Most enterprise buyers now request assurance artifacts before procurement even begins. In 2025, the days of signing a deal based solely on a sales pitch are gone. Security reviews have become the primary gatekeeper in the B2B sales cycle. Without operational security and continuous evidence, deals stall—even when teams believe they are ready on paper.
When a Fortune 500 company or a healthcare provider sends you a security questionnaire, they aren’t just checking if you have a firewall. They want to know what happens when that firewall fails. They care deeply about your resilience. This is where your incident response capabilities face scrutiny.
A weak or unclear response plan signals risk. It tells the buyer that you might not detect a breach until it is too late, or worse, that you lack the discipline to manage their data safely. This guide cuts through the noise of generic advice. We will examine how to build a SOC 2 Incident Response Plan that satisfies auditors, accelerates sales cycles, and actually works when things go wrong.
What a SOC 2 Incident Response Plan Is and Why It Matters
At its core, an incident response plan (IRP) is a set of instructions that dictates how your organization detects, responds to, and recovers from security incidents.
In the context of SOC 2, this is not just an IT document. It is a formalized control required by the AICPA’s Trust Services Criteria (TSC), specifically under Logical Access and System Operations (CC 7.3, CC 7.4, and CC 7.5).
The definition is straightforward: A SOC 2-aligned IRP documents the specific procedures your team follows to manage unauthorized access, data exposure, or system failures. It must cover the full lifecycle of an event, from the first alert to the final lessons-learned meeting.

Beyond the Document
The difference between having a PDF stored in Google Drive and having a usable plan is what separates a clean audit from a "qualified" opinion. Auditors focus heavily on maturity. They do not just check for the existence of the file; they check for evidence of execution.
During an audit, we often see companies present a template they downloaded five years ago. It references tools they no longer use and roles that no longer exist. This is an immediate red flag. For a SOC 2 Incident Response Plan to be valid, it must mirror reality. It acts as the bridge between your technical stack and your business commitments.
SOC 2 vs. General Incident Response Plans
Many engineering teams already have runbooks for outages. If AWS goes down or a database locks up, they know what to do. However, SOC 2 requires a shift in perspective.
A generic operational runbook focuses on uptime. A SOC 2 plan focuses on the Trust Services Criteria you have selected: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Mapping to Criteria
- Security: How do you handle unauthorized access or privilege escalation?
- Availability: If a DDoS attack hits, how do you restore service within your SLA?
- Confidentiality: If a laptop with customer data is stolen, what is the notification protocol?
Auditors will flag gaps if your plan ignores the non-technical aspects of a breach. For instance, a generic playbook might tell you how to patch a server, but a SOC 2 plan tells you when to call legal counsel and when you are contractually obligated to notify a client.
Types of Incidents Covered Under SOC 2
Clarity on "scope" is vital. Not every blip on a dashboard is an incident. Your plan must distinguish between an event (a user failed a login attempt) and an incident (a user failed 500 login attempts in one minute).
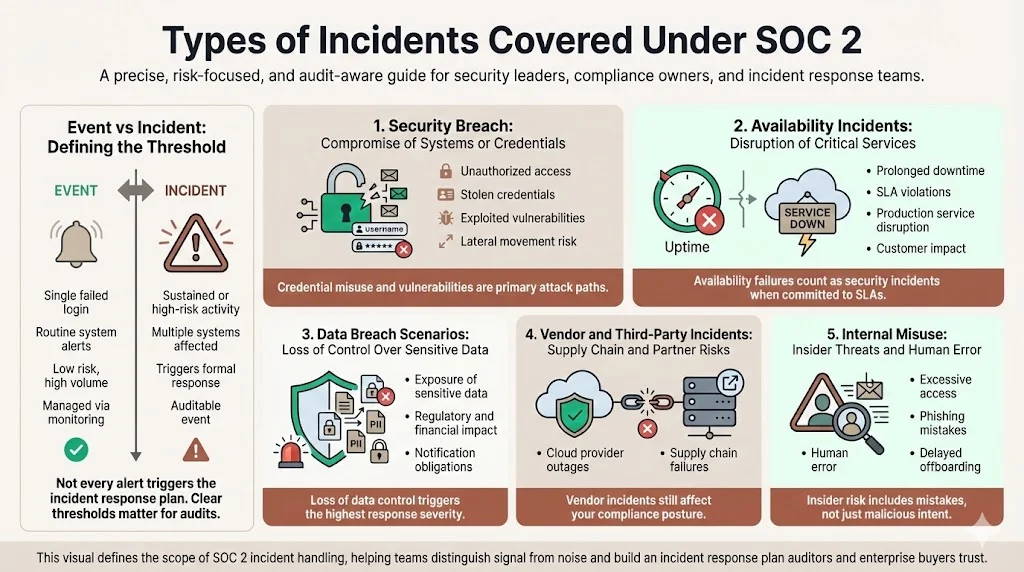
SOC 2 typically governs the following scenarios:
1. Security Breach
This involves unauthorized access to your environment. According to the 2024 Verizon Data Breach Investigations Report (DBIR), stolen credentials remain the number one entry point for attackers, while exploited vulnerabilities saw a 180% increase from the previous year. Your plan must account for these specific vectors.
