Most enterprise procurement teams have added web‑tracking reviews to their due‑diligence checklists. They look beyond product controls and into the marketing stack because uncontrolled scripts can collect personal data and share it with vendors you never vetted. Personal data collected by cookies counts as processing and sits squarely in privacy laws like the General Data Protection Regulation (GDPR), yet it also intersects with security standards. ISO 27001 Cookie Compliance is the practice of managing web cookies with the same rigor that an information security management system (ISMS) brings to servers and code. In today’s market, buyer demands for proof, combined with stricter privacy enforcement and new regulations like NIS2 and DORA, make this discipline a prerequisite for closing deals.
Companies pursuing ISO 27001 certification sometimes assume that passing the audit means they are done with privacy. That’s never been true. The ISO 27001 standard sets requirements for establishing and operating an ISMS, yet it doesn’t replace legal duties around personal data. Consent banners, records of processing, and lawful bases still matter. Enterprise clients check for both security and privacy, and cookie missteps create friction even when the back‑end is tight. This article draws on insights from thousands of audits and up‑to‑date guidance from regulators and trusted frameworks to show why cookies belong in your scope, how they map to controls, and how to build a program that satisfies auditors and buyers.
What “ISO 27001 Cookie Compliance” really means
The ISO 27001 standard is the world’s best‑known ISMS framework. According to the International Organization for Standardization, it defines requirements for establishing, implementing and continuously improving an information security management system. An organization that conforms to ISO 27001 has adopted a risk‑based program to protect the confidentiality, integrity and availability of data. The standard promotes a holistic approach—vetting people, policies and technology—to manage risks and improve cyber resilience. Annex A includes controls on privacy and protection of personally identifiable information (PII); clause 5.34 instructs organizations to identify and meet requirements concerning PII preservation and privacy. However, ISO 27001 doesn’t grant immunity from data‑protection laws. It’s a voluntary certification, not a legal regime.
The GDPR and the ePrivacy Directive create legal obligations around cookies. Recital 30 of the GDPR states that online identifiers like IP addresses and cookie identifiers may be considered personal data because they can be used to create profiles and identify individuals. The ePrivacy Directive requires consent for storing or accessing information on a user’s device, with limited exceptions for strictly necessary cookies. GDPR.eu’s guidance summarises cookie compliance obligations: companies must obtain consent before using any cookie except strictly necessary ones, provide clear information about what each cookie does, document and store consent, allow users to refuse cookies without being blocked from the service, and make withdrawal as easy as giving consent. In other words, even if your ISMS is robust, you still need lawful bases and transparent notices for every cookie that touches personal data.
Privacy laws also apply to other tracking technologies. The European Data Protection Board (EDPB) clarified in 2023 that Article 5(3) of the ePrivacy Directive covers tracking pixels, device fingerprinting and similar techniques. The EDPB noted that the notion of “information” includes both personal and non‑personal data and that consent is required whenever information is stored on or accessed from a user’s device. Its guidance emphasises that cookies are just one of many tracking tools regulated under the “cookie rule.” This reinforces that cookie compliance is not optional; it sits squarely within the scope of privacy regulators.
Taken together, ISO 27001 and privacy laws intersect but do not overlap completely. ISO 27001 provides a systematic process for managing information‑security risks and evidence; GDPR, ePrivacy and other laws define when and how personal data can be collected, processed and shared. Achieving ISO 27001 Cookie Compliance means using the ISMS to support privacy obligations—through inventory, risk assessment, controls and continuous monitoring—while still meeting legal consent requirements. The ISMS gives structure and evidence that auditors can review, but it doesn’t absolve you from documenting lawful bases or giving users genuine choices.

Why cookies belong in your ISMS scope
Cookies touch multiple risk surfaces. They can store unique identifiers that link to user accounts, marketing segments or behavioural profiles. Third‑party scripts often call out to analytics, advertising and social‑media platforms, sending data to destinations outside your control. Because cookies can involve personal data and cross‑border transfers, they are both a privacy issue and a security concern. If a marketing tag loads malicious code or leaks data to an untrusted host, it becomes an incident for your security team. Buyers know this and ask pointed questions about your web tracking in security questionnaires, procurement checklists and legal reviews.
