In enterprise health care, buyers demand proof of security before they sign. Business associate agreements, data protection addenda and security questionnaires are standard in deals involving electronic protected health information (ePHI). A phone call or slide deck isn’t enough – regulated entities must show that their security controls work in practice. The Health Insurance Portability and Accountability Act (HIPAA) and ISO 27002 offer complementary frameworks, yet many covered entities treat them as separate check‑boxes. Aligning HIPAA controls with ISO 27002 brings order to the chaos and helps providers deliver continuous evidence. This article explains why HIPAA Controls Mapped To ISO 27002 matter, how to build a mapping matrix, and how to avoid the pitfalls we see while running more than 6,000 audits over 25 years. We’ll share practical steps, real‑world examples and numbers from our work so that CTOs, CISOs and compliance leaders can design secure operations instead of producing paper promises.
What Is HIPAA?
HIPAA governs the confidentiality, integrity and availability of health information in the United States. It protects medical records and personal health information held by covered entities and their business associates. Three core rules shape the legal landscape:
- Privacy Rule – establishes standards for permissible uses and disclosures of individually identifiable health information.
- Security Rule – requires regulated entities to implement administrative, physical and technical safeguards for ePHI, ensuring that only authorized personnel access, modify or transmit protected information. The rule emphasises risk analysis and risk management.
- Breach Notification Rule – mandates notification to individuals, the HHS secretary and sometimes media outlets when unsecured PHI is compromised.
The Security Rule is flexible and technology‑neutral. It acknowledges that risk varies across organizations and allows entities to choose measures that reduce risks to reasonable and appropriate levels. In practice, the Security Rule’s safeguards underpin any HIPAA program. They provide a baseline for encryption, authentication, audit logging, access management and incident response. Understanding these safeguards is the first step toward aligning with ISO 27002.
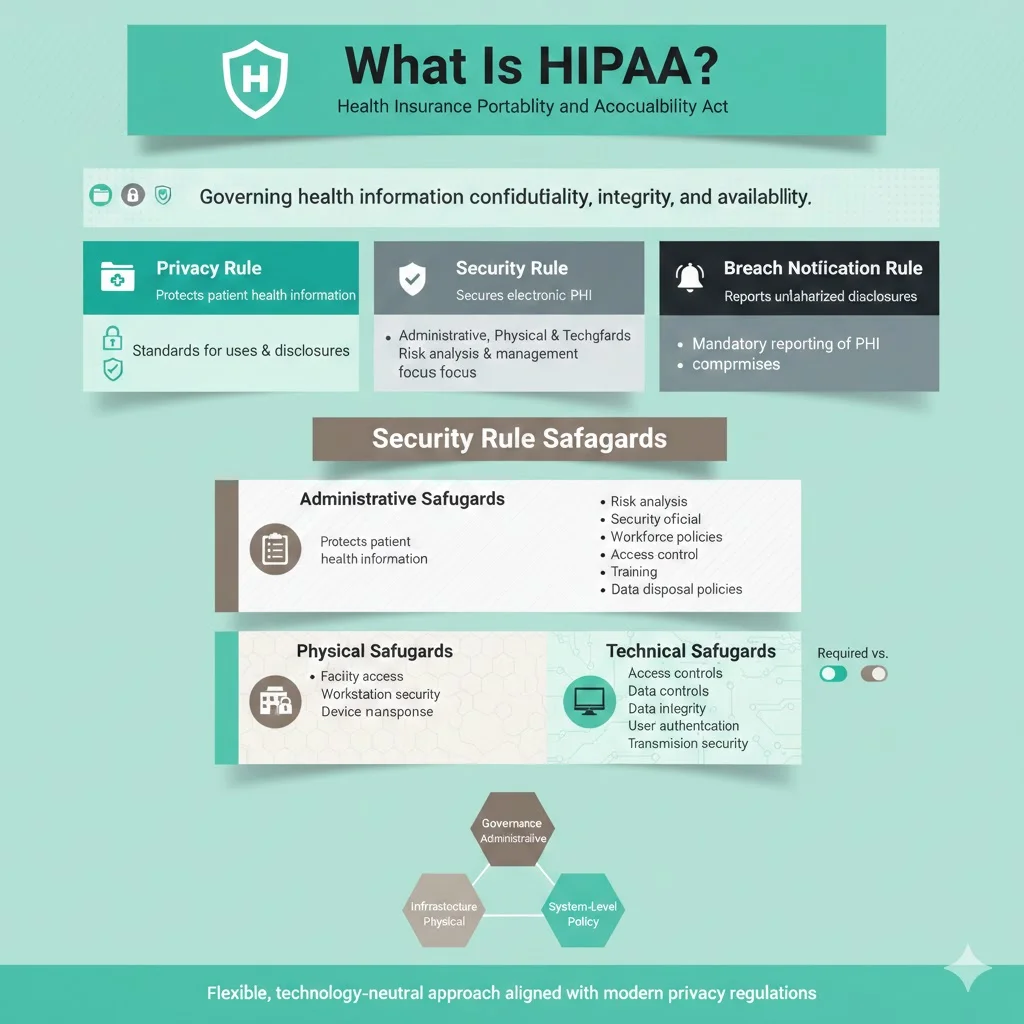
HIPAA Security Rule Safeguards
The Security Rule organizes protections into three safeguard categories:
- Administrative safeguards – These require a thorough risk analysis and a risk management process to ensure appropriate security measures. Organizations must designate a security official, implement workforce security policies, control information access and train all employees on security procedures. Incident response procedures and contingency planning are also mandatory.
- Physical safeguards – Covered entities must control facility access, secure workstations and manage devices and media containing ePHI. Policies must specify how to dispose of or re‑use hardware storing protected data.
- Technical safeguards – Organizations must enforce access controls, implement audit controls, ensure data integrity and authenticate users. Transmission security measures guard against unauthorized interception. The rule differentiates between required and addressable implementation specifications; addressable specifications allow organizations to adopt alternative measures when specific technologies are unreasonable.
