Procurement teams at large companies are no longer satisfied with superficial statements about security. They send detailed questionnaires, request audit reports and want to review how incidents are handled before agreeing to integrate another vendor. For companies that run workloads on Amazon Web Services (AWS), those questions often revolve around the international standard ISO 27001.
Achieving ISO 27001 Cloud Compliance On AWS demonstrates that an organization has a well‑managed security program, not merely a collection of tools. This article aims to show technology leaders and sales teams how to meet that expectation. It blends guidance from industry standards, insights from recent breach reports and lessons from Konfirmity’s experience delivering more than six thousand audits over twenty‑five years.
What enterprise buyers usually ask for
Enterprise procurement teams act as guardians for their organizations. They want confidence that the vendors handling sensitive data will not become the next headline. Typical requests include up‑to‑date audit reports, proof of security controls, incident response procedures, business continuity plans and vendor risk assessments. Recent research shows why: the HIPAA Journal reported in July 2024 that the average cost of a data breach climbed to $4.88 million, with critical infrastructure organizations facing the highest costs. Healthcare breaches remained the costliest, even though healthcare entities saw a modest decline to $9.77 million. Secureframe’s 2025 breach statistics show that the average cost fell to $4.44 million in 2025, yet U.S. incidents averaged $10.22 million. These figures emphasize why buyers insist on seeing incident evidence and control implementations before entrusting sensitive workloads.
Apart from cost, buyers scrutinize operational discipline. They review how often privileged access is reviewed, how vulnerabilities are triaged and patched, how third‑party vendors are managed and whether disaster recovery plans are tested. They expect to see a functioning risk register, a Statement of Applicability (SoA) mapping control applicability and a record of management review meetings. If any of these artefacts are missing or stale, deals can stall.
What ISO 27001 proves (a functioning management system, not just tools)
ISO 27001 is an international standard for information security management systems. It defines best practices for establishing, implementing, maintaining and improving an information security management system (ISMS). The purpose of the standard is to address how organizations set up and monitor controls that keep data secure. Certification verifies that a company’s security processes and controls meet the requirements of the standard during a formal two‑stage audit. An ISMS covers people, processes and technology and requires documentation that clearly defines roles, responsibilities and procedures. It is not a simple check‑the‑box task or a review of tooling; auditors want to see sustained evidence that controls operate effectively over time.
Certification involves internal audits, management reviews, external audits and surveillance audits. As AuditBoard notes, the standard was updated in 2022 and organizations must recertify against the 2022 version by 31 October 2025 to maintain certification. Audits include a Stage 1 documentation review and a Stage 2 assessment of control operation. Surveillance audits follow annually and recertification occurs every three years. Clause 9.2 of the standard requires internal audits at planned intervals to determine compliance, while Clause 9.3 mandates regular management reviews.
In practice, ISO 27001 certification shows that an organization has implemented a risk‑based security program with clear governance. It demonstrates management commitment, documented policies, risk assessment and treatment processes, monitored controls and ongoing improvement. It does not guarantee that no incidents will occur, but it provides assurance that the organization has systematic processes to identify, manage and respond to risks.
ISO 27001 in the cloud: what stays the same and what changes
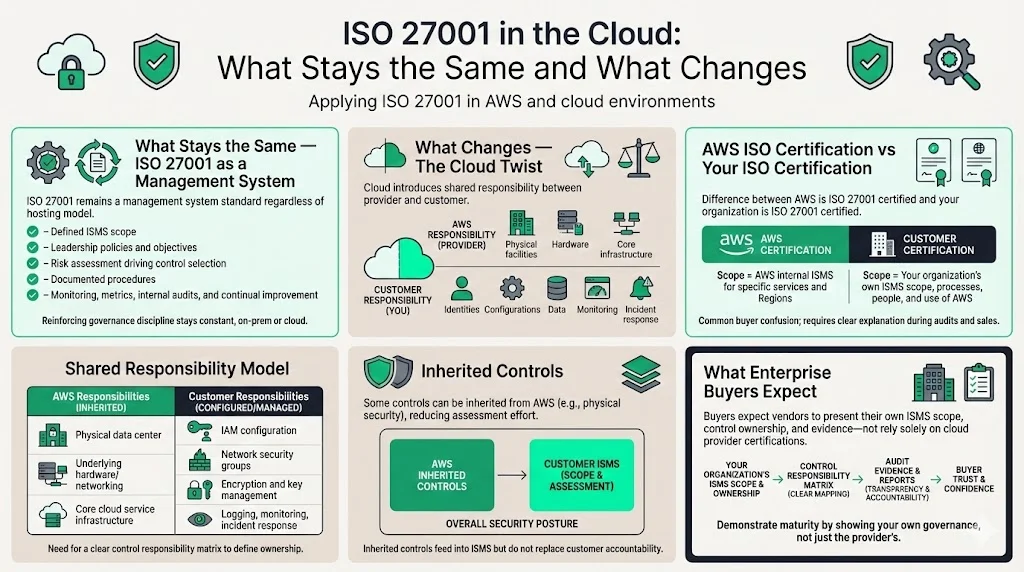
ISO 27001 as a management system standard
The core of ISO 27001 does not change when workloads run in the cloud. It remains a management system standard: leadership defines scope, policies and objectives; risk assessments inform control selection; documented procedures guide implementation; and performance is monitored through metrics and audits. Whether infrastructure is on‑premises or in AWS, companies must establish governance, identify risks, implement controls and continually improve.
