In 2026, enterprise buyers rarely sign a contract without asking for assurance artifacts. Security questionnaires, data processing agreements, and vendor risk assessments arrive early in procurement. Without operational controls and continuous evidence, deals stall—even when teams believe they are “ready” on paper. A well‑run GDPR Gap Assessment Guide builds credibility with these buyers. It verifies that your organisation’s handling of personal data aligns with the General Data Protection Regulation (GDPR) and supports other frameworks like SOC 2, ISO 27001, and HIPAA.
As the founder of Konfirmity, a human‑led managed security and compliance service, I’ve seen how real control design, continuous monitoring, and year‑round operations shorten sales cycles. This article lays out why companies that sell to enterprise clients must prioritise GDPR gap assessments, how to run them effectively, and how to use the findings to strengthen your security program. It integrates lessons from over 6,000 audits supported by our team, 25+ years of combined expertise, and current data on fines, breach costs, and audit timelines. Throughout, I reference authoritative sources such as the AICPA’s Trust Services Criteria, ISO 27001 guidance, NIST’s Privacy Framework, and enforcement statistics to ground the discussion in facts.
What Is a GDPR Gap Assessment?
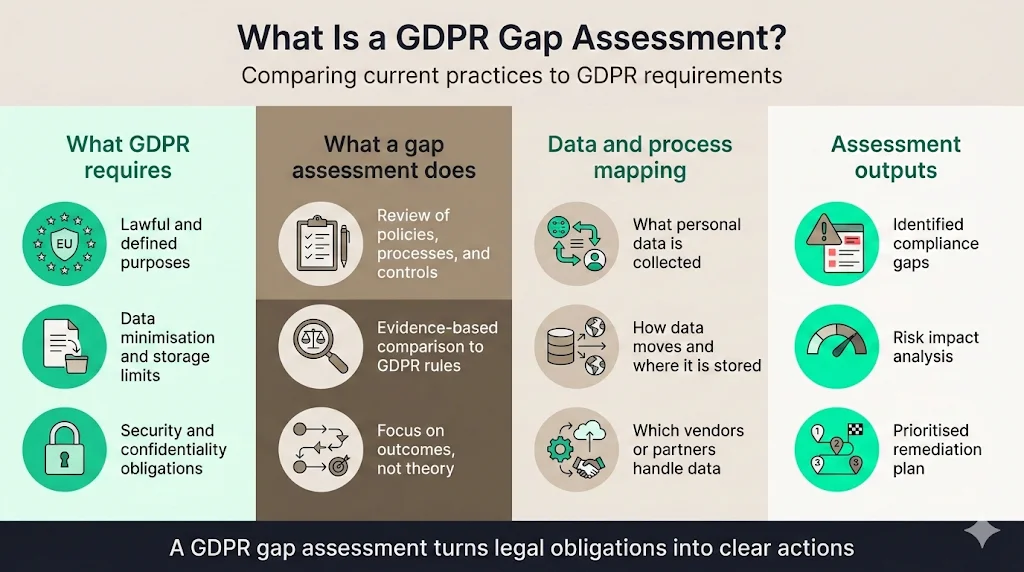
GDPR is the European Union’s data‑protection framework. It governs how organisations collect, use, store, and share personal data about people in the EU. Key principles include purpose limitation, data minimisation, storage limitation, and integrity and confidentiality; Article 5 requires that personal data be collected for specified purposes, kept only as long as necessary, and protected with appropriate security measures. A gap assessment compares your current practices against these legal obligations. It is systematic, evidence‑based, and oriented around outcomes. By mapping processes, policies, and technical controls to GDPR requirements, you identify compliance gaps, understand their risk impact, and develop action plans to close them.
The output of a gap assessment isn’t just a list of problems. It provides:
- A clear inventory of personal data and processing activities—what data you collect, how it flows through your systems, where it is stored, and which third parties handle it.
- An analysis of deficiencies—missing policies, weak controls, outdated practices, or inadequate documentation.
- A risk‑based remediation roadmap—actions ranked by severity and effort to address compliance obligations and improve security.
