Most vendors approach SOC 2 questionnaires as isolated sales obstacles—discrete documents to be completed, submitted, and forgotten. This creates a fundamental gap between questionnaire responses and actual security posture, a gap that becomes apparent when enterprise procurement teams conduct deeper due diligence or when your organization faces its first formal audit. Vendors report dedicating 10-30 hours per questionnaire and submitting 10-20 questionnaires annually, yet many lack the systematic control environment these responses claim to document.
Enterprise buyers increasingly demand comprehensive proof of security controls through vendor risk questionnaires before contract execution. Your ability to answer SOC 2-aligned questionnaires quickly and accurately determines whether you advance through procurement or stall while competitors move forward. This guide addresses the complete lifecycle: from understanding what enterprise clients actually evaluate, through building the control infrastructure required to answer truthfully, to maintaining audit-ready evidence that supports both questionnaire responses and formal SOC 2 examinations.
This is not about manufacturing compliant-sounding answers. Organizations with 6,000+ completed audits recognize that questionnaire responses either reflect genuine security operations or expose vulnerabilities during vendor assessments. We address the technical requirements, documentation standards, control testing protocols, and evidence management systems that allow you to respond to questionnaires while simultaneously building toward SOC 2 Type 2 compliance.
What is SOC 2 and Why Does the Questionnaire Matter?
SOC 2 is a framework established by the American Institute of Certified Public Accountants (AICPA) that outlines standards for safeguarding sensitive data from unauthorized access, security breaches, and more. The framework evaluates service organizations against five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Security is the only Trust Services Criteria required for every SOC 2 audit, while the other criteria can be added to your report scope if your organization chooses.

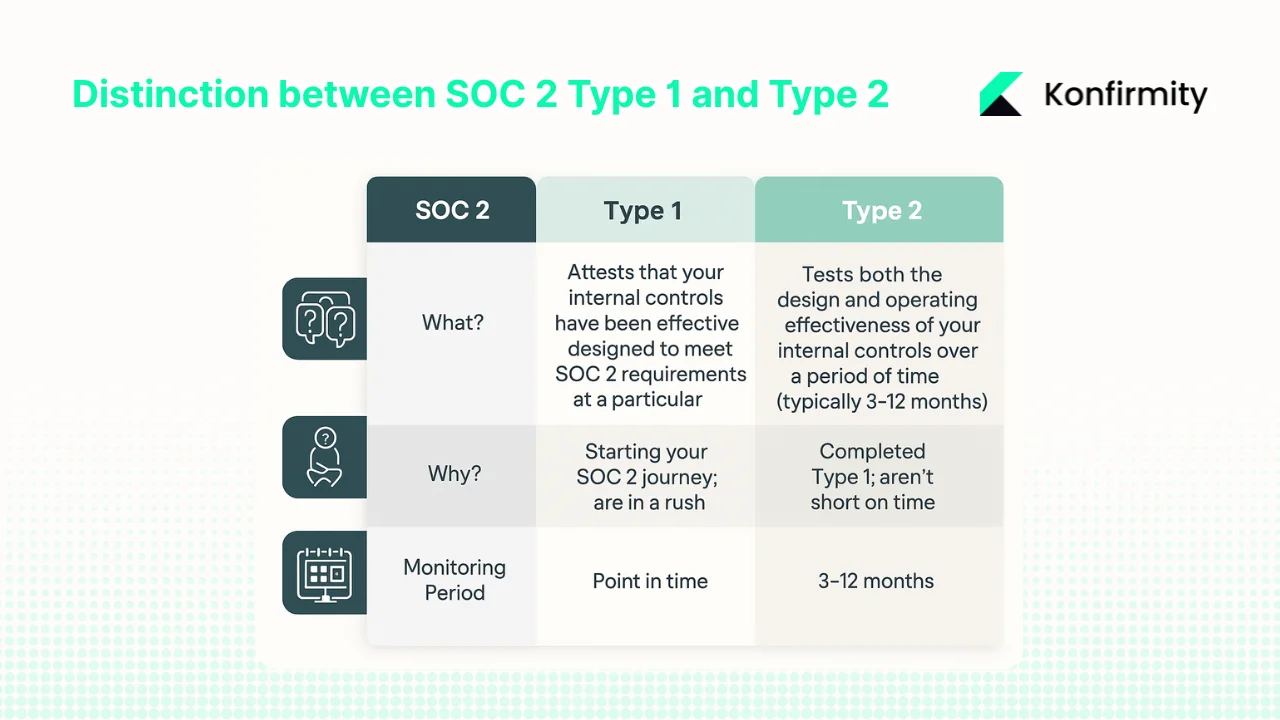
The distinction between SOC 2 Type 1 and Type 2 significantly impacts both questionnaire responses and enterprise expectations. A SOC 2 Type 1 report provides a snapshot of controls at a single point in time, while a Type 2 report demonstrates the effectiveness of your controls over a sustained period, making Type 2 reports significantly more valuable to enterprise and mid-market organizations. For first-time SOC 2 Type 2 reports, best practice considers at least a six-month audit period, though organizations needing reports faster may opt for audit periods between three and six months.