The cloud twist: shared responsibility and inherited controls
When infrastructure lives in AWS, responsibilities are split between AWS and the customer. AWS secures the underlying physical facilities, networking and hardware. Customers configure services securely, manage identities, protect data, monitor activity and respond to incidents. Understanding shared responsibility is vital for ISO 27001 Cloud Compliance On AWS. AWS’s own ISO 27001 certification covers its internal security program for certain services and Regions, but it does not confer certification on customers. Buyers often confuse AWS’s certification with a vendor’s own compliance, so it is important to explain that AWS maintains its own ISMS and is audited by independent third parties, yet each organization must design its own ISMS and define its own scope.
The shared responsibility model means some controls can be inherited. For example, AWS handles physical security of data centers. However, configuration of network security groups, identity policies and encryption keys remains the customer’s duty. A clear control matrix helps show which party is responsible for each control.
“AWS is ISO certified” vs “Your organization is ISO certified”
AWS offers a set of services and Regions that are covered by its ISO 27001 certification. This certification attests that AWS has implemented a mature security program for its infrastructure and managed services, and it can reduce the assessment burden for customers. However, an organization that builds on AWS still needs its own ISMS. Certification applies to the organization’s defined scope, which includes its processes, personnel, assets and the way it uses AWS. Enterprise buyers understand this distinction, so vendors should prepare to present their own ISMS scope and evidence, not rely solely on AWS’s certifications.
Define your ISMS scope on AWS
Setting the right scope is essential to ISO 27001 Cloud Compliance On AWS.
Successful certification begins with scoping. Aim for a focused scope that matches how you actually build and run services on AWS. Overly wide scopes increase effort; overly narrow scopes can lead to awkward carve‑outs that buyers question.
Scoping decisions
- Accounts and organizational units – Identify which AWS accounts and organizational units are part of the ISMS. Include production, staging and development environments that host in‑scope services. Avoid “shadow accounts” created outside governance processes, as these can compromise audit outcomes.
- Products and environments – Specify which products or service lines fall under the ISMS. If some services have different security requirements or run on separate infrastructure, consider separate scopes.
- Regions and data residency – List the AWS Regions used to store or process data, and justify their inclusion. Data residency and customer contract terms often dictate which Regions are allowed. Document any restrictions and ensure data does not inadvertently flow to Regions outside scope.
- AWS services – Clarify which compute, storage, database, identity, logging and monitoring services are used. Identify interfaces such as CI/CD pipelines, ticketing systems, HR systems, customer support platforms and vendor integrations.
Typical scope pitfalls for cloud companies
Common mistakes include forgetting about secondary environments, leaving out third‑party SaaS tools that process sensitive data, or failing to include CI/CD systems that deploy code. Unmanaged identity providers and misconfigured logging pipelines can create gaps. It is better to bring these components into scope from the start rather than scramble during an audit. Our team often sees clients surprised by “shadow” accounts created by developers or acquisitions; we help them consolidate or bring those accounts under management.
