Most enterprise buyers now demand proof that vendors can protect health information. Without operational security and continuous evidence, deals stall. The stakes are high: IBM’s 2025 report shows U.S. breaches average US$10.22 million and healthcare breaches US$7.42 million. The Office for Civil Rights issued ten enforcement actions in 2025. Third‑party processors—cloud services, billing platforms and analytics vendors—handle more PHI, yet outsourcing does not relieve covered entities of liability. When a vendor mishandles PHI, both sides may be accountable. This article explains HIPAA for data processors, translating regulations into working controls and drawing on 6,000+ audits and 25+ years of expertise at Konfirmity.
Why HIPAA for data processors matters in modern healthcare operations
HIPAA for data processors is critical because third‑party processors play an integral role in healthcare operations. Third‑party processors now play an integral role in healthcare operations. Providers rely on external vendors for patient scheduling, electronic health record (EHR) hosting, claims processing, analytics and telehealth. This shift lets hospitals and clinics focus on care, but it also introduces risk. When PHI flows through outside systems, it becomes vulnerable to misconfiguration, vendor negligence and cyberattacks. Many breaches trace back to third parties. A 2025 OCR resolution agreement with Comstar LLC shows how serious these events can be: a ransomware attack exposed the data of 585,621 individuals because the billing vendor failed to perform a thorough risk assessment. Penalties are only part of the fallout; breaches also drive regulatory scrutiny, slow enterprise deals and erode patient trust.
Healthcare companies also face complex procurement questionnaires. Enterprise clients increasingly require evidence of security controls, audit reports and signed business associate agreements (BAAs) before purchasing services. Without clear answers, sales cycles drag on. In Konfirmity’s experience, teams working alone spend 550–600 hours per year maintaining compliance artifacts and responding to due‑diligence requests. Our clients reduce this to around 75 hours by adopting a human‑led, managed program that embeds controls directly in their systems and continuously produces evidence. Meeting HIPAA obligations is therefore both a legal necessity and a competitive advantage.
Understanding HIPAA for data processors
The Health Insurance Portability and Accountability Act (HIPAA) sets national standards for protecting individually identifiable health information. HIPAA distinguishes between covered entities—health plans, healthcare providers and clearinghouses—and business associates, which are vendors that create, receive, maintain or transmit PHI on behalf of a covered entity. HHS defines a business associate as any organization, other than a workforce member, that performs functions such as claims processing, data analysis or billing. Once a vendor touches PHI—even if only to host, transmit or view it—it becomes a business associate and must comply with relevant portions of HIPAA.
Processors operate outside traditional hospital or clinic walls. Cloud infrastructure providers host EHRs, analytics vendors generate dashboards, revenue‑cycle platforms process claims and telehealth services handle live consultations. All of these roles involve PHI. Under the Privacy Rule and Security Rule, these processors must implement administrative, physical and technical safeguards. They may also need to sign a BAA before accessing data.
Covered entities versus data processors
Covered entities must publish privacy notices, provide access to medical records and restrict PHI uses and disclosures. Data processors are not required to post notices but are bound by their BAA. A claims processor, for example, does not post a privacy notice but must limit PHI use to what is necessary and support the covered entity in upholding patient rights.
When a processor becomes a business associate
Any service that handles PHI—electronic, paper or verbal—is a business associate. Even incidental access, such as hosting a health app, can trigger HIPAA duties. PHI includes names, addresses, record numbers and other identifiers relating to a person’s health, care or payment. De-identified data is outside HIPAA when specified identifiers are removed or an expert determines the risk of re‑identification is very small.
Core HIPAA rules that affect processors
Three rules make up the foundation of HIPAA for data processors: the Privacy Rule, the Security Rule and the Breach Notification Rule.
HIPAA imposes three primary rules that processors must understand:
- Privacy Rule (45 C.F.R. Subpart E) – Governs uses and disclosures of PHI. Processors may only use or disclose PHI as permitted by their contract or required by law. They must help covered entities respond to individual requests for access, amendments and accounting of disclosures.
