Modern healthcare organizations sit at the intersection of patient care, technology, and regulation. They handle electronic protected health information (ePHI) across electronic health record systems, cloud environments, and mobile apps. Attackers know this makes hospitals and vendors lucrative targets. A 2025 study found that healthcare breaches cost an average of $7.42 million, and U.S. providers see even higher costs. Investigations from the U.S. Office for Civil Rights (OCR) confirm that many incidents stem from weak risk analysis, poor access control, and lapses in monitoring. While policies and checklists may look satisfactory on paper, leaders need proof that controls work under pressure. This guide explains why HIPAA penetration testing provides that evidence and how to build an effective testing program.
Why security testing matters for healthcare organizations
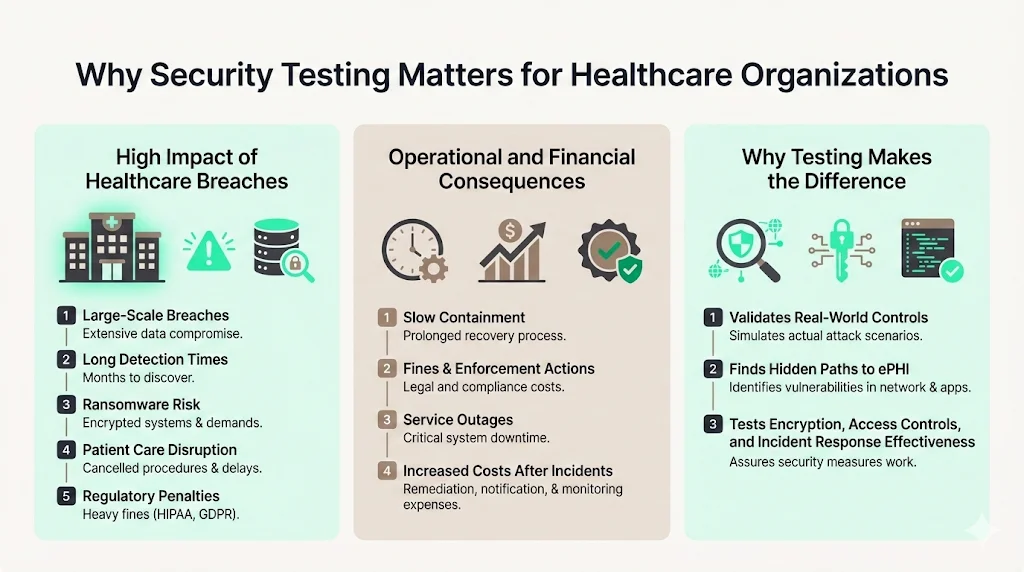
Healthcare breaches disrupt care and erode trust. In 2024 there were 725 reportable incidents, yet they exposed 275 million records. Mega‑breaches at vendors like Change Healthcare cascaded across hundreds of clinics. Average detection and containment took 279 days—five weeks longer than other industries. During that window, attackers moved laterally, siphoning personal information and sometimes deploying ransomware. Fines compound the damage. In 2025 OCR concluded 22 enforcement actions with penalties ranging from $25 k to $1.5 million for failures such as missing risk analysis or delays in breach notification. In addition to financial loss, the 2025 IBM report found that 86 % of organizations experienced service disruptions and 45 % raised prices after an incident.
Security testing helps executives understand whether their investments are working. Technical assessments reveal hidden paths to ePHI that policy reviews miss. They show whether encryption actually protects data, whether access controls prevent privilege escalation, and whether incident response catches malicious activity. Without this feedback loop, teams may assume they are secure until an adversary proves otherwise.
Real risks of breaches involving ePHI
OCR enforcement data exposes recurring themes. BayCare Health paid $800 k for lacking documented risk management and access reviews. Warby Parker paid $1.5 million after investigators found weak identity management and inadequate monitoring. Some providers delayed notifying regulators and patients; Syracuse ASC’s $250 k settlement stemmed from failing to report promptly. Third‑party vendors are often the entry point: Comstar, a billing service, settled for $75 k following a breach.