In practice, including cookies in your ISMS means treating them like other assets. You inventory them, classify their purpose and lawful basis, assess risks, apply controls and collect evidence. ISO 27001’s risk management approach aligns closely with GDPR’s data protection impact assessment (DPIA); both require identifying threats, impacts and treatment plans. Annex A’s privacy control ensures that you capture legal, contractual and regulatory requirements around PII. This interplay makes cookies a natural fit for your ISMS scope. Without explicit inclusion, you risk missing exposures that auditors—and enterprise buyers—will catch.
Why enterprise clients care (and how cookie gaps show up in deals)
Enterprise buyers are under pressure to manage their own risk. Secureframe’s 2026 compliance statistics report that 81 percent of organizations planned or held ISO 27001 certification in 2025, up from 67 percent in 2024. Compliance has become a strategic enabler—77 percent of C‑suite leaders say it contributes significantly or moderately to company objectives, and many companies undertake multiple audits per year. In parallel, data breaches are costly; IBM’s 2025 Cost of a Data Breach report shows that the average breach cost for U.S. organizations reached $10.22 million, a 9 percent increase, and organizations needed an average of 241 days to identify and contain a breach. Regulators are also increasing fines and oversight. The combined effect is that buyers cannot risk weak controls anywhere—not even on marketing pages.
During due diligence, cookies surface in several ways:
- Security questionnaires ask about tracking technologies, third‑party vendors, retention periods and incident response. Buyers want assurance that you know what runs on your site, have classified cookies by purpose, and can block or remove unauthorized scripts quickly.
- Legal reviews evaluate consent flows, privacy‑notice accuracy and cross‑border data sharing. Inadequate cookie disclosures can result in remediation requests or contract clauses requiring immediate fixes.
- Procurement checks look at whether marketing tools introduce new vendors. Each pixel is another supplier to manage, with risk assessments, data‑processing agreements and sub‑processor lists. Unvetted tags can delay or derail deals.
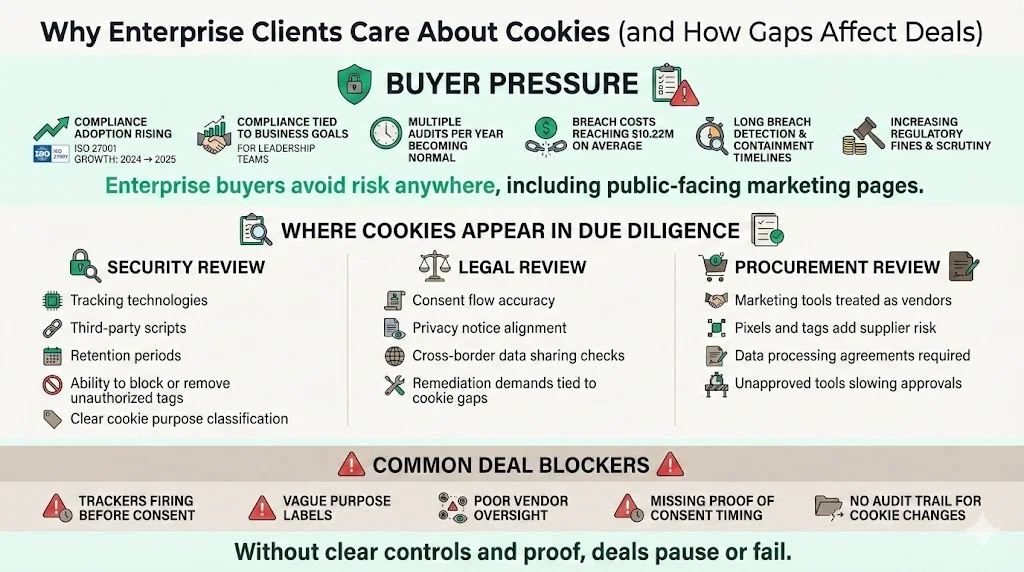
Common deal blockers include unknown trackers firing before consent, unclear purpose categories (“performance” vs. “marketing”), weak vendor oversight, and missing audit trails. Buyers may require evidence that no non‑essential cookies fire before consent, that you can prove when and how a user gave permission, and that you have oversight of third‑party vendors. Without this, deals stall.
Map cookie compliance requirements to ISO 27001 control expectations
Core ISO 27001 themes that map well to cookies
ISO 27001 introduces themes that translate neatly into cookie management. The following table pairs key ISMS concepts with cookie‑compliance activities. It summarises the parallels without lengthy sentences.
