Most enterprise buyers now insist on proof of operational security before procurement. A glossy policy document is not enough – large customers request evidence of controls in operation. Meanwhile, data breaches remain frequent and expensive. IBM’s 2025 report shows that the global average cost of a breach is USD 4.44 million and that the average cost for U.S. organisations has risen to USD 10.22 million. Breach lifecycles have dropped to 241 days, yet attackers continue to profit from weak controls. Regulators are also active; the EU’s data privacy law requires personal data to be “adequate, relevant and limited to what is necessary”, and supervisory bodies have sanctioned companies for over‑collection and continuous monitoring. In this context, adopting disciplined practices for limiting data becomes a strategic advantage. This ISO 27001 Data Minimization Guide aims to show CTOs, CISOs, engineers and compliance leaders how to embed these practices into their security program. Readers will leave with a practical process for implementing data minimization within an information security management system (ISMS) so that sales cycles with large clients move faster and risk is reduced.
Understanding ISO 27001 and Its Role in Data Protection
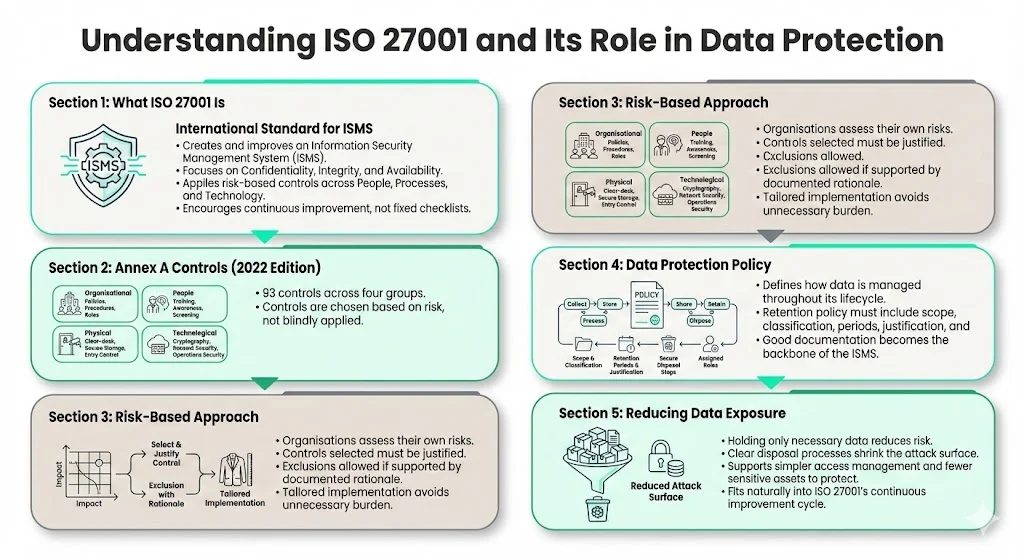
ISO 27001 is an international standard for establishing, implementing, maintaining and improving an ISMS. It helps organisations protect the confidentiality, integrity and availability of their data by applying risk‑based controls across people, processes and technology. Annex A of the 2022 edition contains 93 controls grouped into organisational, people, physical and technological categories. Physical controls include clear‑desk rules, storage and disposal protocols and entry systems for secure areas, while technological controls cover cryptography, operations security and network security. Importantly, ISO 27001 does not force every control on every organisation; instead it asks you to assess your risks and select appropriate controls, justifying exclusions.
An ISO 27001‑compliant data protection policy defines how data is collected, stored, processed, shared, retained and disposed of. Data retention policies must comprehensively address several key components: the defined scope and classification of data, the specific retention periods supported by a clear rationale (including any legal or contractual mandates), procedures for secure data disposal, and clearly assigned roles and responsibilities. A policy that documents data handling practices, assigns ownership and describes deletion processes becomes the backbone of a strong ISMS. Because the standard emphasises risk management and continuous improvement, limiting unnecessary data naturally fits. By storing only what is needed and setting clear disposal steps, you reduce your attack surface and simplify access management.
What Data Minimization Means
Data minimization refers to collecting only the information needed for a specific legitimate purpose, storing it only as long as required and then securely disposing of it. The GDPR defines the principle as ensuring personal data is “adequate, relevant and limited to what is necessary”. RecordPoint’s description of minimization principles adds several dimensions: purpose limitation (collect and use data only for a defined purpose), necessity and proportionality (collect only the amount needed), accuracy (keep information up‑to‑date and dispose of incorrect records), integrity (protect the data during its life) and storage minimization (delete data when it has served its purpose). NIST’s privacy guidance reinforces this, stating that organisations should collect and process only the personal information necessary for identity proofing and that retaining unnecessary information increases vulnerability to unauthorized access.
