Most procurement teams now ask for evidence of security controls before signing a deal. Many sellers think their documentation is ready, only to find that risk questionnaires and audits reveal gaps. A repeatable information‑security management system (ISMS) built around ISO 27001 policies required can shorten sales cycles, reduce findings and protect sensitive data.
This article explains why policies matter, what the standard demands, and how human‑led implementation improves outcomes for cloud businesses selling to regulated sectors. The insights come from our work on more than 6,000 audits over twenty‑five years combined experience and recent statistics.
Why Policies Matter in ISO/IEC 27001 and Enterprise Sales
ISO/IEC 27001 is the world’s best‑known framework for information‑security management. It provides guidance for establishing, implementing, maintaining and continually improving an ISMS. Conformity means that an organisation has put in place a system to manage risks related to data security and follows the best practices set out by the standard.
The standard promotes a holistic approach: vetting people, policies and technology. This structure is crucial when selling to large customers. Procurement teams often have legal obligations under regulations such as HIPAA, GDPR, SOC 2 or the artificial intelligence security frameworks. They send questionnaires covering risk assessment, access control, business continuity and vendor security. Without documented policies that answer these areas, deals stall.
Policies provide broad direction for your security programme. They establish what you do and why you do it; procedures explain how. For enterprise buyers, policies demonstrate management commitment, risk appetite and the scope of your ISMS. They also give assurance that you understand confidentiality, integrity and availability—the three pillars of information security.

Understanding “ISO 27001 Policies Required”
Mandatory vs. De‑Facto Required Policies
ISO 27001 explicitly names one policy in Clause 5.2: the information security policy. DataGuard notes that top management must document, approve, communicate and periodically update this policy. The policy sets out management’s commitment to protecting information, the assets that need protection, the threats faced and the controls used to mitigate them. It must fit your organisational strategy and be communicated to all employees. Without this broad document, you will not pass an ISO 27001 certification audit.
In addition to the information security policy, other documents become effectively required once you implement specific controls from Annex A or address particular risks. Annex A lists 93 controls organised into categories such as people, organisational, technological and physical controls. During certification you must produce a Statement of Applicability explaining which controls apply and why. If you apply an access control measure, for instance, auditors will expect an Access Control Policy. If you classify information, you need an Asset Management Policy. Policies therefore emerge from your risk assessment and the controls you choose.
Policies vs. Procedures
HighTable reminds us that policies describe what you do and why, while procedures describe how. Policies should avoid detailed process steps because they may contain proprietary information or operational specifics that you do not wish to share externally. Instead, a broad policy sets principles and objectives, leaving the “how” to separate procedures. Separating the two helps you share policies with clients without revealing internal secrets.
Policies as the Spine of the ISMS:
ISO 27001 requires a set of documents to cover the ISMS lifecycle. StrongDM summarises the seven mandatory clauses: defining scope, demonstrating leadership commitment, setting objectives, allocating resources, planning operations, measuring performance and managing non‑conformities. Policies underpin each step. A Risk Management Policy supports the risk assessment and treatment plans in clauses 4 and 6. An Access Control Policy supports Annex A controls for identity management and least privilege. A Business Continuity and Incident Response Policy supports clause 8 operations and clause 9 performance evaluation. Document Control, Audit and Compliance policies show auditors that you have a cycle for monitoring, review and improvement. For enterprise sales, clients will expect to see these documents because they fit with vendor risk questionnaires and legal obligations.
Why Enterprise Buyers Care?
Statistics from 2024–2025 illustrate the risk environment. IBM’s 2025 cost‑of‑breach analysis notes that the global average cost of a data breach fell 9 percent to USD 4.44 million, thanks to faster containment driven by machine‑assisted detection. Yet phishing remains the most common attack vector, costing organisations about USD 4.8 million per incident. In healthcare, breaches are even more expensive, with average costs around USD 7.42 million and containment taking nine months. Vendor risk is another major source of breaches. Third‑party attacks were the second most common initial vector and cost USD 4.91 million on average. Healthcare data breaches continued at scale: the U.S. The Department of Health and Human Services recorded 725 breaches of 500 or more records in 2024, with the number of records exposed surging to 275 million. Enterprise buyers need to see evidence that you manage such risks, and policies are the first indicator that you do. This is why many questionnaires ask for vendor security documentation, incident response plans and evidence of training.
