Healthcare organizations are awash in data. Electronic health records (EHRs), imaging systems, telemetry from medical devices, insurance claims, and even patient‑generated data from wearables pour into hospitals and clinics every hour. By 2024 the market for data lakes reached USD 20.1 billion, and analysts expect it to grow more than 20 percent annually to over USD 74 billion by 2031. Health systems are drawn to these technologies because a secure data lake gives them the flexibility to ingest all kinds of data, store it cheaply, and analyze it using machine learning and analytics tools. Yet health data is also one of the most regulated types of information.
Under the United States’ Health Insurance Portability and Accountability Act (HIPAA), an organization must protect electronic protected health information (ePHI) with administrative, physical, and technical safeguards. If there is an impermissible disclosure of PHI that is not encrypted or destroyed, the organization must notify the affected individuals and regulators. Without proper security, a data lake can become a single point of failure.
This article explains how to build a HIPAA‑compliant data lake in healthcare. It clarifies the regulatory requirements, outlines architectural patterns, provides checklists for practitioners, and draws on Konfirmity’s experience delivering over 6,000 audits and 25 years of combined expertise. You will learn how Data Lake and HIPAA considerations influence architecture and operations, why human‑led managed services accelerate compliance, and how security that is strong in practice—not just on paper—can speed enterprise procurement.
What Is a Data Lake in Healthcare?
A data lake is a centralized repository that stores vast amounts of raw data in its native format. Unlike traditional data warehouses that require a rigid schema and store only structured data, data lakes embrace a schema‑on‑read approach and can ingest structured, semi‑structured, and unstructured data such as JSON, XML, images, and audio. This flexibility lets clinicians and data scientists analyze information without first modeling it for a relational database. According to a 2024 market analysis, the global data lake market is projected to triple by 2031, highlighting the adoption of cloud‑native data platforms.
Types of Healthcare Data Stored
- Electronic health records (EHRs): Detailed patient histories, diagnoses, medications, lab results, and clinician notes.
- Medical imaging: Radiology images (CT, MRI), ultrasounds, DICOM files, and pathology slides.
- Device telemetry: Logs from infusion pumps, cardiac monitors, implantable devices, and remote patient monitoring devices.
- Administrative data: Insurance claims, billing data, appointment schedules, and patient satisfaction surveys.
- Genomic and research data: Sequencing data, clinical trial records, and real‑world evidence from observational studies.
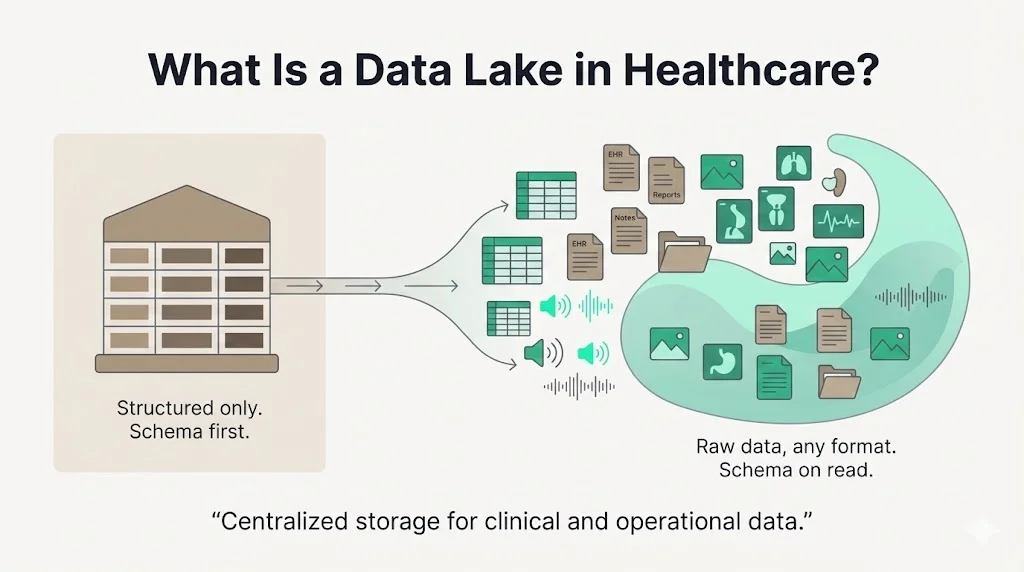
Data Lakes vs. Data Warehouses
Data warehouses rely on a schema‑on‑write model: data must be structured into predefined tables before loading, which makes them suitable for business intelligence and reporting. They often integrate data from multiple sources and store historical information for queries, but they can be rigid and expensive to scale. Data lakes, by contrast, can ingest raw data without forcing it into a strict schema, store it inexpensively, and make it available for various analytics workloads. In healthcare this matters because patient data comes from disparate systems—EHRs, picture archiving and communication systems (PACS), HL7 streams, and wearable devices. A data lake allows these diverse sources to be aggregated and then curated into refined datasets while retaining the full fidelity of the original records.
