Most enterprise buyers now ask for assurance artifacts before procurement. Security questionnaires, data processing agreements, and privacy addenda can stall deals for weeks if there is no evidence behind them. Organisations that process personal data at scale need an approach that treats privacy and security as two sides of the same coin. In this landscape the concept of ISO 27001 Consent Management has gained traction because it links privacy consent with the controls and audit trail expected of an information security management system (ISMS). As we work with hundreds of engineering and legal teams each year at Konfirmity, we see that consent is not an add‑on; it has to be integrated into risk management and access controls from day one. This article sets out how to embed consent into your ISMS, how ISO 27001 ties to other frameworks like GDPR and ISO 27701, and why a human‑led managed service can shorten sales cycles for enterprise buyers.
Why consent management matters for enterprise sellers
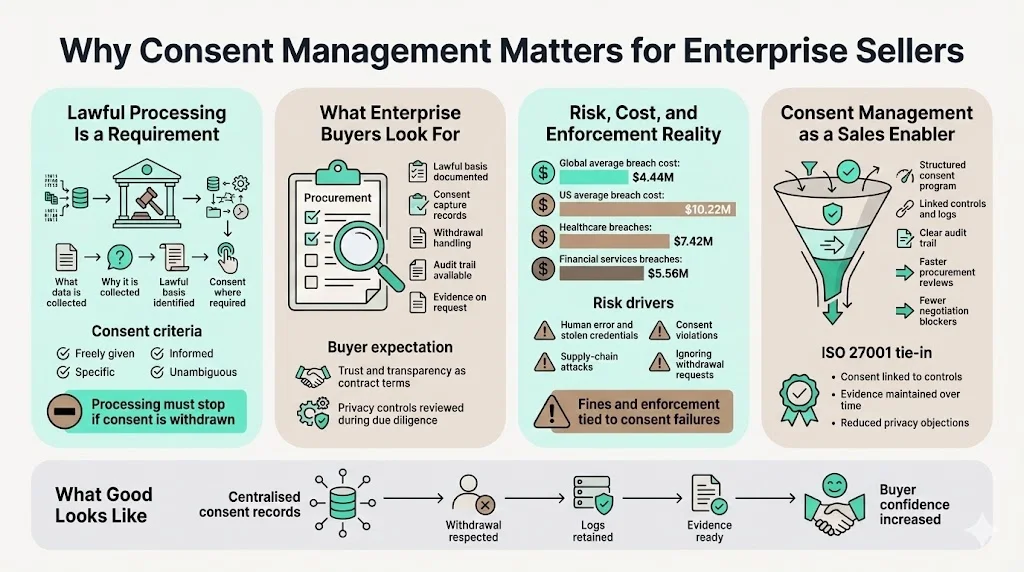
When you sell to large companies or healthcare providers, procurement teams don’t just ask if you have implemented security controls – they ask for evidence that personal data is handled lawfully. Laws such as the EU General Data Protection Regulation (GDPR) prohibit processing personal data unless it is allowed by law or a data subject has given consent. Consent must be freely given, specific, informed, and unambiguous. In the context of enterprise sales, that means you need to know what data you collect, why you collect it, and whether you have a lawful basis for it. Trust and transparency are no longer marketing slogans; they are contractual requirements. Buyers want to see that you can stop processing if consent is withdrawn and that you have an audit trail showing when and how consent was captured. This is where an ISO 27001 Consent Management program can accelerate sales: it gives you a structured way to link consent to controls, logs, and evidence.
Recent cost and enforcement trends underscore why consent management is not optional. Data breach statistics for 2025 show that the global average breach cost reached $4.44 million, while U.S. organisations faced costs of $10.22 million. Healthcare breaches averaged $7.42 million, and financial services saw $5.56 million. Human error and stolen credentials contributed to 68% of breaches, while supply‑chain attacks doubled from 15% to 30% of breaches. Regulators have also started to focus on consent; failing to respect withdrawal or relying on a different lawful basis after a subject opts out can result in fines. For enterprise sellers, any weakness in consent handling quickly becomes a point of negotiation or a blocker in procurement. A structured consent program improves the trust posture and reduces the risk of losing a deal due to privacy concerns.