Why GDPR Gap Assessments Are Essential for Enterprise‑Selling Companies
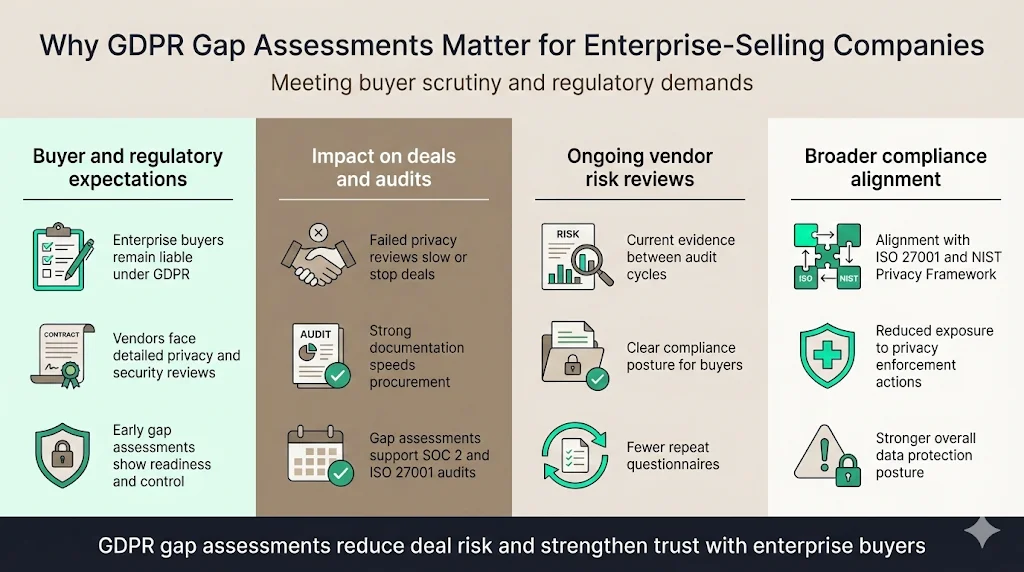
Regulatory and buyer expectations
Enterprise clients must obey strict regulatory requirements. When they outsource processing to a vendor, they remain responsible for personal data under GDPR. As a result, procurement teams issue lengthy questionnaires covering data handling, encryption, access controls, breach notification, and subcontractor oversight. They examine contracts and third‑party risk reviews. A gap assessment done before these conversations shows you have a mature privacy program and can meet data protection obligations. It also positions you to negotiate data processing agreements, security addenda, and indemnity clauses with confidence.
Impact on contracts, audits, and vendor risk reviews
Failing a buyer’s privacy assessment can delay or kill a deal. Conversely, organisations that provide complete documentation—including policies, risk assessments, and evidence of control operation—accelerate closing. A well‑documented gap assessment feeds directly into SOC 2 and ISO 27001 audits. For example, SOC 2 Type II requires controls to operate effectively over an observation period of 3–12 months, and reports are valid for 12 months. An updated gap assessment ensures your evidence remains current between audits. It also simplifies vendor risk reviews, since you can provide buyers with a summary of your compliance posture.
Links to privacy compliance and data protection goals
GDPR compliance supports other frameworks. The ISO 27001 risk assessment process emphasises identifying and evaluating risks to information assets and choosing treatment options based on risk priority. NIST’s Privacy Framework helps organisations manage privacy risk while fostering innovation. By conducting a GDPR gap assessment, you build a strong foundation that aligns with these frameworks. In healthcare, HIPAA penalties can reach over $2.1 million per violation, and 2025 enforcement actions show increasing fines. A robust GDPR program reduces the likelihood of similar privacy violations.
Key Concepts in a Gap Assessment
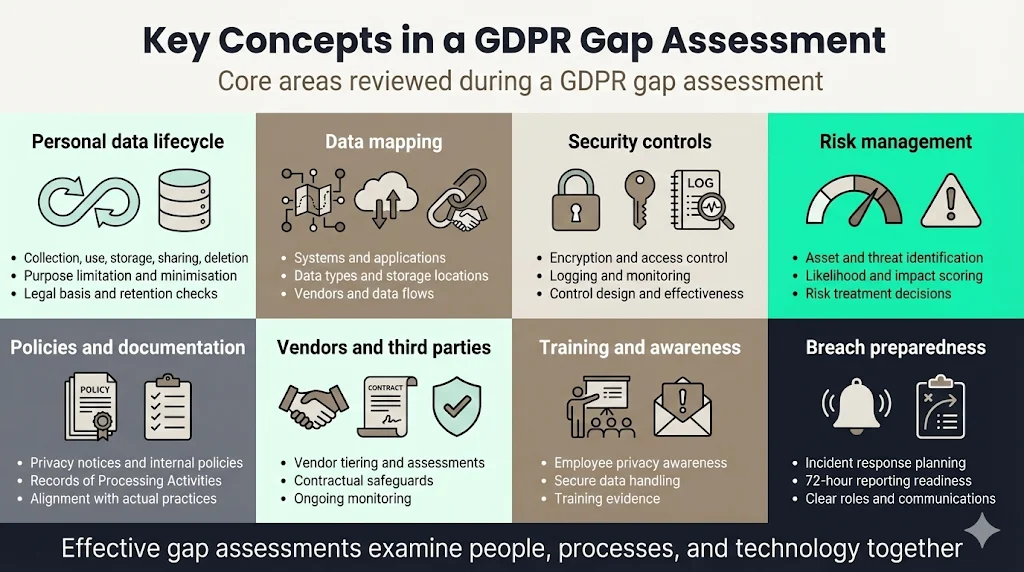
Before diving into step‑by‑step instructions, let’s outline the core topics that underpin an effective GDPR Gap Assessment Guide:
Personal data lifecycle
Personal data flows through stages—collection, use, storage, sharing, and deletion. GDPR’s principles demand minimisation and purpose limitation. A gap assessment traces data from the moment it enters your organisation to its disposal or anonymisation. You’ll ask: Do we collect more data than necessary? Do we process it only for specified purposes? How long do we retain it? For each stage, you document legal basis (consent, legitimate interest, contract) and identify gaps.