Why Enterprise Clients Care
Modern businesses, especially enterprise-size organizations, understand they must evaluate not just their own internal security controls but those of every vendor they work with, and many organizations won't work with a vendor if they're not SOC 2 compliant. Enterprise procurement teams use vendor risk questionnaires as initial screening mechanisms before engaging with security and compliance teams for deeper evaluation.
In most cases, a SOC 2 report provides more comprehensive and independent assurance about a vendor's security practices compared to a vendor security questionnaire, yet questionnaires remain standard in procurement workflows. Your questionnaire responses signal whether you understand fundamental security concepts like least-privilege access, incident response protocols, vendor management processes, and continuous monitoring. Vague or inconsistent answers trigger additional scrutiny, sales cycles, and create doubt about your operational maturity.
The Role of SOC 2 Questionnaires in Readiness and Audit Process
Enterprise questionnaires mirror the Trust Services Criteria and common control frameworks. Questions probe specific areas: "Describe your incident response plan and notification procedures," "How do you enforce access controls and conduct access reviews," "What vendor risk assessment process do you follow for third parties with access to customer data?" These questions directly map to controls that auditors will evaluate during SOC 2 examinations.
Organizations completing questionnaires without established controls face two problems: they either misrepresent their security posture (risking contract termination and reputational damage) or acknowledge gaps that eliminate them from procurement consideration. The questionnaire serves as both a sales tool and a readiness diagnostic. If you struggle to answer questions about control testing, evidence collection, or risk management processes, you have identified the gaps that will fail an audit.
Getting Ready: Pre-Questionnaire Readiness Steps

1) Define Scope and Trust Service Criteria
Determine which Trust Services Criteria apply to your business model and service delivery. Not all organizations require all five criteria. If you don't process personal information, Privacy may not apply. If you provide asynchronous services without uptime commitments, Availability may not be relevant. However, Security is mandatory for every SOC 2 examination.
Define the systems, services, infrastructure, and data flows within scope. This becomes your system description—the documented boundary of what the audit covers and what questionnaires should address. Decide whether you're initially targeting Type 1 (design evaluation at a point in time) or Type 2 (operational effectiveness over 3-12 months). Most enterprise clients expect Type 2 within 12 months of initial vendor engagement.
2) Conduct Gap Analysis and Readiness Assessment
Map existing controls, policies, and procedures to the selected Trust Services Criteria. Identify gaps systematically: missing controls, under-documented processes, inadequate vendor oversight, weak incident response capabilities, insufficient access controls, absent change management procedures, lack of continuous monitoring, incomplete risk assessments. Prioritize remediation based on audit requirements and enterprise buyer expectations.
Organizations with 25+ years of compliance experience recognize that gap analysis must be technically specific. "We need better security" is insufficient. "We lack documented evidence of quarterly access reviews, have no formal incident response plan with defined escalation procedures, and maintain no vendor inventory with risk classifications" identifies actionable remediation targets.