Core Policies Every ISO 27001 Programme Needs
The list below covers the main ISO 27001 policies required for most organisations selling into regulated sectors. Each policy provides broad direction and links to specific controls or client expectations. We’ve included simple examples to illustrate the intent.

- Information Security Policy – Defines management’s commitment to protecting confidentiality, integrity and availability of information assets. It outlines the ISMS scope, objectives and roles. Example: senior leadership commits to protect all company and client information, sets objectives for risk reduction and mandates annual policy review. This policy satisfies clause 5.2 and underpins every control.
- Risk Management and Assessment Policy – Describes how you identify, assess, treat and report risks. It covers risk appetite, risk register maintenance and treatment plans. Example: risks are evaluated quarterly; the company maintains a risk register with likelihood and impact ratings; treatment plans are approved by the CISO. This policy supports clauses 4 and 6.
- Asset Management Policy – Establishes how you inventory, classify and manage the lifecycle of assets. It defines ownership and classification categories (confidential, restricted, public). Example: all information assets are recorded in an asset register; each has an owner; classification is reviewed annually. This supports Annex A controls for asset management.
- Access Control Policy – Governs how privileges are granted, modified and revoked. It sets principles such as least privilege and segregation of duties. Example: role‑based access is enforced; multi‑factor authentication is required for privileged accounts; access rights are reviewed every quarter. This policy corresponds to Annex A controls on identity management and authentication.
- Cryptography and Encryption Policy – Specifies how encryption is used to protect data in transit and at rest, and how cryptographic materials are managed. Example: sensitive customer data stored in databases must use AES‑256 encryption; encryption keys are rotated annually; procedures for handling compromised keys are documented. This ties into Annex A cryptography controls.
- Incident Response and Business Continuity Policy – Defines how the organisation detects, reports and responds to security incidents and how it maintains operations during disruptions. Example: an incident response team is defined; incidents are categorised and escalated within specified time frames; recovery time objectives are set for each critical function. This policy satisfies requirements for operation and performance evaluation (clauses 8 and 9).
- Vendor and Third‑Party Security Policy – Outlines how you select, onboard and monitor vendors. It requires risk assessments and contractual security clauses. Example: vendors processing sensitive data must complete a risk assessment; they must provide certifications (such as ISO 27001 or SOC 2) and agree to notify of incidents within 24 hours. This policy directly addresses vendor risk, which is a major source of breaches.
- Training and Awareness Policy – Ensures employees and contractors receive regular training on security practices and awareness of threats like phishing. Example: all staff complete security awareness training annually; phishing simulations occur twice a year; new hires receive a security briefing during onboarding. This policy responds to the human element in breaches.
- Compliance, Audit and Review Policy – Explains how you monitor and audit the ISMS, manage non‑conformities and stay current with legal requirements. Example: internal audits are scheduled annually; management reviews occur quarterly; a register of applicable laws and regulations is maintained and reviewed for changes. This supports clauses 9 and 10 and demonstrates continual improvement.
- Document and Record Control Policy – Sets the process for creating, approving, versioning, retaining and disposing of policies and other ISMS documents. Example: all documents are stored in a central repository with version history; records are retained for at least three years and then securely destroyed; changes require approval from the policy owner. This ensures documentation integrity.