- Security Rule (45 C.F.R. Subpart C) – Requires administrative, physical and technical safeguards to protect electronic PHI (ePHI). Processors must implement a security management process that includes risk analysis and risk management, assign a security official, control workforce access, train staff and secure systems. Technical safeguards include access controls, audit controls, integrity checks and transmission security.
- Breach Notification Rule (45 C.F.R. Subpart D) – Mandates notification to the covered entity, individuals, media and HHS after certain breaches. A breach is presumed when PHI is accessed or disclosed improperly, unless a risk assessment shows a low probability of compromise. Business associates must notify the covered entity without undue delay and no later than 60 days after discovery.
Types of data covered under HIPAA
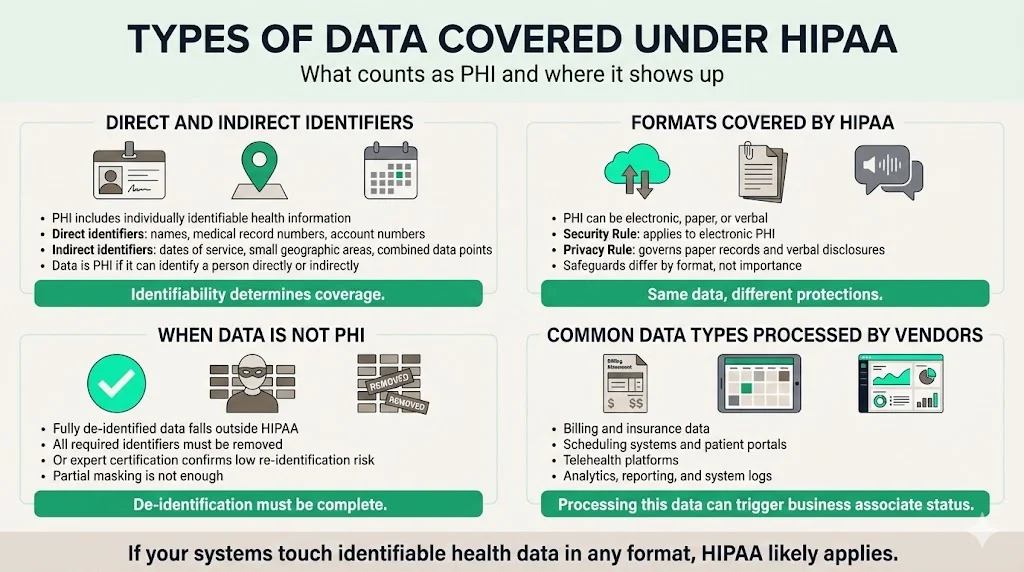
Direct and indirect identifiers
HIPAA protects protected health information (PHI), defined as any individually identifiable health information relating to a person’s health, healthcare provision or payment. Direct identifiers include names, medical record numbers and account numbers. Indirect identifiers include dates of service, geographic subdivisions smaller than a state and other data that, when combined, could identify an individual. Fully de‑identified data falls outside HIPAA when all specified identifiers are removed or an expert certifies that the risk of re‑identification is minimal.
PHI may exist in electronic, paper or verbal formats. The Security Rule applies specifically to electronic PHI, requiring safeguards for data at rest and in transit. The Privacy Rule, which restricts uses and disclosures and requires physical safeguards governs paper records and verbal disclosures.
Common data types handled by processors
- Billing and insurance data – Claims processing and revenue‑cycle platforms store patient identifiers, diagnosis codes and payment details.
- Appointment systems and patient portals – Scheduling platforms and telehealth portals handle names, contact information and clinical information.
- Analytics, reporting and logs – Business intelligence tools and logging services process large data sets containing PHI to produce dashboards or operational insights.
Any of these activities can make a vendor a business associate under HIPAA.