2. Availability Incidents
If you commit to Availability as a criteria, significant downtime is a security incident. Enterprise buyers often include strict uptime SLAs in their contracts. Your IRP must address how you communicate during these outages.
3. Data Breach Scenarios
This is the nightmare scenario where sensitive data (PII, ePHI) leaves your control. The financial impact is severe; the 2024 IBM Cost of a Data Breach Report found the global average cost of a breach reached $4.88 million, with healthcare breaches averaging nearly $9.77 million.
4. Vendor and Third-Party Incidents
If your cloud provider or a sub-processor suffers a breach, it impacts your compliance posture. SOC 2 requires you to monitor vendor risk. Your IRP should outline what steps you take when a critical vendor goes down.
5. Internal Misuse
Often overlooked, insider threats are a major component of SOC 2. The Verizon DBIR highlights that 68% of breaches involve a non-malicious human element, such as a person falling for a phishing scheme or making an error. This covers employees accessing data they do not need or offboarding failures where access remains active after termination.
Core Components of a SOC 2 Incident Response Plan
To pass a Type II audit—and more importantly, to survive a real attack—your plan needs specific components. Based on our experience supporting 6,000+ audits, these are the non-negotiable elements.
1. Incident Detection and Reporting
How do you know something is wrong? Auditors want to see the technical inputs. This section lists your monitoring tools (e.g., AWS GuardDuty, Datadog, Splunk) and the alerts they generate.
It must also cover manual reporting. If an employee receives a phishing email, is there a clear channel (like a specific Slack channel or email alias) to report it? A "see something, say something" policy is only effective if the "say something" part is defined.
Auditor Checkpoint: They will ask for evidence of your logging configurations. If your plan says you review logs daily, but your system settings show logs are only retained for 24 hours, you have a deviation.
2. Incident Classification and Severity Levels
You cannot handle a lost badge the same way you handle a ransomware infection. Your plan must define severity tiers.
- Severity 4 (Low): Suspicious email, no execution.
- Severity 3 (Medium): Malware detected and quarantined automatically.
- Severity 2 (High): Production service degradation or unauthorized access to non-critical systems.
- Severity 1 (Critical): Data exfiltration, active breach of production data, or total service unavailability.
Defining these tiers prevents panic. It ensures you do not wake up the CEO for a minor bug, but you absolutely wake them up for a Severity 1 issue.
3. Roles and Responsibilities
Who is in charge? In a crisis, decision paralysis is the enemy.
- Incident Commander (IC): Runs the response. They make the tactical calls.
- Technical Lead: Investigates the root cause and implements the fix.
- Communications Lead: Manages internal updates and external statements.
- Legal Liaison: Reviews regulatory obligations.
For smaller teams, the CTO might wear three of these hats. That is acceptable, provided it is documented.
4. Investigation Procedures
This section outlines the steps for triage.
- Validation: Is this a false positive?
- Analysis: What systems are affected? What data is involved?
- Containment Strategy: Do we shut down the server, block the IP, or revoke the key?
Critical Note: Avoid the temptation to "wipe and restore" immediately. You must preserve logs for analysis. If you reboot a compromised instance without taking a snapshot, you destroy the evidence required to understand how the attacker got in.