Adhering to these principles offers tangible benefits. Holding less data reduces exposure in the event of a breach, simplifies compliance with privacy laws and lowers storage and management costs. It also clarifies responsibilities; teams no longer have to wade through thousands of old records to respond to data subject requests or audits. For enterprise‑oriented companies, demonstrating that you limit what you collect and how long you store it sends a strong message of accountability to customers and auditors.
How ISO 27001 Supports Data Minimization in Practice
ISO 27001’s controls provide a framework for limiting data throughout its life cycle. Several controls from Annex A are particularly relevant:
- A.8.3.2 Disposal of media – This control requires organisations to ensure that storage media containing sensitive information is disposed of securely using methods such as data erasure, shredding or degaussing. It also encourages re‑use of hardware when possible, but only after wiping the data completely.
- A.8.3.1 Management of removable media – Organisations must implement procedures for using, storing and disposing of USB drives and other removable media. Guidelines include making the contents of reusable media unrecoverable when no longer needed, maintaining records for media removal and protecting sensitive data with cryptographic techniques.
- A.7.14 Secure disposal or re‑use of equipment – Before re‑using or disposing of equipment, organisations must verify that all sensitive data and licensed software have been removed or securely overwritten.
- A.7.10 Storage media control and A.7.7 Clear desk and screen policy – These controls require management of storage media throughout its life and enforce clean desk and screen rules to prevent unauthorized access to printed or displayed information.
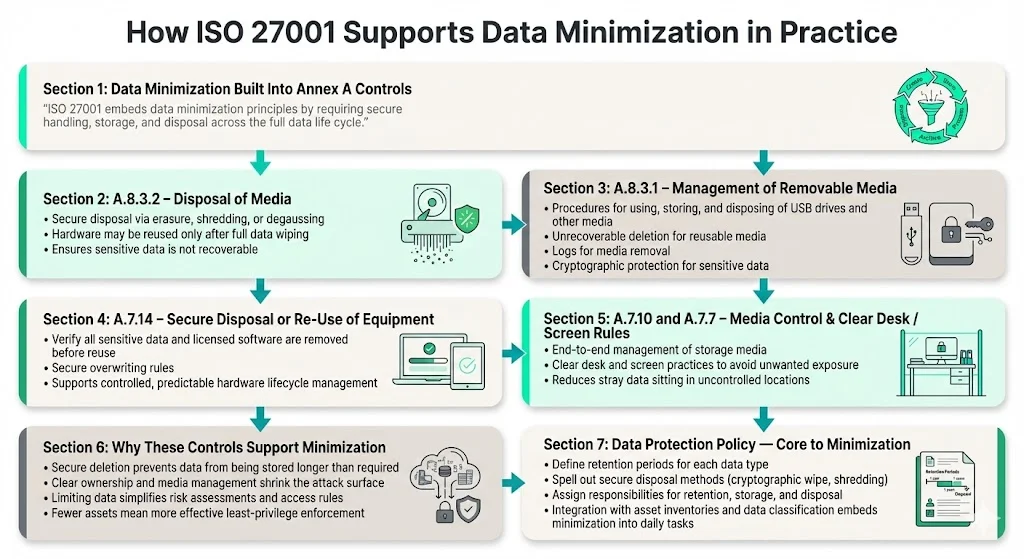
These controls demonstrate that ISO 27001 already embeds minimization principles. By incorporating secure deletion, clear ownership and media management, the standard ensures that data is not kept longer than necessary. Further, limiting data collection simplifies risk assessments and access controls. With fewer records, you can enforce least‑privilege more effectively because there are fewer assets to classify and protect.
A core element of your Information Security Management System (ISMS) is the data protection policy. This policy is essential for data minimization, as it must:
- Define Retention: Specify retention periods for every data type, ensuring compliance with legal, regulatory, and business requirements.
- Detail Disposal: Outline secure disposal methods, such as cryptographic wiping or physical shredding.
- Assign Responsibilities: Clearly assign roles responsible for setting retention schedules, managing secure storage, and executing the disposal process.
When integrated with your asset inventories and data classification system, these clear rules embed data minimization into routine daily operations.
