Procurement teams at large buyers now demand proof of security and compliance before signing anything. Long questionnaires and addenda have become standard in healthcare and enterprise deals. Without operational security and continuous evidence, deals stall—even when teams think they’re “ready” on paper. The 2022 update to ISO 27001 added Control A 5.23, which requires policies and procedures for acquiring, using, managing and retiring cloud services. This was no surprise; research shows that 96 percent of organisations use at least one cloud service. The cloud simplifies infrastructure, but it introduces shared responsibilities and rising risks. Cybercrime is growing more expensive too. IBM’s 2025 Cost of a Data Breach report found the global average cost fell slightly to $4.44 million, yet U.S. breaches climbed to $10.22 million, with the average incident lasting 241 days. Healthcare organisations saw 725 reported breaches in 2023, exposing more than 133 million records and 168 million in 2023. Attackers increasingly exploit cloud misconfigurations and weak controls.
In this guide, I share a practical roadmap for ISO 27001 compliance on Azure. It reflects lessons from delivering more than 6,000 audits over 25 years of combined expertise at Konfirmity. Our team implements controls in client stacks and maintains evidence year‑round, not just for a one‑off audit. The article explains why ISO 27001 matters in the cloud, how Azure’s certification fits into the shared responsibility model, and what steps your team must take to become audit‑ready. Examples and templates help you translate theory into action.
Understanding ISO 27001 and Its Relevance to Cloud Services
For teams pursuing ISO 27001 compliance on Azure, understanding the standard itself is the first step. ISO 27001 is an international standard for creating and maintaining an information security management system (ISMS). It sets requirements for establishing policies, assessing risks, applying controls and monitoring effectiveness. The core goals are confidentiality, integrity and availability. Unlike prescriptive frameworks, ISO 27001 allows organisations to adapt controls to their risk environment, which is why it applies to any sector or size.
Core Principles and Scope
ISO 27001’s structure starts with clauses on context, leadership and planning. The standard then lists Annex A controls spanning organisational, people, physical and technological areas. Since ISO 27001:2022, the controls map to the 2022 edition of ISO 27002. Organisations define their scope—such as specific business units, data sets or cloud subscriptions—and must document a Statement of Applicability explaining which controls are in scope and why. Internal audits and management reviews ensure continual improvement.
Relevance to Cloud Context
When planning ISO 27001 compliance on Azure, consider how cloud computing changes risk. Cloud computing introduces shared infrastructure, multi‑tenancy and flexible provisioning. Organisations might assume the provider manages all security. The U.S. National Security Agency warns that customers often incorrectly assume the provider safeguards resources outside its remit. The shared responsibility model requires customers to secure their data, endpoints, identities and configurations. Microsoft’s own guidance states that in any cloud deployment, you always own your data and identities and are responsible for protecting them. Whether you use Infrastructure‑as‑a‑Service (IaaS), Platform‑as‑a‑Service (PaaS) or Software‑as‑a‑Service (SaaS), the workload responsibilities vary.
ISO 27001 provides a framework for governance that extends naturally to the cloud. Control A 5.23—added in the 2022 revision—requires structured processes for acquiring, managing and exiting cloud services. It calls for clear policies, risk assessments, defined roles, and secure exit strategies. Cloud control guidance also encourages encryption, access controls and incident response planning. That means you can align your cloud security posture with ISO 27001’s risk‑based approach.
Complementary Standards for Cloud
When building ISO 27001 compliance on Azure, you may need more than ISO 27001 alone. Although ISO 27001 covers information security broadly, cloud‑specific guidance is available through ISO 27017 and ISO 27018. ISO 27017 outlines additional controls for cloud service providers and customers, focusing on multi‑tenancy, data isolation and monitoring. ISO 27018 focuses on personal data protection in public clouds, complementing GDPR obligations. Frameworks like NIST CSF 2.0 (released in February 2024) provide a taxonomy of broad cybersecurity outcomes to manage risk and emphasise governance and supply‑chain considerations. Using these frameworks together helps organisations address both security and privacy requirements across jurisdictions.
Azure’s ISO 27001 Compliance — What It Means (and Doesn’t)
Azure’s certification is a starting point for ISO 27001 Cloud Compliance On Azure, not a finish line. Microsoft Azure has achieved ISO/IEC 27001 certification for its core infrastructure and many services. This means a third‑party auditor has verified Microsoft’s information security management system and controls. When you deploy workloads on Azure, you benefit from this baseline. However, Microsoft is clear that you always retain responsibility for protecting data, identities, accounts and access management. Compliance is shared: the provider secures the physical infrastructure and platform; you must configure your resources correctly.
