Most large buyers now ask for proof that vendors manage information properly. Deals stall when teams are unable to show how they control access, safeguard patient data or handle user information across the supply chain. As someone who has built and operated programmes under ISO 27001, SOC 2, HIPAA and GDPR for 25 years, I see that successful assurance starts with clear processes rather than checklists. This article presents a hands-on ISO 27001 Questionnaire Guide that helps busy teams map requirements, collect evidence and stay audit‑ready. By the end, you will have a repeatable method, sample questions and a template you can use right away to support enterprise deals and healthcare obligations.
Why use an ISO 27001 questionnaire
Enterprise clients evaluate vendors on confidentiality, integrity and availability. A structured questionnaire gives them confidence that your organisation understands risks and has the right controls. According to the 2025 IBM Cost of a Data Breach report, the average breach cost dropped 9 % to USD 4.44 million, partly because organisations improved detection and response. However, phishing remains the most common initial attack vector and costs roughly USD 4.8 million per breach. In healthcare, breaches average USD 7.42 million and take nine months to contain. Third‑party breaches cost USD 4.91 million, and incidents involving multiple environments average USD 5.05 million. These figures underline why understanding your posture before an auditor or buyer evaluates you saves money and builds trust.
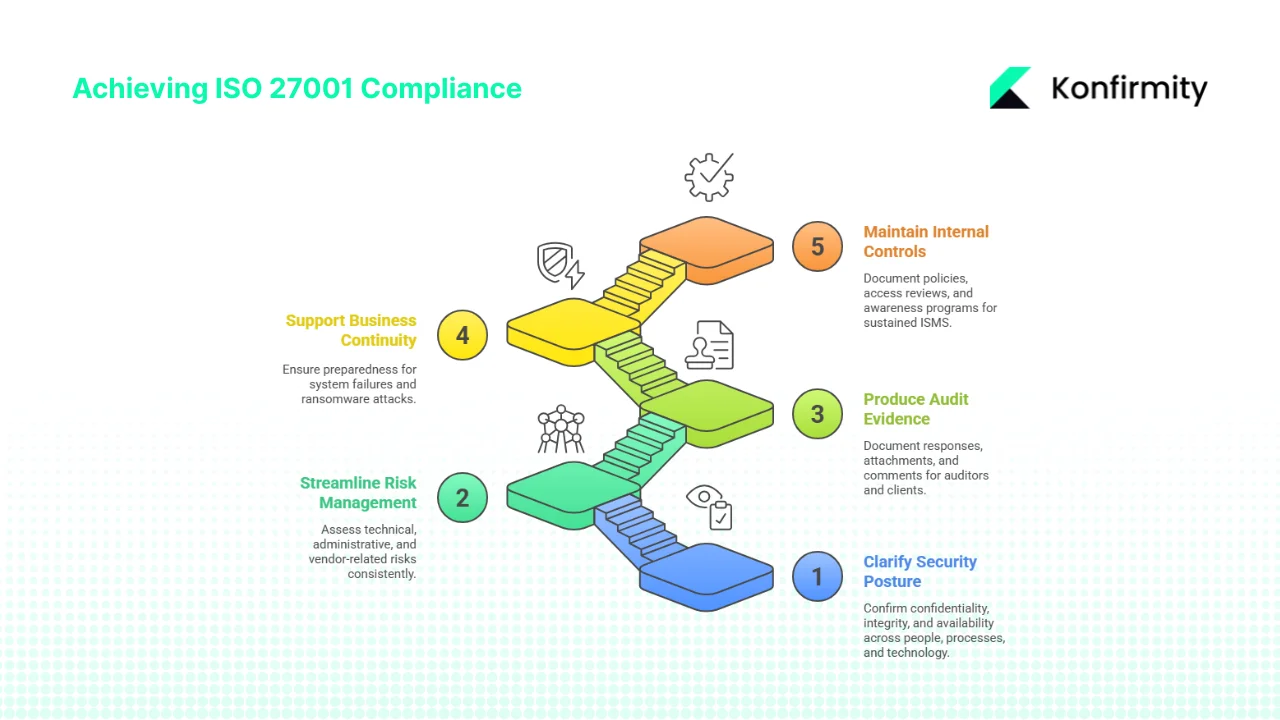
Using a questionnaire offers several benefits:
- Clarifies your security posture – You can confirm whether confidentiality, integrity and availability are addressed across your people, processes and technology before a formal audit.
