Most enterprise buyers now ask for proof that the vendors handling their patient data can manage security on an ongoing basis. Without clear evidence, deals stall—even when teams think they’re “ready” on paper. The emergence of cloud computing, outsourcing, telehealth and international research partnerships means Protected Health Information (PHI) seldom stays within U.S. borders. As a result, the topic of HIPAA International Transfers has moved from a theoretical concern to a daily operational reality. This article explains why cross‑border transfers matter, how U.S. law interacts with local regimes and what steps healthcare organisations can take to remain audit‑ready while serving patients around the world. The goal is practical: understand the rules, implement effective safeguards and pick partners who make long‑term compliance a core part of their service.
What “HIPAA International Data Transfer” really means
HIPAA’s scope: U.S. law with global effects
HIPAA is a U.S. statute designed to protect the privacy and security of medical information within the healthcare sector. The Privacy Rule establishes standards for how covered entities—healthcare providers, health plans and clearinghouses—and their business associates may use or disclose PHI. The Security Rule requires them to implement administrative, physical and technical safeguards to protect electronic PHI (ePHI). While the law only has direct force within the United States, it imposes obligations on any company that manages U.S. health data, no matter where that company is located. Even foreign organisations must follow HIPAA requirements if they act as business associates for U.S. healthcare customers.
When PHI leaves the United States
HIPAA does not forbid international transfers of patient data. Instead, the law requires regulated entities to ensure that PHI remains protected during storage, transmission and processing. Business associate agreements (BAAs) are the primary mechanism for extending these protections across borders; they bind foreign vendors to HIPAA’s privacy, security and breach notification obligations. Without a signed BAA, a covered entity could face penalties even if the vendor sits outside the U.S.. This contractual approach is flexible but creates enforcement challenges—if a foreign vendor suffers a breach, recourse may be limited.
Why international transfers happen
Several forces drive HIPAA International Transfers. Cloud service providers often route data through geographically distributed data centres. Healthcare organisations outsource billing, radiology interpretation and software development to specialised vendors abroad to gain expertise and reduce costs. Research collaborations and telehealth programs involve clinicians and scientists on multiple continents. International insurance claims and multinational employer plans also require patient data to move across borders. These operational realities make it vital to understand both HIPAA and the privacy laws of destination countries.
Legal foundations for cross‑border PHI transfers
Privacy and security rules
The Privacy Rule defines how PHI may be used and disclosed. The Security Rule requires risk analysis and risk management processes to address threats to ePHI. NIST’s 2024 guidance emphasises that regulated entities must identify where ePHI is created, received, maintained and transmitted—including flows to cloud services or foreign processors—and assess risks to confidentiality, integrity and availability. The guidance outlines steps for risk assessment and risk management, starting with mapping data flows, identifying threats and vulnerabilities and implementing controls such as encryption and access control. These steps apply equally whether the data resides in a U.S. facility or on an overseas server.
Business Associate Agreements
A business associate is any entity that performs functions involving PHI on behalf of a covered entity. This includes foreign vendors. BAAs must spell out the vendor’s obligation to safeguard PHI, report breaches and bind subcontractors to HIPAA requirements. The agreement should require appropriate encryption, logging and authentication and specify breach response and indemnity provisions. Without a valid BAA, U.S. regulators can impose fines even if the breach occurs overseas. When offshoring administrative functions, healthcare providers should also consider international arbitration clauses and insurance coverage to address enforcement challenges.
HIPAA vs. local laws
HIPAA’s jurisdiction is tied to the origin of the PHI and the regulated entity’s role, not physical location. Foreign laws may still impose restrictions. Several U.S. states have introduced data‑localisation clauses in Medicaid contracts that require PHI to be stored within U.S. borders. Florida’s Electronic Health Records Exchange Act requires patient records stored offsite to remain in the continental United States or Canada. Texas has proposed legislation requiring electronic health records of state residents to stay inside the country. These state rules overlay HIPAA and can restrict how organisations use overseas vendors.