Important HIPAA requirements for data processors
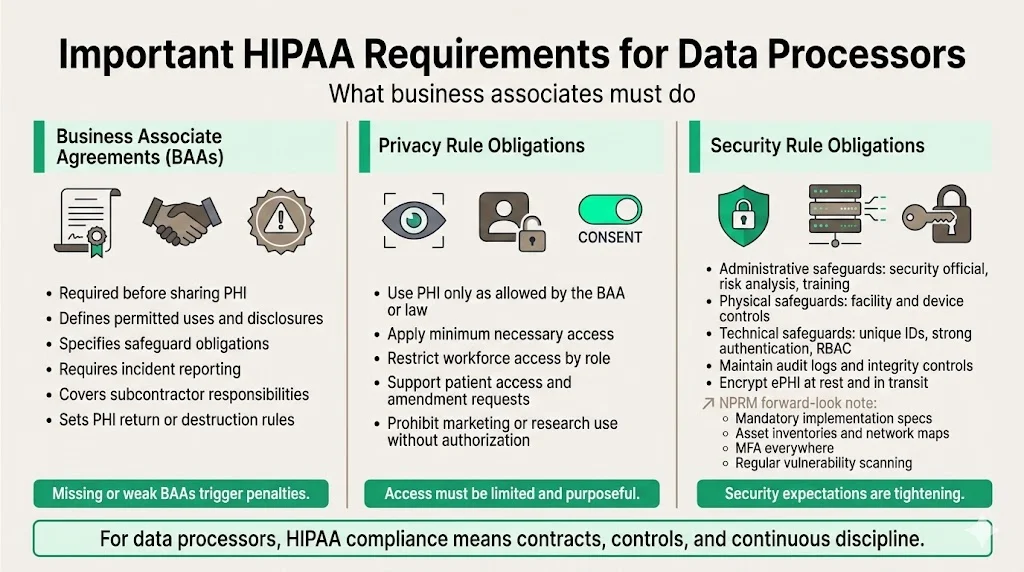
Business associate agreements
In HIPAA for data processors, a BAA outlines the terms under which PHI is shared. A BAA spells out permitted uses and disclosures, required safeguards, incident reporting, subcontractor obligations and destruction of PHI. Regulators have penalized covered entities for failing to execute BAAs, so precise language matters.
Privacy Rule obligations
Under the Privacy Rule, processors may only use or disclose PHI as permitted by the BAA or as required by law. They must follow the minimum necessary principle—accessing only the PHI needed to perform duties and limiting workforce access accordingly. Processors must also help covered entities respond to individual requests for access or amendments. Marketing or research uses of PHI are prohibited unless specifically authorized by the covered entity.
Security Rule obligations
The Security Rule requires processors to establish administrative, physical and technical safeguards. Administrative requirements include appointing a security official, conducting a risk analysis, implementing risk management measures and training the workforce. Physical safeguards involve facility access controls, workstation security and device management. Technical safeguards call for unique user identifiers, strong authentication methods, role‑based access controls, audit logs, integrity checks and encryption for data in transit and at rest. The 2024 Notice of Proposed Rulemaking (NPRM) signals that these requirements will become stricter: all implementation specifications would be mandatory; organizations would need asset inventories, network maps, multi‑factor authentication, encryption of ePHI at rest and in transit and regular vulnerability scanning. Processors should adopt these measures now to stay ahead of enforcement.
Administrative and technical safeguards
Administrative safeguards
Administrative safeguards create the governance framework for security. They include a documented security management process that identifies threats and vulnerabilities and implements risk‑reduction measures, assignment of a security officer, ongoing workforce training and written policies covering access control, incident response, breach notification, data retention and vendor management. Policies and training should be reviewed periodically and after major changes.
Technical safeguards
Technical measures protect systems and data. They include role‑based access with unique user identifiers, multi‑factor authentication, audit logging and monitoring, integrity checks, encryption of data in transit and at rest and automatic session timeouts. The NPRM proposes making encryption mandatory and requiring asset inventories, network maps and regular vulnerability scanning.
