Most enterprise buyers no longer accept vague assurances. Before a security or software partner is approved, the buyer’s procurement team asks for evidence of control design and continuous operations. A vendor can tick all the boxes on paper and still lose a deal because their onboarding and offboarding practices leave gaps that put sensitive data at risk. In this article, I’ll unpack ISO 27001 Asset Onboarding And Offboarding through the lens of someone who has implemented security programs across dozens of tech stacks. I’ll show why thoughtful asset management matters to enterprise risk management, what ISO 27001 and other frameworks expect, where vendors stumble, and how a human‑led managed service keeps you audit‑ready while shortening sales cycles.
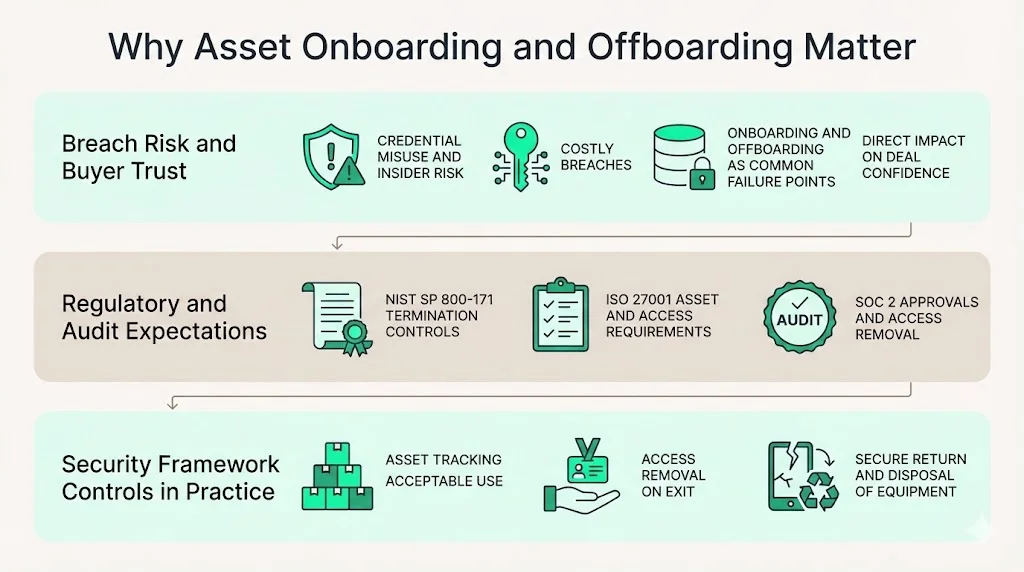
Why Asset Onboarding and Offboarding Matter
Enterprise clients don’t just want to see an “ISO 27001 certificate”; they want confidence that their data will not be mishandled. The cost of a breach underscores why. IBM’s 2024 study found that the average data breach cost rose to US$4.88 million, a 26.4 % increase since 2020. Healthcare breaches were even more expensive, averaging US$9.77 million. Most breaches involve compromised credentials or insider misuse, failures that often occur during employee onboarding or offboarding. A lax exit process lets an administrator retain database access; a sloppy onboarding gives a junior engineer production privileges they never need. These are the sorts of missteps that show up in audit findings, delay contracts, and damage trust.
Regulators and audit bodies pay attention too. NIST SP 800‑171 requires organizations to protect systems during terminations and transfers by ensuring that departed personnel return all system‑related property, complete exit interviews, and have their accounts closed immediately. ISO 27001’s Annex A includes controls on asset inventory (5.9), acceptable use (5.10), return of assets (5.11), responsibilities after termination or role change (6.5), and secure disposal or reuse of equipment (7.14). SOC 2 criteria CC6.2 and CC6.3 require documented approvals for access changes and removal of credentials when access is no longer needed. These requirements illustrate that asset onboarding and offboarding are not administrative niceties; they are critical risk mitigations baked into modern security frameworks.
Common Failures in Join‑Move‑Exit Processes
After supporting more than 6,000 audits over the last decade, I’ve seen patterns repeat across companies of all sizes:
- Manual, email‑driven workflows. When HR sends a spreadsheet to IT and asks them to create or revoke accounts, things fall through the cracks. Accounts remain active long after termination because no one reconciles the lists.