Overlapping frameworks such as GDPR
The European Union’s General Data Protection Regulation (GDPR) applies to the personal data of EU residents regardless of where processing occurs. Cross‑border transfers under GDPR require an adequacy decision, standard contractual clauses or binding corporate rules. GDPR mandates notification of authorities within 72 hours of a breachcensinet.com and fines can reach €20 million or 4 percent of global turnover. HIPAA, by comparison, allows up to 60 days for breach notification and caps annual fines at $1.5 million. Organisations that handle both U.S. PHI and EU personal data must comply with both sets of rules; they may need to implement additional transfer impact assessments and technical measures when moving data from the EU. This dual compliance burden is a common reality for HIPAA International Transfers.
Practical steps for HIPAA compliance across borders
Conduct risk assessments
Regulated entities should perform an accurate and thorough risk analysis as required under HIPAA’s Security Rule. This involves identifying all locations where ePHI is processed—on‑premises, in the cloud or at vendor facilities—mapping data flows and evaluating threats such as ransomware, phishing and unauthorised access. NIST recommends including remote workers, mobile devices and medical IoT in the assessment scope. In the context of HIPAA International Transfers, the risk analysis must consider foreign legal requirements, political stability and the vendor’s security maturity. For example, the Avatier study reports that international HIPAA cases take 40 percent longer to resolve and lead to penalties 28 percent higher than domestic cases. Understanding these risks informs controls and contractual terms.
Secure agreements with partners
Every cross‑border arrangement should start with a robust BAA. The contract should specify permitted uses and disclosures, required security measures (encryption in transit and at rest, multi‑factor authentication, audit logging), breach notification procedures and termination rights. Offshore BAAs may need to address international arbitration, data residency clauses and insurance. The Paubox analysis notes that the obligation to sign a BAA applies regardless of vendor location and failure to have one is itself a violation.
Implement strong technical safeguards
Encryption, network segmentation, zero‑trust access controls, multi‑factor authentication and continuous logging are mandatory components of a cross‑border security program. NIST’s guidance advises encrypting ePHI at rest and in transit, controlling access based on roles and logging activities for audit. The McDermott briefing adds that offshore contractors should not print or archive data locally and that retention periods should be defined in the contract. When data travels across jurisdictions, these controls must extend to cloud service providers and subcontractors.
Define policies for data transfer
Organisations should document how data flows across borders, who has access and what happens in an emergency. This includes diagrams showing systems and vendors, standard operating procedures for transferring or retrieving data, and incident response plans. Offshoring policies should collect and maintain information about each offshore arrangement, define minimum necessary access and require encryption. An effective policy ensures that technical controls align with contractual obligations and that teams know how to respond to incidents.
Monitor and audit continuously
Once HIPAA International Transfers are in place, they require ongoing oversight. NIST recommends periodic risk assessments and continuous monitoring of controls to ensure they stay effective. Healthcare organisations should audit offshore subcontractors at least annually and evaluate whether to continue relationships based on audit results. The Avatier report notes that 67 percent of healthcare organisations struggle with identity and access management across international operations; continuous monitoring helps detect access drift and enforce least‑privilege.
Common scenarios and challenges
PHI in the cloud
Cloud platforms offer scalability and convenience, but they often distribute data across multiple regions. Under HIPAA, a cloud service provider that stores or processes ePHI is a business associate and must sign a BAA. Providers should confirm whether their data centres are in countries with adequate legal protections. When data resides in a jurisdiction with restrictive laws—such as requirements for government access—additional safeguards or relocation may be necessary. Mapping these dependencies is a key part of HIPAA International Transfers.
Offshoring and service providers
Offshoring administrative functions can reduce costs, but it introduces legal complexity. Some U.S. states, such as Wisconsin and Texas, require that patient data be stored and maintained within the United States. Florida’s law ties healthcare providers’ licences to storing records onshore. Healthcare providers must therefore reconcile state localisation mandates with their cost‑saving goals. When offshoring is permitted, best practices include adopting an offshoring policy, entering into tailored BAAs, limiting access to the minimum necessary data and performing regular audits. Contracts often include restrictions on printing data or storing it for longer than needed.