How ISO 27001 fits into the bigger picture
The standard at a glance
ISO/IEC 27001:2022 is one of the world’s best‑known standards for an information security management system (ISMS). The International Organisation for Standardisation explains that it provides guidance for establishing, implementing, maintaining, and continually improving an ISMS. Conformity with ISO 27001 means a company has put in place a system to manage risks related to the security of data. The standard promotes a holistic approach across people, policies, and technology to ensure data integrity, confidentiality, and availability. Risk identification and treatment, management of assets, operational security, and access control are core themes, along with incident management and continuous improvement.
ISO 27001 does not explicitly define “consent.” Its focus is on securing information systems rather than prescribing privacy conditions. However, many of its controls support lawful data processing. For example, Annex A.5 of ISO 27002 (the control catalogue supporting ISO 27001) covers access management. It defines access control as the means to ensure that physical and logical access to assets is authorised and restricted based on business and information security requirements. A documented access control policy must specify procedures for granting, reviewing, adjusting, and revoking user access, including responsibilities and timeframes. Organisations must maintain verifiable records of user accounts. While these provisions are not about consent per se, they create the infrastructure for ensuring that only authorised personnel can view data collected under consent and that such access can be audited.
Overlap with GDPR
Some confusion arises because Article 24 of the GDPR notes that observance of approved certifications, such as ISO 27001, may serve as evidence of compliance. In reality, GDPR covers both data privacy and security, while ISO 27001 covers only security. ISO 27001 is voluntary and prescriptive; it tells you how to implement controls. GDPR is mandatory and descriptive; it defines legal rights and obligations but leaves the implementation details up to controllers. The Data Privacy Manager highlights that GDPR requirements encompass an expanded scope of data, extended rights of data subjects, and mandatory breach notifications. ISO 27001 addresses technical measures to reduce security risks. Organisations can cover roughly 75–80 percent of GDPR security obligations by adopting ISO 27001, but they still need processes for consent and data subject rights.
Bridging the gap with ISO 27701
ISO 27701 was introduced to bridge the gap between security and privacy. As the Data Privacy Manager notes, ISO 27701 serves as a privacy extension of ISO 27001 and ISO 27002, focused on reducing privacy risks and protecting the rights of individuals. It provides guidance for establishing, implementing, and maintaining a privacy information management system (PIMS). ISMS describes ISO 27701 as a framework for data privacy that builds on ISO 27001. It helps companies document policies, procedures, and activities for privacy controls, with records then audited to show compliance. The extension introduces controller‑ and processor‑specific controls and cannot be certified standalone; it must be integrated with an ISO 27001 certification. For enterprise sellers, adding ISO 27701 can streamline the demonstration of compliance with multiple privacy laws and reduce audit costs by allowing internal and external auditors to assess privacy in one cycle.
What ISO 27001 Consent Management means in practice
Consent defined in privacy frameworks
GDPR sets out that processing personal data is generally prohibited unless it is expressly allowed by law or the data subject has given consent. Consent must be freely given, specific, informed, and unambiguous. Controllers need to inform subjects about their identity, the type of data collected, the purpose of processing, and the right to withdraw consent. Consent cannot be implied; it requires a clear affirmative action. Under GDPR, consent should be chosen only when other lawful bases do not apply. This means that if your enterprise application collects analytics or marketing data, you must provide a clear choice to the user and be prepared to stop processing if they opt out.
From an information security perspective, consent is a piece of data that influences access control and risk assessments. It documents the lawful basis for holding specific personal data sets and must be tied to processing activities. During audits, regulators expect to see evidence of when consent was obtained, what information was presented, and whether the subject later withdrew consent. If you cannot produce this evidence, you risk non‑conformities and fines. Therefore, ISO 27001 Consent Management is about integrating these consent records into the ISMS so that they are subject to the same control, logging, and review mechanisms as other sensitive information.
