Most health providers and life‑science firms face procurement questionnaires and security annexes that ask for evidence, not promises. Buyers want proof that access to electronic health records is managed, audit logs exist, and technical controls hold up under stress. When those controls are weak, deals stall and risk grows.
This article, written from the standpoint of Konfirmity’s leadership after running more than 6,000 audits over the past two decades, explains why HIPAA Role-Based Access Control For HIPAA is a keystone in protecting electronic protected health information (ePHI). We will look at the rules that govern data use, discuss how role-based approaches support the “minimum necessary” standard, and walk through a practical access strategy. We also show how real security programs beat “compliance manufacturing” and share insights from our work helping teams shorten audit timelines and strengthen controls.
The stakes are high for healthcare providers. In 2024 alone, data breaches exposed millions of medical records and led to fines approaching $10 million. The average cost of a healthcare breach remains above $7 million, not including legal fees and reputational harm. Beyond direct penalties and remediation, breaches erode patient trust, complicate payer negotiations and delay critical projects. A robust security program grounded in clear access management is therefore more than compliance—it is a strategic necessity.
HIPAA Basics — What Rules Require Access Control
The U.S. Department of Health and Human Services (HHS) issues two major rules under HIPAA that affect access and disclosure:
- Privacy Rule – It covers protected health information in any format. The rule requires covered entities—health plans, providers and clearinghouses—and their business associates to protect PHI and limit its use or disclosure. A central tenet is the “minimum necessary” standard. The rule directs organizations to make reasonable efforts to use or disclose only the minimum amount of information needed to accomplish a task. It further states that internal policies must identify the persons or classes of persons who need access to PHI, the categories of information they need, and the conditions under which they need it.
- Security Rule – This rule is narrower in scope but deeper in technical detail. It covers only ePHI and sets the administrative, physical and technical safeguards that must be in place. Within the technical safeguards, HHS requires regulated entities to implement policies and procedures that allow only authorized persons to access ePHI, maintain audit controls, protect data integrity, authenticate users and secure transmissions. The rule applies to covered entities and business associates alike and requires documented policies and procedures to remain for six years after last use.
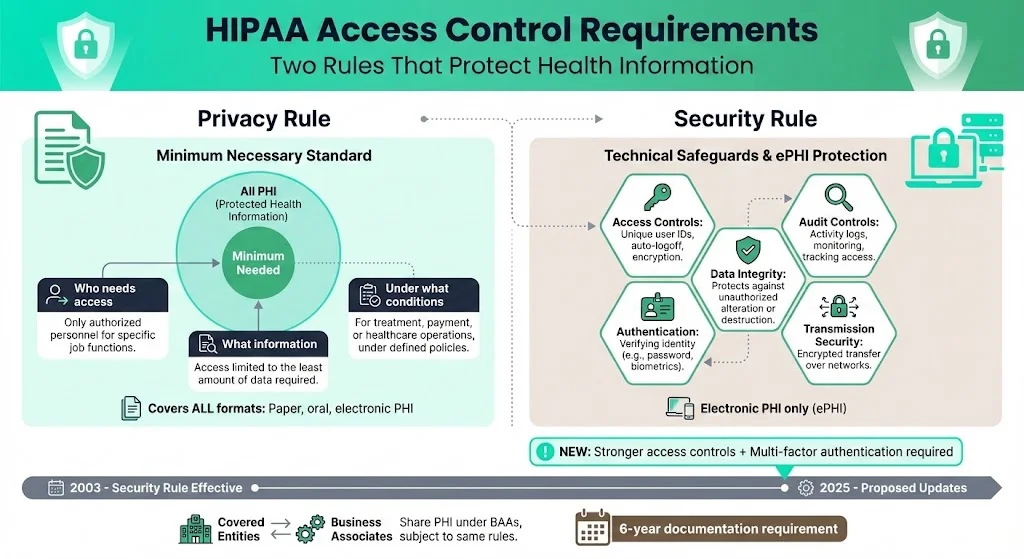
The Privacy Rule explains the minimum necessary standard; the Security Rule defines how to meet it in electronic systems. Together, they require organizations to define roles, restrict access, record activity, and verify identities. The Security Rule has been in effect since 2003, and proposed updates for 2025 emphasize stronger access controls and multi-factor authentication.
Technical and Administrative Safeguards
HIPAA divides security requirements into administrative, physical and technical safeguards. Administrative safeguards involve policies, procedures and workforce management. Physical safeguards restrict access to facilities, workstations and devices. Technical safeguards address systems and data.
