Most enterprise buyers now request security assurances before procurement contracts are signed. SOC 2 is one of the most common frameworks used to demonstrate that a service provider manages its systems and data in a trustworthy way. This article explains why SOC 2 Policies Required is more than a checklist—it is a structured approach to risk reduction and continuous improvement. As breaches grow in cost—IBM’s 2024 study reported the average breach at USD 4.88 million and the 2025 report still found the average around USD 4.4 million—enterprise clients want confidence that vendors have defined policies, controls, and evidence to protect sensitive data. For service providers, policies are not only documentation for auditors; they inform day‑to‑day behaviour and determine whether technical controls operate effectively over time. This guide, written from Konfirmity’s perspective after supporting over 6,000 SOC 2 and ISO 27001 audits, provides a detailed roadmap for drafting, implementing, and maintaining the policies needed for SOC 2 compliance. It also shows how to turn policy requirements into meaningful controls that help close enterprise deals.
What Are SOC 2 Policies and Why They Matter
The American Institute of Certified Public Accountants (AICPA) defines a SOC 2 report as an examination of controls at a service organization that relate to the security, availability, processing integrity, confidentiality, or privacy of the system used to process users’ data. In practice, “policies” are formal documents approved by leadership that set expectations for how an organization will protect information, manage access, handle incidents, retain data, and use third‑party services. Policies are not simply high‑level statements; they provide direction that guides procedures, technical configurations, and ongoing monitoring. When properly designed, they support specific security controls such as multi‑factor authentication, least‑privilege access reviews, encryption, and logging. They also help teams satisfy contractual obligations, regulatory requirements (such as HIPAA’s administrative, physical, and technical safeguards), and risk appetites defined by management. Importantly, auditors rely on documented policies as evidence that an organization has established governance—without them, even strong technical controls may be deemed ineffective. For buyers, clear policies reflect a mature security posture that reduces the friction of vendor due‑diligence processes.

Mapping Policies to the Trust Services Criteria
The SOC 2 Trust Services Criteria (TSC) provides the control framework against which auditors assess service organizations. Security is the only mandatory criterion, while availability, processing integrity, confidentiality, and privacy are optional depending on the nature of services. The security criterion focuses on logical and physical access controls, system operations, change management, and risk mitigation. Policies supporting this criterion include information security, access control, change management, and vendor management. The confidentiality criterion requires controls to protect confidential information; policies should cover data encryption, role‑based access, and nondisclosure agreements. Privacy policies address personal data collection, storage, and deletion, aligning with regulations like GDPR and HIPAA. Availability policies cover business continuity and disaster recovery, ensuring services remain functional during disruptions. Though some criteria are optional, most enterprise buyers now ask for at least security and availability; Vanta’s 2024 State of Trust Report found that 89% of SOC 2 reports include only these two criteria. Mapping policies to the relevant criteria early in the program helps ensure that each requirement is addressed and that controls are not over‑ or under‑scoped.
Step‑by‑Step Guide to Creating Required SOC 2 Policies
Creating the SOC 2 Policies Required for an audit is best approached systematically. Below is a step‑by‑step process based on our field experience.
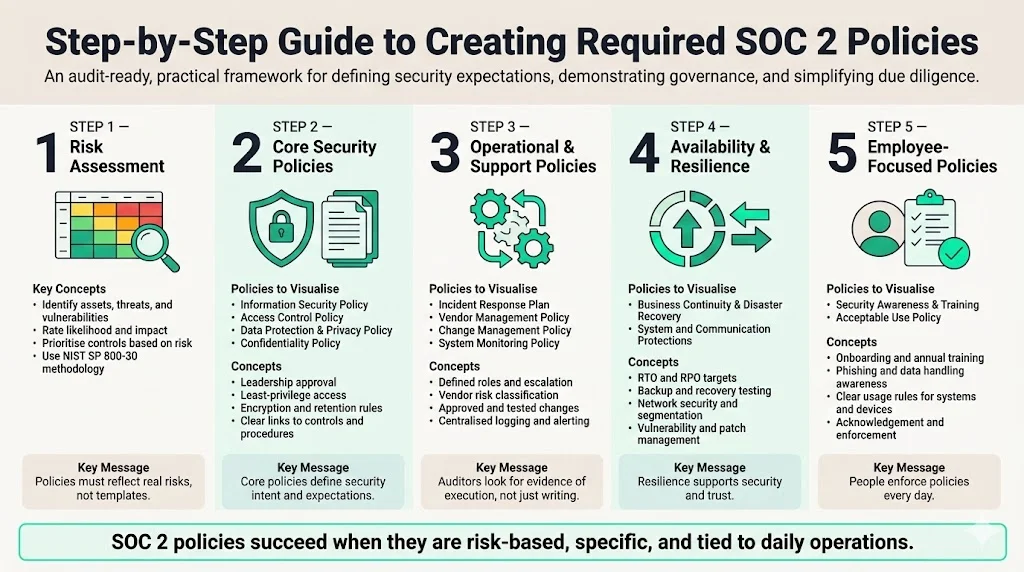
Step 1: Start with a Risk Assessment
A risk assessment establishes the foundation for all subsequent policies. NIST Special Publication 800‑30 outlines a four‑step process: prepare for the assessment, conduct the assessment, communicate results, and maintain the assessment. During preparation, organizations define scope, assumptions, and risk models. In our engagements, we typically facilitate workshops to identify assets (e.g., production systems, customer data, intellectual property), threats (e.g., insider abuse, credential theft, supply‑chain compromise), and vulnerabilities. Each risk is then rated based on likelihood and impact, guiding the prioritization of security controls and the scope of the policies. For example, if the assessment reveals that third‑party cloud services host sensitive customer data, vendor management and encryption policies become a priority. HIPAA’s guidance similarly stresses that risk analysis is the first step before implementing safeguards. For SOC 2, a risk assessment is not just an audit artifact; it informs design decisions and demonstrates that the organization takes a risk‑based approach rather than simply copying templates.
