Most enterprise buyers want more than a checkbox when personal health data is involved. They ask for assurance artifacts long before they sign contracts. Teams that handle patients’ electronic protected health information (ePHI) can recite the clauses of the Health Insurance Portability and Accountability Act (HIPAA), yet their deals stall when they can’t produce proof of daily security operations. Regulators are also tightening expectations: HHS is proposing to make all implementation specifications of the HIPAA Security Rule required and to mandate detailed technology asset inventories, network maps and vulnerability scanning at least every six months. That context makes the work of mapping HIPAA controls to an actionable control set such as the Center for Internet Security (CIS) Controls more than a theoretical exercise—it’s the difference between passing an audit and losing trust. This article explains how HIPAA Controls Mapped To CIS helps healthcare teams demonstrate real security without inventing a GRC program from scratch.
What this guide delivers
- Plain‑English mapping methodology. Rather than legal citations, you get a clear way to connect HIPAA’s administrative, physical and technical safeguards to CIS Controls v8.1.
- Grouped guidance by safeguard type. Each section ties HIPAA expectations to specific CIS Controls and Safeguards, making it easy to assign owners and evidence.
- Templates you can adapt quickly. We include policy and procedure starter packs linked to HIPAA clauses and CIS Safeguards so you don’t start with a blank page.
- Quick definitions. To keep the text light, key terms are defined in one or two lines.
- Use‑case focused. This guide speaks to providers, payers, health‑tech platforms, labs, billing firms and any business associate that touches ePHI.
- Outcome orientation. The goal is to help you produce a controls matrix, policy set and evidence portfolio that withstands buyer scrutiny and auditor questions.
Quick definitions
Why teams need more than HIPAA text
HIPAA tells you what must be protected, not how to protect it. The law instructs regulated entities to ensure the confidentiality, integrity and availability of ePHI but allows flexibility in how to achieve those outcomes. Flexibility without guidance can lead to inconsistency and, worse, exposures. The U.S. Department of Health and Human Services noted that healthcare organizations often leave PHI vulnerable because they don’t align their security programs with detailed frameworks. That gap has real consequences. In 2024 the average cost of a healthcare data breach hit $9.8 million per incident, and a single ransomware attack on Change Healthcare disrupted pharmacy services and cost the parent company $872 million in one quarter. The trend isn’t abating; from 2009 to 2024, 6 ,759 breaches exposed or impermissibly disclosed 846 ,962 ,011 individuals’ PHI. Regulators are responding with more stringent requirements. The 2024 NPRM proposes mandatory asset inventories, network mapping, vulnerability scanning and encryption—controls that map directly to CIS Safeguards.
Beyond regulators, enterprise buyers insist on proof. Healthcare companies selling to payers or large providers face long procurement questionnaires and security reviews. Deals frequently stall when a vendor cannot show evidence of access reviews, patching, incident response drills or vendor due diligence. Internal security teams may have policies but no system to tie HIPAA clauses to daily operations. That’s where mapping HIPAA Controls to CIS provides a consistent, testable control set that can be turned into a living program.
Konfirmity sees this problem repeatedly. With more than 6 ,000 audits supported and 25+ years of combined technical expertise, we’ve watched teams attempt two‑week “compliance manufacturing” projects. The result is often a pile of documents and no durable security. Our managed service works differently. We implement controls inside your stack, monitor them year‑round and provide evidence across frameworks—SOC 2, ISO 27001, HIPAA, GDPR—so that compliance is a natural outcome. Customers typically reach SOC 2 readiness in 4–5 months with our help instead of 9–12 months self‑managed, and they spend around 75 internal hours per year versus the 550–600 hours we see in self‑serve tools. These numbers come from our delivery work across thousands of projects. That experience informs the mapping and templates included here.
HIPAA Security Rule refresher: focus on controls
HIPAA’s Security Rule identifies three safeguard families. Understanding them is essential before mapping to CIS Controls. This section summarizes the requirements without turning into a legal essay.
