Most enterprise buyers now ask for evidence of security and governance before they sign a contract. Security questionnaires, business associate agreements (BAAs), data processing agreements (DPAs) and regulatory addenda often land before a single line of code is demoed. In 2024 IBM’s benchmark study saw the average cost of a breach rise to USD 4.88 million, while the 2025 report noted that U.S. firms now face an average USD 10.22 million breach cost and healthcare remains the hardest‑hit sector at USD 7.42 million. Those numbers translate into procurement pressure: buyers want to know that vendors have a mature program for managing information security and IT governance, not just policies written for the sake of audits. This article on ISO 27001 Controls Mapped To COBIT frames that program in terms business leaders, engineers and auditors can all understand.
As the founder of Konfirmity, I’ve helped companies of every size build and operate programs that hold up under audits, due‑diligence reviews and real‑world incidents. This guide explains why connecting ISO 27001 and COBIT matters, how the frameworks differ, and how to map controls to satisfy auditors and enterprise procurement teams. It’s written for CTOs, CISOs, VPs of engineering, compliance officers and sales leaders who need to turn security into a competitive advantage.
What ISO 27001 Covers in Plain Terms
At its heart, ISO 27001 asks: what information assets do you have, what risks do they face and what controls will reduce those risks to an acceptable threshold? Clause 4‑10 define the management system—the context, leadership responsibilities, planning, support, operational controls, performance evaluation and continual improvement. Annex A lists 93 security controls across four themes. Organizations select controls based on a risk assessment and justify any exclusions in the SoA. The controls range from policy requirements (e.g., management‑approved information security policies) and organisational structures (e.g., defined roles and responsibilities) to technical safeguards (e.g., authentication, encryption, configuration management) and physical protection measures.
ISO 27001’s purpose within information security management is to institutionalise a risk‑based approach that is auditable. It ensures that management commits resources, roles are clear and controls are measured. Because the standard is recognized worldwide, many enterprise clients now use it as a baseline for vendor evaluation. BEMO’s 2025 guide states that for IT service providers and SaaS platforms “ISO 27001 certification has become a near‑standard requirement,” giving clients confidence that the vendor follows rigorous protocols and providing a competitive edge in procurements. Financial, healthcare and government clients are increasingly demanding that vendors follow ISO 27001 as part of due diligence.
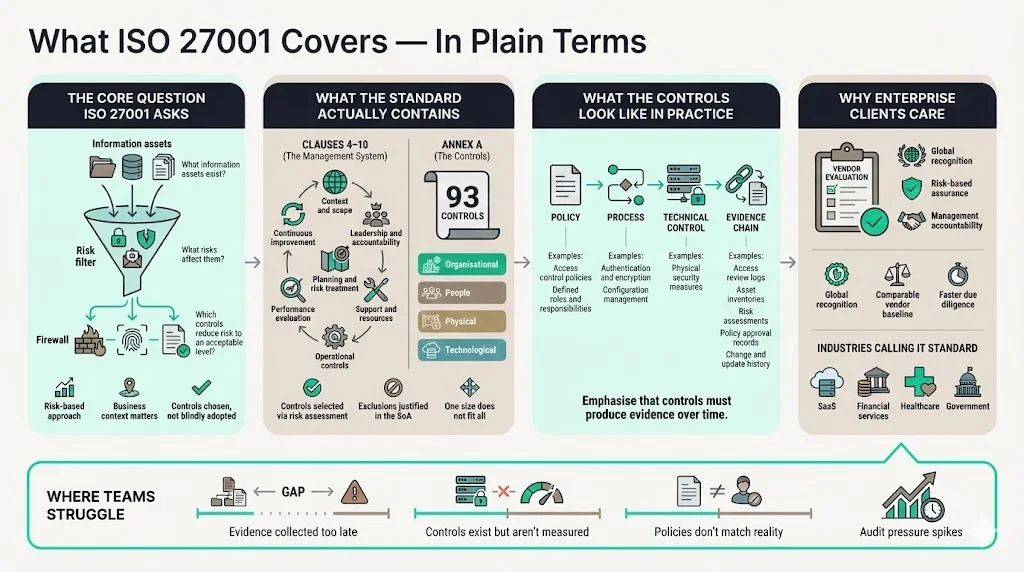
Controls support risk management by requiring evidence. For example, access control policies ensure employees only see data relevant to their roles, and asset management processes classify information assets and assign owners. During an audit, evidence could include logs of access reviews, asset inventories, risk assessments, and records of policy updates. In our practice we see that gathering this evidence over time—not just before an audit—is where teams struggle most.