5. Evidence Preservation
During a SOC 2 audit, you must prove you followed your plan. This means retaining evidence.
- Screenshots of the alerts.
- Logs showing the timestamps of the attack.
- Slack/Teams chat logs from the war room.
- Tickets (Jira/Linear) showing when work started and ended.
This evidence must be stored securely to maintain a chain of custody, ensuring no one tampered with the facts after the event.
6. Containment and Remediation Steps
Containment stops the bleeding. Remediation fixes the wound.
Containment might mean isolating a VPC or disabling a user account. Remediation involves patching the vulnerability, rotating all API keys, or updating WAF rules.
Auditors evaluate remediation proof strictly. If you say you fixed the vulnerability, they will want to see the pull request, the code review, and the deployment log that pushed the fix to production.
7. Communication Plan
Who speaks for the company? Loose lips sink ships—and stock prices.
Your SOC 2 Incident Response Plan must state that only authorized individuals can speak to the press or customers. It should also establish internal cadence. For a Sev-1 incident, the IC might update the executive team every hour. For Sev-3, a daily update might suffice.
8. Stakeholder Notification
This is the section enterprise buyers scrutinize most. If you lose their data, when will you tell them?
Contracts often dictate strict timelines (e.g., "within 24 hours of discovery"). Your plan must reference these contractual obligations. It should list the specific contacts at your client organizations who need to receive the "bad news" email.
Regulatory and Contractual Considerations
SOC 2 does not exist in a vacuum. If you sell healthcare, you are likely a Business Associate under HIPAA. If you sell to Europe, you are a Processor under GDPR.
Your response plan must map to these regulations.
- HIPAA: The Breach Notification Rule requires notification without unreasonable delay and no later than 60 days. However, many enterprise Business Associate Agreements (BAAs) shrink this window to 72 hours or less.
- GDPR: Requires notification to the supervisory authority within 72 hours of becoming aware of the breach.
Failure to map your SOC 2 plan with these laws creates a massive liability. If your SOC 2 plan says "we notify within 30 days," but your BAA says "48 hours," you have a contract breach waiting to happen. At Konfirmity, we map these controls across frameworks so you do not maintain conflicting policies.
Root Cause Analysis and Lessons Learned
The incident is not over when the fire is out. It ends when you understand why it started.
Auditors expect a documented Root Cause Analysis (RCA). We advise using the "5 Whys" technique to drill down past surface-level symptoms.
- Wrong: "The breach happened because Bob clicked a link."
- Right: "The breach happened because our email filter failed to catch the domain (1), and we lacked multi-factor authentication on that specific internal tool (2)."
The output of the RCA must be a corrective action plan. This turns a failure into a control improvement. Perhaps you add a new rule to your IDP or increase the frequency of phishing simulations. This feedback loop proves to auditors that your security program is alive and improving.
Training and Awareness
You cannot hand an employee a complex document during a crisis and expect them to execute it perfectly. Training is mandatory.
Auditors will ask for a list of attendees for your annual security training. But for the IRP specifically, they want to see "Tabletop Exercises."
A tabletop exercise is a simulation. You gather the main stakeholders and walk through a theoretical scenario (e.g., "Ransomware has encrypted our primary database"). You test the plan without the pressure of a real outage.
- Did we know who to call?
- Did we have the phone numbers?
- Did the backup restoration process actually work?
Documenting these sessions acts as proof of competence during your SOC 2 audit.
Plan Testing and Updates
A static plan is a dying plan. NIST SP 800-61 Rev. 2 and SOC 2 standards suggest reviewing and testing your plan at least annually.
Testing pays off. IBM's research indicates that organizations with a dedicated incident response team that regularly tests their plan saved an average of $2 million in breach costs compared to those that did not.
However, you must also update the plan whenever there is a significant business change. Did you switch from AWS to Google Cloud? Your detection tools changed. Did you hire a new VP of Engineering? Your call tree changed.
When we manage programs for our clients, we view the SOC 2 Incident Response Plan as a living code repository, not a dusty binder.
How Auditors Review Your SOC 2 Incident Response Plan
When an auditor looks at your IRP, they are playing detective. Here is their workflow:
- Read the Policy: Does it cover the required criteria?