Data mapping
Data mapping is the process of identifying data sources, flows, and storage locations. It involves creating an inventory of systems, databases, SaaS applications, and vendors that process personal data. A structured mapping template should capture data sources, data types (e.g., contact details, payment information, health data), storage locations, legal bases for processing, and retention periods. Without a complete map, you can’t assess compliance or risk properly.
Security controls
GDPR requires “appropriate technical and organisational measures” to protect personal data. Security controls include encryption, access control, logging, vulnerability management, and incident detection. In the SOC 2 framework, the Trust Services Criteria emphasise security, availability, processing integrity, confidentiality, and privacy; the security criterion is mandatory for every SOC 2 audit. Assessing controls means verifying design and operating effectiveness across these dimensions.
Risk management
Compliance is about risk reduction, not risk elimination. The ISO 27001 risk assessment methodology calls for establishing context, identifying assets and threats, analysing and evaluating risks using a qualitative or quantitative scale, and choosing treatment options (treat, avoid, transfer, accept)o. A privacy risk scoring system helps prioritise remediation actions based on likelihood and impact.
Privacy policies and documentation
GDPR requires clear, transparent privacy notices and internal policies. You must explain how you collect and use data, provide rights for data subjects (access, rectification, erasure), and document processing activities (Records of Processing Activities – ROPA). Policies should align with Article 5 principles and be easily accessible to employees and customers. An assessment checks that policies are up to date and reflect actual practices.
Vendor assessment and third‑party management
Most organisations rely on vendors (cloud providers, analytics tools, customer support software) to process data. Vendor risk assessment involves identifying critical vendors, collecting information, assessing controls, and monitoring performance. Best practices include tiering vendors by criticality, using standard questionnaires (e.g., CAIQ, SIG), aligning with frameworks like ISO 27001, NIST 800-53, SOC 2, HIPAA, and GDPR, and establishing continuous monitoring. Contracts should include data protection clauses and data transfer safeguards.
Employee training and awareness
GDPR compliance is not solely a legal or technical exercise. Employees who handle personal data must understand privacy principles, secure data handling, and reporting obligations. Training should cover data classification, phishing awareness, secure authentication, and incident escalation. Records of training sessions and completion rates form part of the evidence.
Data breach preparedness planning
Despite best efforts, incidents happen. GDPR requires organisations to report breaches to supervisory authorities within 72 hours and notify affected individuals when there is a high risk to their rights and freedoms. Breach preparedness involves having an incident response plan, procedures for containment and eradication, communication plans, and defined roles. Aligning with frameworks like ISO 27001’s Annex A and SOC 2’s security criteria ensures your plan covers necessary controls.
Before You Begin: Preparations
Assemble Your GDPR Assessment Team
A successful gap assessment is cross‑functional. It should involve:
- Legal and privacy counsel: Interpret GDPR requirements, advise on lawful bases, and review policies.
- Security leaders (CISO or equivalent): Oversee technical controls, incident response, and risk management.
- IT and data owners: Provide access to systems, data flows, and technical documentation.
- Business unit representatives: Explain how data supports marketing, sales, product, and support functions.
- Vendor management: Coordinate third‑party assessments and contract reviews.
Clear roles help avoid confusion. Assign a project lead to coordinate tasks, a legal lead to manage interpretations, and control owners for each domain (access control, encryption, incident response, etc.).
Define Scope
Scope determines the boundaries of your assessment. Define which data categories (customer data, employee data, marketing leads), systems (databases, CRM, HR systems), processes (onboarding, billing, analytics), regions (e.g., EU vs. global), business units, and vendors are in scope. A narrow scope may speed up the assessment but risk missing compliance gaps. A broad scope offers more assurance but requires more resources. Consider prioritising high‑risk areas, such as customer personal data or systems subject to regulatory audits.
