When you sell into the enterprise and healthcare segments, security isn’t a checkbox—it’s an operational discipline. Most procurement teams now request proof of controls before contracts are signed. They ask for evidence of incident management, access reviews, vulnerability handling, business continuity and recovery. Deals stall when a vendor offers only a certificate but cannot show how it would handle a security event. The modern buyer looks past the paper; they want confidence that incidents will be handled quickly, transparently, and in line with contractual obligations. In 2024 the global average cost of a data breach rose to US $4.88 million, the steepest increase since the pandemic. Regulators imposed billion‑dollar fines for mishandling sensitive data. In this climate, a strong ISO 27001 Incident Response Plan is as much a sales enabler as a compliance requirement.
Why mature incident response—not just a certificate—matters
Certification alone does not protect clients from breaches or downtime. Enterprise buyers have learned that a framed certificate without continuous operations behind it is worthless. They expect vendors to demonstrate mature incident detection, escalation, containment, communication and recovery. When incidents are mishandled, the consequences are immediate: contracts are rescinded, renewals are delayed, and reputations suffer. According to IBM’s 2024 cost of a breach report, business disruption and customer churn made up the largest share of the US $4.88 million average breach cost. Breaches now take weeks or months to resolve, so buyers look for partners who can limit downtime and communicate effectively during a crisis.
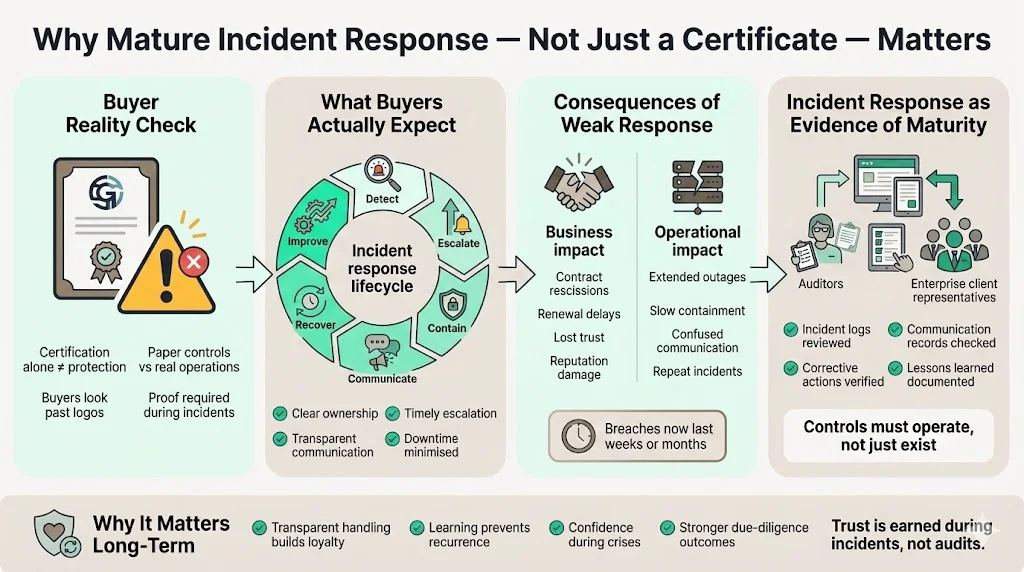
Incident response sits at the intersection of technical controls, legal obligations and customer trust. Auditors inspect incident logs, communication records and corrective actions to judge whether an organisation operates its controls or merely documents them. Enterprise clients stay loyal when they see a vendor handle issues transparently, learn from them and prevent recurrences. Without a mature plan and disciplined execution, even well‑designed controls will crumble under real‑world pressure.
What an ISO 27001 Incident Response Plan is
An ISO 27001 Incident Response Plan is a document and process that outlines how an organisation prepares for, detects, assesses, responds to, recovers from and learns from information security incidents. It lives within the wider Information Security Management System (ISMS) mandated by ISO 27001. The plan’s purpose is to minimise damage and restore service by defining roles, responsibilities, workflows and communications.