- Streamlines risk management – A single questionnaire allows you to assess technical, administrative and vendor‑related risks consistently. You can reference the NIST Risk Management Framework’s seven‑step process for context; it offers a repeatable way to manage information security and privacy risk.
- Produces evidence for audits and client due diligence – The responses, attachments and comments provide a record that can be shared with auditors, procurement teams or regulators.
- Supports business continuity and incident response – Questions about backups, disaster recovery and incident handling ensure you are prepared when systems fail or ransomware hits.
- Maintains internal controls and training – Documenting policy development, access reviews and awareness programmes helps you sustain an information security management system (ISMS) over time.
Understanding ISO 27001 basics
ISO 27001 sets requirements for establishing, operating and continually improving an ISMS. An ISMS encompasses three pillars: people, process and technology. It defines how you identify risks, implement controls, monitor results and update the programme. Enterprise clients care about all three pillars because a weakness in any of them can expose their data. For example, a strong firewall does little good if staff can share passwords, or if an outdated incident response playbook sits unused.
At the heart of information security is the “CIA” triad: Confidentiality, Integrity and Availability. Confidentiality protects sensitive data from unauthorized disclosure. Integrity ensures information remains accurate and unaltered. Availability guarantees that systems and data are accessible when needed. Buyers expect vendors to maintain all three, not just encryption or uptime, because each supports trust.
Recent updates – ISO 27001:2022 and the new Annex A structure
ISO 27001:2022 was released on 25 October 2022, and ISO 27002:2022 followed on 15 February 2022. Organisations seeking certification after April 2024 must use the 2022 version; those certified under the 2013 version must transition by 31 October 2025. The biggest change is the reduction of controls from 114 to 93. Secureframe explains that 57 controls were merged into 24, 11 new controls were added, one was split and 58 remained mostly unchanged. The new Annex A divides controls into four categories: Organisational (37 controls), People (8 controls), Physical (14 controls) and Technological (34 controls). This thematic structure replaces the previous 14 domains, making it easier to map responsibilities across teams.
The update introduces 11 new controls such as Threat intelligence (A.5.7), Information security for cloud services (A.5.23), ICT readiness for business continuity (A.5.30), Physical security monitoring (A.7.4) and Secure coding (A.8.28). When building your questionnaire, ensure you address these new areas, particularly if you use cloud services or develop software. Moreover, the revised standard emphasises attributes such as preventive/detective/corrective control types and information security properties (confidentiality, integrity, availability).
Cross‑framework context – SOC 2, HIPAA and other requirements
Many enterprise buyers ask for SOC 2 reports, which evaluate controls relevant to security, availability, processing integrity, confidentiality and privacy. The AICPA publishes SOC 2 and requires a third‑party audit. HIPAA and GDPR introduce further obligations for handling protected health information and personal data. While ISO 27001 focuses on an ISMS, these frameworks share core principles: risk assessments, control implementation, evidence collection and continuous monitoring. Building a questionnaire around ISO 27001 helps you address overlapping requirements once, reducing duplication when your team pursues SOC 2, HIPAA or GDPR attestations.
Key security domains to include in your questionnaire
The ISO 27001 Questionnaire Guide outlines important domains that help you map controls.
An effective ISO 27001 Questionnaire Guide should cover multiple control areas. Based on the updated structure and cross‑framework practices, ensure your questions touch on these topics:
- Security controls & internal controls – policies, procedures and record keeping to support consistent operations.
- Access control & encryption – who has access to systems, how credentials are managed and whether sensitive data is encrypted at rest and in transit.
- Incident response & business continuity – plans for detecting, responding to and recovering from incidents; how often they are tested.