Gather Essential Documents
Collect documentation up front. Examples include:
- Privacy policies and public notices: Ensure they reflect actual practices and cover purposes, rights, and contact details.
- Records of Processing Activities (ROPA): Document each processing purpose, data category, data subject type, recipients, legal basis, and retention period.
- Security policies: Encryption standards, access control policies, secure coding standards, change management procedures, logging policies.
- Contracts and vendor agreements: Data processing agreements, sub‑processor lists, service addenda, and data transfer safeguards.
- Incident response plans: Step‑by‑step guides for identifying, containing, and reporting breaches.
- Training records: Dates, attendance, and content of privacy and security training sessions.
Step‑by‑Step Gap Assessment Walkthrough
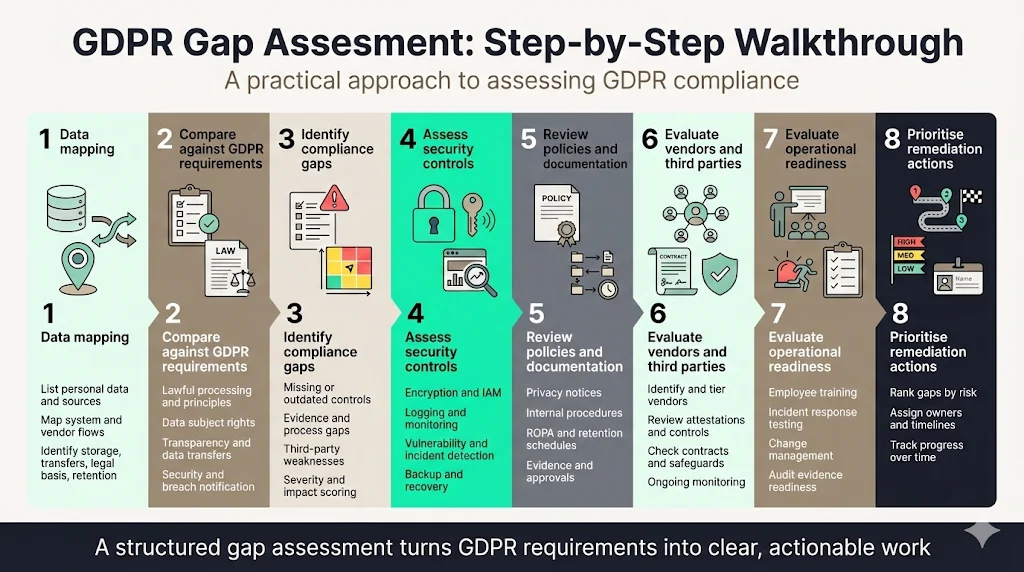
Use this section as the main body of your GDPR Gap Assessment Guide. Each step builds on the previous one and contributes to a comprehensive picture of your compliance posture.
Step 1: Data Mapping
- Document all personal data: List the data you collect (names, contact details, IP addresses, purchase history, health data) and its source (web forms, customer support, analytics tools).
- Map data flows: Draw diagrams showing how data moves between systems—e.g., from your website to your CRM, then to your billing platform and analytics provider.
- Identify storage and transfer locations: Note databases, backups, cloud regions, and third‑party processors.
- Label legal bases and retention periods: For each data element, identify whether the basis is consent, contract, legitimate interest, legal obligation, or vital interest. Document retention schedules and disposal methods.
- Validate accuracy: Review logs, system configurations, and talk to data owners to verify that the map is comprehensive and up‑to‑date.
Step 2: Compare Practices with Regulatory Requirements
Build a GDPR requirements checklist that covers:
- Lawful processing (Articles 6–9): Assess whether each data processing activity has a valid legal basis and whether special categories of data are handled with extra safeguards.
- Principles (Article 5): Check for purpose limitation, data minimisation, accuracy, storage limitation, integrity/confidentiality, and accountability.
- Data subject rights (Articles 12–23): Evaluate your processes for responding to access, rectification, erasure (the “right to be forgotten”), restriction, portability, objection, and automated decision‑making requests.
- Transparency (Articles 12–14): Ensure that privacy notices clearly explain purposes, retention periods, recipients, and rights.
- Data transfers (Chapter V): Confirm that cross‑border transfers use approved safeguards—Standard Contractual Clauses (SCCs), Binding Corporate Rules (BCRs), adequacy decisions, or certification mechanisms.
- Data Protection Impact Assessments (DPIAs): Check whether high‑risk processing undergoes DPIAs and whether the results are reviewed by legal counsel.
- Security measures (Article 32): Evaluate encryption, pseudonymisation, access controls, change management, logging, and incident response.