Annex A controls and incident management
ISO 27001:2022 introduces control 5.24 in Annex A—“Information security incident management planning and preparation”—which requires organisations to develop procedures to manage incidents that compromise confidentiality, integrity or availability. Control 5.24 emphasises assigning clear roles, establishing reporting channels and ensuring training so that only qualified staff handle incidents. Related controls 5.25 and 5.26 cover responses to events and lessons learned. Other clauses tie incident management to business continuity (A.8) and communications. Together, they demand a documented, repeatable and tested process integrated into the ISMS.
Plan versus process
The plan is the written document outlining mission, scope, definitions, severity levels and procedures. The incident management process is the ongoing operational workflow: monitoring, detection, escalation, response, recovery and post‑incident review. NIST’s evolving guidance (Special Publication 800‑61 rev 3) describes incident response as a lifecycle that has become longer and more integrated with risk management. The plan provides the framework; the process is the day‑to‑day execution, using playbooks and automation. Both must align. Many vendors draft a plan during certification but neglect to operationalise it—one of the most common audit findings we see.
Why due diligence focuses on incident response
Vendor questionnaires routinely ask about incident history, breach notifications, and incident response processes. Security teams want to know how soon you would notify them, which legal and regulatory obligations you recognise and whether you have tested your plan. Poor answers slow deals or trigger additional assessments. In regulated industries, customers may require evidence that your plan aligns with HIPAA incident reporting or trust services criteria such as assigning responsibility, containing incidents, documenting actions and evaluating effectiveness. A mature incident response plan therefore isn’t just about compliance; it directly affects revenue.
Why ISO 27001 Incident Response Plans matter for enterprise‑focused companies
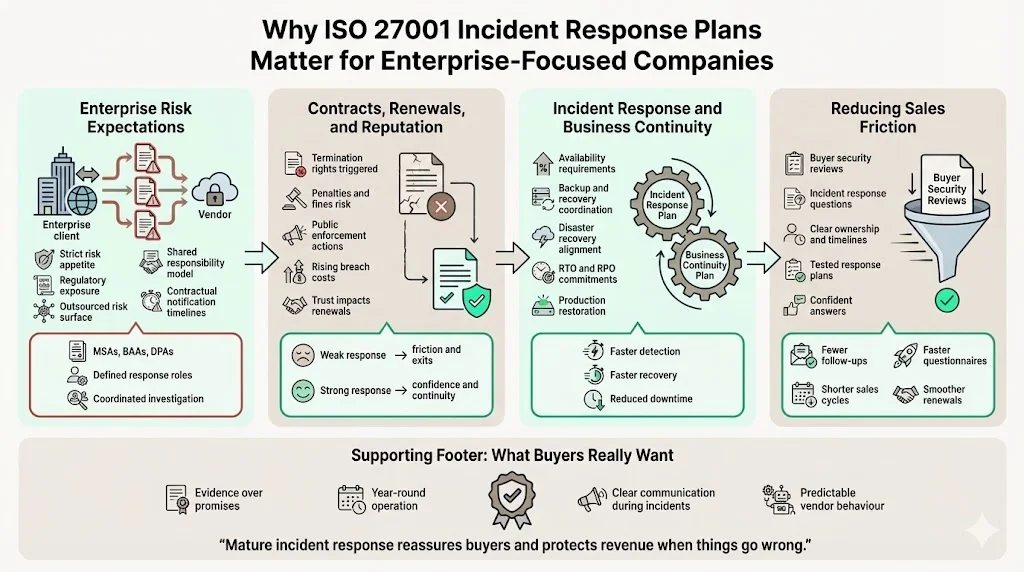
1) Enterprise risk expectations and shared responsibility
Enterprises operate under strict risk appetites. They must protect their own data and that of their customers, abide by regulations (GDPR, HIPAA, industry‑specific rules) and maintain uptime. When they outsource services, they extend their risk surface. Buyers expect vendors to share the burden—this is codified in master service agreements (MSAs), business associate agreements (BAAs) and data processing addenda (DPAs). These contracts often require vendors to notify customers within hours of a suspected breach and to coordinate on investigation and remediation. NIST emphasises that contracts with external providers must spell out incident response roles and authorities; we often negotiate these clauses on behalf of our clients.
