A Data Protection Impact Assessment helps organisations understand how a project or system might affect individuals’ privacy and it formalises the steps to identify, evaluate, and mitigate those impacts. Under the European Union’s General Data Protection Regulation (GDPR), DPIAs are required when processing operations present high risk to the privacy rights of individuals. In contrast, HIPAA, a U.S. law governing health‑care data, does not explicitly mention DPIAs. Instead, the HIPAA Security Rule requires a risk analysis to evaluate potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI. Regulators emphasise that this analysis must be “accurate and thorough” and that it should account for all forms of ePHI regardless of media or location.
Why is this relevant? In 2024 alone, breaches in U.S. health‑care exposed the records of more than 276 million individuals—an average of over 758,000 records per day. The largest single incident, a ransomware attack on Change Healthcare, compromised 190 million records. Such events highlight both operational and reputational risks; IBM’s Cost of a Data Breach study shows that health‑care breaches carry the highest average cost at roughly $10.93 million, and they often take seven months to detect. The Office for Civil Rights (OCR) has increased enforcement as a result: by May 2025, OCR had closed nine investigations with financial penalties under its risk‑analysis enforcement initiative. With regulators proposing to make all Security Rule implementation specifications mandatory and to require more specific documentation, the stakes are rising. The HIPAA DPIA Guide aims to help health‑care organisations meet these obligations while adopting a forward‑looking privacy posture.
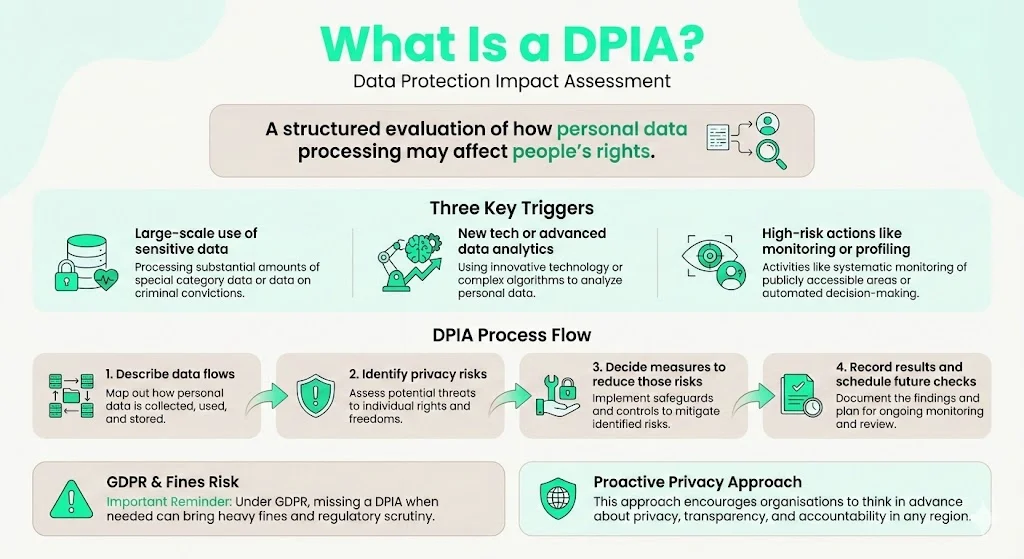
What Is a DPIA?
A Data Protection Impact Assessment is a structured evaluation of how processing personal data may affect individuals’ rights. The concept originates from privacy regulations such as the GDPR and the United Kingdom’s Data Protection Act 2018. A DPIA is typically required when processing involves:
- Large‑scale handling of sensitive personal data, such as medical or genetic information.
- Use of new technologies or novel data‑analytics techniques.
- High‑risk operations, such as systematic monitoring or profiling.
The process involves describing data flows, identifying risks to privacy, and defining measures to mitigate those risks. The output is a documented assessment that includes a mitigation plan and a schedule for ongoing monitoring. Under GDPR, failure to conduct a DPIA when required can result in substantial fines. Even outside the EU, the DPIA framework encourages organisations to think proactively about privacy, transparency, and accountability.