Risk assessment and ongoing compliance
Conducting a HIPAA risk assessment
Effective risk management is a cornerstone of HIPAA for data processors.
A risk assessment is the foundation of security. HIPAA requires an accurate and thorough assessment of potential risks and vulnerabilities to ePHI. An effective assessment identifies where ePHI is created, stored or transmitted, maps data flows and services, defines the scope of systems and users, lists foreseeable threats and vulnerabilities and evaluates their likelihood and impact. Findings inform risk management decisions and must be documented and reviewed periodically. Large organizations may follow NIST SP 800‑30 or ISO 27005; smaller teams can use HHS’s Security Risk Assessment Tool. Konfirmity’s experience shows that a mature assessment takes 3–6 weeks and should be repeated after significant changes.
Maintaining compliance over time
Compliance is continuous. Controls must operate day‑to‑day, and evidence must be collected across observation periods. Ongoing tasks include:
- System and vendor changes – Evaluate how new features, integrations or acquisitions affect PHI flows, update BAAs and adjust permissions accordingly.
- Monitoring and regulatory updates – Deploy tools that track access and configuration changes, document these activities and implement changes when requirements change.
Without dedicated resources, organizations struggle to maintain this cadence. A managed service frees internal teams to focus on product development and patient care while maintaining compliance. Clients working with Konfirmity often achieve SOC 2 Type II readiness in 4–5 months and cut internal effort to roughly 75 hours per year.
Data breach protocols and incident response
HIPAA for data processors includes the Breach Notification Rule, which sets clear requirements for identifying and reporting breaches.
What constitutes a HIPAA breach
A breach is an impermissible use or disclosure of PHI that compromises its security or privacy. Unless a risk assessment determines a low probability of compromise, any unauthorized access, loss or exposure of PHI is presumed to be a breach. Common scenarios include stolen or lost devices containing unencrypted ePHI, unauthorized employee access, phishing attacks and misdirected communications. There are narrow exceptions: incidental disclosures within the organization, unauthorized access by a workforce member acting in good faith, and situations where the unauthorized recipient is unlikely to retain the information.
Response obligations and timelines
After discovering a breach, processors and covered entities must investigate, assess the risk of compromise, notify the covered entity without undue delay (no later than 60 days) and help notify individuals, media and HHS if required. They must document their actions and train staff on breach response. Failing to follow these steps can lead to penalties. Enforcement actions in 2025 included settlements ranging from US$75,000 to US$800,000 for risk analysis failures and delayed notifications, underscoring that both covered entities and processors are expected to respond quickly and thoroughly.
HIPAA‑compliant data handling procedures
Secure collection and storage
Process only the data necessary to perform the contracted service. Avoid collecting extraneous identifiers and use strong encryption for data at rest. Host systems in facilities with strong physical protections and implement backup and disaster recovery plans. Define retention periods in the BAA and purge PHI when it is no longer needed. Implement secure deletion routines so that no remnants remain.
Data sharing and transfer
Use secure channels such as HTTPS, SFTP or VPNs for transferring PHI. Adopt strong encryption keys and rotate them regularly. Map data flows between services and ensure each downstream vendor signs a BAA and implements appropriate safeguards. Maintain logs of data transfers and be able to provide an accounting of disclosures on request.
Accountability and documentation
Maintain written policies covering privacy, security, incident response, training and vendor management. Document control implementation, risk assessments, security incidents and remediation steps. Provide regular training to employees and document completion. Conduct internal audits and management reviews at least annually. Well‑maintained documentation supports audits and demonstrates a commitment to security.
Common mistakes data processors make

1) Assuming HIPAA only applies to covered entities
Some vendors believe they are exempt because they are not healthcare providers. In reality, any processor handling PHI is a business associate. Failure to sign BAAs or implement controls can lead to penalties. In 2024, Providence Medical Institute faced a US$240,000 penalty for lacking a BAA and failing to restrict access to ePHI.
