Procurement cycles have changed. Most enterprise clients now ask vendors for evidence that software and data will be protected over time, not just in a single audit. At the same time, engineering teams are decomposing applications into microservices to gain speed and flexibility. These trends interact in unexpected ways. A microservices architecture multiplies endpoints and hidden dependencies; it also complicates the collection of artefacts needed to pass audits. Microservices And ISO 27001 refers to the interplay between this distributed model and the well‑established information security management standard that helps companies build, operate and prove a robust security posture. This article outlines why microservices raise the stakes, why ISO 27001 matters to enterprise buyers, how to translate the standard into practical controls for microservices, and how to use templates and guidance from NIST to build a program that stands up to regulators and clients.
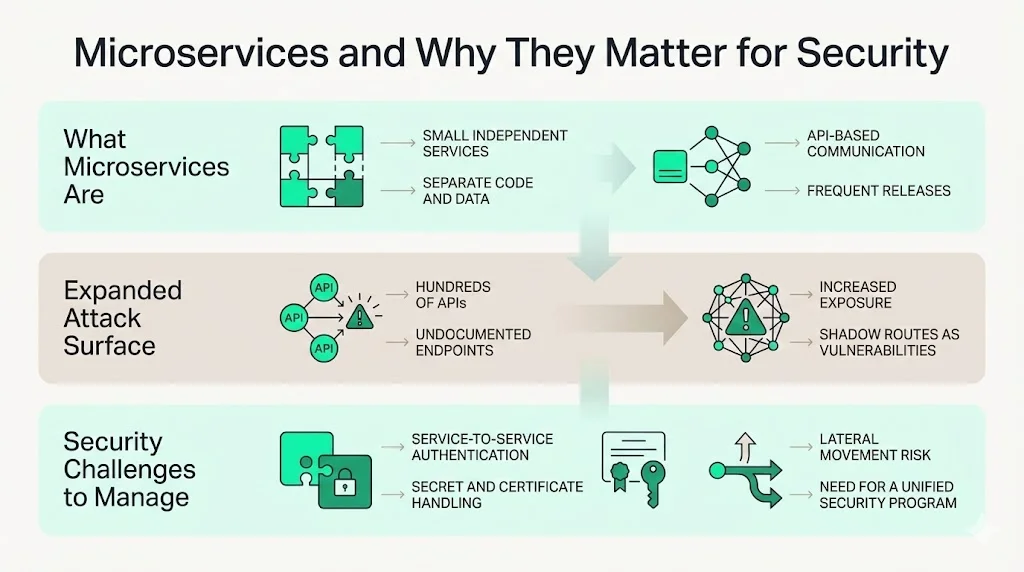
What are microservices and why do they matter for security?
Microservices break a large application into small, independently deployable services. Each service owns its own code, data, and lifecycle, and communicates with other services through APIs. This design enables autonomous teams and frequent releases but introduces more surface area. A 2023 study reported that API calls accounted for 71% of web traffic and that organisations typically managed over 421 APIs, with machine‑learning tools discovering 30.7% more “shadow” endpoints than their owners knew about. Each undocumented endpoint is a vulnerability. Moving a monolith to a microservices architecture can create hundreds of routes. Services must authenticate both user‑generated traffic and service‑to‑service requests, handle secrets and certificates across environments, and guard against lateral movement when one service is compromised. Without a unifying security program, ad‑hoc fixes turn into technical debt.
Why ISO 27001 resonates with enterprise buyers
ISO 27001 is a globally recognised standard for building and maintaining an information security management system (ISMS). It sets out a risk‑based approach: define the scope, identify and assess risks, select controls from Annex A, operate the controls, and continually improve. The 2022 revision reduces the number of Annex A controls to 93 grouped into four themes—organisational, people, physical, and technical. Certification lasts three years with annual surveillance audits. For buyers this matters. A SOC 2 Type II audit, often requested in procurement, includes an observation period of 6 to 12 months; without an ISMS, gathering evidence for this window is painful. The average cost of a data breach in 2024 reached USD 4.88 million, and detection still takes 277 days. Regulators are increasing pressure: the U.S. government has proposed requiring health‑care entities to maintain an asset inventory and network map to track protected data flows. As a result, buyers use ISO 27001 certification as a proxy for security maturity and vendor risk management.