Step 2: Draft Core Security Policies
After identifying risks, organizations should draft the core policies that address the security criterion. These include:
- Information Security Policy: This high‑level document articulates the organization’s overall approach to protecting information assets. It covers the purpose of the security program, roles and responsibilities (such as the CISO and control owners), and the expectation that all employees follow security procedures. It should also reference compliance obligations (e.g., HIPAA, GDPR) and commit to periodic reviews. A strong information security policy sets the tone for the entire program and signals leadership’s commitment to security.
- Access Control Policy: Access management is one of the most scrutinized areas in SOC 2 audits. Policies must specify that access is granted based on job responsibilities (least privilege), require multi‑factor authentication for privileged accounts, and define review frequencies. The policy should outline onboarding and offboarding procedures, approval workflows for new access, and periodic recertification of user privileges. Auditors expect evidence of regular access reviews and removal of unused accounts. Our experience shows that control failures often stem from inconsistent deprovisioning after employee departures or vendor engagement termination.
- Data Protection and Privacy Policies: These documents describe how the organization classifies, collects, uses, stores, and disposes of data. They should require encryption for data at rest and in transit, define retention periods, and address cross‑border data transfers. They also need to align with privacy regulations. The Onspring guide notes that confidentiality policies should include data masking or redaction, role‑based access, encryption, and nondisclosure agreements.
- Confidentiality Policy: While similar to data protection, a confidentiality policy focuses on customer and internal information that must remain confidential. It should define what constitutes confidential information, require nondisclosure agreements for employees and contractors, and outline procedures for handling confidential communications and documents.
These core policies are often the first documents auditors review. They should be concise yet specific, avoid vague language, and clearly link to procedures and controls.
Step 3: Operational and Support Policies
Operational policies govern how technical systems are managed and how the organization responds to incidents. Key policies include:
- Incident Response Plan: This plan defines how the organization prepares for, detects, responds to, and recovers from security incidents. It should assign roles (incident commander, communications lead), specify triggers for invoking the plan, detailed documentation and evidence collection requirements, and reference playbooks for common scenarios (e.g., phishing, ransomware). The Security Boulevard article highlights that an effective incident response policy outlines steps for identifying, reporting, containing, and mitigating incidents. The plan must also require post‑incident reviews and continuous improvement. In our audits, we often see incidents documented in ticketing systems with evidence of containment and communication, which auditors review to assess control effectiveness.
- Vendor Management Policy: Service providers increasingly rely on third‑party vendors, making supply‑chain risk a prominent concern. The NIST Cybersecurity Framework 2.0 emphasises the “Govern” function, which includes inventorying suppliers, incorporating cybersecurity expectations into contracts, and preparing joint incident response plans. Scytale’s vendor risk management guidance recommends classifying vendors based on data sensitivity, performing risk assessments, maintaining a vendor inventory, and monitoring controls. The policy should require onboarding due diligence (security questionnaires, penetration test reports, compliance attestations), define roles for vendor owners, and specify review intervals. Because vendor risk is a common source of findings, we implement automated workflows that track vendor contracts, security posture, and re‑assessment dates.