Template: ISMS scope statement (AWS‑focused)
An ISMS scope statement should clearly describe boundaries. For example:
Scope Statement – The ISMS covers the design, development, deployment and support of the Acme SaaS platform. It includes all code repositories, build pipelines, infrastructure hosted in the AWS Organization under accounts prod-acme, staging-acme and dev-acme, and supporting services such as AWS Identity and Access Management (IAM), Amazon EC2, Amazon RDS, Amazon S3, AWS Lambda, Amazon SQS, AWS KMS, AWS CloudTrail, AWS CloudWatch, AWS Config and AWS Security Hub. The scope also includes corporate processes for personnel onboarding and offboarding, access reviews, vulnerability management, incident management, business continuity, disaster recovery and vendor risk management. Data residency obligations restrict data storage to the ap-south-1 (Mumbai) and us-east-1 (Northern Virginia) Regions.
Such a statement removes ambiguity. It tells auditors and buyers exactly which systems are covered and where data resides.
Build your ISO 27001 control story using AWS’s compliance posture
What AWS’s ISO program covers
AWS’s ISO 27001 certification is performed by independent auditors and covers AWS’s security management processes over a defined scope. The certification attests that AWS has implemented and operates an ISMS for specified services and Regions. Customers inherit certain controls, such as physical security, infrastructure maintenance, redundancy and some service configuration baselines. AWS also publishes assurance documents, including Service Organization Control (SOC) reports and audit artifacts, through AWS Artifact. These documents help customers understand the inherited controls and confirm compliance of underlying services.
Documenting inherited versus customer‑managed controls
To satisfy auditors and buyers, create a shared responsibility matrix that lists each ISO 27001 control theme, indicates whether it is inherited or customer‑managed, and provides evidence links. A simple table can clarify responsibilities.
Documenting responsibilities prevents confusion later. Provide evidence pointers to show where proof lives.
Core ISO 27001 requirements translated to AWS operations
The ISO 27001 standard organizes requirements into clauses and Annex A control themes. Below are practical steps to meet those requirements in AWS environments. Each subsection includes metrics and templates drawn from real audits.
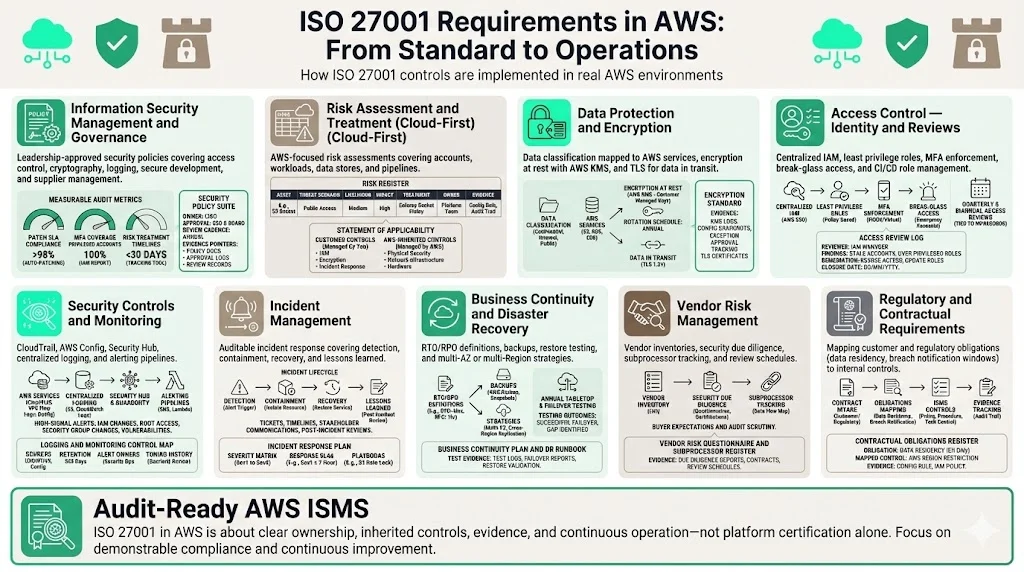
1. Information security management and governance
Establish a set of security policies approved by leadership. Policies should cover information security, access control, cryptography, logging and monitoring, secure development and supplier management. Define ownership for each policy, the approval process and how exceptions are handled. Maintain a schedule for policy review and updates.
Metrics that auditors accept include the percentage of risks with defined treatment plans, the percentage of systems patched within agreed SLA commitments (SLAs) and the completion rate of access reviews. We often measure time from risk identification to treatment, percentage of privileged accounts with multi‑factor authentication (MFA) enabled and the age of unpatched high‑severity vulnerabilities.