From a vendor perspective, aligning microservices with ISO 27001 helps satisfy multiple frameworks. Many SOC 2 controls mirror Annex A. HIPAA’s technical safeguards—access control, audit logs, encryption—map directly. GDPR and India’s Digital Personal Data Protection Act emphasise minimising and documenting data processing, which an ISMS supports. Integrating Microservices And ISO 27001 into program design therefore reduces repetitive work across frameworks and accelerates sales cycles.
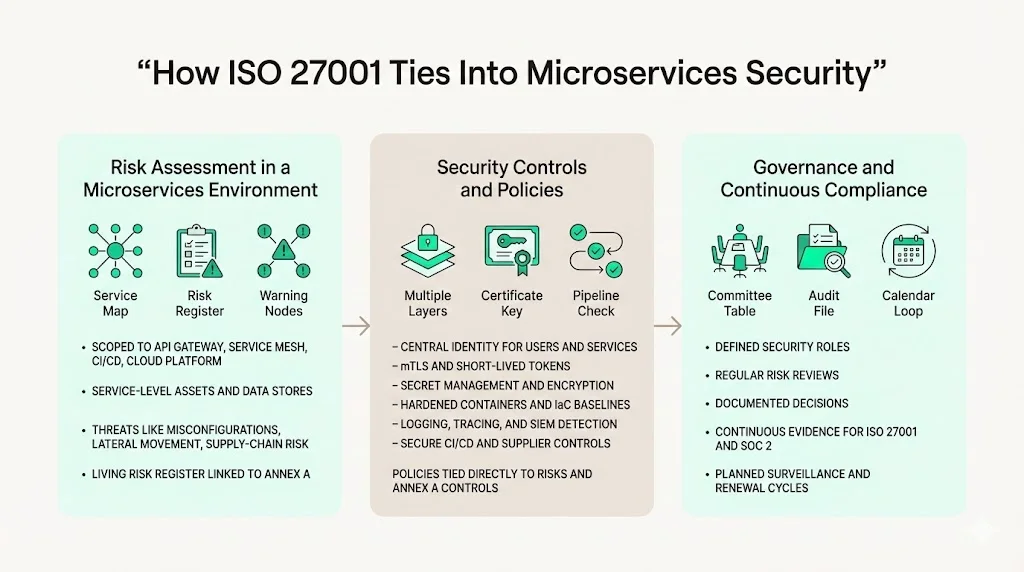
How ISO 27001 ties into microservices security
ISO 27001’s strength lies in its structure: risk assessment, control selection, and governance. Translating these into a microservices world requires understanding the moving parts and tailoring the standard to distributed systems. Konfirmity’s experience with more than 6,000 audits shows that the most successful teams link security goals to compliance requirements through three lenses: risk assessment, security controls and policies, and governance and compliance. Each lens supports both ISO 27001 and microservices realities.
Risk assessment
An ISMS starts with a documented risk assessment. Linford & Company outline the steps: define the scope and context, identify assets, identify threats and vulnerabilities, evaluate likelihood and impact, prioritise risks, decide treatment options, document them, and review regularly. For a microservices environment the scope should include the API gateway, service mesh, identity provider, CI/CD pipelines, container orchestration platform, and underlying cloud services. Assets include each microservice, its data store, secrets, and third‑party dependencies. Threats range from misconfigured identity settings to lateral movement across services and supply‑chain vulnerabilities in container images. A useful template records the asset, threat, likelihood, impact, chosen control, residual risk, and owner. The result is a risk register aligned with Annex A.
Konfirmity recommends holding a half‑day workshop with engineering leads, security engineers, and compliance officers to populate this register. The discussion clarifies which services handle personal data, payment data, or regulated health data. It also exposes hidden dependencies and shadow APIs. This register drives your Statement of Applicability (SoA) and risk treatment plan. At this point the disciplines converge: by cataloguing risks at the service level, you create a living map of the environment that can be reused for SOC 2, HIPAA, and GDPR evidence collection.
Security controls and policies
Once risks are understood, teams select and implement controls. Annex A offers a menu, but each control needs interpretation for microservices. Key examples include:
- Access control (A.5). Use a central identity provider for both human and machine identities. Issue short‑lived tokens for north–south traffic and mutual TLS certificates for east–west service calls. Enforce least‑privilege policies via policy‑as‑code engines like OPA. Review access quarterly to remove unused privileges.