Additional Topic‑Specific Policies
Small organisations may not need dozens of stand‑alone policies, but enterprise buyers often expect them. Additional policies may include Acceptable Use (guidelines for using company assets), Clear Desk/Screen (reducing shoulder surfing), Remote Working (secure remote access), Network Security, Change Management, Data Retention, Malware and Antivirus, Backup, Logging and Monitoring, Secure Development, Physical and Environmental Security, Information Transfer and Secure Coding. Each addresses a specific set of Annex A controls. For example, a Remote Working Policy might require personal devices to register with an endpoint management system and mandate use of a virtual private network. A Change Management Policy might define how changes are requested, assessed, approved and recorded. Instead of writing separate documents for every control, busy teams can group related topics in modular sections attached to core policies.
Mapping Policies to ISO 27001 Controls
The table below links the core policies above to categories in Annex A (ISO 27001:2022). The table uses short phrases rather than long sentences to comply with the formatting guidance.
Building Your Policy Framework: A Practical Step‑by‑Step Guide
Implementing the ISO 27001 policies required can feel overwhelming, but a structured approach helps busy teams make progress without burning out. Below is a nine‑step plan drawn from our delivery work and the requirements of clauses 4–10. Each step includes pragmatic tips.
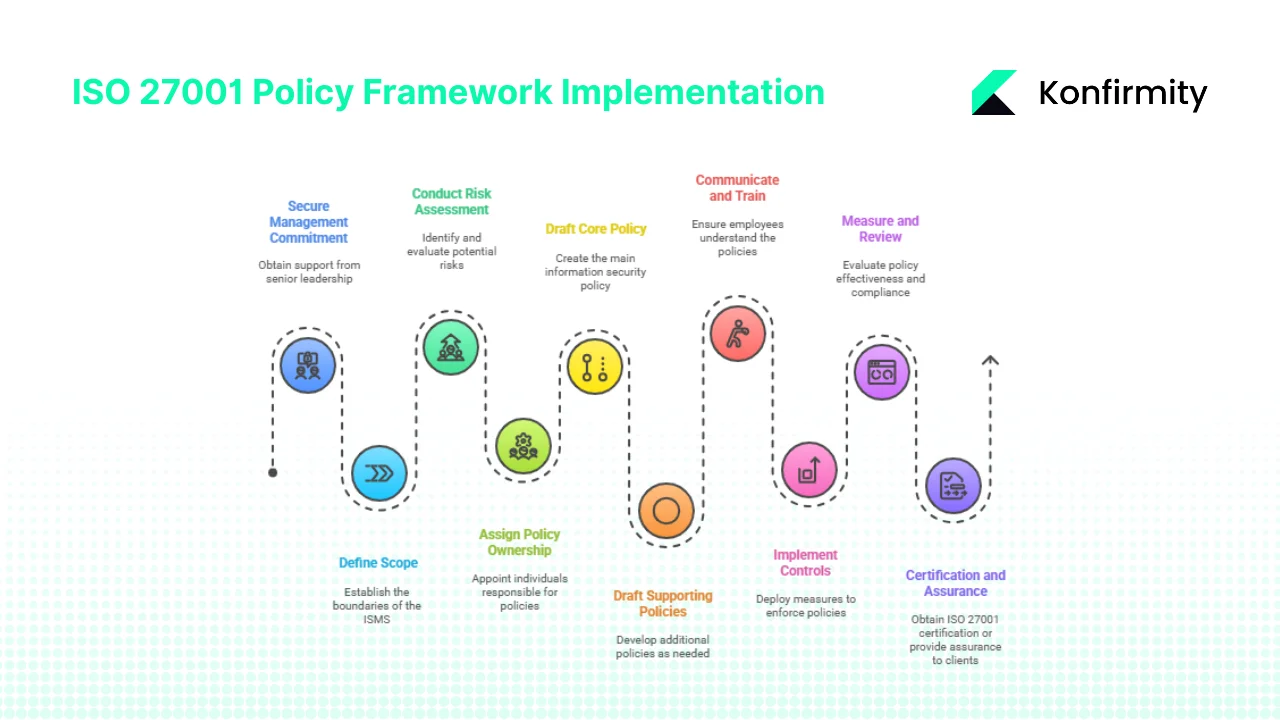
1. Secure Management Commitment and Define Scope
Start by getting explicit support from senior leadership. Clause 4 requires you to define the ISMS scope—the business units, processes, locations and information assets covered. Involve stakeholders from engineering, product, legal and sales to understand client expectations. Draft a scope statement that excludes areas not relevant (e.g., an internal marketing site) and explain why. Management should approve this scope and commit resources for the programme.