Why ISO 27001 Controls Mapped To COBIT Matters
ISO 27001 Controls Mapped To COBIT objectives create a unified picture for stakeholders. The business case is clear:
- Use the same evidence—risk registers, policy reviews and incident records—to satisfy both frameworks rather than maintaining duplicate documents.
- Help procurement reviewers see that you cover risk management, governance and continual improvement, cutting unnecessary back‑and‑forth and saving time.
- Collect evidence once and present it in ways that satisfy both ISO 27001 audits and COBIT governance reviews, reducing interviews and document handling.
Without this mapping, teams often repeat risk assessments, duplicate policies and maintain separate records of access reviews and asset inventories. These activities consume time and cause inconsistencies. A clear mapping forces teams to think holistically about the intent behind each control and ensures that security and governance activities match.
How ISO 27001 and COBIT Actually Differ
Scope and Focus
ISO 27001 is a security‑focused standard. It aims to protect information assets by ensuring a systematic risk assessment, implementing appropriate controls and continually improving the ISMS. COBIT, in contrast, is governance‑driven. It covers how organizations plan, build and operate IT systems in support of business objectives. Security is just one component.
Control Structure Comparison
ISO 27001 lists explicit controls in Annex A, while COBIT defines objectives and practices without enumerating controls. Because of this difference, a single ISO 27001 control can relate to several COBIT practices. For instance, ISO 27001’s asset management control (A.5) touches multiple COBIT practices on data management, service delivery and performance monitoring. Rather than seeking exact matches, think about which objectives your control supports.
Audit and Assurance View
ISO 27001 certification audits review the design and operation of your ISMS against clauses 4‑10 and selected Annex controls. Auditors look for risk assessments, Statements of Applicability, evidence of control implementation and records of monitoring and improvement. COBIT reviews typically occur in internal audit and governance assessments. Reviewers look for evidence of governance structures, roles, accountability and performance measures. Mapping your controls shows both the security safeguard and its governance context, satisfying auditors and buyers.
Mapping Logic in Overview
When discussing ISO 27001 Controls Mapped To COBIT, researchers and practitioners use a combination of process‑based and control‑based approaches. Starting from COBIT objectives, they identify supporting ISO controls; or starting from ISO controls, they identify the COBIT practices that match their purpose. The important thing is to focus on intent rather than wording. For example, ISO 27001’s incident management control (A.16) and COBIT’s practices for managing security services and incidents both address detection, response and learning even though the language differs.
Intent‑based mapping supports broader cybersecurity and risk management goals. It helps ensure that controls are not implemented merely to satisfy auditors but to reduce risk and improve governance. At Konfirmity we also map supporting evidence to each control and objective. For instance, vulnerability metrics, remediation timelines and change records can simultaneously satisfy ISO 27001 A.12, SOC 2 criteria and COBIT objectives.
Core ISO 27001 Control Domains and Their COBIT Links
Below is a table summarising how ISO 27001 controls mapped to COBIT across the main control domains. Use this as a starting point when building your own mapping. Keep in mind that many controls map to multiple COBIT objectives. Focus on intent and evidence rather than forcing a single match.
This table captures only a subset of the control domains. Mapping should include all 93 controls. The focus should remain on evidence and ownership: who executes the control, how often, and how it ties into business processes.
What This Mapping Looks Like in Practice
Example 1: Selling to a Large Enterprise Buyer
During enterprise sales cycles, we often see security questionnaires with hundreds of questions covering SOC 2, ISO 27001 and COBIT. Without mapping, each question is answered separately. For instance, a buyer might ask for your risk management process, incident response plan, asset inventory and access control policies. If you’ve mapped ISO 27001 controls to COBIT, you can package evidence into unified artefacts: a risk register showing risk assessment and treatment (A.6 and COBIT APO 12), an incident response policy mapping to DSS 04 and DSS 05, and an asset inventory linking A.5 with APO 14 and DSS 01. In one client engagement we reduced the number of clarifications from procurement teams by 70% because the mapping made it clear how controls met governance objectives.