Data localisation tensions
Data localisation rules are not confined to the United States. China’s Personal Information Protection Law (PIPL), India’s Digital Personal Data Protection Act and Canada’s provincial health privacy statutes impose residency requirements for certain health data. While our focus is HIPAA, these local laws can affect cross‑border operations. For example, transferring U.S. PHI to a country with mandatory localisation may require that data be stored in the United States while allowing access from abroad. The interplay between HIPAA and local laws often requires legal advice and careful contract drafting.
Security vs. accessibility
Healthcare teams need timely access to information to provide care. Strict controls—such as multi‑factor authentication and limited roles—can slow workflows if not designed well. Conversely, weak controls lead to breaches. The DeepStrike report notes that in 2025 healthcare breaches cost an average of $7.42 million and that the average breach lifecycle is 279 days. Attackers often exploit third‑party vendors; half of healthcare breaches in 2025 involved a business associate. The challenge is to build controls that support clinical workflows while preventing unauthorised access, and to vet vendors rigorously.
Cross‑border PHI transfer: key safeguards
When moving PHI across borders, the following safeguards are essential:
- Executed BAAs: Signed with every vendor, specifying permitted uses, required controls, breach notification and termination rights.
- Encryption and secure channels: Encrypt PHI during transmission and at rest; use VPNs or TLS; avoid public cloud services that do not provide encryption keys.
- Role‑based access: Grant the minimum necessary privileges and enforce multi‑factor authentication; maintain logs and review access regularly.
- Local compliance checks: Confirm that destination countries do not impose conflicting laws; review state localisation requirements in the U.S. and local privacy statutes abroad.
- Incident response procedures: Document how to detect, contain and report breaches; ensure that foreign vendors can meet HIPAA’s 60‑day notification timeline and GDPR’s 72‑hour requirement.
- Regular audits: Perform periodic audits of vendors and internal systems; address gaps promptly; use third‑party assessments for high‑risk vendors.
How HIPAA interacts with global privacy laws
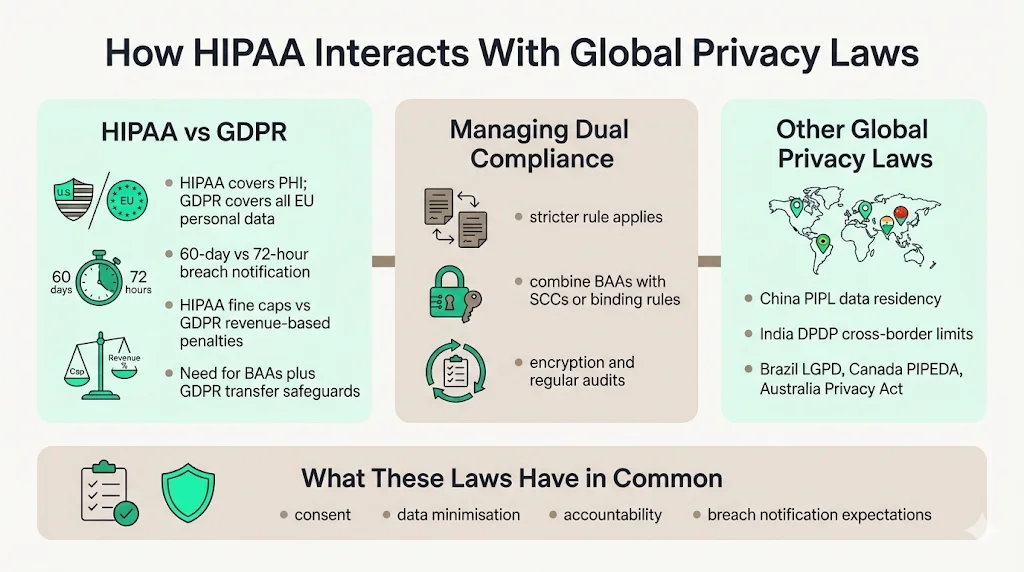
HIPAA and GDPR
GDPR’s broader jurisdiction means that any organisation processing EU residents’ data must comply, regardless of location. Key differences: GDPR requires breach reporting within 72 hours and covers all personal data of EU residents, while HIPAA applies to PHI and allows up to 60 days for notification. Penalties also differ: GDPR fines can reach €20 million or 4 percent of global revenue, whereas HIPAA fines are capped at $1.5 million per year. Organisations handling both frameworks must comply with the stricter provisions and may need to implement standard contractual clauses or binding corporate rules for transfers. Unified strategies should combine BAAs with GDPR‑compliant transfer mechanisms, encryption and regular audits.