- Cryptography and secret management (A.8). Encrypt data at rest and in transit. Store secrets in dedicated secret managers instead of environment variables or Kubernetes Secrets. Rotate encryption keys regularly using a key management service.
- Operations security and configuration management (A.12). Harden container images, scan dependencies for vulnerabilities, and limit container privileges. Use infrastructure‑as‑code and maintain a baseline configuration for your orchestration platform and API gateway.
- Logging and monitoring (A.12). Collect logs and metrics from the API gateway, service mesh, and applications. Implement distributed tracing to follow requests across services. Use a SIEM to detect anomalies.
- Development and change management (A.14). Integrate security into your CI/CD pipeline: code scanning, dependency scanning, secret scanning, and infrastructure scanning. Require peer review and approval for changes affecting critical services.
- Supplier relationships (A.15). Maintain a list of third‑party services, evaluate their security posture, and ensure contracts include data protection obligations.
Policies operationalise these controls. For example, an access control policy might mandate that every API call passes through the gateway and that new microservices register in a service mesh before accepting traffic. A vulnerability management policy could specify scanning frequency and patch timelines based on CVSS scores. The key is to tie each policy back to risks in your register and Annex A controls. The overlap occurs because the controls described above address common microservices weaknesses: uncontrolled endpoints, secret sprawl, inconsistent logging, and configuration drift.
Governance and compliance
Good controls fail without governance. ISO 27001 requires clear roles and oversight. In practice this means establishing a security committee that includes engineering management, product leadership, compliance professionals, and an assigned CISO. The committee should meet regularly to review the risk register, check policy adherence, and approve changes. Document all policies, risk assessments, and meeting minutes in a central repository; auditors will ask for evidence during stage 1 and stage 2 audits. A SOC 2 Type II audit requires demonstrating that controls operate effectively over a 6 to 12 month window. By operating the ISMS daily and producing continuous evidence—access review records, incident response logs, change tickets—you shorten this preparation. Certification cycles matter: ISO 27001 certificates last three years, with annual surveillance audits. Planning your audit calendar against development roadmaps avoids last‑minute crises.
Applying NIST SP 800‑204 guidance to ISO 27001
Technical guidance helps translate policy into practice. NIST’s SP 800‑204, Security Strategies for Microservices‑based Application Systems, lists core features such as authentication and access management, service discovery, secure communication, security monitoring, load balancing, throttling, integrity checking, and session persistence. Each of these features maps to Annex A controls. For example, NIST recommends using API gateways and service meshes to centralise authentication and encrypt service‑to‑service communication. This aligns with access control and cryptographic controls in ISO 27001. NIST also emphasises resilience—circuit breakers, load balancing, and retries—which supports ISO 27001’s focus on availability and business continuity.
At Konfirmity we incorporate NIST guidance directly into the risk treatment plan. During the workshop we ask: Do we use a gateway? Do we enforce mutual TLS within the cluster? How do we handle service discovery? If gaps exist, we create control objectives with deadlines. For example, “Implement mTLS between all services within six months using the Istio service mesh” ties NIST’s secure communication recommendation to a specific Annex A control and a clear owner. The phrase Microservices And ISO 27001 appears again because mapping NIST strategies into the ISMS ensures that technical reality matches policy.
A practical walkthrough using templates
Frameworks can feel abstract, so templates help teams move from theory to execution. ISO 27001 mandates several documents. Below is a concise list of essential templates and their purposes:
Konfirmity uses these templates as a starting point. To tailor them to microservices:
- Use the risk register to list each microservice, its data classification, and threats such as unauthorized internal API calls or insecure default configurations. Attach Annex A controls and NIST strategies to each risk.
- Extend the access control policy with procedures for registering APIs in the gateway, enforcing mutual TLS, and authorising service‑to‑service calls.
- Adapt the vulnerability management policy to include container scanning, dependency scanning, and secret scanning in your CI/CD pipeline. Define patch windows based on service criticality.
- Create an incident response matrix that assigns responsibilities per service and describes which logs (gateway, service mesh, application) must be collected during an incident.
Implementation follows a step‑by‑step sequence:
- Define the scope. Include all microservices, data stores, CI/CD pipelines, and shared infrastructure. Exclude only what you can defend—auditors will test your rationale.