2) Impact on contracts, renewals and reputation
Incidents handled poorly can void contractual obligations, trigger termination rights, and lead to penalties. Regulators across the US and Europe have levied eye‑watering fines: Texas reached a US $1.4 billion settlement with Meta for biometric violations; the Irish Data Protection Commission fined LinkedIn US $336 million for improper advertising; and Uber paid US $324 million over GDPR failures. Meanwhile, the average breach cost continues to climb. Enterprise clients weigh these risks when evaluating vendors. A robust incident response capability reduces the chance of breaches, shortens downtime and builds trust—making renewals smoother and reducing negotiation friction.
3) Connection to business continuity and service availability
Incident response is inseparable from business continuity. ISO 27001 requires organisations to ensure availability of information processing facilities and to restore operations after disruptions. HIPAA’s Security Rule calls for contingency plans including backups, disaster recovery and emergency mode operations. If a ransomware attack takes down production systems, the incident response team must coordinate with disaster recovery teams to restore data and validate integrity. The plan should integrate with service level agreements (SLAs), ensuring that recovery time objectives (RTOs) and recovery point objectives (RPOs) are met. Mature programmes reduce mean time to detect (MTTD) and mean time to recover (MTTR), metrics your clients will ask about.
4) Reducing sales friction
Security reviews can stretch procurement cycles by months. Prospects ask for your latest SOC 2 report, ISO 27001 certificate and detailed answers to hundreds of questions. Many of those questions centre on incident response: Do you have a plan? Who is on your response team? When will you notify us? A tested, documented ISO 27001 Incident Response Plan allows your sales and customer‑success teams to answer confidently. By operating a human‑led managed programme, Konfirmity typically reduces time to complete security questionnaires by 50%, helping clients close enterprise deals faster. Customers see that we not only implement controls but maintain them year‑round, giving them assurance during renewals.
ISO 27001 requirements related to incident response
Where incident response appears in ISO 27001
ISO 27001:2022 integrates incident management throughout the standard. Clause 6 (Planning) requires organisations to plan responses to information security incidents as part of their risk treatment. Clause 9 (Performance evaluation) mandates monitoring, measurement, analysis and evaluation of the ISMS, including incidents. Clause 10 (Improvement) covers nonconformity and corrective action, which includes learning from incidents. In Annex A, control 5.24 mandates a documented incident response process. Controls 5.25 and 5.26 focus on responding to incidents and learning from them. Controls in section 7 (Business continuity) require integration with business continuity. Control 8.1 (Operational planning and control) links incident response to procedures and responsibilities.
Key clauses and Annex A controls
- 5.24 Information security incident management planning and preparation—establish and maintain a process for incident management, including roles, escalation, and training.
- 5.25 Assessment and decision on information security events—define criteria for identifying and assessing events and deciding whether they are incidents.
- 5.26 Response to information security incidents—take action to prevent recurrence, mitigate impacts and inform relevant parties.
- A.8 Business continuity—plan for system availability and recovery, aligning with incident response.
- 4.3 Scope of the ISMS—ensure incident response covers systems and data within scope.
- A.10 Communications—manage internal and external communications during incidents.
Link to risk assessment and security policies
ISO 27001 requires a risk‑based approach. The risk assessment identifies potential threats (e.g., malware, insider threats, third‑party failures) and informs which scenarios must be addressed in the incident response plan. Policies and procedures must include management commitment, scope, definitions, priorities and performance measures. The plan must be documented and repeatable, meaning it can be consistently executed, measured and improved. Evidence of this repeatability—such as logs, playbooks, test reports—is what auditors and customers review.
Incidents that fall under ISO 27001 scope
What constitutes an information security incident
ISO 27001 defines an incident as an event that compromises confidentiality, integrity or availability. According to the guidance, incidents include any unauthorised disclosure, modification, destruction or loss of an asset. In practical terms, this covers events from minor policy violations to full‑scale breaches. The plan should define categories and severity levels to help teams prioritise.
Common examples
- Data breach and data leakage: Unauthorised access to personal or proprietary data; exfiltration via unsecured APIs, misconfigured cloud storage or insider abuse.
- Unauthorised access: Compromised credentials, privilege escalation, bypassing authentication mechanisms.
