Enterprise procurement has changed. Ten years ago, a handshake and a basic nondisclosure agreement might have been enough to close a deal. Today, with the average cost of a data breach hitting an all-time high of $4.88 million globally, the door stays shut until you prove your security posture.
For companies moving data across borders, the scrutiny is even tighter. Your clients do not just care that their data is safe inside your firewall; they need proof that it remains secure when it travels between jurisdictions. This is where SOC 2 International Transfers become a defining factor in your sales cycle.
When a Global 2000 buyer assesses your risk profile, they are not looking for vague promises. They demand rigorous, third-party validation that your controls hold up against real-world threats, regardless of where the data resides. If you cannot demonstrate visibility and control over cross-border flows, you become a liability.
At Konfirmity, we have guided companies through over 6,000 audits. We see the same pattern repeatedly: teams build excellent products but lose momentum in procurement because they treat compliance as a paperwork exercise rather than an operational reality. This guide explains how to operationalize your international data controls so you can pass audits, satisfy enterprise buyers, and close deals faster.
What SOC 2 Actually Means for You

Service Organization Control 2 (SOC 2) is not a certification you hang on the wall and forget. It is an attestation report—a detailed audit of your internal control environment. Unlike ISO 27001, which focuses on your management system's structure, SOC 2 looks at whether your controls effectively protect client data over time.
For a Type II report, an independent auditor observes your systems for a specific period (typically 6 to 12 months) to verify that the controls you claim to have are actually running. Did you revoke access for that terminated engineer within 24 hours? Did you encrypt that batch of data before sending it to a server in Frankfurt? The audit answers these questions with evidence, not intent.
Trust Services Criteria and Global Data
The American Institute of Certified Public Accountants (AICPA) defines five Trust Services Criteria (TSC) for SOC 2. While Security is mandatory, the others are optional based on your specific operations. However, when dealing with SOC 2 International Transfers, specific criteria become non-negotiable for enterprise buyers.
- Security (Common Criteria): The foundation. It asks if your system is protected against unauthorized access. For international data, this includes securing the transmission channels crossing national boundaries.
- Availability: Can the client access their data when they need it?
- Processing Integrity: Does your system perform its function without error or manipulation?
- Confidentiality: Is data designated as confidential protected effectively? This is critical for B2B companies handling trade secrets or intellectual property across borders.
- Privacy: This criterion addresses how you collect, use, retain, and dispose of personal information.
If your platform processes data from EU citizens or handles health records across regions, the Privacy and Confidentiality criteria are vital. They serve as the bridge between US-centric frameworks and international regulations. While SOC 2 is not a law, a report that covers Privacy provides the assurance auditors and legal teams need to see that you respect the principles behind laws like GDPR.
The Reality of Cross-Border Data
The Cross-Border Data Environment
"Cross-border transfer" sounds abstract, but in practice, it happens thousands of times a day in a standard SaaS environment. A user in London uploads a file; it gets processed by a server in Virginia and backed up to a bucket in Singapore.
For your enterprise clients, this movement represents risk. With 75% of the world's population now covered by modern privacy regulations, different countries have strictly different rules about who can access that data and how it must be protected. If you move data from a high-protection jurisdiction (like Germany) to one with looser regulations without adequate safeguards, you expose your client to legal and reputational damage.
Managing SOC 2 International Transfers means you must map these flows explicitly. You cannot protect what you do not track. Many engineering teams we work with are surprised during their initial readiness assessment when they realize how many third-party sub-processors touch their data in regions they hadn't considered.
How SOC 2 Intersects with Global Privacy Laws
A common misconception is that SOC 2 and GDPR are entirely separate tracks. In reality, they reinforce each other.
The General Data Protection Regulation (GDPR) restricts transferring personal data outside the European Economic Area (EEA) unless specific safeguards are in place. While SOC 2 does not grant legal "adequacy" like a decision from the European Commission, a clean SOC 2 Type II report covering the Privacy criteria serves as powerful evidence that you are upholding your side of the contract.