Incidents at Change Healthcare and Ascension in 2024 delayed claims processing and surgeries, illustrating how security failures can disrupt care.
Where testing fits into compliance
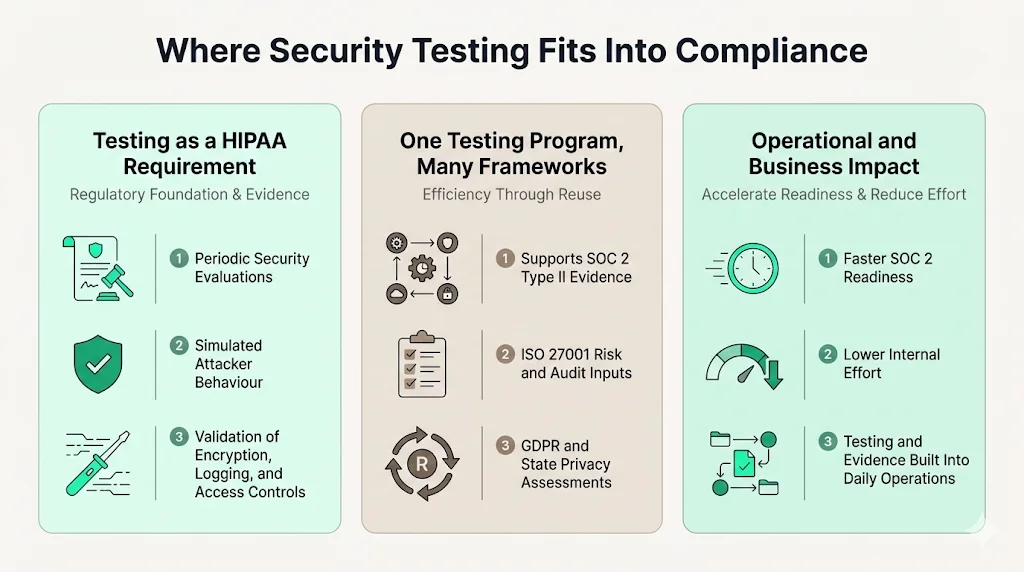
HIPAA’s Security Rule requires covered entities and business associates to implement administrative, physical, and technical safeguards. It also mandates periodic evaluations of the security program. The National Institute of Standards and Technology (NIST) acknowledges that HIPAA penetration testing is a valid method for fulfilling this evaluation requirement. Testing simulates real adversary behaviour to confirm whether controls like encryption, logging, and access restrictions function as intended.
Penetration tests also produce evidence that supports other frameworks. SOC 2 Type II assessments examine operational effectiveness over an observation window. ISO 27001:2022 requires risk assessments, internal audits, and a statement of applicability. GDPR and state privacy laws expect privacy impact assessments and vendor oversight. A single, well‑structured testing program can feed artifacts into multiple compliance efforts, reducing duplication.
Konfirmity’s experience shows the business impact of testing. Our clients, many of whom handle ePHI, typically achieve SOC 2 readiness in 4–5 months instead of the 9–12 months we see in self‑managed programs. Internal effort drops from 550–600 hours to about 75 hours per year because we integrate testing, remediation, and evidence collection into daily operations.