- Interview the Team: They will ask an engineer, "What do you do if you find a vulnerability?" If the engineer's answer contradicts the document, you have a finding.
- Sample Incidents: They will ask to see the ticketing system export for the audit period. They will pick a few "high priority" tickets and ask for the evidence trail.
- Verify Timelines: If the ticket was opened at 2:00 PM and closed at 2:05 PM, but the logs show activity until 4:00 PM, they will dig deeper.
Auditors are trained to spot inconsistencies. They look for "security theater"—documents that look pretty but have no operational backing.
Common Mistakes That Slow Enterprise Deals
We see many companies rush to "get SOC 2" by downloading generic templates. This approach backfires during the enterprise sales cycle.

1. Overly Generic Templates
If your plan refers to "The Company" instead of your actual name, or references "tape backups" when you are cloud-native, buyers lose trust immediately. It shows a lack of attention to detail.
2. Missing Notification Clarity
Enterprise buyers want to know exactly when they will be told about a breach. Vague language like "we will notify appropriate parties" triggers redlines from their legal counsel.
3. No Proof of Testing
A plan that has never been tested is a hypothesis. Buyers ask for the date of your last tabletop exercise. If that field is blank, your risk score goes up.
4. Plans Unknown to Staff
The worst mistake is a plan known only to the Compliance Officer. If your developers do not know incident reporting protocols, the plan is useless.
How to Keep the Plan Lightweight but Audit-Ready
Complexity is the enemy of execution. You do not need a 50-page thesis. You need a 10-page operational guide.
Write for Use, Not Storage
Use bullet points. Use flowcharts. Make it readable at 3 AM when the server is down and adrenaline is high.
Balance Detail with Speed
Do not document every single command line instruction (those belong in technical runbooks). Document the decision logic and the authority levels.
Assign Ownership Without Overhead
Do not create a heavy committee structure for every small issue. Empower the Incident Commander to act.
At Konfirmity, we advocate for a human-led, managed approach. We implement controls inside your stack—configuring the alerts, setting up the Jira workflows, and running the tabletops—so that compliance is a natural output of good security, not a separate administrative burden.
Conclusion
A strong SOC 2 Incident Response Plan is more than a compliance requirement; it is a competitive asset. When you can demonstrate to an enterprise buyer that you have a tested, mature process for handling their worst fears, you remove friction from the sales process.
Preparedness reduces chaos. It creates a controlled environment where technical teams can focus on fixing the problem rather than arguing about who to call.
For teams selling to the enterprise, the message is clear: Security that looks good in documents but fails under pressure is a liability. Build controls that stand up to buyers, auditors, and attackers.
Frequently Asked Questions (FAQ)
1) What is the SOC 2 incident response plan?
It is a documented set of procedures that an organization follows to detect, contain, and recover from security incidents. It is a mandatory requirement for SOC 2 compliance, ensuring that a company can honor its commitments regarding the security, availability, and confidentiality of customer data.
2) What is the SOC 2 plan?
This generally refers to the broader set of policies and procedures required for a SOC 2 audit. It encompasses incident response, but also covers access control, change management, vendor risk, and HR security. Incident response is just one critical pillar within the larger SOC 2 framework.
3) What are the 5 principles of SOC 2?
These are known as the Trust Services Criteria (TSC):
- Security: The system is protected against unauthorized access.
- Availability: The system is available for operation and use as committed or agreed.
- Processing Integrity: System processing is complete, valid, accurate, timely, and authorized.
- Confidentiality: Information designated as confidential is protected.
- Privacy: Personal information is collected, used, retained, disclosed, and disposed of in conformity with commitments.
4) What are the 7 steps of an incident response plan?
While models vary (NIST has 4 steps, SANS has 6), a complete lifecycle often includes:
- Preparation: Getting tools and teams ready.
- Detection: Identifying the potential threat.
- Analysis: Determining scope and impact.
- Containment: Limiting the spread.
- Eradication: Removing the root cause.
- Recovery: Restoring systems to normal operation.
Lessons Learned: Post-incident review to improve future response.





.svg)




.svg)
.svg)