Most enterprise buyers now request assurance artifacts before procurement begins. Whether it is a rigorous security questionnaire or a demand for certification, the message is consistent: without operational security and continuous evidence, deals stall. This happens even when teams believe they are "ready" on paper.
Real readiness requires more than a policy document stating you care about security. It requires proof that your underlying infrastructure—servers, cloud workloads, network devices, and containers—is hardened against attack. This is where ISO 27001 Secure Configuration Baselines become the critical differentiator between a fast sales cycle and a failed audit.
A secure configuration baseline is a defined set of security settings and parameters applied to IT systems to ensure they operate securely. Unlike default manufacturer settings, which prioritize usability and open access, baselines prioritize defense. Within an ISO 27001 Information Security Management System (ISMS), these baselines are not optional housekeeping; they are a mandatory control that links directly to risk management, governance, and threat mitigation.
This guide details how to build, enforce, and monitor baselines that satisfy auditors and enterprise buyers alike.
Why Baselines Are Crucial Within an ISMS
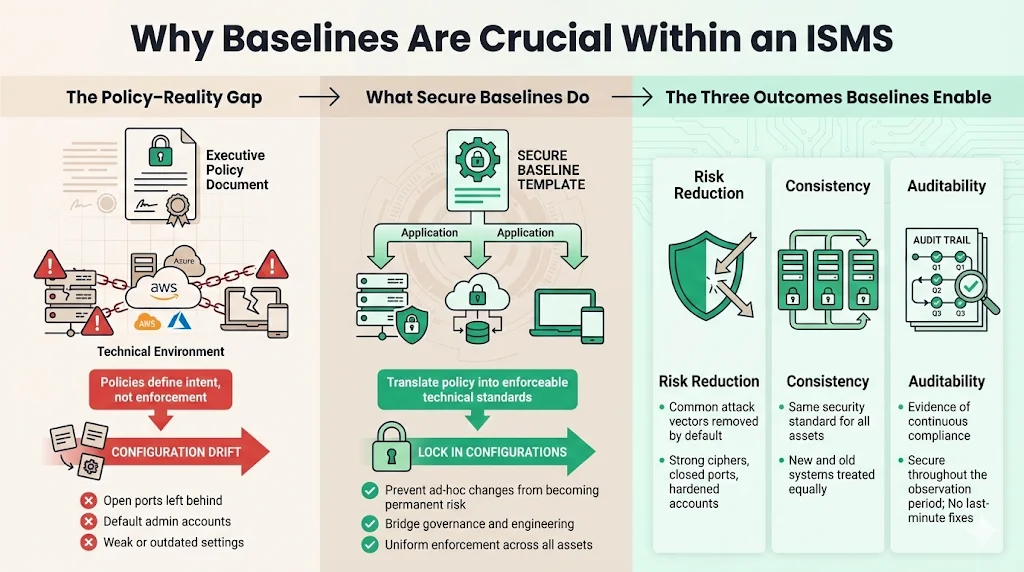
Security governance often fails at the implementation layer. Executives sign off on broad policies regarding data protection, but without technical standards to enforce those policies, the environment remains vulnerable.
Secure baselines bridge the gap between executive intent and technical reality. In our work supporting over 6,000 audits across 25 years of combined expertise, we see a recurring pattern: organizations fail audits not because they lack policies, but because their configurations drift. A developer opens a port for testing and forgets to close it. A default admin account remains active on a production server.
By establishing strict baselines, you achieve three goals essential for ISO 27001 certification:
- Risk Reduction: You eliminate the most common attack vectors (like weak ciphers or open relays) by default.
- Consistency: Every asset, whether spun up today or last year, meets the same security standard.
- Auditability: You can prove to an auditor that your systems were secure throughout the observation period, not just on the day of the audit.