- Incomplete inventories. Teams often maintain a device register but forget about cloud services, SaaS subscriptions, and API keys. When you can’t list your assets, you can’t confirm that they were all recovered or wiped.
- Over‑provisioned access. New hires receive “admin by default” privileges to make onboarding easier. Over time, access drifts away from least privilege. SOC 2’s CC6.2 and CC6.3 call for role‑based approvals and removal of access when no longer needed; ignoring this leads to audit findings.
- Insufficient documentation. During audits, I ask for evidence of offboarding: access removal tickets, asset return receipts, exit interview notes. Too often, none exist. Auditors interpret that absence as a lack of control.
- Delayed revocation. Businesses sometimes wait days to disable accounts so employees can “wrap up work”. Attackers don’t need days; a few hours is enough to exfiltrate data.
These failures aren’t just internal pain points. Enterprise buyers spot them during due‑diligence questionnaires and vendor security reviews. When a vendor can’t articulate how they remove access or track asset returns, deals stall.
These gaps show when an ISO 27001 Asset Onboarding And Offboarding program is missing or immature. Without a structured process, privileges accumulate, devices slip through cracks and audit evidence is scarce. Implementing the program forces you to define tasks, assign responsibility and automate them so that every asset assignment and revocation is traceable.
How ISO 27001 Asset Onboarding And Offboarding Reduce Risk
ISO 27001 (2022) defines an information security management system (ISMS) and provides a catalog of controls (Annex A) from which organizations select based on their risk assessment. Controls relevant to asset onboarding and offboarding include:
- 5.9 Inventory of Information and Other Associated Assets – requires an inventory of information assets, including owners. Without this, you can’t manage assignment, transfer, or return.
- 5.10 Acceptable Use of Information and Other Associated Assets – requires rules for acceptable use and procedures for handling information and assets. This ensures users know what is permitted and what monitoring occurs.
- 5.11 Return of Assets – requires procedures for returning company assets when users leave or change roles. This ties directly into offboarding.
- 6.5 Responsibilities After Termination or Change of Employment – states that information security responsibilities remaining after termination should be defined, enforced and communicated. Examples include maintaining confidentiality, returning assets, and not disclosing information.
- 7.14 Secure Disposal or Re‑Use of Equipment – requires that items of equipment containing storage media be verified to ensure that any sensitive data or licensed software has been removed or securely overwritten before disposal.
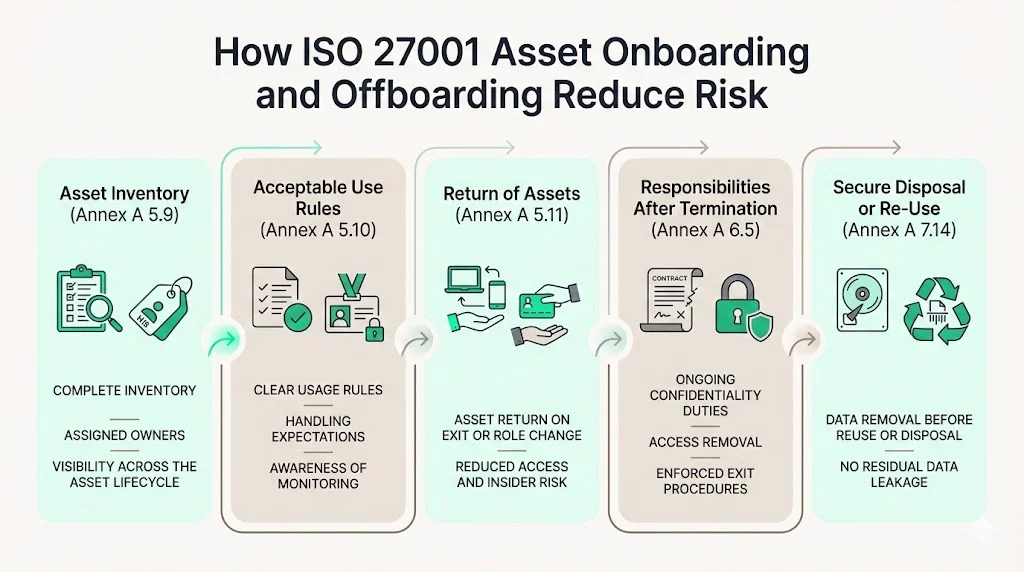
These controls span the asset lifecycle and work together. Inventory tells you what exists and who owns it. Acceptable use sets behavioral expectations. Return of assets and responsibilities after termination codifies exit procedures. Secure disposal ensures that data remnants don’t leak when devices are redeployed or discarded. Together, they establish an auditable trail that shows regulators and buyers that assets are accounted for and sensitive information is not left behind.