Aligning consent with data security and access control
ISO 27002 emphasises that access control policies should define how access to information is managed. For data collected under consent, the access control policy should limit access strictly to personnel who need it and include procedures for reviewing and revoking access when consent changes. Roles and responsibilities must be assigned; often the CTO or IT department grants access, and application owners review it. Logs of user account activity must be kept and regularly reviewed. In other words, if a data subject’s consent is withdrawn, the corresponding data should be flagged in the access control register so that it is no longer available to users. The risk assessment process should also treat consent deficiencies as threats. For example, if marketing databases are not linked to consent records, the ISMS risk register should reflect the risk of processing data without a lawful basis.
Regulatory requirements and audit expectations
External auditors do not just look for policies; they ask for evidence. In 2024 the ISO 27001:2022 update introduced a requirement that organisations recertify against the 2022 version by 31 October 2025. Auditors will examine whether consent processes meet legal requirements and whether documentation and logs are sufficient. They will check access control policies, audit logs, and evidence of withdrawal handling. They may also trace personal data through systems to ensure that it is used only for purposes covered by consent. Enterprises with complex data flows or multiple jurisdictions must show that they can meet different consent requirements across regions. For example, the Middle East saw breach costs drop 18% thanks to advanced security measures; organisations operating in that region may face different consent rules than those in the EU. A centralised consent register that captures the details required by each jurisdiction will make audits smoother.
Steps to implement effective ISO 27001 Consent Management
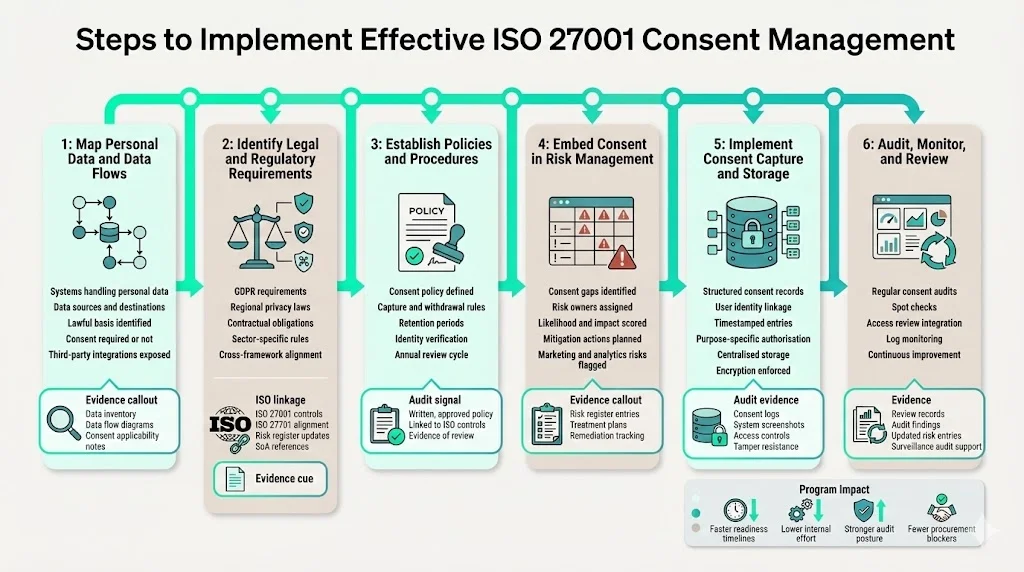
The following steps outline how to build a consent management program that meets ISO 27001 controls and privacy regulations. In Konfirmity’s experience supporting over 6,000 audits and drawing on 25 years of combined expertise, most clients follow a similar pattern. We typically deliver SOC 2 readiness in 4 to 5 months, while self‑managed programs can take 9 to 12 months. Our managed service reduces internal effort from roughly 550–600 hours to 75 hours over the year because our team executes the controls and prepares the evidence.
1. Map personal data and data flows
Start by inventorying every system and process that touches personal data. Identify what data is collected, where it comes from, and what lawful basis applies. Classify systems based on data sensitivity and regulatory scope. For each data flow, document whether consent is required. This exercise reveals “shadow” flows such as telemetry or analytics integrations that may not have been obvious. Without a complete picture, you cannot control access or audit consent properly. In our work with SaaS platforms, we often discover third‑party scripts sending data to marketing networks without clear consent. These should be disabled or covered by a new consent notice before an enterprise deal can proceed.