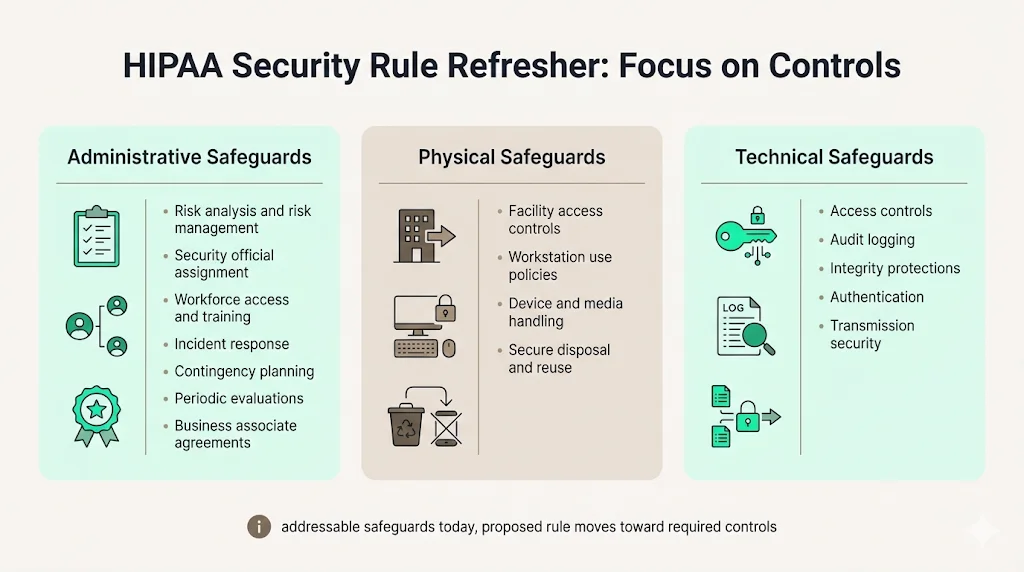
Administrative safeguards
Administrative safeguards require a risk-based program. A regulated entity must perform a thorough risk analysis and manage risks to ePHI. It must designate a security official and ensure workforce security through appropriate authorization, supervision and sanctions. Information access management policies must enforce the “minimum necessary” principle. Training is mandatory—staff must be trained on security policies and procedures. The organization also needs incident procedures for identifying and responding to security incidents and mitigation, contingency plans for emergencies, periodic evaluations and business associate agreements requiring contractors to safeguard ePHI.
Physical safeguards
Physical safeguards control how facilities and devices are accessed. They require facility access controls to limit physical access to information systems and ePHI. Workstation use policies and physical protections are needed. Device and media controls must govern the receipt, removal and disposal of hardware that contains ePHI and ensure secure re‑use.
Technical safeguards
Technical safeguards address system‑level protections. They require access control policies and procedures to allow only authorized persons to access ePHI. Audit controls must log and examine activity in systems containing ePHI. Integrity controls must prevent improper alteration or destruction. Authentication procedures must verify user identities. Transmission security must protect ePHI when transmitted across networks. The current rule categorizes certain implementation specifications as “addressable,” allowing alternatives if documented. The NPRM would eliminate the addressable distinction and make all specifications required.
CIS Controls v8.1 refresher: a common language for security
The CIS Controls provide a prioritized control set that aligns with many frameworks. Version 8.1, released in June 2024, refines the controls and adds a sixth security function—Governance—joining Identify, Protect, Detect, Respond and Recover. It introduces six asset classes (Devices, Software, Data, User, Network and Documentation) and updates Safeguard descriptions. The update aligns with NIST Cybersecurity Framework 2.0 and provides new glossary terms for clarity. There are 18 controls and 153 Safeguards in v8.1, organized into three Implementation Groups (IG1, IG2, IG3) to help organizations tailor scope based on risk and resources. IG1 is a reasonable baseline for small and midsize organizations, IG2 adds depth for moderate maturity, and IG3 covers advanced capabilities. This tiered approach allows healthcare organizations to choose a starting point and expand over time.
CIS guidance emphasizes that the controls are regularly updated and mapped to other frameworks, including PCI DSS, NIST, ISO 27001, HIPAA and GDPR. Healthcare teams value the CIS Controls because they provide a single prioritized list to implement and measure, a common language for internal teams and external assessors, and cross‑framework reusability.