What Enterprise Buyers Expect
When a buyer sends a security questionnaire, they aren’t just checking compliance boxes. They are assessing whether your security posture will protect their data. Here’s what I often see in enterprise questionnaires and data processing agreements:
- Detailed asset lifecycle procedures. Buyers ask how you assign assets, how you provision and deprovision accounts, and how you ensure timely return or destruction of hardware. They expect written policies aligned to ISO 27001 and SOC 2.
- Evidence of control operation. A policy alone isn’t enough. Buyers want to see logs showing that access was revoked within hours of termination; asset inventory reports; and audit trails for each offboarded user.
- Regulatory alignment. Healthcare organizations require HIPAA compliance; EU customers expect GDPR clauses; US financial institutions may demand GLBA or FTC Safeguards compliance. The underlying themes (least privilege, audit logs, secure disposal) are similar across frameworks but must be mapped correctly.
- Third‑party oversight. Buyers ask about your downstream vendors. If you outsource onboarding or disposal, you must have service agreements that mirror your own controls, and you should review those vendors’ SOC 2 or ISO 27001 reports.
In my experience, vendors that provide transparent, well‑documented onboarding and offboarding processes sail through procurement faster. Those that scramble to assemble evidence after receiving a questionnaire often lose deals or face extended negotiation.
Understanding Assets Under ISO 27001
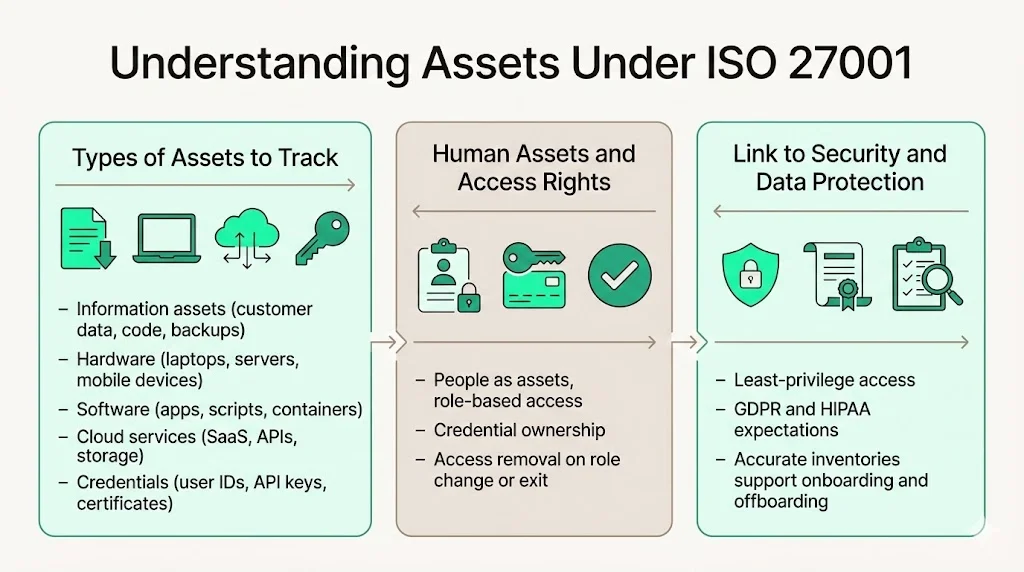
Information, Hardware, Software, Cloud Services and Credentials
An “asset” in ISO 27001 includes any resource valuable to the organization. The standard explicitly calls for an inventory of information and associated assets, including owners. In practice, this means cataloging:
- Information assets: customer data, source code, configuration files, design documents, and backup archives.
- Hardware: laptops, servers, network gear, removable media, mobile devices, and IoT devices.
- Software: operating systems, applications, internal tools, container images and scripts.
- Cloud services: SaaS subscriptions, infrastructure‑as‑a‑service accounts, platform APIs, and cloud storage buckets.
- Credentials: user IDs, API keys, certificates, and tokens.