These safeguards work together. Administrative safeguards build governance; physical safeguards protect the infrastructure; technical safeguards enforce policy at the system level. They align naturally with modern privacy regulations and form the baseline for mapping to ISO 27002.
What Is ISO 27002?
ISO 27002 is a set of guidelines for information security controls. It supports ISO 27001 certification by providing detailed control descriptions and implementation guidance. The 2022 revision reduced the number of controls from 114 to 93 and reorganized them into four themes. This consolidation reflects shifts in technology and emphasises measurable risk reduction.
How It Works (2022 Control Structure)
The four themes are:
- Organizational controls – covering governance, asset management, policy, supplier relationships, and legal compliance.
- People controls – addressing screening, training, and disciplinary measures.
- Physical controls – ensuring secure facilities and equipment.
- Technological controls – covering access management, cryptography, operations security, and system acquisition.
These themes include 11 new controls (e.g., threat intelligence, cloud security, data masking, secure coding) and consolidate dozens of prior controls. Over 75 % of the updated controls fall under organizational and technological categories. This risk‑based structure makes it easier to view security holistically and align with other standards such as NIST, CIS controls and the Cybersecurity Framework.
Why ISO 27002 Matters for Healthcare
Healthcare organizations operate in a global environment. Many handle cross‑border data, rely on cloud services, and face diverse regulations. ISO 27002 offers a common language for security controls and supports certification under ISO 27001. For covered entities, adopting ISO 27002:
- Provides a globally recognized framework that goes beyond U.S. law.
- Helps structure risk assessments and continuous monitoring programs.
- Aligns with other frameworks (NIST CSF, SOC 2, GDPR) and simplifies vendor due diligence.
- Improves resilience – the 11 new controls address modern threats like cloud misconfiguration and secure coding.
As we’ll demonstrate, mapping HIPAA controls to ISO 27002 can eliminate duplication and enable a unified information security management system (ISMS).
Why Healthcare Stakes Are High
Healthcare breaches are uniquely costly and protracted. IBM’s 2024 Cost of a Data Breach Report found that the average healthcare breach costs $7.42 million — roughly 40 % higher than the global average — and takes 279 days to identify and contain. Fines, litigation, notification expenses and operational disruption compound the impact. Breaches trigger Office for Civil Rights investigations, potential corrective action plans and damage to trust. Even small providers face penalties when they fail to conduct risk analyses or implement basic safeguards. Our delivery team has supported clients through breach responses; those with mapped controls recover faster because their evidence and contingency plans are ready. At Konfirmity, we’ve guided more than 6,000 audits over 25 years. We see that self‑managed programs often take 9–12 months to achieve SOC 2 or ISO 27001 readiness, requiring 550–600 hours of internal effort. Our human‑led managed service reduces this to 4–5 months and around 75 hours per year, while keeping clients audit‑ready year‑round. These numbers highlight why a proactive program matters: robust controls reduce the chance of an incident and limit downtime and legal exposure when incidents occur.