HIPAA Basics Every Healthcare Data Architect Should Know
To build a Data Lake And HIPAA compliance program, you must understand HIPAA’s core rules. HIPAA establishes three primary safeguards for ePHI:
- Privacy Rule: Defines protected health information (PHI) as individually identifiable information relating to a person’s health, treatment, or payment. PHI includes data such as names, addresses, birth dates, Social Security numbers, diagnosis codes, and payment information. Covered entities—health providers, insurers, and healthcare clearinghouses—must limit uses and disclosures of PHI and give patients rights over their data.
- Security Rule: Requires covered entities and business associates to implement administrative, physical, and technical safeguards. Administrative safeguards include risk analysis, risk management, assigning security responsibility, workforce training, incident response, and contingency plans. Physical safeguards address facility access controls, device and media controls, and workstation security. Technical safeguards mandate access control, audit controls, integrity controls, authentication, and transmission security.
- Breach Notification Rule: Dictates that organizations must notify individuals, HHS, and sometimes the media if unsecured PHI is breached. However, if ePHI is encrypted or destroyed such that it becomes unreadable or indecipherable, the breach is not considered “unsecured” and notification is not required.
Understanding these rules is foundational. PHI is broader than many engineers assume; it includes any information in a medical record that could identify a patient. A secure data lake must therefore protect not only clinical variables but also metadata like device identifiers, encounter numbers, and IP addresses. It must also support breach response—an overlooked requirement for data lake design. Without proper logging and encryption, a single misconfiguration can trigger a breach notification obligation.
HIPAA Data Lake Security Fundamentals
Health Information Security & Patient Privacy
The first principle of Data Lake And HIPAA compliance is protecting sensitive health information from unauthorized access. HIPAA classifies ePHI as any individually identifiable health data transmitted or stored electronically. This includes not only a patient’s medical history but any associated identifier in the same record set. A data lake must therefore treat clinical notes, imaging metadata, and device logs as sensitive. Encryption is widely regarded as the most effective method to ensure that stolen data cannot be read. The HIPAA Security Rule labels encryption as an “addressable” implementation specification—meaning organizations must adopt it when reasonable and appropriate. In practice, encryption is essential because it transforms data into a form that is unreadable, undecipherable, and unusable without a key.
From Konfirmity’s delivery experience, encryption should be applied at every layer of the data lake—file storage, object buckets, databases, and network channels. We have seen audits fail due to unencrypted backups or plaintext test environments containing PHI. A typical enterprise may have dozens of pipelines feeding raw data into a lake; each must enforce encryption in transit (TLS 1.2+) and at rest using strong algorithms (e.g., AES‑256), with keys rotated regularly and stored in a managed key service. Without encryption, a lost laptop containing API tokens or a compromised network file share could expose millions of records and trigger notifiable breaches.
Regulatory Standards & Compliance
HIPAA compliance does not exist in a vacuum. Enterprise buyers often request proof of compliance with multiple frameworks—SOC 2, ISO 27001, GDPR, and HITRUST. HIPAA shares many of the same control families (access control, incident response, logging, vendor management) with these frameworks. Konfirmity recommends adopting a risk‑based approach and mapping controls across frameworks. For example, NIST SP 800‑66 (2024) provides practical guidance on implementing the Security Rule and mapping it to the NIST Cybersecurity Framework. The technical safeguards section highlights required controls such as unique user identification, audit controls, integrity checks, authentication, and transmission security. The standard emphasises that even “addressable” controls like encryption must be implemented unless an equivalent measure is documented as reasonable and appropriate. Practitioners must document these decisions, as auditors will request evidence that alternatives were evaluated.