- Change Management Policy: Change control ensures that modifications to systems are authorized, tested, and documented. A policy should require change requests to include description, risk assessment, approval from an appropriate authority (e.g., engineering manager), and evidence of testing. It should also define emergency change procedures. Auditors will inspect change management logs and look for evidence that unauthorized changes are prevented and that rollback plans exist. In Konfirmity’s delivery work, we integrate change management with version control and CI/CD pipelines, automatically capturing approvals and testing evidence.
- System Monitoring Policy: Monitoring policies describe logging standards, alert thresholds, and responsibilities for reviewing logs. They should require centralized log management, retention periods, and regular analysis for anomalies. The Onspring guide notes that common SOC 2 controls include intrusion detection and system monitoring. The policy must state who reviews logs, how often alerts are triaged, and how logging covers both production systems and cloud providers.
Step 4: Availability and Resilience Policies
Availability and resilience policies support the optional availability criterion and contribute to security and business continuity. Key policies include:
- Business Continuity and Disaster Recovery (BC/DR) Policy: This policy outlines strategies to keep services running during disruptions. It should define recovery time objectives (RTO) and recovery point objectives (RPO) for critical systems, detail backup and replication procedures, and specify roles in continuity planning. Testing the BC/DR plan at least annually and after significant changes is important; auditors will review test results as evidence.
- System and Communication Protections Policy: This policy describes network security requirements such as firewall configurations, intrusion detection/prevention, network segmentation, and secure protocols (TLS, SSH). It may also include secure configuration baselines for endpoints and servers, patch management schedules, and vulnerability management procedures. These technical safeguards support both security and availability by reducing the likelihood of outages caused by attacks. Our managed service includes continuous vulnerability scanning, CVSS‑based triage, and SLA enforcement for remediation.
Step 5: Employee‑Focused Policies
People are a crucial component of security. Employee‑focused policies ensure that the workforce understands and follows security expectations.
- Employee Training and Awareness Policy: HIPAA requires covered entities to train all workforce members on policies and to implement a security awareness program. SOC 2 auditors likewise expect evidence that employees receive regular training on information security, privacy, acceptable use, phishing awareness, and relevant compliance obligations. The policy should define training frequency (e.g., annually and upon onboarding), content requirements, and methods of tracking completion. In our experience, linking training modules to policy updates helps keep content relevant. The policy should also cover specialized training for engineers on secure coding and threat modelling.
- Acceptable Use Policy: This document defines what employees can and cannot do on corporate systems. It should cover use of company devices, acceptable internet and email usage, restrictions on installing software, rules for handling sensitive data, and consequences of violations. The acceptable use policy ties directly to access control and data protection controls. During audits, evidence may include signed acknowledgements or logs showing enforcement of acceptable use violations.
Procedures vs. Policies
Many organizations confuse policies with procedures. A policy defines the intent and rationale—what must be done and why—while a procedure defines how and who will accomplish it. For example, an access control policy might state that user access must be reviewed quarterly. The corresponding procedure will specify which system administrators run the access reports, what tool is used to compare entitlements to job roles, how exceptions are documented, and who approves remediations. Similarly, an incident response policy declares that all incidents must be documented and reported within 24 hours; the procedure details how the incident ticket is created, which communication channels to use, and how to preserve logs for forensic analysis. Distinguishing policies from procedures helps ensure that high‑level governance is stable while procedural details can evolve with tooling and organizational changes.
Implementation Tips
Implementing the SOC 2 Policies Required goes beyond drafting documents. Success depends on adoption by teams and integration into daily operations:
- Socialize Policies: Engage stakeholders early. Leadership should communicate the importance of policies and provide training. Security champions in engineering, product, and operations teams can advocate for adherence. Use intranet portals, tooltips in ticketing systems, and periodic newsletters to keep policies visible.
- Leverage Tools and Templates: Start with proven templates tailored to your industry, then modify them based on your risk assessment. Konfirmity provides templates that align with the Trust Services Criteria and integrate with common tooling (GitHub, AWS, Jira). Automating evidence collection—access logs, change approvals, vulnerability scans—reduces manual effort and ensures audit‑ready records. In our experience, using integrated tools can reduce internal effort from 550–600 hours per year to around 75 hours, freeing teams to focus on product development.
- Versioning and Approvals: Each policy should have a version number, effective date, and approval signatures (e.g., CEO, CISO). Maintain a revision history and track comments. Use a policy management system to send reminders for periodic reviews. Auditors will look for evidence that policies were reviewed and approved within the observation period.