How to map HIPAA → CIS Controls without creating busywork
Mapping HIPAA requirements to CIS Controls is about translating broad legal standards into actionable security tasks. The principles below will help you build a useful mapping.
Start with clean mapping principles
- One-to-many relationships. A single HIPAA requirement can map to multiple CIS Safeguards. For example, HIPAA’s risk analysis requirement maps to CIS Control 2 (Inventory of Software and Assets) and Control 14 (Security Awareness and Skills Training).
- Context matters. Not every CIS Safeguard is required for every organization. Implementation Groups help you choose what is reasonable.
- Use mappings as a baseline, not a checklist. Validate the mapping against your environment and data flows. Add or remove Safeguards based on how ePHI moves through your systems.
- Iterate. Mapping isn’t a one‑time exercise. As systems change, update the matrix.
Use official crosswalks as a starting point
HHS and NIST released a crosswalk that maps the HIPAA Security Rule to the NIST Cybersecurity Framework. CIS provides a similar mapping for its Controls (v8.1) to HIPAA, although the official document requires registration. The idea is the same: you start by listing the HIPAA clauses relevant to your systems, then pull the mapped CIS Controls and Safeguards. For each Safeguard, assign an owner, document implementation status, collect evidence and define test steps. This mapping becomes the index for your audit.
Use the CIS Controls Navigator for quick lookups
CIS offers a free Controls Navigator that allows you to select a version (v8.1), choose your Implementation Group and filter by mappings (e.g., HIPAA). During workshops, scoping sessions or buyer conversations, the Navigator helps answer “Which Safeguard covers this requirement?” Export the list of Safeguards for your Implementation Group and add columns such as HIPAA citation, system, owner, evidence link and review cadence. This turns the mapping into a living document.
Key HIPAA control areas mapped to CIS Controls
The sections below highlight critical control areas, summarizing what HIPAA expects, how CIS helps you implement them and the evidence you should collect. HIPAA Controls Mapped To CIS is woven throughout these examples. The bullet lists show typical evidence; adjust them based on your environment.
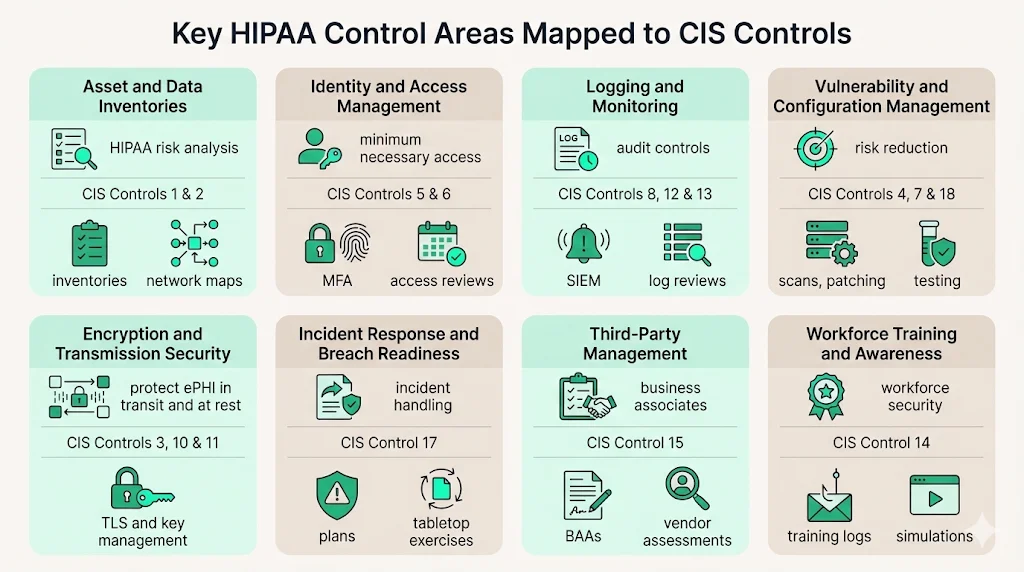
1. Asset and data inventories (know what touches ePHI)
What HIPAA expects: Risk analysis requires an accurate inventory of systems and data that create, receive, maintain or transmit ePHI. The 2024 NPRM would mandate a technology asset inventory and network map updated at least every 12 months.