ISO 27001 & Configuration Management
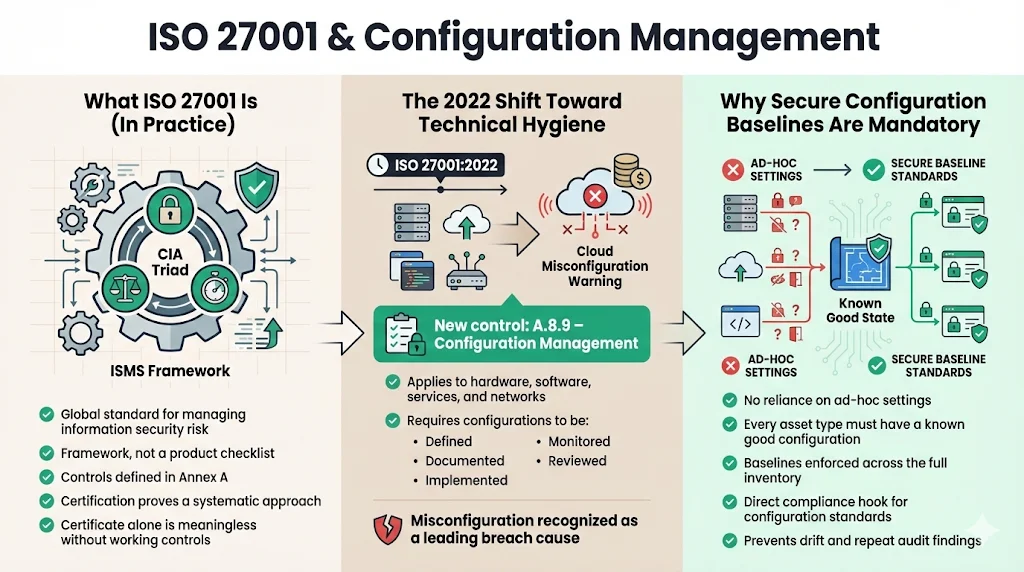
To understand the requirement, we must look at the standard itself. ISO 27001 is the global benchmark for Information Security Management Systems. It does not tell you exactly which firewall to buy, but it dictates a risk-based approach to managing information security.
What ISO 27001 Is
ISO/IEC 27001 provides a framework for organizations to manage their information security risks. It uses a set of controls—outlined in Annex A—to protect the confidentiality, integrity, and availability of data.
For enterprise software vendors and B2B SaaS companies, ISO 27001 is often the table stakes for entering the market. Enterprise clients rely on this certification to verify that their vendors have a systematic approach to managing sensitive data. However, a certificate on the wall is useless if the underlying controls are not functional.
What the 2022 Version Says About Configuration
The 2022 update to ISO 27001 (ISO/IEC 27001:2022) explicitly sharpened the focus on technical hygiene. It introduced Control A.8.9: Configuration Management.
This control requires organizations to establish, document, implement, monitor, and review configurations for hardware, software, services, and networks. The standard recognizes that misconfiguration is a leading cause of data breaches. According to the 2024 IBM Cost of a Data Breach Report, cloud misconfiguration remains one of the most frequent initial attack vectors, accounting for 15% of breaches and costing organizations an average of USD 4.88 million.
Control A.8.9 mandates that you must not rely on ad-hoc settings. You must have a "known good state" for every asset type in your inventory. This is the regulatory hook that makes ISO 27001 Secure Configuration Baselines mandatory for compliance.
Secure Configuration Baselines Explained
A secure configuration baseline is a pre-defined, documented set of specifications for a system or device. It represents the minimum security standard that an asset must meet before it is allowed into a production environment.
Think of it as a "golden image" or a "hardened template." When you deploy a new Linux server, you do not install the OS and start guessing which settings to change. You apply a baseline that automatically:
- Disables unnecessary services and ports.
- Enforces strong password complexities.
- Configures audit logging.
- Removes default manufacturer accounts.
- Restricts root access.
These settings are often derived from industry-accepted standards such as the Center for Internet Security (CIS) Benchmarks or NIST SP 800-70. By adopting these standards, you standardize security across your ecosystem and reduce manual errors—which the 2024 Verizon Data Breach Investigations Report (DBIR) identifies as a significant factor in 28% of breaches.
How Baselines Relate to ISO 27001
Baselines are the operational evidence of your configuration management policy. When an auditor asks how you comply with Control A.8.9, you must not simply say, "We configure our servers securely." You must show the baseline document (the standard) and the evidence that the standard was applied (the implementation).
Baselines support ongoing compliance. In a Konfirmity-managed engagement, we do not view compliance as a once-a-year panic. We handle it as a continuous state. Baselines ensure that as you scale—adding more servers, containers, or employees—your security posture does not dilute. They serve as documented evidence that settings meet security requirements and withstand scrutiny during the audit process.
Connect to Core ISO 27001 Concepts
ISO 27001 Secure Configuration Baselines do not exist in a vacuum. They are the technical enforcement mechanism for several broader ISO concepts.
1) Security Policies & IT Governance
Governance defines the rules; baselines enforce them. Your Information Security Policy might state: "All systems must be protected against unauthorized access." The secure configuration baseline translates that broad statement into technical commands, such as PermitRootLogin no in an SSH configuration file.
This connection strengthens IT governance by setting clear expectations. System administrators and DevOps engineers do not need to debate what constitutes "secure." The baseline defines it. This clarity reduces friction between engineering and security teams, a common challenge in high-growth companies.