- Breach notification (Articles 33–34): Ensure your incident response plan meets the 72‑hour reporting requirement and includes communication procedures.
Compare your current practices against this checklist. Note where you meet requirements, where practices are partially implemented, and where they are missing. This gap list becomes the basis for remediation.
Step 3: Identify Compliance Gaps
With your checklist in place, analyse the evidence to identify gaps. Look for:
- Missing controls: For example, no documented data minimisation policy or no multi‑factor authentication on administrative accounts.
- Outdated controls: Policies not updated in the last 18 months; encryption standards not reflecting current best practices.
- Evidence gaps: Controls are implemented but lack records (e.g., access review results, training logs, system activity logs).
- Process gaps: Data subject requests not tracked or responded to within statutory timelines; lack of DPIA for new product features.
- Third‑party gaps: Vendors without security attestations or outdated data processing agreements.
Categorise each gap by severity (high, medium, low) and potential impact (privacy breach risk, contractual breach, customer trust). Use a risk matrix to score gaps based on likelihood and impact. For example, a missing encryption policy might be high severity because it affects all data; an outdated privacy notice may be medium severity but high reputational risk.
Step 4: Assess Security Controls
Review technical and organisational measures that protect personal data:
- Encryption and key management: Evaluate whether data at rest and in transit is encrypted using strong algorithms. Check key rotation and access to encryption keys.
- Access control: Review identity and access management (IAM) policies—least privilege, segregation of duties, periodic access reviews, multi‑factor authentication. Document evidence of regular reviews.
- Logging and monitoring: Verify that system events (logins, privilege changes, data exports) are logged and monitored for anomalies.
- Vulnerability management: Check patching policies, vulnerability scanning frequency, and severity thresholds (e.g., CVSS scores).
- Incident detection: Assess intrusion detection/prevention, endpoint protection, and security information and event management (SIEM) coverage.
- Business continuity and disaster recovery: Confirm that backup and recovery procedures meet availability requirements. In SOC 2, the Availability criterion emphasises backups and continuity planning.
- Change management and secure development: Ensure that changes to code and infrastructure follow documented processes, with security reviews and approvals.
Link your assessment to established frameworks. For instance, ISO 27001 requires risk assessments, treatment plans, and Annex A controls; SOC 2’s Trust Services Criteria emphasise security, availability, processing integrity, confidentiality, and privacy. By aligning your controls with these frameworks, you can reuse evidence for multiple certifications.
Step 5: Review Privacy Policies and Documentation
Internal and external documentation must match reality. Examine your:
- External privacy notices: Confirm they reflect actual data collection, processing purposes, and third‑party disclosures. Check that they explain rights and contact details.
- Internal policies and procedures: Verify that employees have clear instructions on data classification, acceptable use, retention, and disposal. Ensure policies reference GDPR principles and other frameworks.
- Records of Processing Activities (ROPA): Check that each processing activity is documented with purpose, legal basis, categories, retention, and security measures.
- Data retention schedules: Ensure retention periods align with business needs and regulatory requirements; confirm data is deleted or anonymised when no longer required.
- Audit trails and evidence: Keep logs of policy approvals, changes, and training records. During audits, evidence of policy adherence is critical.
Step 6: Evaluate Vendor and Third‑Party Risks
Third‑party risk management is often the weakest link. To evaluate vendors:
- Identify critical vendors: Determine which vendors handle personal data or provide services critical to your operations (e.g., cloud providers, payment processors, email services).
- Categorise vendors by risk: Group vendors into high, medium, and low risk based on data sensitivity, volume, and criticality.
- Collect information: Use questionnaires (e.g., CAIQ, SIG), due diligence reports, and public attestations (SOC 2, ISO 27001, ISO 27701, PCI DSS).
- Assess controls: Evaluate encryption, access control, incident response, and subcontractor management.
- Review contracts: Ensure agreements include Standard Contractual Clauses, data processing clauses, and requirements to notify you of breaches or changes.
- Monitor performance: Establish continuous monitoring of vendor security (e.g., security ratings services), periodic reassessments, and contract renewals.
Step 7: Evaluate Operational Readiness
A compliance program succeeds only if it operates daily. Evaluate:
- Employee training and awareness: Verify that employees complete privacy and security training annually. Training should cover phishing, secure password practices, data classification, and incident reporting. Keep records of completion.
- Incident handling and breach preparedness: Test your incident response plan by running tabletop exercises. Review detection times, escalation paths, communication templates, and lessons learned.
- Change management processes: Confirm that changes to systems and applications follow documented procedures with security reviews and approvals.