CIS Controls: Control 1 (Inventory and Control of Enterprise Assets) and Control 2 (Inventory and Control of Software Assets) require maintaining a detailed inventory of devices and software authorized to access the network. Safeguards include automatic inventory tools, authorized software lists and physical asset tracking.
Evidence examples:
- System inventory exports or configuration management database (CMDB) entries.
- Data flow diagrams showing how ePHI moves through applications, databases and third‑party services.
- Network maps highlighting segments containing ePHI.
2. Identity and access management (least privilege and strong authentication)
What HIPAA expects: Access control is a core technical safeguard; it requires unique user identification, emergency access procedures and session time‑outs. Information access management demands minimum necessary access. The NPRM proposes mandatory multi‑factor authentication and 24‑hour notification when a workforce member’s access changes.
CIS Controls: Control 5 (Account Management) and Control 6 (Access Control Management) cover provisioning, reviewing and deprovisioning accounts; enforcing multi‑factor authentication; and restricting administrative privileges. Control 16 (Application Software Security) requires separation of duties within applications.
Evidence examples:
- Identity and access management policies defining joiner/mover/leaver processes and privileged access controls.
- Screenshots or exports from identity providers showing MFA enforcement.
- Break‑glass procedure records for emergency access.
- Access review tickets or spreadsheets documenting periodic reviews.
3. Logging, audit trails and monitoring
What HIPAA expects: Audit controls must record system activity, and regulated entities must periodically evaluate the effectiveness of security measures. Incident procedures require documented detection and response.
CIS Controls: Control 8 (Audit Log Management) focuses on centralized logging, log retention and regular review. Control 12 (Network Monitoring and Defense) and Control 13 (Security Operations) address alerting, intrusion detection and continuous monitoring.
Evidence examples:
- SIEM configuration showing retention settings and data sources.
- Log review schedules, meeting notes and sample audit logs.
- Alert tuning records demonstrating how detection rules are updated.
4. Vulnerability management and secure configuration
What HIPAA expects: The risk management process requires reducing risks to a reasonable and appropriate level. The NPRM proposes vulnerability scanning at least every six months, penetration testing at least once every 12 months and baseline configurations with anti‑malware protection.
CIS Controls: Control 7 (Continuous Vulnerability Management) covers scanning, prioritizing and remediating vulnerabilities. Control 4 (Secure Configuration of Enterprise Assets and Software) requires secure baselines, removal of unnecessary services and configuration management. Control 18 (Penetration Testing) guides periodic testing.
Evidence examples:
- Vulnerability scan reports with remediation tickets and evidence of patch deployment.
- Configuration baseline documents for servers, containers and workstations.
- Penetration test reports and follow‑up tracking logs.
5. Encryption and transmission security
What HIPAA expects: Transmission security must protect ePHI in transit, and although not explicitly required in the current rule, encryption at rest is considered a best practice. The NPRM would require encryption at rest and in transit.
CIS Controls: Control 3 (Data Protection) covers encryption standards, data classification and key management. Control 10 (Data Recovery) ensures backups and secure restoration. Control 11 (Secure Configuration for Network Devices) addresses TLS settings.
Evidence examples:
- TLS configuration settings and SSL/TLS test reports.
- Disk or database encryption settings and key management service policies.
- Key rotation logs from cloud providers.
6. Incident response and breach readiness
What HIPAA expects: Entities must identify and respond to security incidents, mitigate harm and document outcomes. The NPRM would require written incident response plans with restoration procedures and annual testing.
CIS Controls: Control 17 (Incident Response Management) covers incident response plans, defined roles, detection and escalation paths, and post‑incident activities. Control 9 (Email and Web Browser Protections) includes phishing controls that tie into incident prevention.
Evidence examples:
- Incident response plan with defined roles and contact information.
- Tabletop exercise reports and corrective actions.
- Incident tickets documenting detection, containment, eradication and lessons learned.
7. Third‑party and service provider management
What HIPAA expects: Business associate agreements must ensure vendors safeguard ePHI, and the NPRM would require annual verification that business associates have deployed required technical safeguards.
CIS Controls: Control 15 (Service Provider Management) requires maintaining an inventory of service providers, assessing their security posture, including security clauses in contracts and monitoring their controls. CIS Safeguards align with HIPAA’s requirement to manage vendor risk and ensure subcontractors sign appropriate agreements.