Each asset should have an owner who is accountable for its security classification, acceptable use, and life cycle. Without ownership, assets drift; no one updates access lists or approves transfers.
Human Assets and Access Rights
Human users are themselves a category of asset because they possess institutional knowledge, roles, and privileges. Access rights must be linked to roles. SOC 2 CC6.3 requires that entities authorize, modify or remove access based on roles, responsibilities or system changes. NIST SP 800‑171 demands that organizations revoke system access and close accounts when individuals leave or transfer. If you classify human assets as part of your asset register, you can tie credentials to identities and roles, review privileges regularly, and document approvals.
Linking to Information Security and Data Protection
Proper asset onboarding and offboarding are the operational glue between your ISMS and data protection obligations. GDPR requires data controllers to ensure that personal data is only accessible on a need‑to‑know basis and that it is deleted when no longer needed. HIPAA mandates that covered entities remove ePHI access immediately upon termination and that devices storing ePHI are sanitized. ISO 27001 provides the structure to manage these cross‑jurisdiction requirements. By maintaining accurate inventories and implementing control‑based onboarding and offboarding, you meet the common denominators across frameworks and demonstrate due care.
Asset Lifecycle Under ISO 27001
The asset lifecycle has four broad phases. Each phase requires controls and documentation.
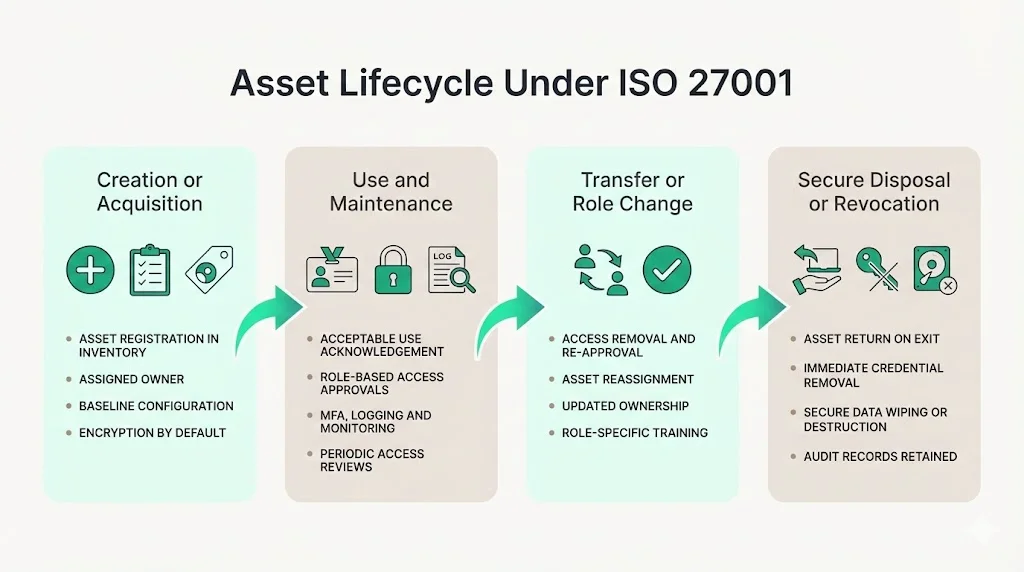
1. Creation or Acquisition
- Identification and registration. As soon as an asset is created or acquired, it should be added to the inventory. ISO 27001 Annex A 5.9 requires maintaining an inventory with owners. For devices, record the serial number, model, user, and location. For information assets, record data classification and retention requirements.
- Assigning ownership. Each asset needs a designated owner who is accountable for its security and life cycle. Owners approve access rights and ensure acceptable use rules are followed.
- Baseline configuration. Hardware and software should be deployed using hardened images. Implement encryption by default (e.g., disk encryption) to support future disposal.
2. Use and Maintenance
- Acceptable use enforcement. Communicate acceptable use policies and obtain acknowledgement from users. ISO 27001 Annex A 5.10 requires rules for acceptable use and documented procedures. Policies should cover expected and prohibited behaviors, monitoring activities, and consequences for violations.
- Access control. Grant access based on role. SOC 2 CC6.2 expects a documented approval from the system owner for each access request. Use multi‑factor authentication and integrate identity providers with HR systems so that changes in status trigger access adjustments.