3) Build the Control Environment and Documentation
Document your control environment comprehensively: security policies addressing all applicable Trust Services Criteria, vendor management policies with risk assessment procedures, incident response plans with notification timelines, data protection controls including encryption standards and data classification schemes, access control procedures with review frequencies, change management processes with approval workflows, business continuity and disaster recovery plans.
Establish your system description: which systems are in scope, how you deliver services, data flows between systems and third parties, infrastructure components, personnel with access to production environments. Create risk management processes: documented risk assessment methodology, risk register with identified threats and assigned controls, monitoring procedures, control testing schedules.
4) Prepare for Audit and Vendor Questionnaires
Build evidence trails before questionnaires arrive. Implement logging and monitoring across infrastructure, maintain change logs with approval records, retain vendor contracts with security addendums, document incidents with root cause analysis and remediation actions, track access provisioning and deprovisioning with timestamps.
Train your team to understand how questionnaires map to controls. Security teams should be able to articulate how controls work, where evidence resides, and how effectiveness is validated. Operations teams should understand access management processes and incident escalation procedures. Leadership should recognize that questionnaire responses commit the organization to documented practices that auditors will verify.
Align responses to enterprise buyer expectations by anticipating questions about security controls, access controls, vendor management, incident response, control testing frequencies, risk assessment methodologies, and evidence collection processes. Use templates and standardized response libraries to ensure consistency across questionnaires while maintaining accuracy for your specific control environment.
SOC 2 Questionnaire: Practical Steps for Completion
Structuring Your Approach:
Categorize questionnaire items by control domain: Security controls, Access controls, Vendor management, Incident response, Data protection, System description, Audit preparation, Controls testing, Risk assessment. Assign internal owners for each domain. Security teams handle intrusion detection, encryption standards, and vulnerability management. IT operations handles access provisioning, access reviews, and system monitoring. Legal handles vendor contracts and data processing agreements. Compliance teams coordinate evidence collection and control documentation.
Set deadlines and track responses systematically. Research shows 55% of organizations struggle to get complete risk information on third parties and have trouble understanding the true risk profiles of their vendors. Enterprise buyers expect timely, complete responses. Delays signal operational immaturity or control gaps.
Interpreting the Questions:
For each question, identify the underlying control or risk being evaluated. "Do you enforce least-privilege access to production systems?" addresses access controls, separation of duties, risk management, and control environment maturity. The enterprise buyer wants to know: Do you grant access based on job function? How frequently do you review access? How quickly do you revoke access when employees leave? What prevents unauthorized privilege escalation?
"Do you have a vendor risk assessment process for third-party vendors with access to customer data?" addresses vendor management, data protection, third-party risk, and supply chain security. The buyer evaluates: Do you maintain a vendor inventory? How do you classify vendor risk? What due diligence do you conduct? How do you monitor vendor controls? What happens when vendors fail to meet security requirements?
Use your documented policies and system description to craft concise, specific answers. Where relevant, reference evidence. "We conduct quarterly access reviews documented in audit logs, with findings tracked in our ticketing system and remediation verified within 5 business days" demonstrates operational rigor. "We review access periodically" signals vague processes that likely lack consistent execution.
Sample Questions and Answer Structures
Question: "Describe how you detect, respond to, and report security incidents."
Answer Structure: "We maintain a documented incident response plan reviewed annually and tested through quarterly tabletop exercises. Our SIEM system generates alerts for suspicious activity based on defined detection rules. Incidents are classified by severity (Critical/High/Medium/Low) with corresponding response timelines. We notify affected customers within 24 hours of confirmed data exposure per our customer notification policy. Post-incident, we conduct root cause analysis, implement corrective controls, and update our risk register. Incident metrics are reviewed monthly by security leadership."
This answer demonstrates documented procedures, testing protocols, classification systems, notification commitments, remediation processes, and management oversight—everything an enterprise buyer and auditor will verify.
Question: "How do you manage access control to your systems?"