Beyond HIPAA, many healthtech firms pursue SOC 2 Type II attestation to satisfy vendor risk questionnaires. A Type II audit requires a continuous observation period, typically three to six months, during which controls such as access reviews, change management, vulnerability remediation, and logging must operate without gaps. Konfirmity’s managed service integrates HIPAA and SOC 2 requirements so clients can reuse evidence across frameworks and avoid duplicate work. In our experience, a well‑run program can achieve SOC 2 readiness in four to five months versus nine to twelve months for self‑managed teams, with a 75% reduction in internal effort.
Encryption Strategies
Encryption needs to be considered holistically—not as an afterthought for storage. The HIPAA Journal’s 2025 guidance notes that encryption solutions aligned with NIST SP 800‑111 for data at rest and NIST SP 800‑52 for data in transit contribute toward recognized security frameworks. Implementing encryption ensures that ePHI is unreadable and unusable by anyone without access rights. Data‑at‑rest encryption should cover all storage mediums: object stores, block volumes, relational databases, caches, and backups. Data‑in‑transit encryption should include TLS for API traffic, secure tunneling for service‑to‑service communication, and encrypted email for transmissions to business associates.
Konfirmity’s practice advises customer‑managed keys whenever possible. With customer‑managed keys, healthcare organizations control the lifecycle—creation, rotation, and destruction—of encryption keys, whereas provider‑managed keys rely on the cloud vendor. While provider‑managed encryption is easier to set up, regulators may view it as less robust because keys could be exposed in a supply‑chain breach. Healthcare providers should also separate production and non‑production keys, enforce strict role‑based access to key management services, and monitor key usage logs for anomalies.
Encryption alone is not enough. It must be paired with integrity controls such as hashing and signing to detect unauthorized modifications. The Security Rule lists integrity and authentication as technical safeguards. A well‑designed data lake pipeline should generate checksums when ingesting files, validate those checksums before processing, and record signatures to provide non‑repudiation. Logging and monitoring should capture any failed integrity checks as potential incidents.
Access Controls
Access controls govern who can view and manipulate data. HIPAA’s technical safeguards require unique user identification, emergency access procedures, automatic logoff, and encryption/decryption mechanisms. In a data lake context, this means enforcing role‑based access control (RBAC) or attribute‑based access control (ABAC) at both the storage and query layers. A least‑privilege model ensures that analysts only see the data needed for their job functions. Konfirmity’s audits often uncover over‑permissive IAM roles; default roles may grant broad read or write access across the data lake. Remediation involves scoping roles to specific S3 buckets, database schemas, or analytics clusters, and enforcing multi‑factor authentication for console access.
Key access control practices include:
- Central identity management: Integrate the data lake with a corporate identity provider using SAML or OIDC to enforce single sign‑on and MFA.
- Segregated environments: Separate production, staging, and development; each zone should have its own access policies to prevent lateral movement.
- Credential rotation and revocation: Rotate service account keys regularly and remove access promptly when personnel change roles.
- Just‑in‑time access: For sensitive operations, require administrators to request elevated privileges only when necessary and log all actions.
Access control misconfiguration is one of the most frequent root causes of healthcare breaches. Attackers often exploit shared credentials or dormant accounts to roam a network undetected. A robust access governance process must include quarterly access reviews, automated detection of unused permissions, and strong password policies.
Audit Trails and Monitoring
Logging is not optional; it is an explicit HIPAA requirement. The Security Rule requires audit controls to record and examine system activity. In practice, a data lake should capture logs for ingestion events, schema changes, query execution, and administrative actions. These logs must be tamper‑evident and preserved for the retention period mandated by HIPAA and other regulations. Regular log review supports breach detection and can shorten the mean time to detect (MTTD) incidents.