Evidence examples:
- Vendor inventory with risk tiering and assessment dates.
- Copies of business associate agreements and security addenda.
- Third‑party audit reports (e.g., SOC 2 or ISO 27001) and security questionnaires.
- Records of periodic vendor reassessments and offboarding.
8. Workforce training and security awareness
What HIPAA expects: Covered entities must train their workforce on security policies and apply sanctions for violations. The NPRM does not change this requirement but proposes to clarify documentation obligations.
CIS Controls: Control 14 (Security Awareness and Skills Training) addresses baseline training, role‑based modules, and phishing simulation. Control 1 and Control 2 emphasize ensuring that users understand their obligations when handling devices and software.
Evidence examples:
- Training completion logs by role.
- Phishing simulation reports and follow‑up training.
- Role‑based training matrix showing which modules apply to which job functions.
Template pack: policies and procedures you can adapt
A key benefit of HIPAA Controls Mapped To CIS is reducing documentation lift. You don’t need to write policies from scratch. JupiterOne’s open security policy templates repository includes policy and procedure templates mapped to frameworks such as HIPAA and CIS. It also provides a JSON controls mapping concept linking procedures to frameworks. Below is a starter pack you can replicate and adapt. Each template includes a purpose, minimum sections and an evidence checklist.
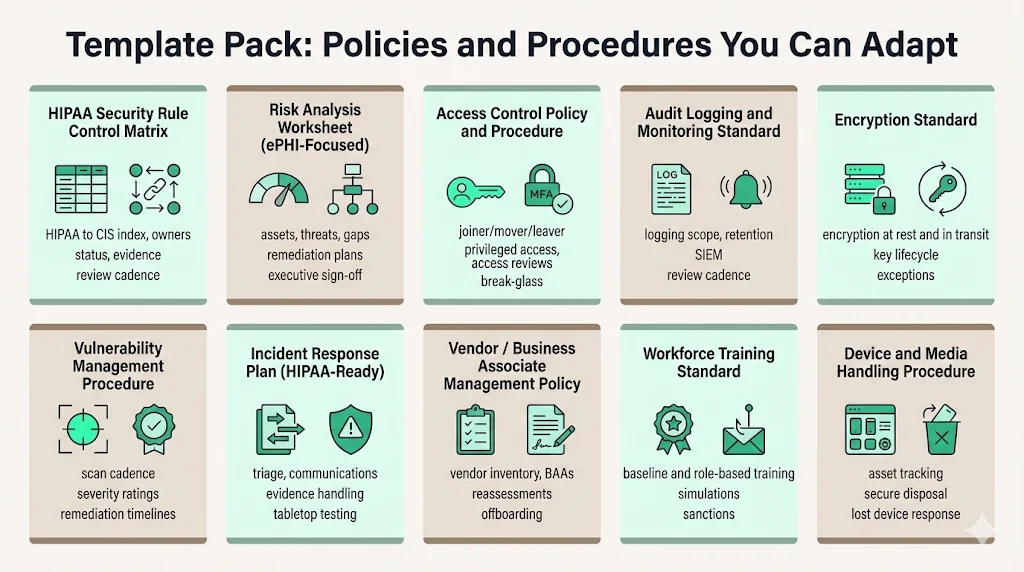
HIPAA Security Rule control matrix
Purpose: Provide a single index linking HIPAA clauses to CIS Controls and Safeguards, with status and evidence.
Minimum sections: HIPAA citation, safeguard type (administrative/physical/technical), CIS Control, CIS Safeguard, system scope, owner, implementation status, evidence link, test method, review frequency.
Evidence checklist: Completed matrix with statuses updated quarterly; review logs showing cross‑functional review; sample evidence attachments.
Risk analysis worksheet (ePHI‑focused)
Purpose: Document assets, threats, vulnerabilities, likelihood, impact, current controls, gaps, remediation plans and target dates.
Minimum sections: Asset/system, threats, vulnerabilities, likelihood/impact, risk rating, existing controls, gaps, remediation actions, responsible owner, target date.