- Malware and ransomware: Infection of systems through phishing, supply‑chain attacks or drive‑by downloads; encryption of data demanding ransom.
- Service outages tied to security events: Distributed denial‑of‑service (DDoS) attacks, system crashes triggered by exploitation.
- Third‑party and supplier incidents: Breaches at a vendor that expose your data; vendor outages affecting your services.
The scope should include all systems and data within the ISMS. Avoid making it so broad that minor issues swamp the team; instead, classify events based on risk and impact. At Konfirmity we typically define four severity levels, each with response times and notification requirements. High‑severity incidents demand immediate escalation to executive and legal teams; low‑severity events are logged and reviewed periodically.
Core components of an ISO 27001 incident response plan
Below is a breakdown of the major elements you should include. Each component should be documented in the plan and supported by evidence in practice.
1. Roles and ownership
Clearly defined roles are the foundation. The incident response manager owns the process end‑to‑end, with authority to declare incidents and coordinate actions. The team typically includes security engineers, IT operations, legal counsel, communications/PR and, for healthcare, a privacy officer. A senior executive (e.g., the CISO) provides sponsorship and approval. NIST and the AICPA emphasise assigning responsibility for maintaining and executing the incident response programme. For each role, define duties, on‑call schedules, backup contacts and decision authority.
2. Incident identification and threat detection
Incidents can be detected via monitoring tools, user reports, third‑party notifications or audit findings. A detection capability might include intrusion detection systems, endpoint detection and response (EDR), security information and event management (SIEM) platforms, API monitoring and automated alerting. Employees should be trained to report suspicious activity through secure channels. Education and awareness are critical; control 5.24 calls for ensuring people know how to report and respond. Integrate detection with vulnerability management to spot exploit attempts early.
3. Incident classification and risk assessment
Once an event is detected, assess its severity based on impact on confidentiality, integrity and availability; scope of affected data; regulatory implications; and business impact. Risk‑based prioritisation enables the team to allocate resources effectively. Use your existing risk assessment to map threats to response actions. For example, a malware infection on a non‑production workstation may be low severity, while unauthorised access to PHI triggers HIPAA breach reporting. The classification drives response timelines, communication requirements and escalation.