- Hold a risk assessment workshop. Involving engineering and security leads to populating the risk register. Prioritise high‑impact, high‑likelihood risks.
- Populate templates. Document the SoA, policies, and treatment plans. Map each risk to a control. Insert NIST‑based objectives where relevant.
- Integrate controls. Update CI/CD pipelines to enforce scanning and gating. Deploy or upgrade API gateways and service meshes. Implement access reviews and logging.
- Operate and audit. Conduct internal audits every six months. Use evidence templates to collect logs, access reviews, and patch records. Prepare for external audits by reviewing the SoA and verifying that controls have operated through at least one observation period.
This structured approach shortens the path to certification and ensures that Microservices And ISO 27001 are addressed together rather than as separate projects. Konfirmity’s clients typically achieve SOC 2 readiness within four to five months and ISO 27001 certification within seven to nine months when following this cadence, compared to nine to twelve months when self‑managing.
Best practices and security controls for microservices
Beyond templates, certain practices make microservices secure in a way that satisfies auditors and buyers alike. We summarise four critical areas:
- Access control. Implement a zero‑trust approach: every request must be authenticated and authorised. Use OAuth 2.0 or OIDC for user traffic, mutual TLS and policy‑as‑code for service calls, and rotate credentials regularly. Perform quarterly access reviews to catch privilege creep. This practice supports Annex A access control and NIST’s authentication recommendations.
- Continuous monitoring. Collect logs and metrics centrally. Use distributed tracing to follow a request across services and detect anomalies quickly. Feed logs into a SIEM and build alerts for suspicious patterns like sudden spikes in 500‑series errors or unusual inter‑service traffic. Continuous monitoring satisfies ISO 27001’s logging requirement and demonstrates control operation over time.
- Threat mitigation and vulnerability management. Automate security checks in your pipeline: code scanning, dependency scanning, container scanning, and secret scanning. Prioritise remediation based on CVSS scores, and enforce patch windows—e.g., seven days for critical vulnerabilities. Track remediation through tickets to provide audit evidence. Adopting least‑privilege container runtimes and regularly rotating keys reduces lateral movement opportunities.
- Data protection. Encrypt sensitive data at rest and in transit, using AES‑256 and TLS 1.2 or higher. Classify data and apply the principle of minimum exposure: share only necessary data between services. Use a central key management system for encryption keys. Maintain an asset inventory and network map of data flows; this not only satisfies HIPAA proposals but also improves understanding of how data moves across microservices.
These practices tie back to the earlier sections. They implement controls identified in your risk assessment and align with NIST guidance. By embedding them in your operations you can use this terminology in procurement discussions with confidence—showing that security outcomes and compliance are managed together.
How to audit and certify a microservices‑based ISMS
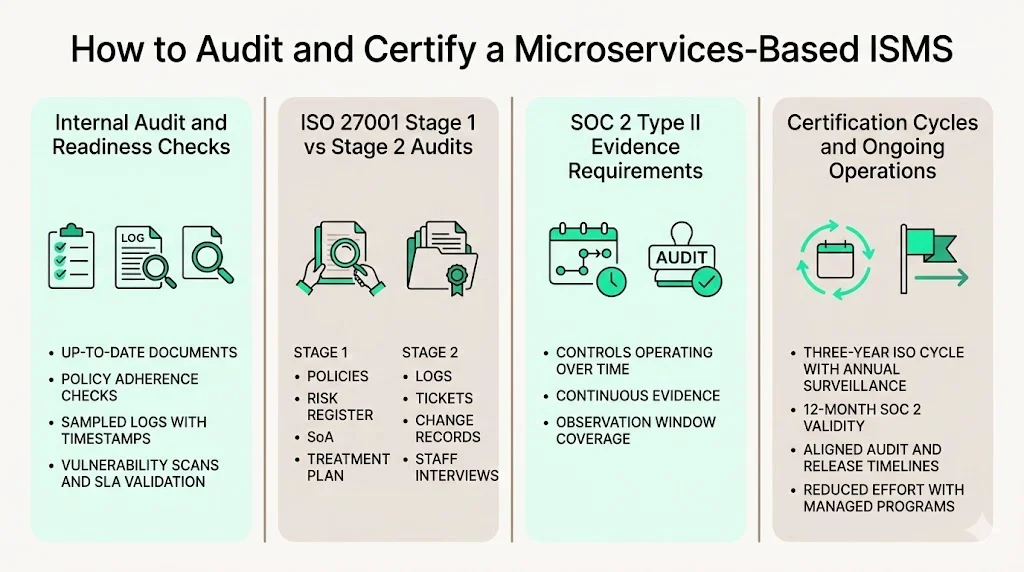
Once your program is running, auditing and certification are the final steps. Internal audits help catch gaps before external assessors do. Use a checklist to confirm that each required document is present and up to date, that policies are being followed (e.g., access reviews completed, incident response tests run), and that the risk register reflects current realities. Sample logs to verify they include timestamps and user or service identifiers. Review vulnerability scan reports and confirm that remediation met defined SLAs.