What testing means
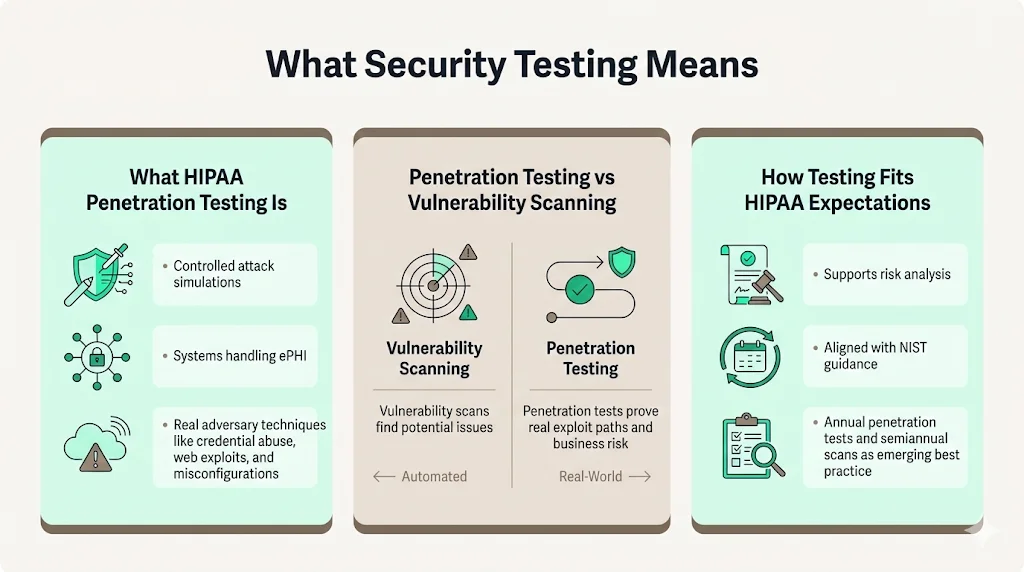
The term HIPAA penetration testing refers to controlled attempts to exploit vulnerabilities in systems that create, receive, maintain, or transmit ePHI. Ethical hackers use the same tools and techniques as adversaries: network scanning, credential stuffing, web exploitation, social engineering, and cloud misconfiguration attacks. Unlike automated vulnerability scans that identify potential issues, penetration tests demonstrate actual exploit paths. DeepStrike explains that vulnerability assessments are broad, automated checks, while penetration tests are targeted exercises that validate real risk.
Under HIPAA, such testing is not explicitly mandated. However, NIST guidance and industry best practices view it as an essential component of risk analysis. Draft updates to the Security Rule propose enterprise‑wide penetration tests at least every 12 months and vulnerability scans every six months. Adopting these intervals now helps organizations match upcoming rules.
How HIPAA rules tie into penetration testing
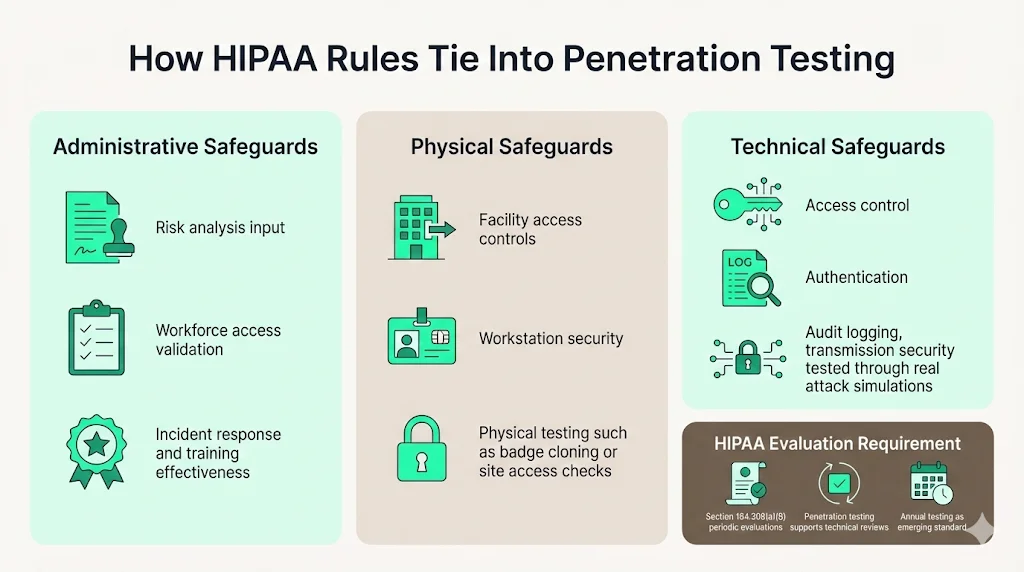
HIPAA’s safeguards fall into three categories:
- Administrative safeguards require organizations to conduct risk analysis, manage workforce access, and document policies. Testing provides input to this risk analysis and validates whether training and incident response procedures work.