2. Conduct Risk Assessment and Asset Inventory
Identify your information assets, classify them (confidential, restricted, public) and map them to the business processes and client obligations. Perform a risk assessment considering threats, vulnerabilities and potential impacts. Record risks in a register and determine treatment plans. Many companies use the Common Vulnerability Scoring System (CVSS) to prioritise fixes. Tie this work to your Risk Management Policy and to clauses 4 and 6 of the standard.
3. Assign Policy Ownership
Appoint owners for each policy. Typically the CISO owns the information security policy, while technical leads may own specific policies such as access control or cryptography. Clarify responsibilities for drafting, approving, communicating and reviewing policies. Set a review cycle (e.g., annual) and record version history in your Document Control Policy. Shared ownership ensures subject matter experts are accountable for content accuracy and enforcement.
4. Draft the Core Policy
Use a template to create your information security policy. Include purpose, scope, definitions, roles, commitments to satisfy applicable requirements and continual improvement, broad objectives and references to supporting documents. Ensure it addresses management commitment and is appropriate to organisational context, as required by clause 5.2. Senior management should review and sign the policy. Make it accessible to employees, contractors and, where necessary, clients.
5. Draft Supporting Policies
Use the core list above as your checklist. Prioritise policies based on risk and client demands. For instance, if you process healthcare data, a Business Continuity and Vendor Security Policy should be among the first, given the high breach costs in healthcare and the prevalence of third‑party attacks. If you host customer data in public cloud platforms, a Cryptography Policy and Network Security Policy are critical. Write policies in clear language; avoid mixing process steps. Where possible, group related topics into modular sections to avoid a proliferation of documents.
6. Communicate, Train and Roll Out
Policies are useless if people don’t know about them. Clause 7 requires competence and awareness. Conduct training for employees, contractors and relevant third parties. Use a variety of formats: e‑learning modules, live sessions, short videos and interactive phishing simulations. Require attestations that employees have read and understood the policies. Include security orientation in onboarding and vendor induction. Make policies accessible through an intranet or knowledge base.
7. Implement Controls and Monitor Enforcement
Deploy technical and organisational controls to enforce the policies. For access control, implement single sign‑on and multi‑factor authentication. For asset management, maintain inventory tools. For incident response, set up monitoring, alerting and incident ticketing. Logging and auditing tools help generate evidence of compliance. Document these controls in procedures and link them to policies. Internal audits should check both the existence of policies and evidence of enforcement, addressing clause 9 requirements.
8. Measure, Review and Improve
Clause 9 and clause 10 require you to evaluate performance and manage non‑conformities. Conduct regular internal audits and management reviews. Use metrics such as number of incidents, mean time to detect and remediate, training completion rates and policy exceptions. Document non‑conformities and corrective actions. Update policies when business models change or new threats emerge. Continual improvement is not optional; auditors look for evidence that you act on findings.
9. Certification and Client Assurance
If you plan to become ISO 27001 certified, engage an accredited certification body. Prepare documentation, evidence of control implementation and records of monitoring. Certification involves Stage 1 (document review) and Stage 2 (evidence of implementation) audits followed by surveillance audits. Without certification, you can still provide assurance to clients. Sharing your policy framework, audit reports and evidence of enforcement can satisfy vendor assessments. In our experience, clients shorten procurement cycles when suppliers provide ready documentation. With Konfirmity’s managed service, customers typically achieve SOC 2 and ISO 27001 readiness in 4–5 months versus 9–12 months through self‑managed efforts, and they save hundreds of hours of internal time—around 75 hours per year versus over 550 hours.