HIPAA Security Rule: Risk Analysis Requirement
HIPAA sets national standards for safeguarding health information. The Security Rule, codified at 45 C.F.R. § 164.302–318, requires covered entities and business associates to implement reasonable safeguards to protect ePHI. Section 164.308(a)(1)(ii)(A) directs regulated entities to conduct an accurate and thorough assessment of potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information. This risk analysis is part of the Security Management Process and is foundational for determining appropriate administrative, physical, and technical safeguards. The guidance from OCR clarifies that the analysis should:
- Identify where ePHI is stored, transmitted, or maintained.
- Document reasonably anticipated threats and vulnerabilities.
- Assess current security measures.
- Determine the likelihood and potential impact of threat occurrence.
- Assign risk levels and document corrective actions.
- Create written documentation and perform periodic reviews.
The Security Rule does not mandate a specific methodology. NIST Special Publications, including SP 800‑30 and SP 800‑66r2, provide widely adopted frameworks. For example, NIST defines risk as the combination of the probability that a threat exploits a vulnerability and the resulting impact. OCR guidance also states that risk analysis should be an ongoing process that integrates with business operations and technology planning.
Importantly, HIPAA’s risk analysis is not a DPIA in name. However, it covers similar ground: both involve understanding data flows, evaluating risks to confidentiality and integrity, assessing controls, and documenting findings. The HIPAA DPIA Guide demonstrates how merging these approaches can strengthen a health‑care organisation’s security posture.
Why Combine DPIA Thinking with HIPAA Compliance?
Although HIPAA does not require a formal DPIA, there are several reasons to adopt privacy‑impact thinking alongside the mandated risk analysis:
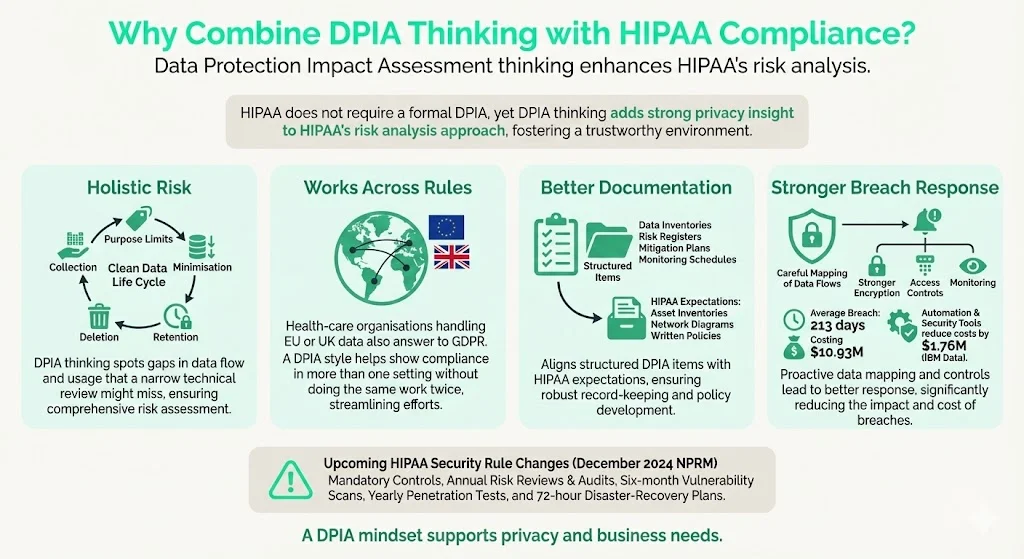
- Holistic risk management. DPIAs encourage organisations to consider the full life cycle of data processing, including collection, purpose limitation, minimisation, retention, and deletion. This complements HIPAA’s focus on safeguarding ePHI and can uncover exposures that a narrow technical assessment might miss.
- Regulatory convergence. Health‑care organisations often operate across jurisdictions. If they process data of EU or UK residents, they must comply with GDPR and other privacy laws. Applying a DPIA framework makes it easier to demonstrate compliance with multiple regimes without duplicative work.