Step‑by‑Step Process for Implementing Data Minimization Under ISO 27001
Drawing on our experience supporting over 6,000 audits at Konfirmity, here is a structured process for implementing minimization. This method turns the ISO 27001 Data Minimization Guide into actionable steps that busy teams can apply.
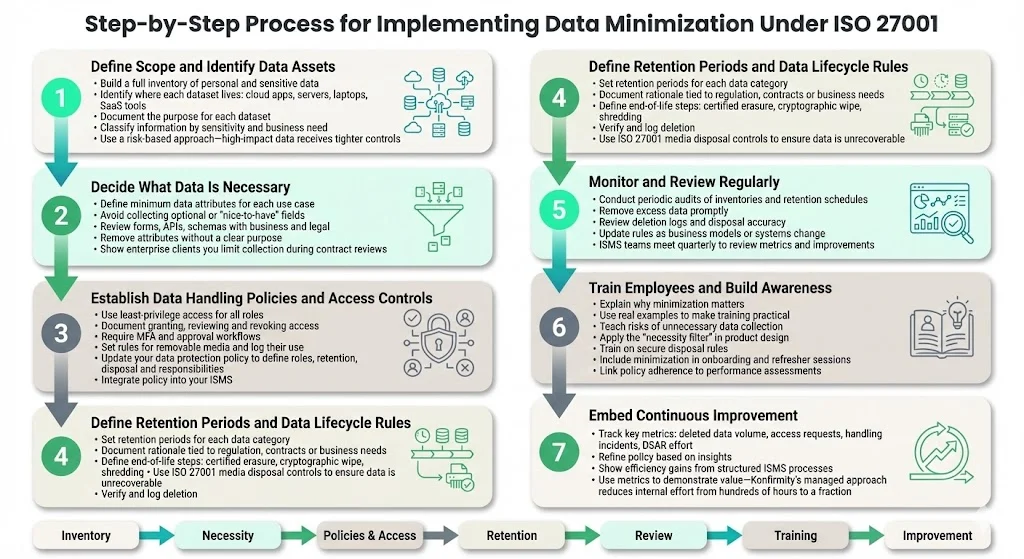
1 Define Scope and Identify Data Assets
To begin, conduct a thorough inventory of all personal and sensitive data your organization collects, processes, and stores. Task the functional owners with providing detailed information on what data they gather, where it is located (e.g., cloud services, servers, laptops), and the specific purpose for each data set. A current and complete inventory is essential because you cannot effectively protect data whose existence you are unaware of, making this initial investment of time critical.
Classify data based on sensitivity, relevance and business necessity. Common categories include personal data (customer records, employee files), confidential business information (pricing, contracts), internal documents and logs. Use a risk‑based approach: high‑impact data like patient records or financial details should be subject to stricter controls and shorter retention schedules, while benign marketing materials can follow lighter rules.
2 Decide What Data Is Necessary
For each use case, define the minimum data attributes required. Avoid collecting “nice‑to‑have” fields that aren’t essential. The GDPR principle of adequacy and relevance means you should only process data necessary for a specified purpose, and RecordPoint’s necessity principle echoes this. In practice, review forms and database schemas with business and legal stakeholders. Remove optional fields unless there is a documented reason to retain them. For example, instead of collecting birth dates for marketing, consider whether age ranges suffice. During contract negotiations with enterprise clients, demonstrate how you limit collection to reassure them that you will not store more than required.
3 Establish Data Handling Policies and Access Controls
Document who can access each data category and under what conditions. ISO 27001 emphasises the principle of least privilege, meaning employees should access only the information necessary for their role. Define procedures for granting, reviewing and revoking access rights; incorporate multi‑factor authentication and approval workflows. For removable media, require authorization and maintain logs. This reduces the chance of accidental over‑sharing or unauthorized transfer.
Ensure your data protection policy is updated or created to reflect these data minimization rules. The policy must clearly:
- Define roles and responsibilities.
- Specify data retention periods.
- Outline secure disposal methods.
Integrate this policy into your Information Security Management System (ISMS) documentation and make it accessible to all employees.
4 Define Retention Periods and Data Lifecycle Rules
For each data category, establish how long information is needed. Regulatory requirements often dictate minimum or maximum retention; for instance, tax laws may require financial records for several years, while privacy regulations require that personal data be deleted as soon as it is no longer necessary. Document the rationale behind each retention period so you can justify it to auditors.