When you sign Standard Contractual Clauses (SCCs) to legalize a transfer, you commit to specific technical and organizational measures. Your SOC 2 report is the proof that you are honoring those commitments. It validates that the encryption, access controls, and incident response plans you promised in the contract are real and functional.
Core Requirements for International Transfers
To support SOC 2 International Transfers effectively, you need to implement specific operational controls. These are not just for the auditor; they are for the security of your business.
1) Information Security and Confidentiality Controls
Data in transit is data at risk. When information leaves your controlled environment to cross a network boundary, it must be shielded.
- Encryption Protocols: You must enforce strong encryption for data in transit. We typically verify the use of TLS 1.2 or 1.3 for all external traffic. Auditors will ask for configuration evidence showing that weaker ciphers are disabled.
- Cryptographic Key Management: Encrypting data is useless if the keys are managed poorly. Your controls must demonstrate that encryption keys are generated, stored, and rotated securely, with access limited to the absolute minimum number of staff.
- Data Classification: You must tag data based on sensitivity. Confidential client data should be treated differently than public marketing assets. Your system should automatically apply stricter transfer protocols to data tagged as "Restricted" or "Confidential."
Use Case: The "Hidden" Transfer We often see developers hard-code API calls to a third-party logging service. If that logging service hosts its data in a different country, you are initiating an international transfer every time an error occurs. A proper SOC 2 control framework includes code reviews and static analysis to catch these unauthorized data egress points before they reach production.
2) Vendor and Third-Party Risk Management
Your compliance posture inherits the weaknesses of your vendors. According to the Verizon 2024 Data Breach Investigations Report, 15% of breaches involved a third party, and these incidents often carry a higher price tag than average. If you use a cloud provider or a customer support tool that processes data globally, their risk becomes your risk.
Enterprise requirements for SOC 2 International Transfers mandate a rigorous vendor management program. You cannot simply sign up for a tool; you must vet it.
- Assessments: Before onboarding, review the vendor's own SOC 2 report or ISO 27001 certificate. Do they cover the regions where they store your data?
- Data Processing Agreements (DPAs): Ensure you have a signed DPA with every sub-processor. This legal document is a standard control auditors look for.
- Annual Reviews: Vendor management is continuous. You must re-evaluate critical vendors annually to ensure their security posture has not degraded.
3) Privacy Policies and Notices
Transparency is a control. Your privacy policy must accurately reflect your actual data flows. If your policy states data stays in the US, but your backup logs show replication to Ireland, you have a control failure.
Your privacy notice should explicitly state:
- The categories of data you collect.
- The purpose of processing.
- The specific cross-border transfers that occur.
- The legal mechanisms (like SCCs) used to protect that data.
Auditors reviewing the Privacy criteria will compare your public statements against your backend configurations. Discrepancies here are among the fastest ways to fail an audit.
Integrating SOC 2 With Global Privacy Standards
Aligning With GDPR, CCPA, and Other Regimes
Smart organizations do not build separate compliance programs for every acronym. They build a single, durable security core that maps to multiple frameworks.
The controls you implement for SOC 2 International Transfers—such as data minimization, encryption, and access governance—are the same operational muscles required for GDPR, CCPA (California), and HIPAA.
For example, the GDPR principle of "Integrity and Confidentiality" maps directly to the SOC 2 Confidentiality criteria. The CCPA requirement to know where consumer data resides maps to the SOC 2 processing integrity and availability controls.
By focusing on the outcome—secure, controlled data movement—you satisfy the underlying requirement of almost every major privacy law. This is the "outcome-as-a-service" philosophy we practice at Konfirmity. Instead of chasing checklists, we implement the security control once and map it to whatever framework your client asks for.
Practical Compliance Steps for International Transfers
If you are preparing for an audit that includes international data flows, follow this execution path:
- Data Mapping: Create a definitive inventory of all data ingress and egress points. Which fields contain PII? Where do they go? Which vendors touch them?
- Transfer Mechanisms: Document the legal basis for every flow. If moving data to the UK from the EU, rely on the adequacy decision. If moving to the US, ensure the Data Privacy Framework or SCCs are active.