Ongoing Maintenance and Review
Policies are living documents. Best practice is to review them at least annually or whenever there is a significant change in systems, processes, regulations, or risk landscape. Onspring recommends leaving at least one to two weeks between the end of the observation period and the audit to organize evidence. The same article notes that Type II audits typically cover a period of 3–12 monthscompassitc.com, and a shorter period (3–6 months) may help first‑time audits but offers less assurance. Documenting review cycles—e.g., specifying that the access control policy is reviewed every 12 months or sooner if a new cloud provider is adopted—satisfies auditor expectations. During reviews, solicit feedback from control owners and incorporate lessons learned from incidents. For example, if a phishing attack exploited a gap in training, update the training policy and modules accordingly. A culture of continuous improvement ensures that policies remain relevant and effective.
Preparing for Audit: What Auditors Look For
Auditors assess both the existence and the effectiveness of controls. Evidence artifacts include logs of policy approvals, sign‑off sheets from training, change management tickets, access review reports, and vendor risk assessments. The Onspring guide lists common controls such as multi‑factor authentication, intrusion detection, encryption, and access reviews. The Security Boulevard article lists 21 policies auditors often examine—such as acceptable use, access control, change management, and vendor management—and emphasizes the need for documentation and regular reviews. Auditors will test whether incidents were detected and handled according to policy, whether user access was regularly recertified, and whether change approvals were logged. They will also sample evidence across the observation period; for example, if a policy requires quarterly access reviews, the auditor may request evidence from every quarter. Our experience shows that preparedness, including organized evidence and established runbooks, reduces audit time from nine months to four to five months. In Type II audits, which cover operating effectiveness over time, auditors may also evaluate continuous monitoring activities. Having documented procedures for system monitoring and incident response ensures that the organization meets the Trust Services Criteria.
Conclusion
Developing SOC 2 Policies Required is not about writing generic documents; it is about designing and operating controls that satisfy business, regulatory, and contractual obligations while supporting growth. As more enterprise and healthcare buyers make SOC 2 Type II a prerequisite—TrustCloud’s 2024 survey noted that 76% of enterprise buyers require it—organizations cannot rely on last‑minute compliance efforts. A mature program starts with risk assessment, develops targeted policies aligned to the Trust Services Criteria, and implements procedures, monitoring, and continuous improvement. Human‑led, managed security programs like Konfirmity’s demonstrate that security and compliance can coexist with product velocity. When policies guide daily behaviour and evidence is collected continuously, audits become a validation of operating excellence rather than a scramble to generate artefacts. Security that reads well in documents but fails under incident pressure is a liability; build the program once, operate it daily, and let compliance follow.
FAQs
1. What is the SOC 2 compliance checklist?
A SOC 2 compliance checklist is a structured list of policies, controls, and evidence required to satisfy the Trust Services Criteria. It typically includes risk assessments, information security policy, access control policy, incident response plan, vendor management, change management, system monitoring, business continuity, and employee training. Each item on the checklist should trace back to a control objective and have associated procedures and evidence. For example, the incident response plan must include documented roles and triggers, and access control must include multi‑factor authentication and regular reviews. The checklist helps ensure that the SOC 2 Policies Required are exhaustive and that evidence is collected during the audit period.
2. Is SOC 2 compliance mandatory?
SOC 2 is not mandated by law, unlike HIPAA or GDPR. However, it has become a contractual requirement in many enterprise procurement processes. Surveys show that a majority of enterprise buyers refuse to do business with vendors lacking a SOC 2 Type II report. The voluntary nature of SOC 2 does not diminish its importance; rather, it allows organizations to proactively demonstrate their control environment and differentiate themselves in the market.
3. What are the mandatory criteria for SOC 2?
The security criterion—often called the Common Criteria—is mandatory for every SOC 2 examination. It covers logical and physical access controls, system operations, change management, and risk mitigation. The other criteria (availability, processing integrity, confidentiality, privacy) are optional and should be included if relevant to the services provided. Many clients request at least availability and confidentiality in addition to security because they relate to uptime and data protection.
4. How often does SOC 2 require policies to be reviewed and approved?
SOC 2 does not dictate a specific frequency, but best practice and auditor expectations call for regular reviews—typically annually or when significant changes occur. Onspring’s guidance recommends selecting an observation period of 3–12 months and leaving time to organize evidence before the audit. Policies should include review cycles, and organizations should maintain evidence of approvals and revisions. In our programs, we align policy reviews with quarterly risk assessments and annual strategic planning to ensure that policies remain relevant and effective.





.svg)



.svg)
.svg)