Plan the end of the data lifecycle. For electronic data, use certified erasure tools or cryptographic wiping; for physical records, use shredding. The ISO 27001 controls for disposal of media and re‑use of equipment provide guidance on ensuring data is not recoverable. Include checks that verify deletion is complete and maintain logs for audit purposes.
5 Monitor and Review Regularly
Data minimization is not a one‑time project. Conduct periodic audits to verify that data inventories are current, retention periods are applied and excess data is removed. Review logs of deletion activities and confirm that disposal methods follow policy. As business needs change, update retention schedules and ensure new data sources are classified and minimized. Teams responsible for the ISMS should meet quarterly to review metrics and identify improvements.
6 Train Employees and Build Awareness
Effective data minimization hinges on human behavior. Employees must clearly understand the rationale behind the organization's data collection practices and their specific responsibilities for data handling.
Therefore, robust training is essential. These sessions should:
- Explain the critical importance of the data minimization policy.
- Use practical, real-world examples to illustrate concepts.
- Educate teams on the risks associated with excessive data collection.
- Detail how to apply the "necessity filter" during product design.
- Provide instruction on secure data disposal methods.
Furthermore, integrate data minimization awareness into the employee lifecycle:
- Include it in all new employee onboarding programs.
- Conduct regular refresher training sessions.
- Make compliance with the policy a formal component of performance assessments.
7 Embed Continuous Improvement
After implementing the above steps, measure outcomes. Track metrics such as the volume of data deleted, the number of access requests, incident reports related to data handling and time spent responding to data subject requests. Use these insights to refine your policy. At Konfirmity, we see that organisations often need 4–5 months to implement an ISO 27001‑aligned program with our managed service versus 9–12 months if they do it themselves. We reduce internal effort to roughly 75 hours per year, compared with 550–600 hours for self‑managed programs. These savings come from structured processes and continuous monitoring.
Below is a simple diagram illustrating the minimization process.
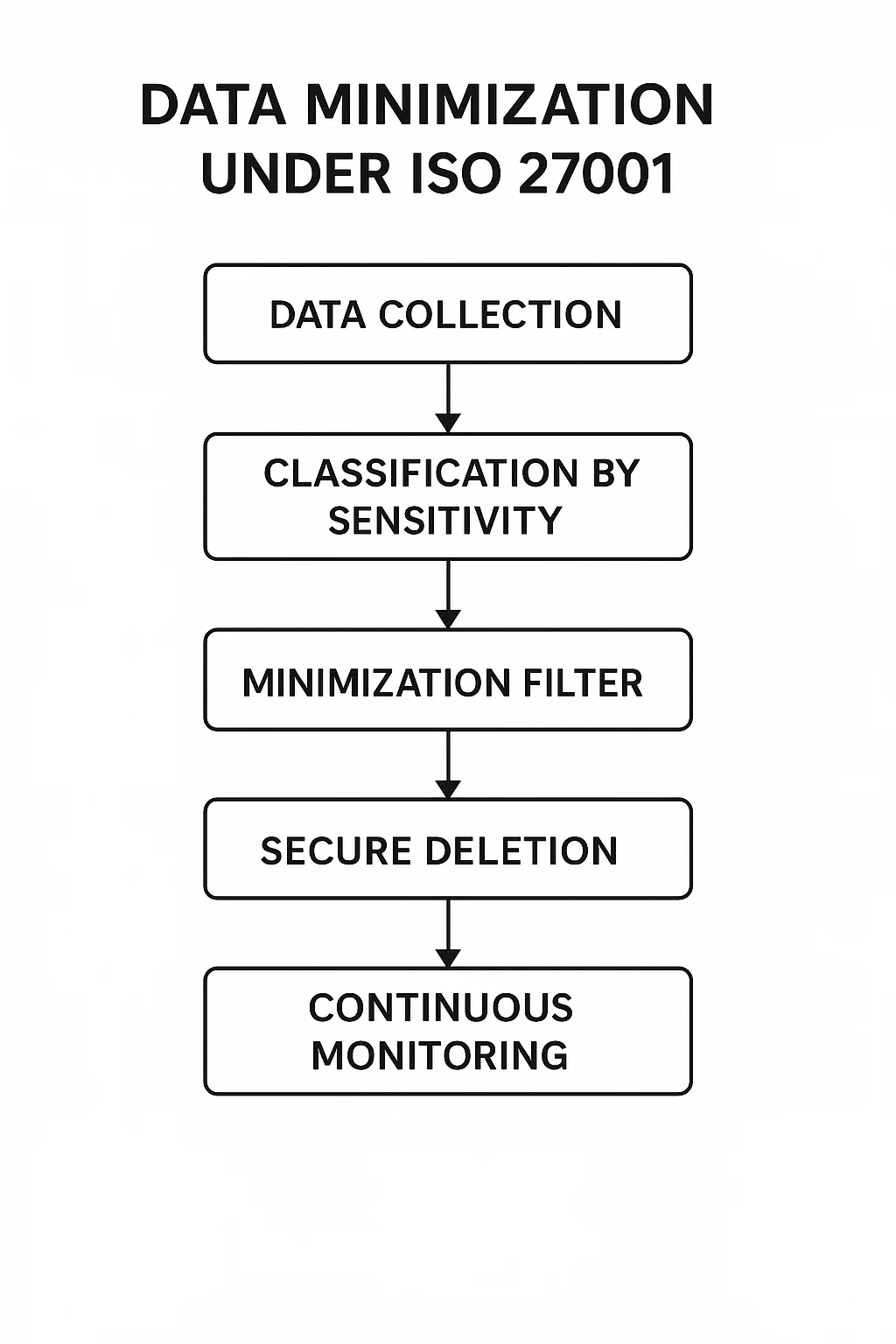
This ISO 27001 Data Minimization Guide outlines each stage clearly to help teams adopt the right habits.
Common Challenges and Ways to Resolve Them
1) Resistance from product or sales teams: Teams often argue for collecting as much data as possible for future analytics. Remind them that enterprise buyers now expect restrictive collection as a sign of maturity and that storing excess data increases liability. Engage stakeholders early to define legitimate purposes and document justifications for each data attribute.
2) Uncertainty about what is essential: It can be difficult to distinguish essential from optional data. Use structured use‑cases and involve legal and privacy experts to avoid over‑collection. When in doubt, omit optional fields or anonymise values. Keep in mind that the GDPR’s definition of adequacy and relevance provides a yardstick.