2) Weak vendor oversight
Covered entities often sign BAAs but fail to verify that vendors have implemented required safeguards. The NPRM proposes requiring business associates to certify annually that technical safeguards are in place and to notify covered entities when contingency plans are activated. Auditing vendors is therefore essential. Konfirmity recommends periodic vendor risk assessments, reviewing attestations (such as SOC 2 reports) and monitoring security posture continuously.
3) Incomplete risk assessments
Many processors perform one‑time assessments using generic questionnaires. OCR enforcement data shows that risk analysis failures are the leading cause of settlements. A thorough assessment maps data flows, identifies threats and vulnerabilities and documents decisions. Assessments should be repeated after system changes, new integrations or incidents.
4) Overlooking administrative safeguards
Organizations often invest in technology but neglect policies, training and contingency planning. A 2024 settlement resulted in a multimillion dollar penalty for failing to conduct a thorough risk analysis and implement system reviews. Documentation, training and governance are as important as technical measures.
Conclusion
Protecting health information is a shared responsibility. HIPAA for data processors is more than a legal requirement; it is a business imperative that influences sales cycles and risk exposure. By implementing solid administrative, physical and technical controls, performing regular risk assessments and documenting every step, processors reduce the likelihood of breaches and penalties. Security programs must operate every day, not just at audit time. Evidence collected over observation periods builds trust with buyers and auditors. Shallow compliance that looks good on paper but fails under incident pressure is a liability.
Konfirmity’s human‑led, managed security and compliance service helps organizations start with security and arrive at compliance. We embed controls inside client systems, perform risk analyses, manage evidence and keep them audit‑ready year‑round. Our clients reach SOC 2 Type II readiness in 4–5 months, compared with 9–12 months for self‑managed programs, and cut internal effort from 550–600 hours to about 75 hours per year. Whether you are pursuing SOC 2, ISO 27001, HIPAA for data processors or GDPR, building a durable program with expert operators accelerates deals, reduces findings and protects patient trust.
Frequently Asked Questions
1. What data requires HIPAA compliance?
HIPAA covers all protected health information, defined as individually identifiable health information related to a person’s health, healthcare provision or payment. Direct identifiers such as names, medical record numbers and Social Security numbers and indirect identifiers that could identify someone when combined are included. PHI may exist in electronic, paper or verbal formats, and all formats are covered. Fully de‑identified data is not subject to HIPAA.
2. Who is exempt from the HIPAA Privacy Rule?
Entities that do not meet the definition of a covered entity or business associate fall outside HIPAA’s scope. For example, a software vendor that hosts an application but never accesses PHI is not a business associate. Employers using employee medical information solely for employment purposes are also exempt. Educational records covered by FERPA and de‑identified data are excluded.
3. Is data mining covered by HIPAA?
Analytics activities trigger HIPAA duties when they involve PHI. If a processor performs data mining using identifiable patient data, it becomes a business associate and must sign a BAA. It may use or disclose PHI only as permitted by the contract and must apply the minimum necessary principle. De‑identified data can be used for analytics without HIPAA obligations. In practice, many analytics vendors pseudonymize data but retain enough identifiers to link sessions; these vendors typically require a BAA.
4. What makes a database HIPAA compliant?
A database used by a processor must implement technical controls such as unique user authentication, role‑based access, audit logging, encryption of data at rest and in transit and strong backup routines. Administrative controls must accompany technical measures: documented policies, regular risk assessments, workforce training and incident response plans. If a vendor hosts the database, a BAA is required, and periodic evaluations must verify that controls remain effective. The NPRM suggests that asset inventories, network maps, multi‑factor authentication and vulnerability scanning will soon be mandatory, so future database design should integrate these capabilities.




.svg)






.svg)
.svg)