Access control sits in the technical category; organizations must implement unique user identifiers, automatic logoff, encryption, and other measures to limit access. However, technical measures alone are not enough. Administrative safeguards, such as a defined security management process, information access management and workforce security, determine who is authorized and how access is granted. Physical safeguards protect devices and storage media. When integrated, these layers support “defense in depth” without relying on a single control.
Implementing HIPAA Role-Based Access Control For HIPAA bridges these administrative and technical safeguards by tying specific permissions to defined job roles. When roles reflect true responsibilities, the technical mechanisms enforce the policies set in administrative safeguards, creating a coherent control environment.
Role-Based Access Control (RBAC) — Definition and Fit for HIPAA
The National Institute of Standards and Technology (NIST) defines role‑based access control as access control based on user roles—collections of access authorizations that reflect a person’s function. In RBAC, permissions are assigned to roles rather than individuals. Users are then assigned to one or more roles based on their job duties. Roles can inherit permissions through role hierarchies, and a role may apply to one or many individuals.
Core components include:
- Roles: Named sets of permissions tied to job functions (e.g., physician, nurse, billing clerk).
- Permissions: Rights to perform actions such as read, create, update or share.
- User-Role Assignment: Mapping of users to roles.
- Role-Permission Assignment: Mapping of roles to permissions.
- Sessions: Instances where a user activates a subset of assigned roles.
RBAC simplifies administration, particularly in large healthcare systems. Instead of granting or revoking permissions for each user, administrators manage roles. This design enforces the least‑privilege principle, making it easier to restrict access to only what is needed. It also clarifies segregation of duties; roles can be segregated so that no single user can both initiate and approve high‑risk actions. Regular audits of roles and permissions support compliance and help catch excess privileges.
Why RBAC aligns with HIPAA
The Security Rule mandates that only authorized persons access ePHI. NIST’s 2024 HIPAA guide instructs organizations to select an access control method—identity‑based, role‑based, location‑based or a combination—and to document how access will be granted. RBAC fits this requirement by explicitly tying permissions to job functions. When roles reflect actual duties, organizations can honor the Privacy Rule’s “minimum necessary” standard and ensure that staff see only the data required to do their jobs.
Under RBAC, auditing becomes more straightforward. Instead of reviewing every user’s unique set of permissions, auditors examine roles and verify that assignments match job functions. The 2025 proposed rule references multi-factor authentication and reminds regulated entities that access controls have been required since 2003. RBAC, combined with strong authentication, satisfies this expectation.
Designing an RBAC Strategy for Healthcare Organizations
Implementing HIPAA Role-Based Access Control For HIPAA is not just a matter of turning on a setting. It requires planning, documentation, and ongoing management. Drawing on lessons from Konfirmity’s managed service and our experience supporting thousands of audits, we suggest the following steps.
1. Identify and Define Roles
Map roles based on real job functions rather than titles. Typical roles in a hospital include physicians, nurses, billing staff, front‑desk workers, auditors and IT support, each requiring different levels of ePHI access. Document each role’s responsibilities and determine what ePHI is needed—read, create, modify or share. Under the Privacy Rule, covered entities must define which classes of persons need access and the categories of information they need.
Avoid assuming that seniority equals more access. Use role hierarchies when appropriate; a senior physician role may inherit permissions from a general physician role and add certain privileges, such as approving medication orders. Role hierarchies simplify management by grouping permissions logically and reducing duplication. They also support career progression without granting blanket rights.
2. Assign Permissions Based on Least Privilege
Assign only the permissions necessary for each role. Resist the temptation to give broad rights “just in case.” In our practice, over-privileged accounts are a common root cause of data breaches. Review each role and remove rights that are not essential. For example, a billing clerk does not need to see clinical documentation.
Avoid creating too many micro-roles. Group similar functions logically to prevent role explosion and unnecessary complexity.
Our clients often reduce dozens of ad-hoc permissions to a handful of well-defined roles. This streamlines onboarding and accelerates due diligence requests. Our managed service also shortens SOC 2 readiness timelines and lowers internal effort compared with self-managed projects.
3. Define Authorization Protocols and Access Procedures
RBAC is not effective without strong identity verification. Combine role assignments with unique user identification and strong authentication. The NIST HIPAA guide requires that each user have a unique identifier and that systems can trace activity back to that user. HHS and NIST now recommend multi-factor authentication to counter stolen credentials.
Establish procedures for granting, modifying and revoking roles through the staff lifecycle. When employees join, change positions or leave, update their assignments promptly. Document who approves access and requires additional authorization for privileged functions. Keep audit logs of role changes, access events and reasons, and integrate RBAC with ticketing systems so requests and approvals are captured automatically. Review logs regularly to detect misuse or misconfiguration.