- Vendor management & third‑party risk – inventory of vendors, contractual requirements for security, frequency of assessments and evidence review.
- Training & awareness – employee education on policies, incident reporting and compliance obligations.
- Document control & policy development – versioning, approval processes and retention schedules for policies, procedures and records.
- Risk assessment & treatment – methodology, frequency and results of identifying, analysing and mitigating risks.
- Auditing & compliance – internal audit schedules, management review, tracking of non‑conformities and corrective actions.
Steps to create your ISO 27001 questionnaire
The following step‑by‑step process reflects the way my team at Konfirmity conducts readiness assessments for enterprises and healthcare providers. We have supported more than 6,000 audits and draw on over 25 years of combined expertise, so these steps are grounded in practice rather than theory.
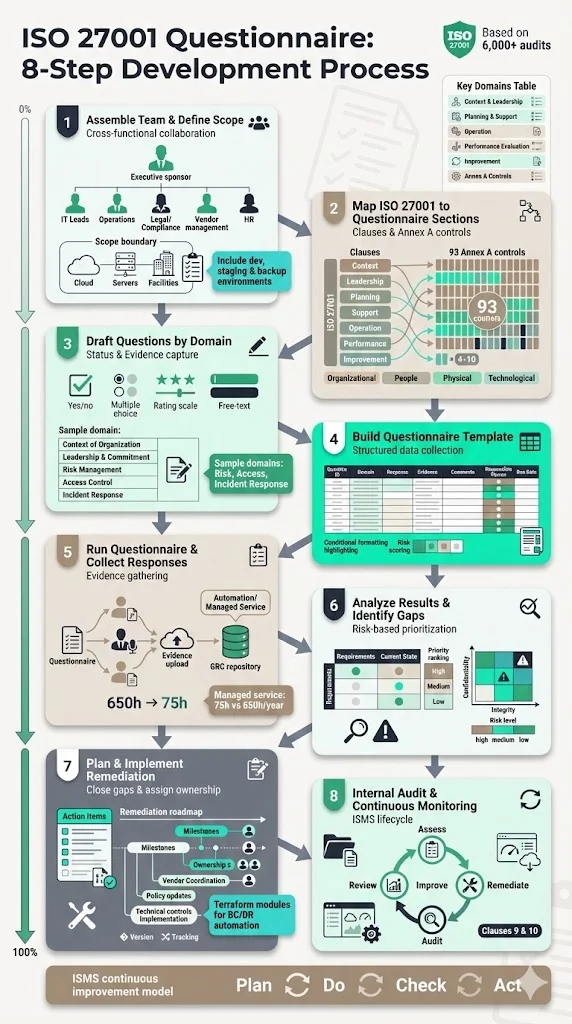
Step 1 – Assemble your team and define scope
Start by forming a cross‑functional team. At minimum include an executive sponsor (CTO, CISO or VP Engineering), IT leads, operations managers, legal or compliance counsel, vendor management and HR. Identify all systems, processes, departments and third‑party relationships that handle sensitive data. Define physical locations and cloud services in scope. Enterprise buyers often ask to see not only production systems but also development, staging and backup environments. Document your scope early; a narrow scope can miss critical assets and lead to audit findings.
Step 2 – Map ISO 27001 clauses and Annex A controls to questionnaire sections
Use Clauses 4–10 to structure questions about the ISMS. Clause 4 covers context and the scope of the ISMS, Clause 5 addresses leadership and policy, Clause 6 deals with planning and risk assessment, Clause 7 covers support (resources, awareness, communication), Clause 8 focuses on operation, Clause 9 on performance evaluation and Clause 10 on improvement. Map each clause to a section in your questionnaire. Then map the 93 controls from Annex A to technical and operational domains such as access control, cryptography, physical security, supplier management and business continuity. The four categories (organisational, people, physical, technological) can help allocate ownership among departments.
