Modern procurement teams are no longer satisfied with generic compliance badges. They want to know exactly where their data is stored, how it moves across borders and whether the vendor’s controls operate effectively. Questions about SOC 2 Data Residency now appear early in enterprise questionnaires because security leaders know that location influences both legal obligations and operational risk. If a vendor does not map data flows to jurisdictions or is unable to explain where logs and backups reside, deals stall and trust erodes. This article outlines why SOC 2 reports intersect with data sovereignty, regional laws and cloud infrastructure choices and provides guidance for vendors and buyers who must match security controls to geographic requirements.
Understanding SOC 2 Data Residency
SOC 2 is a framework developed by the American Institute of Certified Public Accountants (AICPA) to evaluate the design and operating effectiveness of controls related to Security, Availability, Processing Integrity, Confidentiality and Privacy. A SOC 2 Type I report assesses whether controls are suitably designed at a point in time, while a Type II report tests those controls over an observation period—often six to twelve months. The framework is intentionally flexible; it does not mandate where data must reside. Instead, auditors look for evidence that controls work consistently across all environments.
Enterprise buyers often conflate SOC 2 with data localization laws. SOC 2 Data Residency means matching the trust services criteria with commitments about where data is kept. The Security criteria focus on access controls, authentication, encryption and incident response. The Confidentiality criteria require that information designated as confidential is protected through segmentation and encryption. The Privacy criteria ensure that personal data is collected, used and retained according to commitments and laws. Data location influences each criterion because storing data in particular jurisdictions can reduce exposure to weak laws and unauthorized access. However, SOC 2 does not by itself require data to remain in a single country; those obligations come from privacy laws, contractual commitments and sector‑specific regulations.
To understand why location matters, it helps to distinguish three related terms. Data sovereignty means that the laws of the data subject’s home country apply regardless of where the information resides. Data residency refers to the physical location of systems that host and process data and subjects them to the legal frameworks of that jurisdiction. Data localization is the most restrictive type; it requires certain data to remain within a country’s borders for reasons such as national security or public interest.