Konfirmity recommends setting up a security information and event management (SIEM) or security data lake that ingests telemetry from the data lake infrastructure. The SIEM should alert on anomalies such as unexpected API calls, unusual access patterns (e.g., bulk export outside business hours), and failed authentication attempts. We also encourage linking audit logs to incident response protocols; when a high‑priority alert fires, the incident response team should automatically create a ticket, assign roles, and document steps taken. Without integrated monitoring, organizations often miss early indicators of compromise and discover breaches months later.
Architecture Walkthrough: Building a HIPAA‑Compliant Data Lake
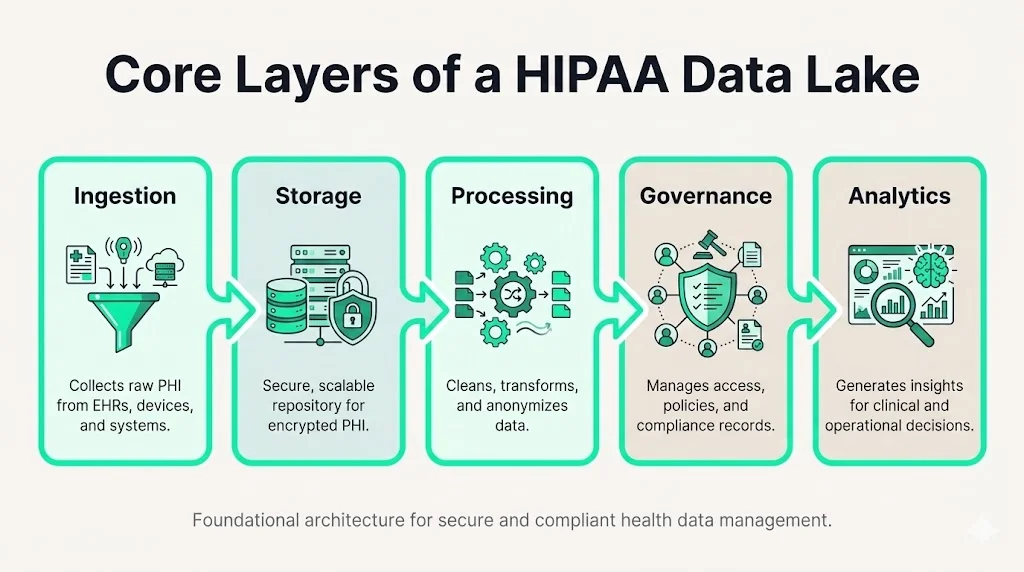
Core Layers of a HIPAA Data Lake
A secure healthcare data lake typically comprises five layers:
- Ingestion Layer: Interfaces that accept data from EHR systems, PACS, laboratories, and medical devices. Ingestion services must support secure protocols (HTTPS, SFTP, HL7 over TLS), validate file formats, and attach metadata such as source system, timestamps, and classification. They should also verify digital signatures and apply encryption upon arrival.
- Storage Layer: The core repository. Choose scalable and durable storage (e.g., object storage like Amazon S3 or Azure Blob) with encryption at rest (server‑side or client‑side) and versioning enabled. Each bucket or container should have strict access policies and separation of duties—no single role should both upload and delete data. Designing this layer with a Data Lake And HIPAA mindset means treating every storage location as if it contains PHI, even when holding de‑identified or tokenized data. That mindset drives consistent encryption, retention, and access controls across the lake.
- Processing Layer: ETL or ELT pipelines that transform raw data into cleansed, curated datasets. Tools might include Apache Spark, AWS Glue, or Databricks. ETL processes should sanitize sensitive fields, tokenize identifiers, and produce hashed linkage keys. The pipeline must log transformations and ensure that any data exported to downstream systems remains compliant.
- Governance Layer: Metadata cataloging, data classification, and policy enforcement. A governance layer tracks data lineage, quality, and ownership. Classification tags indicate whether a file contains PHI, de‑identified data, or public content. Retention policies are applied here to ensure that data is deleted when no longer needed.