- Better documentation and governance. DPIAs typically produce structured artefacts: data inventories, risk registers, mitigation plans, and monitoring schedules. These documents can satisfy audit demands from regulators, customers, or partners. Under the proposed HIPAA Security Rule amendments, regulated entities must maintain a technology asset inventory, network map, and detailed written policies. A DPIA‑style process naturally generates such artefacts.
- Improved breach prevention and response. High‑profile breaches highlight how quickly incidents spiral when organisations lack visibility into their data flows. By systematically mapping data and evaluating privacy risks, teams can prioritise encryption, access controls, and monitoring. IBM’s report notes that health‑care breaches lasting an average of 213 days cost $10.93 million; organisations using automation and AI security tools reduced costs by $1.76 million. A DPIA mindset helps justify investment in such controls.
- Preparedness for evolving rules. The December 2024 HIPAA Security Rule NPRM proposes removing the distinction between “required” and “addressable” controls, making all specifications mandatory. It would also require documented asset inventories, network maps, and periodic compliance audits. Coalfire summarises the proposed changes: annual risk assessments and audits, mandatory encryption and multi‑factor authentication (MFA), vulnerability scans every six months, penetration tests annually, and 72‑hour disaster‑recovery plans. By integrating DPIA elements now, organisations can adapt more quickly when these rules become final.
In short, the HIPAA DPIA Guide is not about adding bureaucracy; it is about building durable security programs that support both privacy and business objectives.
When to Treat HIPAA Risk Assessments as DPIA‑Style Analyses
Not every operational change warrants a full DPIA, but certain scenarios in health‑care clearly align with the triggers under data‑protection laws. Regulated entities should apply DPIA‑style discipline when:
- Implementing new electronic health record (EHR) systems or patient portals. Launching or migrating an EHR involves large‑scale processing of sensitive information and introduces novel workflows. A DPIA ensures data flows are mapped and residual risks are addressed before going live.
- Rolling out telehealth platforms. Remote consultations and remote data storage heighten exposure to interception and unauthorised access. It is essential to evaluate transmission security, endpoint protection, and provider authentication.
- Onboarding business associates or vendors. Under HIPAA, business associates must sign agreements to safeguard ePHI. A DPIA‑style assessment can evaluate whether third‑party controls meet HIPAA and privacy‑law expectations. When sharing patient data with laboratories or imaging providers, map data flows, confirm encryption, and specify audit rights.
- Performing large‑scale analytics. Genomics, mental‑health records, and predictive modelling involve particularly sensitive data. DPIAs can assess whether anonymisation or pseudonymisation techniques are sufficient to minimise re‑identification risk.
- Migrating to cloud infrastructure or significantly changing data retention periods. Cloud migrations can involve cross‑border transfers and change the organisation’s threat landscape. DPIA‑style analysis ensures data residency, encryption, and access controls remain effective. Similarly, decisions to retain or purge data should consider privacy impact and minimisation principles.
- Using new technologies such as artificial intelligence for diagnostic or administrative purposes. The proposed Security Rule revisions would require regulated entities to review their asset inventory and network map at least annually and to identify reasonably anticipated threats and vulnerabilities. Emerging tools introduce new attack surfaces that warrant deeper scrutiny.
Mapping these scenarios to the DPIA triggers—large‑scale processing, new technology, or high‑risk activities—helps teams decide when to expand beyond routine risk assessments.
Step‑by‑Step Guide to Conducting a HIPAA‑Ready DPIA
Drawing on OCR guidance, NIST frameworks, and Konfirmity’s delivery experience, this section presents a practical process that blends the DPIA structure with HIPAA’s Security Rule requirements. Each step should be documented and updated as circumstances change.