3) Legacy data backlog: Organisations that have been operating for years often have large volumes of unstructured data. Tackle this by prioritising high‑risk categories first. Use automated discovery tools to classify and tag data, then apply retention rules. Maintain documentation of what has been deleted to show auditors the process.
4) Regulatory or contractual obligations: Some laws require minimum retention periods or specific data sets (e.g., medical records under healthcare regulations). Document these requirements in your policy and apply minimization once the obligation ends. Keep separate retention schedules for different jurisdictions when operating globally.
How Minimization Supports Wider Compliance and Risk Management
Minimizing data reduces the surface area available to attackers. NIST notes that retaining personal information unnecessarily can lead to privacy problems and that limiting collection reduces the amount vulnerable to unauthorized access. During breaches, having fewer records means fewer notifications and lower remediation costs. IBM’s findings that the global average breach cost is USD 4.44 million and the U.S. average is USD 10.22 million illustrate the stakes. Smaller datasets also make it easier to perform thorough access reviews and respond to subject requests under privacy laws. Auditors appreciate clear documentation and clean deletion practices; reducing clutter improves audit readiness and helps avoid findings.
For companies selling to enterprise clients, demonstrating mature data handling practices can expedite procurement. Many customer questionnaires ask about data minimization and retention. Being able to show a documented policy, a current data inventory and logs of secure deletion builds trust and differentiates you from competitors who still hoard data. In healthcare or regulated industries, minimization also aligns with HIPAA’s “minimum necessary” requirement and GDPR’s storage limitation. Integrating minimization into your ISMS means you can reuse evidence across frameworks like SOC 2, HIPAA and GDPR, reducing duplicate work.
How ISO 27001 Interacts With Other Standards
While this ISO 27001 Data Minimization Guide focuses on the core standard, it is important to understand complementary standards that apply to cloud or privacy scenarios.
ISO 27017 – Cloud security guidance: ISO/IEC 27017 is a code of practice for information security controls for cloud services. It builds on ISO 27002 and provides additional guidance for cloud service providers and customers. Ignyte notes that ISO 27017 offers guidance supporting the implementation of controls for cloud service customers and providers and that it serves as a supplementary guide to ISO 27001. It clarifies roles, responsibilities, and issues like multitenancy, staff access controls and lifecycle management of customer accounts. For data minimization, ISO 27017 encourages cloud customers to understand which party controls the data and ensures that providers have clear policies for data deletion and customer isolation.