- Physical safeguards control facility access, workstation security, and device handling. Tests may include physical penetration exercises or badge cloning to verify building controls.
- Technical safeguards encompass access control, audit logging, integrity mechanisms, authentication, and transmission security. Penetration testing directly measures whether these controls resist exploitation.
Section 164.308(a)(8) calls for periodic technical and non‑technical evaluations. Penetration testing addresses the “technical” component by showing that implemented controls withstand real attacks. The proposed rule’s suggested cadence of annual tests formalizes this expectation.
Penetration testing vs vulnerability assessment
A vulnerability assessment uses automated tools to identify known weaknesses—missing patches, default credentials, misconfigurations, or outdated libraries. It produces a broad list of issues with severity ratings. A penetration test goes deeper. Testers chain vulnerabilities, pivot through networks, and try to access sensitive data. They uncover hidden connections between systems and demonstrate the impact of exploitation. DeepStrike’s comparison emphasizes that both assessments and tests are necessary: scans provide breadth, while tests provide depth.
HIPAA security programs should include both activities. Automated scans run regularly (monthly or quarterly) to catch new issues quickly. Penetration tests occur less frequently but require manual expertise. Using scan results to inform test scope allows ethical hackers to focus on the most promising targets.
Systems included in testing scope
Any system that creates, receives, maintains, or transmits ePHI belongs in scope. Common examples include:
- Electronic health record systems – central patient databases.
- Patient portals and mobile apps – interfaces for patients.
- Internal networks and staff devices – laptops, tablets, and workstations.
- Cloud and hosted environments – cloud storage and analytics platforms.
- Medical devices connected to networks – infusion pumps, imaging systems, and remote monitors.
- Third‑party services – billing, telemedicine, and analytics vendors.
Step‑by‑step testing process
Scoping and planning
The engagement begins by defining the scope. Stakeholders identify in‑scope systems and data, including EHRs, patient portals, cloud accounts, and vendor integrations. Rules of engagement set expectations: which systems can be tested, during what hours, and whether social engineering or physical testing is allowed. Goals should match compliance needs—are test results intended for auditors, customers, insurers, or all three?
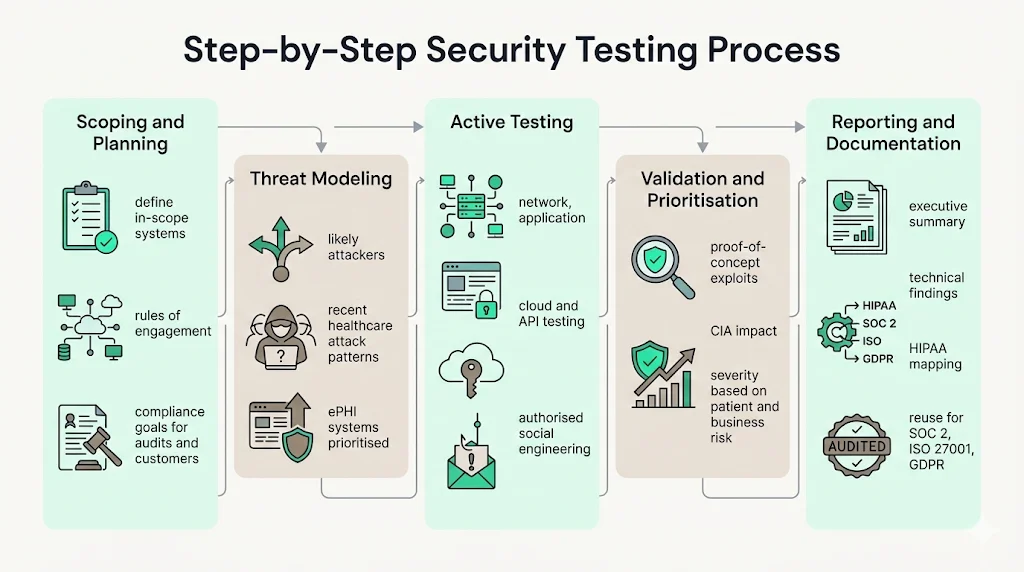
Threat modeling
Testers develop a model of how adversaries might target the environment. They consider threat actors such as ransomware gangs, insiders, and nation‑states. Recent healthcare incidents provide clues: phishing campaigns, exploitation of unpatched VPN appliances, misuse of vendor credentials, and misconfigured cloud buckets. Assets that store or transmit ePHI receive top priority.