2. Identify legal and regulatory requirements
Document all applicable laws and agreements that affect consent. GDPR provides one set of rules, but other regions have variations. For example, under GDPR, consent must be freely given and unambiguous. ISO 27701 helps unify these requirements by serving as a cross‑regulatory framework. Include contractual obligations from business associate agreements (BAAs), data processing addenda, and sector‑specific laws such as HIPAA for health data. For each requirement, a map which ISO 27001 controls supports it. Access management, identity management, authentication, and logging are common across all laws. This mapping becomes part of your Statement of Applicability (SoA) and risk register.
3. Establish policies and procedures
Create a formal consent policy that covers how consent is obtained, recorded, stored, used, and withdrawn. Link it to ISO 27001 controls such as A.5 (access management) and A.18 (compliance). The policy should specify retention periods, define when consent is required versus other lawful bases, and describe how data will be anonymised if consent is withdrawn. Include procedures for verifying the identity of the data subject when they exercise rights. In Konfirmity’s audits, we often see organisations with informal practices (“we keep marketing opt‑ins in Mailchimp”) instead of a written policy. Auditors flag this as a minor or major non‑conformity. A written policy, reviewed annually, demonstrates control over consent processes.
4. Embed consent controls in risk management
Treat consent deficiencies as risks in your ISMS. During risk assessments, identify scenarios where data could be processed without consent or where consent could not be proven. Assign risk owners and set mitigation actions. For example, if your application logs consent for analytics events but your support team can export raw logs without checking consent, this is a risk. Mitigate it by restricting access or by applying tokenisation. Track these risks in your risk register and feed them into your treatment plan. Prioritise remediation actions based on the likelihood and impact of consent gaps. Our clients often assign a moderate to high risk score to marketing systems that use cookies, because these are frequent sources of privacy complaints.
5. Implement consent capture and storage mechanisms
Use systems that capture consent in a structured, tamper‑resistant format. Many companies rely on builtin modules in their identity provider or use purpose‑built consent management platforms. Regardless of technology, ensure that each consent record includes who gave consent, what information was presented, the date and time, and the purposes authorised. Records should be stored centrally, encrypted, and linked to user identities. Avoid scattered spreadsheets or email confirmations that cannot be reconciled. In our managed service we build consent logs into the data platform itself and link them to user accounts through unique identifiers. This design supports audits and reduces the risk that consent records are lost or tampered with.
6. Audit, monitor, and review
Treat consent records like any other critical data set. Regularly audit them to ensure that they match the processing activities. Conduct spot checks of systems to verify that data is processed only if there is a valid consent record. Integrate consent checks into internal and external audit cycles. For example, include consent review as part of quarterly access reviews; when you remove access for a departing employee, verify that they cannot view data collected under consent. Use logs to detect unauthorized access to consented data; update your risk register if suspicious events are found. During certification or surveillance audits, provide evidence of these reviews. A robust ISO 27001 Consent Management program never treats consent as a static checkbox; it is part of continuous monitoring.