What Azure Covers
Azure’s certification covers data centres, networks, hardware and core services like Virtual Machines, storage, databases and Kubernetes. It includes policies for physical security, environmental controls, change management and incident response. Microsoft publishes audit reports that customers can request under non‑disclosure agreements. Azure also supports other frameworks such as SOC 1/2/3, CSA STAR, FedRAMP and HIPAA/HITRUST, giving you a baseline for multiple compliance requirements.
What You Must Cover
Your organisation must design and implement the controls that ISO 27001 calls for. That includes defining the ISMS scope, performing risk assessments, writing policies and applying technical controls. You must maintain identity and access management, encryption, monitoring, incident response and business continuity. In other words, Azure’s compliance does not automatically make your workloads compliant. You must use Azure features correctly—role‑based access control (RBAC), multi‑factor authentication (MFA), Azure Policy, Azure secrets vault, Monitor and Backup—to implement your controls. Azure provides templates and blueprints, but you still need to align them with your policies and verify them through audits.
Why Cloud Compliance Matters
Enterprise buyers and regulators increasingly require evidence of security and privacy controls. In the context of ISO 27001 Cloud Compliance On Azure, several factors drive this trend:
- Regulatory pressure: Data‑protection laws (GDPR, HIPAA, California’s CCPA/CPRA) impose strict obligations on controllers and processors. For healthcare, the U.S. Office for Civil Rights reported 725 healthcare data breaches in 2023 involving 500 or more records and over 133 million records exposed. Breaches are becoming more severe, with 2023 seeing 168 million records compromised and 26 incidents exceeding one million records. OCR backlog data show 857 breaches under investigation as of January 2023. These numbers underscore the scale of compliance risk.
- Financial impact: IBM’s 2025 report shows a global average breach cost of $4.44 million, but U.S. organisations face $10.22 million. Even with faster detection (241 days on average), fines and response costs drive up expenses.
- Client expectations: Enterprise procurement teams ask for security attestations (SOC 2 Type II, ISO 27001 certificates, HIPAA compliance) before onboarding vendors. Without these, deals slow down and renewals become uncertain. Companies that handle protected health information (PHI) must also sign business associate agreements and show HIPAA safeguards.
- Risk management: Misconfiguration and weak access controls remain top causes of cloud breaches. The NSA emphasises that good security results from understanding and upholding the shared responsibility model. Customers must configure services properly across IaaS, PaaS and SaaS. Attackers exploit misconfigurations, poor identity management and unpatched systems.
Compliance is therefore not just a checkbox; it’s a fundamental component of trust. Showing evidence of controls builds credibility with buyers and reduces the risk of costly incidents.
Steps to Achieve ISO 27001 Cloud Compliance On Azure
This section outlines steps to achieve ISO 27001 Cloud Compliance On Azure. A structured program will help your organisation demonstrate control effectiveness and reduce audit friction.
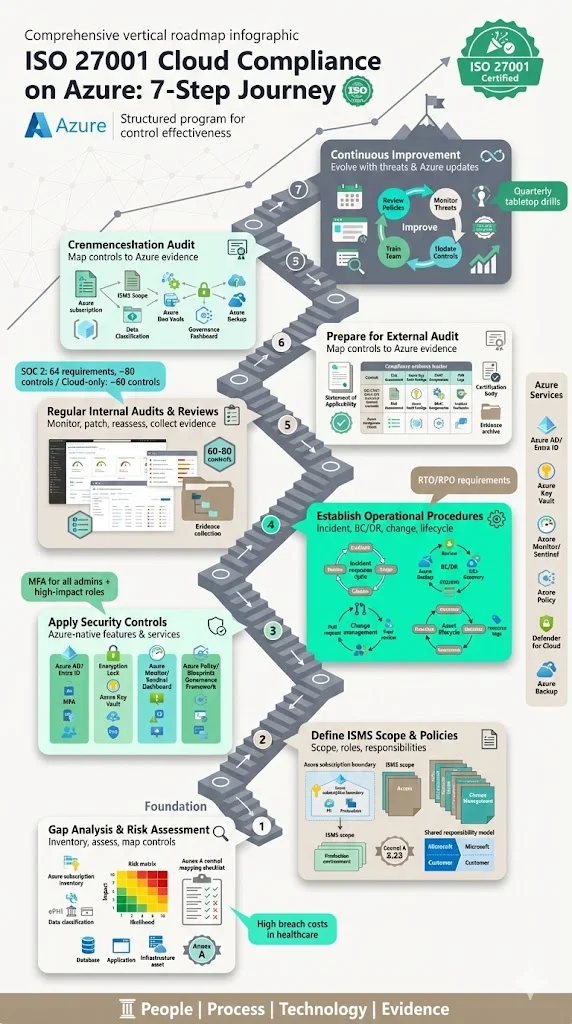
1. Perform a Gap Analysis and Risk Assessment
Inventory assets: Start by listing data sets, applications and infrastructure within your Azure subscriptions. Identify sensitive data (ePHI, PII, financial records) and map where it resides.