Active testing
During the active phase, ethical hackers conduct controlled attacks:
- Network tests – examine open ports, outdated services, and segmentation.
- Application tests – check input validation, authentication, and business logic.
- Cloud and API tests – review IAM roles, storage configurations, and exposed interfaces.
- Social engineering – authorized phishing or calls to gauge workforce awareness.
Active testing often uncovers how minor weaknesses combine into serious breaches—for example, harvesting credentials via phishing, pivoting through a VPN, and exploiting an unpatched service to reach an EHR database. Testers also check segmentation and logging by moving between network zones and reviewing cloud permissions.
Validation of findings
Testers then validate each issue by showing how it affects confidentiality, integrity, and availability. Proof‑of‑concept exploits provide evidence without damaging systems—for example, reading a single record rather than dumping a database. They document the attack path to help defenders understand how the breach unfolded and prioritize fixes.
After validation, testers and internal teams assign severity based on exploitability and patient impact; high‑risk issues demand immediate fixes, while lower‑risk items are scheduled. Prioritization helps teams focus resources on what matters most.
Reporting and documentation
A HIPAA‑focused report should cater to both technical and non‑technical audiences. It includes an executive overview summarizing findings, detailed descriptions of each issue with reproduction steps and remediation advice, severity ratings tied to HIPAA safeguards, and sanitized evidence. Reports must be stored for at least six years to meet documentation requirements and should be ready for auditors or investigators.
High‑quality reports go further. They map each finding to not only HIPAA safeguards but also to control objectives in SOC 2, ISO 27001, and GDPR. This cross‑mapping allows organizations to reuse evidence across multiple compliance frameworks. Reports often contain tables summarizing the number of findings by severity, affected systems, and remediation status. They may include diagrams of attack paths or screenshots of proof‑of‑concept exploits. Clear, jargon‑free language ensures executives understand the business impact, while detailed technical appendices guide remediation teams. Many providers also deliver a management response template, enabling organizations to document how each issue will be addressed and track progress through completion.
Compliance testing and regulatory expectations
The Security Rule expects covered entities and business associates to conduct ongoing risk analysis and implement measures to reduce identified risks. Section 164.308(a)(1) mandates a security management process, while section 164.308(a)(8) requires evaluations. NIST’s 2024 guidance recognizes penetration tests and vulnerability assessments as appropriate evaluation techniques. The draft rule suggests annual penetration tests and semi‑annual vulnerability scans. Test results support audits, insurance underwriting, and procurement questionnaires. Organizations that lack documented testing may face higher fines or longer sales cycles.