Example 2: Preparing for a Combined Audit
Imagine your organization needs ISO 27001 certification, SOC 2 Type II attestation and a COBIT maturity assessment. Auditors will review evidence across overlapping domains. SOC 2 Type II audits assess design and operating effectiveness over an observation period of 3–12 months. Most organizations take 6–12 months for a Type II report. ISO 27001 surveillance audits occur annually and require continuous evidence of control operation. COBIT maturity assessments look at processes and performance metrics.
By mapping controls, you can build one evidence set: access review logs demonstrate ISO 27001 A.9, SOC 2 Common Criteria CC6 and COBIT DSS 01; incident tickets satisfy ISO 27001 A.16, SOC 2 CC7 and COBIT DSS 05; change‑management records cover ISO 27001 A.8, SOC 2 CC8 and COBIT BAI 06. With this approach, we typically see SOC 2 readiness time drop from 9–12 months to 4–5 months because we implement controls inside the client’s stack and maintain them year‑round. For many clients this saves hundreds of hours—our managed service requires around 75 hours of client time per year versus 550–600 hours for self‑managed programs.
In practice this consolidation means your team does not have to scramble to produce separate logs or spreadsheets for each auditor. Evidence is collected once, stored in a structured repository and tagged with the relevant ISO 27001 control, SOC 2 criterion and COBIT practice. During readiness assessments we often see that 60–70 percent of audit requests overlap across frameworks. By planning cross‑framework evidence you reduce the number of meetings with auditors, shorten fieldwork and spend more time improving controls rather than managing paperwork. The stakes are high: regulators and customers expect proof of both security and governance, data breach costs continue to rise and fines for non‑compliance can exceed the revenue from stalled deals. A thoughtful mapping program positions your company as a trusted partner and avoids last‑minute chaos when audits or buyer questionnaires arrive.
Common Mapping Mistakes Busy Teams Make
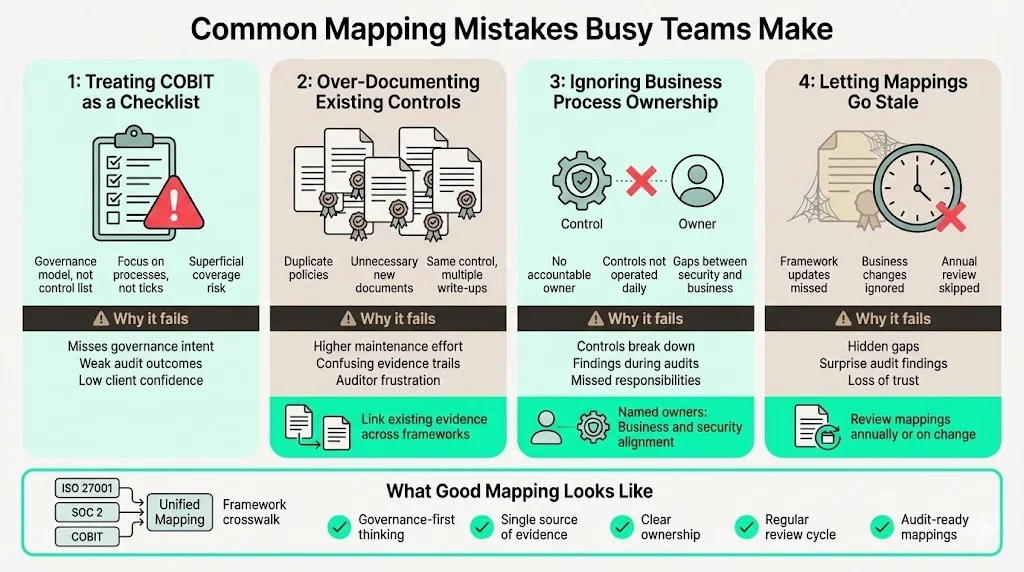
1) Treating COBIT as a checklist. COBIT is a governance model, not a list of controls. Using it as a checklist leads to superficial coverage and does not satisfy auditors or clients who expect governance processes.
2) Over‑documenting controls that already exist. Teams often duplicate policies or create new documents instead of linking existing procedures to COBIT objectives. This increases maintenance burden and confuses auditors. Use the mapping to point to the same evidence from different frameworks.
3) Ignoring business process ownership. Security controls will not operate without owners. Assign responsibility at both the security function and business unit levels. ISO 27001 requires defined roles and responsibilities, and COBIT emphasises stakeholder engagement and accountability.
4) Failing to keep mappings current. Frameworks change (for example, ISO 27001 added 11 controls in the 2022 revision). Your mapping must be reviewed at least annually or whenever frameworks or business processes change. Otherwise you risk gaps that will be exposed during audits.