Answer Structure: "Access is provisioned based on documented role definitions with least-privilege principles. We enforce multi-factor authentication for all system access. Access reviews are conducted quarterly with results documented in our GRC platform. Administrative access requires secondary approval and is logged for audit purposes. Access is revoked within 4 hours of termination notification through automated deprovisioning workflows integrated with our HR system."
Question: "What vendor management process do you follow for third-party risk?"
Answer Structure: "We maintain a vendor inventory in our vendor risk management system with all third parties classified as Critical/High/Medium/Low risk based on data access, service criticality, and regulatory impact. Critical and High-risk vendors undergo security assessments including questionnaire completion and, where applicable, SOC 2 report review. Vendor contracts include security requirements, breach notification obligations, and audit rights. We conduct annual vendor reviews and continuous monitoring through security ratings. Vendor risks are tracked in our enterprise risk register with assigned ownership and mitigation plans."
Ensuring Alignment with Auditor Requirements
Although vendor questionnaires are not formal audits, your answers must reflect controls that would withstand audit scrutiny. SOC 2 Type 2 reports confirm that controls in place are working effectively over a period of time, with auditors testing both the design and operating effectiveness of internal controls over typically three to six months.
Reference auditor requirements when crafting responses: controls must be documented, implemented, tested for effectiveness, and supported by verifiable evidence. Use questionnaire completion as a readiness diagnostic. Questions you cannot answer confidently represent control gaps that will surface during audit. Keep documentation consistent across system descriptions, control matrices, data classification schemes, and control testing results.
Templates and Examples for Busy Teams
Questionnaire Response Template
Create a tracking template with columns for: Question | Relevant Control/Policy | Owner | Evidence Location | Status/Notes. This provides visibility into completion progress, identifies bottlenecks, and ensures no questions are overlooked. Teams with multiple concurrent questionnaires benefit from centralized tracking that prevents duplicate effort and ensures consistent responses.
Policy and Control Mapping Template
Develop a control matrix mapping internal controls to Trust Services Criteria and common questionnaire topics:
This matrix serves as both a questionnaire response guide and an audit preparation tool. When questionnaires ask about specific controls, you reference the matrix to locate relevant policies, evidence, and testing results.
Checklist for Questionnaire Readiness
- Questionnaire distributed to internal owners with assigned deadlines
- Each question analyzed for underlying control and mapped to policies
- Policies and procedures documented and approved
- Evidence collected, organized, and accessible
- Responses reviewed by security and operations leadership
- Supporting documentation (policies, system descriptions, evidence samples) prepared for potential follow-up