- Audit readiness: Ensure that evidence is collected continuously to support audits. In SOC 2, auditors review evidence over 3–12 months; continuous evidence avoids last‑minute scrambles.
Step 8: Prioritise and Document Remediation Actions
After analysing gaps, prioritise actions based on risk and urgency. Use a scoring system combining likelihood, impact, and regulatory significance. For example:
- High priority: Gaps that could lead to immediate non‑compliance or severe breach risk (e.g., no breach notification procedure, missing encryption for sensitive data).
- Medium priority: Gaps that pose moderate risk (e.g., incomplete ROPA, outdated training materials).
- Low priority: Cosmetic or documentation improvements (e.g., minor wording changes in privacy notices).
For each gap, document:
- Description: What’s missing or weak.
- Risk: Potential impact on privacy rights, regulatory compliance, and business objectives.
- Mitigation: Actions required to close the gap—policy updates, technical implementations, new processes.
- Owner: The person or team responsible for implementation.
- Timeline: Target completion date.
This remediation plan becomes a living document that tracks progress and accountability. Integrate it with your project management system to drive execution and ensure nothing falls through the cracks.
Templates and Tools
Templates standardise your assessment and save time. Here are four useful templates:
Gap Analysis Template
Create a table with columns for:
• GDPR requirement/principle (e.g., data minimisation)
• Current state (existing processes and controls)
• Desired state (required controls and practices)
• Risks (impact if gap remains)
• Mitigation actions (steps to close the gap)
This template ensures each requirement is assessed and addressed systematically.
Data Mapping Template
Use a table or spreadsheet with fields for:
• Data source (website, mobile app, customer support)
• Data type (name, email, IP, payment data, health data)
• Storage location (database, file system, third‑party service)
• Legal basis (consent, contract, legitimate interest, legal obligation)
• Retention period (e.g., 3 years, until contract termination)
• Recipients (internal teams, processors, sub‑processors)
Risk Assessment Matrix
Build a matrix with likelihood on one axis and impact on the other. Score each identified gap (e.g., 1–5 for likelihood and 1–5 for impact). Multiply scores to prioritise remediation efforts. This approach reflects ISO 27001’s recommendation to evaluate and prioritise risks.
Audit Checklist
Create a checklist of items to verify during your gap assessment. Include questions like:
• Have all data flows been documented?
• Is there a valid legal basis for each processing activity?
• Are privacy notices accurate and complete?
• Do security controls (encryption, access control) meet current best practices?
• Are vendor agreements up to date and include GDPR clauses?
• Have employees completed privacy training in the last 12 months?
• Is there evidence of regular risk assessments?
Pre‑built templates from compliance tools like Konfirmity’s platform can jump‑start your process. They are mapped to GDPR articles, ISO 27001 Annex A controls, and SOC 2 Trust Services Criteria, allowing reuse of evidence across frameworks.
How to Use Templates Effectively
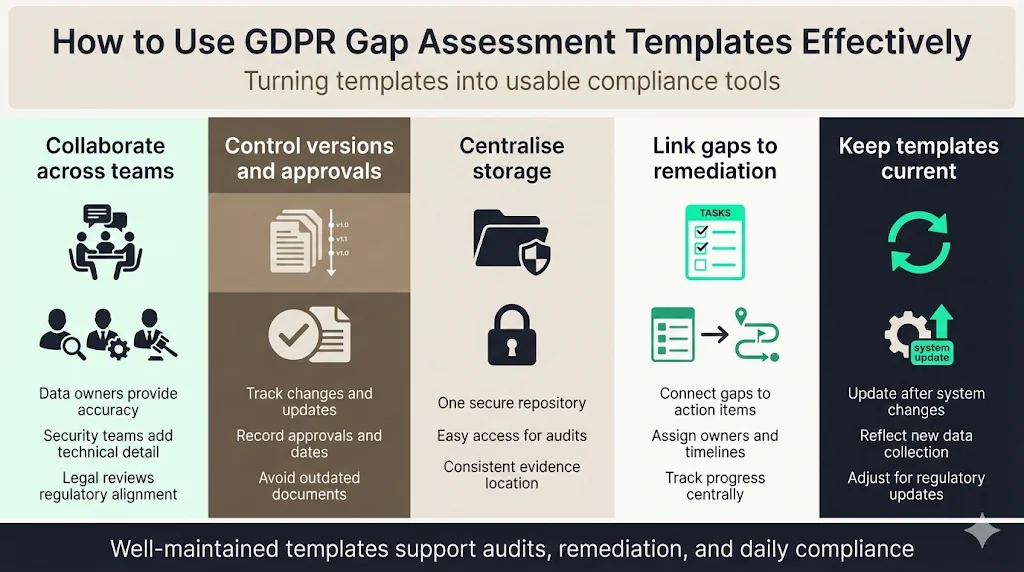
- Collaborate: Involve stakeholders when filling templates. Data owners provide accurate descriptions; security teams supply technical details; legal counsel ensures interpretations align with law.