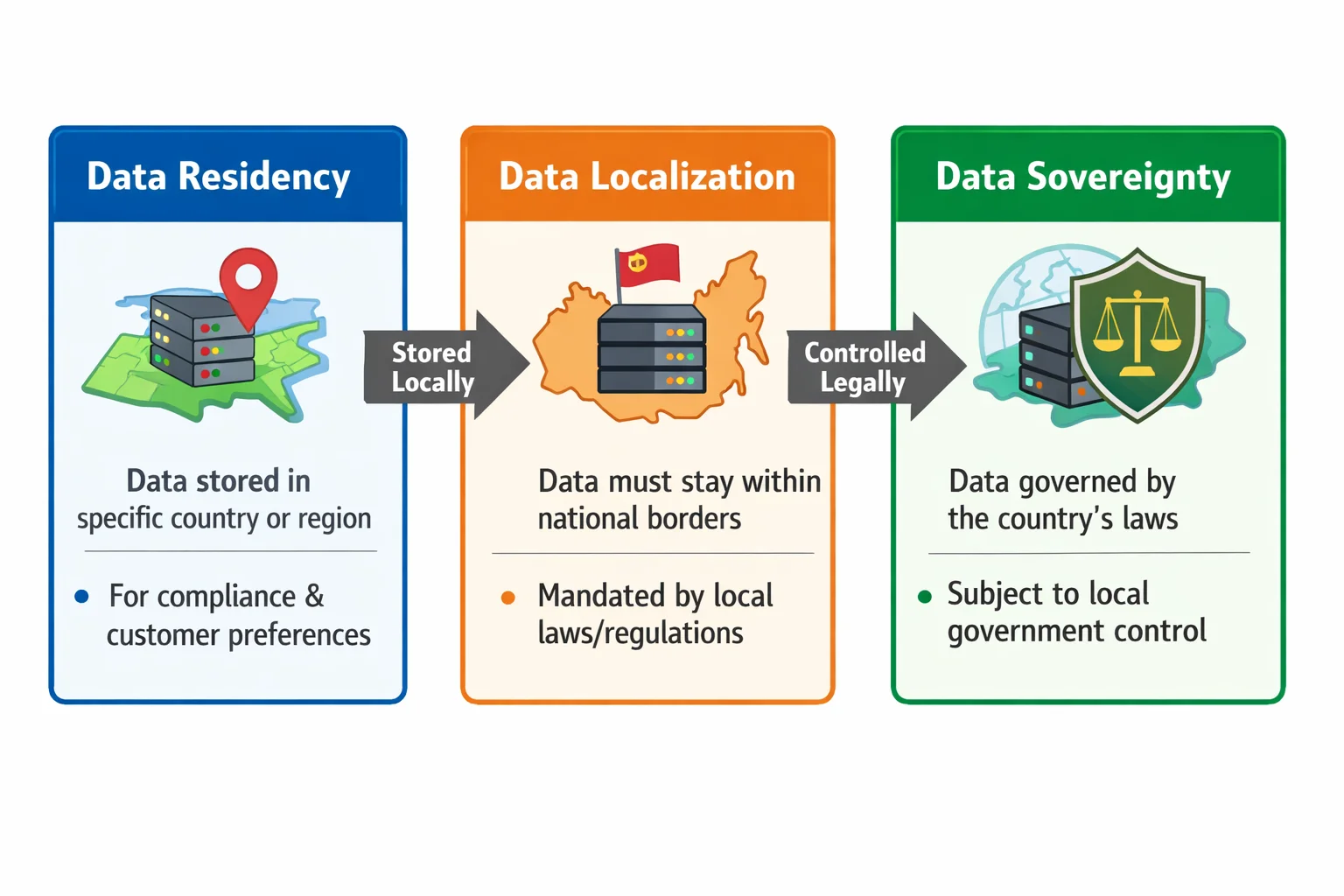
SOC 2 addresses how data is protected, but it is silent about where the protection must occur. For example, HIPAA requires U.S. healthcare providers to implement administrative, physical and technical safeguards for electronic protected health information (ePHI). The HIPAA Times article explains that HIPAA does not impose a U.S. data localization mandate but it does require risk analysis, access controls and audit logging regardless of location. Similarly, the EU’s General Data Protection Regulation (GDPR) requires organizations to use approved transfer mechanisms—such as Standard Contractual Clauses or Binding Corporate Rules—when data leaves the European Economic Area. These frameworks influence SOC 2 audits because auditors will assess whether controls support legal obligations.
In practical terms, SOC 2 Data Residency means showing that security controls operate consistently across all regions in scope and that data flows match contractual commitments. If a company promises its customers that data will remain in the EU, auditors will expect evidence that backups, logs and disaster recovery replicas stay in EU regions, that encryption secrets reside within EU hardware security modules and that subprocessors do not replicate data elsewhere. Vendors should consider data residency as a layer over SOC 2 rather than something contained within the standard itself. By clarifying this distinction, organizations can design controls that satisfy both their auditors and their customers’ legal teams.
Why SOC 2 Data Residency Has Become a Buying Concern
Buyers ask about SOC 2 Data Residency because they see clear links between trust, data location and business outcomes. There are several drivers behind this trend:
Long sales cycles and unclear data flow information. Enterprise procurement teams review data flow diagrams to ensure that data remains in permitted jurisdictions. If a vendor is unable to produce a current map of where customer data is collected, processed, backed up and archived, negotiations drag on. Vendors that provide transparent documentation accelerate sales cycles. In Konfirmity’s experience supporting more than 6,000 audits, readiness timelines shrink from nine to twelve months to about four to five months when vendors map data flows early and maintain evidence.