Step 3 – Draft questions by domain
For each control area, create questions that capture both status and evidence. Use a mix of yes/no, multiple choice, rating scales (e.g., fully implemented / partially implemented / not implemented) and free‑text fields for comments. Below is a sample set covering critical areas:
For vendor management, include questions about business associate agreements for HIPAA or data processing addenda for GDPR. For healthcare clients, ask whether technical safeguards meet the HIPAA Security Rule and whether audit logs are maintained.
Step 4 – Build your questionnaire template
Create a spreadsheet or document with columns that support data collection and analysis. A typical layout includes:
- Question ID – unique identifier for each question.
- Domain – the control area (e.g., risk management, access control).
- Question text – the prompt itself.
- Response – options such as Yes/No/Not Applicable, multiple choice or rating scale.
- Evidence – link to documents, screenshots or system outputs that support the response.
- Comments – space for context, clarifications or remediation plans.
- Responsible person – the team member accountable for the response.
- Due date – when the question must be answered or remediated.
You may also add fields for likelihood and impact if you want to integrate risk scoring. Use conditional formatting to flag high‑risk areas or overdue responses. Keep the template simple so busy teams can complete it without extensive training.
Step 5 – Run the questionnaire and collect responses
Distribute the questionnaire across the organisation. For large enterprises, schedule interviews with system owners and process leads. For smaller teams, a self‑assessment with evidence upload may suffice. Provide clear instructions on how to answer each question and what evidence to attach. Remind participants that incomplete or inaccurate answers slow down audits and procurement. Use a central repository or GRC tool to collect documentation. Consider using our managed service to automate evidence collection from systems (e.g., retrieving access logs or backup reports) and reduce manual work.
Step 6 – Analyse results and identify gaps
Once responses are collected, compare them against the ISO 27001 requirements and Annex A controls. Identify missing or partially implemented controls. Prioritise findings based on risk — confidentiality, integrity and availability — and business impact. For example, if encryption at rest is missing for a database containing patient data, assign a high priority because healthcare breaches cost more and take longer to resolve. Document gaps in a report that lists the issue, affected system, risk rating, recommended remediation, responsible team and target date.
Step 7 – Plan and implement remediation
With gaps identified, develop a remediation plan. This may involve writing or updating policies, implementing technical controls (e.g., enabling multi‑factor authentication), updating vendor contracts, performing employee training, or improving incident response procedures. Assign clear ownership and timelines. For third‑party vendors, include them in the remediation plan by requesting evidence of their own controls. Maintain version control on documents and track changes. At Konfirmity, we often build Terraform modules for business continuity or implement identity provider integrations on behalf of clients; our managed approach reduces internal effort to about 75 hours per year versus 650 hours with typical self‑service tools.
Step 8 – Conduct internal audit and continuous monitoring
After remediation, perform an internal audit to validate controls. Review policies, inspect system configurations, test incident response plans and verify that evidence supports the stated controls. Track non‑conformities and assign corrective actions. Maintain a cycle of assessment → remediation → audit → review → improvement. This is consistent with Clauses 9 and 10 of ISO 27001 and ensures that the ISMS adapts as your organisation grows or regulations change. Continuous monitoring tools can automate checks like access reviews, vulnerability scanning and logging. However, tools alone do not guarantee security; human oversight is needed to interpret results and drive action.
Sample questionnaire and template
This sample in the ISO 27001 Questionnaire Guide demonstrates how to collect structured responses.
Below is a condensed example of a questionnaire covering 15 questions. Each question is consistent with a control area, includes a proposed response scale and suggests evidence to attach. Use this as a starting point and expand based on your scope.
When using a rating scale, define what each tier means. For instance, a “Yes” could mean the control is fully implemented and evidenced, “Partially” may mean implementation has started but gaps exist, and “No” means no implementation. Encourage respondents to provide context in the comments field.
Common mistakes and how to avoid them
The ISO 27001 Questionnaire Guide also highlights common mistakes and how to avoid them.
- Narrow scope – Failing to include critical systems or third parties often leads to audit findings. Avoid this by conducting a thorough asset inventory and involving process owners early.
- Lack of stakeholder buy‑in – Questionnaires created by a single department may not capture operational realities. Include IT, operations, vendor management and leadership when drafting questions.