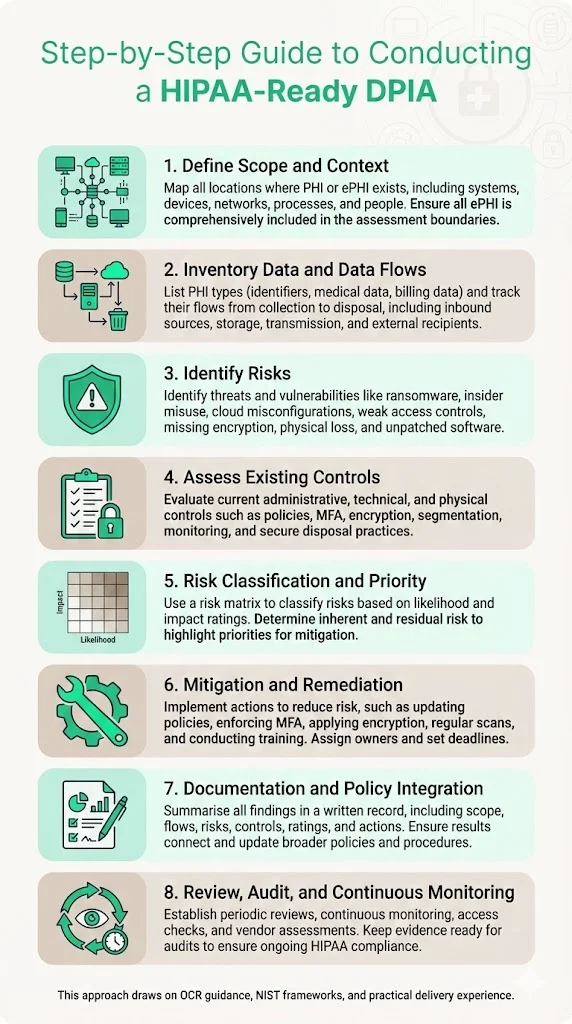
Step 1: Define Scope and Context
The foundation of any assessment is understanding what is within scope. Map all touchpoints where PHI or ePHI is created, stored, processed, transmitted, or disposed of. Include systems (EHRs, billing software, laboratory interfaces), devices (servers, laptops, mobile devices, IoT medical equipment), networks (internal, cloud, third‑party connections), processes (patient intake, billing, telehealth sessions), and people (employees, contractors, vendors). OCR guidance emphasises that the risk analysis must include all ePHI, regardless of medium or location. In practice, Konfirmity teams often start with existing asset inventories, network diagrams, and data retention policies, then validate them through interviews and technical discovery. For non‑electronic PHI (paper records), consider whether retention or destruction processes might expose data.
Step 2: Inventory Data and Data Flows
Develop a catalogue of the types of PHI processed—patient identifiers, medical histories, diagnostic images, billing information, genetic or behavioural data. Map data flows from origination to final disposition: inbound sources (clinics, laboratories, devices), storage locations (databases, cloud services, backups), transmission paths (internal networks, APIs, VPNs), and external recipients (business associates, government registries). Identify where ePHI crosses network boundaries or is handled by third parties. OCR guidance highlights the need to identify where ePHI is stored, received, maintained, or transmitted, and the proposed Security Rule would require an asset inventory and network map updated at least every 12 months.
A useful tool is a data‑flow diagram that illustrates data at rest and in transit. Many breaches occur because organisations are unaware of hidden flows—for example, debug logs containing PHI stored in unencrypted cloud buckets. At Konfirmity, we integrate with log management and cloud configuration APIs to detect such blind spots early.
Step 3: Identify Risks: Threats and Vulnerabilities
List potential threats and vulnerabilities to the confidentiality, integrity, and availability of PHI. OCR guidance cites natural, human, and environmental threats; examples include:
- External attacks (ransomware, phishing, supply‑chain compromise).
- Insider misuse or error (unauthorised access, snooping, accidental disclosure).
- Misconfiguration of cloud services or databases.
- Weak authentication or access controls.
- Lack of encryption for data at rest or in transit.
- Physical threats (theft of devices, improper disposal of hardware).
- Software vulnerabilities and unpatched systems.