4. Periodic Review and Role Audit
Roles evolve as organizations change. Conduct regular reviews—quarterly or bi-annual, depending on risk tolerance—to ensure that roles reflect current responsibilities. The NIST guide advises organizations to review and modify personnel access based on periodic assessments and to document those changes. Remove redundant roles, retire unused ones and update permissions when workflows change. Use automated tooling to detect over-privileged accounts and orphaned identities. Regular reviews catch misconfigurations that static design misses and provide auditors with evidence that access is actively managed.
CTA: Book a demo
Integrating RBAC into a Broader HIPAA Security Program
Adopting HIPAA Role-Based Access Control For HIPAA helps align technical controls with policy requirements and the least‑privilege principle across systems and locations.
Combine RBAC with Administrative and Physical Safeguards – Policies and procedures are required under the Security Rule. Document your access control policy and include RBAC as the chosen method for limiting access. Align your role definitions with your broader security management process, risk assessments and business associate agreements. Physical safeguards—like badge readers, locked server rooms and device encryption—protect the hardware that holds ePHI. Access control should extend to the facility; RBAC does not override the need to restrict physical entry. Ensure physical safeguards support technical controls; for instance, limit access to data centers and encrypt any off-site backups.
Workforce Training and Awareness – HIPAA requires all workforce members to understand privacy and security policies, and those handling ePHI need role‑specific guidance. Training should be refreshed regularly and documented.
Incident Response and Monitoring – Combine RBAC with monitoring so unauthorized access is detected quickly. The Security Rule requires audit controls, and NIST recommends reviewing logs regularly. Modern systems trigger alerts when data is accessed outside assigned roles, and RBAC supports rapid containment by revoking the offending role. Provide temporary, time‑bound access for special projects with approvals and automatic revocation, documenting the reason.
Common Pitfalls and How to Avoid Them
Adopting HIPAA Role-Based Access Control For HIPAA reduces risk when done carefully, but common mistakes can undermine its value.
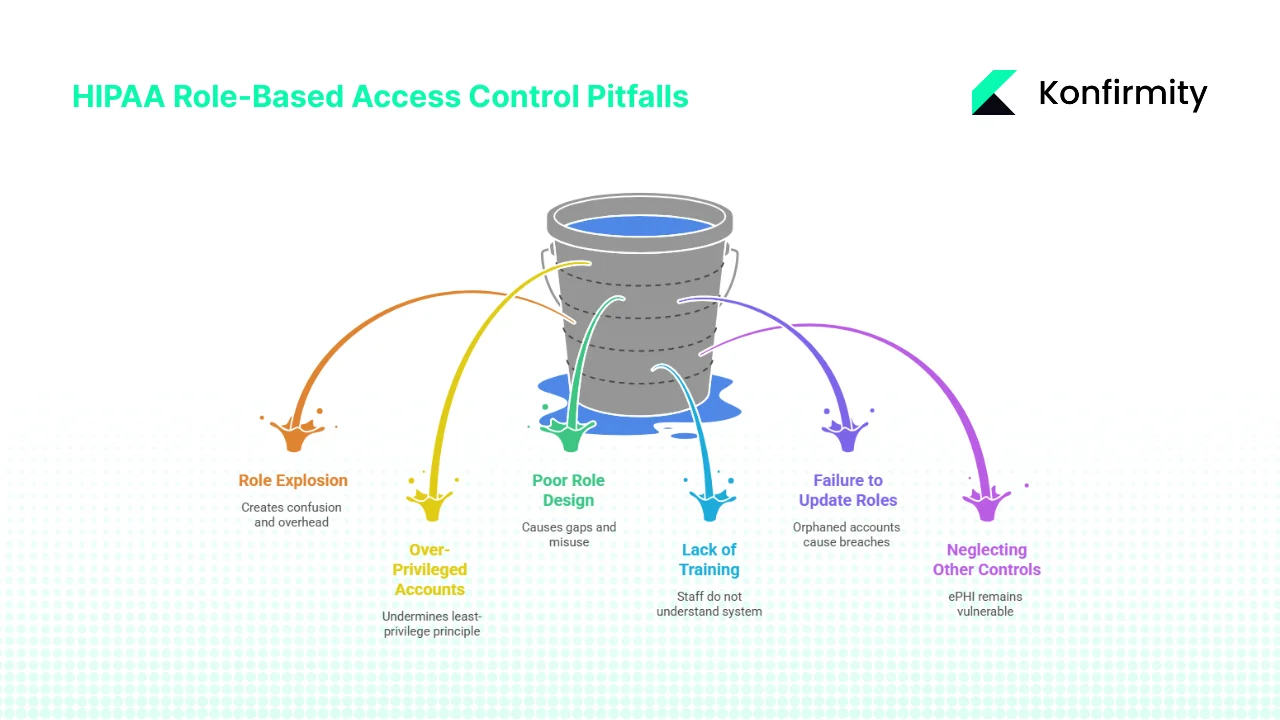
- Role Explosion – Creating too many fine-grained roles leads to confusion and management overhead. To avoid this, group similar privileges and use role hierarchies to inherit permissions.