4. Response procedures
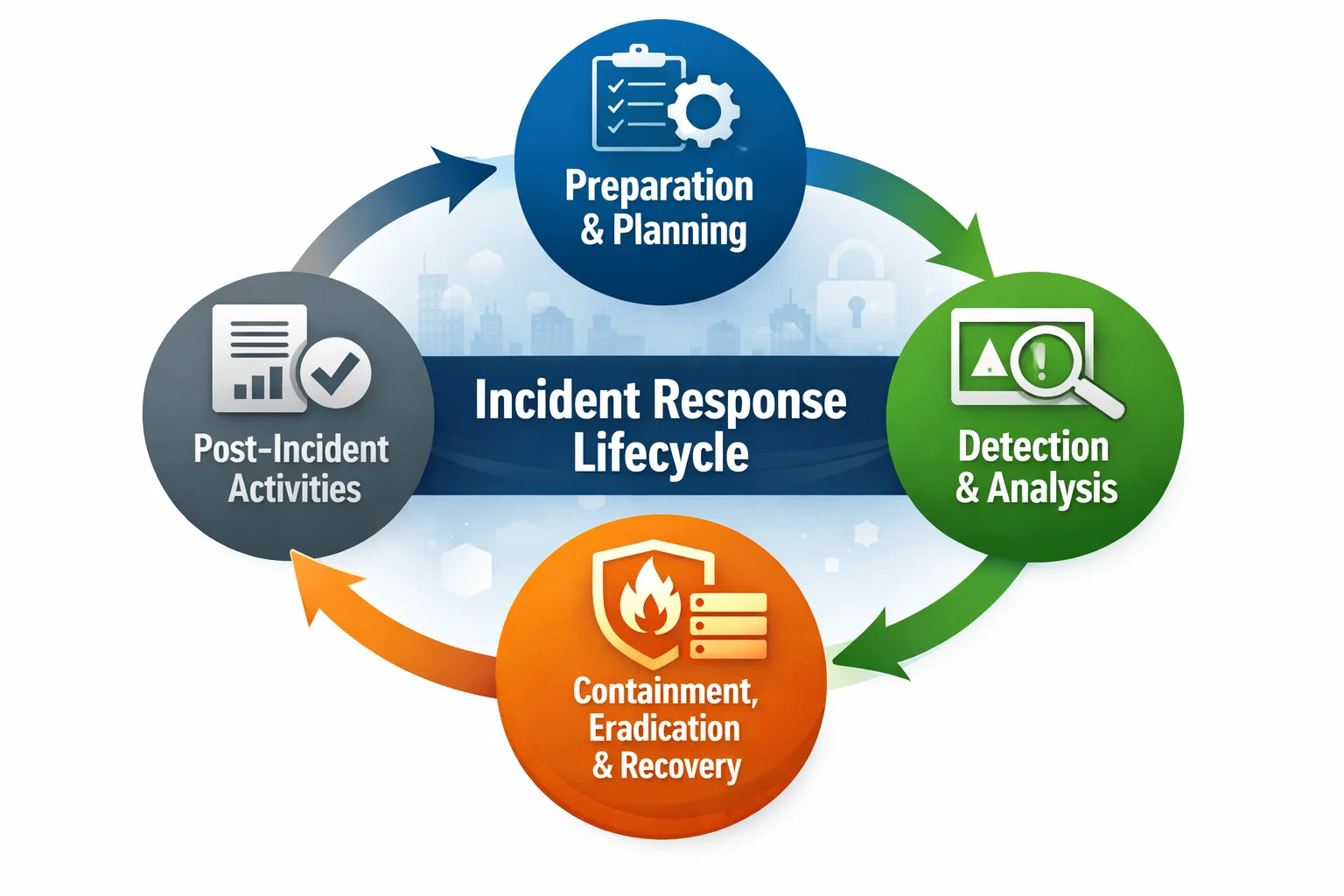
Document step‑by‑step actions for each incident type and severity level. Procedures typically include verifying the incident, containing it (isolating affected systems, revoking credentials), preserving evidence, notifying stakeholders, eradicating the threat, recovering systems (restoring from backups, verifying integrity) and closing the incident. NIST’s lifecycle emphasises these stages: Preparation, Detection & Analysis, Containment, Eradication & Recovery, Post‑Incident Activities. The plan should specify who executes each step, what approvals are needed, and what tools are used. Include triggers for involving third parties—e.g., when to contact cloud providers, vendors or incident response retainers.
5. Investigation and root cause analysis
Auditors look for evidence that the organisation investigates incidents thoroughly and implements corrective actions. After containment and recovery, perform a root cause analysis to determine why the incident occurred, how it was detected and what controls failed. Document findings in an incident report; include timeline of events, systems affected, data exposed, actions taken and lessons learned. The AICPA’s criteria call for evaluating the effectiveness of the incident response and implementing improvements. Use post‑mortems to strengthen controls, update policies and feed into the risk assessment.
6. Communication plan
Communication must be timely, accurate and appropriate to the audience. Internally, notify the incident response team, leadership and any affected departments. Executives and boards require high‑level updates on impact and recovery progress. For customer communications, have pre‑approved templates that comply with legal and contractual obligations. Privacy regulations such as GDPR and HIPAA require notifying affected individuals and regulators within specific timeframes. The plan should define communication channels, spokespersons and escalation points. NIST notes that external relations (public affairs, legal, HR) play critical roles in incident response.
7. Legal and regulatory considerations
Incident response intersects with many laws and contracts. HIPAA’s Security Rule demands policies to identify and respond to incidents, mitigate harmful effects and document outcomes. GDPR mandates notifying authorities within 72 hours of becoming aware of a personal data breach and informing affected individuals if there is a high risk to their rights. Contracts may impose stricter notification timelines or specific communication formats. Work closely with legal counsel to interpret obligations, coordinate with insurance providers, and decide whether to involve law enforcement. Keep in mind cross‑border data transfers, attorney‑client privilege and discovery implications.