- Monitoring and logging. Enable audit logs on systems, cloud services, and endpoints. Logs should show account creation, privilege escalation, and data transfers. ISO 27001 Annex A 8.15 (Logging) and 8.16 (Monitoring Activities) emphasize this. Logs become evidence during audits and investigations.
- Periodic review. Perform access reviews quarterly or semi‑annually, as recommended by SOC 2 CC6.2. Owners should verify that access still aligns with job responsibilities and that unused accounts are removed.
3. Transfer or Role Change
- Role change approvals. When an individual moves to a new team, handle it like partial offboarding. Remove access that is no longer required and request new access using the same approval workflow. CC6.2 and CC6.3 stress removal of access when no longer needed and authorizing modifications based on roles.
- Asset reassignment. If hardware or software is transferred, update the inventory and reassign ownership. For SaaS accounts, update the account manager. For information assets, confirm that new owners understand classification and retention obligations.
- Training and awareness. Provide targeted training when roles change. For example, an engineer moving into a security role may need additional training on handling incident data. A sales rep moving into management may need training on regulatory restrictions on data exports.
4. Secure Disposal or Revocation
- Return of assets. Implement formal exit procedures requiring employees and contractors to return all equipment, keys, access cards, and documentation. Conduct an exit interview to remind individuals of ongoing confidentiality obligations. Log asset return and obtain signatures.
- Credential revocation. Terminate or disable all accounts immediately. NIST SP 800‑171 demands that system accounts be closed upon termination; SOC 2 CC6.2 expects timely removal with documented evidence.
- Secure disposal and data wiping. When equipment will be reused or discarded, verify that all sensitive data and licensed software are securely overwritten or removed. Use certified destruction services for hardware that is not reusable. Keep certificates of destruction as evidence.
- Record keeping. Maintain audit trails for disposal activities, including date, method, and responsible party. These records support audit readiness and demonstrate compliance.
Why Asset Onboarding and Offboarding Build Enterprise Trust
Enterprise Risk Management Expectations
Large buyers have mature risk management frameworks. They score vendors based on residual risk across domains like access control, incident response, and personnel security. Weak join‑move‑exit processes increase residual risk because unauthorized users may retain access or sensitive data may remain on devices. An effective ISO 27001 Asset Onboarding And Offboarding program reduces residual risk by enforcing least privilege, timely revocation, and secure disposal. It also supports frameworks like SOC 2 and NIST CSF, enabling cross‑framework reuse of controls.
Regulatory and Compliance Drivers
- ISO 27001:2022 transition. Organizations certified under ISO 27001:2013 must transition to the 2022 version by 31 October 2025, when 2013 certificates expire. The new version clarifies Annex A controls, including those on asset inventory and disposal.
- SOC 2 Type II. Type II reports require evidence of control operation over an observation window (typically three to twelve months). Failing to revoke access promptly is a common deficiency. CC6.2 and CC6.3 require documented approvals and timely removal of access.
- HIPAA. Covered entities must implement administrative safeguards to manage workforce security and implement termination procedures. Delays in disabling accounts can lead to civil penalties if ePHI is exposed.
- GDPR. The General Data Protection Regulation requires controllers and processors to implement technical and organizational measures to ensure a degree of security appropriate to the risk. Unused accounts or forgotten devices storing personal data constitute a breach of Article 32 obligations.
Insider Threat and Access Misuse
Insider incidents account for some of the most damaging breaches. IBM’s 2024 report notes that malicious insiders cause average losses of nearly US$4.99 million. Many of these incidents involve former employees retaining access or disgruntled staff misusing privileges. By implementing immediate revocation and clear exit processes, you reduce the window for insider misuse. Exit interviews also reinforce confidentiality obligations and reduce the likelihood of data theft.
Audit Readiness and Customer Reviews
Audit evidence must show that controls are operating. For onboarding and offboarding, this means:
- Tickets and approvals for every account created, modified or removed. The ticket should reference the request, approval, and date executed.
- Asset return logs, with signatures and date/time. Combine this with your inventory to show that no device is missing.
- Exit interview notes, confirming that the individual understood ongoing responsibilities.
- Disposal certificates, proving that devices were destroyed or wiped.
- Access review records, showing periodic reviews and remedial actions. SOC 2 CC6.2 expects these reviews.