- Final responses submitted to vendor/client or uploaded to vendor risk portal
- Internal lessons learned captured for future questionnaire improvements
Post-Questionnaire: What Comes Next
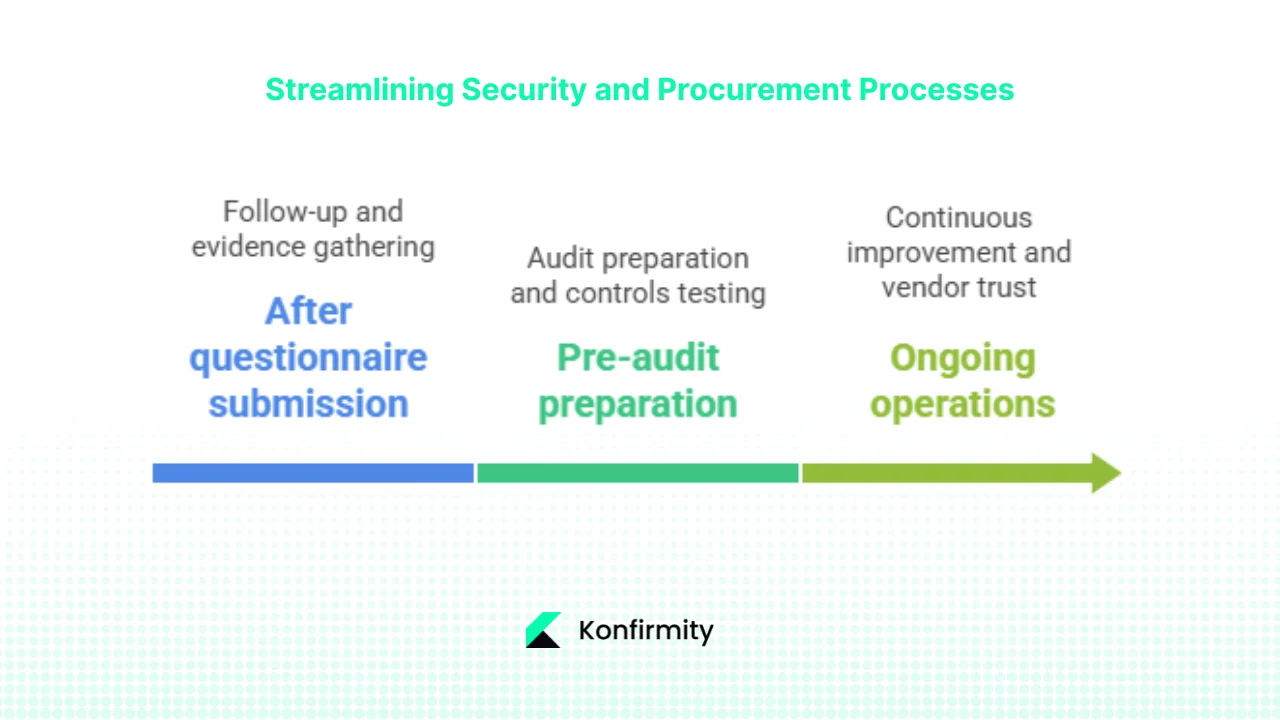
1) Follow-Up and Evidence Gathering
After questionnaire submission, enterprise buyers often request clarification or supporting evidence. Use your tracking template to quickly retrieve relevant documentation. If questions reveal control gaps, create remediation plans with specific actions, assigned owners, and target completion dates. Track remediation status and update your control matrix as controls are implemented.
Organizations that treat questionnaires as one-time exercises rather than continuous processes face repeated cycles of inadequate responses and delayed procurement. Build questionnaire readiness into your operational cadence.
2) Audit Preparation and Controls Testing
If you have not completed a SOC 2 audit, use questionnaire responses to prepare for formal examination. Auditors evaluate a sample of controls over a period of time, requiring demonstrated operational effectiveness. Conduct control testing to validate that controls work as documented: test access review completion and remediation timeliness, verify incident response procedures through tabletop exercises, validate vendor risk assessments are completed on schedule, confirm change management approvals are documented.
Schedule recurring internal reviews: quarterly risk assessments, semi-annual incident response drills, annual policy reviews, continuous vendor monitoring, regular system description updates as infrastructure or services change.
3) Continuous Improvement and Vendor Trust
Use the questionnaire process as a living asset rather than a point-in-time burden. Maintain updated control mapping, evidence repositories, vendor risk summaries, incident response metrics, and access review results. Organizations with mature programs maintain a "vendor trust kit"—standardized documentation packages that include current policies, control matrices, recent audit reports, and evidence samples that can be shared with enterprise buyers upon request.
This operational readiness accelerates sales cycles, reduces questionnaire completion time from weeks to days, and positions your organization as a mature, security-focused vendor. Enterprise buyers recognize vendors who respond quickly, thoroughly, and confidently versus those who struggle to articulate basic security practices.
Key Concepts and Questionnaire Mapping
Understanding how technical concepts map to questionnaire items allows you to recognize what buyers are actually evaluating:
- Security Controls: Questions about firewalls, intrusion detection systems, encryption standards, multi-factor authentication, vulnerability management, and endpoint protection. Enterprise buyers verify you implement defense-in-depth strategies.
- Trust Service Criteria: Questions are often explicitly organized by Security, Availability, Processing Integrity, Confidentiality, and Privacy. Understanding which criterion each question addresses helps you provide focused, relevant responses.
- Auditor Requirements: Questions about how you test controls, monitor effectiveness, collect evidence, and report results align with what auditors will verify during SOC 2 examinations.