- Over-Privileged Accounts – Granting broad rights for convenience undermines least-privilege. Review role definitions and remove unnecessary permissions.
- Poor Role Design – Roles should reflect actual duties and workflows. Do not base roles on job titles alone; conduct interviews and observe how staff use data. Poorly designed roles can leave gaps or cause misuse.
- Lack of Training or Unclear Policies – Even a well-designed RBAC system fails if staff do not understand it. Ensure that policies are clear, accessible and reinforced through training.
- Failure to Update Roles – When people change jobs or leave, update or remove their role assignments. Orphaned accounts are a frequent cause of breaches. Use automated provisioning systems to tie role changes to human resources events.
- Neglecting Administrative and Physical Controls – RBAC is only one layer. Without a security management process, risk assessment, incident response, and physical controls, ePHI remains vulnerable.
Market Trends and Enforcement Insights (2024–2025)
Healthcare remains a top target for attackers. IBM’s 2025 Cost of a Data Breach Report shows that the average healthcare breach cost in the United States dropped to $7.42 million, yet healthcare breaches remain the most expensive across all industries. The report notes that average containment time for breaches fell to 279 days, still longer than other sectors.
These trends underscore why HIPAA Role-Based Access Control For HIPAA must be central to any security strategy. By systematically restricting access, organizations can reduce the attack surface and demonstrate to regulators that they are meeting the “minimum necessary” standard.
The HHS Office for Civil Rights is stepping up enforcement. In 2024, the OCR collected over $9.9 million in penalties across 22 enforcement actions related to web tracking tools. Penalties are tiered and can reach more than two million dollars per violation category. The proposed Security Rule update signals that regulators expect stronger controls, including enterprise-wide encryption and multi-factor authentication.
We see organizations that invest in durable security programs—not quick fixes—close deals faster and face fewer findings. Buyers now request evidence of policies, risk assessments and access reviews before signing business associate agreements, so mature RBAC programs integrated with vulnerability management and incident response give firms a competitive edge.
Conclusion
HIPAA compliance is an ongoing program, and access control sits at its core. Implementing HIPAA Role-Based Access Control For HIPAA helps enforce the “minimum necessary” standard, simplifies administration and improves audit readiness. The Security Rule requires technical, administrative and physical safeguards; RBAC supports these requirements but must be paired with strong authentication, policies, training and incident response. Our managed programs reduce internal effort and shorten audit timelines by embedding security controls and evidence collection across SOC 2, ISO 27001 and GDPR. Build controls that stand up to buyers, auditors and attackers, and let compliance follow.
FAQs
1) What exactly is the role of ‑based access control under HIPAA?
Role-based access control ties permissions to roles rather than individuals. Each role reflects a job function, and users receive only the permissions associated with that role. Under HIPAA, this method supports the requirement to limit access to ePHI to authorized persons and simplifies auditing. A well-implemented HIPAA Role-Based Access Control For HIPAA program enforces the minimum necessary principle and makes reviews easier.
2) Do I need to train all employees, even those without direct access to ePHI?
Yes. The Privacy and Security Rules require training for all workforce members. Those who do not handle ePHI still need awareness of privacy practices, and those with access need role‑specific guidance. Training should cover policies, incident reporting and safe handling. Without training, even good technical controls can be bypassed.
3) How often should access permissions be reviewed?
At least annually and whenever roles change. NIST’s HIPAA guide advises organizations to regularly review and modify user rights based on their current duties. In practice, quarterly reviews catch drift sooner and provide fresher evidence for auditors. Use automated tools to detect over-privileged accounts and tie reviews to risk assessments.
4) Can RBAC alone guarantee compliance with HIPAA?
No. RBAC is part of the technical safeguards. It must be integrated with administrative policies, physical security, risk management, training, incident response and monitoring. A HIPAA Role-Based Access Control For HIPAA program supports compliance, but it is not a substitute for a full security program.
5) What if staff need one-time access outside their defined role?
Implement temporary elevation procedures. Grant only the permissions needed for the specific task, set an expiration, and record the authorization and reason. RBAC systems and ticketing workflows make this process manageable. After the task is done, revoke the temporary rights and log the change for future audits. This ensures that exceptions do not become backdoors.





.svg)






.svg)
.svg)