For each threat, consider the associated vulnerabilities—e.g., exposed remote desktop services, outdated libraries, or untrained staff. Schellman notes that common pitfalls include incomplete scoping of the ePHI environment and ignoring identified risks. Given the ever‑changing threat landscape, incorporate threat intelligence feeds and vulnerability scanning results into the assessment. Konfirmity uses CVSS scoring to prioritise vulnerabilities based on severity and exploitability.
Step 4: Assess Existing Controls
Review administrative, technical, and physical controls in place:
- Administrative: policies for access management, hiring and termination procedures, training and awareness, incident response plans, vendor due diligence, and sanctions for violations.
- Technical: encryption at rest and in transit, multi‑factor authentication, network segmentation, intrusion detection/prevention, secure coding practices, vulnerability management, and logging/monitoring.
- Physical: facility access controls, locking mechanisms, video surveillance, secure disposal of devices, and environmental protections (fire suppression, UPS systems).
The proposed Security Rule would make encryption and MFA explicit requirements. Evaluate whether current controls satisfy these expectations. Also review business associate agreements to ensure vendors implement comparable safeguards.
Step 5: Risk Classification and Prioritisation
Assign a risk level to each threat–vulnerability combination based on its likelihood and potential impact. NIST and OCR suggest using qualitative or quantitative methods; a simple 5 × 5 matrix (Very Low, Low, Moderate, High, Very High) can help visualise priorities. Schellman recommends calculating inherent risk (before controls) and residual risk (after controls). High‑impact, high‑likelihood risks should be addressed promptly, while lower‑level risks can be tracked for future mitigation. Document the methodology and criteria used—auditors will want to understand how you derived scores.
Step 6: Define Mitigation and Remediation Actions
For each high‑priority risk, propose concrete actions and assign owners and timelines. Mitigation strategies might include:
- Updating policies to clarify permissible uses of PHI and sanctions for violations.
- Implementing encryption across databases, backups, and endpoints.
- Enforcing MFA and least‑privilege access controls.
- Conducting periodic access reviews and off‑boarding procedures.
- Performing regular vulnerability scanning (semi‑annual) and penetration testing (annual), as proposed in the NPRM.
- Training workforce members on phishing awareness, social engineering, and secure handling of PHI.
- Reviewing and updating business associate agreements to require annual certifications and audits.
- Improving incident response plans to ensure detection and reporting within mandated timeframes.
For each action, specify deliverables, responsible parties (e.g., security team, IT operations, compliance officer), and due dates. Track progress in a remediation log integrated with your risk register.
Step 7: Documentation and Policy Integration
Write up the entire assessment—including scope, data flows, identified threats, existing controls, risk ratings, and mitigation plans. HIPAA requires documentation but does not prescribe a format; however, regulators and auditors expect to see clear evidence that an assessment occurred. Integrate findings into existing policies: update incident response procedures, vendor selection criteria, data retention schedules, and training programs. The proposed Security Rule will require written documentation of all policies, procedures, plans, and analyses; using a DPIA‑style template helps maintain consistency.
Konfirmity’s managed service uses a centralized portal where clients can store risk assessments, associated evidence, and policy documents. We align these documents with SOC 2 and ISO 27001 control mappings so that one assessment supports multiple frameworks.
Step 8: Review, Audit, and Continuous Monitoring
Risk analysis should not be a one‑time event. OCR guidance emphasises that the process must be ongoing. Schedule periodic reviews—at least annually, as proposed in the NPRM—and whenever significant changes occur (system upgrades, new vendors, mergers). Continuous monitoring should include:
- Automated alerts for configuration drift or unusual access patterns.
- Regular review of audit logs and anomaly detection using security information and event management (SIEM) tools.
- Periodic access recertifications and privilege reviews.
- Vendor security assessments and updates to business associate agreements.
By integrating these activities into day‑to‑day operations, you avoid the scramble of periodic “compliance sprints.” Konfirmity’s approach reduces the internal effort required for audit readiness by approximately 75 percent, based on our experience with 6,000+ audits—our teams maintain control evidence year‑round so clients can focus on their core missions.