Other local laws
China’s PIPL requires certain critical data to be stored locally and subjects international transfers to security assessments. India’s Digital Personal Data Protection Act of 2023 imposes similar cross‑border restrictions. Brazil’s LGPD, Canada’s Personal Information Protection and Electronic Documents Act and Australia’s Privacy Act all contain rules about international transfers and breach notifications. While these laws vary, they share a focus on consent, data minimisation and accountability. Organisations engaged in HIPAA International Transfers must therefore track multiple regimes and align controls accordingly.
Real‑world compliance tips
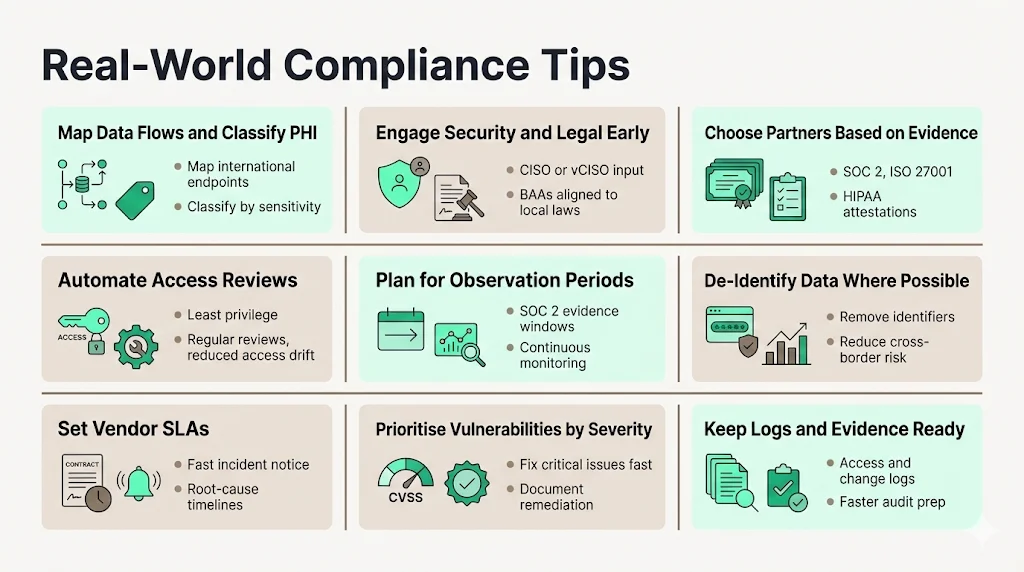
Drawing on more than 6,000 audits and over 25 years of combined expertise at Konfirmity, the following practices help teams manage HIPAA International Transfers while supporting enterprise sales cycles:
- Map data flows and classify information. Use diagrams to show where PHI is created, stored and transmitted, including international endpoints. Classify data by sensitivity so that resources are directed where they are most needed.
- Engage security and legal experts early. Involve a dedicated CISO or virtual CISO to design controls and legal counsel to draft BAAs that account for local laws and arbitration.
- Select partners based on evidence, not promises. Evaluate vendors on their ability to provide continuous security evidence (e.g., SOC 2 reports, ISO 27001 certificates, HIPAA compliance attestations). Avoid “compliance manufacturing” claims that offer quick certification without underlying security work.
- De‑identify data whenever possible. Remove direct identifiers or aggregate data before sending it abroad. Under HIPAA, de‑identified data is not considered PHI. This reduces risk and simplifies compliance.