Regulatory and national security pressures. Governments have introduced laws that restrict cross‑border transfers. A U.S. Department of Justice rule issued in April 2024 restricts data transactions with six “countries of concern”—China, Cuba, Iran, North Korea, Russia and Venezuela—and requires due diligence, record retention and annual audits. Penalties include fines exceeding USD 350,000 per violation and potential criminal liability. Healthcare providers must comply with HIPAA safeguards irrespective of data location. The GDPR invalidated the EU‑US Privacy Shield and requires organizations to rely on Standard Contractual Clauses or other mechanisms to transfer personal data. India’s DPDP bill categorizes healthcare information as sensitive and may require local mirroring. Because of these restrictions, procurement teams want assurance that vendors know where data resides and how it crosses borders.
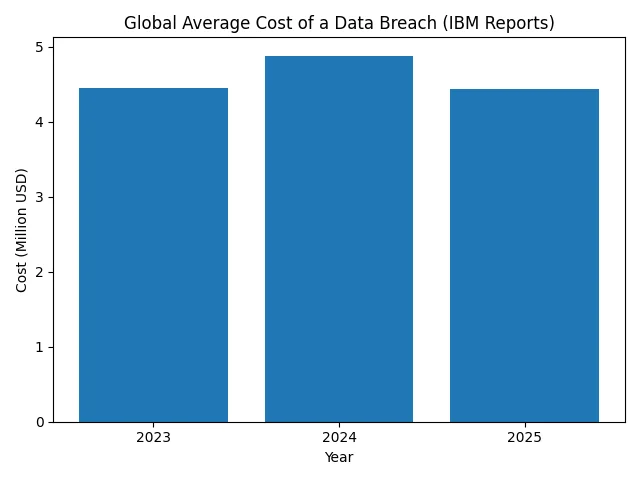
Escalating breach costs tied to location. IBM’s 2024 report shows that the global average cost of a breach rose to about USD 4.88 million, driven by business disruption and remediation. The following year the cost fell slightly, but U.S. breaches averaged more than USD 10 million. Buyers therefore consider whether vendors operate in jurisdictions with strong privacy regimes and have the resources to respond quickly.
Sector-specific obligations. Regulated industries impose stricter location requirements; for instance, healthcare providers must secure ePHI and maintain audit trails, while critical infrastructure may require sovereign clouds. Vendors that are unable to meet such restrictions may be excluded from contracts.
Customer trust and reputational impact. Without clear answers about data location, buyers question whether vendors take privacy and security seriously. A vague or inconsistent response about where logs, backups or support data reside undermines confidence. Conversely, precise answers build trust and can differentiate vendors. This is why many procurement teams view SOC 2 Data Residency as a threshold requirement.
Another factor behind the focus on location is the complexity of cross‑border laws. Each jurisdiction has its own rules about retention, transfer mechanisms and government access. Multinational vendors must show compliance across regions or risk stalled or lost deals.
Data Sovereignty and Mapping Data Flows
One common misunderstanding is that a SOC 2 report proves that data never leaves a particular country. In reality, SOC 2 evaluates control design and effectiveness; it does not guarantee geographic boundaries. To manage expectations, organizations must clarify where SOC 2 ends and sovereign rules begin. The Scale Computing paper explains that data sovereignty applies regardless of physical location. This means that even if data is stored in the United States, the laws of the data subject’s home country may still apply. Data localization rules may further restrict cross‑border transfers.
To ensure compliance with privacy frameworks and contractual commitments, vendors should map data flows in detail. A detailed mapping process includes:
- Identifying creation and storage points. Determine where customer data is generated, processed, stored, backed up and archived. For each location, record the cloud region or data center and the applicable jurisdiction. Document whether data resides in primary production, staging, analytics or logging systems.
- Handling cross‑border restrictions. When data crosses borders, ensure that there are legal mechanisms for transfer. For EU data, use Standard Contractual Clauses or Binding Corporate Rules. For U.S. data, ensure compliance with the DOJ’s rule prohibiting transactions with countries of concern. For sensitive data under India’s DPDP bill, maintain local copies and specify transfer rules.