Assess risks: Evaluate threats like unauthorised access, data loss, ransomware, misconfiguration, legal violations and operational disruption. Use risk matrices to rank impact and likelihood. Keep in mind the high breach costs noted earlier and the increase in healthcare breaches.
Map to ISO 27001 controls: Compare your existing controls to Annex A. Determine which policies, procedures or technical measures are missing. Control A 5.23 requires structured processes for cloud services. Document gaps across access management, encryption, monitoring, incident response, vendor management and business continuity.
2. Define the ISMS Scope and Security Policies
Scope definition: Decide which Azure subscriptions, environments and applications fall under your ISMS. For SaaS vendors, this might include all production subscriptions and supporting services like identity providers and logging pipelines.
Write policies: Draft clear, actionable policies covering access management, data classification, encryption, logging, incident response, change management and asset lifecycle. For cloud services, specify responsibilities across your team and the provider. Control A 5.23 advocates defining roles and responsibilities and establishing robust service agreements with confidentiality, integrity, availability and incident management provisions. Include security considerations when acquiring new services and requirements for secure exit.
3. Apply Security Controls Using Azure Features
Access controls: Use Azure Active Directory (Entra ID), RBAC and Privileged Identity Management to enforce least‑privilege. Require MFA for all administrators and high‑impact roles. Implement Conditional Access policies to restrict access based on device state, location or user risk. For sensitive workloads (ePHI), implement just‑in‑time access and review entitlements regularly.
Encryption: Enable encryption at rest for storage accounts, databases and managed disks. Use Azure secrets vault to manage encryption secrets and tokens. Turn on TLS for all communications. For regulated data, use customer‑managed cryptographic material and double encryption where required.
Logging and monitoring: Activate Azure Monitor, Activity Logs and Diagnostic Logs for all resources. Forward logs to a Security Information and Event Management (SIEM) or use Microsoft Sentinel. Set up alerts for anomalous activities such as failed logins, privilege escalations and configuration changes. Keep logs for the retention period required by your policies or laws.
Configuration baselines: Use Azure Policy and Azure Blueprints to enforce consistent configurations. Policies can audit or deny non‑compliant deployments. Blueprints help deploy resource groups with pre‑approved templates, RBAC assignments, policies and resource locks.
4. Establish Operational Procedures
Incident response: Define a process that covers detection, triage, containment, eradication and post‑incident review. Specify roles, responsibilities and communication channels. For cloud services, ensure you understand how to raise support tickets with Microsoft and how to collect forensic evidence. Document this in your incident response plan.
Business continuity and disaster recovery: Use Azure Backup and Site Recovery to meet recovery time objective (RTO) and recovery point objective (RPO) requirements. Test backups regularly. For mission‑critical services, design high‑availability architectures across Availability Zones or regions.
Change management: Implement a change‑control process for infrastructure as code and manual changes. Use pull requests, peer reviews and automated testing to detect misconfigurations before deployment.
Asset lifecycle management: Track provisioning, configuration, maintenance and decommissioning. Tag resources with owners, classifications and environment (e.g., dev, test, prod). Remove or reassign access when employees or contractors leave.
5. Perform Regular Internal Audits and Reviews
Continuous monitoring: Assess the effectiveness of controls by reviewing logs, alerts and compliance dashboards. Use Azure Security Center (Microsoft Defender for Cloud) to identify misconfigurations and vulnerabilities.
Patching and vulnerability management: Apply updates to operating systems, containers and third‑party software promptly. Use vulnerability scanning tools and threat intelligence. For workloads processing sensitive data, align patching timelines with CVSS severity and regulatory obligations.
Periodic risk reassessment: Re‑evaluate risks whenever there are changes in business processes, architecture or threat landscape. Update your risk register and treatment plans.