- Superficial answers – Yes/No answers without evidence or context are useless. Ask for documents, screenshots and logs to support claims.
- Poor documentation practices – Without version control and retention schedules, teams lose track of policies and evidence. Use a document management system and assign ownership.
- One‑time approach – Compliance is continuous. Treat the questionnaire as a living document that changes with your business, technology and regulatory environment.
- Ignoring vendor risk – Many breaches involve third parties. Include vendor assessments and demand comparable controls from your suppliers.
Tips for busy teams
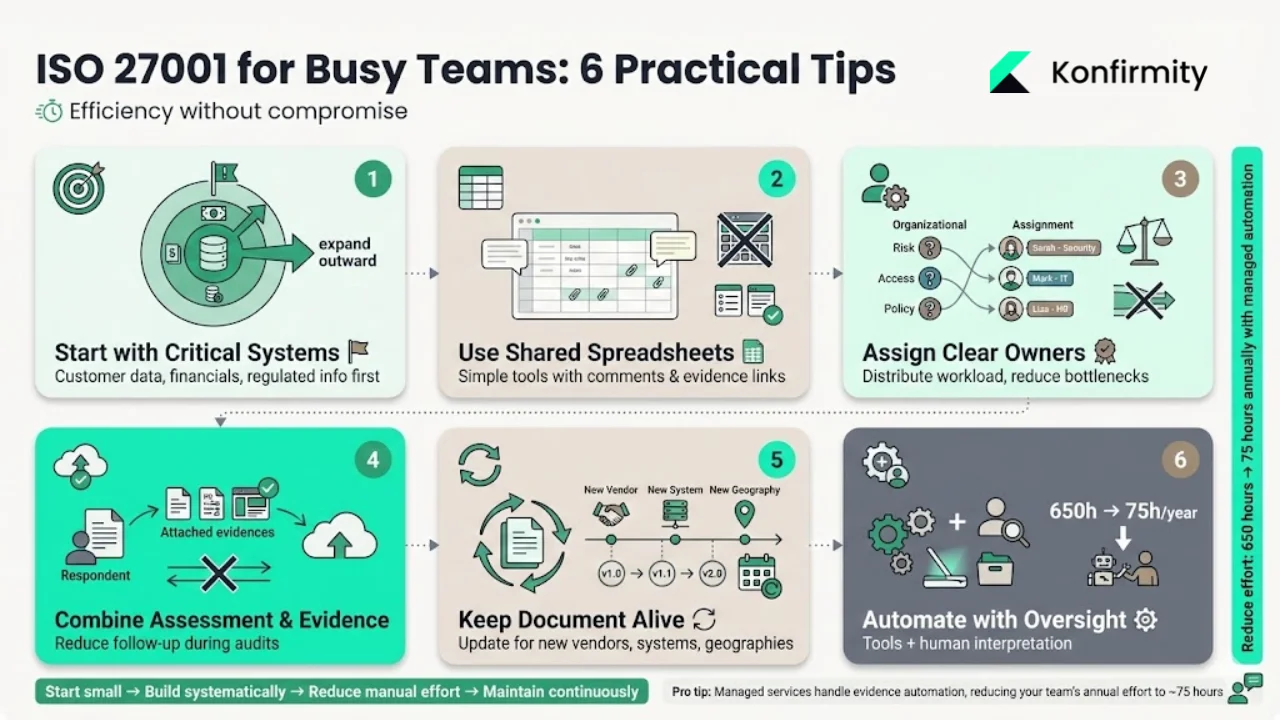
- Start with critical systems and vendors – You don’t have to cover every process at first. Focus on services that handle customer data, financial records or regulated information, then expand the scope.
- Use a shared spreadsheet or light tool – Avoid complex software when starting. A simple spreadsheet with comments and evidence links works well.
- Assign clear owners – Each question or domain should have a responsible person. This distributes workload and reduces bottlenecks.
- Combine self‑assessment with evidence upload – Ask respondents to provide proof (policy documents, logs, screenshots) alongside their answers. This reduces follow‑up questions during audits.