Example Scenarios and Use Cases
To illustrate how the HIPAA DPIA Guide works in practice, consider the following examples. These anonymised scenarios derive from Konfirmity’s engagements but reflect common patterns across the health‑care sector.
Example 1: Small Clinic Adopting a Cloud‑Based EHR
Scope: A clinic with 12 staff members and roughly 15,000 active patients wants to move from paper charts to a cloud‑hosted EHR. The project involves scanning existing records, implementing a patient portal, and connecting to a billing system.
Assessment:
- Data inventory: Patient names, contact details, medical histories, lab results, billing data.
- Data flows: Records scanned and uploaded to the cloud; portal allows patients to view results; billing data transmitted to an external revenue‑cycle vendor.
- Risks identified: Data in transit between scanning centre and cloud; misconfigured access controls; reliance on a third‑party for hosting; insufficient staff training.
- Controls: Use encrypted transport (TLS) for all uploads; enforce MFA for staff portal access; restrict admin privileges; sign business associate agreements with cloud provider and billing vendor; configure automatic backups.
Outcome: By applying DPIA‑style documentation, the clinic created a clear data map, updated access policies, and scheduled annual risk reviews. During go‑live, the vendor’s default configurations lacked encryption at rest, which the clinic corrected before uploading sensitive data. The clinic completed its first third‑party audit three months after implementation, with zero findings.
Example 2: Telehealth Provider Onboarding Remote Consultations
Scope: A telehealth startup offers video consultations for behavioural health. The platform integrates with scheduling, payment processing, and a cloud‑based EHR.
Assessment:
- Data inventory: Video and audio sessions (not stored), chat transcripts, appointment details, payment information, mental‑health notes.
- Data flows: Patients access via web or mobile; sessions traverse video‑conferencing infrastructure; recordings are not retained; transcripts stored in EHR; payment processor handles billing.
- Risks identified: Eavesdropping on video streams; insecure APIs between modules; potential misrouting of mental‑health notes; remote access by clinicians from personal devices.
- Controls: Use end‑to‑end encrypted video; implement secure API gateways; ensure role‑based access to transcripts; mandate device hardening and MFA for clinicians; document and test incident response for telehealth outages.
Outcome: The DPIA‑style process prompted the provider to redesign its architecture: transcripts were initially stored in a general chat database but were segregated into the EHR after risk identification. The provider added network segmentation and vulnerability scanning; these changes also supported its SOC 2 Type II audit, completed after five months with Konfirmity’s assistance.
Example 3: Large Hospital Integrating Third‑Party Labs and Imaging Vendors
Scope: A regional hospital connects its EHR to several external labs and imaging centres via HL7 interfaces. Patient data flows automatically to third‑party systems and back to clinicians.
Assessment:
- Data inventory: Orders, diagnostic codes, results, images, patient demographics, insurance details.
- Data flows: EHR generates orders; HL7 messages sent to labs; results returned; images transferred via picture archiving and communication systems (PACS).
- Risks identified: Unencrypted HL7 traffic; insufficient vendor authentication; inconsistent audit logging; third‑party systems outside the hospital’s network perimeter.
- Controls: Implement secure messaging (e.g., MLLP over TLS); enforce mutual TLS certificates; establish audit log forwarding from vendors to hospital SIEM; require vendors to certify compliance annually and permit audits; include incident notification clauses in contracts.
Outcome: The hospital’s DPIA revealed that one imaging vendor’s interface transmitted data over an unsecured channel, which was remedied. The hospital also formalised vendor monitoring and added a quarterly compliance review. During a later OCR investigation, the organisation provided its DPIA documentation to demonstrate due diligence, resulting in no penalties.
Sample Templates and Checklists
Busy teams need practical artefacts. Below are abbreviated templates that can serve as starting points; adjust fields as necessary. Keep entries concise—tables should list data assets and risks rather than long descriptions.
DPIA / HIPAA‑Ready Risk Assessment Template
Pre‑Implementation Checklist
- Have all data flows been documented?
- Does the project involve new technology or sensitive processing that could impact privacy?