Evidence collection: Prepare for audits by retaining policy documents, risk assessments, access reviews, incident reports, backup records and system logs. Use templates to standardise evidence. A typical SOC 2 Type II audit covers 64 requirements and often evaluates around 80 controls. For cloud‑only organisations, the average control count drops to about 60. ISO 27001 certification also requires internal audits and management review at planned intervals.
6. Prepare Documentation and Evidence for External Audit
Certification bodies will ask for your Statement of Applicability, risk assessments, policies, procedures and evidence of controls operating effectively. Create a compliance evidence tracker to map each ISO 27001 control to Azure settings, policies and documents. For example, map the encryption policy to Azure secrets vault configuration, the access management policy to RBAC and PIM assignments, and the incident response plan to runbooks and ticket logs. Provide evidence of at least one incident or test per control to demonstrate operating effectiveness.
7. Continuous Improvement
Security is a moving target. Regularly review and update policies to reflect new threats, business changes or Azure updates. Monitor Microsoft’s feature releases and service retirements. Engage your team in quarterly tabletop drills and awareness training. Encourage a security‑by‑design mindset so that compliance becomes an outcome of good engineering rather than a last‑minute scramble.
Examples and Templates
These templates can assist your ISO 27001 Cloud Compliance On Azure project. They are practical examples; customize them for your environment.
ISMS Scope Document
- Context: Describe the organisation, mission, stakeholders and external issues.
- Scope: List Azure subscriptions, resource groups and services covered by the ISMS.
- Exclusions: Explain any business units or systems outside scope.
- Interfaces: Describe dependencies on third‑party services, such as identity providers or payment gateways.
- Information classification: Identify data types (e.g., PHI, PII, public data) and their sensitivity.
Risk Assessment Matrix (Sample)
Access Control Policy Snippet
- Roles: Define roles such as System Owner, Administrator, Developer, Support and Auditor.
- Permissions: Map roles to Azure RBAC permissions. Use built‑in roles where possible; create custom roles only if necessary.
- Approval workflow: Document the process for granting access, including who approves and how requests are logged.
- MFA requirements: Require MFA for all privileged roles and remote access.
- Periodic review: Conduct quarterly access reviews to verify that permissions match job functions. Remove unnecessary privileges immediately.
Incident Response Plan Outline
- Detection and Reporting: Describe how incidents are detected (alerts, user reports, anomaly detection) and how they should be reported (ticket, hotline, chat channel). Provide clear criteria for what constitutes an incident.
- Triage and Classification: Assign severity levels based on impact and urgency. Identify the incident coordinator.
- Containment and Eradication: Outline steps to isolate affected systems, revoke compromised credentials, and block malicious traffic.
- Communication: Establish internal and external communication protocols. For breaches involving personal data, include regulatory notification procedures.
- Recovery: Define how to restore systems from backups, verify integrity and monitor for recurrence.
- Lessons Learned: Document the root cause, corrective actions and control improvements.
Backup and Disaster‑Recovery Plan
- Backup frequency: Daily for databases, weekly for file shares, monthly for full system images.
- Storage locations: Use geo‑redundant storage for critical backups. Keep offline or immutable copies when required by regulation.
- Restore procedures: Document how to restore from backups, including testing steps and expected recovery times.
- RTO/RPO: Specify acceptable downtime and data loss windows for each system.
Audit Checklist / Evidence Tracker
Hypothetical Case Study
Consider a SaaS provider handling appointment scheduling for clinics. They host their application on Azure Kubernetes Service (AKS) with a PostgreSQL database in Azure Database for PostgreSQL. They process PHI and must comply with HIPAA and ISO 27001. Using the templates above, they define an ISMS scope covering production and staging subscriptions. During the risk assessment, they identify ransomware and misconfiguration of AKS clusters as high risks. They mitigate these by enabling Azure Defender for Kubernetes, using RBAC and network policies, and implementing daily database backups. Their access control policy enforces MFA and least‑privilege roles for engineers. During the internal audit, they discover an outdated container image lacking security patches; they update the image and implement a vulnerability scanning pipeline. By maintaining logs and incident records, they prepare for an external ISO 27001 audit and can show evidence of continuous control operation.
Mapping ISO 27001 Cloud Compliance On Azure Controls to Azure Features and Cloud Security Practices
The table below maps selected ISO 27001 Cloud Compliance On Azure control areas to Azure capabilities and general cloud practices. Use this as a quick reference when designing your ISMS.
For workloads processing personal data, ISO 27018 and privacy regulations add specific obligations around data minimisation, purpose limitation and rights of data subjects. Map these requirements to Azure features such as Purview for data cataloguing and compliance manager for assessment tasks.