Mapping HIPAA Controls to ISO 27002
Control mapping involves cross referencing requirements from one standard (HIPAA) to relevant controls in another (ISO 27002). The goal is not to replace HIPAA but to find common controls that satisfy multiple obligations. A 2025 analysis from Pivot Point Security estimates that 65 of the 134 ISO 27002 controls map to the HIPAA Security Rule’s safeguards, with the only unaddressed HIPAA standard being business associate agreements. By centralizing compliance efforts, organizations reduce complexity, avoid re‑inventing controls and focus resources on meaningful risk reduction.
Mapping has several benefits:
- Efficiency – Implement one control that satisfies multiple frameworks, reducing documentation overhead.
- Consistency – Align policies and procedures across business units, suppliers and partners.
- Audit readiness – Evidence collected for ISO 27001 or SOC 2 can support HIPAA audits and vice versa.
At Konfirmity we see mapping as a practical necessity. When we combine SOC 2, ISO 27001 and HIPAA requirements for our clients, we typically reduce control duplication by 30–40 % and shorten readiness times by months.
Common HIPAA‑to‑ISO 27002 Alignments
- Administrative safeguards to organizational controls – HIPAA’s risk analysis, risk management and workforce training map to ISO 27002’s controls for governance, risk management and personnel onboarding. For example, ISO 27002 requires organizations to define roles and responsibilities and ensure personnel understand security obligations, aligning with HIPAA’s assigned security responsibility and workforce training mandates.
- Physical safeguards to physical controls – HIPAA’s facility access controls and device management align with ISO 27002’s physical security measures that restrict physical access, secure offices and protect equipment.
- Technical safeguards to technological controls – Access control, audit logging, data integrity and transmission security requirements in HIPAA correspond to ISO 27002 controls on identity and access management, logging and monitoring, cryptography and secure communications.
- Incident response and contingency planning – HIPAA requires incident response procedures and contingency plans. ISO 27002 includes controls for information security incident management, business continuity and disaster recovery – these can be mapped directly.
- Risk management – NIST SP 800‑66r2 clarifies that HIPAA’s risk analysis is an “accurate and thorough assessment of the threats and vulnerabilities to ePHI” and that risk management requires implementing security measures to reduce risks to a reasonable level. ISO 27002’s risk management controls support a similar process, enabling organizations to leverage a single risk register for both frameworks.
Mapping Matrix Essentials
To map HIPAA Controls Mapped To ISO 27002 effectively, build a cross‑reference table. Each row lists a HIPAA safeguard, its citation (e.g., §164.308(a)(1)(ii)(A)), the corresponding ISO 27002 control category and notes on overlap. A simple example looks like this:
Keep descriptions short in the table and use narrative text for detailed explanations. Include column notes to highlight where HIPAA goes beyond ISO 27002, such as requiring specific documentation for business associate agreements.