- Managing subprocessors. Subprocessors such as cloud providers, analytics platforms and support tools may store or process data in different jurisdictions. Maintain an up‑to‑date list of subprocessors, their locations and the data they handle. Ensure that subprocessor agreements include equivalent controls and restrict onward transfers. Under HIPAA, business associate agreements require subcontractors to follow the same protections. SOC 2 auditors and buyers will want evidence of these agreements.
- Documenting for audits and contracts. Use diagrams and tables to visualize data flows and annotate them with regions. For each data type and jurisdiction, record the governing law, transfer mechanism and retention period. Keep this documentation current and share it with customers as part of the due diligence package. At Konfirmity, we find that clients who maintain detailed data maps reduce audit efforts and avoid last-minute surprises during procurement.
Third‑party vendors can undermine data residency commitments when they replicate logs outside the agreed region. Effective vendor management requires vetting each subprocessor’s regional capabilities, reviewing their audit reports and restricting the data sent to them. Because auditors and customers ask for subprocessor lists, keeping accurate records and reviewing them regularly is essential.
Mapping data flows not only satisfies auditors but also informs security design. By knowing where data resides, teams can implement controls adapted to each jurisdiction’s requirements and limit exposure to conflicting laws.
Cloud Infrastructure and Regional Controls
Most organizations rely on hyperscalers such as Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP). These providers offer regional options to support data residency requirements. For example, the AWS European Sovereign Cloud stores both data and metadata exclusively within the EU and ensures that operations and support are handled by EU residents. It operates under independent European governance, uses separate infrastructure, and applies strict access controls. Such offerings help organizations meet sovereignty requirements, but they also emphasize the shared responsibility model: cloud providers secure the underlying infrastructure, while customers must configure identity, encryption and monitoring correctly.
When designing multi‑region architectures, vendors must balance performance with compliance. Deploying applications in multiple regions can improve latency and resilience, but it may also replicate data across jurisdictions. To maintain SOC 2 Data Residency, vendors can:
they should rely on region‑specific storage services, keep encryption secrets in the same region as the data and segregate logging and monitoring systems to avoid unintended cross‑border transfers. Some providers offer guardrails—such as AWS Control Tower—that enforce region restrictions and prevent deployments outside approved zones.
Teams should also consider how failover, caching and content delivery networks replicate data. Read replicas and caches can store copies outside the primary region. Vendors can disable cross‑region replicas and configure content delivery networks to use approved regions to maintain residency commitments.
Buyers will expect cloud providers to provide transparency about data location, metadata residency and potential access by foreign authorities. The U.S. CLOUD Act allows certain law enforcement agencies to request data stored outside the U.S., which is why some customers insist on sovereign clouds. Vendors should work with providers that support encryption at rest and in transit, customer‑managed cryptographic secrets, hardware security modules and external secret management options. They should also ensure that providers are certified against relevant standards such as SOC 2 Type II, ISO 27001, ISO 27017 and ISO 27701.