- Risk Assessment: Conduct a specific risk assessment for international transfers. What happens if the sub-processor in Region X fails? What is the impact of a government access request in Region Y?
- Evidence Collection: Configure your systems to generate logs that prove these transfers are encrypted and authorized.
Templates You Can Use
To move from theory to practice, here are structural templates based on what we implement for clients. These are starting points to be adapted by your legal and security teams.
International Data Transfer Policy Template
Use this to establish internal rules for engineering and product teams.
Policy Title: Cross-Border Data Transfer and Security Owner: CISO / Head of Compliance
1. Purpose This policy defines the security and legal requirements for transferring Client Data across national borders to ensure compliance with SOC 2 Confidentiality/Privacy criteria and applicable laws (GDPR, CCPA).
2. Scope Applies to all production systems, employees, and third-party vendors handling Client PII or Confidential Information.
3. General Requirements
- Authorization: No new cross-border data flow may be established without prior approval from the Security Committee.
- Encryption: All international transfers must occur over TLS 1.2+ channels.
- Minimization: Only the minimum amount of data required for the specific function may be transferred.
4. Transfer Mechanisms
- Transfers to Adequate Jurisdictions: Permitted with standard logging.
- Transfers to Third Countries: Requires execution of Standard Contractual Clauses (SCCs) and a Transfer Impact Assessment (TIA).
5. Monitoring DevOps shall maintain logs of all egress traffic volume by destination country. Anomalies (e.g., spikes in traffic to unsanctioned regions) must trigger a high-severity alert.
Cross-Border Risk Assessment Template
Use this to document your risk analysis for auditors.
Third-Party Transfer Checklist
Run this before signing any new vendor.
- Does the vendor store or process data outside our primary region?
- If yes, list all countries involved.
- Does the vendor hold a valid SOC 2 Type II or ISO 27001 certificate covering those regions?
- Have we signed a Data Processing Agreement (DPA) with international transfer clauses?
- Does the vendor support data residency (pinning data to a specific region)?
- Review the vendor's specialized sub-processors. Do they chain transfers further?
Privacy Notice Snippet for Global Transfers
Insert this into your public-facing privacy policy to satisfy the transparency requirement.
International Data Transfers: "To provide our Services, we may transfer your personal information to countries other than the one in which you live. We deploy the following safeguards to ensure your data remains protected:
- Adequacy Decisions: We rely on determinations by the European Commission where available.
- Standard Contractual Clauses: For transfers to countries without adequacy status, we implement SCCs to guarantee GDPR-equivalent protection.
- Security Measures: All transfers are protected by enterprise-grade encryption and strict access controls verified by our annual SOC 2 Type II audit."
Common Pitfalls and How to Avoid Them
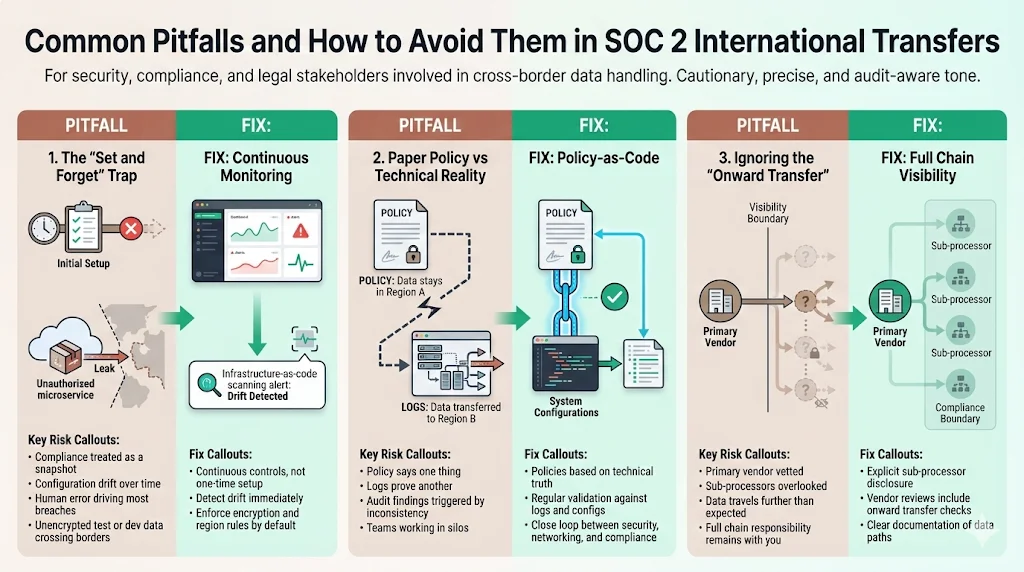
Even with good intentions, we see organizations stumble. Here are the specific failure modes related to SOC 2 International Transfers that can derail an audit or a deal.