Having this evidence on hand speeds up audits and satisfies customer auditors. In our experience, clients that operate well‑defined join‑move‑exit processes see up to 75% fewer audit findings and shorten procurement cycles by 30% or more, because there are fewer back‑and‑forth clarifications.
ISO 27001 Controls Applicable to Onboarding and Offboarding
Responsibilities After Termination or Role Change (Annex A 6.5)
ISO 27001 (2022) states that information security duties that remain valid after termination or change of employment should be defined, enforced and communicated. Implement this by:
- Contract clauses. Include confidentiality and asset return clauses in employment and contractor agreements. Contracts should survive termination.
- Policy communication. Provide employees with policies during onboarding and remind them during exit interviews. Keep signed acknowledgements.
- Legal enforcement. Engage HR and legal professionals to draft enforceable clauses. For high‑risk roles, consider non‑compete or non‑disclosure agreements.
Acceptable Use of Assets (Annex A 5.10)
ISO 27001 Annex A 5.10 requires that rules for acceptable use and procedures for handling information and other associated assets be identified, documented and implemented. To comply:
- Policy scope. Describe expected and unacceptable behaviors (e.g., no personal use of production databases, no installation of unauthorized software). Include monitoring practices so users know that access is logged.
- Awareness training. Provide mandatory training during onboarding and annual refreshers.
- Enforcement. Establish disciplinary procedures for violations. Document incidents and corrective actions.
Inventory of Assets (Annex A 5.9)
Annex A 5.9 requires an inventory with owners. Best practices:
- Centralized asset register. Use an asset management system that integrates with identity management and procurement tools. Capture physical and logical assets.
- Ownership fields. Record asset owner, classification, business purpose, location, and status. Change ownership when employees move or leave.
- Regular reconciliation. Reconcile the inventory with HR and financial records quarterly. Remove or archive assets that are no longer active.
Secure Disposal or Re‑Use of Equipment (Annex A 7.14)
The control requires verification that storage media is wiped before disposal or reuse. Steps include:
- Drive encryption. Encrypt devices by default to reduce risk if they are lost or stolen. Even with encryption, wipe them before reuse.
- Certified destruction. Use accredited third‑party disposal services. They should provide evidence of destruction.
- Record retention. Maintain certificates, serial numbers, and dates for audit purposes.
SOC 2 CC6.2 and CC6.3: Access Management
CC6.2 requires organizations to register and authorize users before issuing credentials and to remove credentials when access is no longer authorized. CC6.3 requires authorizing, modifying, or removing access based on roles and segregation of duties. These criteria map to ISO 27001’s focus on access control:
- Documented approval workflows. Use ticketing systems integrated with identity providers. Store approvals and timestamps.
- Role‑based access control (RBAC). Define roles and map privileges. Avoid generic admin accounts. Regularly review roles for segregation of duties.
- Timely revocation. Set timing targets (e.g., remove all access within two hours of termination). Automate triggers from HR to identity management to achieve this.
Best Practices for Asset Onboarding Under ISO 27001
An ISO 27001 Asset Onboarding And Offboarding program begins with disciplined onboarding that ensures each asset is registered, configured securely and assigned to an owner from day one.
1) Asset Identification and Inventory
- Capture assets from day one. When an employee is hired or a device is procured, add it to the inventory with details like serial number, MAC address, assigned user, and classification.
- Link assets to business purposes. Document why the asset exists and what data it stores or processes. This helps in risk assessment and disposal decisions.
- Track user provisioning. Record which systems and applications a user can access and link those permissions to the user’s asset record. Regularly reconcile identity provider lists with asset inventory.
2) Secure Access Control During Onboarding
- Role‑based access. Use RBAC and least privilege. Approvals should come from asset owners or managers. Avoid default admin privileges.
- Identity governance. Integrate HR systems with identity and access management (IAM) to automate provisioning. When HR marks an employee as active, IAM triggers account creation with the approved roles.
- Multi‑factor authentication. Enforce MFA on all remote and privileged access.
3) Configuration and Security Setup
- Hardened builds. Use secure baseline images with disk encryption, antivirus, endpoint detection, logging, and vulnerability scanning enabled.
- Logging and audit trails. Configure logs to capture security‑relevant events (authentication, privilege changes, file access). Send logs to a centralized SIEM for monitoring.
- Baseline security. Apply security benchmarks (e.g., CIS Benchmarks) and track deviations through configuration management. Document configuration as code when possible.