- Analytics Layer: Query and analysis tools such as Amazon Athena, Google BigQuery, or Snowflake. Access here should be limited to authorized users with proper RBAC and data masking. Tools should support dynamic data masking or tokenization to hide direct identifiers while still enabling research. A governed analytics environment ensures that analysts cannot inadvertently reconstruct identities.
Data Zoning Best Practices
Segmenting the data lake into zones reduces risk and simplifies compliance: when you align zoning with Data Lake And HIPAA requirements, you ensure that sensitive PHI remains isolated from less restricted data and that controls can be tailored to the sensitivity of each zone.
- Raw zone: Stores unprocessed ingestion files. Access is tightly restricted, and encryption is mandatory. Data may include PHI and must not be used directly for analysis.
- Clean zone: Holds standardized data after initial validation. Sensitive identifiers are masked or tokenized. Only trusted ETL services can write here.
- Curated zone: Contains datasets designed for analytics and machine learning. Data is de‑identified when possible. Analysts access this zone to run queries.
Applying zoning allows different security policies by sensitivity. For example, the raw zone may be accessible only to system accounts, while the curated zone can be exposed to data scientists under strict audit logging.
Cloud Platform Considerations
Major cloud providers offer HIPAA‑eligible services such as AWS HealthLake, Google Cloud Healthcare API, and Microsoft Azure Health Data Services. These platforms provide encryption, identity management, and audit logging out‑of‑the‑box. According to a case study on AWS HealthLake, the service offers advanced cloud security and encryption support compliant with HIPAA regulations, enabling organizations to store data with authorized access control for privacy and safety. Nonetheless, organizations must sign a Business Associate Agreement (BAA) with the cloud provider, configure encryption keys, and set up monitoring. Provider defaults are not enough; misconfigured S3 buckets or open ports have been responsible for numerous healthcare breaches.
Templates & Checklists
Building a HIPAA‑compliant data lake is complex. Practitioners benefit from standardized templates to track controls, evidence, and gaps. Konfirmity provides the following templates to our clients; each is tailored for a data lake environment:
Security Controls Checklist
- Encryption: Verify that all storage and backup locations enable encryption at rest. Confirm that TLS 1.2+ or HTTPS is used for all data in transit. For each resource, document whether encryption keys are customer‑managed or provider‑managed and confirm rotation policies. Remember that applying encryption broadly reduces attack surface and can prevent notifiable breaches.
- IAM Roles and Policies: List all IAM roles associated with the data lake. Document the permissions granted, ensuring least privilege. Identify any wildcard permissions and tighten them. Confirm that MFA is enforced for all human users.
- Logging and Monitoring: Identify all log sources (ingestion logs, access logs, ETL logs, query logs). Confirm that logs are forwarded to a SIEM and retention policies meet HIPAA and internal requirements. Verify that alert thresholds and escalation procedures are defined.
HIPAA Compliance Validation Template
- Risk Assessment: Document the methodology used to assess threats and vulnerabilities. NIST SP 800‑66 emphasizes the need for an accurate and thorough assessment of risks to ePHI. Include threat models for insider threats, external attackers, and system failures.
- Gap Assessment: Map existing controls to the HIPAA Security Rule’s required and addressable specifications. Identify gaps, such as missing audit controls or insufficient training, and propose remediation steps.
- Evidence Collection: Gather proof of control operation—access review records, encryption key rotation logs, training attendance. Ensure evidence covers at least three months for a Type II observation window.
Incident Response Plan for Data Lakes
- Detection: Define triggers for potential incidents—failed logins, anomalies in data exfiltration, or ETL failures.
- Containment: Steps for isolating affected workloads or accounts. Include instructions for disabling credentials and revoking tokens.
- Eradication and Recovery: Procedures for purging malicious code, validating data integrity, and restoring from backups.
- Communication and Reporting: Outline how to notify internal stakeholders, legal counsel, and regulators. The Breach Notification Rule requires timely notification when unsecured PHI is breached. However, if data is encrypted or destroyed, the incident may not be notifiable.
- Lessons Learned: After the incident, conduct a post‑mortem to identify root causes and update controls.