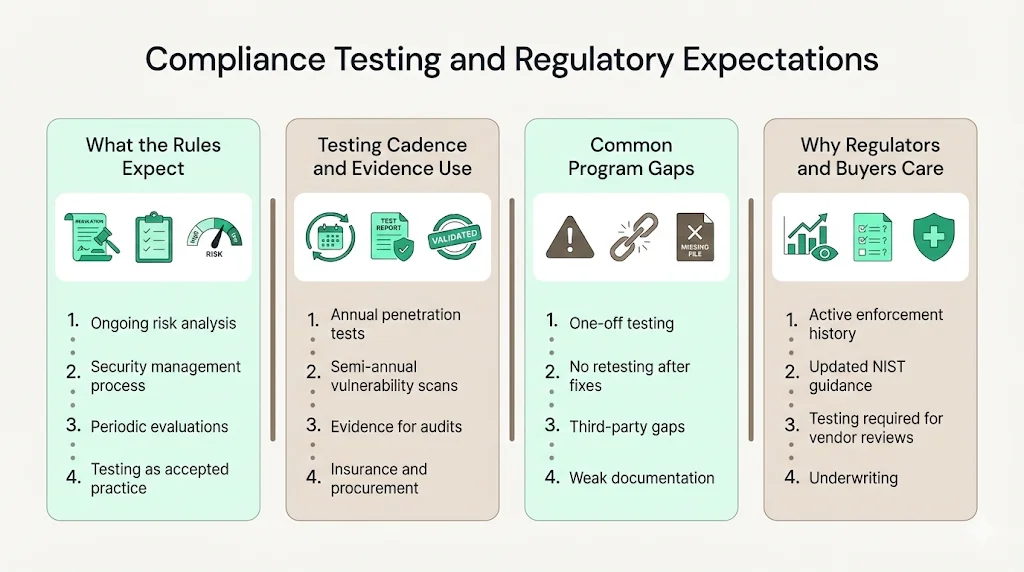
Common pitfalls include treating testing as a single activity instead of an ongoing program, failing to remediate and retest, leaving legacy interfaces or third‑party connections out of scope, and poor documentation. A mature program integrates testing with risk management, remediation tracking, and executive reporting.
Regulators have made clear that enforcement is not theoretical. Since HIPAA compliance dates took effect in 2003, OCR has received over 348,877 complaints and initiated 1,182 compliance reviews, resolving more than 99 % of cases. These numbers show the scale of oversight and the expectation that organizations maintain strong programs. NIST SP 800‑66 revision 2, released in early 2024, provides updated guidance on implementing the Security Rule and stresses the importance of risk analysis, workforce training, vendor oversight, and periodic evaluation. It encourages entities to consider penetration testing and vulnerability assessments as part of a defensible security strategy.
Testing results are also increasingly requested during enterprise procurements and cyber insurance underwriting. Health plans and large hospital networks use security questionnaires to vet vendors. Without recent penetration test reports and evidence of vulnerability management, deals can stall or insurers may impose higher premiums. Investing in regular testing therefore supports both compliance and business growth.
How often should HIPAA penetration testing occur?
Baseline practice is to perform HIPAA penetration testing annually, following the proposed rule. However, additional tests should occur after major system changes, significant code releases, mergers or acquisitions, or security incidents. Routine vulnerability scans should run quarterly or monthly on critical systems. Regular testing identifies weaknesses early, reduces remediation costs, and demonstrates proactive risk management to regulators and partners.
Risk‑based scheduling is equally important. Organizations undergoing rapid technology-driven transformation—adopting cloud services, building mobile apps, or deploying Internet of Medical Things devices—should increase testing cadence. Similarly, institutions connected to academic networks or participating in clinical trials may face higher severity of threats and warrant more frequent assessments. Conversely, smaller practices with stable infrastructure might extend the interval slightly if they have strong vulnerability management and continuous monitoring. It is important to revisit testing frequency whenever there are material changes to the environment or threat conditions.
Who is responsible for testing?