4) Security Awareness at Onboarding
- Policy training. Cover acceptable use, data classification, incident reporting, phishing awareness, and regulatory obligations. Make training interactive and role‑specific.
- Incident response responsibilities. Clarify who to contact and what to do when suspicious activity is noticed. Provide contact information for the security team.
- Proof of awareness. Keep records of completed training, quiz results, and signed policy acknowledgements. Auditors will ask for this evidence.
Best Practices for Asset Offboarding Under ISO 27001
1) Access Removal and User Deprovisioning
- Immediate revocation. Terminate access as soon as HR confirms termination. This includes disabling network accounts, removing VPN access, revoking API keys, and removing physical badges. SOC 2 CC6.2 expects removal when access is no longer authorized.
- Handle role changes. If the user transitions internally, perform a partial offboard. Remove access tied to the previous role and provision new access using the onboarding workflow.
- Validation checks. Perform automated scans to detect orphaned accounts on servers, SaaS platforms, and third‑party systems. Use identity governance tools to reconcile accounts.
2) Asset Return and Secure Data Handling
- Device return procedures. Provide a checklist for returning laptops, mobile devices, tokens, keys, badges and documentation. Require sign‑off from both the employee and the receiving administrator.
- Data transfer, retention or deletion. Determine whether data on the user’s devices must be retained (e.g., for legal holds or project continuity) or deleted. Transfer ownership of relevant files to a supervisor or secure archive. Document the handover.
- Protection of customer and enterprise data. Remove sensitive data from local drives, email accounts, and cloud storage before reassigning devices. Use encryption and secure deletion methods.
3) Secure Disposal Procedures
- Data wiping and destruction. Use software that performs multiple overwriting passes or degaussing for magnetic media. For SSDs, use manufacturer‑approved secure erase commands. For devices that are not wipeable, engage certified shredding services. Verify removal of data before disposal.
- Third‑party disposal risks. Vet disposal vendors for compliance with ISO 27001 or R2 (Responsible Recycling) standards. Ensure contracts include confidentiality obligations and reporting requirements.
- Evidence collection for audits. Retain destruction certificates, chain‑of‑custody records, and logs showing that devices were sanitized and removed from the asset register.
Managing Risk Throughout the Lifecycle
Risk Assessment at Each Stage
ISO 27001 requires a risk-based approach. Assess risks when:
- Adding assets. Determine the inherent risks of the asset and assign controls accordingly (e.g., encryption for laptops).
- Changing roles. Evaluate whether new privileges increase risk and whether segregation of duties is maintained.
- Disposing assets. Assess risks associated with residual data and select appropriate sanitization methods.
For high‑risk roles (e.g., database administrators, DevOps engineers), implement additional controls such as privileged access management, session recording, and continuous monitoring. Integrate risk findings into your incident response plan so that the team knows which assets warrant priority containment and investigation.
Audit, Monitoring and Continuous Improvement
- Logging access changes and asset movements. Use automation to record every asset assignment, reassignment, and retirement. Correlate logs with HR events.
- Internal audits and management reviews. ISO 27001 Clause 9 requires planned internal audits and management reviews. Include asset lifecycle controls in these audits. Use findings to improve processes.
- Use audit findings to improve. Track root causes of findings (e.g., manual approvals, outdated inventories) and implement corrective actions such as workflow automation or training.
Role of HR and IT in ISO 27001 Asset Onboarding And Offboarding
Effective asset lifecycle management requires cooperation between HR, IT, security and compliance teams:
- HR initiates onboarding and offboarding events, ensures contracts contain confidentiality clauses, and triggers access changes in a timely manner.
- IT provisions and deprovisions hardware and software, maintains the asset inventory, and ensures secure configuration and disposal.
- Security defines policies, monitors access, and performs audits. It also drives training and awareness.
- Legal and compliance ensure that policies meet regulatory requirements and that contractual obligations extend to third parties.
Enterprise buyers care about this alignment because it demonstrates a mature, cross‑functional approach rather than ad hoc processes. During due diligence, buyers often request RACI charts or process diagrams to validate roles and responsibilities.
Common Mistakes Buyers Watch For
Enterprise buyers and auditors have seen all the shortcuts. They look for signs of the following:
- Manual offboarding delays: Evidence shows that accounts remain active days after termination. Buyers ask for metrics on time‑to‑revoke.