CTA: Book a demo
Templates, Examples and Practical Tips
Structure of a Policy Document
Policies should be concise and structured. A typical layout includes:
- Purpose/Objectives – Why the policy exists and its intended outcomes.
- Scope – The business units, locations, systems and data covered.
- Definitions – Clarification of technical terms used in the policy.
- Roles and Responsibilities – Who is accountable for implementing and enforcing the policy.
- Policy Statements – Broad rules or principles (e.g., “All users must use multi‑factor authentication when accessing production systems”).
- Compliance/Enforcement – Consequences for violations and process for exceptions.
- Review/Revision History – Dates and responsible parties for reviews and updates.
- Approval – Senior management sign‑off, often recorded in meeting minutes or an electronic approval system.
Sample Snippets
Below are example statements that can be adapted:
- Access Control Policy – “User access to systems must be authorised by the asset owner. Access rights are removed within 48 hours of employee exit. Privileges are reviewed quarterly by the system owner.”
- Incident Response Policy – “Any employee who becomes aware of a security incident must report it immediately to the incident response team via the designated channel. The team classifies incidents within one hour and initiates appropriate response plans. Lessons learned are documented and feed into process improvements.”
- Vendor Security Policy – “Before onboarding a third‑party service provider, the vendor risk management team must conduct a risk assessment, obtain assurance reports such as SOC 2 or ISO 27001 certificates, and include security obligations in the contract. Vendors processing sensitive data must notify the company of any security incident within 24 hours.”
Practical Tips for Busy Teams
- Use Policy Libraries – Many organisations waste months writing policies from scratch. Use vetted templates as a starting point, then customize them to your context. Konfirmity provides libraries compatible with ISO 27001, SOC 2, HIPAA and GDPR.
- Prioritise Based on Risk – You do not need to produce dozens of documents on day one. Start with the core policies that address the highest risks and the topics clients ask about most, then add more as your programme matures.
- Make Policies Living Documents – Schedule regular reviews. Use version control and document change history. Update policies based on audit findings, incident post‑mortems and changes in the threat landscape.
- Record Evidence of Enforcement – Policies alone do not satisfy auditors. Keep records of training completions, access reviews, risk assessments and vendor questionnaires. Use automation where possible to collect and store evidence.
- Fit Policies to Business and Regulatory Context – Consider your business model, geographic markets and regulatory environment. For example, healthcare organisations must meet HIPAA rules; companies processing personal data in Europe must meet GDPR; SaaS companies may need SOC 2. Map policies to these requirements to avoid duplication.
- Use Dedicated Expertise – A human‑led managed service, like Konfirmity, embeds experienced practitioners into your team. We do the heavy lifting of implementing controls and collecting evidence so your team only needs to spend around 75 hours per year maintaining audit readiness, compared with over 550 hours in self‑managed programmes.
Common Pitfalls and How to Avoid Them
- Policies exist on paper but are not enforced – Auditors look for evidence that policies are applied. Make sure procedures, controls and monitoring back up the statements in your policies.
- Using generic templates without adaptation – Simply downloading a template without customising it to your business context can signal a lack of ownership. Adjust content to reflect your environment, processes and risk appetite.
- Outdated policies – A policy that hasn’t been reviewed in three years suggests neglect. Schedule regular reviews and updates to reflect new threats, regulatory changes and business growth.
- Over‑documenting without risk context – Policies should flow from risk assessments. If you deploy a control because a template said so but it doesn’t mitigate a relevant risk, clients will ask why. Document the link between each policy and specific risks or client requirements.
- Neglecting vendor risk – Third‑party breaches cost organisations millions. Make vendor assessments a formal part of your ISMS. Require vendors to provide assurance reports and follow your security expectations.