8. Recovery plan and business continuity
Effective recovery is more than restoring data—it includes validating system integrity, ensuring that the vulnerability is patched and confirming that business operations are fully functional. Integrate your incident response plan with business continuity and disaster recovery plans. HIPAA requires contingency plans for backup and restoration; the AICPA recommends restoring affected environments, determining root causes and improving procedures. After recovery, test that systems meet performance requirements, and monitor for reinfection or recurrence. Document recovery actions and ensure that lessons inform future planning.
The following diagram illustrates the incident response lifecycle used by Konfirmity and many standards bodies:
Step‑by‑step: how to build an ISO 27001 incident response plan
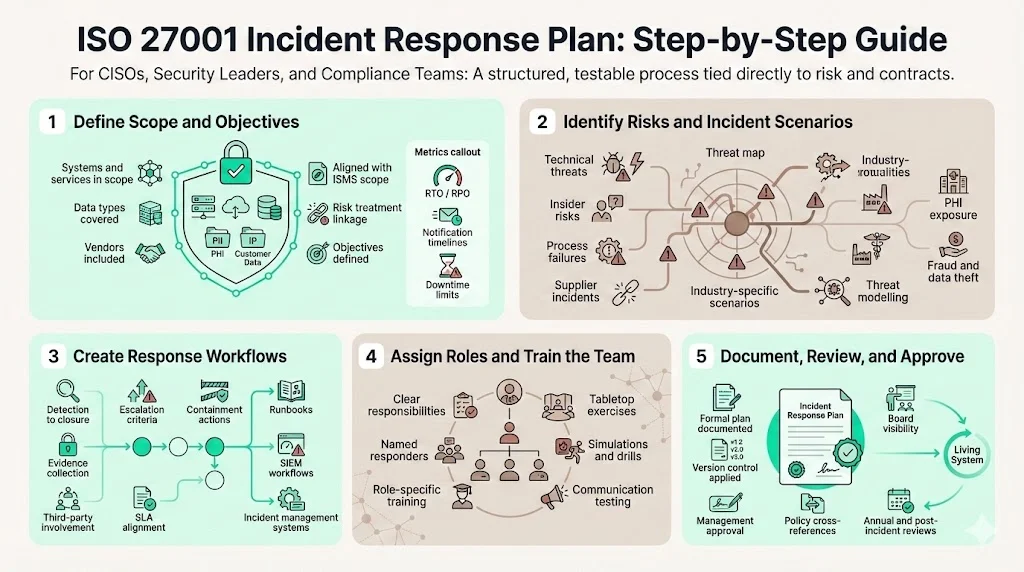
Step 1: Define scope and objectives
Identify which systems, data types, services and vendors fall under the plan. Align this with the ISMS scope (clause 4.3) and risk treatment plan. Define objectives such as minimising downtime, protecting confidentiality and meeting contractual obligations. Include metrics like maximum acceptable outage (RTO/RPO) and notification timelines.
Step 2: Identify risks and likely incident scenarios
Leverage your existing risk assessment to identify threats and vulnerabilities. Consider technical threats (zero‑day exploits, insider threats), process failures (improper access reviews, unpatched systems) and supplier risks. Map these scenarios to response actions. For healthcare, include potential exposures of PHI; for fintech, emphasise payment fraud and data theft. Use threat modelling to prioritise scenarios.
Step 3: Create clear response workflows
Develop decision trees or playbooks for each category of incident. Define the sequence from detection to closure. Include criteria for escalation, containment strategies (network isolation, service failover), evidence collection and involvement of third parties. Align workflows with contractual SLAs. Tools such as runbooks in your incident management system or orchestrated workflows in your SIEM help automate tasks.
Step 4: Assign roles and train the team
Document responsibilities and ensure that the incident response team knows them. Provide role‑specific training and conduct tabletop exercises, simulations and red‑team drills. The HHS guidance recommends testing plans through tabletop exercises and communications drills to identify weaknesses before a real incident. Periodic training ensures that new staff understand their duties and that procedures remain current.
Step 5: Document, review and approve
Produce the formal plan, including all components described above. Implement version control and track changes. Obtain approval from senior management and the board. Incorporate the plan into the ISMS; cross‑reference related policies (access control, change management, business continuity). Schedule regular reviews—at least annually or after significant incidents—to keep the plan aligned with evolving threats and business changes.