- Automate access reviews and change management. Use tools to enforce least‑privilege access, conduct regular reviews and document evidence for audits. In our delivery work, automated reviews reduce effort by 75 percent and cut access drift findings by half.
- Plan for observation periods. For SOC 2 Type II, auditors require evidence across observation periods of six months or more. Build continuous monitoring into your operations to avoid evidence gaps.
- Set service‑level agreements (SLAs) for vendor responsiveness. For example, require vendors to notify you of incidents within 24 hours and provide root‑cause analyses within a week. Tie these expectations to contractual remedies.
- Use vulnerability management aligned with CVSS scores. Prioritise remediation based on severity and set SLAs (e.g., critical vulnerabilities fixed within seven days). Document patching to prove control operation.
- Keep audit logs and evidence ready. Maintain detailed logs for access, changes and incident response. In our experience, keeping logs and evidence up to date reduces audit preparation time from 550–600 internal hours to about 75 hours when working with a managed service partner.
Konfirmity’s practitioner perspective
Konfirmity is a human‑led managed security and compliance service. Unlike software tools or short‑term consulting, we embed seasoned practitioners who design, implement and operate controls inside your environment. We have supported more than 6,000 audits and maintain a combined 25+ years of expertise across HIPAA, ISO 27001, SOC 2 and GDPR. Our approach is to start with security and arrive at compliance. For example, typical SOC 2 readiness projects self‑managed by engineering teams take nine to twelve months and require about 550–600 internal hours. With Konfirmity, our clients achieve readiness in roughly four to five months and reduce internal effort to around 75 hours by relying on our managed service model. We provide continuous monitoring, evidence collection, vendor risk workflows and remediation tracking. That means when an enterprise buyer requests proof of HIPAA or SOC 2 compliance, our clients can deliver artefacts immediately, accelerating sales cycles.
Cross‑framework alignment is another advantage. Many controls map across HIPAA, SOC 2 and ISO 27001. For instance, access control, encryption, incident response and vendor risk management are common themes. Our team designs controls once and produces evidence that satisfies multiple frameworks, saving time and reducing complexity. We also use CVSS‑based triage for vulnerabilities, enforce least‑privilege reviews and implement DPIA triggers for GDPR. These processes ensure that HIPAA International Transfers are part of a broader security program, not treated as a one‑off problem.
Conclusion
Healthcare organisations cannot avoid HIPAA International Transfers. Cloud services, global supply chains and telehealth mean that U.S. PHI will continue to cross borders. HIPAA does not end at the water’s edge; it follows the data and applies to any vendor handling U.S. PHI. By conducting thorough risk assessments, entering into detailed BAAs, implementing technical safeguards and regularly auditing partners, organisations can protect patient privacy and remain audit‑ready. Equally important is understanding local laws and overlapping frameworks like GDPR. Finally, remember that real security programs are built daily, not during a once‑per‑year audit. Work with partners who deliver outcomes—program design, implementation, monitoring and evidence collection—rather than just advice. Security that looks good on paper but collapses under pressure puts patients and business at risk. Build the program once, operate it continually and let compliance follow.
Frequently asked questions
1. Can PHI be stored outside the United States?
Yes. HIPAA permits storage abroad, but covered entities must put proper BAAs and safeguards in place. Some U.S. states and foreign jurisdictions may impose additional restrictions, so review all applicable laws.
2. Does HIPAA apply to non‑U.S. companies?
HIPAA itself does not directly govern foreign firms, but if they handle U.S. PHI as business associates they must comply with HIPAA and sign a BAA.
3. How does HIPAA interact with GDPR?
GDPR applies to EU residents’ personal data no matter where it is processed. Organisations handling both HIPAA‑protected PHI and GDPR‑protected data must meet both sets of requirements, including stricter breach notification timelines and possible use of standard contractual clauses or adequacy decisions.
4. What safeguards are required for cross‑border PHI transfers?
Required safeguards include executed BAAs, encryption during transmission and at rest, role‑based access controls, local compliance checks, incident response plans and regular audits. These controls should align with both HIPAA and any applicable local regulations.





.svg)






.svg)
.svg)