguards protecting electronic protected health information through technical, physical, and administrative controls. The Privacy Rule governs use and disclosure of all protected health information regardless of format (electronic, paper, or verbal), establishing who can access information and under what circumstances. The Security Rule implements the "how" of protection while the Privacy Rule governs the "who" and "when" of access.
4) What happens if companies fail to comply?
The Office for Civil Rights enforces Security Rule compliance through investigations and audits, imposing civil monetary penalties ranging from $100 to $50,000 per violation with annual maximums reaching $1.5 million per violation category. Enforcement includes corrective action plans requiring multi-year security program remediation, third-party assessments, and ongoing OCR reporting. Organizations also face business associate agreement terminations, customer attrition, litigation exposure, and reputational damage impeding future business development.



.svg)
.svg)
.svg)