Evidence checklist: Completed worksheets for each system handling ePHI; approval by security officer; periodic updates; sign‑off from executive leadership.
Access control policy and procedure
Purpose: Define joiner/mover/leaver processes, privileged access management, multi‑factor authentication and access reviews.
Minimum sections: Purpose, scope, definitions, policy statements (unique IDs, MFA requirements, privileged access controls, emergency access), procedures (provisioning, deprovisioning, break‑glass, periodic reviews), sanctions.
Evidence checklist: Signed policy; access request and approval tickets; MFA enforcement evidence; access review logs; break‑glass test results.
Audit logging and monitoring standard
Purpose: Define what to log, retention periods, alert rules, review cadence and exceptions.
Minimum sections: Logging scope (systems, events), log retention, SIEM configuration, alert tuning process, regular review cadence, exceptions process.
Evidence checklist: SIEM configuration exports; retention policy; log review meeting notes; alert tuning records; exceptions approvals.
Encryption standard
Purpose: Specify encryption requirements for ePHI at rest and in transit, key management and approved algorithms.
Minimum sections: Encryption scope (databases, backups, storage devices, network connections), acceptable algorithms and key sizes, key lifecycle management, key rotation and escrow, exception handling.
Evidence checklist: Encryption settings on storage and databases; TLS cipher suites configuration; key management system policies; key rotation logs; exception approvals.
Vulnerability management procedure
Purpose: Establish scanning cadence, severity ratings, patch timelines and verification steps.
Minimum sections: Roles and responsibilities, scanning frequency, vulnerability classification (e.g., CVSS), remediation timelines by severity, patch verification, risk acceptance process.
Evidence checklist: Scan schedules; vulnerability and patch reports; remediation tickets; risk acceptance documentation; verification evidence.
Incident response plan (HIPAA‑ready)
Purpose: Outline roles, triage, containment, communications, evidence handling and post‑incident review.
Minimum sections: Plan purpose, scope, definitions; roles and responsibilities; incident categories; incident handling procedures; communication plan; evidence collection and chain of custody; post‑incident analysis; training and testing.
Evidence checklist: Approved plan; incident logs; communication templates; tabletop exercise reports; lessons learned; plan revisions.
Vendor/business associate management policy
Purpose: Manage vendor risk tied to ePHI through inventory, risk tiering, contract clauses, business associate agreements and reassessments.
Minimum sections: Vendor inventory, risk classification criteria, due diligence process, contract clause requirements (security obligations, right to audit, incident notification), onboarding and offboarding procedures, periodic reassessment.
Evidence checklist: Updated vendor inventory; completed vendor assessments and security questionnaires; signed BAAs; periodic reassessment records; offboarding documentation.
Workforce training standard
Purpose: Ensure all workforce members, including management, receive baseline and role‑specific training.
Minimum sections: Training roles and responsibilities; baseline training frequency; role‑based training modules; training delivery methods; phishing simulations; sanctions for non‑completion; annual refresh requirements.
Evidence checklist: Training completion logs; role‑based curriculum; phishing simulation results; re‑training records for failures.
Device and media handling procedure
Purpose: Govern inventory, disposal, reuse and lost device response.
Minimum sections: Device inventory procedures; assignment of device custodians; media disposal and sanitization methods; reuse policy; lost/stolen device response.
Evidence checklist: Device inventory list; destruction certificates; sanitization logs; lost device incident reports; hardware assignment records.
Adapting templates quickly
- Define scope boundaries first. Identify systems that create, receive, maintain or transmit ePHI. This scoping influences which CIS Controls apply.
- Select an Implementation Group. For most small and midsize healthcare companies, IG1 provides a solid baseline, while IG2 adds depth. Use IG3 only for high‑risk environments or large enterprises.
- Fill in owners and evidence locations during implementation. Treat the matrix and templates as living documents; update them while implementing controls rather than retroactively.
- Leverage automation where sensible. Use configuration management, identity providers and logging platforms to collect evidence continuously.
- Engage stakeholders early. Map owners to control areas; involve IT, compliance, HR, legal and vendor management so that evidence collection becomes collaborative.
- Schedule periodic reviews. Set a cadence for reviewing the matrix and templates (e.g., quarterly) to ensure they reflect current systems and controls.