- Incomplete asset inventories: When the inventory doesn’t include cloud services or SaaS subscriptions, buyers question how you manage sprawl.
- Weak access control practices: Generic admin accounts or shared credentials indicate poor security hygiene. Auditors expect unique, traceable identities.
- Missing documentation: Lack of ticket history, policy acknowledgements, exit interview records and destruction certificates is a red flag.
Addressing these gaps ahead of audits prevents last‑minute scrambling and demonstrates maturity.
How Strong Onboarding and Offboarding Support Enterprise Sales
Meeting Security Questionnaires and Due Diligence
Most enterprise procurement processes include extensive security questionnaires that map to ISO 27001, SOC 2, HIPAA and GDPR controls. When you have a documented ISO 27001 Asset Onboarding And Offboarding program, you can answer these questions quickly with evidence. This reduces back‑and‑forth and speeds up deal cycles. In our experience at Konfirmity, vendors that proactively provide control descriptions and evidence complete due diligence 40% faster and often bypass deeper audits.
Shortening Procurement Cycles
Procurement teams often wait for internal audit or legal sign‑off before issuing a purchase order. When the vendor shows they meet ISO 27001 and SOC 2 controls with documented asset lifecycle practices, internal teams have fewer concerns. This can cut four to six weeks off a sales cycle. We’ve seen enterprise clients move from initial contact to contract signing in under 60 days when controls and evidence were ready.
Building Long‑Term Customer Confidence
Strong asset lifecycle management isn’t just about winning the initial sale. It also supports renewals and expansion. When a customer’s security team trusts that you are diligent, they are more likely to expand their use of your platform without reopening a full security review. This leads to longer contract terms and lower churn.
Conclusion: Build Security That Works Under Pressure
Asset onboarding and offboarding are often overlooked, yet they are central to every major security framework. ISO 27001 (2022) explicitly requires an asset inventory, acceptable use rules, responsibilities after termination, and secure disposal. NIST and SOC 2 reinforce the need for timely access revocation and secure hardware disposal. The 2024 IBM breach report reminds us why: breaches are costly and often result from compromised credentials or insider misuse.
As you prepare for enterprise deals, do not rely on checklists alone. Build your program so that security controls operate continuously and generate evidence automatically. Integrate HR, IT and security workflows. Assign ownership and track every asset from cradle to grave. Use role‑based access, automate revocation, enforce acceptable use policies and securely dispose of equipment.
Strong asset lifecycle management is a sign of enterprise readiness. It reduces risk, satisfies auditors, and accelerates sales. In a world where breaches are both common and expensive, security that reads well but fails under pressure is a liability. Start with real security and let compliance follow.
Invest in a mature ISO 27001 Asset Onboarding And Offboarding program and you will see long‑term security and compliance benefits.
FAQs
1) What is the process of onboarding and offboarding?
Onboarding begins with registering an asset or user in the inventory, assigning ownership, provisioning access based on role and configuring the asset securely. Training and policy acknowledgement are part of this phase. Offboarding involves revoking access immediately, retrieving all assets, transferring or deleting data, conducting exit interviews and ensuring that devices are wiped or destroyed. Documentation of each step is essential for audits.
2) What is the ISO 27001 acceptable use of assets policy?
ISO 27001 Annex A 5.10 requires organizations to identify, document and implement rules for the acceptable use of information and other associated assets. The policy defines expected and unacceptable behaviors, sets out procedures for handling information, and informs users of monitoring. Enforcement and regular training ensure that users understand their responsibilities and that violations are managed.
3) What is the IT asset onboarding process?
IT asset onboarding includes registering the asset in the inventory, assigning an owner, configuring the device with hardened settings, and granting access rights based on job role. It also involves recording serial numbers, applying encryption and logging, and providing the user with acceptable use and security awareness training. Each step must be documented.
4) What is onboarding and offboarding in cybersecurity?
In cybersecurity, onboarding is the controlled introduction of a new asset or user into an environment, including inventory registration, secure configuration, and least‑privilege access assignment. Offboarding is the process of safely removing assets or users, which includes revoking access, returning or destroying devices, wiping data and updating the asset inventory. Together, these processes reduce the attack surface and are integral to risk management and incident prevention.





.svg)






.svg)
.svg)