How to Use This Mapping Without Slowing Down
Start by listing your existing ISO 27001 controls and evidence, then map each one to a COBIT objective. If you already have COBIT processes, perform a gap analysis to see which ISO controls they satisfy and which need more work. Prioritise high‑risk areas such as access control, asset management and incident response. Document your mappings in a simple spreadsheet or control library and automate evidence collection where possible. Use a single policy library and central evidence repository rather than creating separate documents for each framework. Assign clear owners for each domain and involve process owners across security, engineering, HR, legal and operations so that everyone knows why evidence is needed and how it will be used. Using ISO 27001 Controls Mapped To COBIT as a foundation will make your mapping project easier.
How Enterprise Clients View ISO 27001 and COBIT Together
Procurement teams usually start with basic questions: do you have an ISMS, are you certified to ISO 27001 and what scope does that certification cover? They then ask how your IT governance supports business goals and whether you have a mature risk management process. Security teams want evidence of access reviews, vulnerability management, incident handling, service continuity and third‑party risk management. Because COBIT includes objectives on managing vendors and service providers, mapping these to ISO 27001 controls demonstrates that you address supply chain security. Presenting ISO 27001 certification together with ISO 27001 Controls Mapped To COBIT objectives shows that your program covers both security and governance, builds trust and supports long contracts.
Making ISO 27001 Controls Mapped To COBIT Work for You
Using ISO 27001 Controls Mapped To COBIT is not about adding complexity. It’s about clarity. This mapping helps you tell a coherent story that your security controls serve broader governance objectives. It supports cybersecurity, governance and growth by reducing duplicate work, speeding up sales cycles and strengthening your audit posture.
At Konfirmity, our human‑led, managed security and compliance service starts with security and arrives at compliance. We build and operate controls inside your stack, collect evidence continuously and keep you audit‑ready year‑round. With more than 6,000 audits supported and over 25 years of combined expertise, we’ve learned that durable controls beat paper promises every time. We don’t just advise—we execute. When our clients undergo SOC 2 Type II audits, we handle the heavy lifting during the 3–12 month observation period, letting them focus on building products while we manage evidence collection and remediation. This managed approach saves them months of internal work and reduces findings in final reports.
Final Thoughts for Teams Balancing Security and Sales Demands
Security that looks good in documents but fails under incident pressure is a liability. Use ISO 27001 Controls Mapped To COBIT to provide a clear narrative linking technical safeguards to governance practices. This mapping enables cross‑team collaboration and streamlines evidence collection for auditors and clients.
The stakes are rising: the IBM 2025 report showed that U.S. data breach costs reached USD 10.22 million, and 51% of organizations reported malicious breaches. Regulators are levying higher fines, and security staffing shortages persist. A risk‑based ISMS based on ISO 27001, coupled with COBIT’s governance framework, provides the structure needed to withstand this pressure. Build the program once, operate it every day and let compliance follow.
ISO 27001 Controls Mapped To COBIT: Frequently Asked Questions
1) What is the main goal of mapping ISO 27001 controls to COBIT?
To connect security controls with governance processes in a way enterprise stakeholders understand. ISO 27001 Controls Mapped To COBIT show how your risk‑based controls underpin business objectives and support both audits and sales conversations.
2) Is ISO 27001 enough without COBIT?
It depends on client expectations. ISO 27001 certification demonstrates that you manage information security risks, but many enterprises also expect visibility into how IT governance supports business goals. Mapping to COBIT satisfies that need and reduces procurement friction.
3) Do all ISO 27001 controls map directly to COBIT?
No. COBIT defines governance and management objectives, not individual controls. Mapping is based on intent and outcomes. Many ISO 27001 controls map to multiple COBIT objectives, and some COBIT practices have no equivalent control. Interpret purpose rather than looking for exact matches.
4) Does this mapping reduce audit effort?
Yes. When done well, it cuts duplicate evidence and speeds reviews. We’ve seen SOC 2 readiness drop from nine months to around five months when mapping was used to use the same evidence across frameworks. It also reduces the number of clarifications from auditors and procurement teams.
5) How often should mappings be reviewed?
At least once a year or whenever frameworks are updated (e.g., ISO 27001’s 2022 revision added 11 controls) or when business processes change. Regular review ensures that your mapping remains accurate and supports continual improvement.





.svg)






.svg)
.svg)