Add the regulatory convergence lens for 2025–2026 buyers
Privacy and security frameworks are converging. The EU’s NIS2 directive mandates stronger risk management, stricter incident reporting and clearer accountability across industries. DataGuard’s NIS2 guide notes that NIS2 widens the net beyond critical infrastructure and applies to many organizations, requiring robust security measures, incident reporting within 24 and 72 hours, and evaluation of third‑party security. Organizations must implement measures like multi‑factor authentication, encryption, backups, incident response procedures and third‑party assessments. Senior management is directly accountable and must approve cybersecurity strategies. The directive expands enforcement and imposes heavy fines for non‑compliance.
Financial entities face additional obligations under the EU’s Digital Operational Resilience Act (DORA). DORA, which took effect on 17 January 2025, aims to ensure banks, insurance companies and other financial firms can withstand ICT disruptions; it harmonises rules across the sector. The regulation covers ICT risk management, oversight of third‑party providers, resilience testing and incident reporting. It creates an EU‑wide oversight framework for critical ICT third parties. For vendors selling to financial institutions, demonstrating that your web tracking falls under the same governance as your core systems becomes part of procurement.
Enterprise buyers increasingly aim to run a single evidence set across frameworks. They expect unified controls that map to ISO 27001, SOC 2, GDPR, NIS2 and DORA. A cookie‑management program that aligns with ISO 27001 control themes, documents lawful bases and logs consent events positions you as ready for this convergence. It also reduces the friction of updating multiple frameworks separately.
Best practices for ISO 27001 Cookie Compliance
1) Governance and ownership
Cookie compliance is cross‑functional. Assign clear owners across security, legal/privacy, marketing and web operations. Define who can approve new tags, who maintains the inventory, and who handles incident response. Create decision rights: which categories of tags are allowed, what is the process for approval, and how to shut down scripts quickly in emergencies. Document these rules in your ISMS and train stakeholders accordingly.
2) Privacy policy and consent text that match reality
Your privacy notice and cookie banner must reflect actual behaviour. The GDPR requires clear and specific information about what each cookie does. Use plain language to explain categories such as analytics, marketing, functional or essential. Avoid ambiguous “legitimate interest” claims when consent is required. Update the policy whenever you add or remove vendors, and ensure regional variants align with local laws. Provide mechanisms to withdraw consent that are as easy as giving it.
3) Data protection controls for cookies and trackers
Limit collection to what’s needed for the stated purpose. Disable or shorten cookie lifetimes if data isn’t essential. Reduce third‑party exposure by choosing fewer vendors and configuring them to minimize data sharing. Enforce least privilege on tag management platforms; restrict who can add or edit tags, and require peer review and staging tests. Use content‑security policies or script management tools to block unauthorized calls. Retain logs to show when and by whom changes were made.
4) Evidence‑first mindset (for audits and buyer reviews)
Auditors and buyers want proof. Maintain snapshots of your cookie inventory and tag configurations at regular intervals. Capture approvals for new tags and classification decisions. Store consent logs, showing timestamp, user choice, and region. Keep vendor assessments and data processing agreements in your repository. When you adjust the banner or policies, save screenshots and test results. This evidence provides a chain of custody for every decision and helps during surveillance audits and buyer due diligence.
Key steps: an audit‑ready implementation plan
Implementing ISO 27001 Cookie Compliance isn’t done overnight. The following playbook breaks it into steps. Each step ends with the evidence you should save.