- Risk Management: Questions about risk assessment methodology, risk registers, threat identification, control assignment, and risk monitoring evaluate your systematic approach to identifying and mitigating security risks.
- Control Environment: Questions about governance structure, policy frameworks, leadership oversight, organizational culture, and accountability mechanisms assess the foundation supporting your security program.
- Data Protection: Questions about data classification, encryption (at rest and in transit), data retention, secure deletion, and access controls for sensitive data verify you handle customer information appropriately.
- Vendor Management: Questions about third-party due diligence, vendor risk classification, contract security requirements, continuous monitoring, and vendor incident response evaluate your supply chain security.
- Incident Response: Questions about detection capabilities, classification systems, escalation procedures, notification timelines, root cause analysis, and corrective actions assess your ability to manage security events.
- Access Controls: Questions about provisioning processes, least-privilege principles, access review frequencies, multi-factor authentication, privilege management, and deprovisioning procedures verify you control who accesses what systems and data.
- System Description: Questions about infrastructure, architecture, data flows, service delivery, and boundaries establish scope for risk evaluation and control assessment.
Conclusion
The SOC 2 questionnaire serves dual purposes: it functions as a vendor risk gate that determines whether you advance through enterprise procurement, and it provides a diagnostic tool for evaluating your control readiness before formal audit. Organizations that treat questionnaires as isolated sales obstacles rather than operational readiness assessments repeatedly face delayed deals, failed audits, and security incidents that expose the gap between documented claims and actual practices.
Using questionnaires, control mapping templates, evidence repositories, and systematic documentation processes allows you to both win enterprise deals and achieve audit success. The controls, policies, evidence, and testing procedures required to answer questionnaires accurately are the same controls auditors will evaluate during SOC 2 examinations. Building these operational capabilities creates a foundation for genuine security rather than performative compliance.
Maintain a proactive approach: keep documentation current, policies reviewed and updated, evidence collection automated where possible, and questionnaire responses integrated into your standard vendor risk and sales operations workflows. Organizations with 6,000+ completed audits recognize that questionnaire readiness reflects operational maturity, and operational maturity determines both market competitiveness and security effectiveness.
FAQ
1) What are the 5 criteria for SOC 2?
The five Trust Services Criteria for evaluating SOC 2 compliance are Security, Availability, Processing Integrity, Confidentiality, and Privacy. Security is mandatory for all SOC 2 reports, while the other four criteria are included based on the nature of your services and customer requirements.
2) What is the SOC 2 compliance checklist?
A SOC 2 compliance checklist is a structured set of tasks your organization completes to prepare for audit or vendor questionnaire completion. Typical items include: defining scope and applicable Trust Services Criteria, conducting gap analysis to identify control deficiencies, documenting policies and procedures, implementing required controls, establishing evidence collection processes, conducting control testing to verify effectiveness, and selecting a qualified auditor for formal examination.
3) How to evaluate a SOC 2 report?
When evaluating a SOC 2 report (whether your own or a vendor's), assess: the scope including which Trust Services Criteria are covered and which systems are included, the report type (Type 1 for design evaluation or Type 2 for operational effectiveness), the auditor's opinion (unqualified opinions indicate controls met criteria; qualified, adverse, or disclaimer opinions indicate issues), the system description to understand service delivery and boundaries, the detailed tests of controls and results including any exceptions noted, and the time period covered to ensure adequate overlap with your evaluation needs.
4) What is a SOC 2 Type 2 assessment?
A SOC 2 Type 2 assessment is an independent audit that evaluates both the design and operating effectiveness of a company's security controls over a specific period, usually three to 12 months. Unlike Type 1 reports that assess control design at a single point in time, Type 2 reports provide stronger assurance to enterprise clients by demonstrating that controls operated effectively throughout the examination period. Type 2 assessments require documented evidence of control operation, systematic testing by auditors, and validation that exceptions were identified and remediated appropriately.





.svg)






.svg)
.svg)