Data Lake Governance Policy Template
- Ownership and Lifecycle Management: Assign data owners for each dataset and define responsibilities for data quality, classification, and deletion.
- Data Classification and Retention Rules: Adopt a classification scheme—PHI, de‑identified, operational, public. Specify retention periods in line with legal requirements and research value. Ensure automated deletion for expired data.
- Access Review Cadence: Set quarterly reviews of IAM roles and permissions. Document approvals and adjustments. Ensure that terminated employees are promptly removed.
Data Breach Prevention in Healthcare
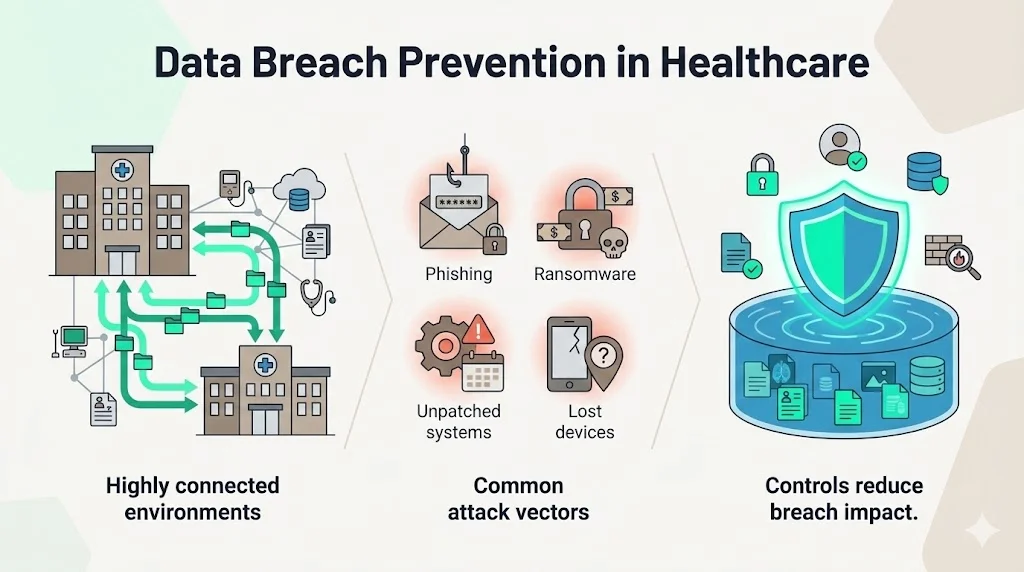
Healthcare has become a lucrative target for attackers because health data commands high prices on the dark web and organizations maintain complex, interconnected systems. Implementing a comprehensive Data Lake And HIPAA program is critical in this environment because it ensures encryption, fine‑grained access control, and continuous monitoring are applied consistently across the lake. In 2024 alone, approximately 275 million healthcare records were breached in the United States. The average cost of a healthcare breach reached $9.77 million in 2024, compared with a global average cost per record of $148. IBM’s 2024 report cites an even higher figure—$11 million per breach—for the healthcare sector. Common attack vectors include phishing, ransomware, unpatched systems, and lost or stolen devices.
A secure data lake mitigates these risks by implementing layered controls. Encryption renders stolen data useless. Access controls reduce the number of entry points. Logging and monitoring detect suspicious activity. Incident response procedures ensure swift containment. Without these measures, organizations face not only financial losses but also regulatory penalties and reputational damage. For example, in 2025 the Syracuse Ambulatory Surgery Center settlement with the HHS Office for Civil Rights involved a $250,000 penalty and a corrective action plan after a breach of 24,891 individuals’ data due to inadequate risk analysis and delayed notifications. The case underscores that regulators expect organizations to perform thorough risk assessments, apply appropriate controls, and report incidents quickly.
Case Examples
To illustrate how Data Lake And HIPAA requirements are implemented in practice, consider two high‑level case scenarios drawn from anonymized projects.