Testing, monitoring and continuous improvement
Merely having a plan is insufficient; you must test and monitor its effectiveness. Conduct regular tabletop exercises to simulate scenarios and evaluate communication and decision‑making. Perform live simulations to test technical procedures, such as failover to backup systems or restoring from backups. Track metrics such as incident frequency, detection time, containment time, recovery time and recurrence rate. Feed these metrics back into the ISMS to refine controls and update risk assessments. NIST emphasises continuous improvement and performance measurement in incident response. After each real incident, conduct a retrospective to identify root causes and implement corrective actions.
Common mistakes companies make
From our experience supporting thousands of audits, several patterns recur:
- Treating incident response as a one‑time document: Teams rush to draft a plan to pass an audit and then forget about it. Months later, the plan is outdated, roles have changed and new systems are uncovered. Auditors expect evidence of ongoing execution and improvement.
- Overly technical plans that no one follows: Plans that read like system manuals are unusable in a crisis. Keep procedures clear, actionable and accessible. Focus on who, what, when and how; avoid jargon that non‑technical stakeholders can’t understand.
- Weak communication planning: Many plans ignore communications beyond the IT team. In practice, legal, HR, PR and customer success are critical. Without a communication plan, inconsistent or delayed messages can damage trust and violate regulations.
- Failing to link incidents back to risk management: Incident lessons should update risk registers, influence control improvements and inform investments. Organisations often skip this step and thus repeat mistakes.
What auditors look for during ISO 27001 audits
Auditors assess both documentation and evidence of execution. Expect them to request:
- Incident logs: Records of events, detection times, classification, actions taken and closure. Evidence must show that incidents are tracked and managed consistently.
- Investigation reports and root cause analyses: Detailed reports of significant incidents with lessons learned and corrective actions. These demonstrate continuous improvement.
- Communication records: Evidence of notifications to stakeholders and customers. Auditors will check whether notifications met contractual timelines and included required information.
- Test results: Reports from tabletop exercises and live simulations, showing who participated, what issues were found and how they were addressed. HHS recommends testing to identify weaknesses.
- Corrective actions and policy updates: Proof that incidents led to policy or control changes. Auditors will ask for change logs, updated risk assessments and evidence that management approved improvements.
Auditors are alert to red flags: plans with no evidence of testing; incident logs missing severity classifications; delayed notifications; or repeated incidents without remediation. Being transparent, providing comprehensive records and showing a culture of learning will build confidence.
How a strong incident response plan supports enterprise sales
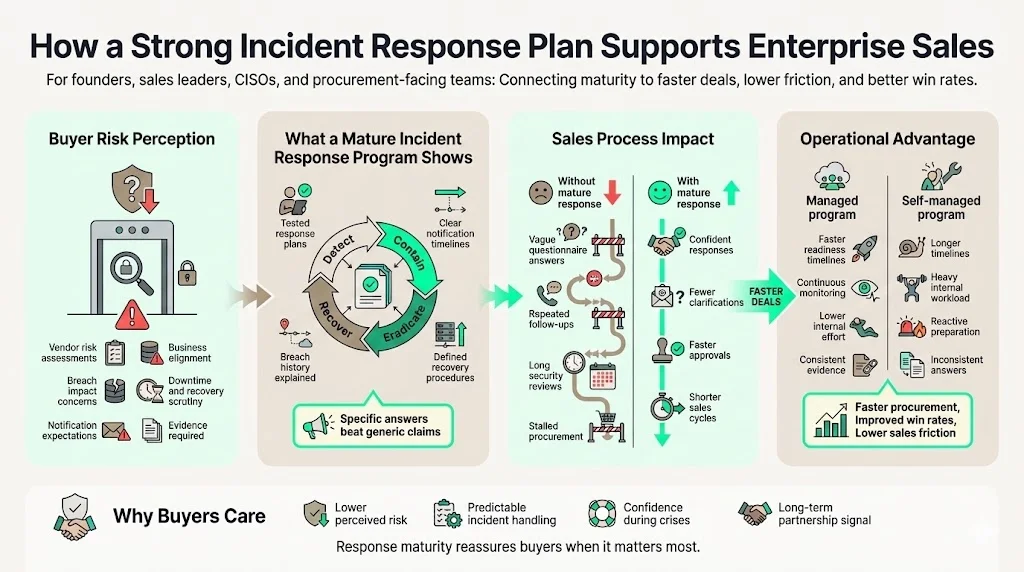
When your incident response programme is mature, procurement and security teams see less risk. This translates into faster security reviews. During vendor risk assessments, you can answer questions about breach history, notification timelines and recovery procedures with specifics rather than generalities. Your responses to vendor questionnaires about incident response and business continuity become differentiators. Customers appreciate partners who practice “outcome as a service” rather than offering a self‑serve compliance tool.