Common Pitfalls and How Busy Teams Can Avoid Them
Assuming Azure’s certification covers everything. Many teams believe that deploying on a certified cloud automatically makes them compliant. In reality, you must implement and operate your own controls. The NSA emphasises that both the customer and the cloud service provider are accountable for securing cloud environments.
Poor documentation. Without a defined ISMS scope, policies and evidence collection, audits become painful. You need version‑controlled policies, risk assessments and change logs. Tools like Confluence or Notion are not substitutes for a systematic evidence repository. A managed service provider can organise these artefacts and provide continuity as staff turnover occurs.
Configuration drift. Manually applied settings drift over time. Use infrastructure‑as‑code (Terraform, Bicep) and policy enforcement to keep environments consistent. Schedule regular scans with Defender for Cloud or third‑party tools to detect deviations.
Neglecting operations. Backups, incident response drills, patching and access reviews are often treated as afterthoughts. They are critical evidence points in a SOC 2 Type II or ISO 27001 audit. Failing to test backups or simulate incidents can lead to extended outages or non‑compliance. Konfirmity’s managed service includes weekly backup verification and quarterly incident drills.
Ignoring privacy and data‑specific requirements. If you process PHI or personal data, you must consider HIPAA and GDPR obligations. OCR statistics reveal that 239 percent more hacking incidents occurred between 2018 and September 2023, and 2023 had 168 million breached records. Data‑specific risks require encryption, auditing and strict access control, plus Data Processing Agreements with vendors.
Underestimating human factors. Insider threats and improper offboarding can lead to breaches. Enforce training, separation of duties and timely revocation of access. Document these processes and collect evidence.
Practical Tips
- Automate where possible: Use Azure Policy and Blueprints for consistent deployment. Automate evidence collection using continuous compliance platforms or scripts.
- Schedule regular reviews: Set quarterly risk assessments and monthly access reviews. Use dashboards to track control effectiveness.
- Assign clear responsibilities: Define a compliance owner, security champion and audit coordinator. Keep roles separate to avoid conflicts of interest.
- Start small: Begin with a limited scope—perhaps one critical application—and expand as controls mature. Achieving SOC 2 Type II readiness often takes 4–5 months with a managed service versus 9–12 months self‑managed. Our clients reduce internal effort from 550–600 hours to around 75 hours per year, freeing engineers to focus on product development.
- Treat compliance as continuous: Don’t view certification as an end state. Monitor changes in frameworks and cloud services. Use improvement logs to track adjustments.
Conclusion
ISO 27001 is a powerful framework for building a repeatable security program, and Azure’s certification gives a strong foundation. Yet the shared responsibility model means you must design, implement and operate controls yourself. The 2022 addition of Control A 5.23 underscores the need for structured processes for acquiring, managing and retiring cloud services. With breach costs averaging millions of dollars and healthcare incidents hitting record numbers, the stakes are high.
ISO 27001 Cloud Compliance On Azure is a continuous effort. Konfirmity’s human‑led, managed service helps companies build these programs correctly. We implement controls inside your stack and keep you audit‑ready year‑round. Our approach focuses on outcomes—secure systems, reduced findings, faster sales cycles and peace of mind. Security that looks good on paper but fails under pressure is a liability. Build your program once, operate it daily, and let compliance follow.
FAQ
1) Does ISO 27001 cover cloud security?
Yes. ISO 27001 is an information‑security management standard that applies to cloud environments. The 2022 update introduced Control A 5.23, which requires policies and procedures for acquiring, using, managing and retiring cloud services. Additional guidance comes from ISO 27017 for cloud services and ISO 27018 for privacy.
2) Is Azure ISO compliant?
Yes. Microsoft Azure is certified against ISO/IEC 27001, meaning an independent auditor has assessed its information security management system. Azure’s compliance covers infrastructure and many services, but you retain responsibility for your data and configurations.
3) Does Microsoft have ISO 27001?
Yes. Microsoft has ISO 27001 certification for its cloud services, including Azure. You can request audit reports through the Service Trust Portal. However, certification does not automatically extend to your workloads; you must implement your own controls.
4) Is Azure cloud PCI compliant?
Azure supports PCI DSS compliance through features like dedicated infrastructure, encryption and logging. The platform provides attestation of compliance and guidance for customers to build PCI‑compliant systems. Achieving PCI compliance still requires proper configuration, segmentation and continuous monitoring by your organisation.





.svg)





.svg)
.svg)