Step‑by‑Step Approach to Mapping
To map HIPAA Controls Mapped To ISO 27002 efficiently, follow a concise method that scales from small practices to enterprise providers:
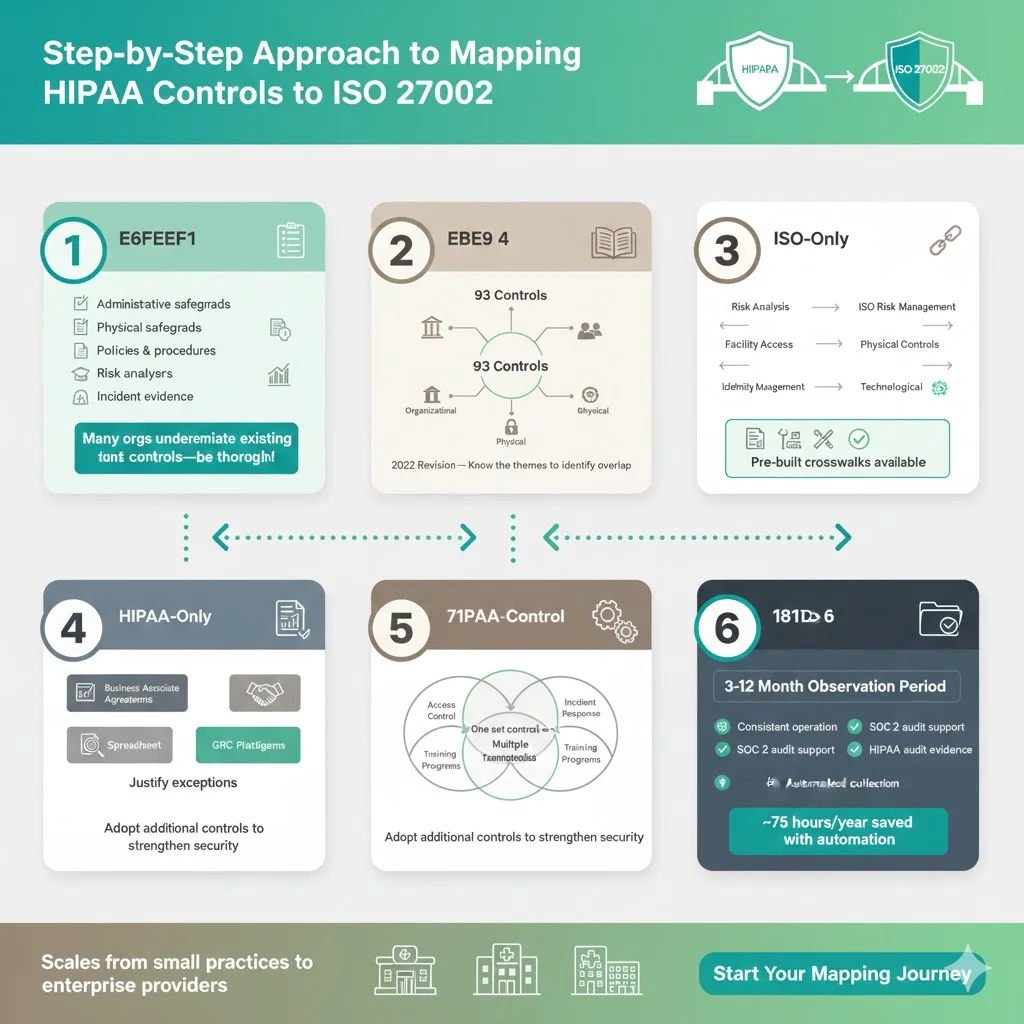
- Inventory your safeguards. Catalog every administrative, physical and technical safeguard, including policies, risk analyses, training records and incident evidence. Many organizations underestimate how many controls they already have, so a thorough inventory is essential.
- Understand ISO 27002. Review the 93 controls and identify which apply to your context. The 2022 revision groups them into organizational, people, physical and technological themes. Knowing this helps you identify overlap when HIPAA Controls Mapped To ISO 27002 are compared.
- Create a cross‑reference. Use a spreadsheet or GRC platform to match each HIPAA safeguard to one or more ISO controls. Map risk analysis to ISO risk management, facility access to physical controls, and identity management to technological controls. Many tools include pre‑built HIPAA Controls Mapped To ISO 27002 crosswalks that highlight overlaps and reduce guesswork.
- Assess gaps and overlaps. Identify where HIPAA requires safeguards that ISO 27002 lacks – such as business associate agreements – and where ISO introduces additional controls like threat intelligence. Consider adopting those controls to strengthen security and document any justifications for not doing so.
- Update policies. Integrate both frameworks into your policies and procedures. Align access control, incident response and training programs so that one set of controls satisfies multiple frameworks.
- Document evidence. Collect and retain evidence showing that mapped controls operate consistently. SOC 2 audits often test controls over a 3–12 month observation period; the same evidence can support HIPAA audits. Automated evidence collection can reduce manual effort to roughly 75 hours per year in our managed programs.