- Version control: Use a repository or compliance tool to manage versions. Track changes, approvals, and dates.
- Central storage: Store templates and evidence in a secure, central repository accessible to auditors.
- Link to remediation: Tie each gap to actions in your project management system.
- Update regularly: Treat templates as living documents; update them when systems change, new data is collected, or regulations evolve.
Common Compliance Gaps & How to Address Them
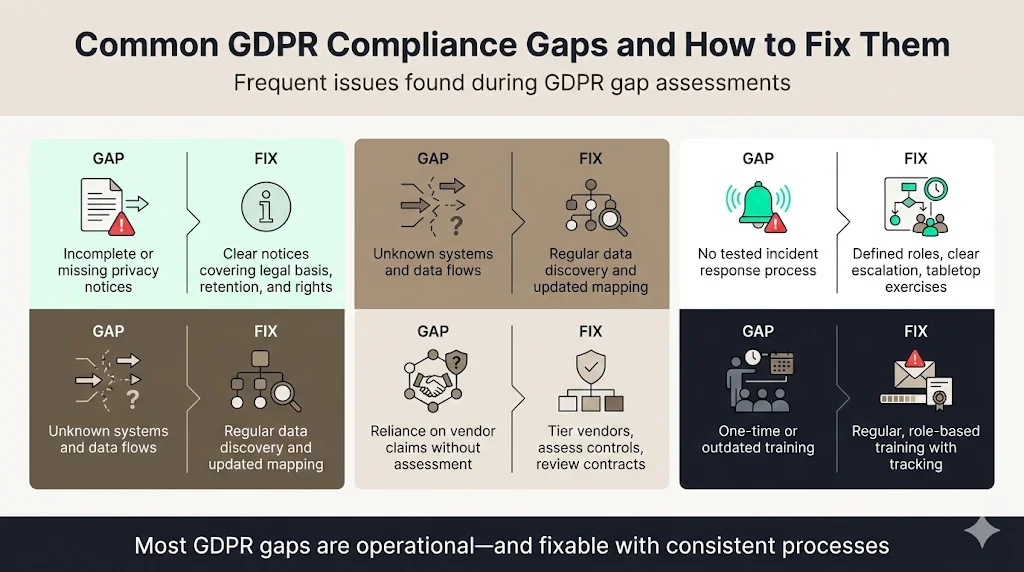
Through hundreds of privacy assessments, we see recurring deficiencies:
Missing privacy notices
Some organisations collect personal data without providing clear privacy notices, or their notices omit essential information (e.g., legal basis, data retention). This violates GDPR transparency requirements. Fix: Draft notices that cover all processing activities, use plain language, and explain rights. Publish them in prominent places (website, sign‑up forms). Review them annually or whenever processes change.
Lack of accurate data maps
Teams often underestimate how many systems store personal data. Unmapped data flows lead to unknown risks. Fix: Conduct regular data discovery scans, involve engineers and business units, and update your map whenever you add new tools. Use automated data mapping tools when possible.
Weak vendor risk assessment
Many companies rely on vendors’ marketing statements instead of formal assessments. They seldom tier vendors or review contracts. Fix: Implement a vendor risk management program that categorises vendors by criticality, collects standardized questionnaires, reviews controls, and monitors performance. Ensure contracts include GDPR clauses and data transfer safeguards.
Incomplete breach response procedures
Some organisations have no formal incident response plan or fail to test it. Breach notifications may be delayed or mishandled. Fix: Develop an incident response plan aligned with Article 33 and 34 requirements; define roles, communication procedures, and escalation paths. Run tabletop exercises to ensure readiness. Confirm your plan meets other frameworks like SOC 2 and ISO 27001.
Patchy employee training
Employees sometimes receive one‑time training at onboarding but no follow‑up. They may not know how to recognise a data subject request or report a potential breach. Fix: Provide regular training (at least annually), tailored to roles. Cover phishing, data handling, GDPR rights, and incident reporting. Track attendance and performance to ensure accountability.
Integrating Gap Assessments into Ongoing Compliance
A gap assessment should not be a one‑off exercise. To maintain compliance and support enterprise sales cycles:
- Set assessment frequency: Perform assessments at least annually. Higher‑risk organisations or those undergoing rapid change should assess quarterly or bi‑annually. Tie reviews to product launches, major system changes, or new client audits.