Template pack: Security policy suite – Provide a table of contents listing each policy and its owners. This includes the Information Security Policy, Access Control Policy, Cryptography Policy, Logging and Monitoring Policy, Secure Development Policy and Supplier Policy. Each policy document should state purpose, scope, responsibilities, control requirements and evidence collection procedures.
2. Risk assessment and treatment (cloud‑first)
Run a risk assessment that covers AWS workloads, accounts, data stores and pipelines. Identify assets, potential threat scenarios (such as misconfiguration, credential abuse, data exposure or vendor outages), assess likelihood and impact and decide on treatment (mitigate, transfer, accept or avoid). Document existing controls and assign owners for remediation.
Create a risk register with columns for asset/workload, threat scenario, likelihood, impact, existing controls, treatment plan, owner and evidence pointer. Use the Statement of Applicability worksheet to record which controls are applicable, not applicable or managed by AWS. Update these documents whenever significant changes occur or at least annually.
3. Data protection and encryption techniques
Classify data based on sensitivity (such as public, internal, confidential and regulated) and map each classification to storage and processing paths. For each AWS service handling sensitive data, enforce encryption at rest using AWS KMS-managed encryption materials. Ensure encryption in transit by configuring Transport Layer Security (TLS) on endpoints and using modern cipher suites. Define ownership for cryptographic material management, including creation, rotation and access control. Document exceptions and approval processes.
Template: Encryption Standard – Outline minimum encryption requirements, such as mandatory use of customer‑managed KMS keys for S3 buckets, RDS, DynamoDB and EBS; TLS 1.2 or higher for APIs; and rotation of keys every twelve months. Provide a table for exceptions with justification, approval authority and temporary controls. Include evidence pointers, such as KMS rotation logs and encryption configuration snapshots.
4. Access control: identity, permissions and reviews
Implement a centralized identity strategy using AWS IAM and single sign‑on. Enforce least‑privilege permissions through managed policies and roles. Require multi‑factor authentication for all human users, particularly administrators. Design break‑glass procedures for emergencies and document their use. Map privileged access paths, including console, Command Line Interface (CLI) and CI/CD roles.
Perform periodic access reviews (quarterly for privileged roles; biannual for general roles). Compare actual access with approved access, remove unnecessary permissions and document completion. Use automated tools or scripts to generate lists of current access and cross‑reference with HR records. Record evidence in an access review log.
Template: Access Review Procedure and Log – Define the steps for conducting reviews, including who generates the report, who verifies it and who approves remediation. Include a log with columns for account, role/user, reviewer, review date, issues found, remediation actions and closure date.
5. Security controls and monitoring
Establish baseline logging across all services. Enable AWS CloudTrail in all Regions and forward logs to a central account with write‑once storage. Use AWS Config and Security Hub to detect misconfigurations and gather evidence. Implement alerting for high‑severity events using AWS CloudWatch, Amazon SNS or third‑party systems. Maintain runbooks for responding to alerts.
Define signal thresholds to reduce noise. Focus on high‑value events such as changes to security groups, new IAM users, root account usage, failed login attempts and high‑severity vulnerabilities. Assign owners to each alert category and record response times.
Template: Logging and Monitoring Control Map – List log sources (CloudTrail, VPC Flow Logs, application logs), retention periods, alert types, owners and locations of evidence. Include tracking of detection tuning and evaluation of false positives.
6. Incident management (auditable response)
Design an incident lifecycle that covers detection, triage, containment, eradication, recovery and lessons learned. Define severity categories based on customer impact and regulatory obligations. Keep incident response plans up to date and accessible.
Auditors expect to see tickets, timelines of actions, communications with stakeholders and post‑incident actions. Maintain a post‑incident review process that records root causes, corrective actions and prevention measures. Link incidents to risk assessments and update controls accordingly.
Template: Incident Response Plan and Post‑Incident Review Template – Provide step‑by‑step guidance on who to notify, how to classify incidents, response steps for each severity category and how to document incidents. Include a severity matrix that ties response times to impact on customers and regulatory requirements.
7. Business continuity and disaster recovery
Define recovery time objective (RTO) and recovery point objective (RPO) for each service tier. Implement backups for databases and critical configurations and test restore procedures regularly. Use multi‑Region and multi‑Availability Zone architectures where necessary. Document failover procedures and ensure staff know how to execute them.
Conduct tabletop exercises and live failover tests at least annually. Keep records of test dates, participants, results, issues identified and corrective actions. Provide these records as evidence during audits.