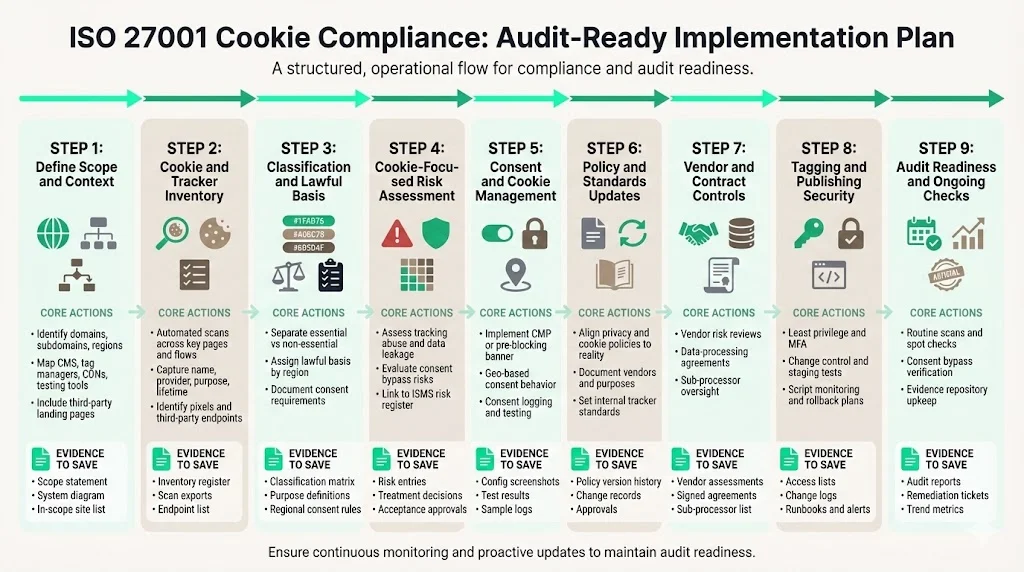
Step 1: Define scope and context (ISMS + website stack).
Identify all domains, subdomains, landing pages, application pages and regional variants. Map the technologies involved—tag managers, content management systems (CMS), A/B testing tools, chat widgets, content delivery networks (CDNs). Include third‑party landing pages if they collect data on your behalf. Evidence to save: scope statement, system diagram, list of sites and applications in scope.
Step 2: Build a cookie and tracker inventory.
Run automated scans across representative pages and flows, such as your homepage, pricing page, demo request form, sign‑up flow and documentation. For each cookie, capture name, provider, purpose, category (essential, functional, analytics, marketing), lifetime, and pages where it fires. Identify third‑party endpoints and pixels. Evidence to save: inventory register, scan exports, list of third‑party endpoints.
Step 3: Classify cookies by purpose and lawful basis.
Separate essential cookies (required for the service) from those used for analytics or marketing. For jurisdictions with consent regimes like the GDPR, non‑essential cookies require affirmative consent. Document the lawful basis for each cookie (consent, legitimate interest, contract) and note regional differences. Evidence to save: classification matrix, purpose definitions, consent requirements by region.
Step 4: Perform a risk assessment focused on cookies.
Use your ISMS risk methodology to assess cookie‑related threats: unauthorized tracking (e.g., piggybacking scripts), data leakage to vendors, misconfigured scripts that bypass consent, and vulnerabilities introduced by third parties. Evaluate impacts such as regulatory exposure, buyer trust erosion, and incident response costs. Link this analysis to your broader risk register and treat or accept risks accordingly. Evidence to save: risk register entries, treatment decisions, acceptance sign‑offs.
Step 5: Select and configure consent and cookie management.
Choose a consent management platform (CMP) or implement your own banner with pre‑blocking to ensure non‑essential tags don’t fire until consent is given. Configure banner behaviour by geography to align with regional laws. Provide granular choices and easy withdrawal. Implement consent logging for proof. Test the configuration on staging and production to verify that scripts remain blocked until users opt in. Evidence to save: configuration screenshots, test results, sample consent logs.
Step 6: Update privacy policy, cookie policy and internal standards.
Align your policies with the actual tools and data sharing. Include vendor names and purposes where required. Update the policies whenever you change vendors or categories. Create an internal standard that prohibits adding new trackers without review and sets maximum cookie lifetimes. Evidence to save: version history of policies, change tickets, approval records.
Step 7: Vendor and contract controls for marketing/analytics tools.
Conduct due diligence on every vendor that receives data via cookies. Assess what data is collected, how it’s processed, sub‑processors, security controls and breach history. Negotiate data‑processing agreements with terms on data use, breach notification and deletion rights. Maintain a sub‑processor list. Evidence to save: vendor assessments, signed data‑processing agreements, sub‑processor lists, renewal reviews.
Step 8: Implement security controls around tagging and publishing.
Enforce least privilege for tag managers and CMS accounts. Require multi‑factor authentication for administrative access. Implement change control: peer review, staging testing and rollback plans. Set up monitoring to alert on new scripts or calls to unapproved domains. Maintain runbooks for rollback. Evidence to save: access control lists, change logs, monitoring alerts, rollback runbooks.
Step 9: Internal audit readiness and continuous checking.