- Are third‑party vendors involved, and do they have current business associate agreements?
- Does the change modify retention periods or cross‑border data transfers?
- Has a DPIA‑style risk assessment been performed and documented?
Controls and Safeguards Checklist
Administrative
- Access control policies defined and communicated.
- Workforce training on HIPAA and privacy obligations.
- Security incident response plan tested and updated.
- Business associate agreements reviewed annually.
Technical
- Data encryption at rest and in transit.
- MFA enforced for remote and privileged access.
- Vulnerability scanning at least semi‑annually; penetration testing annually.
- Continuous monitoring and logging; SIEM configured.
Physical
- Secure disposal procedures for paper and electronic media.
- Facility access controls and visitor management.
- Environmental controls for data centres (power, fire suppression).
Review and Audit Schedule Template
These templates help structure assessments and provide evidence for auditors. For larger organisations, tooling can automate data collection and risk scoring, but the underlying disciplines remain the same.
Aligning with HIPAA Compliance and Regulatory Requirements
The HIPAA Security Rule provides the legal basis for risk analysis and sets minimum standards for administrative, technical, and physical safeguards. A DPIA‑style approach does not replace HIPAA’s Security Risk Assessment (SRA); rather, it enhances it. By expanding the scope to consider data minimisation, purpose limitation, and broader privacy impacts, organisations can reduce the likelihood of violations and strengthen trust with patients and partners.
Regulators’ signals are clear. The NPRM would mandate written documentation for all policies, procedures, and analyses and require development of a technology asset inventory and network map, updated at least annually. It would remove the distinction between “required” and “addressable” controls, meaning that encryption, MFA, vulnerability scanning, penetration testing, and disaster‑recovery planning could soon become explicit requirements. OCR’s current enforcement initiative already focuses on the risk‑analysis provision. A thorough, documented DPIA helps demonstrate compliance with these evolving standards.
Cross‑framework alignment offers further efficiencies. Many of the controls needed for HIPAA also map to SOC 2 Trust Services Criteria and ISO 27001 Annex A controls. For example, encryption, access control, incident response, and vendor management appear across frameworks. Konfirmity’s program design leverages this overlap—our human‑led, managed service implements controls once and collects evidence continuously, reducing audit effort across HIPAA, SOC 2, and GDPR obligations. Typical SOC 2 readiness takes 4–5 months with Konfirmity versus 9–12 months when self‑managed, and clients save hundreds of internal hours by outsourcing evidence collection and control operation.
Common Challenges and Ways to Overcome Them
Despite the benefits, organisations often struggle with resource constraints, rapid technological change, and cultural resistance. Here are common challenges and practical strategies:
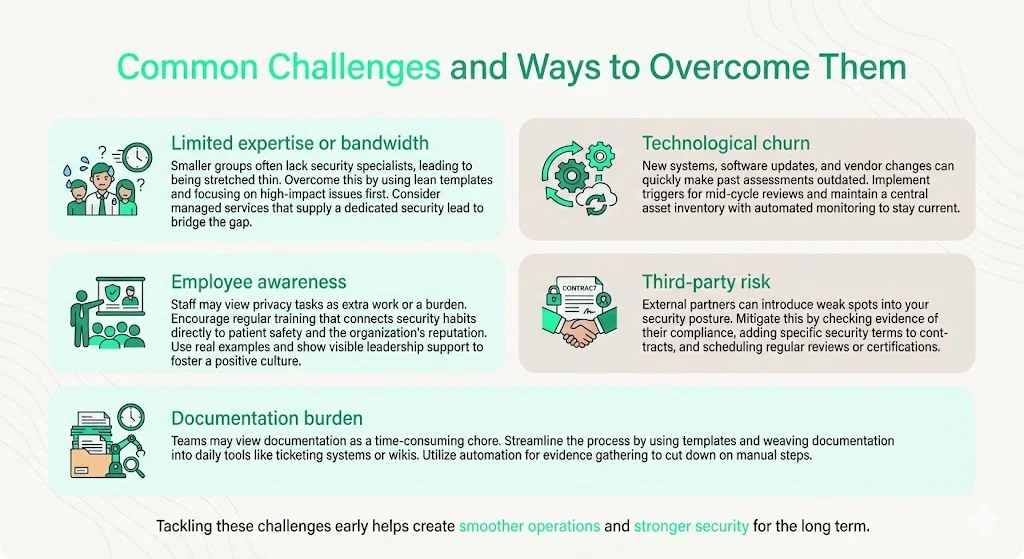
- Limited expertise or bandwidth: Small clinics and startups may lack dedicated security staff. Use lean templates like those provided in this guide and prioritise high‑impact risks first. Consider partnering with a managed compliance service; Konfirmity’s team operates the program and provides a dedicated CISO for strategic guidance.