At Konfirmity, we typically achieve SOC 2 Type II readiness in 4–5 months compared to 9–12 months for self‑managed programmes, thanks to our dedicated teams and continuous monitoring. For ISO 27001, small organisations reach readiness in 6–12 months, while mid‑sized ones take 12–18 months. Because we operate the programme, clients invest around 75 hours per year instead of hundreds of internal hours. In sales cycles, this translates into fewer follow‑up questions, faster procurement and improved win rates.
Conclusion
Building a ISO 27001 Incident Response Plan is not just a compliance task—it is a business asset. In an era of rising breach costs and aggressive enforcement, enterprises and regulators demand proof that vendors can detect, contain and recover from incidents. A mature plan integrates with risk management, business continuity and communications. It assigns clear roles, outlines procedures, complies with legal obligations and continuously improves through testing and lessons learned. For companies selling to enterprise clients, a strong incident response capability accelerates sales, reduces renewals friction and protects long‑term relationships.
Key takeaways:
- Incident response is operational, not just documentation. Define clear roles, workflows and communications, and practise them.
- Align the plan with your risk assessment and ISMS. Use threat models to prioritise scenarios and define severity levels.
- Test regularly. Tabletop exercises and live simulations uncover gaps. Document and implement improvements.
- Integrate with business continuity and legal requirements. Recovery is more than restoring data; it includes complying with notification laws and contractual obligations.
- Leverage human‑led managed services. A partner that executes controls and maintains evidence year‑round reduces the burden on your team and improves audit and sales outcomes.
By starting with security and arriving at compliance, you build a programme that stands up under buyer scrutiny, auditor inspection and adversary attacks. An ISO 27001 Incident Response Plan designed and operated with discipline becomes a competitive advantage.
Frequently asked questions (FAQ)
1) Is an incident response plan mandatory for ISO 27001?
Yes. ISO 27001:2022 requires organisations to plan and prepare for incidents. Annex A control 5.24 specifically states that a formal incident management process must be established. Without it, you cannot claim conformity. Beyond compliance, such a plan is vital for protecting customer data and maintaining trust.
2) What incidents fall under ISO 27001 scope?
Any event that compromises confidentiality, integrity or availability of information within the ISMS scope qualifies. This includes data breaches, unauthorised access, malware infections, service outages caused by attacks and third‑party incidents. Minor policy violations may be treated as security events until severity is assessed. Use a risk‑based classification to determine which events require full incident response.
3) Who owns the incident response process?
Ownership typically resides with the incident response manager or CISO, who is responsible for maintaining the plan and coordinating activities. However, effective response is cross‑functional: IT operations handle system recovery, security engineers analyse and contain threats, legal manages regulatory obligations, communications leads external messaging and executives make high‑level decisions. Responsibility should be assigned in the plan and supported by training.
4) How often should incident response plans be tested?
Plans should be tested at least annually and after significant changes to systems or organizations. NIST and HHS recommend tabletop exercises and live simulations to identify weaknesses. Some organisations test quarterly for critical systems. Testing frequency should align with your risk profile and contractual obligations.
5) What evidence do auditors expect to see?
Auditors look for incident logs with timestamps and classifications, investigation reports with root cause analyses, communication records, corrective actions, test reports and proof of management review. They also check that the plan is versioned, approved and periodically reviewed. Evidence of continuous improvement—such as updates after incidents or tests—is key.





.svg)






.svg)
.svg)