Templates – A Business Continuity Plan outlines roles, contact lists, communication protocols, alternate workspace arrangements and restoration sequences. A Disaster Recovery runbook provides step‑by‑step instructions for restoring services, along with a test report capturing outcomes and improvements.
8. Vendor risk management (a priority for buyers)
Maintain an inventory of all third‑party services, data processors, subcontractors and critical contractors. For each vendor, perform due diligence that covers security controls, audit reports, data processing agreements and exit plans. Document vendor assessments and track their renewal schedule.
Auditors and buyers will ask about sub‑processors and the frequency of vendor reviews. Keep a register with vendor name, services provided, data classification, location, assessment results, contract expiration and next review date. Involve legal and procurement teams in approving vendors.
Templates – A vendor risk assessment questionnaire covers topics such as data handling, encryption, access controls, incident history and regulatory compliance. A subprocessor register lists all sub‑processors with contact information, service description, security certifications and review cadence.
9. Regulatory and customer contractual requirements
Enterprises often impose contractual obligations such as data residency, breach notification windows and specific data protection measures. Map each requirement to internal controls, assign an owner and track evidence. For instance, a customer may require notification of a breach within seventy‑two hours; this maps to incident management procedures and communication plans. Use a one‑page intake sheet to capture requirements during contract negotiation, then ensure those requirements flow into the ISMS.
Compliance auditing on AWS: making evidence collection repeatable
Use AWS Audit Manager with care
For teams pursuing ISO 27001 Cloud Compliance On AWS, AWS Audit Manager provides some automation.
AWS Audit Manager provides a prebuilt ISO/IEC 27001:2013 Annex A framework that helps collect evidence from AWS services and produce reports. It gathers data from CloudTrail, Config, Security Hub and other services to show compliance with selected controls. For example, Audit Manager can show whether encryption is enabled on S3 buckets or if IAM password policies meet certain criteria. Automation reduces manual effort, supports continuous monitoring and shortens audit preparation. As the KirkpatrickPrice article notes, automatic data sources include CloudTrail, Config, Security Hub and daily or weekly API calls. The tool also integrates with IAM to control access to evidence.
However, the Audit Manager has limitations. It can only collect evidence from AWS; it does not cover on‑premises or other cloud environments, and it does not verify control design or guarantee passing an ISO audit. Many procedural controls – such as risk assessments, access reviews, incident documentation and management reviews – still require manual evidence. Therefore, use an Audit Manager to complement, not replace, your evidence plan.
Evidence plan: what to collect and where it lives
Prepare an evidence index that lists each control, the evidence item, the system of record, the owner, the frequency and a link to the evidence. Categories include policies and approvals, risk assessments and SoA, access reviews, incident records, disaster recovery tests, vendor reviews and change management samples. For example, the evidence item for access reviews might be “Q3 2025 Access Review Log” stored in a GRC system and owned by the Security Operations lead.
Assign owners to each evidence item and set a schedule for collection (quarterly, biannual or annual). Make sure evidence is accessible to auditors but protected from unauthorized access.
Auditing processes: internal audits and sampling strategy
Internal audits should occur at least quarterly for high‑risk controls and annually for the full ISMS. Each internal audit should follow a checklist covering all applicable controls. Record findings, severity, root cause, corrective actions, due dates and closure evidence. Use a findings tracker to manage remediation and report progress to leadership.
Sampling involves selecting a subset of evidence to verify control operation. For example, auditors may review five change tickets from the past quarter to check whether peer review, testing and approval were documented. Define sampling criteria to balance thoroughness with efficiency.
Infrastructure as code guardrails
Preventive controls reduce drift and surprise findings. Implement policy‑as‑code to enforce rules across AWS accounts. Tools like Pulumi CrossGuard provide prebuilt policy packs that match ISO 27001 control themes. Top rules to implement include blocking public S3 buckets, enforcing encryption on storage, restricting open security group ports, requiring MFA for console access, preventing wildcard IAM permissions and ensuring CloudTrail is enabled in all Regions. Write these policies once and integrate them into deployment pipelines so that non‑compliant configurations are blocked before they reach production.
Templates and checklists bundle
These materials accelerate ISO 27001 Cloud Compliance On AWS.
The following list summarizes the templates referenced in this article. Use them as building blocks for your ISMS:
- Core ISMS templates – ISMS Scope Statement, Information Security Policy, Risk Assessment Register, Risk Treatment Plan, Statement of Applicability worksheet, Control Matrix (Inherited/Shared/Customer).