2) Risk Assessment & Vulnerability Management
ISO 27001 is fundamentally a risk management standard. You identify risks to your information assets and apply controls to treat those risks. Baselines are a primary treatment method.
If your risk assessment identifies "unauthorized access via default credentials" as a high risk, the baseline mitigates this by mandating the removal of default accounts. In addition, baselines interact heavily with vulnerability management. Vulnerability scanners often check against baselines. If a system deviates from the baseline (e.g., an insecure protocol is re-enabled), the scanner flags it as a vulnerability.
Effective baselines must be informed by risk. If you process highly sensitive PII or ePHI (Protected Health Information), your baselines will be stricter—perhaps disabling USB ports or requiring higher encryption standards—than if you were handling public data.
3) Access Control
Access control (Annex A.5 and A.9) is about ensuring the right people have the right access. While Identity and Access Management (IAM) systems handle the "who," baselines handle the "how."
Baselines enforce access rights at the operating system and application layer. They determine:
- Which users can invoke sudo or administrative privileges.
- Session timeout durations (forcing re-authentication).
- Account lockout policies after failed login attempts.
By baking these rules into the configuration, you prevent "access creep" where users accumulate privileges they do not need. This connects directly with the principle of least privilege, a core tenet of ISO 27001.
Building Secure Configuration Baselines
Creating ISO 27001 Secure Configuration Baselines is a systematic process. At Konfirmity, we follow a structured lifecycle to ensure baselines are effective without stifling operational agility.
1) Define Scope
You cannot secure what you cannot see. The first step is an accurate asset inventory (Control A.5.9). Identify all asset types in the scope of your ISMS:
- Operating Systems (Windows, Linux, macOS).
- Cloud Infrastructure (AWS S3, Azure Blob, VPCs).
- Network Devices (Firewalls, Routers, Load Balancers).
- Databases (SQL, NoSQL).
- Applications and Runtimes (Docker, Kubernetes, Java).
Do not forget SaaS configurations. If you use Salesforce or Microsoft 365, those platforms also require secure configuration baselines to ensure data protection settings are active.
2) Create Baseline Templates
Once you know what to secure, develop the templates. Do not start from scratch. Use established benchmarks like CIS or DISA STIGs as your foundation. These organizations retain thousands of experts to determine the best settings.
However, do not blindly apply a "Profile 2" CIS benchmark (which is highly restrictive) to a general-purpose web server, or you risk breaking functionality. Customize the template:
- Select the Standard: Choose the relevant CIS Benchmark.
- Review Settings: Analyze each setting against your operational needs.
- Harden: Remove insecure defaults (e.g., disable SMBv1, turn off unneeded services).
- Test: Apply the baseline in a staging environment to ensure applications still function correctly.
3) Document & Approve Configurations
Formalization is vital for ISO 27001. Create a document for each baseline (e.g., "Production Linux Server Baseline v1.0"). This document should list the specific settings, the rationale for each (linking back to risk), and the method of implementation.
This documentation serves as evidence. During an audit, you show the auditor this approved document. It proves that management has reviewed and authorized the specific configuration standards.
4) Deploy & Enforce Baselines
Manual configuration is a liability. It is slow, prone to error, and impossible to scale. Modern baselining relies on Infrastructure as Code (IaC) and Configuration Management tools.
- Golden Images: Bake the baseline into the machine image (AMI) used to launch new instances.
- Orchestration: Use tools like Ansible, Chef, or Puppet to apply settings automatically.
- Cloud Policy: Use AWS Control Tower or Azure Policy to prevent non-compliant resources from being deployed.
Automation ensures that every new server born into your environment is compliant from second zero.
5) Monitor & Review
Security is not a point-in-time achievement. Configuration drift occurs when administrators make "temporary" changes to fix an issue and forget to revert them.
You must implement continuous monitoring. Tools should scan your environment against your defined baselines and alert on deviations.
- Drift Detection: If a file permission changes, the system flags it.
- Remediation: Ideally, the system automatically reverts the change to the secure state.
- Review: Review baselines at least annually or when significant technology changes occur (e.g., migrating to a new OS version).
This creates a closed loop of continuous improvement, satisfying the "Monitor and Review" requirement of Control A.8.9.