- Technological churn: New systems, mergers, and software updates can invalidate previous assessments. Establish triggers for conducting interim reviews—e.g., after major system changes or vendor onboarding. Maintain a central asset inventory and automate monitoring where possible.
- Employee awareness: Staff may view privacy and security tasks as obstacles. Provide regular training that ties security actions to patient safety and organisational reputation. Reinforce policies with practical examples and leadership engagement.
- Third‑party risk: Vendors can be the weakest link. Perform due diligence before engagement: request evidence of HIPAA compliance, SOC 2 reports, or ISO 27001 certification. Include security clauses in contracts (e.g., requirement to notify within 24 hours of access changes) and schedule periodic audits or certifications.
- Documentation burden: Teams may view documentation as a distraction. Use templates and integrate documentation into existing workflows (ticketing systems, wikis). Tools can automate evidence collection (e.g., pulling system logs, configuration snapshots) to reduce manual effort.
By addressing these challenges proactively, health‑care organisations can transform compliance from a reactive exercise into a driver of operational excellence.
Conclusion
Protecting patient data is more than a legal requirement; it is a moral and business imperative. The HIPAA DPIA Guide synthesises privacy‑impact thinking with HIPAA’s risk‑analysis mandate, providing a framework for assessing and mitigating risks across the data lifecycle. With breaches reaching unprecedented scale and regulators proposing sweeping changes, organisations that build durable security programs now will be better positioned to adapt. By adopting a structured assessment process, documenting data flows and controls, prioritising remediation, and committing to continuous monitoring, health‑care companies can meet current obligations and prepare for the future.
Konfirmity’s human‑led, managed service demonstrates that achieving and maintaining compliance need not overwhelm internal teams. We start with security and arrive at compliance, operating the program every day so that clients can focus on patient care. Security that only looks good on paper is a liability; security that is embedded into daily operations and supported by continuous evidence is an asset.
Frequently Asked Questions
1. Is a DPIA mandatory under HIPAA?
No. HIPAA requires a risk analysis under the Security Rule, but it does not explicitly require a DPIA. However, applying DPIA principles can help organisations meet HIPAA obligations and align with other privacy regulations.
2. When should a health‑care organisation conduct a DPIA‑style assessment?
Perform one when implementing new patient‑data systems, migrating to the cloud, adding vendors, conducting large‑scale analytics, or making significant process changes. These scenarios mirror the triggers for DPIA under GDPR and correspond to high‑risk activities.
3. How often should the assessment be updated?
At least annually and whenever there is a major change in technology, process, data flows, or business operations. The NPRM proposes requiring annual risk assessments and audits.
4. Can small clinics use this approach?
Yes. Even small practices benefit from mapping data flows and documenting risks. They can use simplified templates and focus on key areas such as encryption, access control, and vendor management.
5. Does a DPIA replace the HIPAA Security Risk Assessment?
No. The risk assessment remains mandatory under HIPAA. A DPIA should be viewed as an enhanced, privacy‑centric layer that complements and extends the SRA.
6. What if we use third‑party vendors or cloud providers?
Include them in your scope. Map data flows to and from vendors, evaluate their controls, ensure business associate agreements include specific security obligations, and require periodic certifications or audits.





.svg)






.svg)
.svg)