Practical best practices for enterprises
1. Link consent with data governance and protection strategy
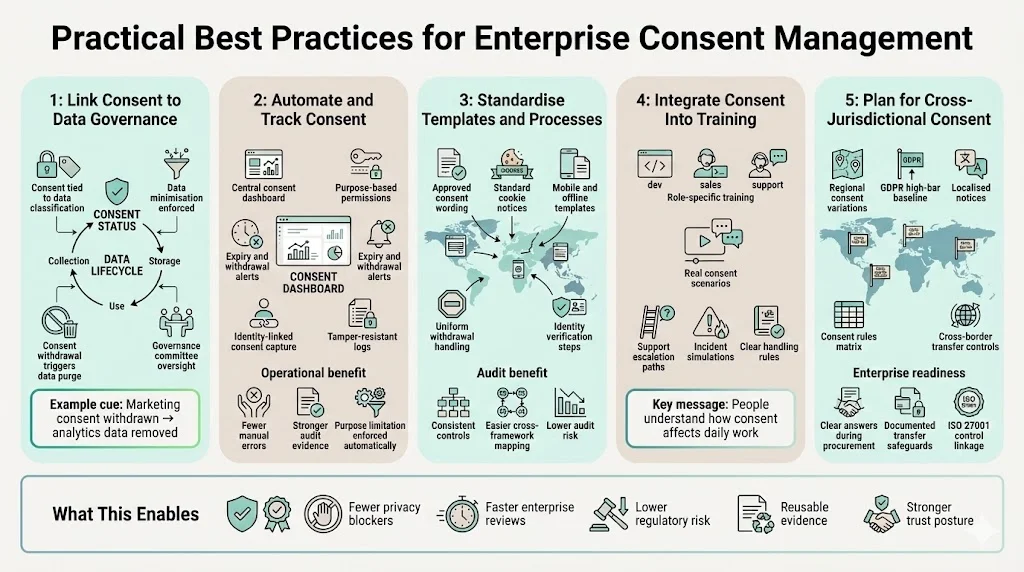
Don’t treat consent as a silo. Integrate consent requirements into your broader data governance program. This means tying consent status to data classification, data minimisation, and retention policies. In practice, if a subject withdraws consent for marketing emails, your system should not only remove them from the mailing list but also purge related data from analytics tables. Data governance committees should review consent metrics alongside access review metrics. When you adopt new features or vendors, the same committee should decide whether consent is needed and update the consent notice accordingly.
2. Use technology to automate and track consent
Automation reduces manual errors and improves evidence quality. Use a consent dashboard that shows who has given or withdrawn consent, the purposes granted, and expiry dates. Alerts should notify data owners when consents are about to expire or have been withdrawn. Some of our clients integrate consent management with their identity platform so that user sign‑ups include consent capture by default. Others use secure log storage to keep time‑stamped consent records. Automation also helps enforce “purpose limitation”—processing data only for the purposes specified during consent—and prevents the misuse of data in other contexts.
3. Standardise templates and processes
Consistency is crucial for enterprise sellers with multiple product lines or geographical regions. Use standard consent wording approved by legal counsel and apply it across applications. Develop template policies for cookie notices, mobile app permissions, and offline consent forms. Standardise control documents, such as procedures for handling withdrawal requests and guidelines for verifying subject identity. This reduces the risk that one business unit implements a different process that fails an audit. When your process is mature, you can map the same set of controls to various frameworks – SOC 2, HIPAA, and GDPR – saving time when cross‑referencing evidence.
4. Integrate consent with privacy and security training
People remain the weakest link in data protection. Training should explain why consent matters, how it affects data handling, and how to respond to requests for withdrawal. Use real scenarios: an employee receives a marketing contact list, but half of the names have withdrawn consent; what should they do? Train support staff to redirect privacy complaints promptly. Use short, role‑based modules rather than generic “privacy training.” Include consent scenarios in incident simulations so that the team knows how to contain a breach that involves consented data.
5. Plan for cross‑jurisdictional consent challenges
Enterprise sellers often operate in multiple jurisdictions where consent rules differ. GDPR sets a high bar for consent; other regions may allow inferred consent or have lower age thresholds. Your consent program should allow you to adapt notices and processes by region. Maintain a matrix of consent requirements and use geolocation or user‑selected location data to present the correct notice. When negotiating with enterprise clients, be prepared to explain how your system handles cross‑border data transfers and consent. Document how you manage third‑country transfers, such as using standard contractual clauses, and link those documents to your ISO 27001 controls.
Measuring success
How do you know if your ISO 27001 Consent Management efforts are working? Track metrics that capture both compliance and operational efficiency. Examples include:
- Completeness of consent records: the percentage of personal data elements with a valid consent record attached. Aim for 100%, but highlight any system that falls below 95% so you can remediate quickly.
- Audit findings: number of consent‑related non‑conformities in internal and external audits. A downward trend shows improvement.
- Unauthorized access events: number of access log entries where users accessed data beyond their consent scope. This should trend towards zero. Use the logs and review processes described above to detect anomalies.
- Response time to withdrawal requests: average time to process a withdrawal and remove data. Buyers may ask for these metrics during procurement.
- Effect on sales cycles: time saved during procurement by having ready evidence. At Konfirmity, clients report that deals close weeks faster when they can produce consent logs alongside their ISMS SoA.