Common Pitfalls & How to Avoid Them
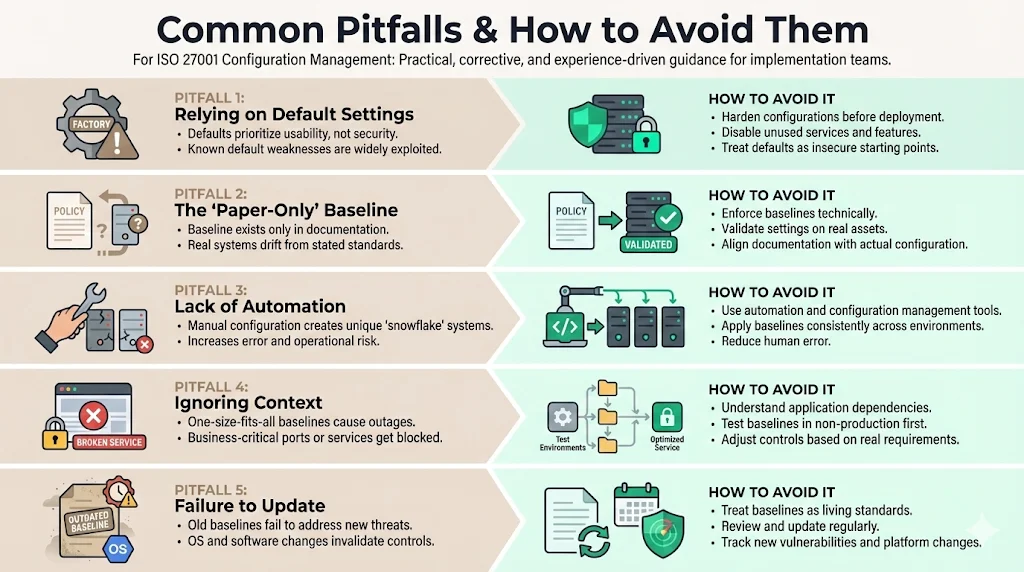
Even with good intentions, organizations often stumble. Here are the pitfalls we see most often in our delivery work.
1) Relying on Default Settings
The "out-of-the-box" configuration is designed for ease of use, not security. Manufacturers enable every feature to ensure the product works for the widest possible audience. Leaving these defaults active invites attackers who script attacks targeting known default vulnerabilities.
2) The "Paper-Only" Baseline
Some organizations create a beautiful PDF describing their security configuration but never implement it technically. Auditors will check sample systems. If the document says "Password Age: 90 Days" but the server says "Never Expires," you will receive a non-conformity.
3) Lack of Automation
Deploying baselines manually is unsustainable. It leads to "snowflake" servers—where every server is slightly unique. This makes troubleshooting difficult and security impossible to guarantee.
4) Ignoring Context
Applying a rigid baseline without understanding application requirements can cause outages. For example, disabling a specific port required for a database cluster to communicate. Always test baselines in a non-production environment first.
5) Failure to Update
Threats change. A baseline from 2021 is likely insufficient for the threat environment of 2026. Baselines must be living documents, updated as new vulnerabilities are discovered and new OS versions are released.
Real-World Use Cases
Example: Hybrid Cloud Security
Consider an enterprise with a hybrid environment: legacy on-premise servers and modern AWS cloud workloads.
- On-Premise: They use Active Directory Group Policy Objects (GPOs) to enforce baselines on Windows servers.
- Cloud: They use Terraform to define the infrastructure state, ensuring all S3 buckets are private and encrypted by default.
- Outcome: Despite the different technologies, the security outcome is consistent. Both environments meet the ISO 27001 Secure Configuration Baselines defined in the ISMS.
Audit Evidence
During an ISO 27001 audit, the auditor selects a sample of five laptops and five servers.
- Without Baselines: The admin frantically logs into each machine, hoping they are configured correctly. Inconsistencies are found. The auditor writes a finding.
- With Baselines: The admin shows the automated report from their configuration management tool, demonstrating that 100% of agents are compliant with the defined profile. The auditor accepts this as evidence of effective control implementation.
Tools and Techniques
The market is flooded with tools, but success depends on selection and operation.
Configuration Management Tools
- Ansible, Chef, Puppet: These tools automate the application of settings. They can check the state of a machine and force it back to compliance if it drifts.
- Microsoft Endpoint Manager (Intune): Essential for managing workstation baselines (Windows/macOS) in a remote-first world.
Cloud Security Posture Management (CSPM)
- AWS Security Hub, Wiz, Prisma Cloud: These tools monitor your cloud environment against standards like CIS and ISO 27001. They provide real-time visibility into configuration gaps.
Scanners
- Tenable (Nessus), Qualys: Traditional vulnerability scanners that also perform configuration auditing against benchmarks.
Choosing the Right Tooling
For enterprise environments, integration is vital. Your configuration tool should feed data into your risk register or GRC dashboard. Avoid tools that operate in silos. At Konfirmity, we utilize a stack that integrates directly into client environments, ensuring that evidence collection is automated and continuous.