1) The "Set and Forget" Trap
Compliance is not a snapshot; it is a film. A common error is setting up strict transfer controls during the implementation phase but failing to maintain them. The human element still accounts for 68% of breaches, meaning a single developer spinning up a new microservice that pipes unencrypted data to a test server in a different region can break your compliance posture. The Fix: Implement continuous monitoring. Use infrastructure-as-code scanning to detect configuration drift immediately.
2) Paper Policy vs. Technical Reality
Auditors hate surprises. If your policy says "We never transfer data to Country X," but a firewall log shows traffic going there, you have a finding. This often happens because policy writers do not talk to network engineers. The Fix: Your policy must be a living document derived from technical ground truth, not aspirational templates.
3) Ignoring the "Onward Transfer"
You vetted your primary vendor, but did you vet their vendor? If your cloud provider uses a sub-processor for analytics, your data might be traveling further than you think. Under SOC 2 and GDPR, you are responsible for the entire chain. The Fix: rigorous vendor reviews that specifically ask for sub-processor maps.
Conclusion
Managing SOC 2 International Transfers is about visibility and discipline. It is the difference between hoping your data is safe and knowing it is safe.
For enterprise buyers, this distinction is everything. They are under immense pressure to manage their own supply chain risk. When you present a clean SOC 2 report that explicitly covers privacy and international transfers, you are solving a problem for them. You are removing friction from the procurement process.
At Konfirmity, we believe that you should not have to choose between building a great product and being compliant. We deliver a human-led, managed security service that embeds these controls directly into your stack. We handle the 64+ control points, the evidence collection, and the audit defense, so you can focus on shipping code.
Do not treat this as a checkbox. Build a security program that stands up to scrutiny. Your clients will notice the difference.
Frequently Asked Questions (FAQ)
Q1. Does SOC 2 require legal compliance with GDPR or other laws?
SOC 2 is an auditing framework, not a law. It does not enforce GDPR directly. However, the Privacy and Confidentiality criteria within SOC 2 force you to adopt controls—like data minimization and consent management—that support and evidence your legal compliance with laws like GDPR.
Q2. Can SOC 2 streamline international vendor assessments?
Absolutely. Instead of filling out hundreds of security questionnaires for every prospect, you can share your SOC 2 report. It serves as verified, third-party proof of your security posture, significantly reducing the time spent on vendor due diligence.
Q3. What’s the difference between SCCs and BCRs when moving data across borders?
Standard Contractual Clauses (SCCs) are pre-approved template terms used to legalize data transfers between two specific entities (e.g., you and a vendor). Binding Corporate Rules (BCRs) are internal rules adopted by multinational groups to allow data transfers between their own global offices. SCCs are more common for vendor relationships.
Q4. Should international transfers be in your SOC 2 audit scope?
If your service involves moving personal or confidential data across borders, you should absolutely include it in your scope. Excluding it might make the audit easier, but it renders the report less valuable to enterprise clients who specifically care about that risk.
Q5. How do enterprise clients evaluate international transfer risk?
They look for three things: a clear data flow diagram showing where data goes, documented risk assessments for those transfers, and technical evidence (like your SOC 2 report) proving that encryption and access controls are active and effective.





.svg)





.svg)
.svg)