Harmonizing Controls and Policies Across Standards
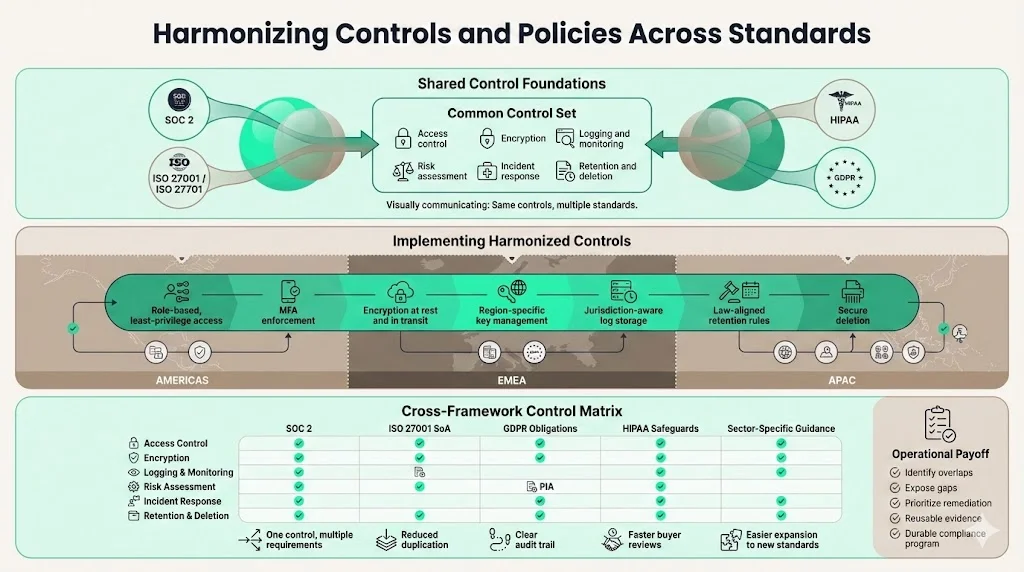
Compliance frameworks such as SOC 2, ISO 27001, ISO 27701, HIPAA and GDPR share common themes: access controls, encryption, logging, risk assessment, incident response, retention and deletion. The challenge is to harmonize these controls across regions so that SOC 2 Data Residency commitments are met without creating contradictory policies. Important considerations include:
To meet these commitments, organizations should implement role‑based and least‑privilege access with multi‑factor authentication, encrypt data at rest and in transit using region‑specific secret management, store logs in permitted jurisdictions with appropriate retention periods, and define retention and secure deletion rules that conform to applicable laws. Continuous compliance monitoring and infrastructure‑as‑code templates help ensure consistency as new regions and services are added.
Linking each legal requirement to the corresponding SOC 2 control in a control matrix helps auditors and buyers understand how data residency obligations are addressed. This matrix should include references to ISO 27001’s Statement of Applicability, GDPR obligations (such as data minimization and lawful basis), HIPAA safeguards (administrative, physical and technical), and sector‑specific guidelines. Presenting controls in a unified framework demonstrates understanding of the interaction among different standards and ensures durable security.
A cross‑framework control matrix reduces duplication and exposes gaps. Mapping such connections helps prioritize remediation, shows auditors that one control satisfies multiple requirements and simplifies the addition of new standards.
Building and Maintaining Data Residency Policies
A clear policy is essential to operationalizing SOC 2 Data Residency. It should define which regions are supported, whether customers can choose a location, how data is transferred and retained, and who within the organization is responsible for decisions.
Data residency policies should link to retention policies, defining how long each data type is kept and where deletion occurs; for instance, backups may be kept for 30 days in the U.S. but 90 days in the EU due to local requirements. When a customer requests deletion, the policy should specify how data is purged across all copies. Collaboration between security, legal and engineering teams is essential to ensure that controls, contracts and product features meet regional commitments.
Policies should not be static documents. Laws change, and infrastructure changes over time. Vendors should review data residency policies at least annually and whenever there are significant regulatory updates, architectural changes or audit findings. For example, the DOJ’s Data Security Rule and India’s DPDP bill introduced new obligations in 2025. Regular reviews help prevent gaps and ensure that controls remain effective.
Preparing for SOC 2 Audits with Data Residency in Scope
When data location commitments are in scope, SOC 2 auditors will ask for specific evidence. They may request:
- Architectural diagrams showing which regions host production workloads, backups and logs.
- Infrastructure‑as‑code templates, cloud console screenshots and configuration files that demonstrate regional settings.
- Records of encryption secrets and secret management services, along with evidence that these secrets are located in the same region as the data.
- Records of encryption secrets and secret management services, along with evidence that these secrets are located in the same region as the data.
- Logs and monitoring outputs stored in permitted jurisdictions.
- Contracts with cloud providers and subprocessors, including data protection addenda and Standard Contractual Clauses.