Both covered entities and business associates must protect ePHI. Contracts should require business associates to implement safeguards and provide testing evidence. Within an organization, a security or compliance leader should own the testing program, coordinate scoping, track remediation, and maintain records. Boards and executives should receive periodic updates on findings and risk posture. Internal security teams may conduct tests if they possess the necessary expertise, but many providers engage independent specialists to ensure objectivity and deep technical skills.
Choosing the right approach
Organizations weigh in‑house and third‑party options. Internal programs offer control but require hiring and retaining skilled testers, maintaining tools, and ensuring independence. External providers bring specialized expertise, healthcare experience, and independence appreciated by auditors. Konfirmity has conducted more than 6,000 audits with a team of 25 years combined expertise. Our managed service integrates testing, remediation, and evidence collection. Clients often see readiness timelines shrink from 9–12 months to 4–5 months, and internal effort drop from hundreds of hours to about 75 hours annually.
When selecting a partner, ask about healthcare experience, data‑handling practices, tester certifications, ability to map findings to HIPAA safeguards, and support for remediation and retesting. Ensure that providers can sign Business Associate Agreements and assist with vendor risk questionnaires.
Skills and questions to consider
Testers should have strong offensive skills, hold certifications such as OSCP or GPEN, and understand healthcare protocols like HL7, FHIR, and DICOM so they can work safely around medical devices and clinical workflows. When vetting providers, ask about experience with EHRs, portals, and cloud platforms; inquire about data‑handling practices; request sample reports that map findings to HIPAA and other frameworks; confirm that the firm helps with remediation and retesting; and verify willingness to sign Business Associate Agreements and answer vendor questionnaires.
Common findings in healthcare penetration tests
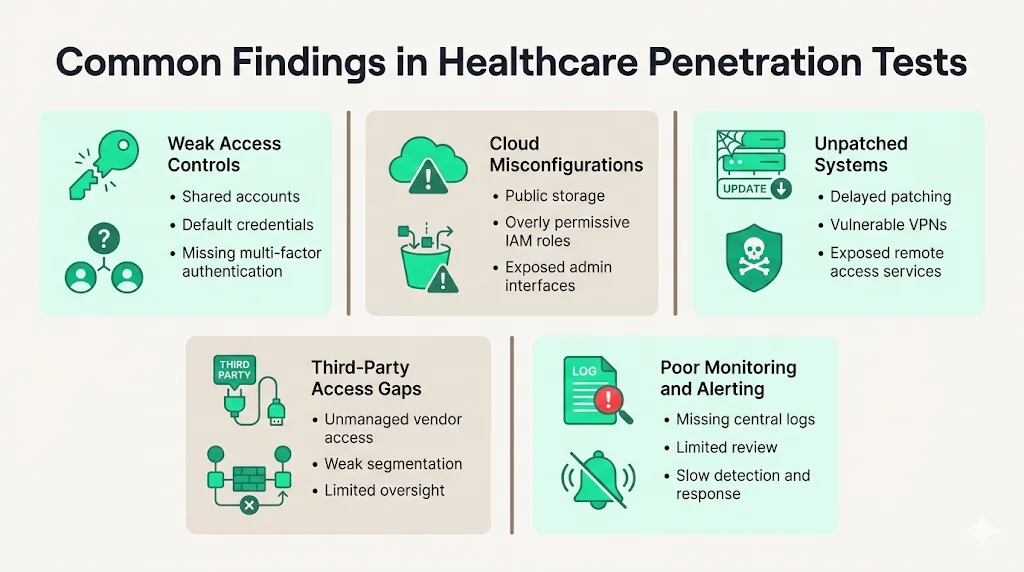
Patterns we see across many engagements include:
- Weak access controls – shared accounts, default credentials on devices, or missing multi‑factor authentication. Warby Parker’s penalty shows the cost of poor identity management.
- Misconfigured cloud services – unrestricted storage buckets, overly permissive IAM roles, and exposed management interfaces.