- Keep the document alive – Update questions, controls and evidence requirements when you add new vendors, implement new systems or expand to new geographies.
- Automate where possible – Use tools for access reviews, vulnerability scanning and log collection, but pair them with human oversight. Our managed service reduces internal effort by automating evidence capture while our team interprets results.
How this questionnaire supports vendor management, client trust and sales
For companies selling to enterprise clients, a strong questionnaire does more than tick compliance boxes. It demonstrates that you manage risk across the supply chain, keep clear records and are ready for an audit at any time. Vendors with mature programmes reduce breach costs and containment times, an important differentiator in negotiations. A structured questionnaire helps you:
- Show buyers you take security seriously – Detailed answers and supporting evidence signal maturity. Many procurement teams insist on reviewing such documents before signing a contract.
- Streamline due diligence – When you have an up‑to‑date questionnaire and supporting documentation, you can respond quickly to security addenda, business associate agreements and data processing agreements.
- Reduce risk in third‑party relationships – By holding your vendors to the same standard, you lower the chance that a supply chain breach disrupts your service.
- Accelerate sales cycles – Enterprise buyers move faster when they can verify your controls rather than waiting for ad‑hoc answers.
- Support continuous compliance – A questionnaire structured according to ISO 27001:2022 ensures your ISMS remains effective and ready for surveillance audits.
Conclusion
Security that looks good on paper but fails in practice is a liability. A well‑designed ISO 27001 Questionnaire Guide gives you visibility into your organisation’s controls, reduces the cost of breaches and builds trust with buyers and regulators. By mapping the latest ISO 27001 requirements to your processes, drafting clear questions, collecting evidence and iterating through assessment and remediation, you create a living programme that scales with your business. Whether you’re preparing for a first certification or maintaining compliance across multiple frameworks, start small, engage your team and use the sample template provided here. With a human‑led, managed approach, you can focus on building your product while we handle security and compliance.
Frequently asked questions
1) What is a gap analysis questionnaire and why is it important?
A gap analysis questionnaire compares your current controls to the requirements of ISO 27001:2022. It helps you identify areas where your ISMS does not meet the standard and guides remediation. Without a structured gap analysis, teams may overlook critical weaknesses and face delays during certification or procurement.
2) Do we need a questionnaire if we’re already certified?
Yes. Certification is not a one‑time event. Surveillance audits and buyer due diligence require up‑to‑date evidence. A questionnaire helps you monitor changes, document improvements and prepare for periodic audits.
3) How often should we update and run the questionnaire?
At a minimum, run it annually or when major changes occur: new products, acquisitions, significant system upgrades or new regulatory requirements. Many organisations run a lighter quarterly version focusing on high‑risk areas.
4) How detailed should answers be?
Avoid simple Yes/No responses. Provide supporting evidence (policies, logs, screenshots) and contextual comments. Where controls are partially implemented, describe remaining tasks and target completion dates.
5) How do we handle third‑party vendors?
Include vendor management questions in your questionnaire and require vendors to complete similar assessments. Review their SOC 2 reports, ISO 27001 certifications or HIPAA attestations. For high‑risk vendors, conduct onsite visits or independent audits.
6) Can small teams do this without hiring external consultants?
Yes. Small teams can start with a concise questionnaire and gradually add depth. However, many find that partnering with a managed service like Konfirmity reduces internal workload and provides expertise in control implementation, evidence collection and audit support.
7) What evidence should we collect and maintain?
Collect policies, procedures, risk registers, access logs, configuration files, incident reports, training records and vendor assessments. Store them in a secure repository with version control. Evidence should demonstrate that controls exist, are operating and are reviewed.
8) How does the questionnaire tie into internal audit and external certification?
Internal audit uses the questionnaire responses and evidence to verify control design and operation. External auditors review the same evidence during certification. Maintaining a complete questionnaire reduces prep work for audits and increases the likelihood of a clean report.





.svg)




.svg)
.svg)