- Evidence of cross‑border transfer mechanisms and any required approvals or risk assessments.
Auditors test controls over a six‑ to twelve‑month observation period. If data residency measures are added midway, they may not be covered. Konfirmity therefore suggests starting readiness work well before the observation begins. Our continuous monitoring and automated evidence collection reduce gaps; managed clients spend about 75 hours per year on audit tasks versus 550 to 600 hours in self‑managed projects. Automation across control points means evidence is always ready and timelines shrink to four to five months. If a customer requests a new region, document the risk assessment and mitigation. Transparency satisfies auditors and clients.
Pitfalls and Best Practices
Organizations often fall into common traps when addressing SOC 2 Data Residency. They may overstate control by claiming that data never leaves a country even when metadata or logs are replicated; neglect backups and monitoring data; or lose track of subprocessors as new tools are adopted. To avoid these mistakes, vendors should design systems for regional flexibility from day one using infrastructure as code, publish transparent documentation—such as data flow diagrams and subprocessor lists—to build trust, and monitor regulatory changes so that policies and controls remain current.
Keep an up‑to‑date subprocessor list and verify each vendor’s ability to meet region commitments. Use infrastructure‑as‑code templates to enforce region settings, encryption and logging. Pair technical safeguards with contractual clauses in data‑processing agreements specifying permitted regions and subprocessors. Cross‑team coordination ensures that commitments made to customers match actual practices and that any limitations are communicated clearly.
Continuous improvement and transparency underpin long‑term success across the organization.
Conclusion
Data location is now central to enterprise security reviews. SOC 2 Data Residency is more than a buzzword; it captures the intersection of compliance frameworks, privacy law and cloud architecture. Buyers demand evidence that vendors understand where data lives, how it flows across borders, and how controls operate in each jurisdiction. They also expect vendors to map region‑specific legal obligations to the SOC 2 trust services criteria. For vendors, a disciplined approach to location commitments becomes a competitive advantage. Clear documentation and strong controls allow teams to respond to procurement questionnaires quickly, avoid costly remediation after contract signing and focus engineering effort on product features instead of constant compliance firefighting. Organizations that design regional flexibility, document data flows, ensure policies comply with laws and continuously monitor controls earn trust, shorten sales cycles and reduce audit findings. Security that reads well on paper but fails under incident pressure is a liability. Build your program once, operate it every day and let compliance follow. Sustainable compliance requires daily discipline.
Frequently Asked Questions
1. Does SOC 2 require data to stay in one country?
No. SOC 2 is control‑based and does not mandate data location. It evaluates whether controls operate effectively across all environments. Location mandates come from privacy laws like GDPR and sector regulations like HIPAA.
2. How does data residency affect SOC 2 audits?
Auditors will examine where data is stored, processed and backed up, and whether controls are consistent across regions. They will review transfer mechanisms, encryption and access controls. If data spans multiple regions, they will require legal transfer mechanisms and evidence that backups and logs stay within permitted jurisdictions.
3. What data locations matter most to enterprise customers?
Customers care about primary production data, backups, logs, analytics stores and support access. They expect assurance that all copies of data—including metadata—stay within approved regions. Sovereign cloud offerings like AWS’s EU cloud store both data and metadata within the EU.
4. How should cloud providers handle regional data laws?
Providers should offer region‑specific services with complete data and metadata residency, operational autonomy and independent governance. They must implement encryption, customer‑managed cryptographic secrets and guardrails that prevent cross‑region deployment. Providers should also be transparent about potential access under laws like the U.S. CLOUD Act.
5. How often should data residency policies be reviewed?
Policies should be reviewed at least annually and whenever there are significant regulatory changes, infrastructure updates or audit findings. New rules like the DOJ’s Data Security Rule or India’s DPDP bill introduce new obligations. Regular reviews ensure that controls remain consistent with current requirements.





.svg)





.svg)
.svg)