Real‑Life Examples
A telehealth start-up aligned HIPAA Controls Mapped To ISO 27002 by implementing unique user identifiers, least‑privilege roles and automated log analysis. The unified controls satisfied HIPAA and ISO requirements and shortened the SOC 2 observation window. In another case, a hospital network mapped contingency planning and business continuity controls by combining HIPAA’s backup and disaster recovery requirements with ISO’s ICT readiness provisions. During the 2024 Change Healthcare incident the network remained operational, illustrating how mapped controls protect revenue and patient safety.
Challenges and Best Practices
Mapping HIPAA Controls Mapped To ISO 27002 is not straightforward. Terminology differs – HIPAA refers to “security incident procedures” and “risk analysis,” whereas ISO 27002 speaks of “information security incident management” and “risk assessment.” NIST SP 800‑66r2 clarifies that risk analysis is an accurate and thorough assessment of threats and vulnerabilities. Some HIPAA obligations, such as business associate agreements and breach notification details, have no ISO equivalent. Conversely, ISO introduces controls like threat intelligence, data masking and secure coding that go beyond HIPAA. To navigate these differences, organizations should adopt a risk‑based mindset, prioritize high‑risk systems, engage cross‑functional teams (IT, compliance and legal), automate control monitoring and evidence collection, and update their mapping matrix as frameworks evolve.
Conclusion
Mapping HIPAA controls to ISO 27002 is more than a compliance exercise. Done right, HIPAA Controls Mapped To ISO 27002 unify risk management, policy design and evidence collection. When controls serve multiple frameworks, organizations save time and reduce audit fatigue. Our experience shows that aligning controls can cut readiness timelines from nine months to four or five and reduce internal effort by 75 % (75 hours per year versus 550–600 hours self‑managed). Most importantly, it builds security programs that operate under pressure. Security that reads well but fails under incident pressure is a liability. By starting with robust security and implementing HIPAA Controls Mapped To ISO 27002 consistently across people, processes and technology, healthcare leaders can protect patients, accelerate enterprise deals and satisfy regulators.
FAQs
1. What does “mapping HIPAA to ISO 27002” mean?
Mapping HIPAA to ISO 27002 involves crossreferencing HIPAA’s administrative, physical and technical safeguards with corresponding ISO 27002 controls. The purpose is to implement one set of controls that satisfy both frameworks. Pivot Point Security estimates that 65 of the 134 ISO 27002 controls map to HIPAA, leaving only business associate agreements as a HIPAA‑specific requirement.
2. Is there a certification for HIPAA or ISO 27002?
There is no formal HIPAA certification – compliance is assessed through audits and enforcement actions by the Office for Civil Rights (OCR). ISO 27002 is not certifiable on its own; organizations are certified against ISO 27001, which references ISO 27002 controls. Certification requires implementing an information security management system (ISMS), undergoing an independent audit and maintaining continuous improvement.
3. Do all HIPAA controls map directly to ISO 27002?
No. While many HIPAA safeguards correspond to ISO 27002 controls, some requirements – such as business associate agreements, specific breach notification procedures and certain documentation obligations – have no direct ISO 27002 equivalents. Conversely, ISO 27002 includes controls like threat intelligence and secure coding that go beyond HIPAA. Organizations should treat ISO 27002 as a baseline and implement additional controls where needed.
4. How does mapping help with audits and compliance checks?
Mapping enables organizations to collect evidence once and reuse it across audits. For example, access logs and incident response records can support HIPAA, SOC 2 and ISO 27001 audits simultaneously. Evidence must demonstrate that controls operate over a defined period – SOC 2 Type II audits test control effectiveness over 3–12 months, and OCR investigations often examine past incidents and corrective actions. A well‑designed mapping matrix ensures that evidence aligns with each framework’s requirements, streamlining audit preparation and reducing the risk of findings.
5. Can this help with other frameworks like NIST or HITRUST?
Yes. Mapping HIPAA Controls Mapped To ISO 27002 provides a foundation for aligning with NIST CSF, NIST 800‑53 and the HITRUST CSF. ISO 27002’s attributes support categorization by cybersecurity concepts, which align with NIST functions (Identify, Protect, Detect, Respond, Recover). HITRUST, a certifiable framework used widely in healthcare, integrates ISO 27001/27002, SOC 2 and HIPAA controls. By mapping once and reusing controls, organizations can accelerate compliance across multiple frameworks and reduce overall effort.





.svg)






.svg)
.svg)