- Unpatched systems – healthcare often delays patching due to compatibility concerns; attackers exploit outdated VPNs and remote desktop services.
- Third‑party access gaps – vendors with remote access may bypass segmentation and monitoring.
- Poor monitoring and alerting – lack of centralized logging or log review delays detection and response.
Turning test results into action
Testing only matters if findings lead to fixes. Teams should rank issues by patient impact and CVSS scores, assign each finding to an owner with a deadline, and track progress. High‑risk issues may require interim mitigations, such as disabling vulnerable services, while permanent fixes are developed. Retesting verifies that remediation is effective—Health IT Answers advises a focused retest after patching critical issues. Records of findings, remediation actions, retest results, and communications should be retained for at least six years.
Effective remediation requires collaboration across departments. Security teams identify and prioritize vulnerabilities, but IT operations, development, and clinical engineering must implement fixes. A centralized tracking system can help coordinate assignments, deadlines, and status. For complex issues, such as replacing an outdated authentication mechanism across multiple applications, project management techniques may be needed. Testing programs should also include a “lessons learned” process: after each engagement, teams review what went well, what could improve, and how to prevent similar issues in the future. These insights feed back into security awareness training, architecture reviews, and vendor selection criteria, gradually raising the organization’s maturity.
Benefits of testing
Well-developed HIPAA penetration testing programs deliver several benefits:
- Reduced breach risk – identifying and fixing exploitable weaknesses lowers the chance of incidents. IBM research shows that strong security automation can cut breach lifecycles by 80 days and save almost $1.9 million.
- Improved trust – testing demonstrates commitment to protecting patient data. Providers can share summary results with customers and insurers to accelerate due diligence.
- Audit readiness – test reports provide evidence of risk analysis, evaluation, and remediation required by HIPAA and other frameworks.
- Operational insight – manual testing reveals hidden attack paths, enabling targeted investments and measuring improvement over time.
Conclusion
Security that looks strong in documentation but fails under real attacks is a liability. Healthcare operates in a high‑risk environment where breaches are costly and can disrupt patient care. HIPAA penetration testing is a practical tool to verify that safeguards work. It satisfies evaluation requirements, produces evidence for audits and sales cycles, and supports a ongoing improvement. By integrating annual tests with frequent scans and ongoing remediation, organizations can reduce long‑term exposure and deliver safer patient services. Building a program once and operating it daily lets compliance follow naturally. Regular training and executive oversight embed security into everyday workflows. When leadership treats penetration testing as a routine part of quality management, it becomes easier to secure funding, coordinate teams, and demonstrate progress. Ongoing programs also support due diligence during mergers and partnerships, giving stakeholders confidence that patient data is safeguarded. Mapping penetration test results to other standards, such as SOC 2 and ISO 27001, further streamlines audits and reduces the cost of assurance.
Frequently asked questions (FAQ)
1. Is HIPAA penetration testing mandatory?
HIPAA does not list penetration testing as a specific requirement, but the Security Rule mandates ongoing risk analysis and evaluations. NIST guidance and proposed rule updates recognise penetration tests as an effective way to meet this evaluation. Many insurers and regulators now expect documented testing.
2. How often should HIPAA penetration testing be performed?
Annual tests match draft regulatory guidance. Additional tests should follow major system changes, code releases, mergers, acquisitions, or security incidents. Quarterly or monthly vulnerability scans complement annual tests.
3. What systems should be included?
Any system that creates, receives, maintains, or transmits ePHI falls under scope: EHRs, patient portals, mobile apps, internal networks, cloud environments, connected medical devices, and third‑party services.
4. Who is responsible?
Covered entities must ensure that both their own systems and those of business associates meet HIPAA safeguards. A designated security or compliance leader should oversee testing, remediation, and documentation. Many organizations partner with specialized providers to conduct tests and ensure independence.





.svg)






.svg)
.svg)