Schedule routine scans—monthly or after major releases—to verify that your cookie inventory remains accurate and that no non‑essential tags fire without consent. Conduct spot checks for consent bypass, such as verifying that analytics scripts don’t fire before opt‑in. Update your evidence repository with audit reports, remediation tickets and trend metrics. Evidence to save: audit reports, remediation tickets, metrics showing compliance over time.
Audit and enterprise buyer proof pack
What auditors and enterprise security teams typically want
Auditors and buyer security teams look for tangible artefacts. At minimum, prepare the following:
- Cookie inventory and classification: your register with details on name, purpose, provider, category and lawful basis.
- Risk assessment entries and treatment decisions: show how cookie‑related risks were identified and mitigated.
- Consent behaviour testing evidence: test results demonstrating that non‑essential cookies remain blocked until consent is given; logs showing opt‑in/out choices.
- Vendor oversight documentation: due‑diligence questionnaires, data‑processing agreements, sub‑processor lists, and periodic reviews.
- Incident management references: guidelines on how security events involving cookies are handled, including escalation and notification. These align with ISO 27001 incident management and NIS2’s reporting obligations.
Simple metrics that help in reviews
Metrics make review meetings easier. Consider tracking:
- Number of trackers by category (essential, analytics, marketing).
- Percentage of pages passing the “no non‑essential before consent” test.
- Time to remove an unauthorized tag once identified.
- Vendor count trend over time—aim to reduce vendor sprawl.
- Consent opt‑in rate by region (to inform users‑experience decisions).
You can tie these metrics to broader security roadmaps, such as vulnerability remediation times or compliance KPIs. They show maturity and continuous improvement.
Common pitfalls (and how to avoid them)
Teams often misinterpret what ISO 27001 Cookie Compliance involves. A few common mistakes:
- Assuming ISO 27001 certification alone equals privacy compliance. ISO 27001 supports privacy, but you still must meet GDPR and ePrivacy requirements, including consent and lawful bases.
- Allowing marketing teams to add tags without controls. Uncontrolled tag managers lead to unknown trackers. Enforce change control and approvals.
- Banner is present, but tags still fire early. Test your implementation to ensure scripts are blocked until consent; many off‑the‑shelf banners need configuration.
- Stale cookie lists in policies. Update policies and inventories regularly; some regulators require real‑time transparency.
- Weak vendor oversight and missing agreements. Without DPAs and sub‑processor lists, you may breach contractual obligations and GDPR Article 28.
Conclusion
Cookies are not “just marketing.” They collect identifiers and behavioural data, introduce unvetted third parties, and can create paths for attackers. In a world where compliance drives revenue—81 percent of organizations plan for ISO 27001 certification and breach costs average $10.22 million—you need to treat cookies with the same discipline you apply to your core systems. ISO 27001 Cookie Compliance means building cookie management into your ISMS: inventory, risk assessment, controls, evidence, and continuous checks. It doesn’t replace legal obligations; it reinforces them with governance, accountability and proof. When you operate cookies as part of your security program, audits go smoother, enterprise deals close faster, and regulators see that you take privacy seriously.
FAQs
1) Does ISO 27001 certification mean our website is cookie compliant?
No. ISO 27001 supports strong security practices, but cookie compliance depends on privacy laws and how you handle personal data. You must obtain consent, provide clear information and document consent choices even if you are certified.
2) Which ISO 27001 activities help most with cookie compliance?
Risk assessments, incident management, vendor oversight and recordkeeping map well to cookie and tracker controls. These align with Annex A’s privacy control and NIS2’s risk management requirements.
3) What evidence should we keep for ISO 27001 Cookie Compliance?
Save your cookie inventory, classification matrix, risk register entries, consent configuration history, consent logs, vendor assessments, data‑processing agreements, change control records, scan reports and audit logs. This evidence proves you operate the controls continuously.
4) How often should we re‑scan cookies and trackers?
At minimum, scan after major site releases and on a regular cadence—many teams do monthly. Also scan whenever you add new marketing tools or change tag manager setups. NIS2’s emphasis on continuous improvement means frequent checks.
5) How do NIS2 and DORA pressure affect what enterprise buyers ask about cookies?
NIS2 mandates stronger risk management, incident reporting and third‑party oversight across sectors, while DORA applies similar principles to financial entities. Buyers increasingly seek evidence that your cookie controls align with these frameworks: robust inventory, risk assessments, vendor governance and rapid response.





.svg)






.svg)
.svg)