External auditors expect documentation and operational evidence. During the ISO 27001 stage 1 audit they will review your policies, risk register, SoA, and treatment plan. Stage 2 focuses on evidence: logs, tickets, change records, and interviews with staff to confirm they understand roles. For SOC 2 Type II audits they will verify that controls operated effectively over the observation period—hence the need for continuous evidence. To streamline this, use evidence templates that link each Annex A control to specific logs, tickets, and documents. Store these in a trust centre or version control system so you can share them with clients as part of due‑diligence.
Certification cycles should be planned alongside business timelines. ISO 27001 certification is valid for three years with annual surveillance audits; SOC 2 reports are generally valid for 12 months. Aligning renewal dates with product releases prevents resource conflicts. Managed services like Konfirmity can run the program year‑round, reducing the internal effort to around 75 hours per year versus 550‑600 hours when self‑managed.
Conclusion
Microservices unlock velocity but complicate security. Each new service adds endpoints, secrets, and dependencies, and attackers exploit misconfigurations and shadow APIs. Enterprise buyers and regulators increasingly require proof that vendors can protect data over time. Microservices And ISO 27001 offers a path to meet these expectations. By performing a risk assessment that covers every service, selecting and implementing appropriate controls, and establishing governance and continuous monitoring, companies can turn distributed complexity into a programme of record. NIST SP 800‑204 provides technical strategies that map cleanly to ISO 27001 controls, and templates ensure that documentation and evidence are consistent. A managed approach—human‑led, focused on real control implementation rather than checklists—can cut readiness timelines in half and improve audit outcomes. In the end, security that works in production is the only security that matters.
When the program runs smoothly, clients notice the professionalism, diligence, and dedication behind your security approach every day.
FAQs
1. What is Microservices And ISO 27001 all about?
The phrase refers to aligning a microservices architecture—a set of small, API‑driven services—with the ISO 27001 standard for information security management. Together they address the increased attack surface of microservices and the need for structured risk management. Implementing Microservices And ISO 27001 means building controls, policies, and evidence that link each service’s risks to Annex A controls and NIST recommendations.
2. Do I need separate security controls for microservices?
Not separate, but more granular. Access control, encryption, logging, and vulnerability management still apply, but they must operate at multiple layers—API gateway, service mesh, and CI/CD. Use policy‑as‑code to enforce decisions at runtime and in pipelines. A risk‑based approach ensures that your controls focus on the services that matter most.
3. Can I use standard ISO 27001 templates for microservices?
Yes, start with the standard templates—scope statement, risk register, SoA, and policies. Then tailor them: list each microservice, map its data flows, and define controls for API registration, secret management, and pipeline security. These adaptations connect Microservices And ISO 27001 in a way that auditors and buyers can trace.
4. How does ISO 27001 certification impact enterprise procurement?
Certification signals that your company operates a mature security programme with continuous evidence. Many buyers require ISO 27001 or SOC 2 Type II before signing. Having a valid certificate reduces the time spent on vendor risk questionnaires. It also supports other frameworks, as controls and evidence can be reused. With a managed service, companies achieve certification faster and free up engineering time for product work.
5. How do I map NIST SP 800‑204 into ISO 27001 compliance?
Identify NIST’s core features—authentication, service discovery, secure communication, monitoring, and resiliency—and map each to an Annex A control. Incorporate NIST guidance into your risk treatment plan and policies. For example, implement service meshes for mutual TLS and map that to access control and cryptographic controls. By doing this, you demonstrate that Microservices And ISO 27001 are not only conceptually aligned but also practically integrated.





.svg)






.svg)
.svg)