Using CIS Controls during audits: a playbook
Pre‑audit preparation (2–4 weeks before)
- Freeze your controls matrix. Finalize which HIPAA clauses and CIS Safeguards are in scope. Document implementation status and evidence links.
- Verify evidence links. Ensure that all artifacts (logs, screenshots, policies, tickets) are accessible and not behind personal accounts.
- Conduct a tabletop “audit interview.” Run through typical auditor questions with system owners. Confirm they can speak to control implementation and produce evidence.
During the audit
- Use the matrix as your single index. For each HIPAA topic, present the relevant CIS Control, show the policy, demonstrate the procedure and produce evidence. This keeps conversations factual and repeatable.
- Focus on outcomes, not checkboxes. Auditors care about whether controls are operating effectively over time, not just that policies exist. Provide evidence of cadence—access reviews performed every quarter, logs reviewed weekly, vendors reassessed annually.
- Stay responsive. Assign a point person to coordinate document requests and schedule follow‑up conversations.
After the audit
- Turn findings into remediation plans. For each gap, identify root cause, assign an owner and commit to a target date.
- Track repeat findings as program issues. If auditors note the same gap across frameworks (e.g., access review delays), treat it as a program‑level issue rather than a one‑off fix.
- Reflect and improve. Conduct a post‑mortem with stakeholders, update the controls matrix and templates, and plan improvements for the next cycle.
Buyer expectations: are CIS Controls accepted by healthcare buyers?
Healthcare buyers assume HIPAA compliance as a minimum. They want assurance that vendors run a security program aligned with recognized standards. CIS Controls often provide the common language buyers and security teams need. When presenting to a buyer:
- Show a CIS‑based control matrix tied to HIPAA. Highlight which Safeguards cover which HIPAA clauses.
- Demonstrate cadence. Provide evidence of regular access reviews, patching, log reviews and vendor checks.
- Discuss continuous monitoring. Buyers appreciate a managed service that goes beyond an annual audit.
Konfirmity’s experience shows that when vendors present a clear controls matrix and evidence of continuous operations, procurement cycles shorten significantly. Without it, deals can stall for months.
Conclusion: build durable security and let compliance follow
Security that looks good on paper but fails during an incident is a liability. HIPAA provides the legal obligations, but without a clear control set and evidence, it doesn’t satisfy buyers or protect patients. Starting with HIPAA Controls Mapped To CIS offers a practical path: map each HIPAA requirement to a CIS Safeguard, assign ownership, implement policies and procedures, and collect evidence along the way. Use tools like the CIS Controls Navigator to speed up mapping discussions and keep stakeholders aligned. Leverage policy and procedure templates to establish documentation quickly, then integrate evidence collection into daily operations so that audits become routine rather than chaotic. By focusing on real security practices—asset inventories, least‑privilege access, logging, vulnerability management, encryption, incident response, vendor oversight and workforce training—you create a program that withstands auditor scrutiny and wins buyer trust.
Frequently asked questions
1) Do CIS Controls replace HIPAA requirements?
No. CIS Controls are a security control set, whereas HIPAA is a legal and regulatory requirement. Use CIS Controls to implement and demonstrate security measures that fulfil HIPAA obligations. You still must comply with all HIPAA standards and document how each requirement is met.
2) Which CIS Controls apply to HIPAA compliance?
It depends on your scope and Implementation Group. Common areas include asset inventories, access control, audit logging, vulnerability management, encryption, incident response, vendor management and training. Use official mappings and the CIS Controls Navigator to select Safeguards aligned with the ePHI flows in your environment.
3) How do enterprises use CIS Controls during audits?
They create a mapping matrix linking HIPAA clauses to CIS Controls and Safeguards, then show policies, procedures and evidence for each. This approach turns the audit into a structured conversation rather than a scavenger hunt.
4) Are CIS Controls accepted by healthcare buyers?
Many buyers see CIS as a practical control set that clarifies how a company runs security day to day. When vendors can show traceability from HIPAA text to CIS Safeguards and produce real evidence, buyers are more confident. CIS also offers a Navigator tool to view mappings across standards, which helps during due‑diligence conversations.





.svg)






.svg)
.svg)