Large Integrated Delivery Network (IDN)
An IDN with ten hospitals and hundreds of clinics wanted to consolidate EHR, imaging, and claims data into a cloud‑based lake to support population health analytics and machine learning. The existing environment spanned dozens of on‑premises systems with inconsistent security controls. Konfirmity designed a HIPAA‑compliant data lake that enforced encryption at rest and in transit, integrated with the IDN’s identity provider for RBAC, and segmented data into raw, cleansed, and curated zones. We mapped controls to HIPAA, SOC 2, and HITRUST, reusing evidence for multiple frameworks. The program implemented automated access reviews and continuous vulnerability scanning. Over a six‑month observation window the IDN recorded zero material control failures, achieved SOC 2 Type II attestation on its first attempt, and accelerated four enterprise deals that previously stalled due to security questionnaires.
Digital Health Startup
A Series B digital health company developed a remote patient monitoring platform that streams device telemetry and user‑entered symptoms to a data lake. Without a dedicated security team, the company struggled to meet procurement requirements from hospital customers. Konfirmity implemented a human‑led managed service that established an encrypted ingestion pipeline, built automated alerting for abnormal device readings, and developed a HIPAA Incident Response Plan. We also created a role‑based access system with just‑in‑time admin access. Within four months the startup passed its first HIPAA security assessment and secured a large health system contract. The company saved hundreds of hours compared with building an in‑house compliance program and avoided the “compliance manufacturing” trap by designing durable controls rather than focusing only on audit artifacts.
These examples highlight common pitfalls: underestimating the effort needed to implement controls, over‑provisioning access, neglecting key rotation, and failing to integrate logging with incident response. They also demonstrate that human‑led, managed security and compliance can significantly reduce effort and accelerate commercial outcomes.
Conclusion
Building a secure healthcare data lake is not just about technology. It requires understanding HIPAA’s privacy, security, and breach notification rules; adopting encryption, access controls, and audit logging; aligning with multiple frameworks such as SOC 2 and ISO 27001; and designing architecture that scales without compromising security. Healthcare records are valuable, and the consequences of a breach can be severe—average breach costs exceed $9 million, and regulatory penalties can be significant. The good news is that a well‑designed Data Lake And HIPAA program—one that focuses on real security outcomes—can protect patients, satisfy auditors, and unlock business growth.
Konfirmity’s approach is grounded in experience: we have supported more than 6,000 audits and delivered outcomes‑as‑a‑service with dedicated experts. Our clients typically achieve SOC 2 readiness in 4–5 months with 75 percent less internal effort, and they avoid the two‑week promises of “compliance manufacturing” vendors that neglect observation periods and evidence depth. We implement controls inside your stack and operate them year‑round. Our goal is simple: start with security and arrive at compliance. Security that looks impressive on paper but fails during an incident is a liability. Build your program once, operate it daily, and let compliance follow.
FAQs
1 ) What is a data lake in healthcare?
A healthcare data lake is a centralized repository that stores structured and unstructured data—EHRs, medical images, device logs—in its raw form. Unlike a data warehouse, which requires a predefined schema, a data lake uses a schema‑on‑read approach, making it flexible for analytics and machine learning. It is the foundation of modern population health management, precision medicine, and research applications.
2 ) What data is considered HIPAA data?
HIPAA data refers to protected health information (PHI)—any individually identifiable health, treatment, or payment information. PHI can include names, medical record numbers, insurance details, biometric identifiers, or any combination of information that could identify a patient. In a data lake, you must treat all data that could be linked to an individual as PHI and apply the appropriate safeguards.
3 ) What is the difference between a data lake and a security lake?
A data lake stores raw, diverse data for analytics. A security lake—often built on the same platform—collects security telemetry such as logs, events, and audit trails for threat detection and incident response. While a data lake supports research and business intelligence, a security lake focuses on monitoring, detection, and compliance. In practice, integrating a security lake with your data lake helps meet HIPAA’s audit control requirements and accelerates investigations.
4 ) What is the purpose of a data lake?
The purpose of a data lake is to centralize large volumes of data from multiple sources so that organizations can govern, discover, analyze, and apply machine learning without being constrained by rigid schemas. In healthcare, this means unifying clinical, imaging, and device data to gain insights that improve care, reduce costs, and advance research.





.svg)






.svg)
.svg)