- Automate where possible: Use tools to automate evidence collection, control monitoring, and risk scoring. For example, continuous monitoring platforms can track access changes, encryption status, and vulnerability scans. This aligns with SOC 2’s requirement for continuous evidence over the observation period.
- Integrate with governance: Embed gap assessments into your risk management and information security management system (ISMS). Use them to inform risk registers, internal audits, and improvement plans.
- Engage leadership: Present findings and remediation progress to executives. Align actions with business objectives and budget planning.
- Communicate with buyers: Share high‑level results (without disclosing sensitive details) with enterprise clients. Demonstrate transparency and commitment to continuous improvement.
Case Study: A SaaS Provider’s Journey
Context: A B2B SaaS company based in Europe builds a collaboration platform used by enterprises in finance and healthcare. Enterprise clients required proof of GDPR compliance and SOC 2 Type II attestation before signing contracts.
Challenges:
• Minimal documentation of data flows and retention periods.
• No formal vendor risk management; sub‑processors lacked GDPR clauses.
• Privacy notices were generic and incomplete.
• Controls like access reviews and incident response were informal.
• Sales cycles stalled because procurement teams asked for evidence the company could not provide.
Actions:
- Conducted a GDPR gap assessment: The team mapped all personal data, identified high‑risk processing activities, and compared practices against GDPR requirements. They discovered 38 gaps, including missing DPIAs and inadequate data minimisation.
- Implemented controls: They encrypted all databases, enforced multi‑factor authentication for administrative access, deployed a SIEM for logging and monitoring, and updated their incident response plan.
- Updated policies and notices: New privacy notices explained purposes, legal bases, retention periods, and rights. Internal policies mandated regular access reviews and defined retention schedules.
- Established vendor management: Vendors were tiered, questionnaires were collected, and contracts were revised with SCCs and audit rights.
- Trained employees: Everyone completed privacy and security training; product teams learned how to conduct DPIAs.
- Aligned with SOC 2 and ISO 27001: The company implemented controls mapped to the SOC 2 Trust Services Criteria and ISO 27001 Annex A. They started an observation period for SOC 2 Type II.
Results:
• Within six months, the company completed its gap remediation.
• They achieved SOC 2 Type II attestation after a nine‑month observation period, satisfying enterprise buyers.
• Sales cycles shortened by 30%, and the company won a large healthcare client after demonstrating compliance.
• They reduced the number of findings in their first ISO 27001 audit from 12 to 3 by addressing privacy risks early.
• Employee awareness improved, with phishing simulation click‑through rates dropping from 18% to 3%.
This example shows how a robust GDPR Gap Assessment Guide not only meets legal obligations but drives business outcomes by building trust.
Conclusion
Enterprise buyers, regulators, and auditors demand evidence that personal data is protected. Average GDPR fines exceeded €2.36 million as of March 2025, with cumulative penalties approaching €5.88 billion. In the U.S., the average cost of a data breach reached $10.22 million in 2025. These figures underscore the stakes. A structured gap assessment identifies weaknesses before they lead to fines or lost deals. It aligns your organisation with GDPR, SOC 2, ISO 27001, HIPAA, and other frameworks. It also reinforces a culture of continuous improvement and transparency.
As practitioners, we must build programs that operate daily, not just at audit time. Compliance manufacturing—rushing to produce documents before a buyer’s questionnaire—fails when real incidents occur. By embracing a human‑led, managed service approach, we design controls inside your stack, monitor them continuously, and provide outcome‑driven compliance. The GDPR Gap Assessment Guide outlined here equips you to start with security and arrive at compliance. Prioritise gap assessments, close high‑risk gaps, and let robust security become your competitive advantage.
FAQ
1) What is a GDPR gap assessment?
It is a systematic review of your current data protection practices against GDPR rules. You document data flows, compare them to legal requirements, identify gaps, and prioritise remediation. The goal is to ensure compliance and reduce privacy risk.
2) Who should perform a GDPR gap assessment?
A cross‑functional team that includes legal, IT/security, privacy, data owners, and business leaders. For higher‑risk companies or limited expertise, external consultants or managed service providers can help.
3) How often should a GDPR gap assessment be done?
At least annually. However, assessments should also occur when you introduce new data processing activities, onboard major vendors, update systems, or prepare for significant audits. SOC 2 audits are annual and require continuous evidence, so aligning your assessment schedule with audit cycles is beneficial.
4) What documents are needed for a GDPR gap assessment?
Key items include privacy policies, Records of Processing Activities (ROPA), contracts with third parties, security controls documentation, incident response plans, and training records. You may also need data processing agreements, Standard Contractual Clauses, and vendor risk assessments.





.svg)






.svg)
.svg)