How This Supports Enterprise Sales
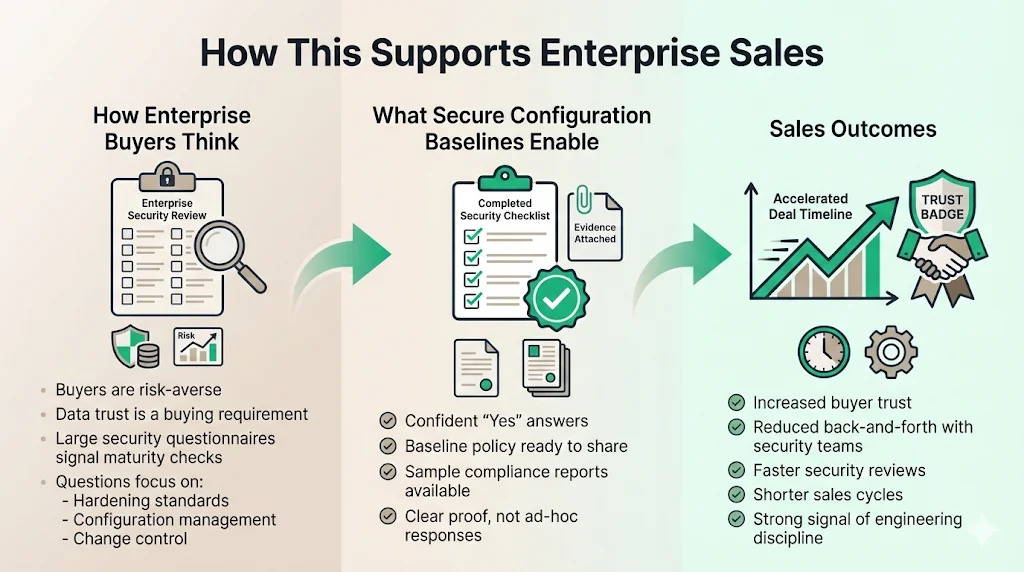
Security is no longer just an IT problem; it is a revenue problem. Enterprise buyers are risk-averse. They will not put their data into your platform unless they trust you.
When a prospect sends a 300-question security assessment, they are looking for maturity. Questions like "Do you have formal hardening standards?" or "How do you manage configuration changes?" are standard.
If you have ISO 27001 Secure Configuration Baselines in place:
- You Answer "Yes" Confidently: You can attach your baseline policy and a sample compliance report.
- You Build Trust: It shows you are not making things up as you go. You have a disciplined, professional engineering culture.
- You Speed Up the Deal: Instead of scrambling for weeks to find answers, you provide evidence immediately.
We have seen clients reduce their sales cycle friction significantly by having these artifacts ready. It signals to the buyer's security team that you speak their language and respect their data.
Conclusion
ISO 27001 Secure Configuration Baselines are more than a compliance checklist item; they are the bedrock of a defensible security posture. They translate high-level governance into concrete technical reality, reducing the attack surface and ensuring consistency across your infrastructure.
For the modern enterprise, the goal is not just to pass an audit but to maintain a state of continuous readiness. By defining rigorous baselines, automating their enforcement, and monitoring for drift, you build a system that is resilient against attacks and transparent for auditors.
At Konfirmity, we believe in a human-led, outcome-driven approach. We don't just advise you to create baselines; we help you implement them inside your stack. We do not just advise—we execute. Start with security, operate it daily, and compliance will naturally follow.
FAQ
Q1: What is an ISO 27001 secure configuration baseline?
A predefined set of system and device settings that reflect hardened, secure settings for infrastructure, aligned with ISO 27001 configuration requirements (Control A.8.9).
Q2: How do secure baselines help with audits?
They act as documented evidence showing systems are configured to meet required controls and security policies. They prove consistency and control over the IT environment.
Q3: How often should baselines be reviewed?
Ideally, at least annually or whenever systems are updated (e.g., major OS release), threats change, or new best practices emerge from bodies like CIS or NIST.
Q4: Do secure baselines replace patching or vulnerability scanning?
No. They work alongside patching and scanning as part of a layered security and vulnerability management strategy. A system can be securely configured but still have a software vulnerability that needs patching.
Q5: Can I just use the default settings from AWS or Azure?
Generally, no. While cloud providers offer secure defaults, the "Shared Responsibility Model" dictates that you are responsible for the configuration of what you put in the cloud. You must explicitly configure settings to meet your specific risk tolerance and compliance obligations.





.svg)





.svg)
.svg)