ISO 27018 – Protecting PII in public clouds: ISO 27018 provides control objectives and guidelines for protecting personally identifiable information in public cloud environments. According to ANSI’s overview, the 2025 edition sets out commonly accepted controls and guidelines for implementing measures to protect PII, building on the privacy principles in ISO 29100. It emphasises transparency, accountability and secure erasure of temporary files and includes an extended control set for PII protection such as notification of disclosures. This standard is intended for public cloud PII processors and helps bring cloud providers into compliance with privacy obligations.
ISO 27701 – Privacy Information Management System: ISO 27701 extends an ISMS to cover privacy management. The 2025 edition has been re‑drafted as a standalone management system standard. ANSI explains that it specifies requirements for establishing, implementing and continually improving a Privacy Information Management System (PIMS), providing guidance for both PII controllers and processors. It maps to privacy frameworks such as ISO 29100 and GDPR and strengthens the governance of personal data. For organisations handling large volumes of personal data, layering ISO 27701 on top of ISO 27001 ensures that privacy controls (including minimization, consent management and data subject rights) are addressed systematically.
These standards show that minimization is not just an ISO 27001 concept; it is a consistent theme across cloud and privacy frameworks. By adopting minimization, you are better prepared to meet cross‑framework obligations and support due diligence during enterprise sales.
Checklist for Implementing Data Minimization
- Complete a data asset inventory.
- Apply a minimization filter to every data collection page and process.
- Define data classification tiers based on sensitivity.
- Define and enforce access controls and least‑privilege.
- Establish retention periods for each data category with rationale.
- Implement secure deletion or anonymisation procedures.
- Document the data protection policy, retention schedules and handling rules.
- Train employees on minimization practices and responsibilities.
- Set a periodic audit schedule to review inventories, retention and deletion.
Conclusion
Companies targeting enterprise clients need more than policies; they need operational security that can withstand scrutiny from buyers, auditors and attackers. Data minimization under ISO 27001 is a core part of that program. Limiting collection, defining retention periods and enforcing secure deletion shrink the attack surface, reduce costs and simplify compliance across privacy laws. This ISO 27001 Data Minimization Guide provides a structured process that busy teams can apply. Start with a clear inventory and classification, set necessary data fields, establish access and retention rules, and embed monitoring and training into everyday routines. Draw on external standards like ISO 27017, ISO 27018 and ISO 27701 when cloud or privacy contexts apply to ensure your program is complete.
At Konfirmity we have seen that organisations that integrate minimization early spend far fewer hours on audits and enjoy smoother procurement. Security that reads well but fails in practice is a liability; build controls once, operate them daily, and let compliance follow. Start with security and arrive at compliance. This ISO 27001 Data Minimization Guide can serve as a blueprint for your program.
Frequently Asked Questions
1) What are the three main points of data minimization?
The core themes are purpose limitation – collect data only for a specific legitimate purpose and use it only for that purpose; data reduction – avoid collecting extraneous fields and limit information to what is required; and retention limitation – keep data only as long as needed and then securely delete or anonymise it.
2) What is the ISO 27001 data management policy?
Under ISO 27001, a data management or data protection policy defines how your organisation collects, stores, processes, shares, retains and disposes of information. It includes scope and classification, retention periods based on legal and business requirements, secure disposal procedures and clearly defined roles and responsibilities. This policy forms part of your ISMS documentation and guides daily data handling practices.
3) What is ISO 27017 and ISO 27018?
ISO 27017 is a code of practice that provides guidance for information security controls for cloud services. It supplements ISO 27001 and ISO 27002 and outlines responsibilities for both cloud service providers and customers. ISO 27018 is a code of practice for protecting personally identifiable information in public clouds. It sets out commonly accepted control objectives and guidelines for PII protection, including secure erasure of temporary files and disclosure notifications. Both standards complement an ISMS when you handle data in cloud environments.
4) Does ISO 27001 require data loss prevention (DLP)?
ISO 27001 does not mandate specific technologies. Instead, it requires organisations to perform a risk assessment and apply appropriate controls. Measures such as encryption, access control, secure deletion and monitoring fulfil similar objectives. If your risk assessment identifies that preventing unauthorized data exfiltration is necessary, implementing DLP tools or equivalent controls may be justified, but the standard itself is technology‑agnostic.





.svg)






.svg)
.svg)