How a Strong Policy Framework Helps You Win Enterprise Clients
Documented policies show maturity. Enterprise buyers want evidence that your security programme is not ad‑hoc. When responding to due‑diligence questionnaires, you can provide copies of your Information Security, Access Control, Vendor Security and Incident Response policies instead of writing ad‑hoc answers. This reduces friction and builds trust. It also helps satisfy compliance requirements. For instance, healthcare clients under HIPAA must ensure their business associates protect electronic protected health information. When you share your Business Continuity and Incident Response Policy and training records, you address this obligation. GDPR, SOC 2 and emerging artificial intelligence security frameworks all require documented governance and control design. A thorough policy set shows you take these obligations seriously.
Konfirmity’s managed service is built around “start with security and arrive at compliance.” We implement controls inside your stack, monitor them continuously and maintain audit readiness year‑round. Compared with software platforms that only collect artefacts or consultants who leave after handing over a report, our team executes and operates the programme. That approach yields tangible results: clients see 75 percent fewer audit findings, achieve readiness months sooner and have evidence ready when procurement teams ask for it. Instead of chasing paperwork before each sale, you present a mature security programme with strong policies, procedures and controls.
CTA: Book a demo
Conclusion
Policies are the backbone of an ISO 27001 programme and a critical signal to enterprise buyers. While only the information security policy is explicitly named in the standard, implementing Annex A controls and addressing your risks means producing a suite of supporting policies. Together, these documents define what your organisation stands for in information security, guide behaviour, and demonstrate governance. Building this framework requires management commitment, risk assessment, clear ownership, thoughtful drafting, training, control implementation, monitoring, review and improvement. Using templates, engaging experts and prioritising based on risk can make the task manageable.
For cloud vendors selling to regulated sectors, strong policies can differentiate you. They reduce delays in procurement, show that you understand client obligations and provide a foundation for SOC 2, HIPAA, GDPR and artificial intelligence security compliance. Start with your information security policy, build out the supporting documents, and treat them as living guidance. Combined with continuous monitoring and evidence collection, this approach not only satisfies auditors but also protects your customers and your business.
FAQs
1) What are the mandatory policies for ISO 27001?
Clause 5.2 of ISO 27001 requires top management to establish an information security policy. This policy must be documented, approved, communicated and updated. Other policies become effectively required when you implement specific Annex A controls or when your risk assessment identifies the need for them. Common examples include access control, asset management, risk management, incident response and vendor security policies.
2) Which ISO 27001 clauses are mandatory for certification?
The mandatory clauses are clauses 4 through 10. Clause 4 covers the organisation’s context and scope; clause 5 addresses leadership and commitment; clause 6 deals with planning and risk management; clause 7 covers support activities such as resources, competence and communication; clause 8 covers operation and implementing controls; clause 9 covers performance evaluation and internal audit; and clause 10 covers improvement and corrective actions.
3) What are the ISO 27001 requirements?
The requirements involve establishing, implementing, maintaining and continually improving an ISMS. Organisations must define their scope, secure leadership commitment, set objectives, allocate resources, plan operations, perform risk assessments, implement controls, measure performance, conduct internal audits and handle non‑conformities. A Statement of Applicability must show which Annex A controls apply and why.
4) What are “5.1 policies for information security” in ISO 27001?
In older versions of the standard (ISO 27001:2013), Annex A.5.1 contained a control titled “Policies for information security,” which required organisations to define management direction via policies. In ISO 27001:2022 this requirement corresponds to clause 5.2, which requires an information security policy appropriate to the organisation’s purpose and context. In practice, this means having a broad policy and supporting topic‑specific policies.
5) What’s the difference between a policy and a procedure under ISO 27001?
A policy is a broad statement of intent that sets direction (“we commit to protecting the confidentiality, integrity and availability of information”). A procedure describes how to implement that intent, often in step‑by‑step detail. HighTable stresses that policies communicate what you do and why, and should not include detailed process steps. Procedures, work instructions and runbooks provide the specifics.





.svg)



.svg)
.svg)