- Operational templates – Access Review Procedure and Log, Incident Response Plan and Post‑Incident Review Template, Logging/Monitoring Control Map, Change Management SOP (CI/CD and infrastructure), Vulnerability and Patch SOP with SLA table.
- Resilience and third‑party templates – Business Continuity Plan, Disaster Recovery Runbook and Test Report, Vendor Risk Assessment questionnaire, Subprocessor register and review schedule.
- Audit execution templates – Audit Evidence Index, Internal Audit Checklist and Findings Tracker, Management Review agenda and minutes template.
Providing these documents to auditors and buyers demonstrates maturity and readiness.
Conclusion
Enterprise buyers and healthcare providers demand evidence of operational security. A successful program begins by scoping your ISMS to match how you run services on AWS, conducting risk assessments, selecting and implementing controls, collecting evidence and repeating the cycle. ISO 27001 Cloud Compliance On AWS is not a one‑time project but a continuous program. Our experience shows that clients who regard security as an ongoing function rather than a project reduce findings, accelerate buyer approvals and shorten sales cycles. Typical SOC 2 readiness can take four to five months with our managed approach compared to nine to twelve months when self‑managed; our clients often see a 75 percent reduction in internal effort and higher audit pass rates.
In the next 30 days, define your ISMS scope, start a risk assessment and draft your SoA. Within 60 days, implement core policies, begin access reviews, set up logging and monitoring, and start vendor assessments. By 90 days, complete your evidence index, run an internal audit and prepare for an external certification audit. Package proof for buyers by providing an SoA excerpt, audit letter, control overview and important policies. Build security that operates daily and ISO 27001 Cloud Compliance On AWS will follow.
Frequently asked questions
1. Is AWS already ISO 27001 certified, and does that make my company certified too?
AWS maintains its own ISO 27001 certification for a defined scope of services and Regions. This certification demonstrates that AWS operates a compliant ISMS. Your organization is not certified by association; you still need your own ISMS and audit. AWS’s certification can help reduce the assessment burden by allowing you to inherit certain controls.
2. Which AWS Regions and services are covered under AWS’s ISO 27001 certification?
AWS publishes detailed documentation on the Regions and services within scope through AWS Artifact. Check the latest ISO certificates to identify covered Regions and services. When defining your ISMS scope, include only those Regions and services that are both in scope for AWS and used by your workloads.
3. How does AWS Audit Manager help with ISO 27001 audits?
AWS Audit Manager provides a prebuilt ISO/IEC 27001:2013 Annex A framework and collects evidence from AWS services such as CloudTrail, Config and Security Hub. It automates evidence gathering and organizes it for auditors. It does not evaluate control design or guarantee compliance; manual processes and evidence are still needed.
4. Will AWS Audit Manager guarantee we pass an ISO 27001 audit?
No. Audit Manager only collects technical evidence from AWS; many procedural controls require manual documentation. Passing an audit depends on the design and operation of your ISMS, not the tool.
5. What evidence do enterprise customers usually ask for during vendor review?
Common requests include your ISO certificate (if obtained), a SoA excerpt, security policies, incident response process, access review proof, vulnerability management process, disaster recovery test results and vendor management approach. Having these materials ready can accelerate due diligence.
6. What’s the fastest way to show progress if we’re not certified yet?
Provide a defined ISMS scope, a current risk register with treatment plans, a draft SoA with real evidence links and a schedule of internal audits. Buyers often accept “audit‑ready” signals when they see concrete artefacts.
7. How can we keep AWS controls from drifting between audits?
Use preventive guardrails such as policy‑as‑code to block misconfigurations and enforce standards. Monitor for drift using Config and Security Hub, and remediate quickly.
8. Do we need ISO 27001:2013 or ISO 27001:2022?
The most recent version is ISO 27001:2022. Organizations must recertify against the 2022 version by 31 October 2025 to maintain certification. Some tools still reference 2013 control mappings, so you may need to map controls to both versions during the transition.
9. Why do buyers care so much about evidence?
Breach costs continue to rise, with 2024 seeing an average cost of $4.88 million and U.S. breaches averaging $10.22 million in 2025. Evidence of controls and incident handling gives buyers assurance that you can protect their data and respond effectively when incidents occur.





.svg)





.svg)
.svg)