By collecting these metrics, you not only satisfy auditors but also demonstrate to enterprise buyers that your consent processes are mature and effective. Over time, you can set benchmarks (e.g., internal SLAs for processing consent withdrawals within 72 hours) and measure improvement.
ISO 27001, ISO 27701, and GDPR — working together
Implementing ISO 27001 controls lays the groundwork for meeting GDPR security requirements. The Pivot Point Security article notes that ISO 27001 helps businesses identify and manage personal data, ensure its availability and integrity, emphasise risk assessment, mandate supplier controls, and require breach notification practices. ISO 27001 compliance does not automatically make an organisation privacy‑law compliant, but it is a major step. ISO 27701 extends ISO 27001 by adding privacy controls and creating a PIMS. ISMS.online explains that ISO 27701 allows organisations to demonstrate compliance with GDPR and other privacy laws by documenting policies and procedures and providing operational checklists. For enterprise sellers, the combination of ISO 27001, ISO 27701, and GDPR offers a layered approach: security controls protect data, privacy controls ensure lawful processing, and legal requirements define the rights and obligations. When integrated, these frameworks reduce duplication of work and enable cross‑framework reuse of evidence.
Konfirmity’s managed service implements this layered approach. We start with security and arrive at compliance. By embedding consent into the ISMS, mapping controls across standards, and operating the program year‑round, we reduce the risk of non‑conformities and accelerate buyer due diligence. We don’t just advise—we execute; our team implements controls inside your stack and prepares evidence on an ongoing basis. This approach contrasts with one‑off consultants, who may deliver policies but do not operate them, and software platforms, which require hundreds of hours of internal work. Our human‑led service is outcome‑driven: fewer audit findings, faster buyer approvals, and repeatable renewals.
Conclusion
In today’s data‑intensive market, organisations cannot treat consent as an afterthought. The concept of ISO 27001 Consent Management highlights how privacy and security need to be woven together. ISO 27001 provides the framework for managing information security, while GDPR and ISO 27701 impose obligations to manage personal data lawfully. By mapping consent to controls, logging consent events, and embedding consent into risk management and audits, companies not only comply with regulations but also win the trust of enterprise buyers. The cost of neglecting these controls is high: breach costs in 2025 averaged $4.44 million, rising to $10.22 million in the U.S., and regulators have imposed multi‑million‑euro fines for ignoring withdrawal rights. The reward for doing it right is tangible: deals close faster, reputational risks drop, and you build a defensible program that stands up under scrutiny. As practitioners, we advise teams to build the program once, operate it daily, and let compliance follow.
FAQs – ISO 27001 Consent Management
1. Is ISO 27001 certification required to manage consent?
Certification is not required. ISO 27001 is voluntary and focuses on information security. However, following its controls helps you design processes for managing personal data securely and demonstrating that consent is respected. Certification can give buyers confidence that you follow best practices, but consent obligations come from laws like GDPR.
2. How does ISO 27701 relate to consent management?
ISO 27701 is a privacy extension of ISO 27001. It adds privacy‑specific controls and a PIMS. Implementing ISO 27701 alongside ISO 27001 makes it easier to document and audit consent, because it provides detailed guidance on how to capture, store, and respond to data subject rights. Certification demonstrates that your privacy program meets international standards.
3. Can consent records be used as evidence in audits?
Yes. Auditors expect to see time‑stamped consent records showing when and how consent was obtained. Logs and withdrawal records support your compliance claims. Without this evidence, you may receive non‑conformities or penalties.
4. Do enterprises need special tools for consent management?
Tools help automate and track consent, reducing manual effort and improving the quality of evidence. A structured platform can centralise consent records, alert you to withdrawals, and integrate with identity providers. However, tools alone are not enough; you need policies, procedures, and people to operate them. A managed service can reduce your internal workload by handling both the tools and the operations.
5. What’s the role of audit trails in consent management?
Audit trails prove accountability. They show when consent was given, by whom, and for what purpose. They also record withdrawals and access events. During an audit, these trails allow you to trace personal data to its lawful basis and demonstrate compliance with ISO 27001 and privacy laws.





.svg)






.svg)
.svg)